Submitted:
27 July 2024
Posted:
30 July 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Introduction of Public Key Infrastructure
1.2. Working of Asymmetric Cryptography
Generation of Public and Private Key Pair
Encryption
Decryption
Key Security
Potential Vulnerability
1.3. Introduction to Quantum Computers
2. Background
2.1. Need for Post-Quantum Cryptography
2.1.1. Shor’s Algorithm
2.1.2. NIST’s Post-Quantum Cryptography
2.1.3. Threat of Data Harvesting
2.2. IoT and Post-Quantum Cryptography
2.3. Problem Statement
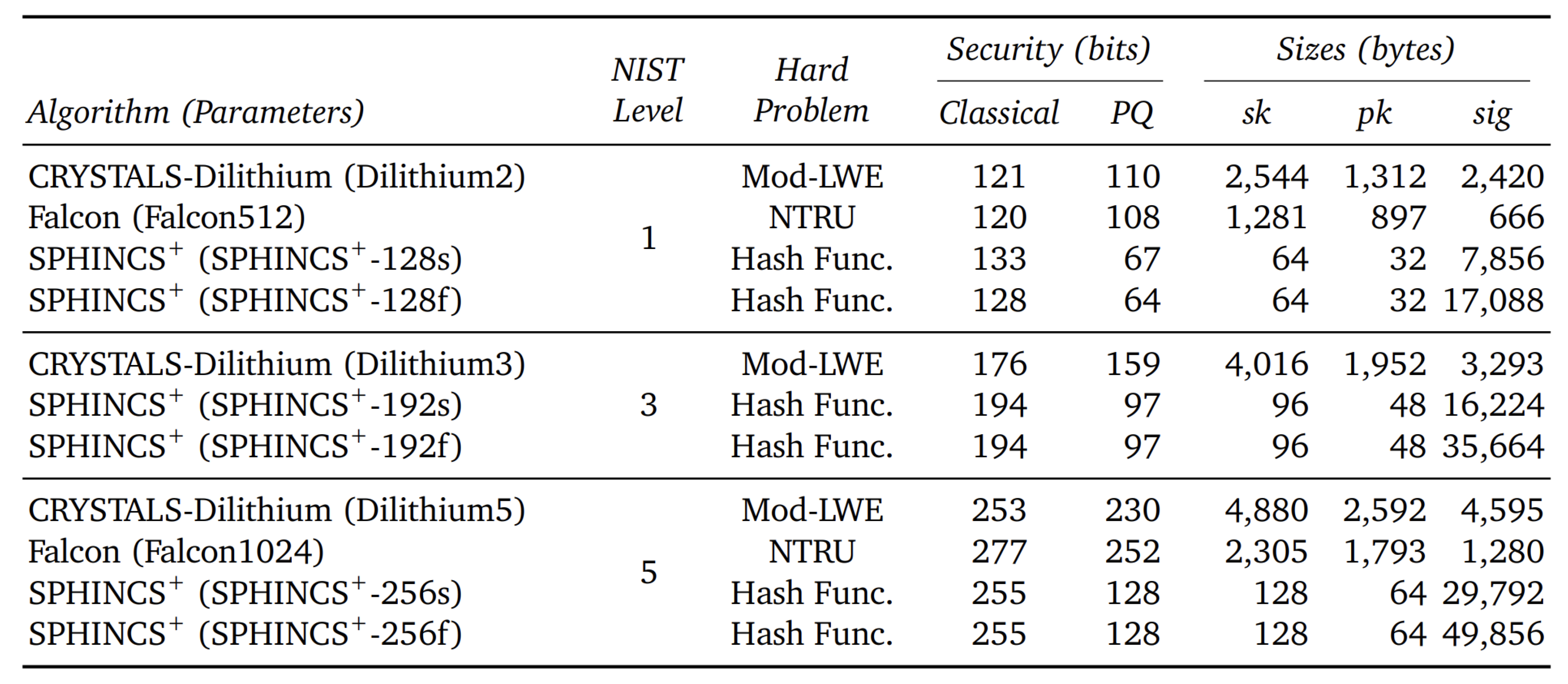
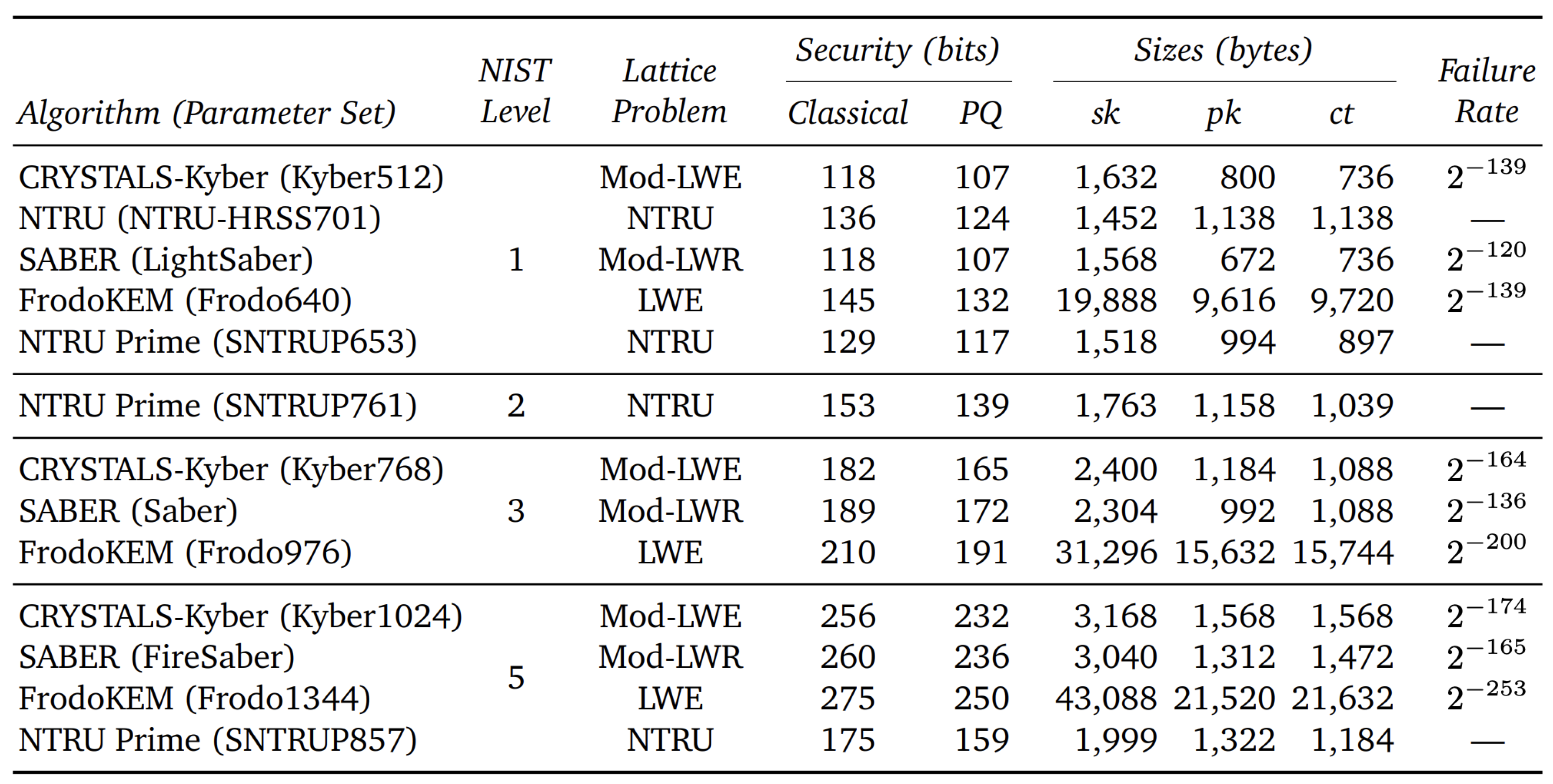
