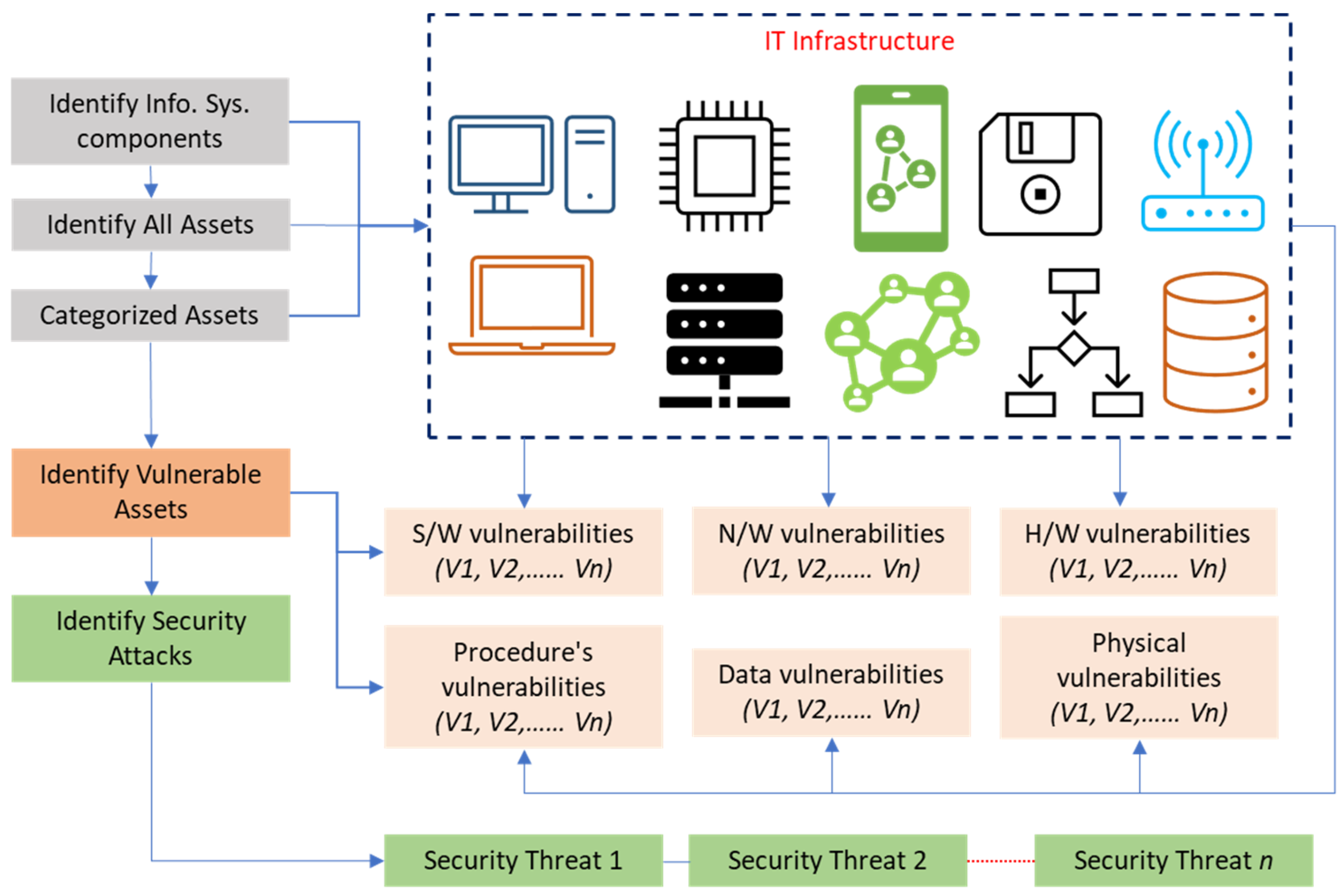
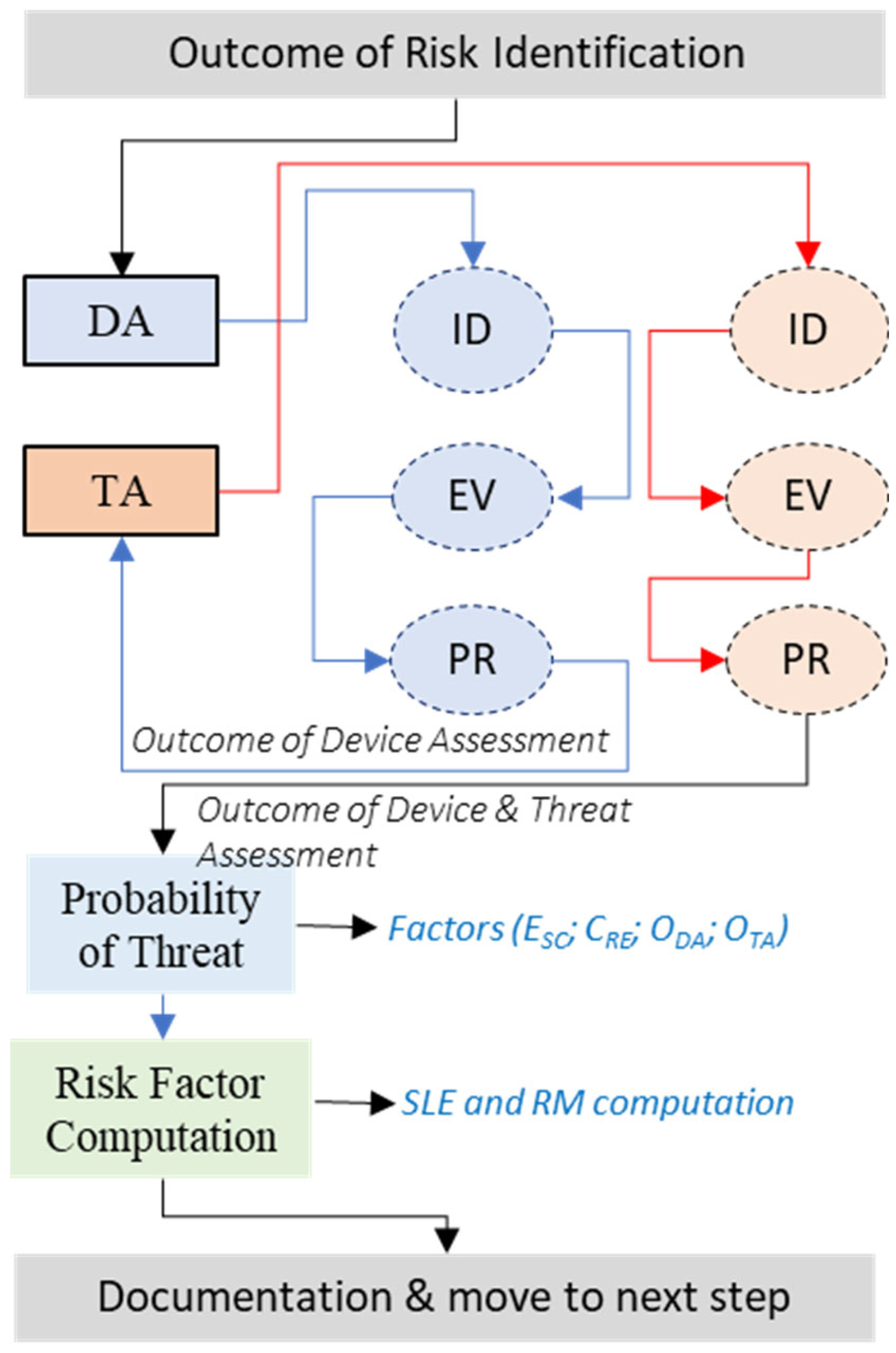
3.2. Risk Evaluation
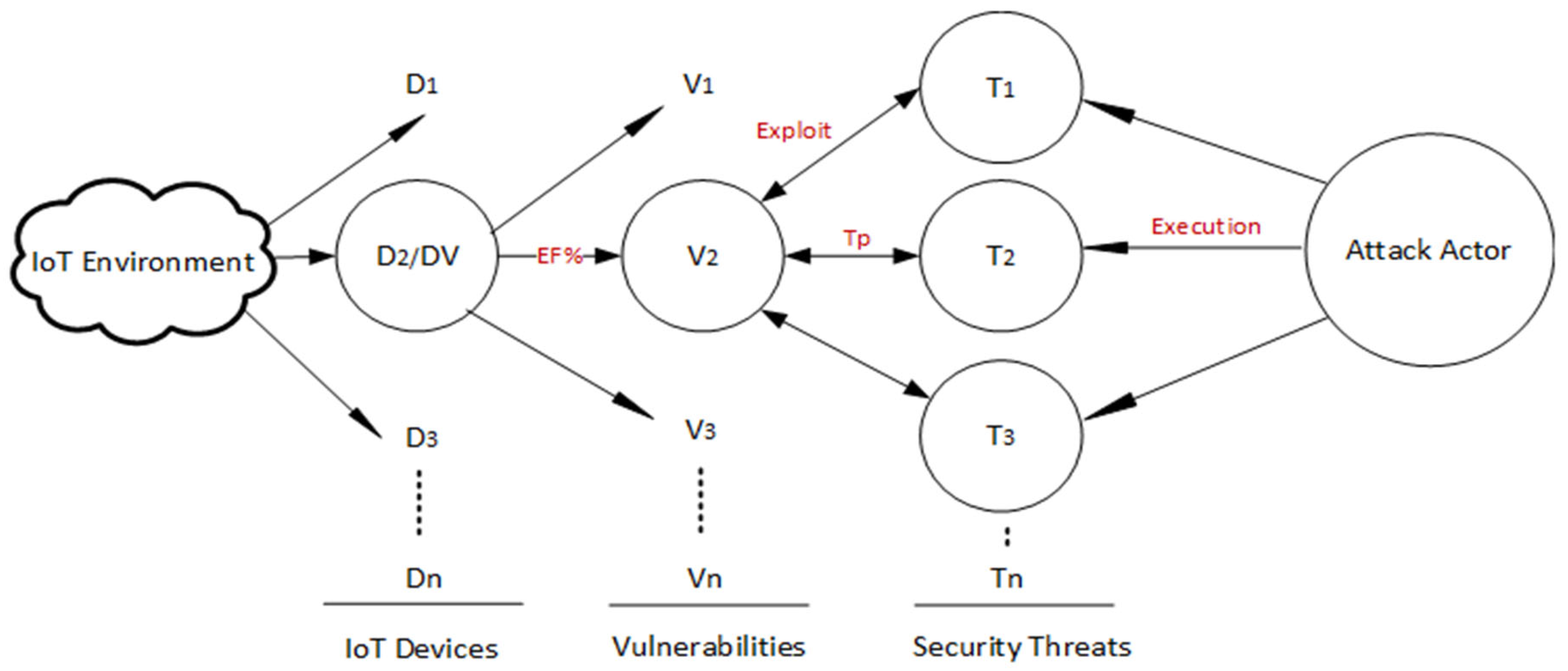
During this phase, a comprehensive examination is conducted on each threat that was identified in the previous phase, aiming to determine its potential impact on the IoT network. At this stage, all possible attack paths have been uncovered, necessitating an evaluation of their potential severity and the prioritization of necessary mitigation measures. This phase will incorporate ML models into each step to improve the accuracy and efficiency of this process. ML analyzes historical data and real-time assessments to predict criticality, potential impacts, and risks on IoT devices.
Leveraging automated systems and ML will help make the evaluation process more dynamic and accurate, allowing for continuous risk assessment as the organization obtains new data. To enhance visual comprehension of the attacker's routes to different network components, a tree map is utilized to display all possible attack paths. This step is crucial as it entails enumerating all identified threats and assigning priorities based on their associated level of risk
3.2.1. IoT Device Assessment (DA)
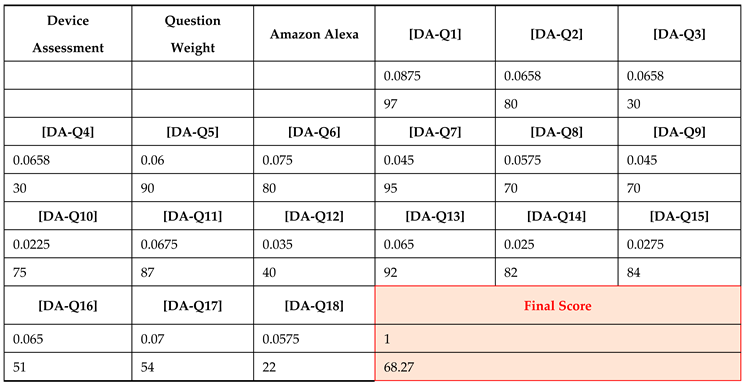
To assess the risks confronting your organization, it is necessary to examine the assets that require protection and assign them a ranking based on their significance. This evaluation involves categorizing the assets to identify those of critical importance, which demand the highest level of safeguarding. The objective is to ensure that any potential damage inflicted will not have a severe impact on the IoT network, while prioritizing the protection of the most essential assets. Recognizing that certain assets hold greater value than others, this approach allows for the safeguarding of key IoT devices during an attack and facilitates the reconstruction of any lost components. Given the subjective nature of asset valuation, it is essential to adopt a more universal approach that can be applied across various IoT domains. As part of the risk management framework, we have developed a set of questions to be posed by the security management group (SMG) or the IT department for each identified IoT device. Within each question, specific criteria are established to evaluate the identified IoT devices from the previous step. ML algorithms and predictive analytics are incorporated. These models analyze historical data, real-time inputs, and various operational parameters to assess the criticality, usage patterns, and vulnerability levels of IoT devices. This automated evaluation provides a comprehensive understanding of each device's risk profile, ensuring the most critical assets receive the highest level of protection. The SMG will review the outputs generated by the automated system at the end of the DA process.
-
A.
