1. Introduction
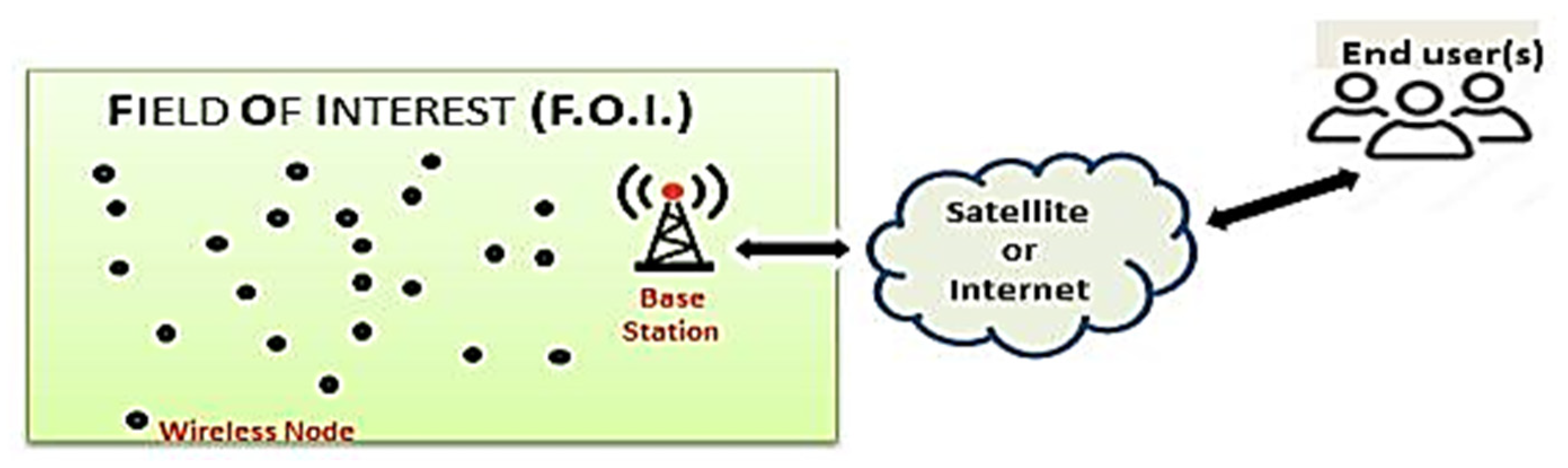
A typical Wireless Sensor Network (WSN) consists of a set of wirelessly interconnected electronic devices, called sensor nodes, along with at least one sink node called base station (BS),which are placed over a given area that is referred as Field of Interest (FOI), as illustrated in
Figure 1 [
1,
2].
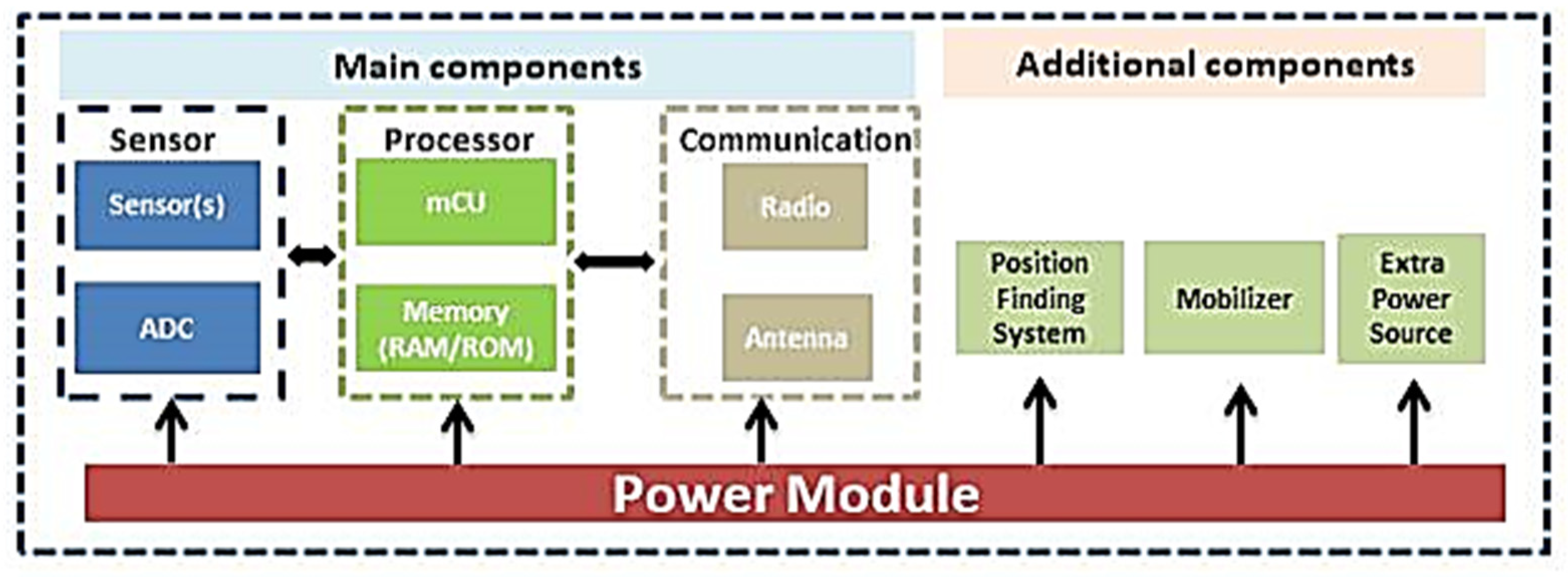
As depicted in
Figure 2, a typical sensor node consists of the following main components:
Sensing Module: It contains appropriate sensors that are able to monitor ambient conditions.
Processing Module: It typically contains a microcontroller or microprocessor and may also comprise additional memory and processing units. The processing unit plays a critical role in handling the data collected by the sensing unit and controlling the data storage and/or transmission.
Communication Module: It is responsible for establishing and maintaining communication between the sensor node and other sensor nodes and/or a BS.
Power Module: This module refers to the energy source that provides the necessary electrical power to the sensor node. Since sensor nodes in WSNs are often deployed in remote or generally difficult to approach locations, they must rely on self-contained power sources. Typically, this component is a battery.
A sensor node, may also contain a position finding system and an additional source of energy. Furthermore, it may be mobile thanks to the use of an appropriate motion mechanism or system.
WSNs, taking advantage of the collaborative use of the sensing, processing and communication abilities of their sensor nodes and the BS, are able to monitor ambient conditions in any kind of FOIs. This is why, WSNs, although initially invented exclusively for military use, nowadays are the basis for Internet of Things (IoT) and have an ever increasing variety of applications [
4]. Particularly, in urban sector, WSNs serve various applications concerning smart homes, smart cities, security and surveillance, transportation, and building health monitoring [
5,
6,
7,
8,
9]. In flora and fauna, greenhouse monitoring, crop monitoring and livestock farming enjoy the benefits of the usage of WSNs [
10,
11,
12]. Likewise, WSNs are applied in healthcare applications such as patient monitoring and home assisting systems [
13,
14]. In Industry WSNs are used in machinery health monitoring, robotics and logistics [
15,
16,
17]. WSNs are also used in environmental applications such as water monitoring, air monitoring and emergency alerting [
18,
19]. Battlefield surveillance, combat monitoring, and intruder detection are the main military applications of WSNs [
20].
On the other hand, the operation of WSNs is obstructed due to certain limitations of their sensor nodes, inherent weaknesses of wireless communications and other application-related problems, thus posing numerous challenges and optimization needs [
21,
22]. For instance, WSNs comparatively to wired networks, are more likely to face congestion due to buffer overflow of their sensor nodes or/and saturation of the wireless communication channels that takes places when an excessive number of sensor nodes attempt to simultaneously use them [
23]. Appropriate methods for congestion avoidance that try to prevent the occurrence of congestion [
24,
25], and congestion control that attempt to alleviate existing congestion, are used [
26]. Also, in WSNs, connectivity loss occurs frequently because of factors such as interference, node malfunctions, and energy depletion. At the same time, the maximization of coverage and/or k-coverage is very important. For this reason, the use of specialized control schemes is necessitated [
27,
28,
29]. Likewise, security challenges are greater in WSNs, because sensor nodes may operate unattended and be connected with numerous devices within the context of zero-trust security, thus dictating the use of special methodologies [
30,
31,
32]. Similarly, the attainment of high QoS is more difficult in WSNs than in conventional networks due to various factors such as the limited resources of the sensor nodes, the dynamic nature of networks, the unbalance of traffic, the heterogeneity of nodes, scalability requirements, differences in message priorities, the variety of traffic types, and the coexistence of various sinks [
33]. Additionally, in cases involving multimedia data, supplementary control strategies have to be applied [
34,
35,
36,
37].
Yet, the particularly constrained energy adequacy of the sensor nodes is by far the most important among all weaknesses that obstruct the operation of WSNs. Actually, energy scarcity is caused by the fact that in most WSNs the sensor nodes are powered by batteries that are difficult or even impossible to either recharge or replace. In a WSN the energy insufficiency of its nodes is a mostly severe concern because it may result to the rapid cessation of their operation and thus the gradual failure of communications within the network until the overall WSN collapses. This is why, the enhancement of energy sustainability of WSNs is necessitated [
38].
In order to extend the lifetime of sensor nodes, the elimination of the energy waste that is caused by various phenomena such as idle listening, overhearing, packet collision, interference, control packet overhead, and over-emitting is necessitated [
39]. Actually, there are numerous hardware-based and algorithm-based methods that pursue energy sustainability of WSNs via not only energy saving but also energy harvesting, or even wireless energy transfer [
38,
39,
40,
41,
42,
43,
44,
45]. Among them, the use of routing protocols that are energy efficient has proven to be a widely used energy saving method, because sensor nodes consume the most of their residual energy when they transmit and route data [
46].
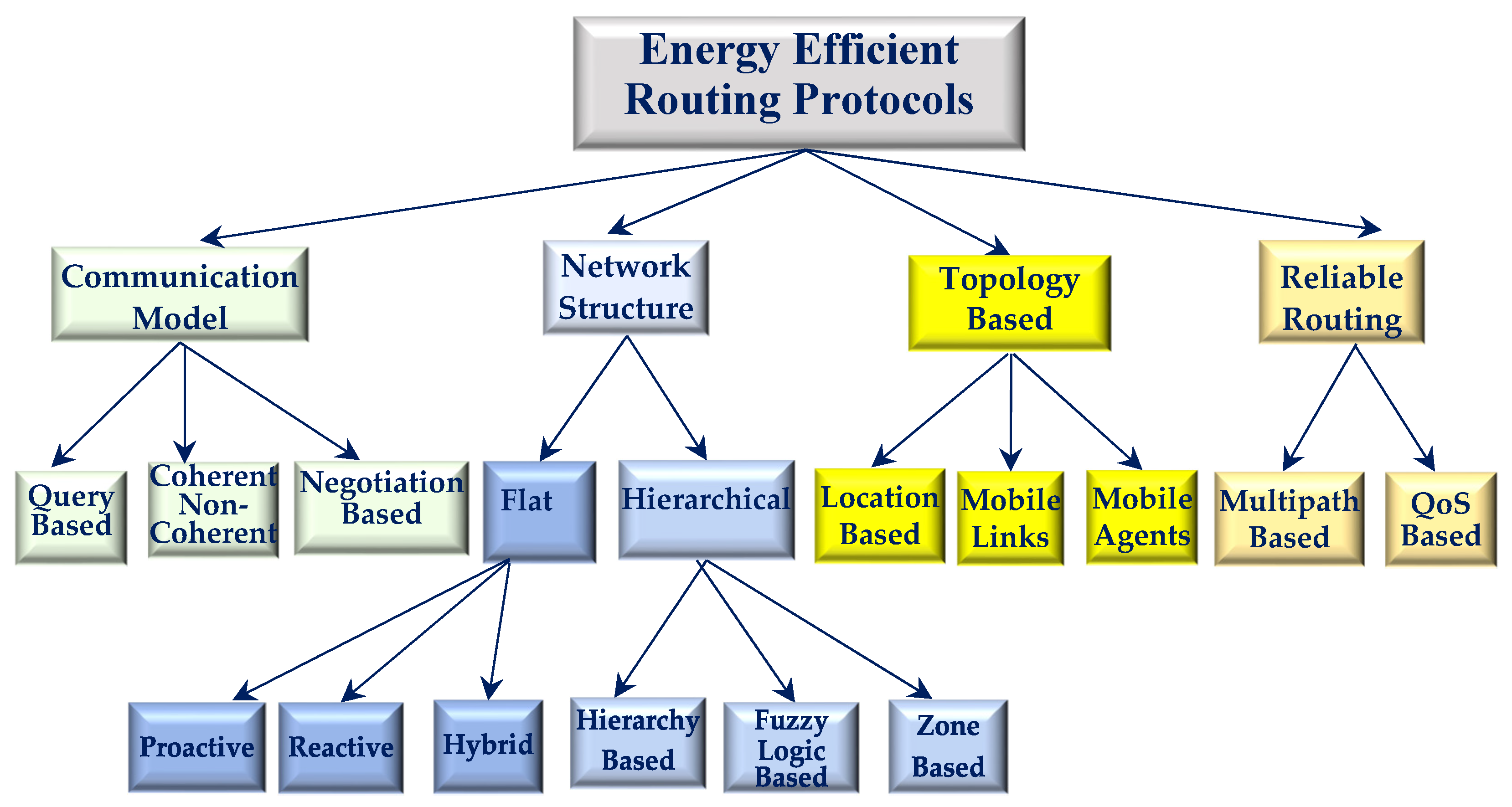
According to their organizational or operational features, the energy efficient routing protocols are classified into four main categories that namely are Communication Model, Network Structure, Topology, and Reliable Routing and various subcategories, as illustrated in
Figure 3 [
47].