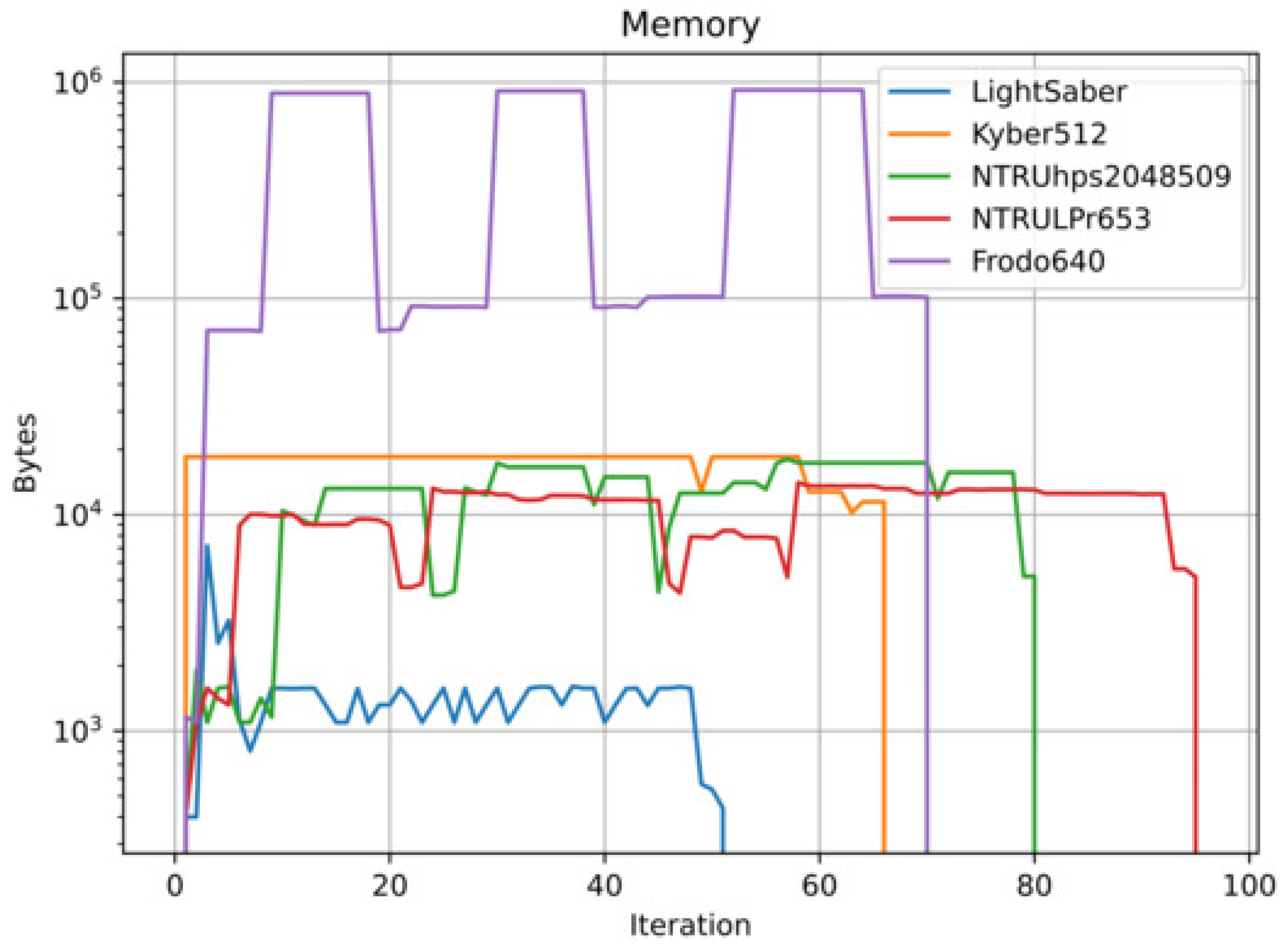
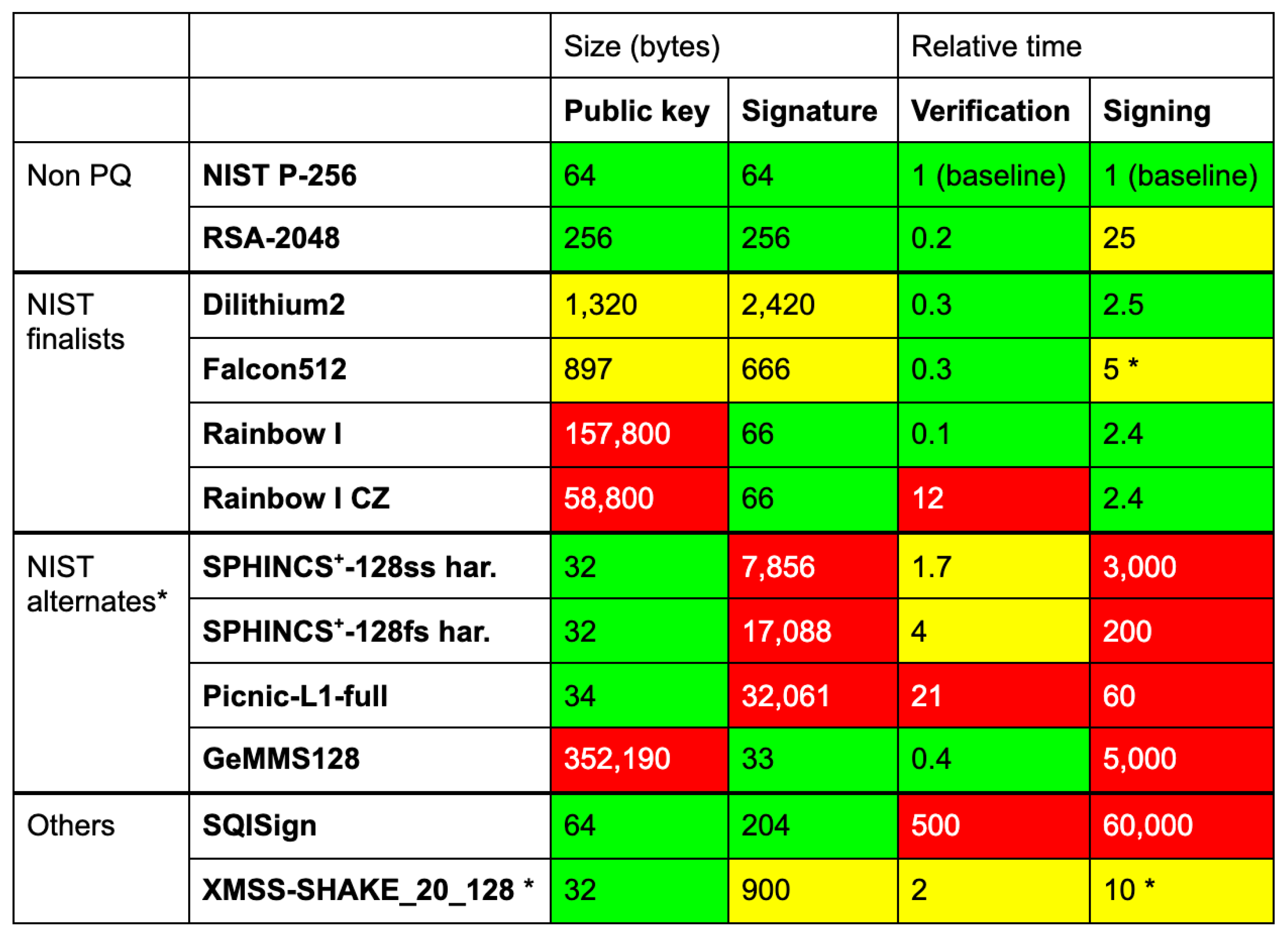
3. Literature Review
4. Proposed System
4.1. Current Smart Cities Infrastructure
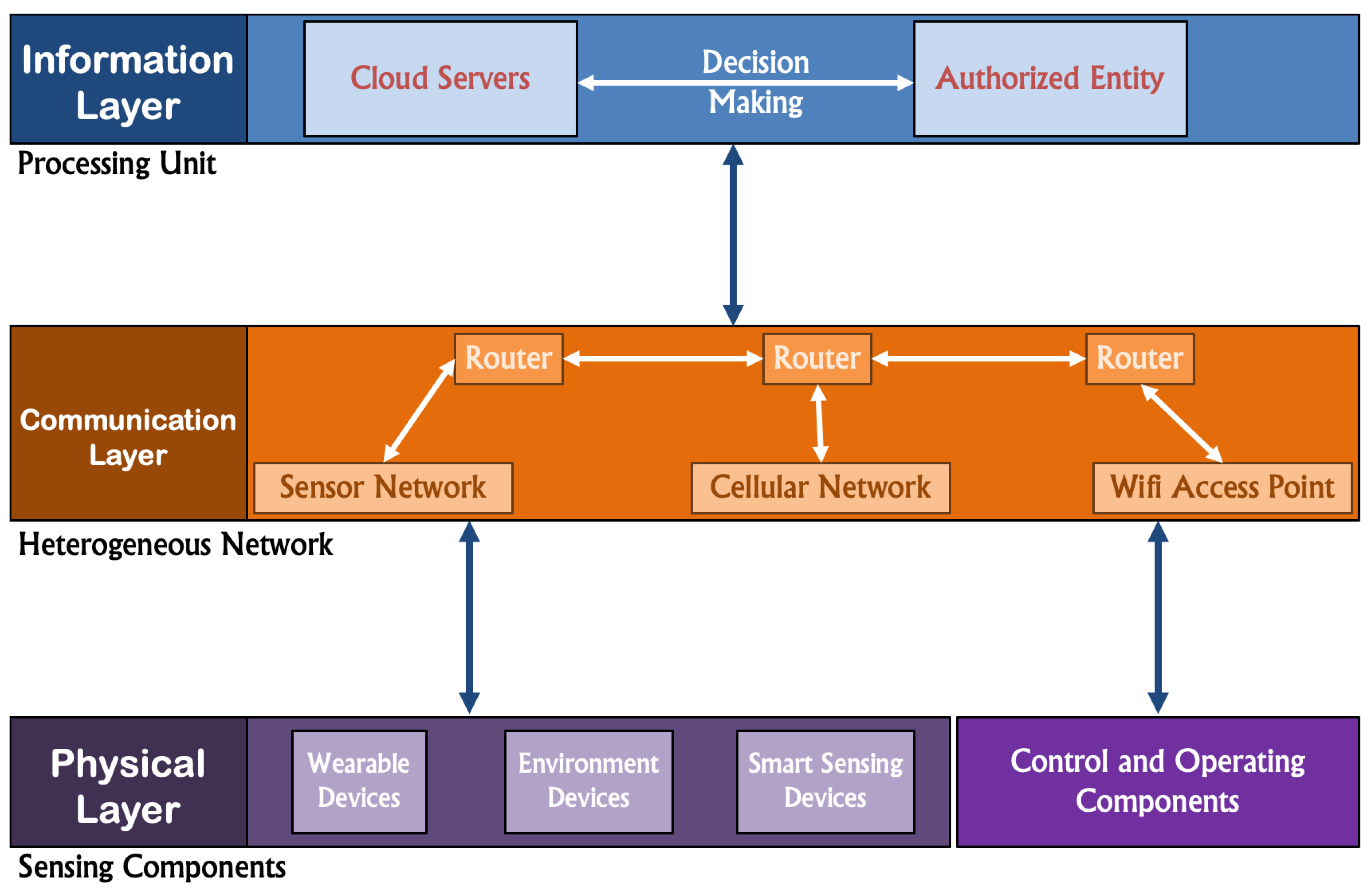
4.2. Issues with the IoT in Smart Cities
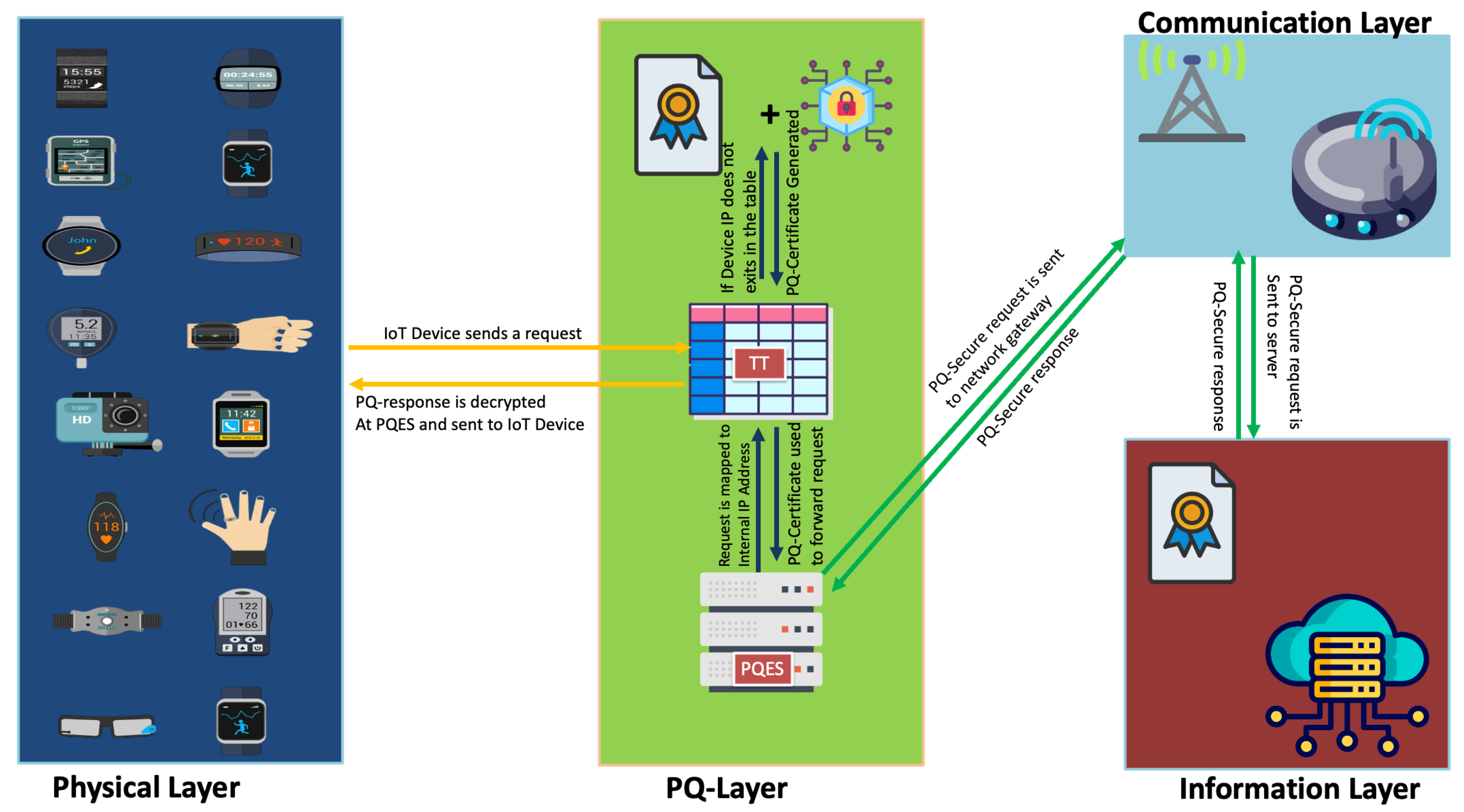
4.3. Proposed Solution
4.4. Implications of Proposed System on Smart Cities
4.4.1. Efficiency and Performance
4.4.2. Scalability and Interoperability
4.4.3. Security and Future-Readiness
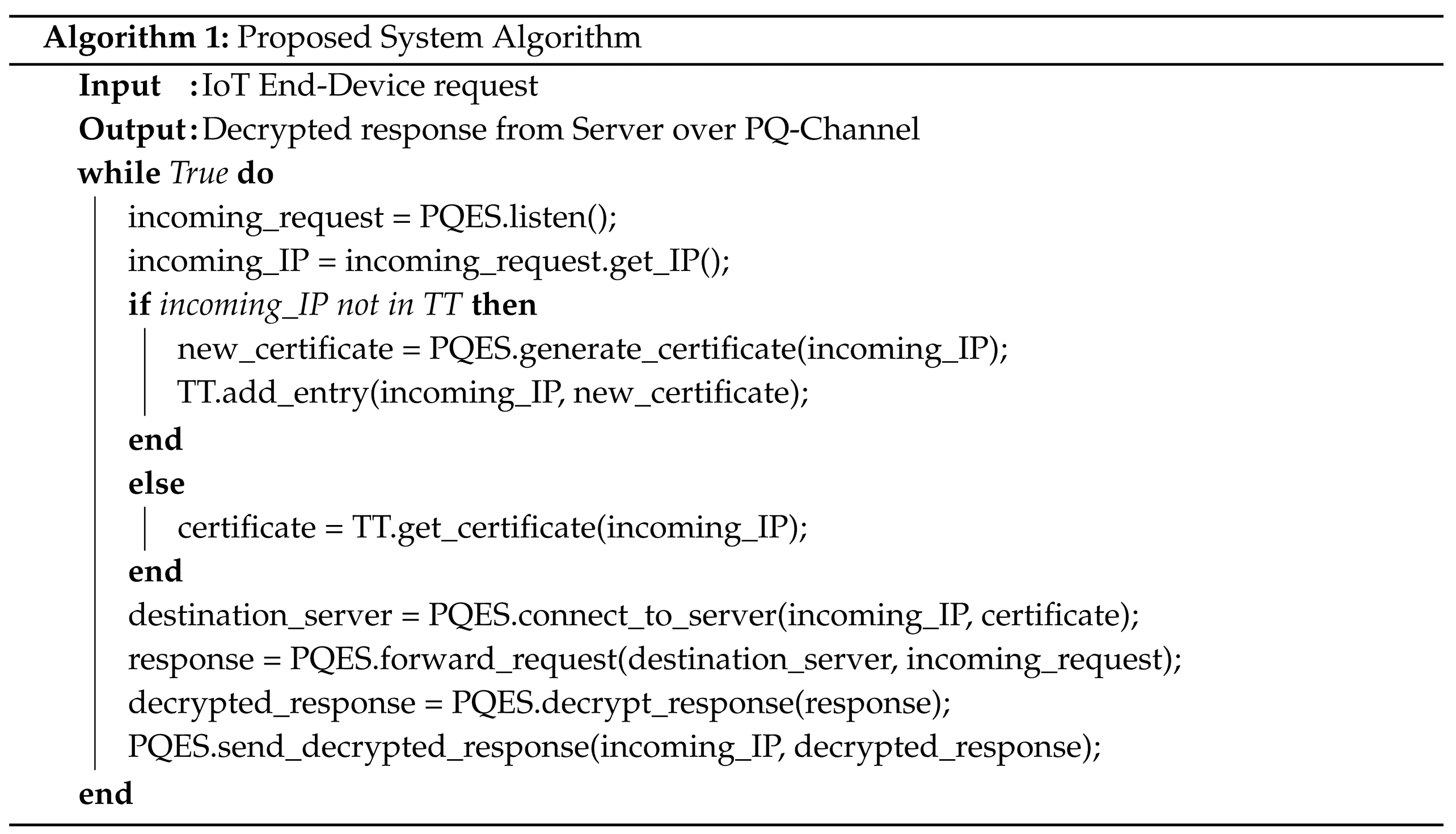
4.5. Proposed System Algorithm
Initialization
- Set up the proposed network-level proxy server.