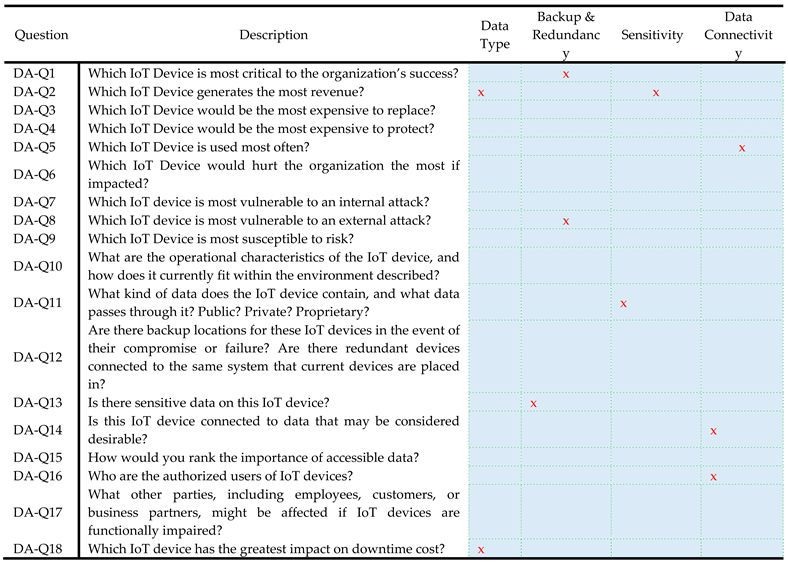
Template Questions for DA
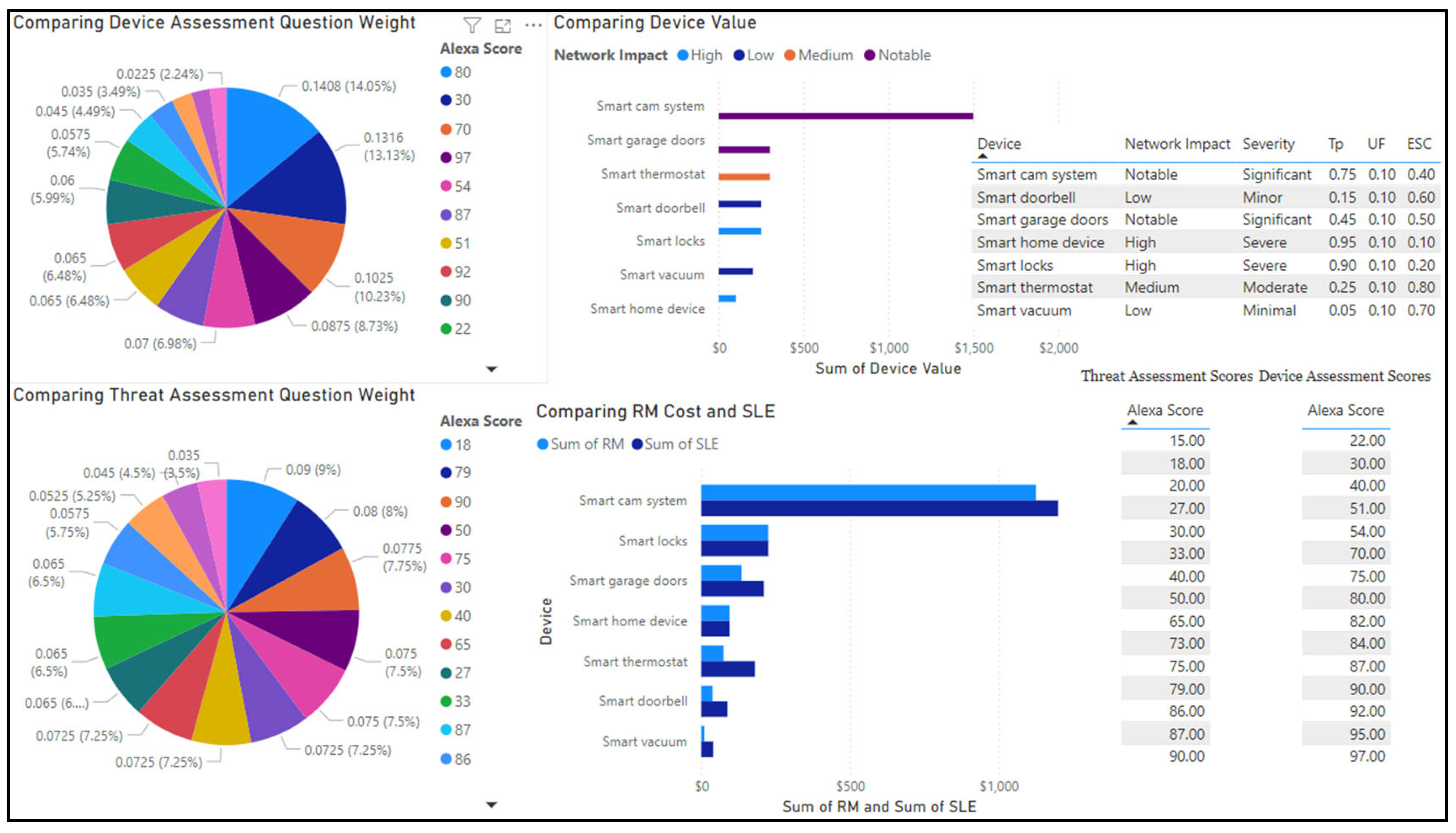
Template 1 presents a set of device assessment questions aimed at evaluating various aspects of IoT devices, including their criticality, revenue generation, replacement and protection costs, vulnerability to attacks, data characteristics, backup/redundancy measures, and impact on downtime cost. Additional columns provide information on the goal/objective of each question, data type, backup/redundancy status, sensitivity of data, and data connectivity. Automated systems will use these questions to gather comprehensive data points and provide a detailed assessment of each IoT device, making the evaluation process more thorough and data driven.
-
B.
Explanation of DA Template Questions
Q1: This question assesses IoT devices based on the organization's goals and objectives. ML algorithms will analyze operational data, historical usage, and impact metrics to determine device criticality. Devices that are less essential will receive a lower score compared to the most critical devices.
Q2: This question evaluates IoT devices based on their contribution to revenue. Each device's impact on total revenue is considered using its net value (revenue generated minus upkeep costs) over a specific time period (e.g., year, quarter, month). Predictive analytics will process financial records and revenue data to identify and rank devices based on their revenue generation.
Q3: This question examines IoT devices based on their replacement cost, taking into account the initial cost of replacing the device, costs associated with physical installation or removal, and any expenses required to ensure the device operates at its maximum effectiveness (e.g., backups). ML models will estimate replacement expenses by analyzing market prices, installation costs, and maintenance data.
Q4: This question considers IoT devices in terms of their protection cost, focusing on the total cost required to fully secure the device. Predictive models will evaluate the cost-effectiveness of various protection measures by analyzing security implementation costs and their potential Return on Investment (ROI).
Q5: This question highlights the frequency of usage of a particular IoT device for various operations within the organization. The evaluation is based on the total usage time of the device. ML algorithms will detect usage patterns by analyzing operational logs and real-time usage data.
Q6: This question assesses the potential harm to the organization in financial and operational terms if a specific device is impacted. The evaluation measures the projected loss, which takes into account the loss of revenue directly or indirectly generated by the device minus the device's upkeep costs. Predictive analytics will quantify potential harm by evaluating historical incident data and projecting future impact scenarios.
Q7: This question identifies IoT devices that are most vulnerable to attacks, either from the internal network or physical security measures. The evaluation considers the level of security access required to interact with the device and the number of vulnerabilities affecting the device within the internal network. Vulnerability assessment models will identify internal vulnerabilities by analyzing security logs and conducting real-time threat simulations.
Q8: This question focuses on IoT devices that are most vulnerable to external threats. The evaluation considers the number of external vulnerabilities that affect the device. Threat intelligence systems will assess external threat vectors by analyzing threat intelligence feeds and historical breach data.
Template 1.
IoT Device Assessment Questions and Attributes.
Template 1.
IoT Device Assessment Questions and Attributes.
Q9: This question examines IoT devices based on the total number of vulnerabilities they possess. The evaluation takes into account the sum of internal and external vulnerabilities affecting the device. ML models will aggregate and analyze vulnerability data from various sources to provide a comprehensive risk profile.
Q10: This question evaluates how an IoT device fits into the organization's current operational framework. It considers factors such as the device's use in business transactions, the specific network traffic flowing through it, and the potential operational impact if the device is compromised. Predictive analytics will analyze operational data, network traffic, and business processes to evaluate the device's integration and significance.
Q11: This question examines the type of information flowing through the IoT device, such as customer data, proprietary organization data, sensitive documents, or other potentially compromising data if breached. Data classification algorithms will evaluate data types and their sensitivity and potential exposure risks.
Q12: This question assesses whether there is a backup infrastructure in place for the IoT device. It considers factors such as backup processes, failover mechanisms, data redundancy, and the device's operating framework. Redundancy analysis models will evaluate backup measures by analyzing system configurations and redundancy protocols.
Q13: This question identifies IoT devices that contain sensitive data, including financial account numbers, social security numbers, biometric data, and compliance-related information such as HIPAA or FISMA. ML models will analyze and perform privacy risk evaluation.
Q14: This question focuses on IoT devices connected to a network that contains sensitive data. Network analysis ML models will assess data connectivity and sensitivity by analyzing network configurations and data types.
Q15: This question considers the importance of the data flowing through the IoT device, ranging from low importance (e.g., addresses, phone numbers) to high importance (e.g., social security numbers, biometric data). Learning to rank (LTR) algorithms will classify data types and evaluate and rank their potential impact.
