1. Introduction
1.1. Quantum Communication
Quantum communication has sparked a revolution in conventional communication systems, offering unparalleled security measures. Beginning with the BB84 quantum key distribution protocol [
1] and quantum teleportation protocol [
2], quantum communication has made significant strides in its development and application. Recently, significant progress has been made in experimental quantum communication. Various quantum communication protocols, such as quantum key distribution [
3], quantum teleportation [
4], and superdense coding [
5], have been experimentally validated using photonics or superconducting qubit. Recent advancements have witnessed the implementation of various quantum communication protocols on NISQ (Noisy Intermediate-Scale Quantum) devices [
6,
7,
8,
9].
Quantum communication can show a significant advantage against traditional communication methods that rely on classical information encoding, which can be vulnerable to eavesdropping and interception, posing significant risks to sensitive data and communications. One of the main reasons of this advantage of quantum communication is due to the presence of superposition and entanglement. These properties help us design protocols which either inform us about eavesdropping or make the system resistant to it, even if the original qubit source is untrusted. Moreover, the no-cloning theorem doesn’t allow the information to be copied, making the system far more secure than classical communication.
One of the big problems in classical Key distribution is generating the key to secure our communication. To address this problem, quantum key distribution (QKD) is proposed that uses the randomness of quantum measurement or the power of the maximally entangled states to generate the key for classical communication. In QKD, the presence of an eavesdropper can be easily detected by examining the correlations between the parties involved. Quantum random walk is currently being explored for quantum key generation, due to its intrinsically quantum characteristics [
10].
1.2. Quantum Random Walk
A quantum random walk is considered a quantum analogue of classical random walks. In a classical random walk, a particle moves randomly according to certain probabilities [
11]. Recent research on quantum random walks indicates that they may exhibit behaviour distinct from that of their classical counterparts [
12,
13,
14]. Quantum Walk can be both discrete [
12] and continuous time [
15] version. Each version has brought a novel perspective to do quantum task [
16]. In a quantum random walk, there is a coin space and a position space. In the first step, we use a unitary operator on the spin of the coin space and then apply a conditional shift operation on the position space. A minor change in the unitary operator of the coin space of the quantum walk can significantly change the output. In a quantum random walk, the particle starts in a superposition state and evolves governed by quantum operations. At each step, the particle’s state spreads out over multiple locations, creating interference patterns that can lead to different outcomes compared to classical random walks. This spread of states and interference effects are crucial for various quantum algorithms and quantum information processing tasks. The quantum random walk has found use in various areas [
17,
18,
19]. In the following we will showcase its usefulness for quantum communication as also the use of weak measurement in protecting the quantum communication protocol against noise.
1.3. Weak Measurements
Weak measurement is a counter intuitive measurement protocol initially introduced by Aharonov, Albert, and Vaidman in 1988 who explore the efficiency of the weak measurement scheme against decoherence and this measurement scheme is now used to perform various tasks in the field of quantum information theory [
20]. Weak measurement has a unique property, that it can extract information without completely disturbing the state, unlike strong measurements [
21].
Weak measurements have found applications across various domains of quantum physics, including quantum information processing, quantum metrology, and fundamental tests of quantum mechanics. In quantum information processing, weak measurements play a crucial role in quantum state tomography, quantum error correction, and enhancing the efficiency of quantum algorithms. Moreover, in quantum metrology, weak measurements allow for the precise estimation of parameters with high sensitivity, surpassing the limitations imposed by classical measurement techniques [
22].
In this paper, we propose a novel controlled quantum communication protocol using quantum random walk. We perform quantum tomography of the output state to calculate the fidelity. Furthermore, we perform a weak measurement-based protection protocol on a qubit designed to protect it from amplitude damping. A comparison is made on the performance of the protocol with and without the weak measurement-based protection protocol graphically.
1.4. Contributions of the Paper
The contributions of this paper can be summarized as follows:
We propose a controlled quantum communication protocol using quantum random walk that can teleport any N-dimensional quantum state.
The fidelity of the quantum states after quantum tomography for this protocol is high.
We present a comparative analysis between the protocol under amplitude damping and the performance of the protocol with weak measurement protocol in the presence of amplitude damping noise to showcase the usefulness of the weak measurement.
1.5. Organization
The structure of the paper is as follows:
Section 2 covers related work. In
Section 3, we describe the theoretical framework of the algorithms.
Section 4 presents the results. Finally,
Section 5 discusses the findings, concludes the paper, and suggests potential extensions for future research.
2. Related Works
In the teleportation protocol proposed in the paper [
23]. A sender, Alice, successfully transmits an unknown state of a two-level particle to a remote receiver, Bob. This transmission is facilitated by a triplet of entangled particles initially shared and controlled by a supervisor, Charlie. In the paper [
24], the researcher implements some perfect state transfer tasks on various graphs using quantum random walk. The work in this paper is inspired by the one-dimensional protocol proposed by Y. Chatterjee
et al. [
6]. They teleported qubits using quantum walk but did not have a controller. Furthermore, the circuits for transferring higher-dimensional qubits were not straightforward.
3. Theory
3.1. Quantum Random Walk
As mentioned earlier Quantum Random Walk (QRW) serves as a quantum counterpart to the classical random walk, wherein the evolution of a walker is governed by principles of quantum mechanics rather than classical probability distributions. A pivotal component in QRWs is the quantum coin flip, often realized through the application of a Hadamard gate. This gate creates a superposition of states analogous to “heads" and “tails", mimicking the randomness inherent in classical coin flips. In our proposed algorithm, we leverage this quantum coin flip methodology by employing a Hadamard gate on the coin qubit, followed by conditional operations on the walker qubit, typically implemented using controlled-NOT gates. These conditional operations dictate the walker’s movement based on the state of the coin qubit, analogous to the classical random walk’s directional shifts. The resultant quantum circuit facilitates the simulation of the walker’s probabilistic evolution, emulating classical random walks in a quantum framework.