Specifically, protocols belonging to the Network Structure category are classified as either Flat or Hierarchical [
47,
48]. Flat protocols, which are further classified as proactive, reactive or hybrid, consider all network nodes as being equal entities that have unique global addresses. These protocols perform well in WSNs that comprise of few sensor nodes. Yet, such protocols have extremely low scalability. On the other hand, in hierarchical protocols, which are further classified as hierarchy based, zone based, or fuzzy logic based, sensor nodes are treated according to the place they hold within the hierarchical architecture of the network. Specifically, all network nodes are distributed in individual groups, called clusters, each of which has one cluster head and a number of cluster nodes. Hierarchical protocols are generally considered to be the most popular among all types of energy efficient routing protocols, because they enable data aggregation, reduce the communication overhead, and achieve great scalability. For these reasons, hierarchical protocols are ideal for large scale WSNs that have heavy communication load and cover wide FOIs [
49,
50]. The formation and composition of clusters, and the selection of cluster heads are common challenges for the protocols of this kind [
47].
This article focuses on hierarchical energy efficient routing protocols, and particularly on hierarch-based protocols that are based on LEACH, which is considered to be the forerunner protocol of this type of protocols. In
Section 2, LEACH is studied. In
Section 3, some of the most well-known descending of LEACH protocols, T-LEACH included, are investigated. In
Section 4, a novel protocol of this kind, named T-LEACH
SAS is introduced. In
Section 5, the performance of T-LEACH
SAS is compared against that T-LEACH via simulation tests performed. Finally, in
Section 6 concluding remarks are presented.
2. LEACH Protocol
Low Energy Adaptive Clustering Hierarchy (LEACH) [
51] is one of the first and most well-known hierarchical protocols. Its main objective is to extend the lifetime of the sensor nodes that are disseminated within clusters in WSNs. Specifically, given that within every cluster the cluster head consumes much more energy than the rest cluster nodes, LEACH aims to perform the selection of the cluster heads among the cluster nodes evenly.
LEACH adopts a two-phase cycle consisting of the set-up phase and the steady-state phase in order to achieve efficient distribution and coordination of the clusters sensor nodes in a WSN.
In the set-up phase, the key goals are the creation of clusters, the selection of the cluster heads and the creation of a TDMA (Time Division Multiple Access) schedule for the communication of the cluster head with its cluster nodes. Within every cluster, all nodes participate in a procedure to elect the appropriate cluster head. This procedure is initiated by generating a random priority value ranging from 0 to 1. If this value does not exceed the randomly generated number T(n), the node is selected to be the cluster head. The value of T(n) is calculated via the following formula:
n ∊ G,
where P denotes the percentage of the cluster nodes to become cluster heads, r represents the number of current round and G stands for the total number of the cluster nodes that have not been elected as cluster heads during the 1/P previous rounds. According to this formula, once a node has been elected as a cluster head in a given round, it cannot be selected as a cluster head again in the subsequent 1/P rounds. This technique ensures an equitable selection of cluster heads and a better uniform distribution of energy consumption for the network nodes. The ideal proportion of cluster heads has been experimentally found to be equal to 5%. Whenever a node becomes a cluster head, it transmits an advertising (ADV) message to the rest of the nodes in the network. Each node that receives this message and wants to participate in the specific cluster, sends a replying (RPL) message back to the designated cluster head. This sequence of actions results in the establishment of clusters with their respective cluster heads. The cluster head then proceeds to create a TDMA schedule, which is subsequently shared with the nodes that are members of its cluster. This TDMA schedule determines the specific time that each node is both prompted and allowed to transmit data. As soon as the TDMA schedule has been defined the set-up phase is finalized.
During the steady-state phase, data propagation occurs among nodes and their respective cluster heads, as well as amid cluster heads and the base station. The nodes send their data to the relative cluster heads based on the designated timeslots specified in the TDMA schedule. During the time slot of every node, all of the rest nodes that belong to the same cluster reduce their energy consumption by being inserted into a low-power state. This approach not only effectively prevents congestion but also conserves the energy stored in the nodes' batteries. After the cluster head has gathered the data from its cluster nodes, it utilizes the TDMA schedule to send these aggregated data to the base station, ensuring efficient data transmission.
As highlighted earlier, LEACH effectively balances the cluster head election process across network nodes, thereby extending the overall network lifespan. Notably, it does so without necessitating global network knowledge. Additionally, by enabling a TDMA schedule, the network avoids data collisions during transmissions, enhancing network efficiency.
However, it's worth noting that LEACH does not consider the remaining energy levels of nodes when electing cluster heads. Consequently, nodes with low energy reserves have the same probability of becoming cluster heads as those with ample energy. Also, in LEACH clustering is random and consequently unbalanced, because not only the number but also the position and the formation of clusters is unsystematic. Moreover, LEACH may not be suitable for networks deployed in wide areas due to its reliance on single-hop routing, which is impractical for large scale WSNs. Furthermore, the dynamic clustering approach is associated with higher overhead.
3. LEACH-Based Energy Efficient Routing Protocols
It is noteworthy that although LEACH was introduced in the beginning of 21
st century, numerous energy efficient protocols keep on being proposed every year since then, as modifications and optimizations of LEACH [
47,
52,
53,
54,
55,
56,
57,
58]. Many of these LEACH descendants have proven to enhance the operation of their predecessor. Yet, these protocols have different pros and cons when compared in terms of not only their energy efficiency but also many other features such as scalability, overhead, load balance, latency, complexity, cluster formation, location information, fault tolerance modulation techniques, communication model , and channel encoding [
50]. Also, in order to perform the communication among each cluster head and the base station, some of these protocols utilize single-hop routing while other ones use the multi-hop routing which is necessitated in large scale WSNs. Consequently, based on the above considerations, it is obvious the selection of the most suitable hierarchical routing protocol is application dependent. In what follows in this section, various descending protocols of LEACH are indicatively referred as examples of reference.
Threshold-LEACH (T-LEACH) [
59] is a single hop routing protocol. Similarly to LEACH, T-LEACH also strives to extend the lifetime of a WSN by decreasing the energy consumption that is associated with data transmission and aggregation. Yet, contrary to LEACH where cluster heads are selected with a certain probability in each round, in T-LEACH new cluster heads are selected only when the residual energy of the existing cluster heads becomes lower than a specific energy threshold. In this way, T-LEACH reduces the frequency of cluster head changes in order to decrease the energy that is consumed due to the message transmission that takes places every time that a new cluster head is selected and broadcasts its selection to the rest cluster nodes. It has experimentally been demonstrated that T-LEACH achieves higher energy savings than LEACH. On the other hand, the configuration and utilization of the appropriate threshold value can be challenging and it may be associated with additional communication overhead.
LEACH-Balanced (LEACH-B) [
60] is a single hop routing protocol. It aims to balance the formation of clusters by taking into consideration both the residual energy of the sensor nodes and the desired proportion of cluster heads in the whole network. The total number of cluster heads is defined by the product
n ∙
p, where
n represents the total number of network nodes and
p symbolizes the desired percentage of the cluster heads. The first cluster heads are selected randomly by a procedure similar to that adopted by LEACH. All cluster heads are sorted according their residual energy. If the number of the randomly nominated cluster heads is lower than the product
n ∙
p, then some normal network nodes are selected as cluster heads. If this number is larger than the product
n ∙
p, then cluster heads with lower energy are one by one converted to normal network nodes until the number of cluster heads becomes equal to the product
n ∙
p. LEACH-B achieves energy balance in cluster head selection and cluster formation. Yet, it suffers from high complexity, high overhead, and low scalability.
Centralized-LEACH (LEACH-C) [
61] is a single hop routing protocol. It has a steady phase which is alike that in LEACH, and a setup phase which differs from that of LEACH, since the cluster heads are selected by the base station. Specifically, all nodes report to the base station both their location and the quantity of their residual energy. In this way, the base station acquires global knowledge of the status of its network nodes and processes the relative information, in order to create clusters that consume less energy during transmission. The base station calculates the average residual energy of the nodes and extracts from the list with eligible to become cluster heads during the specific round the nodes whose remaining energy is less than the average energy. Upon the formation of clusters and the selection of cluster heads, the base station broadcasts the identities of the cluster heads that have been selected. LEACH-C performs better than LEACH in terms of cluster formation and energy efficiency. However, not only it requires the knowledge of the position of each node, but also it is associated with the problem of the early death of cluster heads with low energy, since it does not guarantee that the nodes having the highest energy reserves are selected as cluster heads.
LEACH-CE (LEACH-Centralized Efficient) [
62] is another single hop routing protocol. Actually, it is an improved version of LEACH-C in the sense that it eradicates the main disadvantage of LEACH-C, i.e. the early deaths of the cluster heads. Practically, LEACH-CE follows the same process as in LEACH-C only during the first round, until the clustering is completed. Next, the base station defines as cluster head in every cluster the node having the highest residual energy among the cluster nodes.
LEACH-D [
63] is a multi-hop routing protocol. In this protocol the selection of the cluster heads is performed by considering the density distribution of nodes along with their residual energy. Specifically, the nodes that have high priority in being selected as cluster heads are those that have high energy residues and are located in high density areas. During the clustering phase, each cluster head node decides what the radius of its own cluster will be according to its distance from the base station and the degree of connectivity. The nodes that have not been selected as cluster heads, select the proper cluster to join by taking into account their distance to the neighboring cluster heads and the residual energy of these cluster heads. Finally, the cluster heads transmit their data to the base station via multi-hop communication. LEACH-D performs fine regarding energy efficiency and scalability. Yet is associated with high complexity and overhead.
In LEACH-L [
64], which is a multi-hop routing protocol, cluster heads are classified in two categories, i.e. the ones that are located close to the base station and those that are positioned far away from the base station. The cluster heads that belong to the 1
st category transmit their data directly to the base station. Yet, the cluster heads that belong to the 2
nd category are positioned far away from the base station transmit their data to the base station via one relay node that is chosen, among the cluster heads belonging to the 1
st category, based on its residual energy and its distance from the base station. LEACH-L achieves remarkable energy saving especially in large scale WSNs in which the base station is located in distant position. On the other hand, the requirement of location knowledge is associated with higher communication load and complexity.
In Two Levels-LEACH (TL-LEACH) [
65], which is a multi-hop routing protocol, a two-level hierarchy is adopted. Specifically, the cluster heads located close to the base station are characterized as primary while cluster heads located away from the base station are characterized as secondary. The data that are sensed by cluster nodes are initially collected by the corresponding secondary cluster heads, which next aggregate, partially process and finally transmit the resultant data to the primary cluster heads. Similarly, primary cluster heads perform additional local processing and finally transmit the final data directly to the base station. The advantage of this two-level hierarchy is that the majority of data transmissions is performed over short distances and consequently nodes consume less energy during transmissions and therefore achieve longer lifetime. The disadvantage of this hierarchy is that the primary cluster heads are associated with heavier communication load and consequently end to be depleted faster than the secondary cluster heads.