Q16: This question evaluates the probability of an attack based on the number of authorized users with access to the IoT devices. A lower number of authorized users reduces the probability of an intrusion, while a higher number increases the probability. ML algorithms will analyze user access patterns and evaluate the risk associated with the number of authorized users.
Q17: In the event of device failure or attack, this question quantifies the total number of impacted parties, including employees, customers, or business partners, with regard to the operations and data contained within the IoT device. ML algorithms will analyze organizational relationships and data dependencies to assess potential impact.
Q18: This question focuses on recovery costs by identifying IoT devices with the highest maximum downtime. The maximum downtime refers to the maximum acceptable outage (MAO) for a particular device. ML models will analyze historical downtime data and identify the potential recovery costs.
-
C.
Device Score Computation
For each identified device, the automated system calculates the device score by assigning weights to each criterion. The importance given to each criterion may vary depending on the organization's priorities. For example, some organizations may prioritize protection cost over profit, resulting in a different device score during the assessment process. The formula computes the final device score for a given IoT device is as follows:
where
W is the specific weight assigned by the SMG after performing a careful device assessment (
DA) and n is the number of questions in the template.
3.2.2. IoT Threat Assessment (TA)
The subsequent phase in risk evaluation entails identifying and ranking all the threats that pose a risk to your network. This process allows us to prioritize the threats and assets by assigning them rankings, enabling us to address the ones that require immediate attention. By doing so, we aim to anticipate potential attacks, determine their targets, and implement necessary safeguards to prevent their destruction. This step holds immense significance in safeguarding our IoT infrastructure and comprehending the nature of the threats and their potential consequences. Without adequately assessing the threats, we would remain oblivious to their magnitude and the extent of potential damage they could inflict. In this section of our risk management framework, we recommend that the SMG pose the following questions. Each question serves as a basis for evaluating the identified IoT devices. ML are integrated into each step of the threat assessment to automate and enhance the accuracy of this process, machine. These models analyze historical incident data, real-time threat intelligence, and various environmental factors to predict and prioritize threats effectively. By leveraging ML, the evaluation becomes more dynamic and precise, allowing for continuous updating and refinement of threat assessments as new data is gathered. The SMG will review the outputs generated by the automated system at the end of the TA process. The insights gained from these questions also assist in informed decision-making regarding security investments, risk management strategies, and resource allocation. It enables the organization to make informed choices based on the identified threats and their potential consequences.
- A.
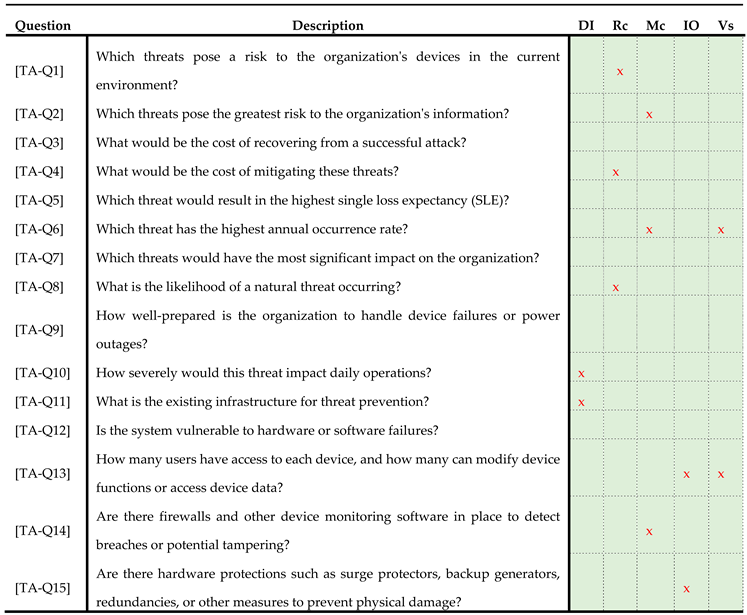
Template Questions for TA
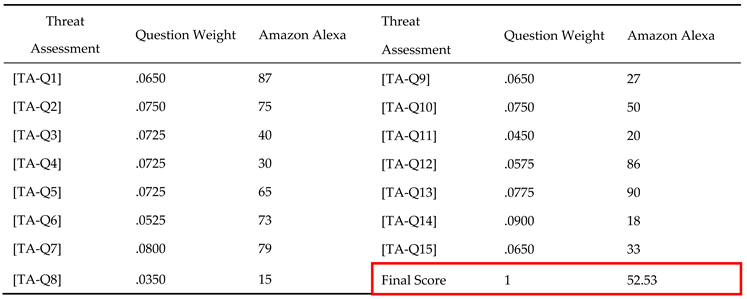
Template 2 presents the Threat Assessment (TA) questions related to the risks and impacts on devices and information in an organization's environment. It includes additional columns for device and information impact, cost considerations, single loss expectancy (SLE), impact on the organization, and system vulnerability. Automated systems will use these questions to gather comprehensive data points and provide a detailed assessment of each threat, making the evaluation process more thorough and data driven.
- B.
Explanation of TA Template Questions
Q1: This question evaluates the potential harm posed by threats to the devices in their specific environment. By estimating the probability of each threat occurring, ML algorithms can identify and eliminate threats with the lowest probability, ensuring that resources are focused on addressing more significant risks.
Q2: This question aims to determine which threats pose the greatest danger to the organization's information integrity. By evaluating the impact of each threat on the organization's information assets, ML algorithms can prioritize measures to safeguard sensitive data, assess threat data and identify risks to information security based on vulnerability scans and incident reports, and mitigate risks to information security.
Q3: The goal of this question is to assess the cost of recovery from a successful attack. By using the "Recovery Cost" as a criterion, predictive analytic tools will estimate the expenses associated with recovering from each identified threat. Identifying threats with higher recovery costs allows the organization to prioritize the mitigation of those threats posing a more substantial financial impact.
Q4: This question aims to determine the cost of preventing the identified threats. By calculating the prevention cost for each threat and device, cost estimation ML algorithms can assess the resources required to implement preventive measures. Identifying threats with higher prevention costs helps allocate resources effectively to address serious risks.
Q5: This question aims to identify the threat that results in the highest SLE for the organization. Risk assessment ML algorithms will calculate SLE by evaluating potential impact and exposure.
Q6: This question aims to identify the threat with the highest annual rate of occurrence. Statistical ML models will predict annual occurrence rates by analyzing historical threat data. By examining the frequency of each threat's occurrence, the statistical ML models can prioritize measures to address threats that pose a higher risk.
Q7: This question is designed to identify threats that have the most substantial impact on the organization. These threats can harm the organization financially, affect operational time, and impact productivity. ML models will analyze potential threat scenarios and their consequences. Identifying such threats allows the organization to prioritize mitigation efforts to minimize their impact.
Template 2.
IoT Device Level Threat Assessment (TA) Questions and Attributes.
Template 2.
IoT Device Level Threat Assessment (TA) Questions and Attributes.
Q8; This question focuses on assessing the chance of natural disasters based on the organization's geographical location. Predictive ML models will use geographical and historical data to estimate the likelihood of natural threats. By considering historical data on natural disasters, such as floods, fires, or tornadoes, the organization can plan and prepare for these events accordingly.
Q9: The objective of this question is to evaluate the accessibility of device and power backups within an acceptable timeframe known as Maximum Acceptable Outage (MAO). ML algorithms can help determine the duration the organization can operate without electricity or critical functions and help assess the availability and timeliness of backups for resuming normal operations.
Q10: This question aims to assess the impact of threats on everyday operations. The objective is to determine whether the organization can continue operating and resume daily functions without a loss of critical assets. Operational ML models can simulate threat scenarios to evaluate their impact on daily operations.
Q11: This question focuses on quantifying the effectiveness of the current threat prevention infrastructure. Infrastructure analysis ML tools can help evaluate the performance of firewall systems, anti-virus software, and user authorization controls, helping to determine the level of protection provided by the existing infrastructure and suggest necessary improvements.