- Setup the proposed PQES with a TT.
Listening for Requests
- The PQES listens for incoming requests.
Processing Incoming Requests
- The PQES checks if the incoming IP exists in TT.
- If does not exist in TT, PQES generates a new PQ certificate for incoming IP and adds an entry for the respective TT.
- If exists in TT, then PQES reads the respective PQ certificate.
Establishing Connection
- PQES creates a connection with the destination server using PQ-certificate for .
Forwarding Request
- PQES forwards the request to the destination server.
Receiving and Decrypting Response
- PQES receives the response from the destination server and decrypts the response.
Sending Decrypted Response
- PQES sends the decrypted response to .
5. System Implementation
5.1. Algorithms Evaluated
- Dilithium Level 2 with Kyber Level 1.
- Dilithium Level 2 with Kyber Level 3.
- Dilithium Level 2 with Kyber Level 5.
- Dilithium Level 3 with Kyber Level 1.
- Dilithium Level 3 with Kyber Level 3.
- Dilithium Level 3 with Kyber Level 5.
- Dilithium Level 5 with Kyber Level 1.
- Dilithium Level 5 with Kyber Level 3.
- Dilithium Level 5 with Kyber Level 5.
5.2. Implementation Details
- A Raspberry-Pi Model-B with 1GB RAM and 1.5 GHz Processor to act as the end IoT device running a TCP client programmed in GoLang with a front-end developed using SvelteJS and Wails.
- This Raspberry Pi is connected with a DS18B20 body temperature sensor and Max30100 Heart Rate and Oxygen Saturation sensor to generate and send data to a remote server.
- Another Raspberry Pi Model-B with 1GB RAM and 1.5 GHz Processor to act the PQES.