3.2. Theoretical Framework of the Algorithm
Here We propose a controlled quantum communication protocol using a quantum random walk. The steps for the protocol can be summarized as follows:
3.3. Receiver Operation
The General operation rule before doing the measurement for the receiver can be understood through this analysis. The state that was produced was a superposition state of this term:
If we want the j=1 case as the receiver and others of the M as controllers, then the desired state should be
To generate the state for the receiver, we perform the CNOT operation with a controller on the position space and on the controller coin space. The resultant state is given by
The resource state has an extra term
, which can be removed by a controlled Z operation. This leads to
Now, let us substitute the summation symbol to produce the resultant state. This step is ready to be measured by the receiver. Hence, the above equation takes the following form:
Through this analysis, we concluded that the receiver’s operation on each qubit line is contingent upon the sender’s coin space, position space measurement output and the controller’s coin space output. Specifically, if the sender obtains a 1 as the output for the i-th qubit in the coin space, the receiver performs a Z gate operation on the i-th qubit line. If the sender’s output corresponds to 1 in the position space, the receiver performs an X gate operation. Additionally, for the controller’s measurement outcomes on the i-th qubit, if the outcome is 1, the receiver applies an X gate operation.
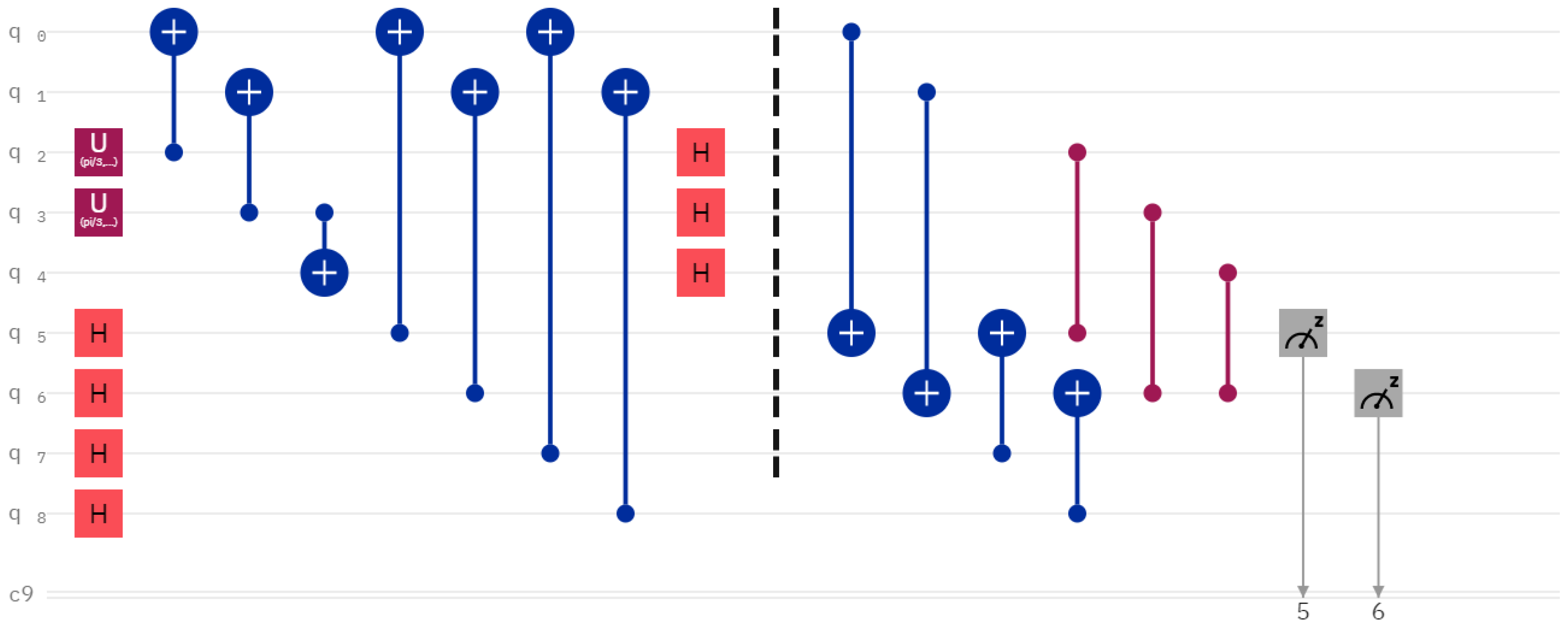
3.4. Communication between Symmetrical and Asymmetrical Coin space
The communication protocol given here demands the receiver and the sender coin space to be of the same dimension. However, it is possible to communicate between coin spaces that are not equal by reducing the dimension of the coin space by using entanglement. Exploiting this property, we can communicate between asymmetrical coin spaces. An example circuit is shown in
Figure 2.
3.5. Amplitude Damping
In the realm of quantum computing, amplitude damping is a crucial quantum error that can lead to the loss of quantum information. This phenomenon occurs when a qubit, representing a quantum state, interacts with its environment, causing the qubit’s amplitude to decay. Amplitude damping is primarily observed in quantum systems where the qubits are susceptible to energy dissipation. Amplitude damping is commonly quantified using Kraus operators, which describe the evolution of the quantum state when subjected to noise. For amplitude damping, the Kraus operators are given by
This map can also be represented in the following form:
3.6. Weak Measurement Based Protection Protocol
Weak measurement has found uses in protecting the quantum state from amplitude damping Noise. The protocol given in the paper [
25] is used to protect the state from decoherence. The steps involved in the process are
-
Step 1: Weak Measurement
In the initial step, weak measurements are applied to gain partial information about the system. These measurements are characterized by operators
and
, oriented along the z-axis of the Bloch sphere. The operators
and
are defined as follows:
Here, dictates the measurement’s strength, with three distinct schemes: “no measurement" (NM) when , “projective measurement" (PM) when , and “weak measurement" (WM) when .
-
Step 2: Offsetting Operations
Following the measurement, corrective operations are enacted to counteract noise effects before amplitude damping (ADC). These operations, denoted as
and
, are determined by the measurement outcomes:
Where corresponds to the result of and corresponds to the result of .
-
Step 3: Amplitude Damping Correction
In this phase, the system is readied for ADC by addressing amplitude damping using Kraus operators for each qubit:
Here,
represents the probability of decay from the excited state, determined by
, where
is the energy relaxation rate and
t is the evolution time. Note that the r mentioned here is same as the p mentioned in
Section 3.5.
-
Step 4: Post-Amplitude Damping Correction
Following ADC, the same offsetting operations from Step 2 are applied.
-
Step 5: Correction Rotation
Finally, correction rotations are implemented to restore the state to its initial condition. These rotations,
and
, are applied based on the measurement outcomes:
Where corresponds to the result of and corresponds to the result of . The value of is given by
This protocol systematically shields the quantum Fisher information of the N-qubit GHZ state from decoherence by integrating weak measurements, corrective operations, amplitude damping correction, and correction rotations. Adjusting the measurement strength allows for a balance between information acquisition and disturbance minimization.