Improved-LEACH (I-LEACH) [
66] aims at achieving high energy efficiency in both cluster formation and cluster head selection. Specifically, the optimal number of clusters is found based on the locations of nodes and the base station. Additionally, during cluster head election, an appropriate threshold used considers for every node its residual energy, the number of its neighboring nodes and its distance from the base station. According to the value of this threshold, a node is preferred to be elected as cluster head, when having many neighbors, residual energy greater than the average energy of network nodes and be located closer to the base station. I-LEACH achieves network stability and energy efficiency. On the other hand, it has not any mechanism for data aggregation.
Equalized Cluster Head Election Routing Protocol (ECHERP) [
67] performs cluster head selection based on the Gaussian Elimination algorithm. Specifically, the specific algorithm is used in order to compute for all possible node combinations, the energy outflow that every node is going to have if being a cluster head during the next round. Eventually, ECHERP selects the arrangement of cluster heads that minimizes the overall consumption of energy. ECHERP performs great in terms of energy efficiency and scalability. Nevertheless, it does not take into consideration metrics related to QoS and time constraints.
Enhanced Heterogeneous LEACH-(EHE-LEACH) [
68] pursues energy efficiency based on the use of a distance threshold. Specifically, nodes whose distance from the base station is below the value of the specific distance threshold, i.e. nodes positioned nearby the base stations, do not form clusters. Instead, they communicate directly with the base station. All other nodes, which are located in more distant positions, are grouped in clusters. Within each one of these clusters, there are some advanced nodes, which have higher energy reservoirs than the rest cluster nodes. EHE-LEACH provides advanced nodes with higher probability to be elected as cluster heads, and subsequently extends the network lifetime. However, non-clustered nodes do not adopt any sleep-awake scheduling and consequently have relatively high energy consumption.
LEACH-Expected Residual Energy (LEACH-ERE) [
69] makes use of the so-called Expected Residual Energy (ERE) value, which represents for every single node its anticipated residual energy in case that this node is elected as a cluster head. Specifically, the cluster heads are elected at the end of every round by making use of both a predefined threshold, which expresses the percentage of the tentative nodes, and a function that generates a random number between 0 and 1. The cluster nodes that are associated with greater generated numbers of the threshold become cluster heads and calculate the probability, utilizing a fuzzy inference system, with inputs the residual energy and the ERE value. A bigger probability results in a higher possibility to be elected as a cluster head. LEACH-ERE achieves stable performance. On the other hand, it provides no consideration of distance to the BS, resulting in early death of faraway nodes.
Orphan LEACH (O-LEACH) [
70], which is a single-hop routing protocol, introduced the concept of orphan nodes that characterizes the nodes that have not been assigned to any cluster head. O-LEACH proposes two different schemes. In the first of them, orphan nodes transmit the data they sense to adjacent nodes which, operating as gateways, aggregate and forward these data to the base station. In the second scheme, sensor nodes lying in an uncovered area of the network compose a sub-cluster and choose a cluster head based on the shortest distance from the gateways. The orphan node that is located closer to the gateway is selected to be the cluster head. O-LEACH is evinced to outperform LEACH in terms of energy efficiency, scalability connectivity and coverage. However, it suffers because of the rapid energy drainage of the nodes that are positioned far away from the base station, as a consequence of single-hop routing.
In Quadrature -LEACH (Q-LEACH) [
71] the field of interest is divided into four quadrants based on information location of networks nodes, so that cluster balancing is achieved. Every node randomly picks a number between 0 and 1, while in each one of the four quadrants a threshold between 0 and 1 is set. If the random number picked by a node is less than the threshold of the network quadrant it belongsτο and the predefined number of cluster heads for this quadrant has not been filled, then this node turns into a cluster head and broadcasts this information to the network. Based on the Received Signal Strength Indicator (RSSI) of these broadcast messages, each one of the rest network nodes decides the cluster head within their quadrant to be associated with and communicates with this cluster head during its own TDMA slot. In Q-LEACH, cluster head election is energy efficient and the overall network lifetime is extended comparatively to LEACH. Nevertheless, it is associated with higher probability of energy holes’ creation
In Multi-hop routing LEACH (MR-LEACH) [
72], the field of interest is divided into different levels, according to the number of hops needed to reach the base station. Each one of these levels includes its own clusters, while all clusters have the same size. In each one of these layers the cluster heads collaborate with cluster heads of their adjacent layer. Specifically, the data that are aggregated from the more distant clusters are transmitted to the base station by multi-hop routes via the cluster heads of layers being located nearer to the base station. Nodes having greater energy residues are selected to be cluster heads while the rest nodes choose their own cluster head based on RSSI. The communication among the base station and the cluster heads is performed by using an appropriate TDMA schedule. The use of multi-hop paths MR-LEACH achieves high energy efficiency. The rapid energy drainage of the nodes close to the base station is its main disadvantage.
4. Threshold LEACH with Sleep-Awake Scheduling Protocol
As aforementioned, this article proposes a novel hierarchical protocol for energy efficient routing in WSNs, named T-LEACH with sleep-awake scheduling (T-LEACHSAS). In what follows in this section, an overview of T-LEACHSAS is provided regarding first its operation and next its architecture.
4.1. Overview of T-LEACHSAS Operation
T-LEACHSAS protocol aims to achieve energy conservation in both the selection of cluster heads and the operation of non-cluster head nodes. In order to do so, it combines an energy threshold-based approach for the selection of cluster heads along with a sleep-awake scheduling mechanism for managing the energy states of sensor nodes.
Specifically, in T-LEACH
SAS protocol, following [
53], as long as the residual energy of an existing cluster head exceeds the value of a predefined threshold, this node remains being a cluster head. A round for the election of a new cluster head is initiated as soon as the remaining energy of a cluster head becomes less than this threshold.
At the same time, T-LEACHSAS adopts the usage of a Sleep-awake scheduling which is a well-known energy management technique employed in WSNs, where nodes periodically alternate between active (awake) and inactive (sleep) states. The nodes during the awake periods perform sensing, data transmission, and other tasks before returning to a low-power sleep mode, while in sleep mode, the nodes skip the rest of the processing for that round, conserving energy. Practically, in T-LEACHSAS, a scheduler assigns specific time slots for when nodes should be awake and when they should sleep. This can be on a periodic basis, in order to let a node be awake for certain duration and sleep all rest time. This scheduling strategy plays a critical role in conserving energy and extending network longevity.
The operation of T-LEACHSAS is performed in two phases, which namely are the setup phase and the steady state.
As soon as the operation of T-LEACHSAS begins the setup phase is initiated. During this phase, the formation of clusters takes place and each sensor node decides whether to become or not a cluster head, based on a probability model that considers the node's residual energy and the desired percentage of cluster heads within the overall network. This strategy aims to perform rotation of cluster heads in a way that distributes energy consumption evenly across the network nodes. Each new cluster head broadcasts its status to other nodes in an advertisement message, which includes its identity and possibly its location (if this is known). The nodes in the network that are not selected as cluster heads, receive these advertisements, choose which cluster to join and then notify their decision to the corresponding cluster heads. In this way, each cluster head forms its cluster. Following cluster formation, each cluster head creates a TDMA schedule, which is crucial for the sleep-awake mechanism. This schedule assigns each member node a specific time slot for transmission, allowing them to know when to be awake for transmitting data and when they can turn off their radio components to save energy. Finally, cluster heads broadcast this schedule to their cluster members. As soon as the set up phase is completed, the steady state is initiated.
During the steady state phase, sensor nodes monitor their ambient conditions. During their allocated time slot, and if the value of sensed data exceeds a predefined threshold, sensor nodes wake up, transmit their data to their cluster head and then go back to sleep. Otherwise, if the value of sensed data does not exceed the specific threshold, nodes stay asleep. During each round, cluster heads collect the data that have been transmitted to them from their cluster members, perform data aggregation to remove redundancies, and then transmit the aggregated data to the base station, further reducing energy consumption and enhancing data transmission efficiency. Nodes and cluster heads update their energy levels after each round, and if any node depletes its energy, it is identified as a dead node and is henceforth excluded from any participation in the overall protocol operation during all future rounds. This continuous monitoring and adaptation of energy usage, coupled with the threshold-based data transmission and sleep-awake scheduling, significantly enhance the network's overall energy efficiency and prolong its operational life.
4.2. Overview of T-LEACHSAS Architecture
The high level design (HLD) of T-LEACHSAS protocol involves structuring the system into several key components, each one of them being responsible for distinct aspects of the aforementioned operation of the protocol, as shown below:
-
Network initialization module
- i.
Objective: Establishment of the initial state and parameters of the network.
- ii.
Components:
- o
Node initialization: Assignment of initial energy to each sensor node;
- o
Threshold Configuration: Definition of thresholds for data transmission;
-
Round management module
- i.
Objective: Network operation management in rounds, each of one consisting of multiple phases.
- ii.
Components:
- o
Round scheduler: Triggering of the start of a new round and management of its progression.
- o
Cluster Management: Activation of the processes for cluster formation and cluster head selection.
- o
Schedule Management: Supervisory control of the creation and distribution of sleep-awake schedules.
-
Cluster formation module
- i.
Objective: Organization of network nodes into clusters with designated cluster heads.
- ii.
Components:
- o
Cluster head selection algorithm: Definition of which nodes will become cluster heads based on their remaining energy.
- o
Cluster assignment: Allocation of non-cluster head nodes to their relative cluster heads.
- o
Advertisement Mechanism: Management of the messages that cluster heads broadcast in order to notify their status to other nodes.
-
Sleep-awake schedule module
- i.
Objective: Optimization of energy consumption by controlling when nodes are active (awake module).
- ii.
Components:
- o
Schedule creator: Schedule creation by cluster heads dictating when their member nodes should be awake to measure and transmit data and when they should be asleep.
- o
Schedule distributor: Distribution of the sleep-awake schedule by cluster heads the to their cluster members.
-
Data transmission module
- i.
Objective: Handling of data sensing, processing, and transmission.
- ii.
Components:
- o
Threshold Checker: Checking of whether the value of sensed data exceeds or not the pre-defined threshold.
- o
Transmission Controller: Management of data transmission from nodes to their relative cluster heads, and sleep-awake status of nodes based on the sleep-awake schedule and threshold check.
-
Data aggregation and communication module
- i.
Objective: Data aggregation in cluster heads and communication with the base station.
- ii.
Components:
- o
Data Aggregator: Aggregation of data transmitted from nodes to their cluster heads in order to eliminate redundancies.
- o
BS Communicator: Transmission of aggregated data from cluster heads to the base station.
-
Energy management module
- i.
Objective: Monitoring and management of the energy consumption of nodes.
- ii.
Components:
- o
Energy tracker: Tracking of energy consumption for all activities of nodes.
- o
Low Energy Detector: Detection of nodes having low or zero residual energy.
-
Network monitoring & maintenance module
- i.
Objective: Evaluation of the ongoing well-being and efficiency of the network.
- ii.
Components:
- o
Performance Monitor: Collection and analysis of network performance metrics.
- o
Visualization Tools: Visual representation of the performance of the network.
5. Comparative Performance Evaluation
With the intention of appraising the efficiency of T-LEACH
SAS, its performance was comparatively evaluated against that of T-LEACH. The selection of T-LEACH as the protocol to compare the protocol proposed in this research article with, is made based on that the two protocols have many similarities while T-LEACH has already been demonstrated to outperform LEACH [
58].
In the simulation tests performed in MATLAB software platform it was supposed that a specific number of sensor nodes having initial residual energy equal to 0.5 J are distributed within a 200 m x 200 m square field of interest, while the WSN includes also one base station that receives the data sent by the sensor nodes.
The metrics evaluated are the number of sensor nodes remaining alive, the total residual energy in network and the total number of data bits that are transmitted by the network nodes to the base station per simulation round, while the influence of the density of the nodes, and the location of the base station within the field of interest, was investigated. In order to achieve higher accuracy in simulation results, 150 different network topologies were considered in each one of all scenarios examined. In what follows in this section the simulation results are both presented and discussed.