Q12: The goal of this question is to evaluate the vulnerability of hardware and software components to failure. ML based vulnerability assessment can help conduct diagnostic tests, identifying potential weaknesses and assign ratings based on performance, enabling targeted efforts to address vulnerabilities.
Q13: This question determines the number of users with access to each device and their ability to alter device functions or access device data. Access control automated systems will analyze user permissions and monitor access patterns to identify risks. Understanding user interactions helps identify potential compromises and reinforces the importance of limiting access to as few users as possible for improved threat protection.
Q14: The objective of this question is to assess the presence of firewalls and other device monitoring software that can detect breaches or potential tampering. Security monitoring systems will evaluate the deployment and performance of firewalls and other monitoring tools. Proper monitoring enhances device traffic control and facilitates the interception and prevention of breaches. The absence of firewall protection or inadequate physical safeguards can leave devices vulnerable to external attacks and tampering.
Q15: This question focuses on evaluating the implementation of hardware protections such as surge protectors, backup generators, redundancies, and other measures to prevent physical damage. Physical security assessment ML models will analyze the presence and effectiveness of hardware protections. By having appropriate countermeasures in place, the organization can safeguard hardware from undetectable physical events like power surges, leaks, fires, and emergencies.
-
C.
Threat Score Computation
For each identified threat, the automated system will calculate the threat score by assigning weights to each criterion. For instance, some organizations give more preference to recovery cost than the probability of the threat, which may change the threat score during the evaluation process. The formula to compute the final threat score for a given IoT device is as follows:
(2)
where W is the specific weight assigned by the SMG after performing a careful threat assessment (TA) and n is the number of questions in the template.
Ts: Threat Score, which is the final score assigned to the identified threat.
TAQi: Threat Assessment Question (TAQ) score for each criterion. This score represents the evaluation of the threat based on a specific criterion.
Wi: Weight assigned by the SMG to each criterion i. This weight reflects the relative importance or preference given to the criterion during the threat assessment process.
To calculate the threat score, the equation sums up the products of the TAQ scores and their corresponding weights for each criterion. The resulting sum is then divided by the total number of questions or criteria, n, to obtain the average score, The purpose of this equation is to provide a quantitative measure of the threat's severity and potential impact based on the assessment criteria and their assigned weights. By assigning weights to different criteria, the automated system can prioritize certain aspects of the threat evaluation process, such as recovery cost or probability. This allows for a tailored assessment that aligns with the specific preferences of the organization conducting the evaluation.
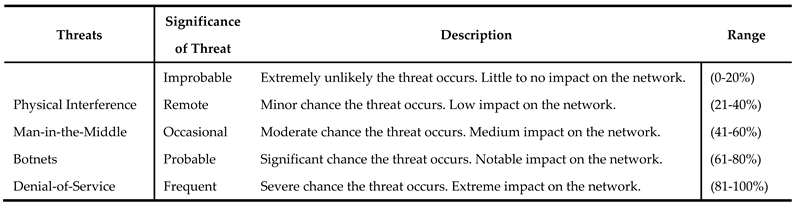
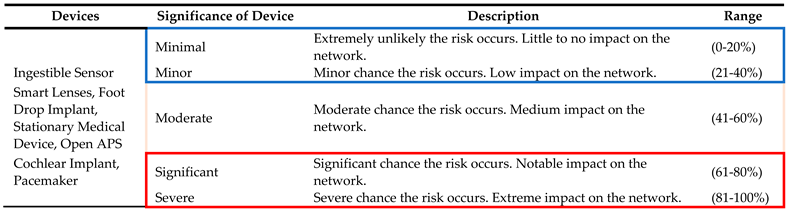
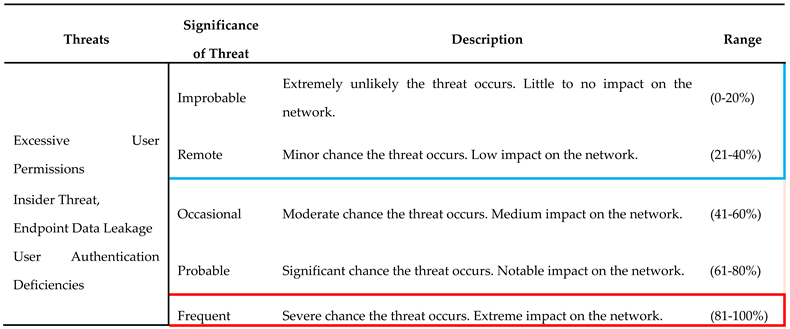
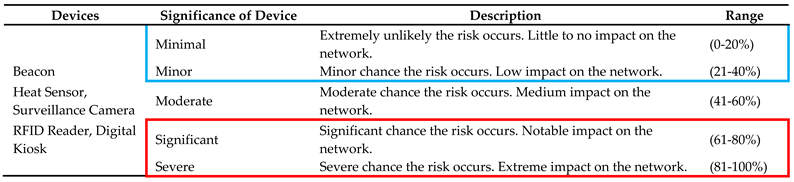
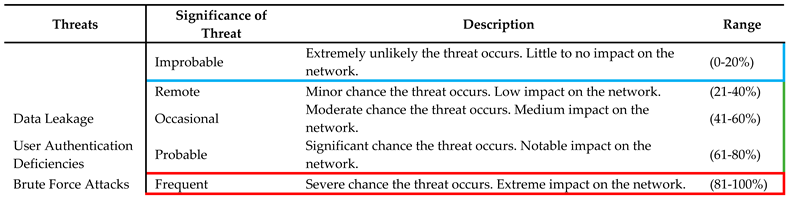
3.2.3. Likelihood of Threat Occurring
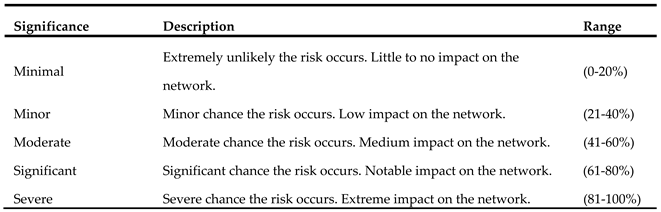
The third phase in the risk evaluation process involves determining the probability of each identified threat occurring. The probability assessment is typically categorized on a scale, and we propose a five-step scale: frequent, probable, occasional, remote, and improbable. It is vital to assess threat likelihood because of the varying impacts that different threats can have. Several threats may bring high impact but a low probability of occurrence; regardless, these threats must be addressed, as even infrequent incidents can result in significant harm. Thus, it is paramount to be prepared for an incident as such. Although, there are threats that pose low risk and have low probability indicating that they do not pose substantial risk. The highest level of risk is associated to threats with a high probability of occurrence and capability for significant damage. In estimating threat event probability, ML models consider the outcomes of the device and threat assessments conducted in the previous steps of the risk management framework. Initially, ML models consider the outcomes of the previous two steps of the risk management framework, which involve device and threat assessments Additionally, the existing security controls implemented as part of the organization's security infrastructure should be considered. Conclusively, the overall risk environment and health of the organization play a crucial role. It is important to note that the probability of a threat is inversely related to the effectiveness of existing security controls and the overall risk environment within the organization.