3.7. Quantum State Tomography
Quantum state tomography is a powerful technique used to reconstruct unknown quantum states by performing measurements on an ensemble of identically prepared quantum systems. In quantum mechanics, a quantum state is fully characterized by a density matrix, which encapsulates all information about the system’s state, including its superposition and entanglement properties. The process of quantum state tomography involves preparing a large number of identical quantum systems in the same initial state, subjecting them to a series of measurements in different bases, and then using the statistics of these measurements to infer the underlying quantum state. By collecting sufficient measurement data, researchers can reconstruct the density matrix with high fidelity, providing a complete description of the quantum state. For a single qubit, the equation for constructing the experimental density matrix
is given as follows:
Here, X, Y and Z correspond to the
The , , and are expectation values calculated for this basis.
The general form of the two-qubit density matrix using expectation values is:
where
are the Pauli matrices:
and ⊗ represents the tensor product.
3.8. Quantum Fidelity
Quantum fidelity is a fundamental concept in quantum mechanics that quantifies the similarity between two quantum states [
26]. It serves as a measure of how well one quantum state can be transformed into another while preserving its essential features. Mathematically, the fidelity
between two quantum states represented by density matrices
and
is defined as the squared overlap between them:
Here, Tr denotes the trace operation, and and represent the square roots of the density matrices.
High fidelity indicates a strong resemblance between the states, implying that they are nearly indistinguishable. In contrast, low fidelity signifies significant deviations or differences between the states.
3.9. Attack Analysis
The system is safe from external attack, as the protocol as for transferring N dimensional qubit, with m controller with symmetrical coin space. For Eve to extract the state, she has to guess the operation correctly. And the probability of guessing the operation correctly is . Moreover, the protocol is secure against various external attacks like intercept-resend attacks, measurement-based attacks and measurement-resend attacks. attack
4. Experimental Results
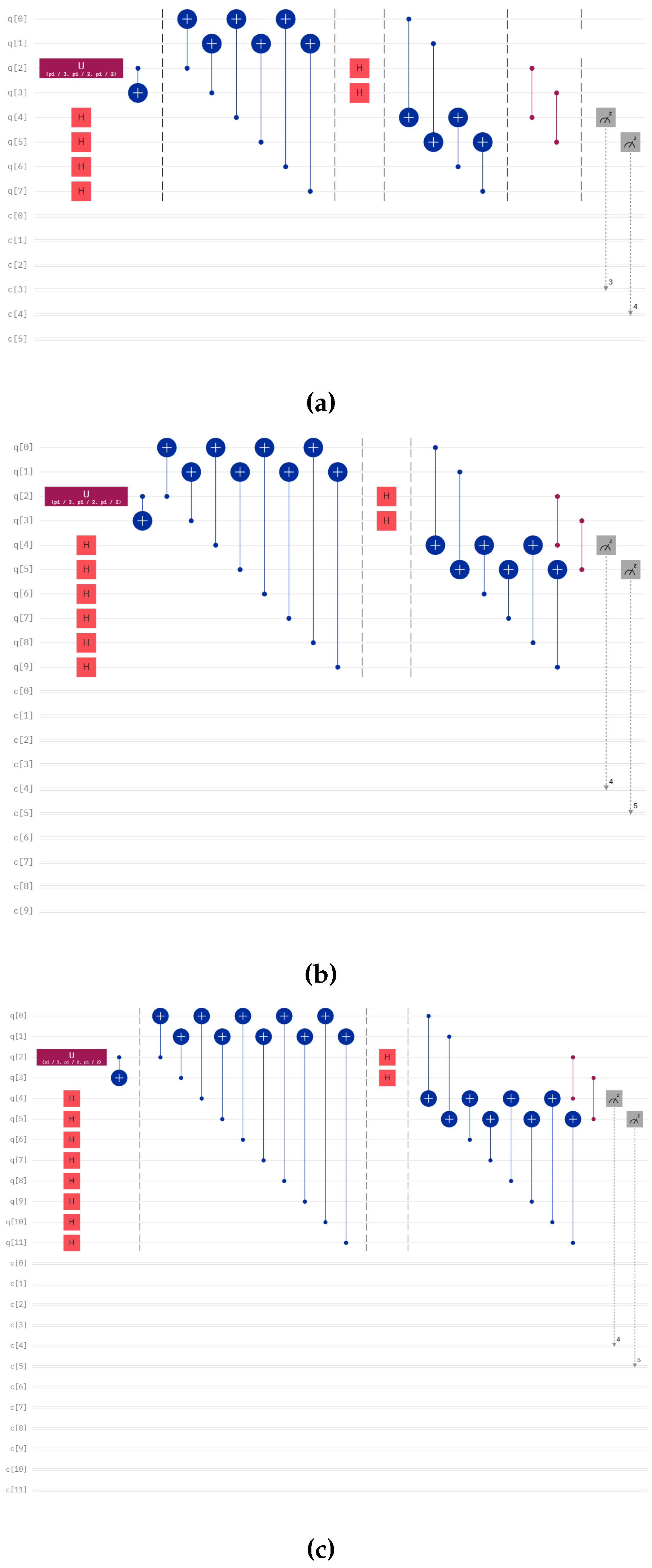
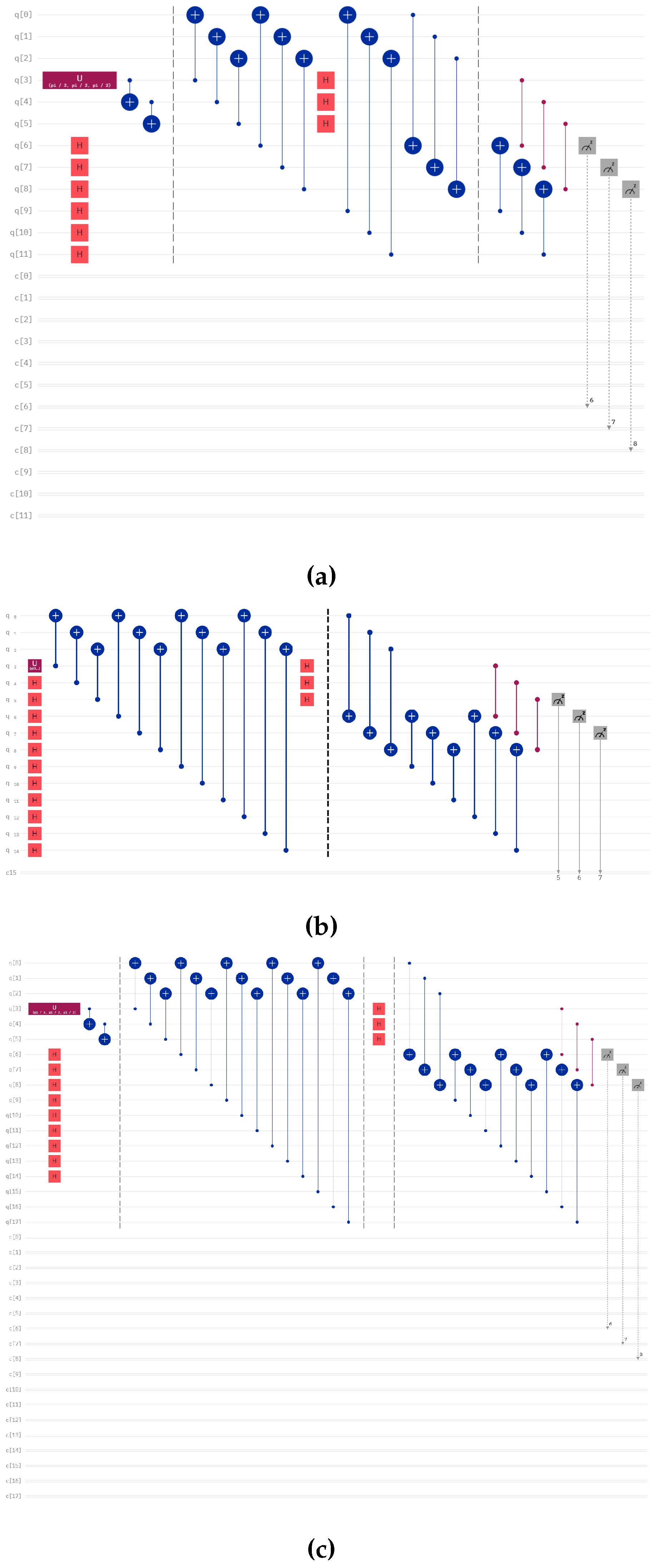
4.1. Circuits Output on Simulators
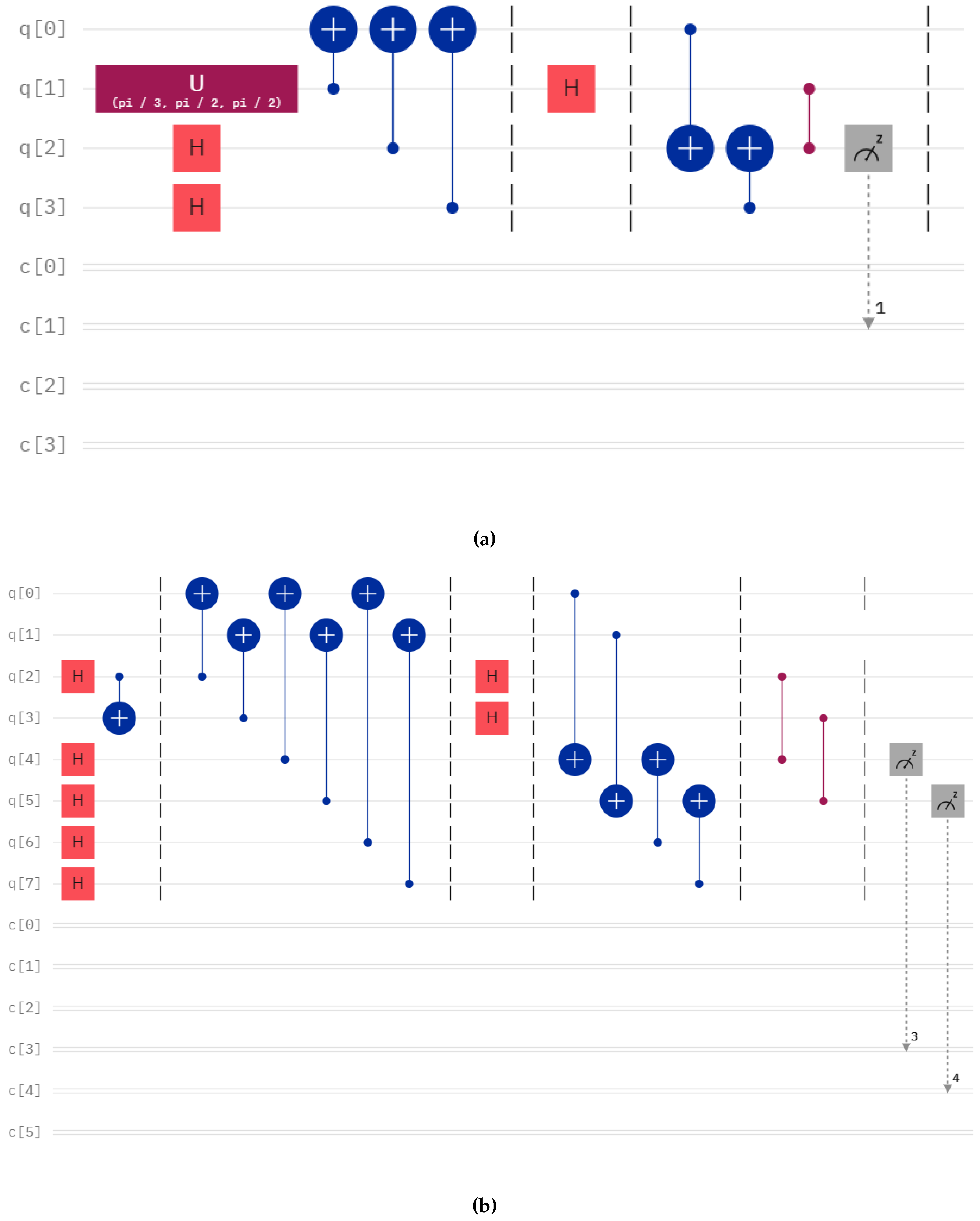
We teleport different numbers of qubits with different numbers of controllers using our protocol using IBMQ QASM Simulator of IBM for 8193 shots. The diagram of those circuits are given in
Figure 1, Figure 7 and Figure 8. We present the output of the run of those circuits on
Table 1,
Table 2 and
Table 3 for different numbers of controllers and senders.