- An Intel Core-i5 2.60 GHz processor with 8GB RAM running a PQ TCP server on WSL programmed in C language.
- PQES is a combination of a PQ-TCP server and a PQ-TCP client where the earlier interacts with the end IoT device and later interacts with the WSL PQ-TCP server. Both components of PQES were programmed in C language.
- LibOQS+WolfSSL generated the PQ certificates generated and used in these settings.
Evaluation Metrics
- Percentage of CPU used by each algorithm.
- Number of CPU context switches performed.
- RAM (in MBs) used during each test run.
- Network used (in Bytes) to perform each transaction between client-server by using the respective algorithm.
6. Results
6.1. Proposed System Results
| Algorithm | Architecture | CPU % Usage | CPU Context Switch | RAM MB Usage | Network Bytes Transferred |
|---|---|---|---|---|---|
| Dilithium2_Kyber1 | CN | 49.715 | 1858.55 | 435.33 | 600589.750 |
| PR | 1.380 | 49.84 | 10.14 | 2150.78 | |
| Dilithium2_Kyber3 | CN | 52.738 | 1904.85 | 437.22 | 754461.1 |
| PR | 1.375 | 45.70 | 10.22 | 1689.14 | |
| Dilithium2_Kyber5 | CN | 46.95 | 1841.8 | 438.96 | 616428.78 |
| PR | 1.14 | 42.70 | 10.53 | 1254.59 | |
| Dilithium3_Kyber1 | CN | 52.39 | 1838.6 | 438.99 | 667720.73 |
| PR | 1.31 | 50.54 | 11.55 | 1655.54 | |
| Dilithium3_Kyber3 | CN | 58.26 | 2131.52 | 440.61 | 962430.88 |
| PR | 1.33 | 39.30 | 9.92 | 1733.32 | |
| Dilithium3_Kyber5 | CN | 52.63 | 1799.74 | 441.75 | 718451.23 |
| PR | 1.43 | 51.79 | 10.31 | 1946.38 | |
| Dilithium5_Kyber1 | CN | 60.05 | 2096.56 | 444.79 | 1050030.4 |
| PR | 1.49 | 52.05 | 11.34 | 2244.16 | |
| Dilithium5_Kyber3 | CN | 51.66 | 1824.91 | 443.31 | 592386.83 |