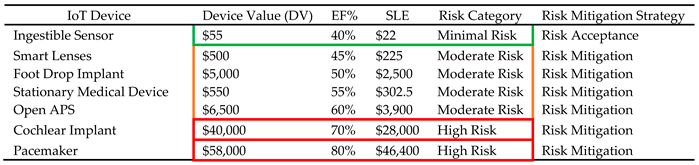
3.2.4. Risk Factor Computations
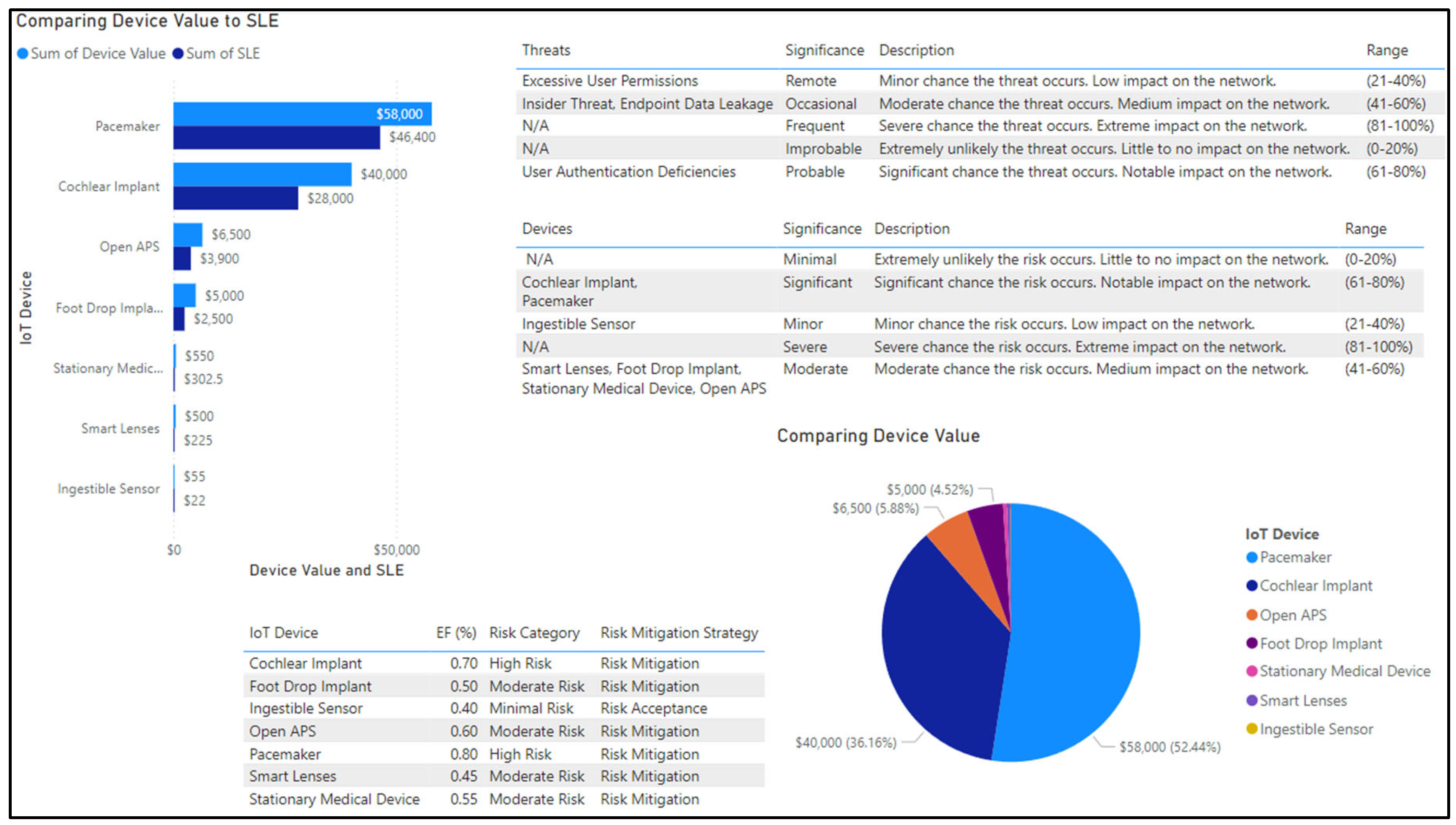
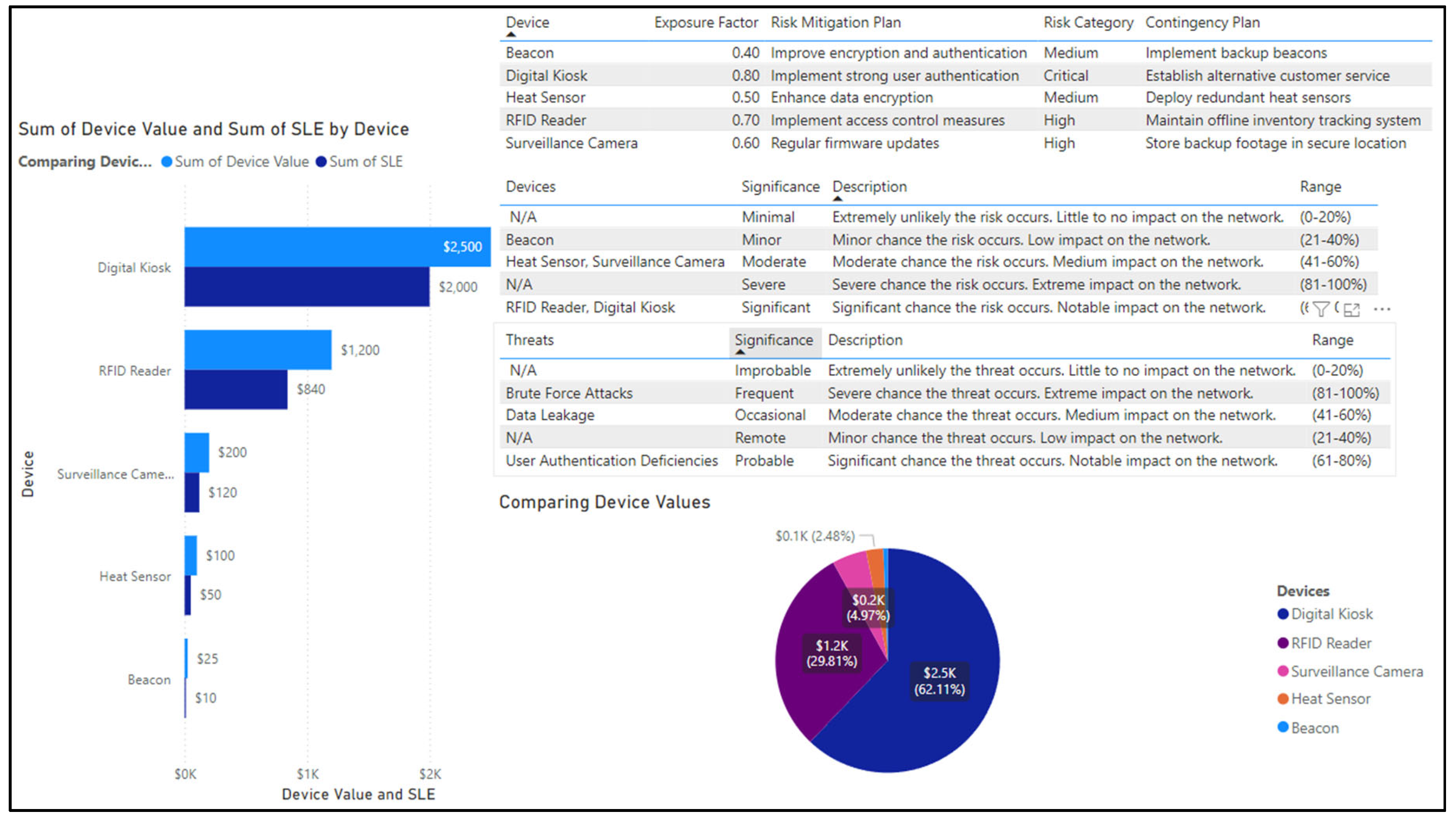
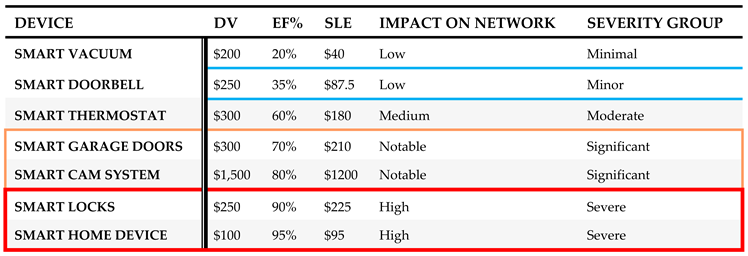
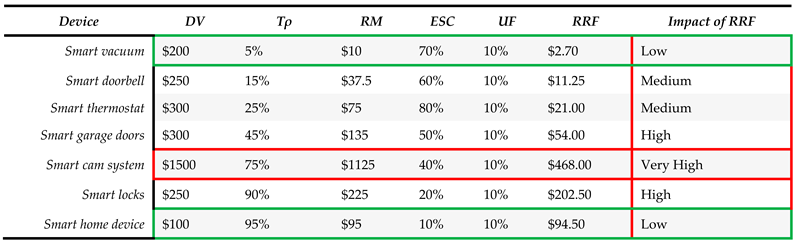
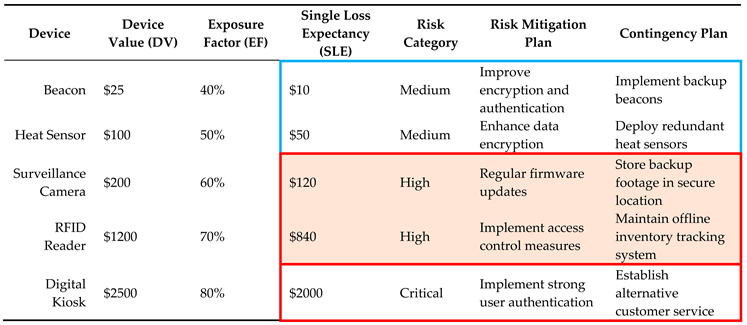
The fourth step is to calculate relative risk factors for each IoT device. The relative risk factors are found by utilizing SLE and Risk Magnitude (RM). SLE is used to represent how much money we can expect to lose if a risk occurs. This can be found by multiplying the device value by the exposure factor percentage, as shown in (3).