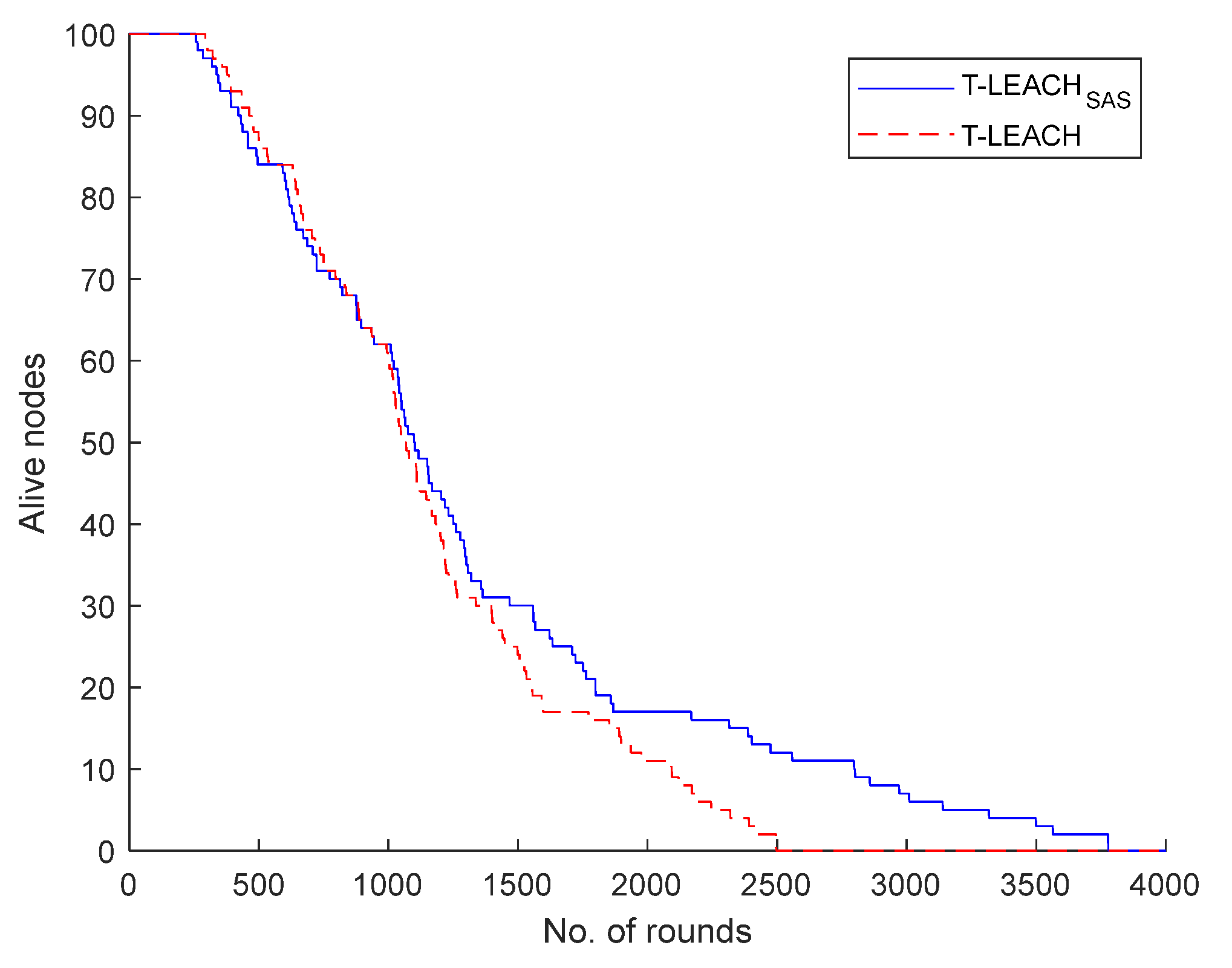
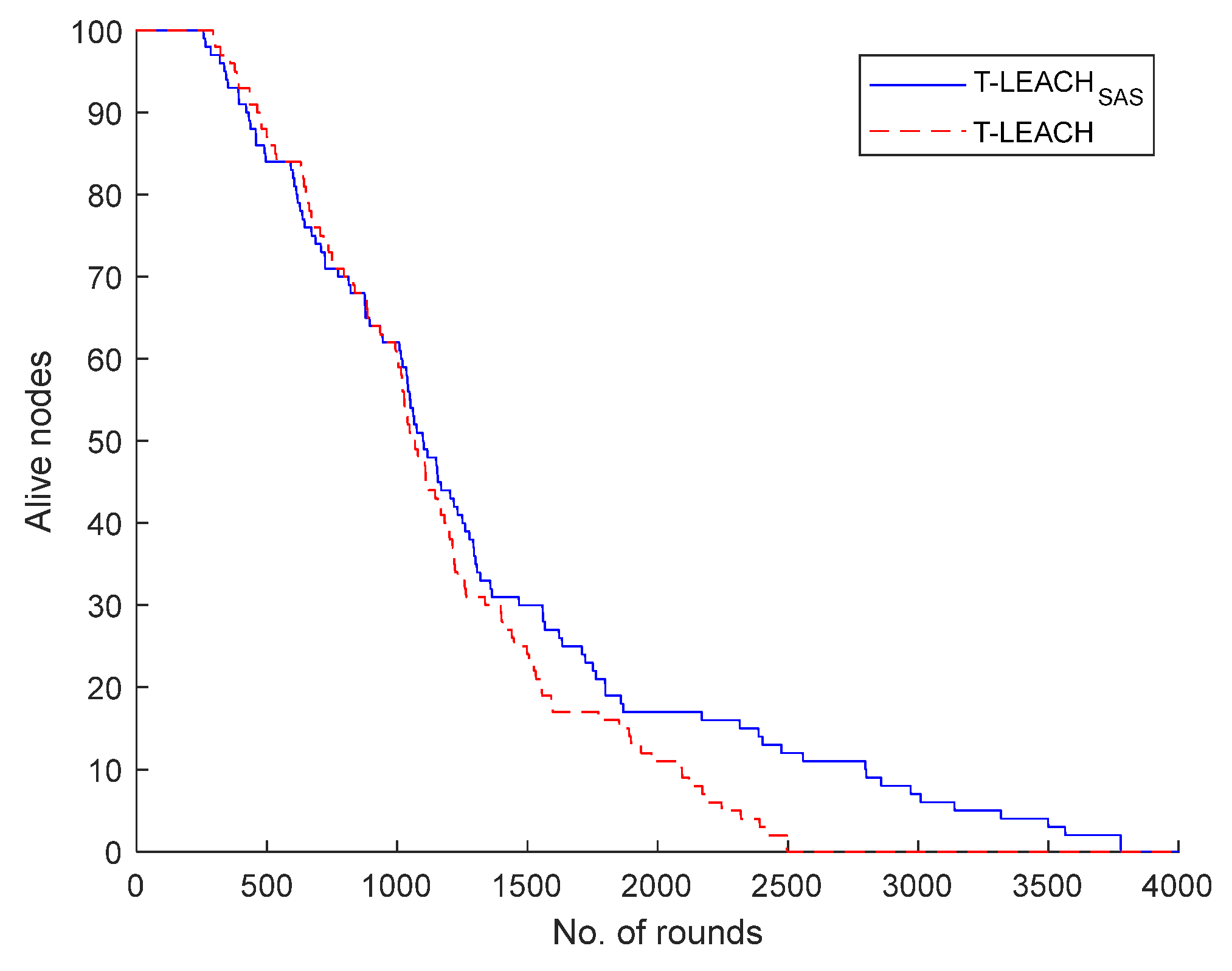
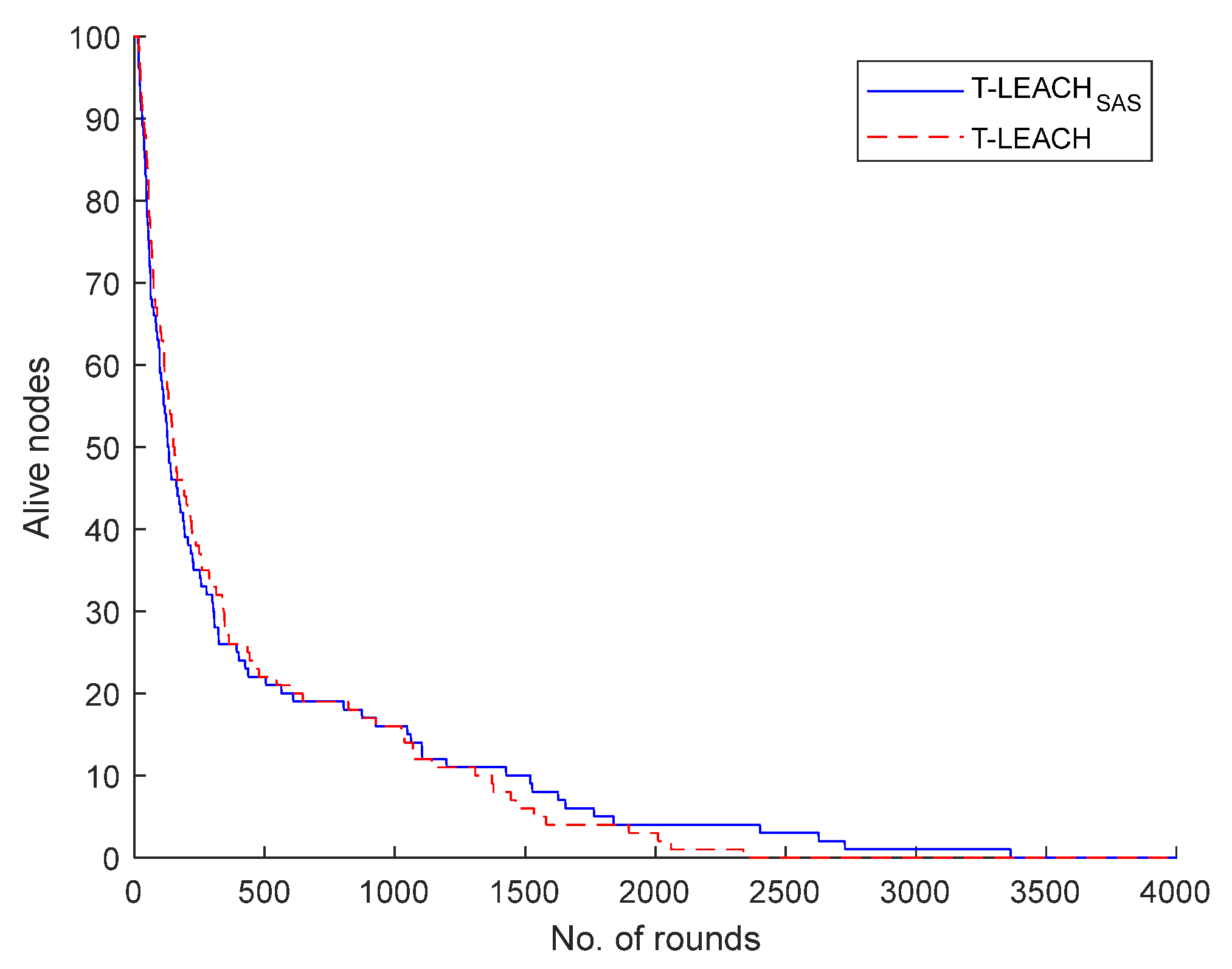
Specifically, in the 1
st scenario studied it was supposed that the WSN under consideration comprises of a base station located at position (100, 100) along with 100 nodes. It was found that T-LEACH
SAS, considering the depletion of last living node, achieves extension of network lifetime by 51.3% when compared to T-LEACH.
Figure 4 illustrates the number of the network nodes that remain alive per simulation round.