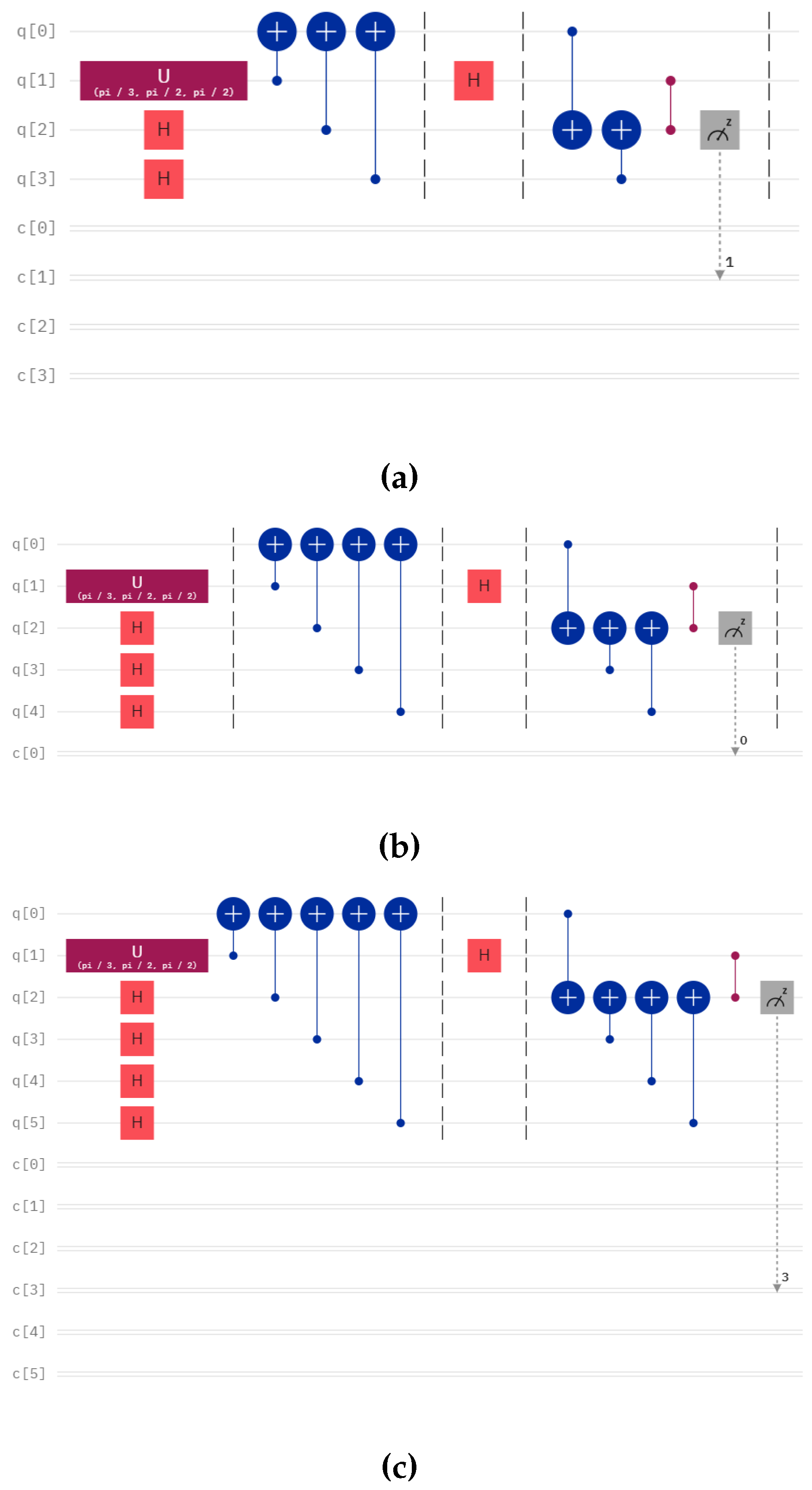
4.2. Results of Quantum State Tomography
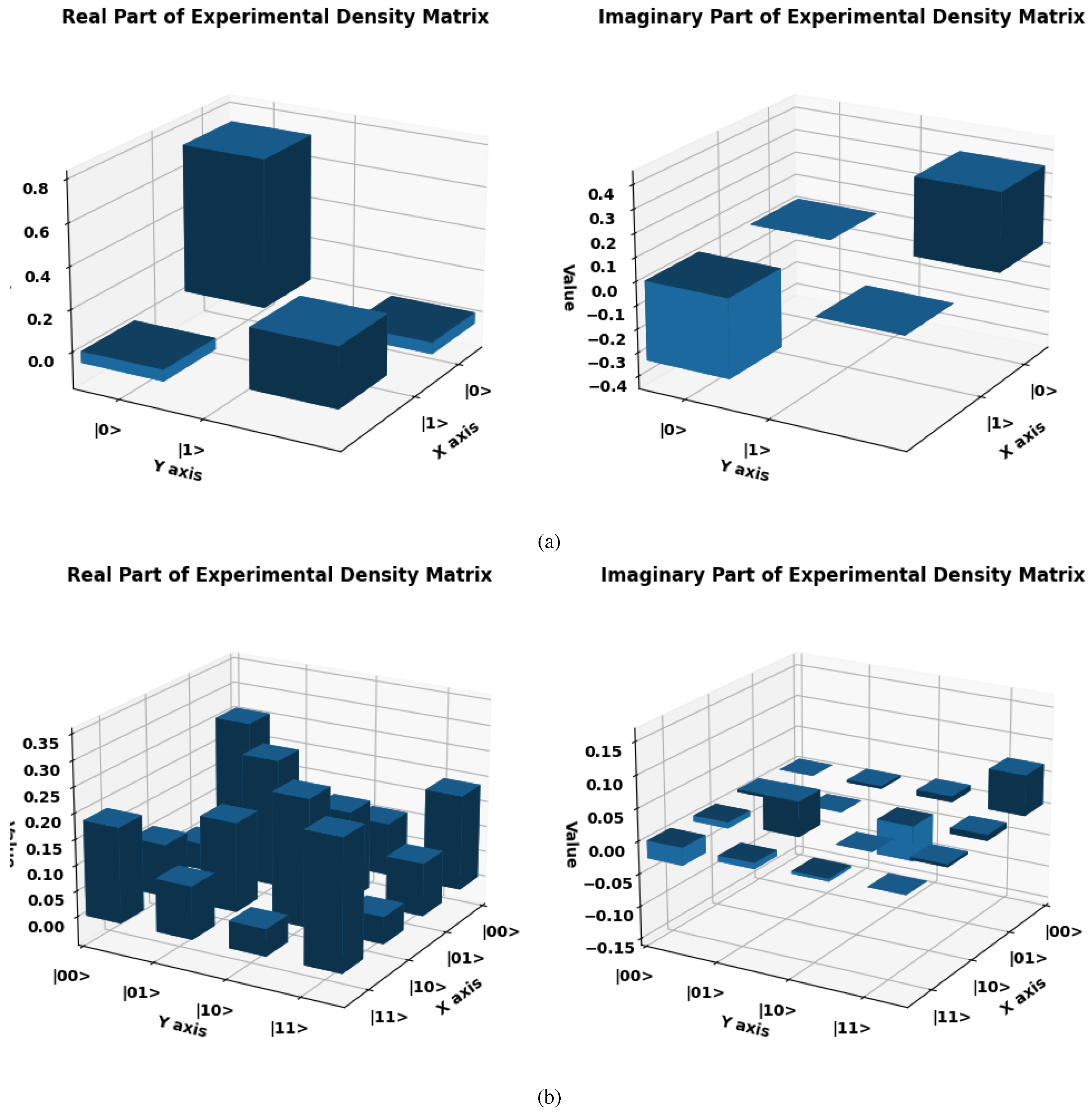
In this section, we discuss the results of quantum state tomography to check how well the quantum states are teleported in our algorithm. We checked the performance of two circuits. The circuits used for the tomography are given in Figure 4. The theoretical density matrix is calculated using:
For one qubit and one controller circuit, we teleport
in IBM Sherbrooke for 8193 shots generate by action of
. The theoretical density matrix of the state is
The experimental density matrix given in equation
16 for a single qubit after substituting matrices
X,
Y, and
Z, the Pauli matrices, and
which is the identity matrix, we get:
The expectation values was found out to be
,
, and
, substituting the values, we get:
The fidelity achieved for this circuit was found out to be 0.81.