where
DV: Device Value and
EF: Exposure Factor. Since Exposure Factor is a subjective value, it is possible that a risk analyst or SMG may not have a good estimate of EF or it is not available at all. In this case, we compute risk magnitude (RM) to estimate the impact of a potential security risk. We use RM to combine how significant the effects of risk are with the probability of that risk occurring. This can be found by multiplying the asset value and the probability of a threat, as shown in (4).
where
DV: Device Value and
Tρ:Threat Probability.
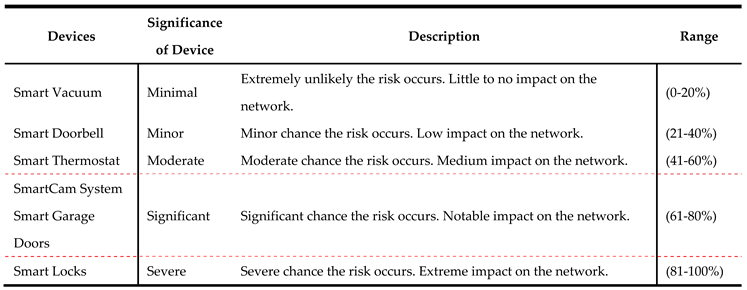
To enhance the accuracy and precision of threat impact estimation, machine learning (ML) models are used to compute the relative risk factor (RRF) for each IoT device. ML models analyze historical data, real-time threat intelligence, and environmental factors to provide dynamic and precise risk evaluations. When calculating the RRF for a device, we must first consider what the threat is, how vulnerable the device is, and the importance of the asset that could be made unavailable. In addition, we also consider the existing security controls () and the uncertainty factor () as part of RRF computation since both () and () play a role in neutralizing the impact of a threat. For instance, a higher value of reduces the RRF whereas a higher value of increases the RRF.
The ML models can dynamically adjust these factors based on continuous learning from new data, improving the accuracy of the risk assessment over time. Lastly, in the documentation part of this step, ML models could calculate the risk factor and document all relevant findings. By incorporating ML into the computation of risk factors, the organization can achieve a more automated, precise, and dynamic approach to evaluating the risks associated with IoT devices. This approach ensures that the risk assessments are continuously updated and based on the most current data, enabling better preparedness and response strategies.
where RM: Risk Magnitude = (
);
: Existing security control;
: Uncertainty Factor
C. Template Questions for DA
For each identified threat, the automated system will calculate the threat score by assigning weights to each criterion. For instance, some organizations give more preference to recovery cost than the probability of the threat, which may
3.4. Risk Analysis
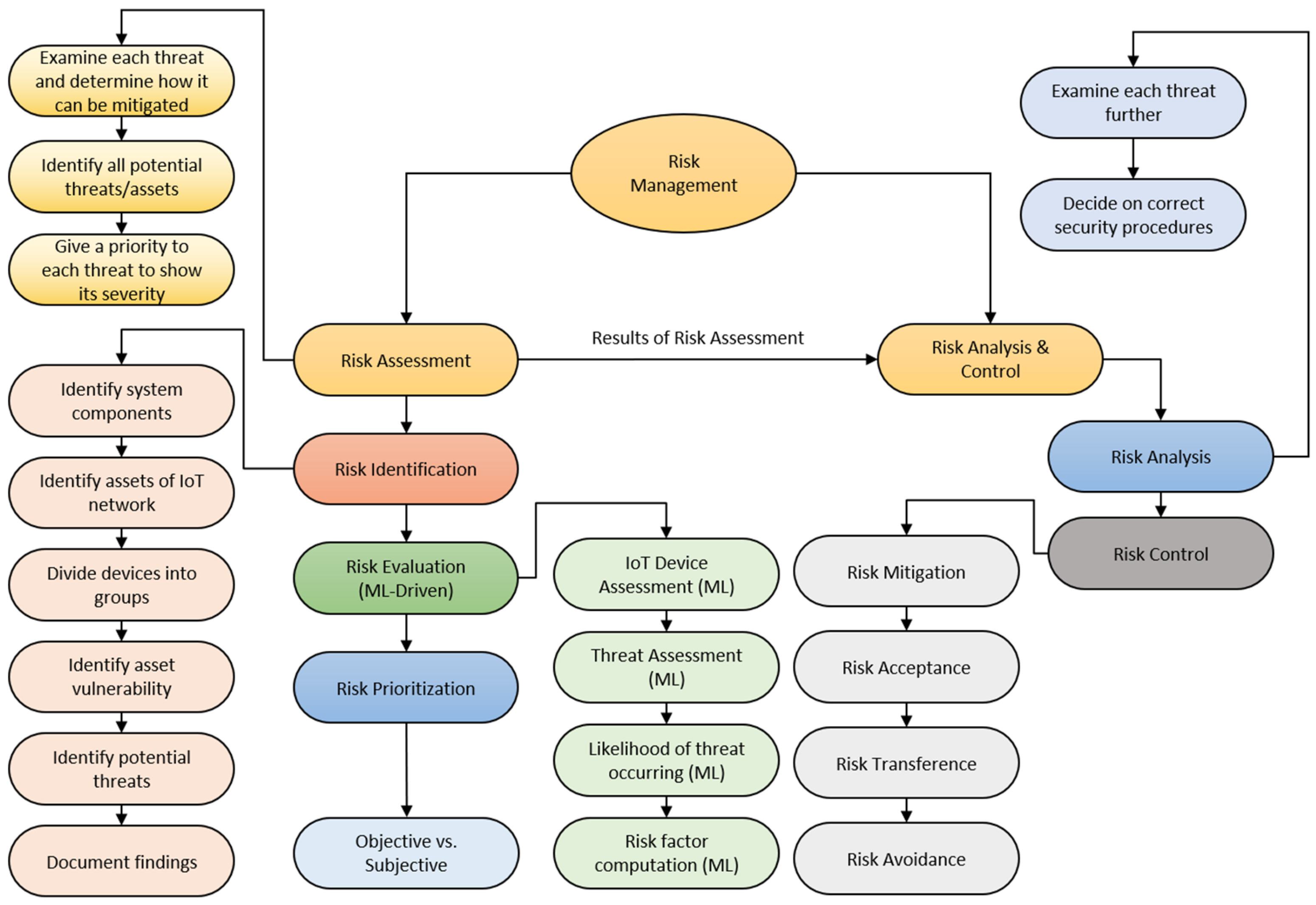
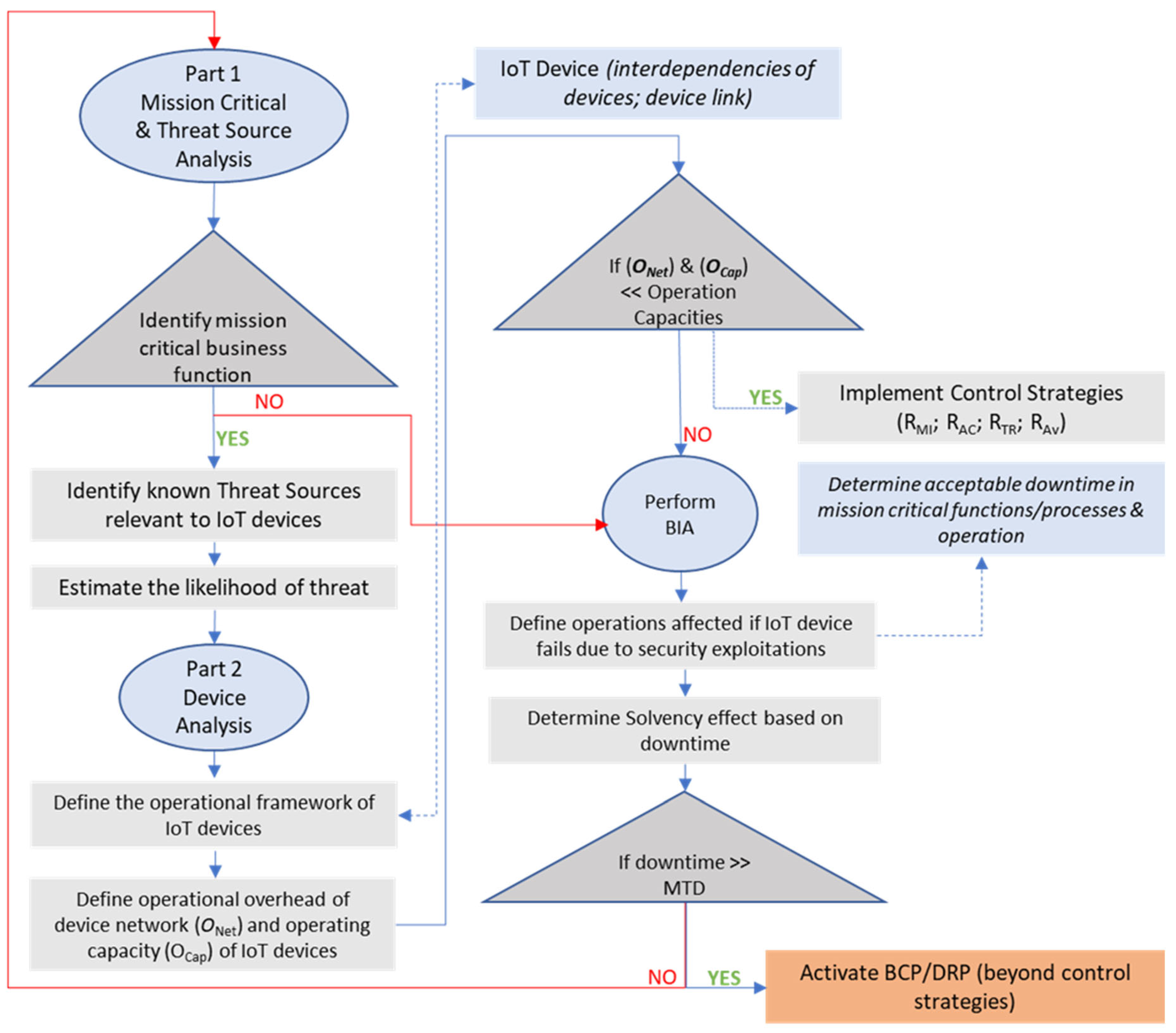
During this phase, we further inestigate each threat to determine the appropriate security policies and procedures for managing the risks faced by IoT devices. This step allows us to identify any vulnerabilities in the IoT devices and strengthen their security measures. Conducting a comprehensive analysis enables us to devise effective countermeasures against the identified threats. To streamline the risk analysis process, this section offers a step-by-step approach outlined in
Figure 4. Risk analysis can be a time-consuming aspect of the overall assessment process, particularly in the case of IoT devices. These devices often operate within multiple frameworks, making it challenging to apply a standardized framework. Consequently, they require diverse aspects of protection. The risk analysis phase is divided into two parts. In part 1, the SMG examines the mission-critical resources of the business and conducts a thorough analysis of the sources of threats. In part 2, the SMG analyzes each IoT device to define its operational framework, understanding the necessary measures to safeguard it from the known threat sources. For each part of this phase, we present a systematic methodology that the SMG can adopt during the risk analysis process.
3.4.1. Part 1: Mission-Critical and Threat Source Analysis