| PR | 1.36 | 47.81 | 11.31 | 1592.71 | |
| Dilithium5_Kyber5 | CN | 57.97 | 2085.27 | 445.85 | 893928.28 |
| PR | 1.50 | 52.29 | 11.38 | 2288.23 |
6.2. Evaluation Metrics Results
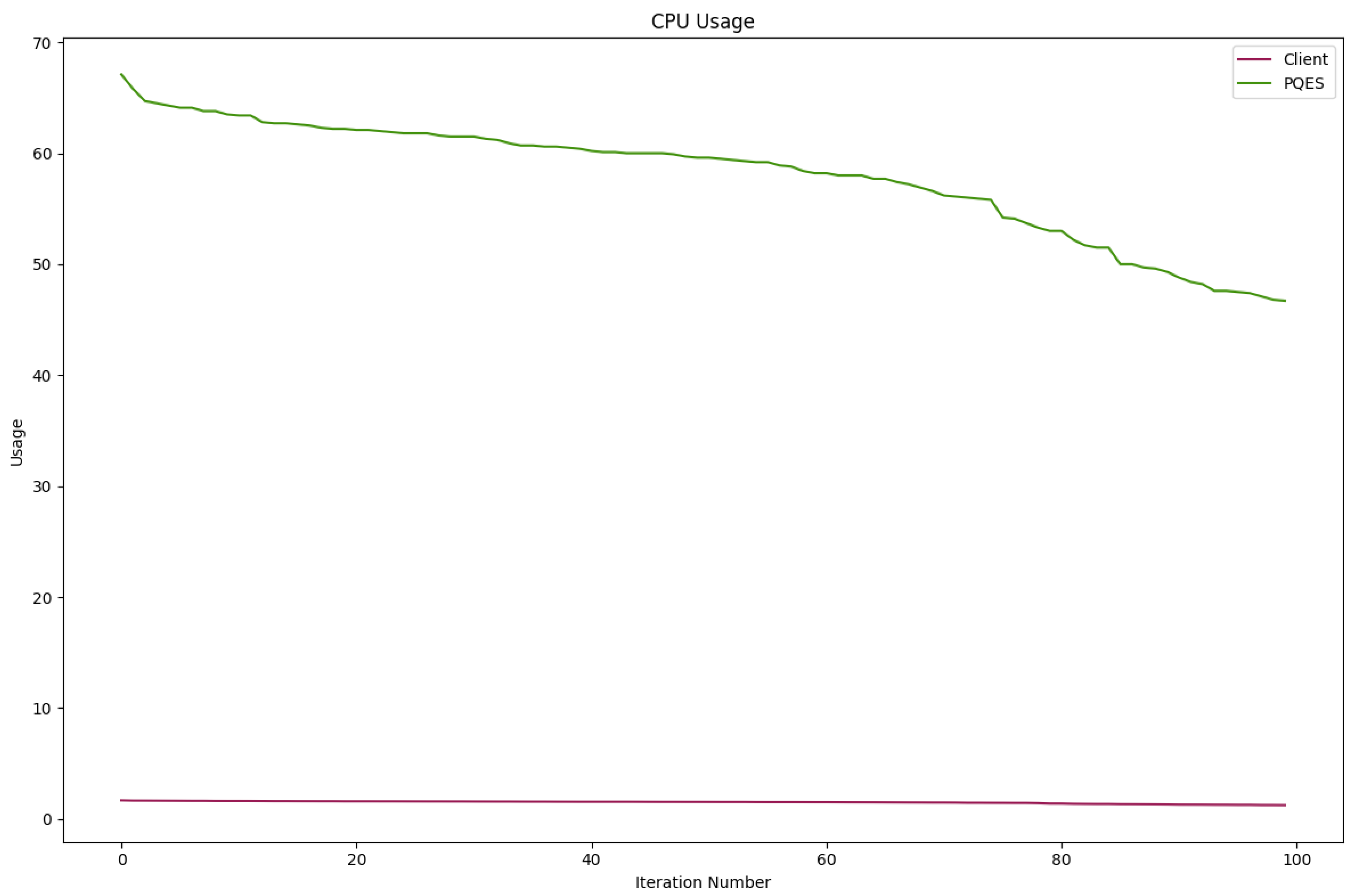
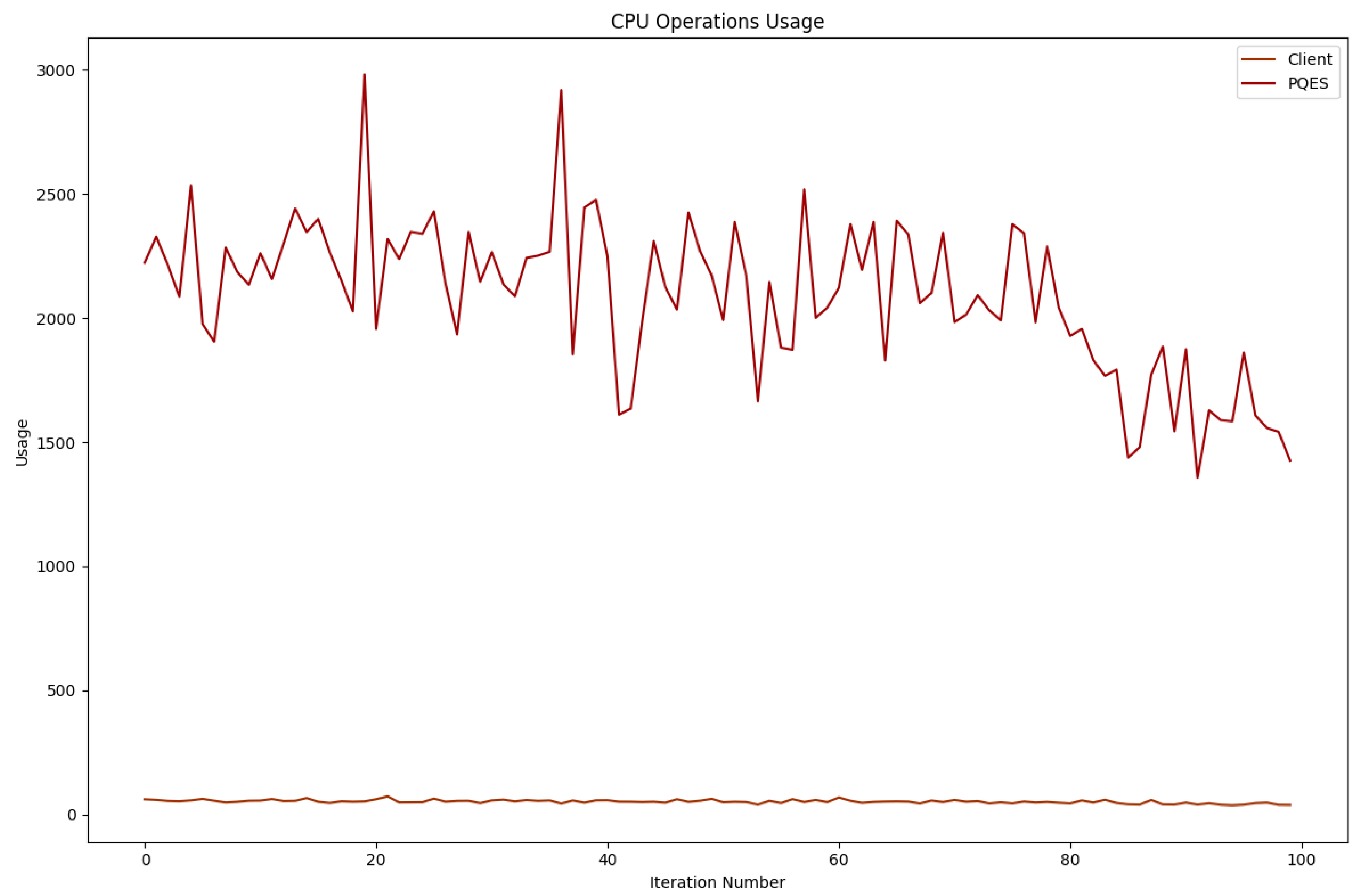
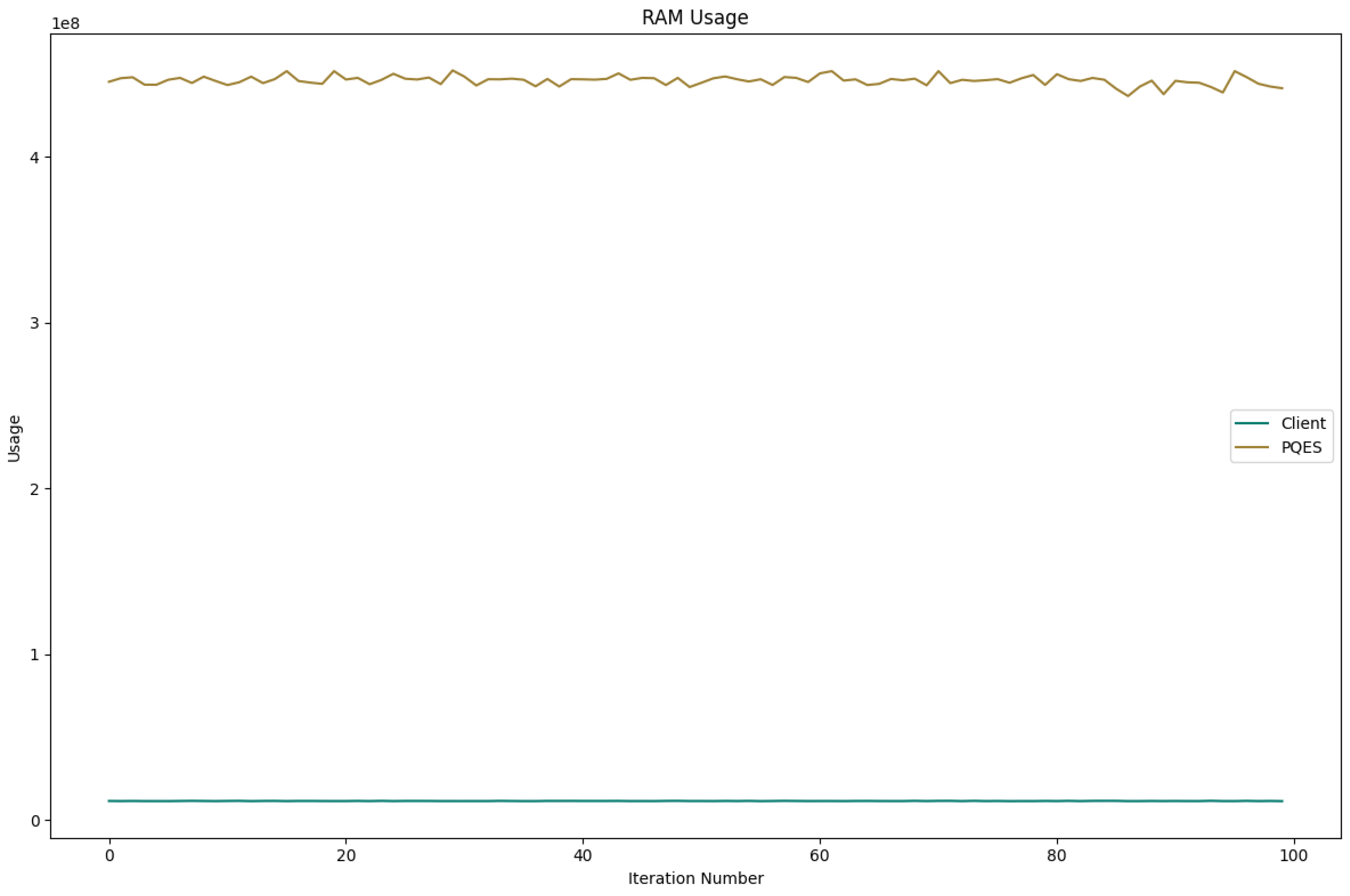
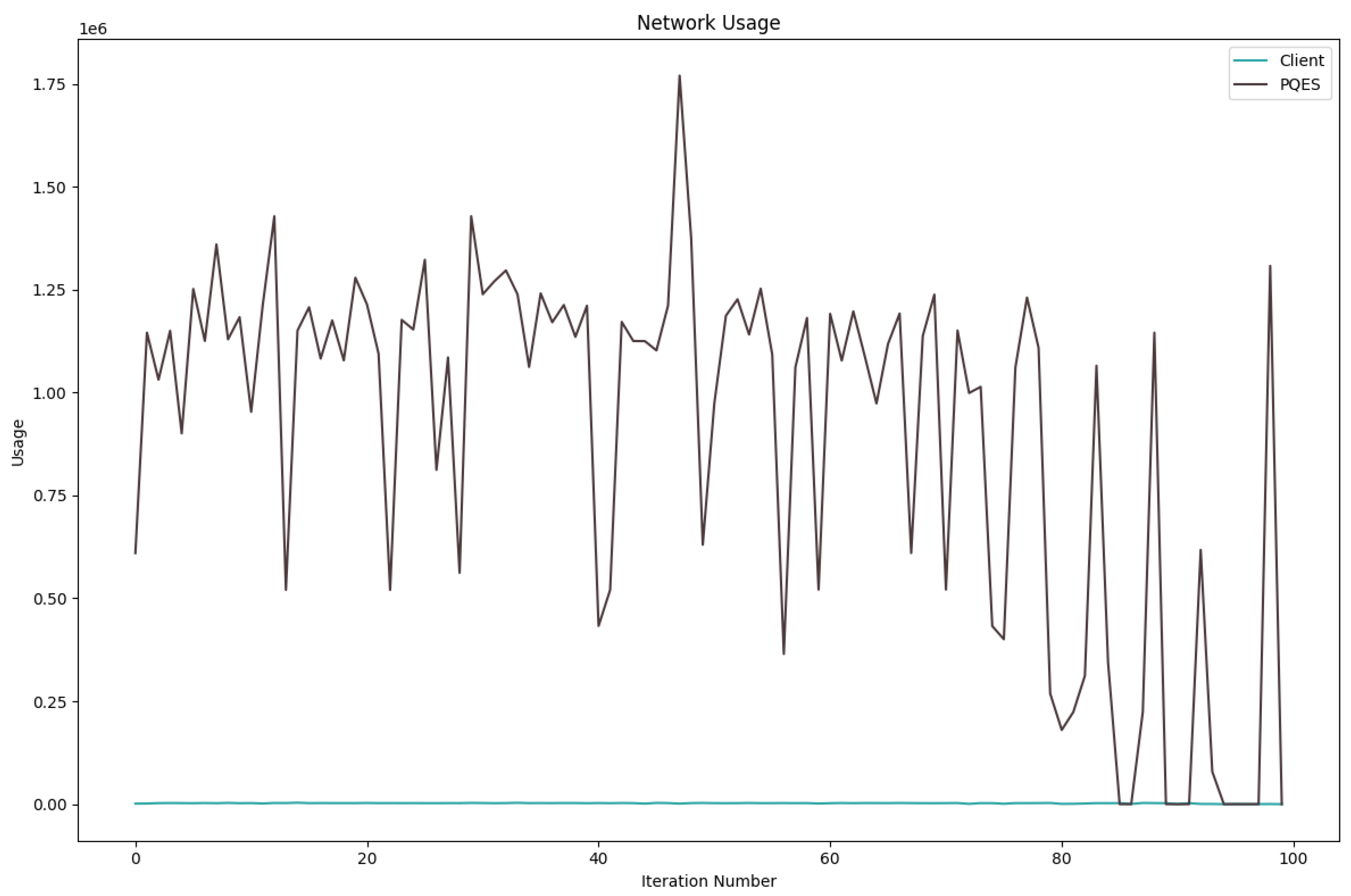
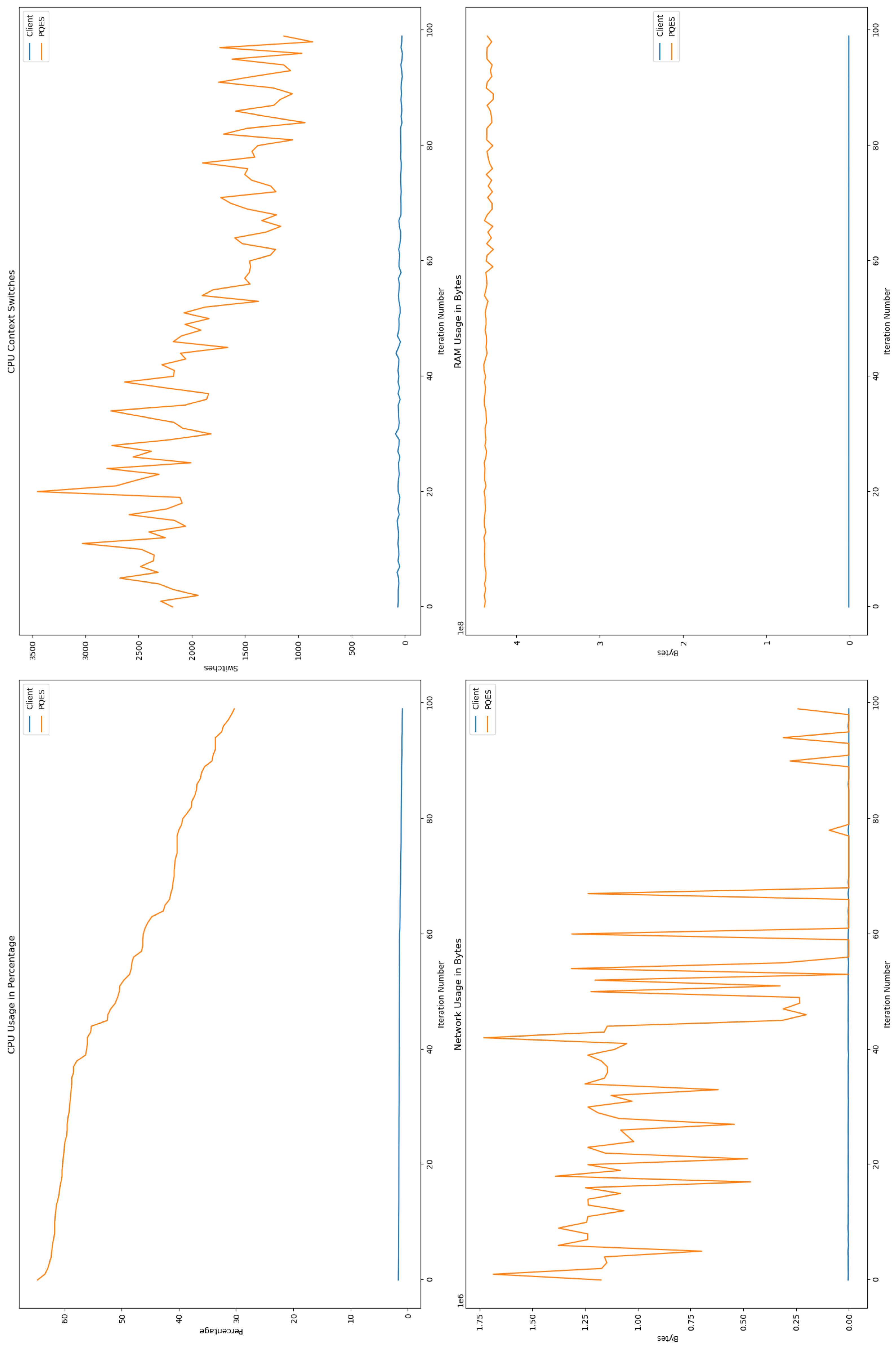
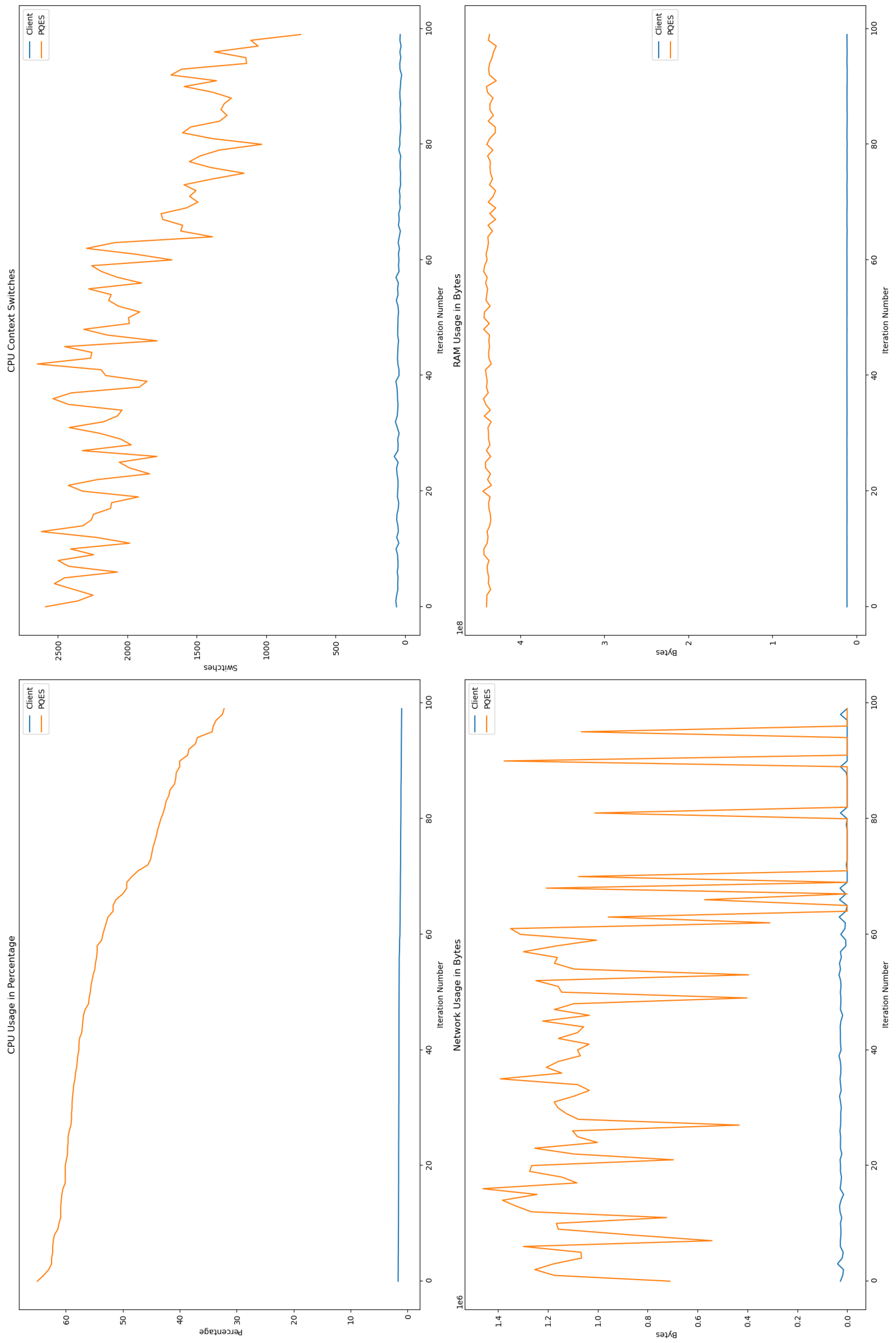
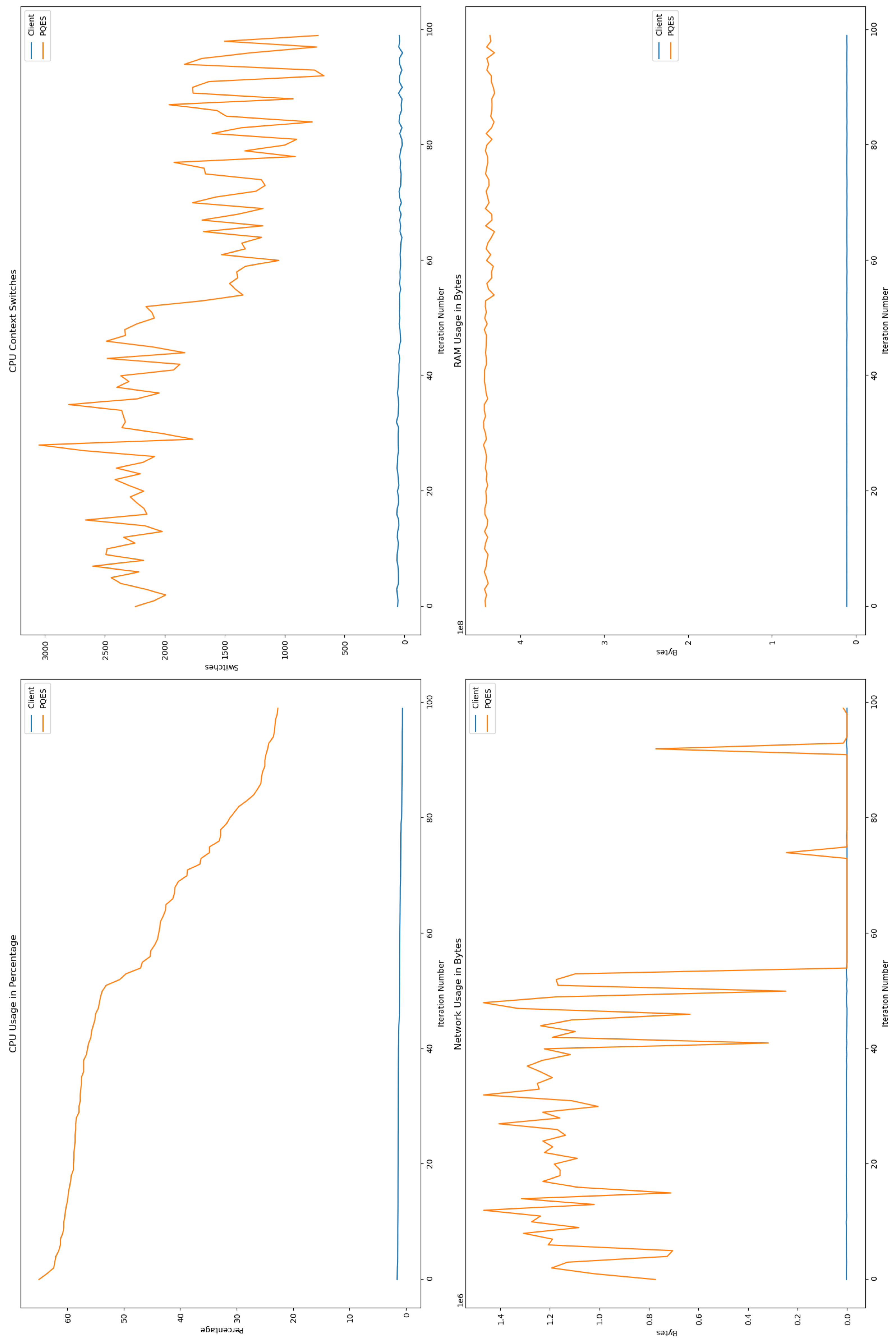
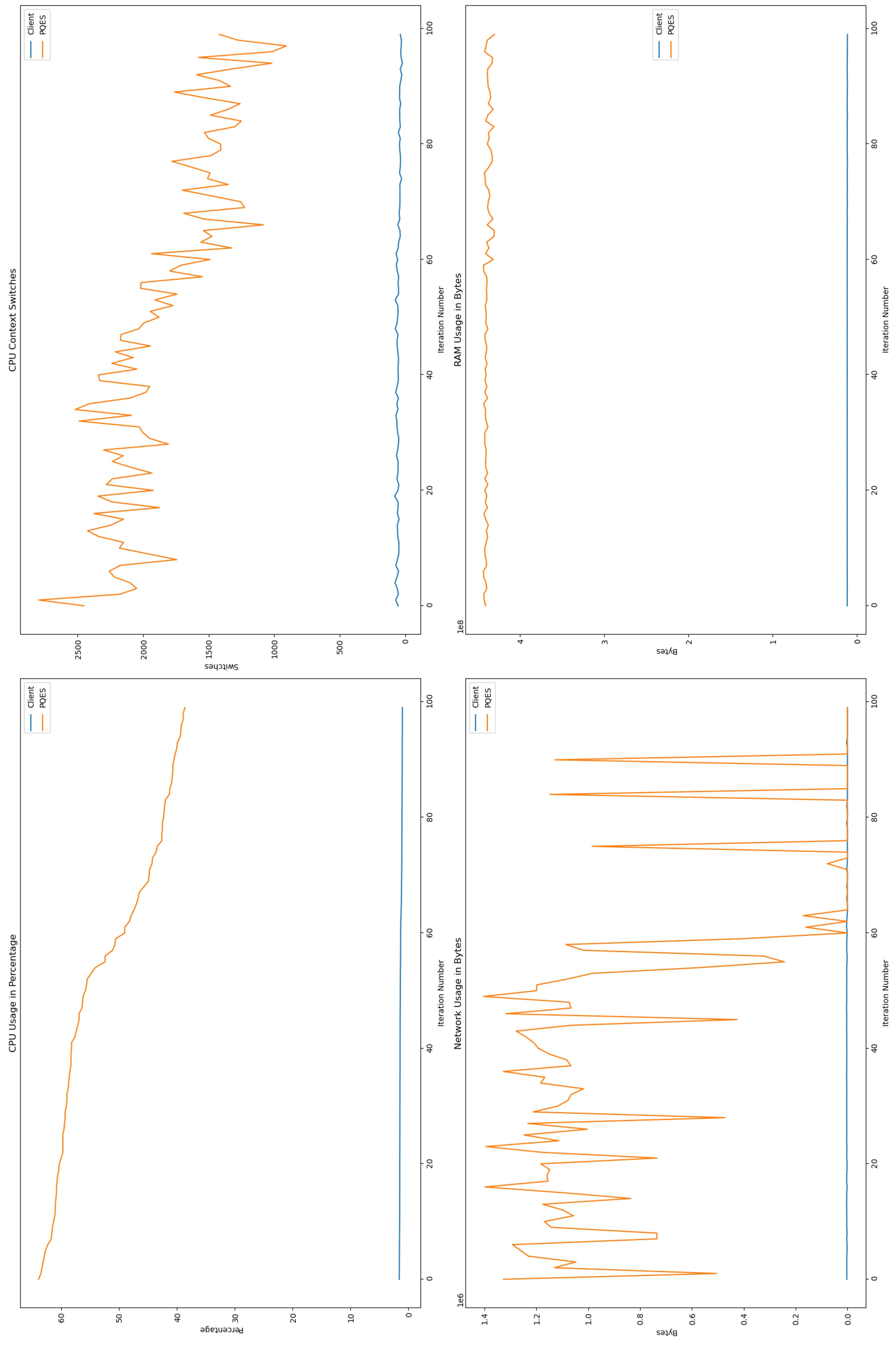
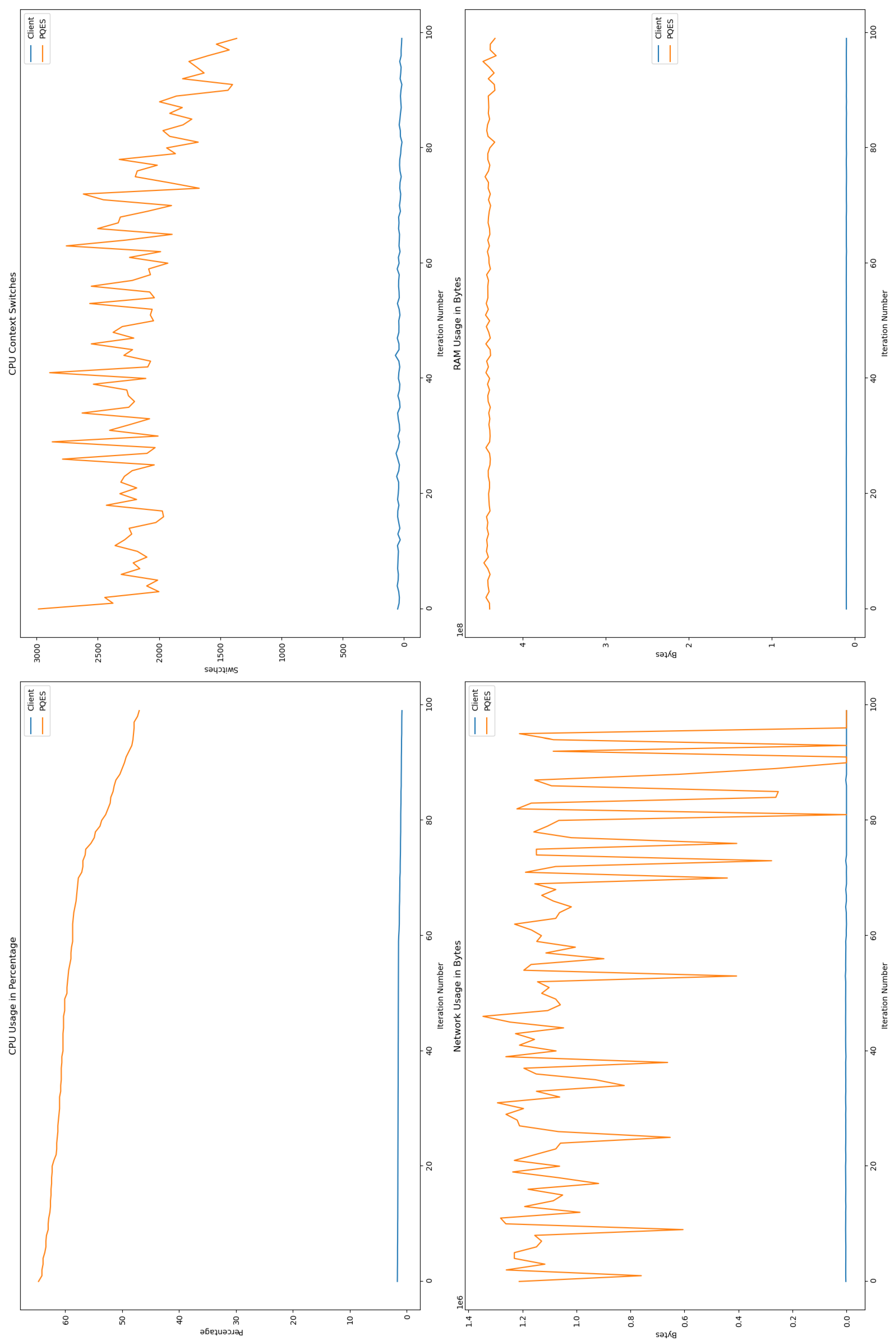
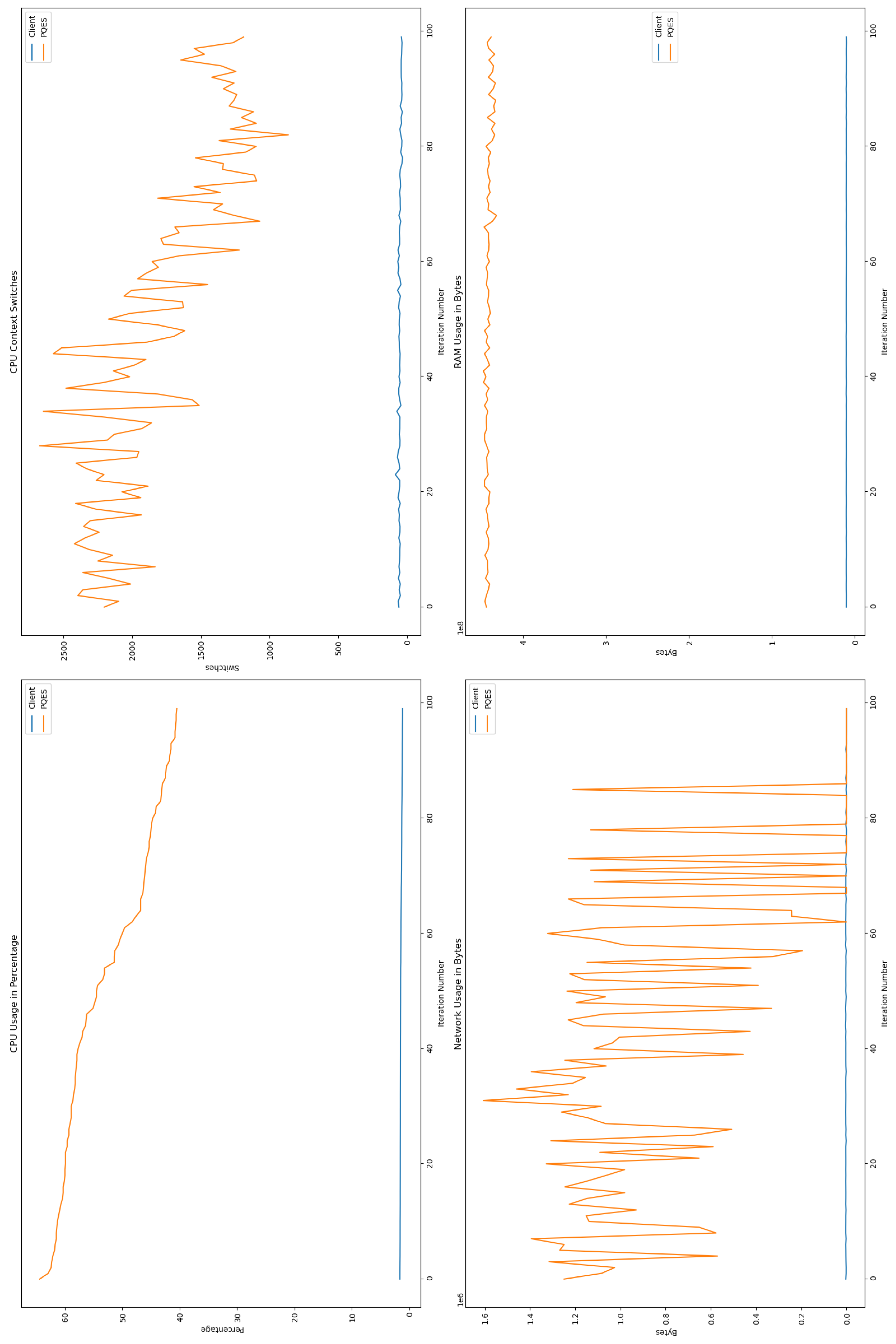
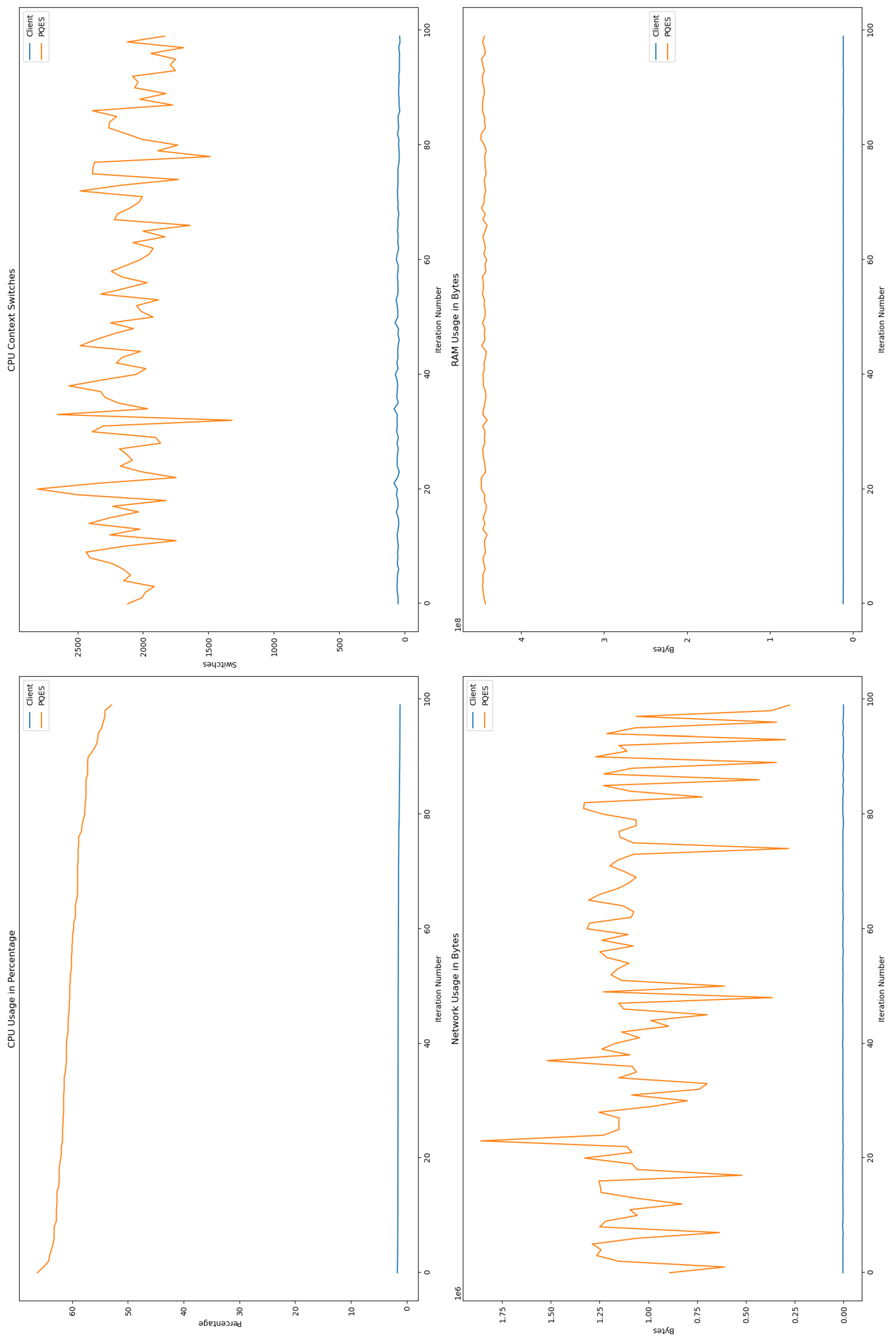
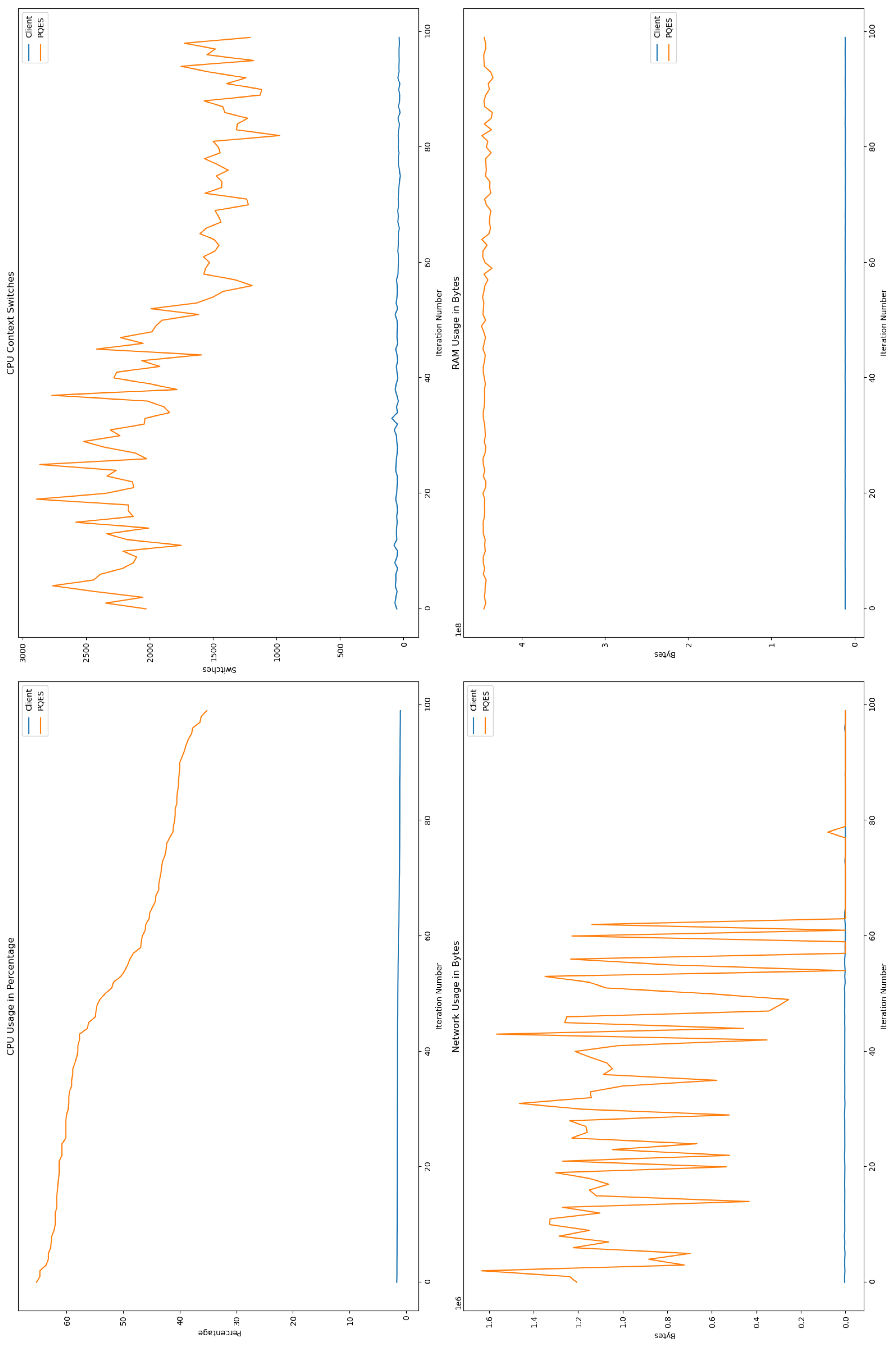
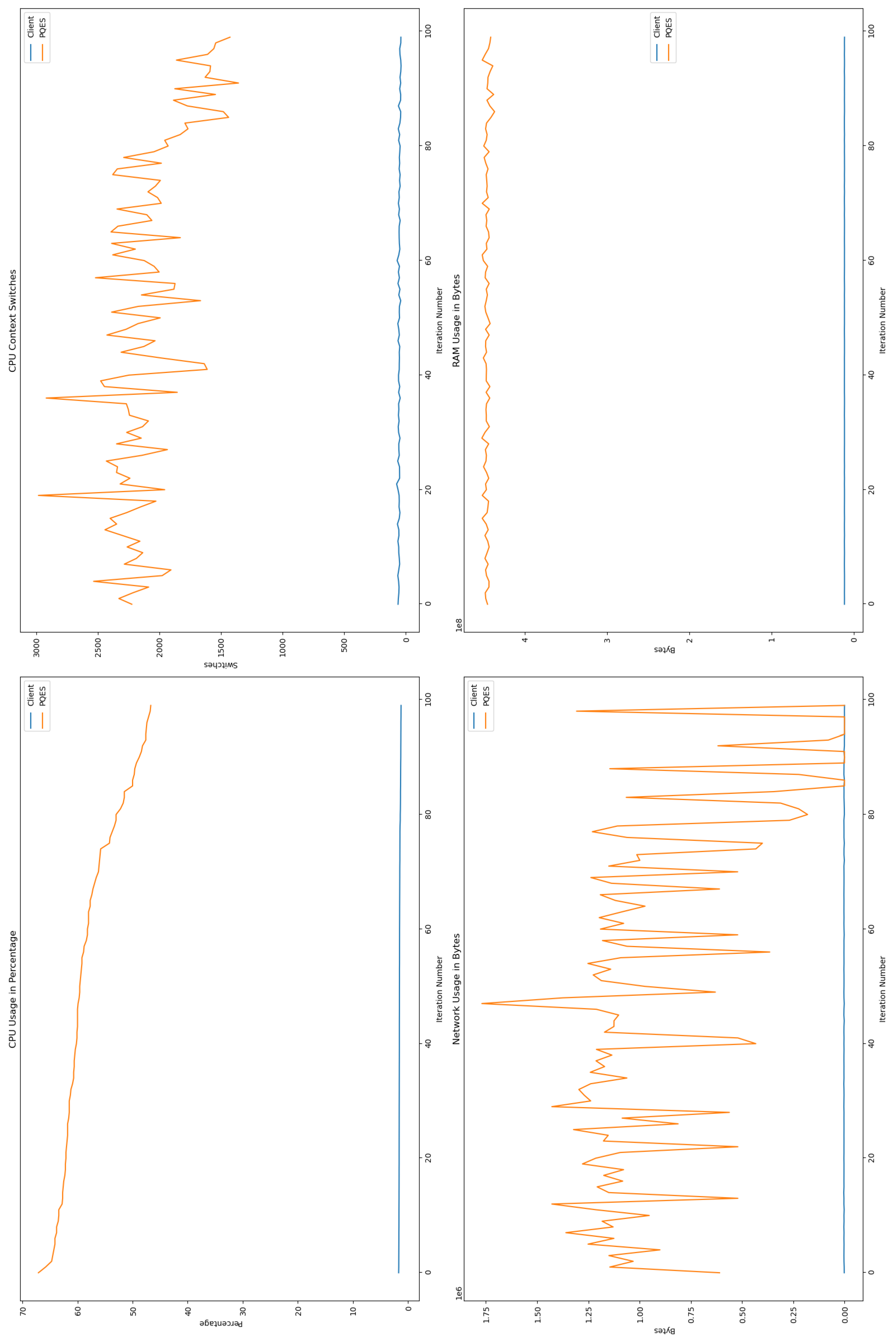
6.2.1. Percentage of CPU Used By Each Algorithm
6.2.2. Number of CPU Context Switches Performed
6.2.3. RAM Used By Each Algorithm
6.2.4. Network Used By Each Algorithm
6.3. Comparative Analysis
6.4. Discussion
7. Future Work and Conclusion
7.1. Limitations
- Our scheme was evaluated by using a RaspberryPi-4B with 1GB. However, we can evaluate the proposed scheme on IoT devices on even more low-powered devices like ARM Cortex-M4 and other microprocessors. This can provide us with more authentic, realistic, and solid results to verify our approach.
- Our proposed architecture implements PQC-based security for all data going out from a network; however, this does not provide data security for traffic inside the network as our scheme assumes that the traffic inside the internal network is secure. This can open up attacks on devices that do not use any encryption for their regular traffic between themselves and the router.