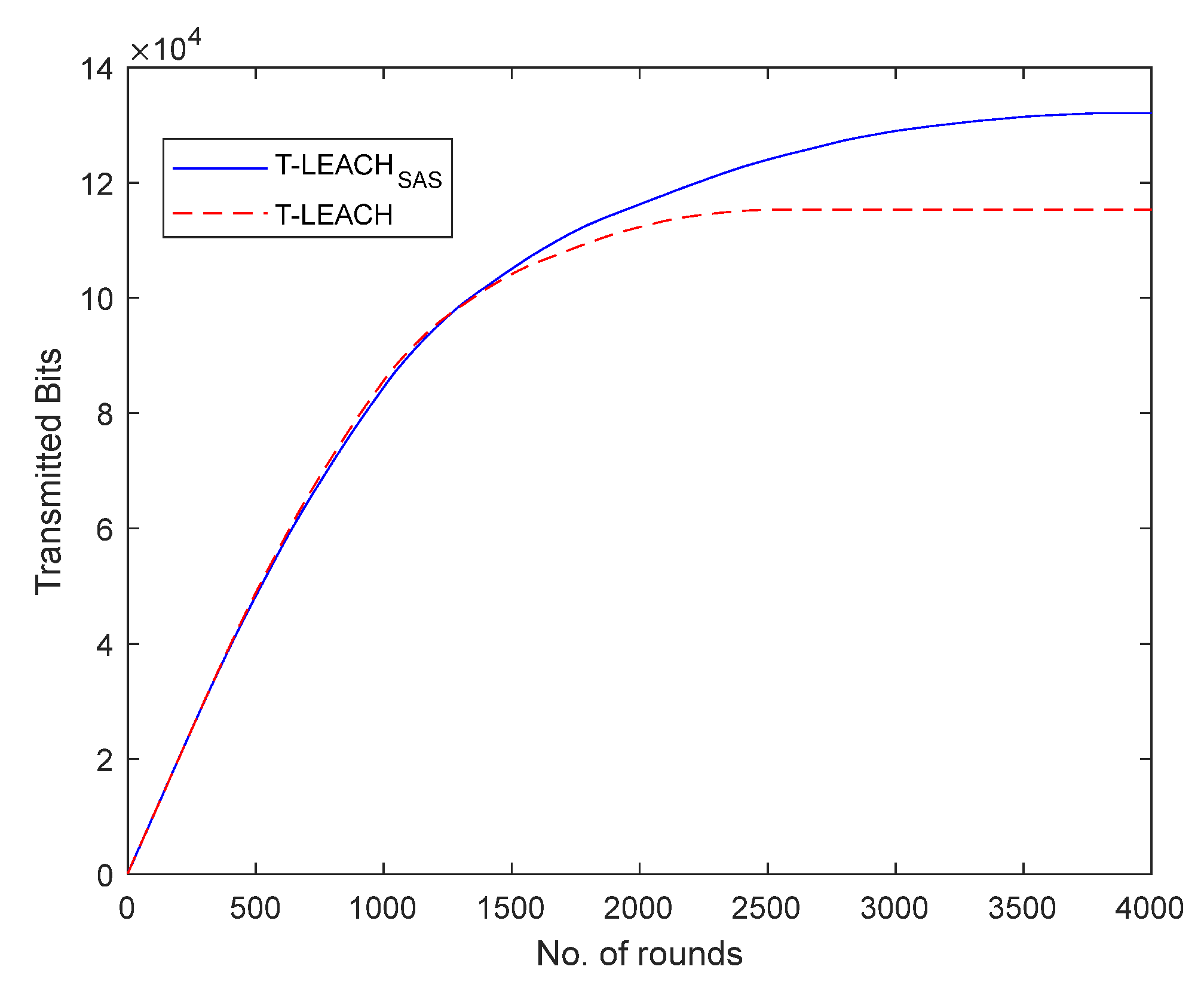
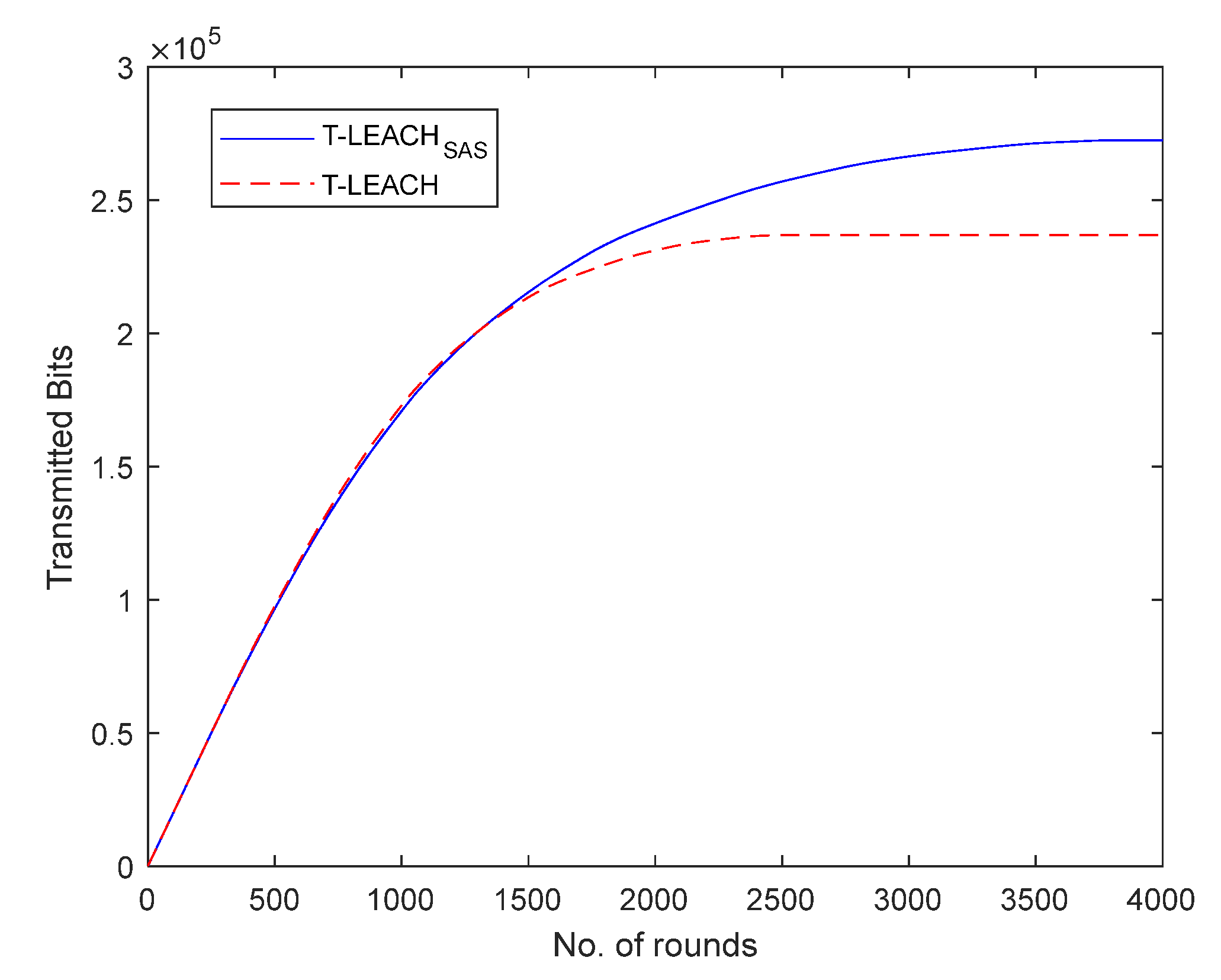
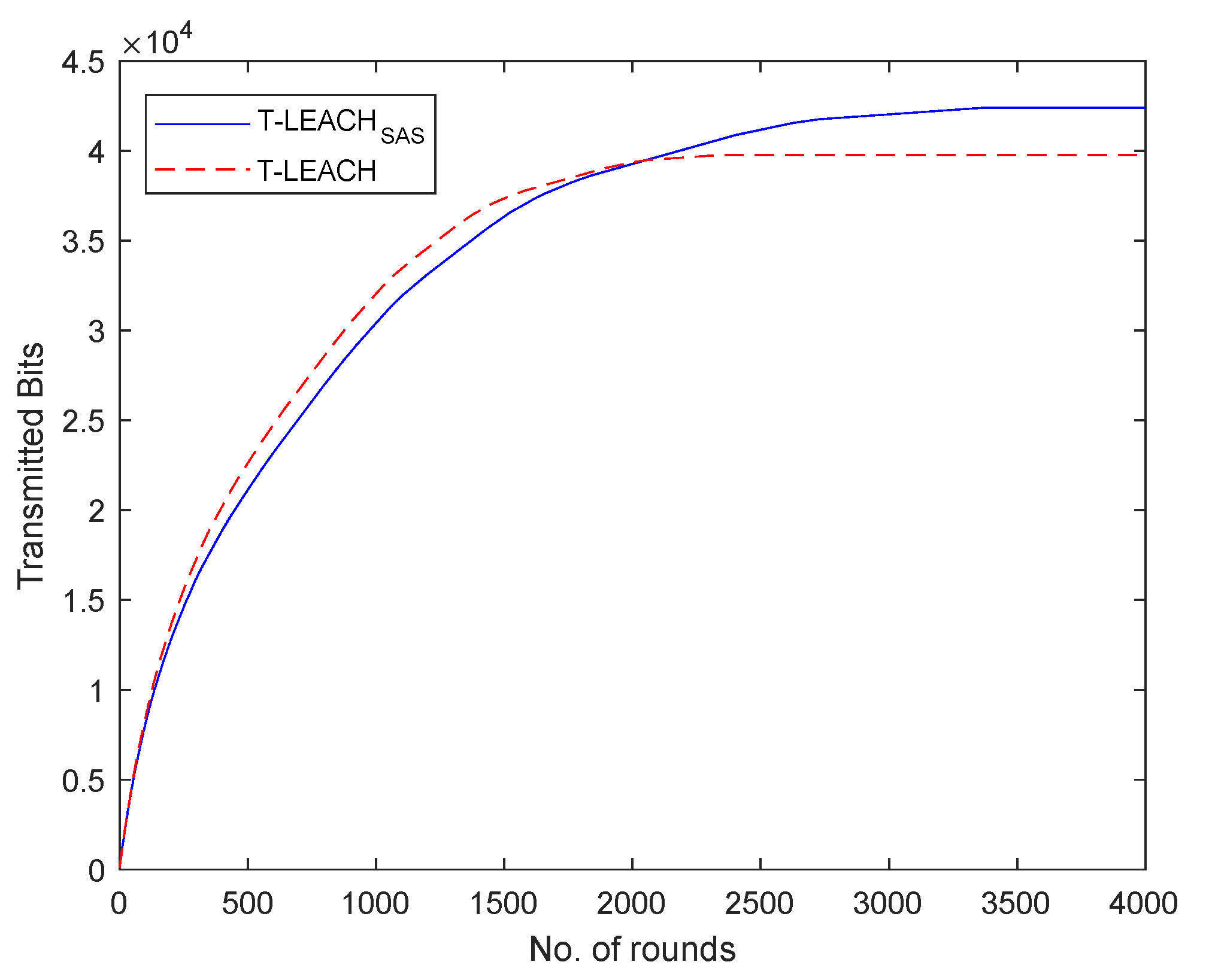
Also, it was found that the total volume of data transmitted to the base station by using T-LEACH
SAS are increased by 14.49% when compared to that achieved when using T-LEACH.
Figure 5 illustrates the total volume of data transmitted per simulation round in the 1
st simulation scenario.