For two qubit state, we teleport the Bell state
, the theoretical density matrix is
For the Bell state, the experimental density matrix state is calculated using the IBM Brisbane processor of IBM Quantum computer using equation
17. The density matrix
is given in Eq.
23.
The protocol achieved a fidelity of 0.61 for teleporting the Bell state.
Figure 3.
Experimental density matrix plot for (a) single qubit and (b) two-qubit teleportation with one controller.
Figure 3.
Experimental density matrix plot for (a) single qubit and (b) two-qubit teleportation with one controller.
Figure 4.
Circuit for teleportation of Bell states with one controller and one receiver. We calculated the fidelity for this circuit in IBM-Q of IBM Quantum Computer.
Figure 4.
Circuit for teleportation of Bell states with one controller and one receiver. We calculated the fidelity for this circuit in IBM-Q of IBM Quantum Computer.
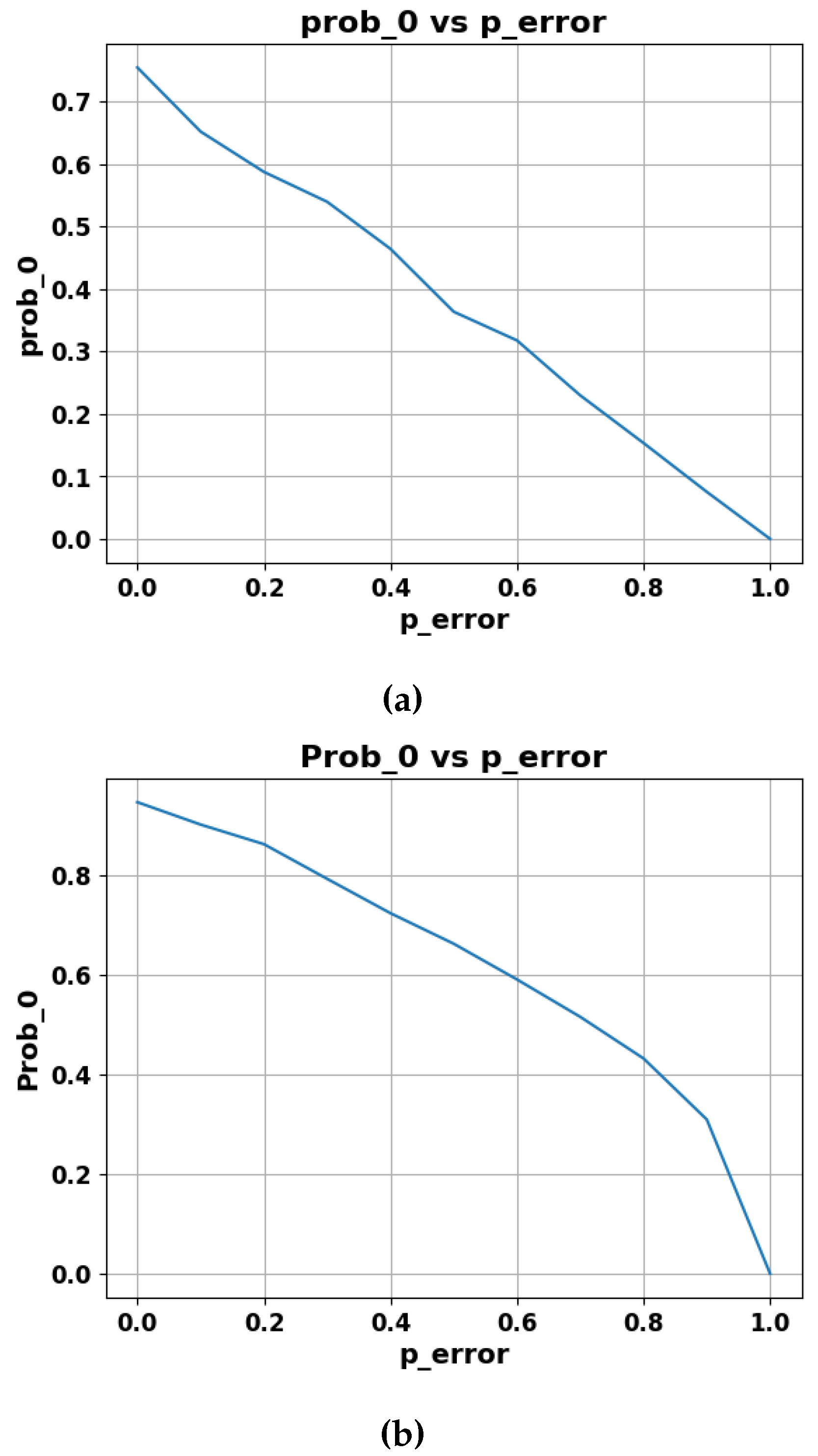
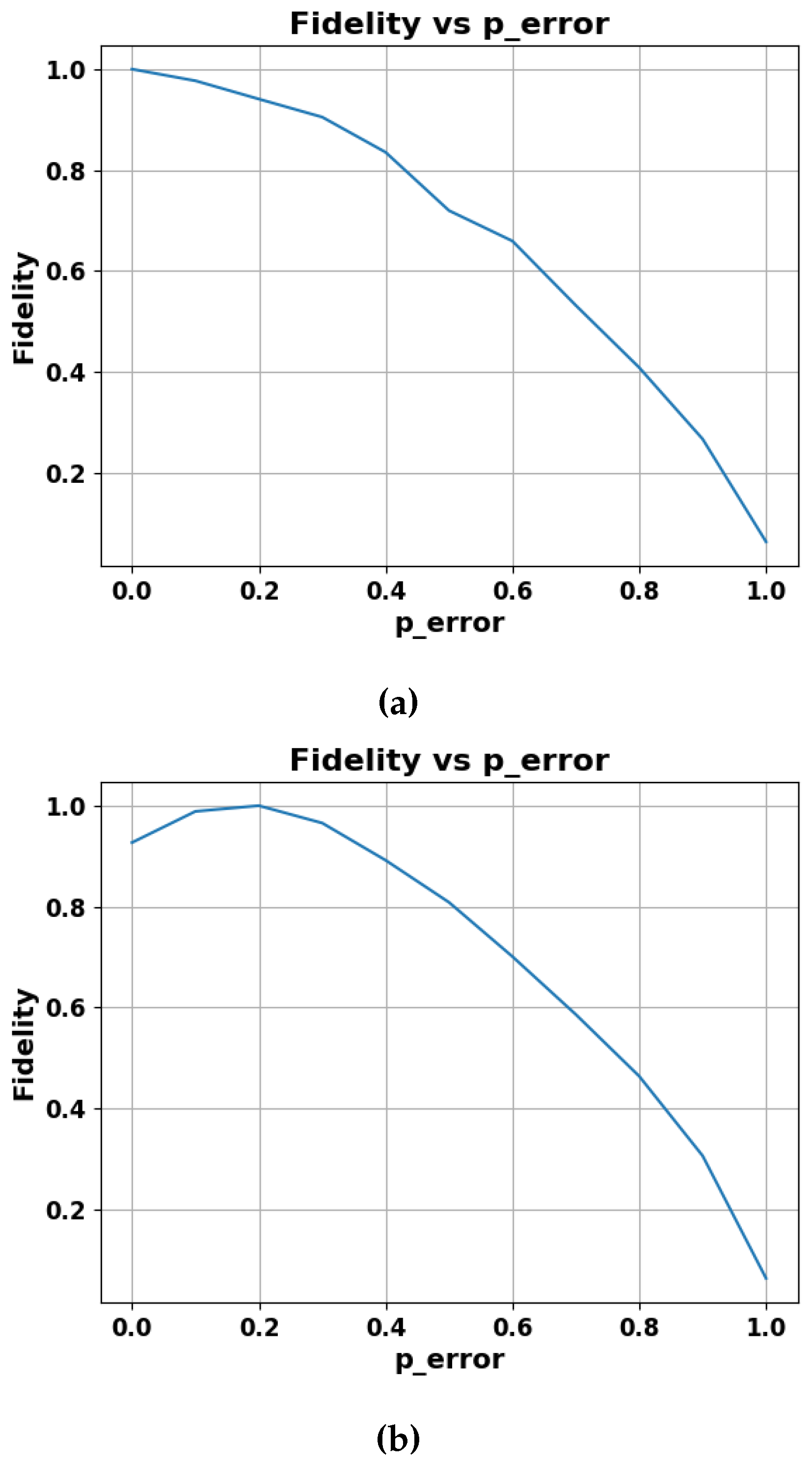
4.3. Results of Weak Measurements
We investigate a weak measurement protocol’s ability to protect quantum states from amplitude-damping noise. Fidelity versus noise strength (p-error) graphs are presented for two scenarios: utilizing the weak testing protocol and not using it. Moreover, we illustrate the probability of the state (Prob-0) against noise strength (p-error), where p-error represents the intensity of amplitude damping. Our results provide insights into the effectiveness of the protocol in mitigating different levels of amplitude damping. The weak measurement strength implemented in the protocol was . In Figure 6, Figure 6a demonstrates the performance of the communication protocol without the weak measurement-based protocol under the influence of amplitude damping, while Figure 6b presents the performance of the communication protocol after implementing the Weak measurement protocol. Clearly, the protocol with Weak measurement maintained a higher Fidelity compared to the protocol under the influence of noise levels represented by p-error or p-values within the range from 0 to 0.5.
Figure 5.
The plot illustrates the probability of obtaining the state as a function of the increasing p-value of amplitude damping, clearly indicating the slow decay rate of fidelity in presence of weak measurement.