- Even though we propose using just the transport layer protocol for data communication for these devices to avoid implementing application layer protocols, we have used HTTP as our application protocol. We can enhance this work by evaluating this scheme with other application layer protocols like MQTT and CoAP.
7.2. Future Work
- To conduct additional evaluations on IoT devices with lower power specifications, such as ARM Cortex-M4 and other microprocessors, to provide more authentic and realistic results. This will help validate the effectiveness of the proposed system over a wider range of IoT devices.
- To enhance the internal network security by implementing additional security protocols to protect internal network traffic. One approach is to explore encryption techniques for internal network traffic to protect against potential attacks on devices that do not have encryption in their communication with the router.
- Evaluate the proposed architecture in combination with other application layer protocols such as MQTT, CoAP and others to improve and evaluate the performance. This will provide the assessment for scheme’s compatibility and effectiveness with other protocols, providing validation on its scalability and flexibility.
- Investigate other approaches to improve the effectiveness of the suggested approach, especially on low-powered IoT devices. This includes reducing computational overhead, enhancing energy efficiency, and optimizing system performance while assuring the same level of security.
- Evaluate the proposed approach in IoT environments to assess its suitability, scalability, and effectiveness in practical applications. This includes collaborating with industry and testing the program in a controlled IoT environment to gather empirical data and validate its efficiency.
7.3. Conclusion
Acknowledgments
Abbreviations
| IoT | Internet of Things |
| PQC | Post-Quantum Cryptography |
| PQES | Post-Quantum Edge Server |
| PKI | Public-Key Infrastructure |
| ICT | Information and Communication Technology |
| UMI | Universal Metering Interface |
| CA | Certificate Authority |
| RA | Registration Authority |
| KEM | Key-Exchange Mechanism |
| CBE | Code-Based Encryption |
| LBE | Lattice-Based Encryption |
| MQEE | Multivariate-Quadratic-Equation Encryption |
| HBE | Hash-Based Encryption |
| NIST | National Institute of Standards and Technology |
| DigSig | Digital Signatures |
| IBE | Identity-Based Encryption |
| LWE | Learning With Errors |
| CSIDH | Commutative Supersingular Isogeny Diffie–Hellman |
| SQALE | Sublinear Vélu Quantum-resistant isogeny Action with Low Exponents |
| CTIDH | Constant Time CSIDH |
| dCSIDH | Distributed CSIDH |
| OPC UA | Open Platform Communications Unified Architecture |
| WLAN | Wireless Local Area Networks |
| WAN | Wide Area Networks |
| D2D | Device-to-Device |
| TT | Translation Table |
| PoC | Proof-of-Concept |
Appendix A. Quantum Information and Computing Primer
Appendix A.1. Introduction
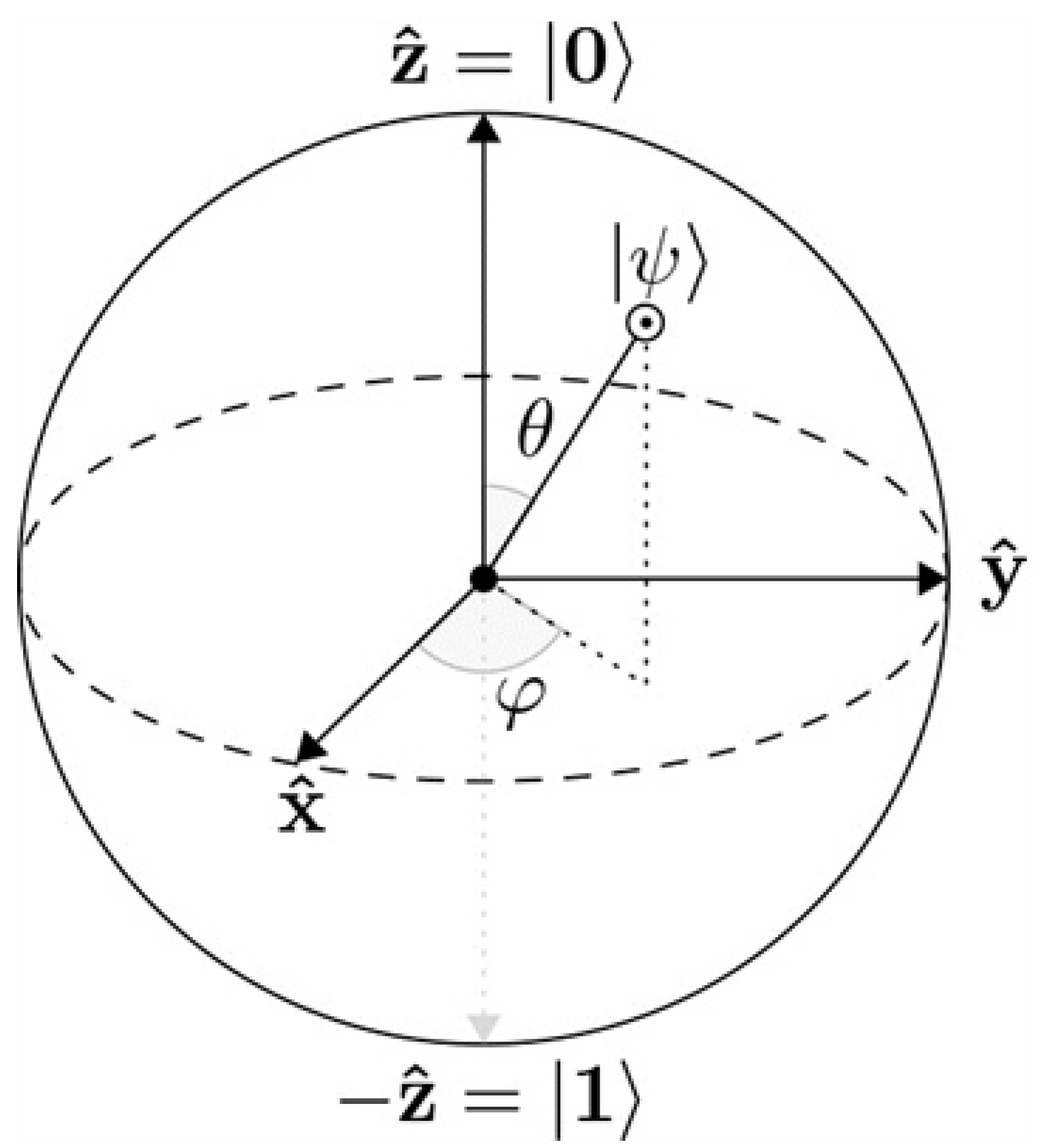
Appendix A.2. Measuring Qubits
- The remaining qubelets in the cauldron disappear because, according to the principles of quantum physics, you cannot choose another qubelet.