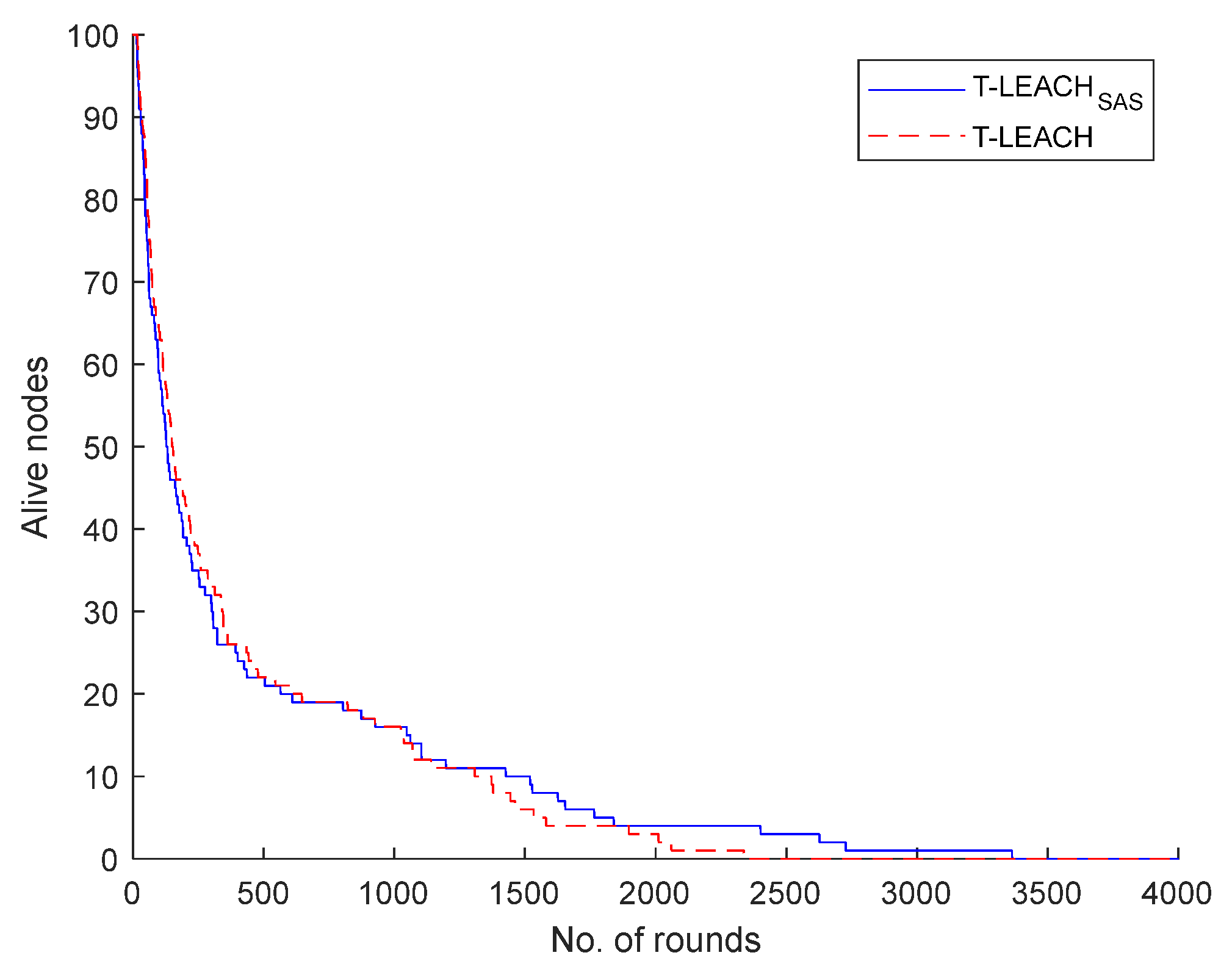
Similarly, in the 2
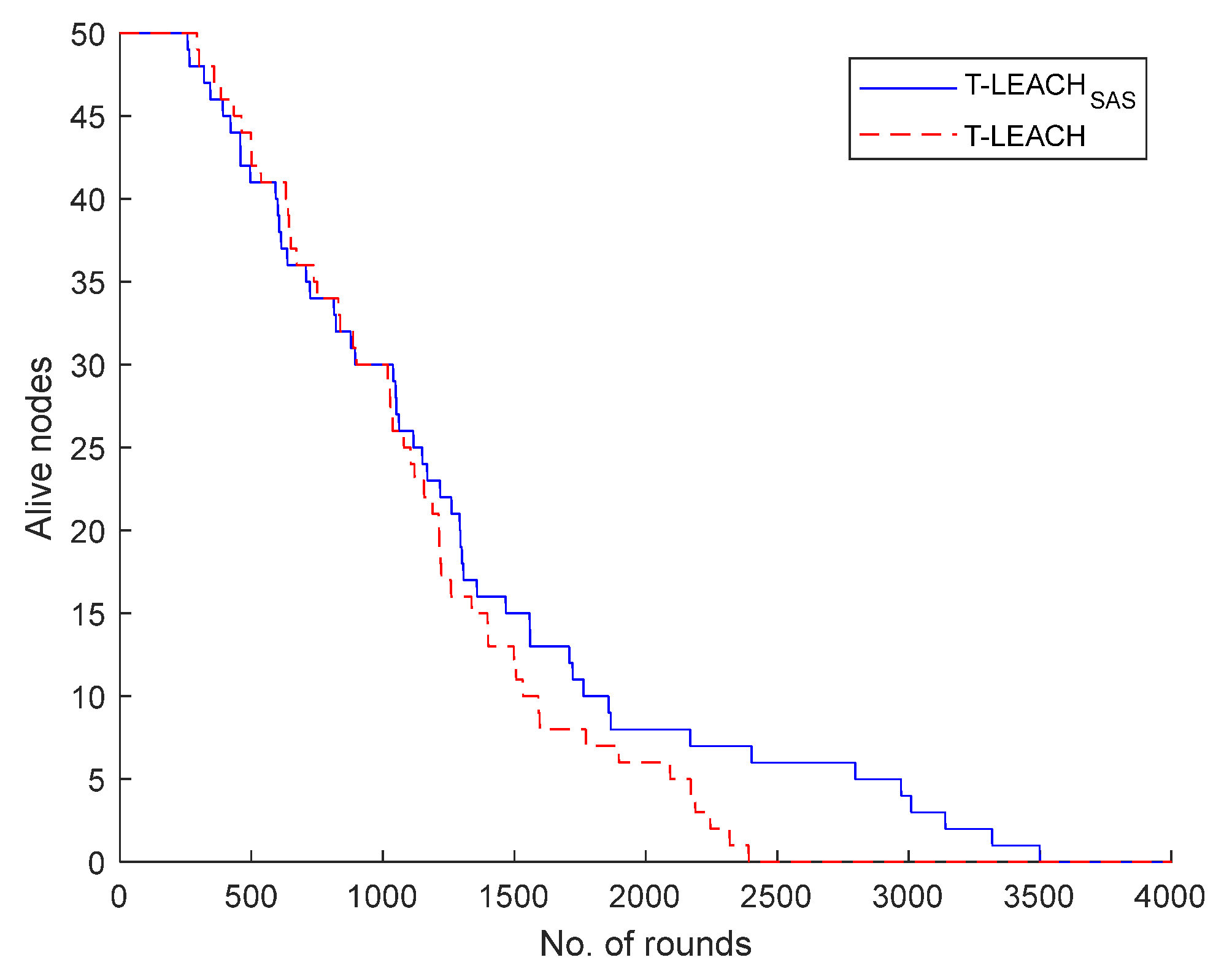
nd scenario studied it was supposed that the WSN under consideration comprises of a base station located at position (100, 100) along with 50 nodes. It was found that T-LEACH
SAS, considering the depletion of last living node, achieves extension of network lifetime by 46.47% when compared to T-LEACH.
Figure 6 illustrates the number of the network nodes that remain alive per simulation round.
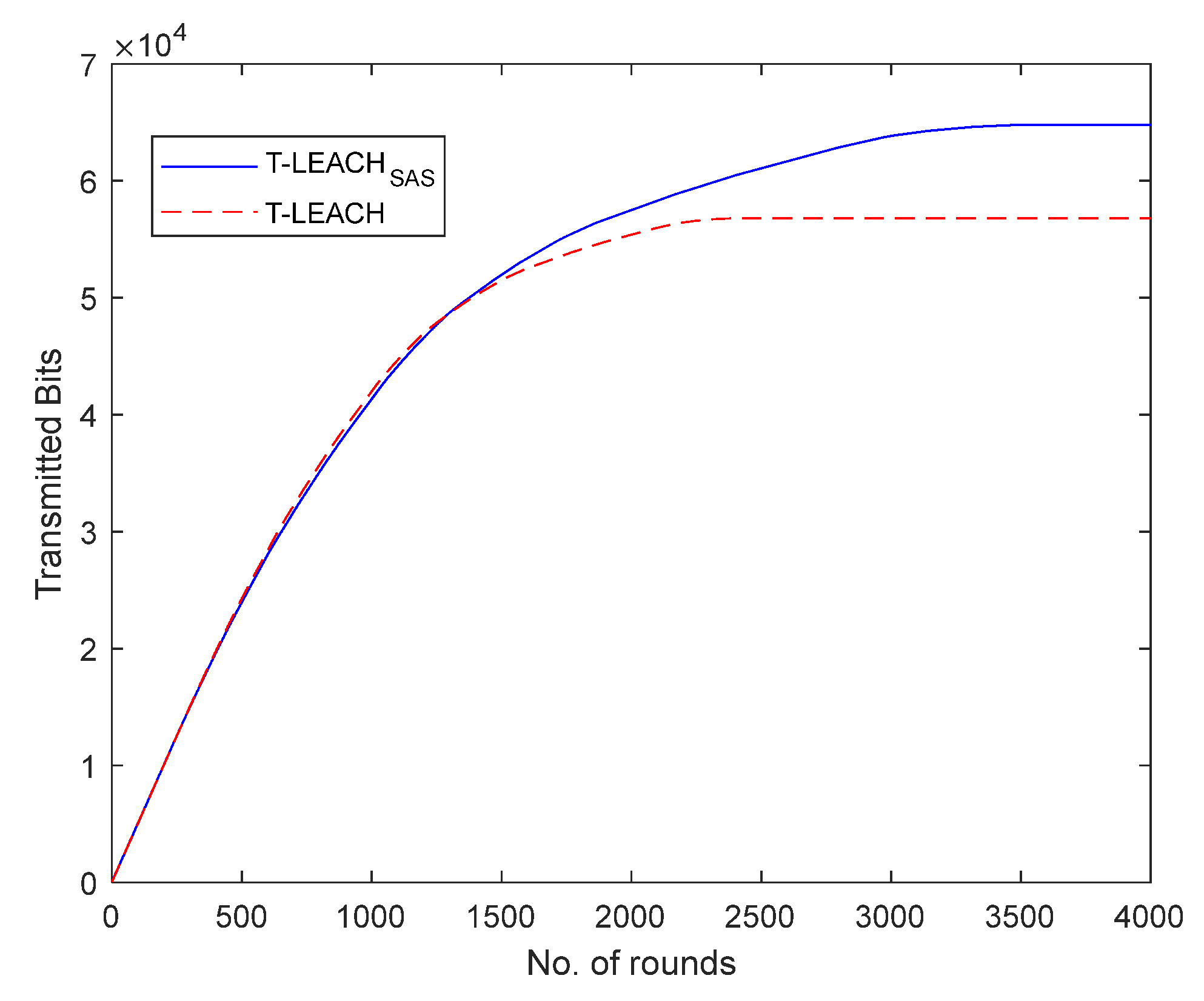
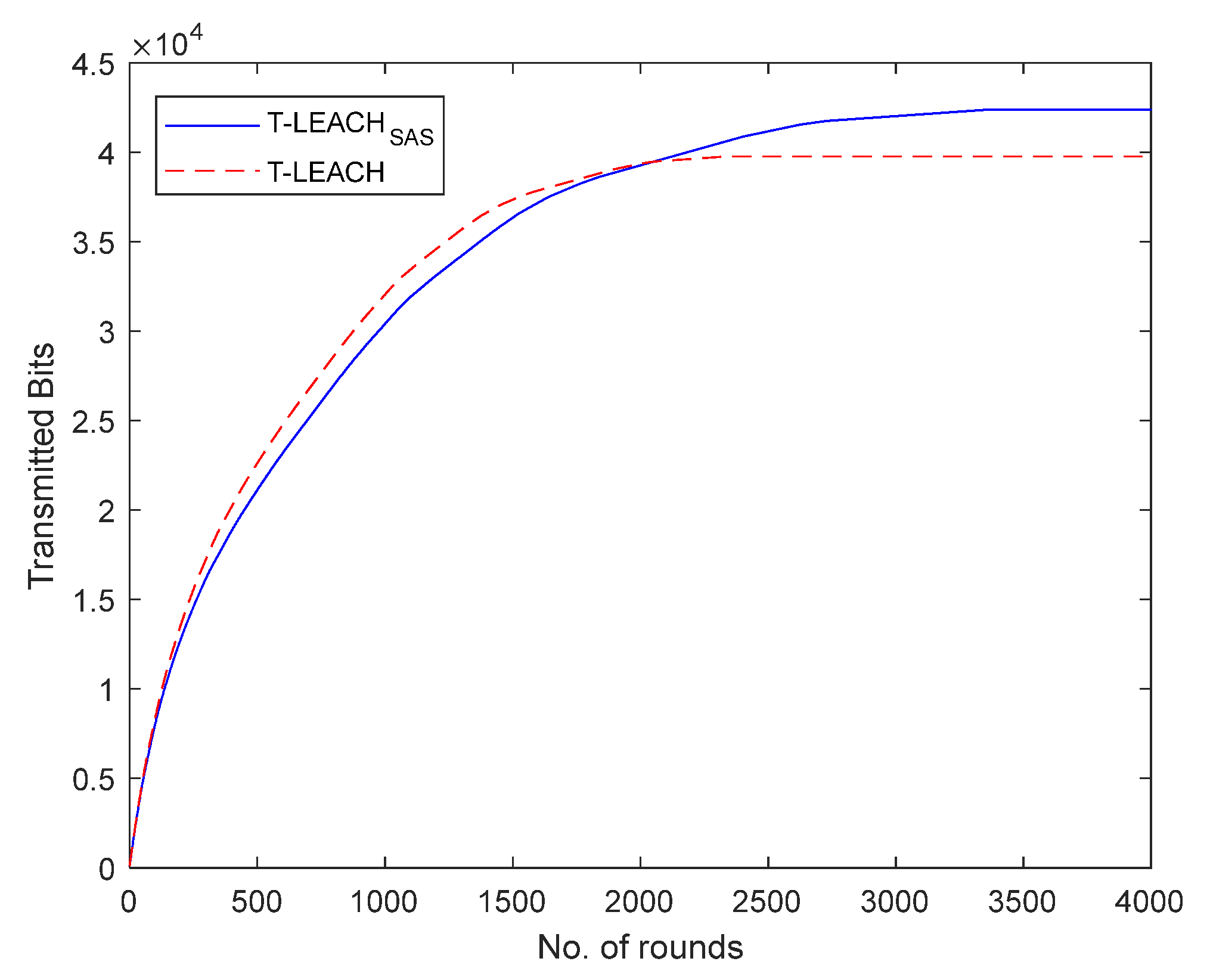
Moreover, it was found that the total volume of data transmitted to the base station by using T-LEACH
SAS are increased by 14.09% when compared to that achieved when using T-LEACH.