Figure 5.
The plot illustrates the probability of obtaining the state as a function of the increasing p-value of amplitude damping, clearly indicating the slow decay rate of fidelity in presence of weak measurement.
Figure 6.
The plot illustrates fidelity with respect to increasing p-value of the amplitude damping.
Figure 6.
The plot illustrates fidelity with respect to increasing p-value of the amplitude damping.
5. Discussion and Conclusion
In our study, we have introduced a controlled quantum communication protocol designed for general N-dimensional quantum states with multiple controllers. Additionally, we have proposed modifications to facilitate communication between symmetrical and asymmetrical coin spaces. The protocol is implemented on the IBM QASM simulator, varying the number of controllers and qubits.
We have evaluated the fidelity of the protocol, which exhibits high fidelity in both single-qubit and two-qubit circuits governed by a single controller. Furthermore, we investigated the efficacy of a weak measurement-based protection protocol tailored to shield qubits against amplitude damping. This protection protocol was assessed using a single-qubit circuit with a single controller.
Our evaluation included graphical representations of performance outcomes in terms of the p-value, indicating the strength of amplitude damping. Our results encompass a comparative analysis demonstrating the protocol’s performance in environments with and without amplitude noise. Notably, the weak measurement-based protection protocol exhibited exceptional performance within the range of p-values from 0 to 0.5.
Acknowledgments
We extend our sincere appreciation to OpenAI’s ChatGPT for its invaluable assistance in refining sentence structures and rectifying grammatical errors throughout the course of this research paper. Additionally, we would like to express our gratitude to the I-HUB Quantum Technology Foundation for issuing the award letter for the Chanakya scholarship during both the mid and end phases of the project. Furthermore, we extend our thanks to IBM for providing us with the opportunity to utilize their quantum computers to calculate the fidelity of our protocols.