- The chosen qubit, either a or a , is designated as the state of the qubit, resulting in the collapse of the qubit. The cauldron is adjusted only to contain the chosen qubelet.
Appendix A.3. Unitary Operations
Appendix A.4. Pauli Operations
Appendix A.5. Hadamard Operation
Appendix A.5.1. Phase Operations
Appendix A.6. Entangled States
Appendix A.7. Bell States
Appendix A.7.1. GHZ and W States
Appendix A.8. Application of Entanglement
Appendix A.9. Teleportation
Appendix A.10. Conclusion
Appendix B. Proof of Concept
References
- Taylor, P. Global IOT Connections Data Volume 2019 and 2025, 2022.
- Pathak, S.; Pandey, M. Smart cities: Review of characteristics, composition, challenges and technologies. 2021 6th International Conference on Inventive Computation Technologies (ICICT). IEEE, 2021, pp. 871–876.
- Silva, B.N.; Khan, M.; Han, K. Towards sustainable smart cities: A review of trends, architectures, components, and open challenges in smart cities. Sustainable cities and society 2018, 38, 697–713. [Google Scholar] [CrossRef]
- Popescul, D.; Genete, L.D. Data security in smart cities: challenges and solutions. Informatica Economică 2016, 20. [Google Scholar] [CrossRef]
- Frick, K.T.; Abreu, G.; Malkin, N.; Pan, A.; Post, A. The cybersecurity risks of smart city technologies: What do the experts think. White Paper, CLTC White Paper Series; UC Berkeley: Berkeley, CA, USA, 2021. [Google Scholar]
- Gerck, E.; Gerck, A. QC Algorithms: Faster Calculation of Prime Numbers. published at https://www. researchgate. net/publication/373516233/. Accessed January 2024, 12.
- VATRA, N. Public key infrastructure overview. Scientific Studies and Research 2009, 19. [Google Scholar]
- Nihal, M. Quantum Computing: Program Next-gen Computers for Hard, Real-world Applications. Quantum Computing 2020, pp. 1–581.
- Sutor, R.S. Dancing with Qubits: How quantum computing works and how it can change the world; Packt Publishing Ltd, 2019.
- Hayward, M. Quantum computing and shor’s algorithm. Sydney: Macquarie University Mathematics Department 2008, 1. [Google Scholar]
- Process, P.S. Announcing Four Candidates to be Standardized, Plus Fourth Round Candidates. URl: https://csrc. nist. gov/News/2022/pqc-candidates-to-be-standardized-and-round-4# newcall 2022.
- Cryptography, P.Q. NIST.
- Weger, V.; Gassner, N.; Rosenthal, J. A survey on code-based cryptography. arXiv 2022, arXiv:2201.07119 2022. [Google Scholar]
- Feldmann, A. A survey of attacks on multivariate cryptosystems. Master’s thesis, University of Waterloo, 2005.
- Bernstein, D.J.; Lange, T. Post-quantum cryptography. Nature 2017, 549, 188–194. [Google Scholar] [CrossRef] [PubMed]
- Tan, T.G.; Zhou, J.; Sharma, V.; Mohanty, S.P. Post-Quantum Adversarial Modeling: A User’s Perspective. Computer 2023, 56, 58–67. [Google Scholar] [CrossRef]
- Bai, S.; Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schwabe, P.; Seiler, G.; Stehlé, D. CRYSTALS-dilithium: Algorithm specifications and supporting documentation (version 3.1). NIST Post-Quantum Cryptography Standardization Round 2021, 3.
- Bos, J.W.; Renes, J.; Sprenkels, A. Dilithium for memory constrained devices. International Conference on Cryptology in Africa. Springer, 2022, pp. 217–235.
- Kannwischer, M.J.; Rijneveld, J.; Schwabe, P.; Stoffelen, K. pqm4: Testing and Benchmarking NIST PQC on ARM Cortex-M4 2019.
- Nouma, S.E.; Yavuz, A.A. Post-quantum forward-secure signatures with hardware-support for internet of things. ICC 2023-IEEE International Conference on Communications. IEEE, 2023, pp. 4540–4545.
- Scott, M. On TLS for the Internet of Things, in a Post Quantum world. Cryptology ePrint Archive 2023. [Google Scholar]
- Kaushik, A.; Vadlamani, L.S.S.; Hussain, M.M.; Sahay, M.; Singh, R.; Singh, A.K.; Indu, S.; Goswami, P.; Kousik, N.G.V. Post Quantum Public and Private Key Cryptography Optimized for IoT Security. Wireless Personal Communications 2023, 129, 893–909. [Google Scholar] [CrossRef]
- Satrya, G.B.; Agus, Y.M.; Mnaouer, A.B. A Comparative Study of Post-Quantum Cryptographic Algorithm Implementations for Secure and Efficient Energy Systems Monitoring. Electronics 2023, 12, 3824. [Google Scholar] [CrossRef]
- Paul, S. On the Transition to Post-Quantum Cryptography in the Industrial Internet of Things 2022.
- Samandari, J.; Gritti, C. Post-quantum authentication in the MQTT protocol. Journal of Cybersecurity and Privacy 2023, 3, 416–434. [Google Scholar] [CrossRef]
- Schwabe, P.; Stebila, D.; Wiggers, T. Post-quantum TLS without handshake signatures. Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, 2020, pp. 1461–1480.
- McLoughlin, C.; Gritti, C.; Samandari, J. Full Post-Quantum Datagram TLS Handshake in the Internet of Things. International Conference on Codes, Cryptology, and Information Security. Springer, 2023, pp. 57–76.
- Schöffel, M.; Lauer, F.; Rheinländer, C.C.; Wehn, N. Secure IoT in the era of quantum computers—where are the bottlenecks? Sensors 2022, 22, 2484. [Google Scholar] [CrossRef] [PubMed]
- Malina, L.; Popelova, L.; Dzurenda, P.; Hajny, J.; Martinasek, Z. On feasibility of post-quantum cryptography on small devices. IFAC-PapersOnLine 2018, 51, 462–467. [Google Scholar] [CrossRef]
- Tasopoulos, G.; Li, J.; Fournaris, A.P.; Zhao, R.K.; Sakzad, A.; Steinfeld, R. Performance evaluation of post-quantum TLS 1.3 on resource-constrained embedded systems. International Conference on Information Security Practice and Experience. Springer, 2022, pp. 432–451.
- Sikeridis, D.; Kampanakis, P.; Devetsikiotis, M. Post-quantum authentication in TLS 1.3: a performance study. Cryptology ePrint Archive 2020.
- Gonzalez, R.; Wiggers, T. KEMTLS vs. post-quantum TLS: Performance on embedded systems. International Conference on Security, Privacy, and Applied Cryptography Engineering. Springer, 2022, pp. 99–117.
- Campos, F.; Chavez-Saab, J.; Chi-Domínguez, J.J.; Meyer, M.; Reijnders, K.; Rodríguez-Henríquez, F.; Schwabe, P.; Wiggers, T. On the practicality of post-quantum tls using large-parameter csidh. Technical report, Cryptology ePrint Archive, Paper 2023/793, 2023.
- Septien-Hernandez, J.A.; Arellano-Vazquez, M.; Contreras-Cruz, M.A.; Ramirez-Paredes, J.P. A Comparative study of post-quantum cryptosystems for Internet-of-Things applications. Sensors 2022, 22, 489. [Google Scholar] [CrossRef] [PubMed]
- Kern, D.; Krauß, C.; Lauser, T.; Alnahawi, N.; Wiesmaier, A.; Niederhagen, R. Quantumcharge: Post-quantum cryptography for electric vehicle charging. International Conference on Applied Cryptography and Network Security. Springer, 2023, pp. 85–111.
- Chung, C.C.; Pai, C.C.; Ching, F.S.; Wang, C.; Chen, L.J. When post-quantum cryptography meets the Internet of Things: An empirical study. Proceedings of the 20th Annual International Conference on Mobile Systems, Applications and Services, 2022, pp. 525–526.
- Barton, J.; Pitropakis, N.; Buchanan, W.; Sayeed, S.; Abramson, W. Post quantum cryptography analysis of TLS tunneling on a constrained device 2022.
- Sizing Up Post-Quantum Signatures. https://blog.cloudflare.com/sizing-up-post-quantum-signatures. (Accessed on 04/10/2024).
- Liu, Z.; Choo, K.K.R.; Grossschadl, J. Securing edge devices in the post-quantum internet of things using lattice-based cryptography. IEEE Communications Magazine 2018, 56, 158–162. [Google Scholar] [CrossRef]
- Karakaya, A.; Akleylek, S. A novel IoT-based health and tactical analysis model with fog computing. PeerJ Computer Science 2021, 7, e342. [Google Scholar] [CrossRef] [PubMed]
- Roy, K.S.; Deb, S.; Kalita, H.K. A novel hybrid authentication protocol utilizing lattice-based cryptography for IoT devices in fog networks. Digital Communications and Networks 2022.
- Seyhan, K.; Nguyen, T.N.; Akleylek, S.; Cengiz, K. Lattice-based cryptosystems for the security of resource-constrained IoT devices in post-quantum world: a survey. Cluster Computing 2022, 25, 1729–1748. [Google Scholar] [CrossRef]
- Zhang, K.; Ni, J.; Yang, K.; Liang, X.; Ren, J.; Shen, X.S. Security and privacy in smart city applications: Challenges and solutions. IEEE Communications Magazine 2017, 55, 122–129. [Google Scholar] [CrossRef]
- Butt, T.A.; Afzaal, M. Security and privacy in smart cities: issues and current solutions. Smart Technologies and Innovation for a Sustainable Future: Proceedings of the 1st American University in the Emirates International Research Conference—Dubai, UAE 2017. Springer, 2019, pp. 317–323.
| 1 | For a primer on Quantum Information and Computing, please see Appendix A. |
| Algorithm | Class | Public Key | Private Key | Signature | Cert Size |
|---|---|---|---|---|---|
| Dilithium 2 | PQ | 1312 | 2528 | 2420 | 3870 |
| Dilithium 3 | PQ | 1952 | 4000 | 3293 | 5982 |
| Dilithium 5 | PQ | 2592 | 4864 | 4595 | 7486 |
| Falcon 512 | PQ | 897 | 1281 | 690 | 2202 |
| Falcon 1024 | PQ | 1793 | 2305 | 1330 | 4122 |
| Sphincs 128f | PQ | 32 | 64 | 17088 | 115 |
| Sphincs 192f | PQ | 48 | 96 | 35664 | 166 |
| Sphincs 256f | PQ | 64 | 128 | 49856 | 214 |
| RSA-2048 | C | 256 | 256 | 256 | 1191 |
| ECC 256-bit | C | 64 | 32 | 256 | 712 |
| Alogrithm | Key Gen. | Sign | Verify |
|---|---|---|---|
| Dilithium 2 | 1,400,412 | 6,157,001 | 1,461,284 |
| Dilithium 3 | 2,282,485 | 9,289,499 | 2,228,898 |
| Dilithium 5 | 3,097,421 | 8,469,805 | 3,173,500 |
| Falcon 512 | 197,793,925 | 38,090,446 | 474,052 |
| Falcon 1024 | 480,910,965 | 83,482,883 | 977,140 |
| Sphincs 128f | 16,552,135 | 521,963,206 | 20,850,719 |
| Sphincs 192f | 24,355,501 | 687,693,467 | 35,097,457 |
| Sphincs 256f | 64,184,968 | 1,554,168,401 | 36,182,488 |
| Algorithm | Key Gen. | Sign | Verify |
|---|---|---|---|
| Dilithium 2 | 36,424 | 61,312 | 40,664 |
| Dilithium 3 | 50,752 | 81,792 | 55,000 |
| Dilithium 5 | 67,136 | 104,408 | 71,472 |
| Falcon 512 | 1,680 | 2,484 | 512 |
| Falcon 1024 | 1,680 | 2,452 | 512 |
| Sphincs 128f | 2,192 | 2,248 | 2,544 |
| Sphincs 192f | 3,512 | 3,640 | 3,872 |
| Sphincs 256f | 5,600 | 5,560 | 5,184 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