Figure 7 illustrates the total volume of data transmitted per simulation round in the 2
nd simulation scenario.
Likewise, in the 3
rd scenario studied it was supposed that the WSN under consideration comprises of a base station located at position (100, 100) along with 200 nodes. It was found that T-LEACH
SAS, considering the depletion of last living node, achieves extension of network lifetime by 55.33% when compared to T-LEACH.
Figure 8 illustrates the number of the network nodes that remain alive per simulation round.
Also, it was found that the total volume of data transmitted to the base station by using T-LEACH
SAS are increased by 14.98% when compared to that achieved when using T-LEACH.
Figure 9 depicts the total volume of data transmitted per simulation round in the 3
rd simulation scenario.
Based on the first three scenarios investigated, it becomes obvious that both in sparse and dense network topologies T-LEACHSAS compared to T-LEACH provides considerably longer lifetime of network nodes. Consequently, thanks to their extended lifespan network nodes transmit greater volume of data to the base station, as after all confirmed by the simulation results.
Next, in the 4
th scenario studied it was supposed that the WSN under consideration comprises of a base station located at position (0, 0) along with 100 nodes. It was found that T-LEACH
SAS, considering the depletion of last living node, achieves extension of network lifetime by 43.88% when compared to T-LEACH.
Figure 10 graphically demonstrates the number of the network nodes that remain alive per simulation round.
Furthermore, it was found that the total volume of data transmitted to the base station by using T-LEACH
SAS are increased by 6.59% when compared to that achieved when using T-LEACH.
Figure 11 depicts the total volume of data transmitted per simulation round in the 4
th simulation scenario.
Finally, in the 5
th scenario studied it was supposed that the WSN under consideration comprises of a base station located at position (100, 220) along with 100 nodes. It was found that T-LEACH
SAS, considering the depletion of last living node, achieves extension of network lifetime by 41.19% when compared to T-LEACH.
Figure 12 graphically demonstrates the number of the network nodes that remain alive per simulation round.
Moreover, it was found that the total volume of data transmitted to the base station by using T-LEACH
SAS is increased by 4.06% when compared to that achieved when using T-LEACH.
Figure 13 depicts the total volume of data transmitted per simulation round in the 5
th simulation scenario.
The study of the 1st scenario in common with the 4th scenario and the 5th scenario makes it clear that both in T-LEACHSAS and T-LEACH the closer to the center of the field of interest the base station is located, the higher energy efficiency and greater data transfer are achieved. Yet, in all cases still T-LEACHSAS proves to be superior to T-LEACH in regards of both these metrics.
6. Conclusions
This research article focused on hierarchical energy efficient routing protocols for WSNs and particularly LEACH, which is a pioneering protocol of this type, along with some of its numerous descendants. Specifically, an overview of typical examples of these protocols was provided while their main advantages and disadvantages were indicated. From the study conducted it was made evident that LEACH descendants have proven to enhance the operation of their ancestor regarding energy efficiency. Nevertheless, such protocols differentiate too in terms of many other metrics such as scalability, throughput, cluster formation, complexity, load balance, processing and communication overhead, latency, communication model, location information, modulation techniques, fault tolerance, and channel encoding. For these reasons, it is apparent that the study is that the aptness of each hierarchical protocol for energy efficient routing in WSNs is application dependent.
Additionally, a novel protocol of this type named T-LEACHSAS was proposed. The specific protocol combines the threshold – based approach for selecting cluster heads that was first introduced in T-LEACH, , which is a well-known protocol, along with a mechanism for sleep-awake scheduling which ensures that nodes transition between active and sleep modes judiciously and thus conserve energy during periods of inactivity. The results of the simulation tests that were executed in various scenarios examined evinced that T-LEACHSAS enhances the beneficial outcomes of T-LEACH and consequently constitutes a promising choice for energy-efficient routing in WSNs because it effectively reduces energy wastage on unnecessary data transmissions and inefficient clustering. On the other hand, sleep-awake scheduling is inevitably associated with intermittent operation of the network which may be inappropriate for a certain number of applications.
The authors of this article intend to extend their future research so that it will incorporate energy efficiency along with other metrics in order to achieve multiobjective optimization of WSNs’ performance.
Author Contributions
Conceptualization, D.R, G.S. and D.K.; methodology, D.R, G.S. and D.K.; software, D.R. and G.S.; validation, D.R., G.S. and D.K.; formal analysis, D.R., G.S. and D.K.; resources, D.R., G.S. and D.K.; writing—original draft preparation, D.R., G.S. and D.K.; writing—review and editing, D.R., G.S. and D.K.; visualization, D.R., G.S. and D.K.; supervision, D.K.; project administration, D.R. G.S. and D.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless Sensor Networks: A Survey. Comput. Netw. 2002, 38, 393–422. [Google Scholar] [CrossRef]
- Wang, Q.; Balasingham, I. Wireless sensor networks-an Introduction. In Wireless Sensor Networks: Application-Centric Design; InTechOpen: London, UK, 2010; pp. 1–14. [Google Scholar]
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless Sensor Network Survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Kandris, D.; Nakas, C.; Vomvas, D.; Koulouras, G. Applications of Wireless Sensor Networks: An Up-To-Date Survey. Appl. Syst. Innov. 2020, 3, 14. [Google Scholar] [CrossRef]
- Kafi, M. A.; Challal, Y.; Djenouri, D.; Doudou, M.; Bouabdallah, A.; Badache, N. A Study of Wireless Sensor Networks for Urban Traffic Monitoring: Applications and Architectures. Procedia Computer Science 2013, 19, 617–626. [Google Scholar] [CrossRef]
- Papadakis, N.; Koukoulas, N.; Christakis, I.; Stavrakas, I.; Kandris, D. An IoT-Based Participatory Antitheft System for Public Safety Enhancement in Smart Cities. Smart Cities 2021, 4, 919–937. [Google Scholar] [CrossRef]
- Sunehra, D.; Rajasri, S. Automatic Street Light Control System Using Wireless Sensor Networks. 2017 IEEE International Conference on Power, Control, Signals and Instrumentation Engineering (ICPCSI), 2017. [Google Scholar] [CrossRef]
- Noel, A.; Abderrazak, Abdaoui; Tarek, Elfouly; Ahmed, M. H.; Badawy, A.; Shehata, M. Structural Health Monitoring Using Wireless Sensor Networks: A Comprehensive Survey. IEEE Communications Surveys and Tutorials 2017, 19, 1403–1423. [Google Scholar] [CrossRef]
- Orfanos, V. A.; Kaminaris, S. D.; Papageorgas, P.; Piromalis, D.; Kandris, D. A Comprehensive Review of IoT Networking Technologies for Smart Home Automation Applications. Journal of Sensor and Actuator Networks 2023, 12. [Google Scholar] [CrossRef]
- Benyezza, H.; Bouhedda, M.; Kara, R.; Rebouh, S. Smart Platform Based on IoT and WSN for Monitoring and Control of a Greenhouse in the Context of Precision Agriculture. Internet of Things 2023, 23, 100830. [Google Scholar] [CrossRef]
- Nikolidakis, S.A.; Kandris, D.; Vergados, D.D.; Douligeris, C. Energy efficient automated control of irrigation in agriculture by using wireless sensor networks. Comput. Electron. Agric. 2015, 113, 154–163. [Google Scholar] [CrossRef]
- Arshad, J.; Siddiqui, T. A.; Sheikh, M. I.; Waseem, M. S.; Nawaz, M. A. B.; Eldin, E. T.; Rehman, A. U. Deployment of an Intelligent and Secure Cattle Health Monitoring System. Egyptian Informatics Journal 2023, 24, 265–275. [Google Scholar] [CrossRef]
- Bouazizi, A.; Zaibi, G.; Samet, M.; Kachouri, A. Wireless Body Area Network for e-Health Applications: Overview. In Proceedings of the 2017 International Conference on Smart, Monitored and Controlled Cities (SM2C,), Sfax, Tunisia, 17-19 February 2017; pp. 64–68. [Google Scholar]
- Jabeen, T.; Jabeen, I.; Ashraf, H.; Jhanjhi, N. Z.; Yassine, A.; Hossain, M. S. An Intelligent Healthcare System Using IoT in Wireless Sensor Network. Sensors 2023, 23(11), 5055. [Google Scholar] [CrossRef] [PubMed]
- Majid, M.; Habib, S.; Javed, A. R.; Rizwan, M.; Srivastava, G.; Gadekallu, T. R.; Lin, J. C.-W. Applications of Wireless Sensor Networks and Internet of Things Frameworks in the Industry Revolution 4.0: A Systematic Literature Review. Sensors 2022, 22. [Google Scholar] [CrossRef]
- Jiang, J.; Wang, H.; Mu, X.; Guan, S. Logistics Industry Monitoring System Based on Wireless Sensor Network Platform. Computer Communications 2020, 155, 58–65. [Google Scholar] [CrossRef]
- Kim, D.-S.; Tran-Dang, H. Wireless Sensor Networks for Industrial Applications. Computer communications and networks 2018, 127–140. [Google Scholar] [CrossRef]
- Christakis, I.; Tsakiridis, O.; Kandris, D.; Stavrakas, I. Air Pollution Monitoring via Wireless Sensor Networks: The Investigation and Correction of the Aging Behavior of Electrochemical Gaseous Pollutant Sensors. Electronics 2023, 12. [Google Scholar] [CrossRef]
- Pantazis, N.A.; Nikolidakis, S.A.; Kandris, D.; Vergados, D.D. An Automated System for Integrated Service Management in Emergency Situations. In Proceedings of the 2011 15th Panhellenic Conference on Informatics, Kastonia, Greece, 30 September-2 October 2011; pp. 154–157. [Google Scholar]
- Đurišić, M.P.; Tafa, Z.; Dimić, G.; Milutinović, V. A Survey of military applications of wireless sensor networks. In Proceedings of the 2012 Mediterranean Conference on Embedded Computing (MECO), Bar, Montenegro, 19–21 June 2012; pp. 196–199. [Google Scholar]
- Kandris, D.; Anastasiadis, E. Advanced Wireless Sensor Networks: Applications, Challenges and Research Trends. Electronics 2024, 13, 2268. [Google Scholar] [CrossRef]
- Kandris, D.; Alexandridis, A.; Dagiuklas, T.; Panaousis, E.; Vergados, D. D. Multiobjective Optimization Algorithms for Wireless Sensor Networks. Wireless Communications and Mobile Computing 2020, 2020, 1–5. [Google Scholar] [CrossRef]
- Ploumis, S. E., Sgora, A., Kandris, D., & Vergados, D. D. (2012, October). Congestion avoidance in wireless sensor networks: A survey. In Proceedings of the 16th Panhellenic Conference on Informatics (PCI 2012), Piraeus, Greece, 5-7 October 2012; pp. 234-239. [CrossRef]