Appendix
Here, we provide the quantum circuit for the teleportation of two and three-qubit states with the assistance of single and multiple controllers, which are given in Figure 7 and Figure 8.
Figure 7.
Circuit for teleportation of two-qubit states with (a) one controller, (b) two controllers, (c) three controllers.
Figure 7.
Circuit for teleportation of two-qubit states with (a) one controller, (b) two controllers, (c) three controllers.
Figure 8.
Circuit for teleportation of three-qubit state with (a) one controller, (b) two controllers, (c) three controllers.
Figure 8.
Circuit for teleportation of three-qubit state with (a) one controller, (b) two controllers, (c) three controllers.
References
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. Theoretical computer science 2014, 560, 7–11. [Google Scholar] [CrossRef]
- Bennett, C.H.; Brassard, G.; Crépeau, C.; Jozsa, R.; Peres, A.; Wootters, W.K. Teleporting an unknown quantum state via dual classical and Einstein-Podolsky-Rosen channels. Physical review letters 1993, 70, 1895. [Google Scholar] [CrossRef] [PubMed]
- Zhao, Y.; Qi, B.; Ma, X.; Lo, H.K.; Qian, L. Experimental quantum key distribution with decoy states. Physical review letters 2006, 96, 070502. [Google Scholar] [CrossRef] [PubMed]
- Bouwmeester, D.; Pan, J.W.; Mattle, K.; Eibl, M.; Weinfurter, H.; Zeilinger, A. Experimental quantum teleportation. Nature 1997, 390, 575–579. [Google Scholar] [CrossRef]
- Williams, B.P.; Sadlier, R.J.; Humble, T.S. Superdense coding over optical fiber links with complete Bell-state measurements. Physical review letters 2017, 118, 050501. [Google Scholar] [CrossRef] [PubMed]
- Chatterjee, Y.; Devrari, V.; Behera, B.K.; Panigrahi, P.K. Experimental realization of quantum teleportation using coined quantum walks. Quantum Information Processing 2019, 19. [Google Scholar] [CrossRef]
- Rajiuddin, S.; Baishya, A.; Behera, B.K.; Panigrahi, P.K. Experimental realization of quantum teleportation of an arbitrary two-qubit state using a four-qubit cluster state. Quantum Information Processing 2020, 19, 1–13. [Google Scholar] [CrossRef]
- Sk, R.; Dash, T.; Panigrahi, P.K. Quantum information splitting of an arbitrary three-qubit state by using three sets of GHZ states. IET Quantum Communication 2021, 2, 122–135. [Google Scholar] [CrossRef]
- Sisodia, M.; Shukla, A.; Thapliyal, K.; Pathak, A. Design and experimental realization of an optimal scheme for teleportation of an n-qubit quantum state. Quantum Information Processing 2017, 16, 1–19. [Google Scholar] [CrossRef]
- Sarkar, A.; Chandrashekar, C. Multi-bit quantum random number generation from a single qubit quantum walk. Scientific reports 2019, 9, 12323. [Google Scholar] [CrossRef]
- Kempe, J. Quantum random walks: An introductory overview. Contemporary Physics 2003, 44, 307–327. [Google Scholar] [CrossRef]
- Aharonov, Y.; Davidovich, L.; Zagury, N. Quantum random walks. Phys. Rev. A 1993, 48, 1687–1690. [Google Scholar] [CrossRef]
- Childs, A.M.; Farhi, E.; Gutmann, S. An example of the difference between quantum and classical random walks. Quantum Information Processing 2002, 1, 35–43. [Google Scholar] [CrossRef]
- Shenvi, N.; Kempe, J.; Whaley, K.B. Quantum random-walk search algorithm. Phys. Rev. A 2003, 67, 052307. [Google Scholar] [CrossRef]
- Farhi, E.; Gutmann, S. Quantum computation and decision trees. Physical Review A 1998, 58, 915. [Google Scholar] [CrossRef]
- Venegas-Andraca, S.E. Quantum walks: a comprehensive review. Quantum Information Processing 2012, 11, 1015–1106. [Google Scholar] [CrossRef]
- Qu, D.; Matwiejew, E.; Wang, K.; Wang, J.; Xue, P. Experimental implementation of quantum-walk-based portfolio optimization. Quantum Science and Technology 2024, 9, 025014. [Google Scholar] [CrossRef]
- Razzoli, L.; Cenedese, G.; Bondani, M.; Benenti, G. Efficient Implementation of Discrete-Time Quantum Walks on Quantum Computers. Entropy 2024, 26. [Google Scholar] [CrossRef]
- Shi, W.M.; Xu, F.X.; Zhou, Y.H.; Yang, Y.G. A Novel Image Segmentation Algorithm based on Continuous-Time Quantum Walk using Superpixels. International Journal of Theoretical Physics 2023, 63, 4. [Google Scholar] [CrossRef]
- Aharonov, Y.; Albert, D.Z.; Vaidman, L. How the result of a measurement of a component of the spin of a spin-1/2 particle can turn out to be 100. Physical review letters 1988, 60, 1351. [Google Scholar] [CrossRef] [PubMed]
- Modak, N.; Singh, A.K.; Guchhait, S.; BS, A.; Pal, M.; Ghosh, N. Weak measurements in nano-optics. Current Nanomaterials 2020, 5, 191–213. [Google Scholar] [CrossRef]
- Zhang, L.; Datta, A.; Walmsley, I.A. Precision metrology using weak measurements. Physical review letters 2015, 114, 210801. [Google Scholar] [CrossRef] [PubMed]
- Ting, G.; Feng-Li, Y.; Zhi-Xi, W. Controlled quantum teleportation and secure direct communication. Chinese Physics 2005, 14, 893. [Google Scholar] [CrossRef]
- Shang, Y.; Li, M. Experimental realization of state transfer by quantum walks with two coins. Quantum Science and Technology 2019, 5, 015005. [Google Scholar] [CrossRef]
- Harraz, S.; Cong, S.; Zhang, J.; Nieto, J.J. Quantum fisher information protection of N-qubit Greenberger-Horne-Zeilinger state from decoherence. 2021; arXiv:quant-ph/2112.11590. [Google Scholar] [CrossRef]
- Nielsen, M.A.; Chuang, I.L. Quantum computation and quantum information; Cambridge university press, 2010.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).