Step 1: Identify Mission-Critical Business Functions: This involves defining the current essential functions and activities that must be safeguarded during a threat event. To effectively mitigate or prevent threats, it is crucial to prioritize the protection of mission-critical activities and functions. Thus, before considering other device-related factors, it is necessary to determine the business's current objectives, critical functions, and mission statements in order to frame the risk analysis and ensure the preservation of these elements during threat events.
Step 2: Identify Relevant Threat Sources: Identify all known threat sources that are applicable to the organization and the devices under examination. Consolidate information about existing threats into a comprehensible document that outlines which devices or functions they may exploit and the potential consequences of successfully exploiting vulnerabilities in those devices or functions.
Step 3: Assess the Likelihood of Threat Sources: Evaluate the probability of threat sources posing credible threats to the organization and the likelihood of them exploiting assets or device functions. Each threat source presents a potential problem for the organization's operations. Therefore, it is necessary to examine the likelihood of their occurrence and weigh it against the potential negative impact if a threat event successfully exploits a vulnerability. Considering the potential rate of occurrence and the potential consequences of exploitation will enable more accurate risk management considerations for the assets.
3.4.2. Part 2: Device Analysis
Step 4: Define the operational framework of the threatened devices: It is necessary to examine how the device aligns with the organization's current operational framework. This entails understanding the device's role within the chain of operations, its interface with other devices, and its contribution to accomplishing the organization's mission statement or goals.
Step 5: Define the current operational overhead and capacity of the device network: The network infrastructure of the organization requires a specific level of overhead to ensure efficient functioning. When implementing controls or risk management techniques on the device, it is essential to ensure that they do not exceed the operational capacity. Otherwise, it may negatively impact other services, slow down network activities, and potentially disrupt mission-critical functions due to increased overhead.
Step 6: Identify the operational impact of device failure due to exploitation by a threat: Once the device's position in the current operational framework is established, the next step is to determine the consequences of a device compromise resulting from a threat event. Will certain mission-critical functions and operations experience downtime? If so, to what extent? Will a failure in one device trigger a cascade of failures, or will the impact be contained within a closed system?
Step 7: Assess the financial implications of downtime caused by threat exploitation: IoT devices, given their interconnected nature, can have wide-ranging effects if they fail and cause disruptions or delays in operational performance. It is crucial to determine the acceptable duration of such delays before the organization starts incurring financial losses and potentially suffers damage to factors such as consumer trust and reputation due to service outages or failures.
Step 8: Evaluate information security risks: In addition to threats to assets, operations, and individuals, it is necessary to examine information security risks. These risks involve the likelihood and potential impact of occurrences such as the exposure of user data, personal data, and other confidential information due to device failures or the exploitation of vulnerabilities.