- Kandris, D.; Tselikis, G.; Anastasiadis, E.; Panaousis, E.; Dagiuklas, T. COALA: A Protocol for the Avoidance and Alleviation of Congestion in Wireless Sensor Networks. Sensors 2017, 17. [Google Scholar] [CrossRef] [PubMed]
- Kandris, D.; Vergados, D.J.; Vergados, D.D.; Tzes, A. A routing scheme for congestion avoidance in wireless sensor networks. In Proceedings of the 6th Annual IEEE Conference on Automation Science and Engineering (CASE 2010), Toronto, ON, Canada, 21–24 August 2010; pp. 21–24. [Google Scholar]
- Bohloulzadeh, A.; Rajaei, M. A Survey on Congestion Control Protocols in Wireless Sensor Networks. International Journal of Wireless Information Networks 2020. [Google Scholar] [CrossRef]
- Tripathi, A.; Gupta, H. P.; Dutta, T.; Mishra, R.; Shukla, K. K.; Jit, S. Coverage and Connectivity in WSNs: A Survey, Research Issues and Challenges. IEEE Access 2018, 6, 26971–26992. [Google Scholar] [CrossRef]
- Farsi, M.; Elhosseini, M. A.; Badawy, M.; Arafat Ali, H.; Zain Eldin, H. Deployment Techniques in Wireless Sensor Networks, Coverage and Connectivity: A Survey. IEEE Access 2019, 7, 28940–28954. [Google Scholar] [CrossRef]
- Tarnaris, K.; Preka, I.; Kandris, D.; Alexandridis, A. Coverage and K-Coverage Optimization in Wireless Sensor Networks Using Computational Intelligence Methods: A Comparative Study. Electronics 2020, 9. [Google Scholar] [CrossRef]
- Vikas; Sagar, B. B.; Munjul, M. Security Issues in Wireless Sensor Network – a Survey. Journal of Discrete Mathematical Sciences and Cryptography 2021, 24, 1415–1427. [CrossRef]
- Yu, J.-Y.; Lee, E.; Oh, S.-R.; Seo, Y.-D.; Kim, Y.-G. A Survey on Security Requirements for WSNs: Focusing on the Characteristics Related to Security. IEEE Access 2020, 8, 45304–45324. [Google Scholar] [CrossRef]
- Shanmugapriya, T.; Kousalya, K.; Rajeshkumar, J.; Nandhini, M. Wireless Sensor Networks Security Issues, Attacks and Challenges: A Survey. In Proceeding of the International Conference on Computer Networks, Big Data and IoT (ICCBI - 2019) 2020, 1–12. [CrossRef]
- Nikolakopoulos, G.; Kandris, D.; Tzes, A. Adaptive Compression of Slowly Varying Images Transmitted over Wireless Sensor Networks. Sensors 2010, 10, 7170–7191. [Google Scholar] [CrossRef]
- Dionisis, Kandris; Michail, Tsagkaropoulos; Politis, I.; Tzes, A. Dionisis Kandris; Michail Tsagkaropoulos; Politis, I.; Tzes, A.; Stavros Kotsopoulos. A Hybrid Scheme for Video Transmission over Wireless Multimedia Sensor Networks. 2009. [CrossRef]
- Nikolakopoulos, G.; Kandris, D.; Tzes, A. Adaptive Compression of Slowly Varying Images Transmitted over Wireless Sensor Networks. Sensors 2010, 10, 7170–7191. [Google Scholar] [CrossRef] [PubMed]
- Muhammad Noman Hayat; Khan, H.; Iqbal, Z.; Zia Ur Rahman; Tahir, M. Multimedia Sensor Networks: Recent Trends, Research Challenges and Future Directions. 2017. [CrossRef]
- Nikolakopoulos, G.; Stavrou, P.; Tsitsipis, D.; Kandris, D.; Tzes, A.; Theocharis, T. A Dual Scheme for Compression and Restoration of Sequentially Transmitted Images over Wireless Sensor Networks. Ad Hoc Networks 2013, 11, 410–426. [Google Scholar] [CrossRef]
- Evangelakos, E.A.; Kandris, D.; Rountos, D.; Tselikis, G.; Anastasiadis, E. Energy Sustainability in Wireless Sensor Networks: An Analytical Survey. J. Low Power Electron. Appl. 2022, 12, 65. [Google Scholar] [CrossRef]
- Rezaei, Z. Energy Saving in Wireless Sensor Networks. Int. J. Comput. Sci. Eng. Surv. 2012, 3, 23–37. [Google Scholar] [CrossRef]
- Engmann, F.; Katsriku, F.A.; Abdulai, J.-D.; Adu-Manu, K.S.; Banaseka, F.K. Prolonging the Lifetime of Wireless Sensor Networks: A Review of Current Techniques. Wirel. Commun. Mob. Comput. 2018, 2018, 8035065. [Google Scholar] [CrossRef]
- Rault, T.; Bouabdallah, A.; Challal, Y. Energy Efficiency in Wireless Sensor Networks: A Top-down Survey. Comput. Netw. 2014, 67, 104–122. [Google Scholar] [CrossRef]
- Khan, J.A.; Qureshi, H.K.; Iqbal, A. Energy Management in Wireless Sensor Networks: A Survey. Comput. Electr. Eng. 2015, 41, 159–176. [Google Scholar] [CrossRef]
- Anastasi, G.; Conti, M.; Di Francesco, M.; Passarella, A. Energy Conservation in Wireless Sensor Networks: A Survey. Ad Hoc Netw. 2009, 7, 537–568. [Google Scholar] [CrossRef]
- Patel, H.; Shah, V. A review on energy consumption and conservation techniques for sensor node in WSN. In Proceedings of the IEEE 2016 International Conference on Signal Processing, Communication, Power and Embedded System (SCOPES), Paralakhemundi, India, 3–5 October 2016; pp. 594–599. [Google Scholar]
- Stankovic, J.A.; He, T. Energy Management in Sensor Networks. Philos. Trans. R. Soc. A Math. Phys. Eng. Sci. 2012, 370, 52–67. [Google Scholar] [CrossRef]
- Kandris, D.; Tsioumas, P.; Tzes, A.; Nikolakopoulos, G.; Vergados, D. Power Conservation through Energy Efficient Routing in Wireless Sensor Networks. Sensors 2009, 9, 7320–7342. [Google Scholar] [CrossRef]
- Nakas, C.; Kandris, D.; Visvardis, G. Energy Efficient Routing in Wireless Sensor Networks: A Comprehensive Survey. Algorithms 2020, 13, 72. [Google Scholar] [CrossRef]
- Pantazis, N. A.; Nikolidakis, S. A.; Vergados, D. D. Energy-Efficient Routing Protocols in Wireless Sensor Networks: A Survey. IEEE Communications Surveys Tutorials 2013, 15, 551–591. [Google Scholar] [CrossRef]
- Kandris, D.; Tsioumas, P.; Tzes, A.; Pantazis, N.; Vergados, D. D. Hierarchical energy efficient routing in Wireless Sensor Networks. In Proceedings of the 16th Mediterranean Conference on Control and Automation, Ajaccio, France, 25-27 June 2008; pp. 1856–1861. [Google Scholar] [CrossRef]
- Xin, H.; Liu, X. Energy-Balanced Transmission with Accurate Distances for Strip-Based Wireless Sensor Networks. IEEE access 2017, 5, 16193–16204. [Google Scholar] [CrossRef]
- Heinzelman, W. R.; Chandrakasan, A.; Balakrishnan, H. Energy-efficient communication protocol for wireless microsensor networks. In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Maui, USA, January 4–7, 2000; pp. 1–10. [Google Scholar] [CrossRef]
- Singh, S. K.; Kumar, P.; Singh, J. P. A Survey on Successors of LEACH Protocol. IEEE Access 2017, 5, 4298–4328. [Google Scholar] [CrossRef]
- Kandris, D.; Evangelakos, E. A.; Rountos, D.; Tselikis, G.; Anastasiadis, E. LEACH-Based Hierarchical Energy Efficient Routing in Wireless Sensor Networks. AEU - International Journal of Electronics and Communications 2023, 169, 154758. [Google Scholar] [CrossRef]
- Mahapatra, R. P.; Yadav, R. K. Descendant of LEACH Based Routing Protocols in Wireless Sensor Networks. Procedia Computer Science 2015, 57, 1005–1014. [Google Scholar] [CrossRef]
- Rountos, D.; Kandris, D.; Evangelakos, E. A.; Tselikis, G. Energy efficient routing in wireless sensor networks: A comparative study on leach protocol and its successors. Proceedings of 2022 Panhellenic Conference on Electronics & Telecommunications (PACET), Tripolis, Greece, 2-3 December 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Daanoune, I.; Abdennaceur, B.; Ballouk, A. A Comprehensive Survey on LEACH-Based Clustering Routing Protocols in Wireless Sensor Networks. Ad Hoc Networks 2021, 114, 102409. [Google Scholar] [CrossRef]
- Liu, X. A Survey on Clustering Routing Protocols in Wireless Sensor Networks. Sensors 2012, 12, 11113–11153. [Google Scholar] [CrossRef] [PubMed]
- Qubbaj, N. N. A.; Taleb, A. A.; Salameh, W. LEACH Based Protocols: A Survey. Advances in Science, Technology and Engineering Systems Journal 2020, 5, 1258–1266. [Google Scholar] [CrossRef]
- Hong, J.; Kook, J.; Lee, S.-J.; Kwon, D.; Yi, S. T-LEACH: The Method of Threshold-Based Cluster Head Replacement for Wireless Sensor Networks. Information Systems Frontiers 2009, 11, 513–521. [Google Scholar] [CrossRef]
- Tong, M.; Tang, M. LEACH-B: an improved LEACH protocol for wireless sensor network. Proceedings of 2010 6th International Conference on Wireless Communications Networking and Mobile computing (WiCOM), Chengdu, China, 23-25 September 2010; pp. 1–4. [Google Scholar] [CrossRef]
- Heinzelman, W. B.; Chandrakasan, A. P.; Balakrishnan, H. An Application-Specific Protocol Architecture for Wireless Microsensor Networks. IEEE Transactions on Wireless Communications 2002, 1, 660–670. [Google Scholar] [CrossRef]
- Tripathi, M.; Battula, R. B.; Gaur M., S.; Laxmi, V. Energy efficient clustered routing for wireless sensor network. Proceedings of 2013 IEEE 9th International Conference on Mobile Ad-hoc and Sensor Networks (MSN), Dalian, Liaoning, China, 1-13 Dec. 2013; pp. 330–335. [Google Scholar] [CrossRef]
- Liu, Y.; Xu, K.; Luo, Z.; Chen, L. A reliable clustering algorithm base on LEACH protocol in wireless mobile sensor networks. Proceedings of 2010 International Conference on Mechanical and Electrical Technology, Singapore, 10-12 September, 2010; pp. 692–696. [Google Scholar] [CrossRef]
- Shang, F.; Lei, Y. An Energy-Balanced Clustering Routing Algorithm for Wireless Sensor Network. Wireless Sensor Network 2010, 02, 777–783. [Google Scholar] [CrossRef]
- Loscri, V.; Morabito, G.; Marano, S. A Two-Levels Hierarchy for Low-Energy Adaptive Clustering Hierarchy (TL-LEACH). 2006. [CrossRef]
- Beiranvand, Z.; Patooghy, A.; Fazeli, M. I-LEACH: An Efficient Routing Algorithm to Improve Performance & to Reduce Energy Consumption in Wireless Sensor Networks. In Proceedings of the 5th Conference on Information and Knowledge Technology, Shiraz, Iran, 28–30 May 2013. [Google Scholar] [CrossRef]
- Nikolidakis, S.; Kandris, D.; Vergados, D.; Douligeris, C. Energy Efficient Routing in Wireless Sensor Networks through Balanced Clustering. Algorithms 2013, 6, 29–42. [Google Scholar] [CrossRef]
- Tyagi, S.; Gupta, S.K.; Tanwar, S.; Kumar, N. EHE-LEACH: Enhanced Heterogeneous LEACH Protocol for Lifetime Enhancement of Wireless SNs. In Proceedings of the 2013 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Mysore, India, 22–25 August 2013. [Google Scholar] [CrossRef]
- Lee, J.S.; Cheng, W.L. Fuzzy-Logic based Clustering Approach for Wireless Sensor Networks Using Energy Predication. IEEE Sens. J. 2012, 12, 2891–2897. [Google Scholar] [CrossRef]
- Jerbi, W.; Guermazi, A. ; Trabelsi, H, O-LEACH of routing protocol for wireless sensor networks. In Proceedings of the 13th International Conference on Computer Graphics, Imaging and Visualization (CGiV), Beni Mellal, Morocco, 29 March -1 April 2016; pp. 399–404. [Google Scholar] [CrossRef]
- Manzoor, B.; Javaid, N.; Rehman, O.; Akbar, M.; Nadeem, Q.; Iqbal, A.; Ishfaq, M. Q-LEACH: A New Routing Protocol for WSNs. Procedia Comput. Sci. 2013, 19, 926–931. [Google Scholar] [CrossRef]
- Farooq, M. O.; Dogar, A. B.; Shah, G. A. MR-LEACH: Multi-hop Routing with Low Energy Adaptive Clustering Hierarchy. In Proceedings of the 4th International Conference on Sensor Technologies and Applications, Venice, Italy, 18-25 July 2010; pp. 262–268. [Google Scholar] [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).