Submitted:
09 May 2024
Posted:
10 May 2024
Read the latest preprint version here
Abstract
Keywords:
1. Introduction
1.1. Research Motivation
- To comprehensively identify and discuss the vulnerabilities of the ADS-B system and explore potential exploitation scenarios.
- To assess and acknowledge the limitations of existing security solutions, emphasizing their inability to offer complete defense to the ADS-B system and their lack of practical implementation in real-world scenarios (experimental phase).
- To evaluate existing security solutions from multiple perspectives, including cost-effectiveness, implementation difficulty, scalability, and coverage against potential attacks.
- To highlight the challenges and obstacles researchers face in developing holistic security solutions tailored to the unique complexities of the ADS-B system.
1.2. Research Objectives
- Offer a detailed overview of the aviation system to enhance readers' understanding of ADS-B technology and its security implications.
- Provide an in-depth analysis of ADS-B vulnerabilities, potential threats, and attack vectors supported by illustrative diagrams.
- Evaluate existing security solutions based on cost-effectiveness, scalability, implementation complexity, and coverage against various attack scenarios.
- Identify the security requirements and challenges in ADS-B systems and propose future research directions to address emerging threats and enhance system resilience.
1.3. Paper Structure
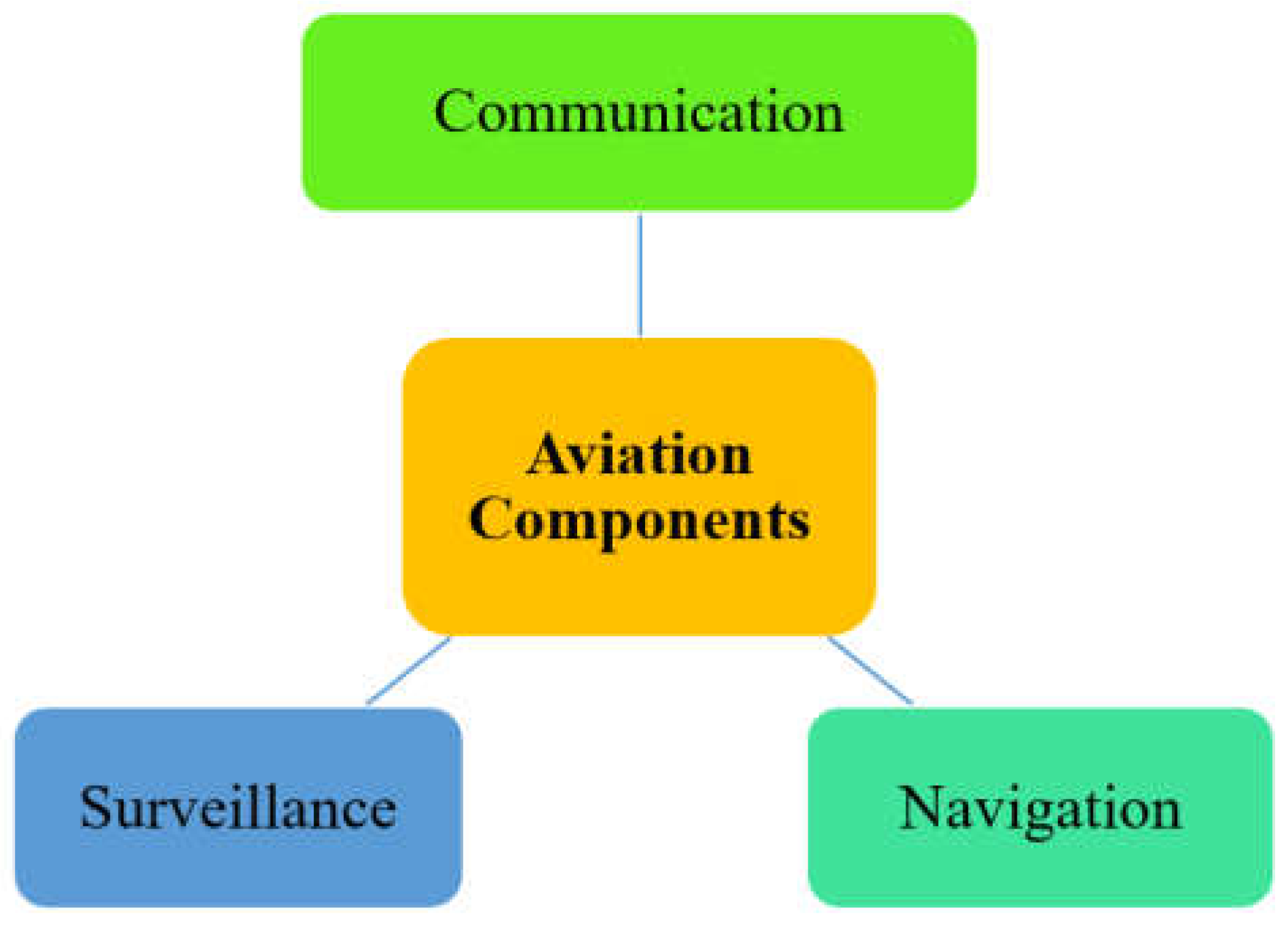
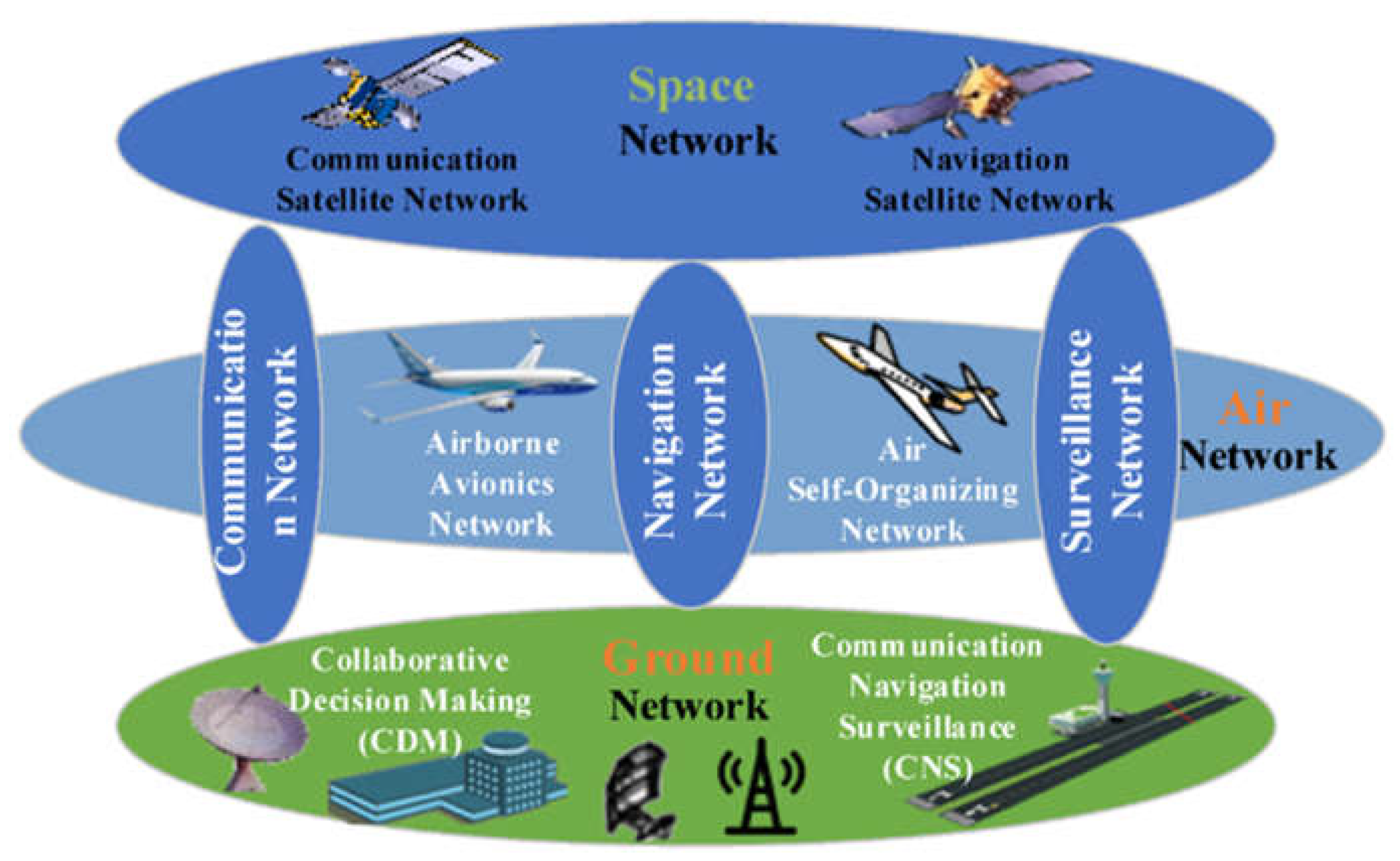
2. Overview of Aviation System
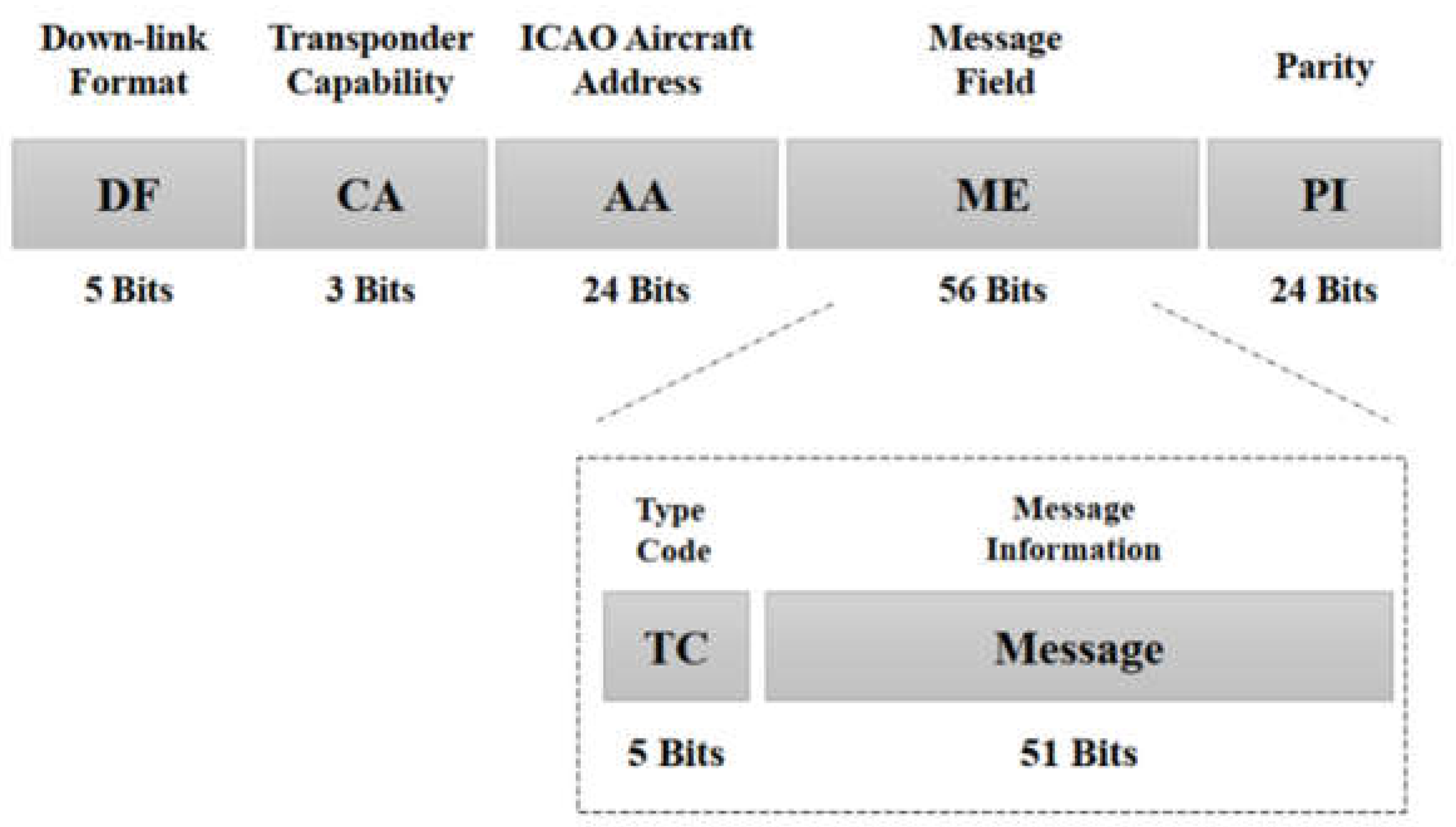
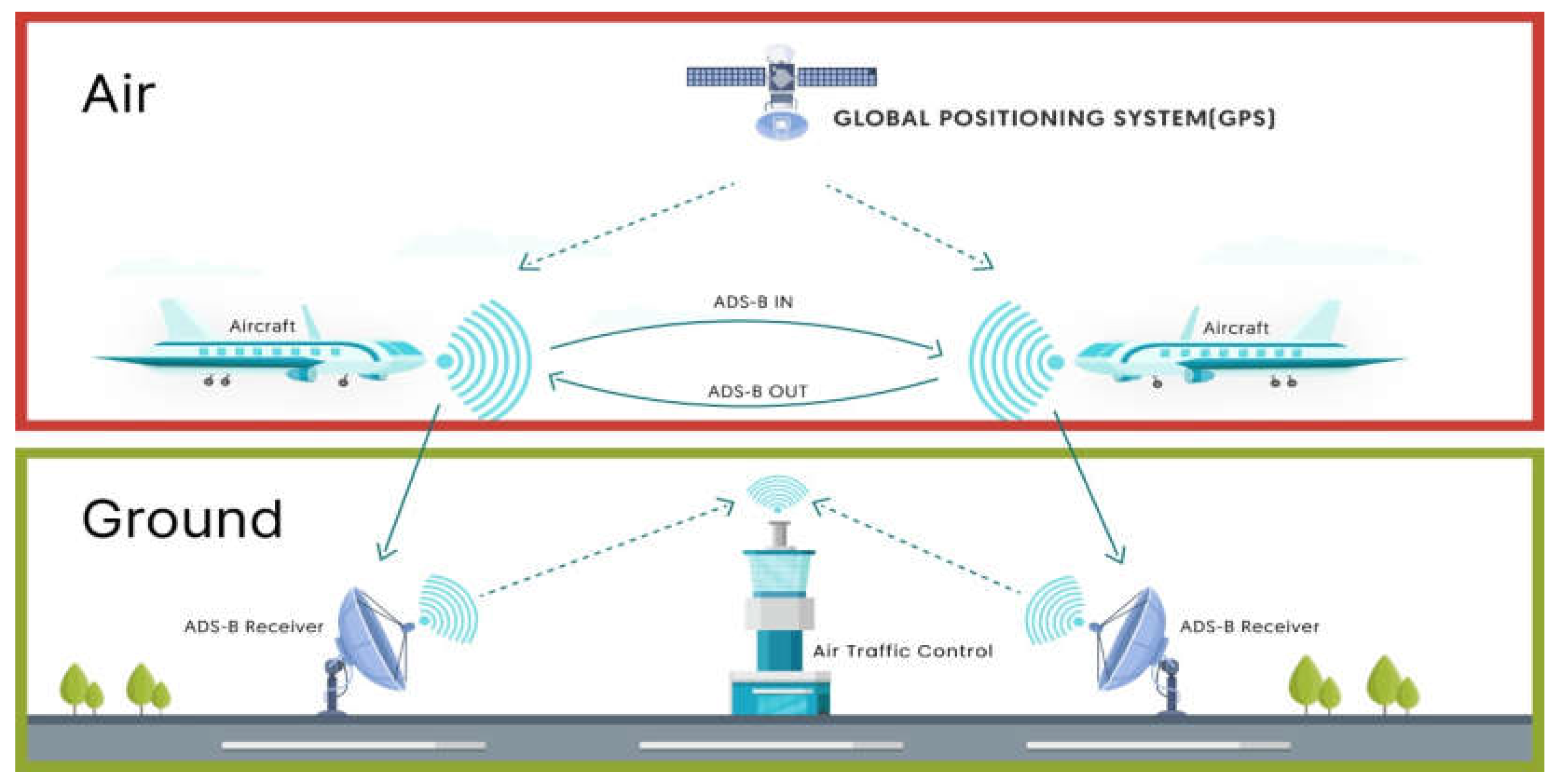
3. Overview of Automatic Dependent Surveillance-Broadcast (ADS-B)
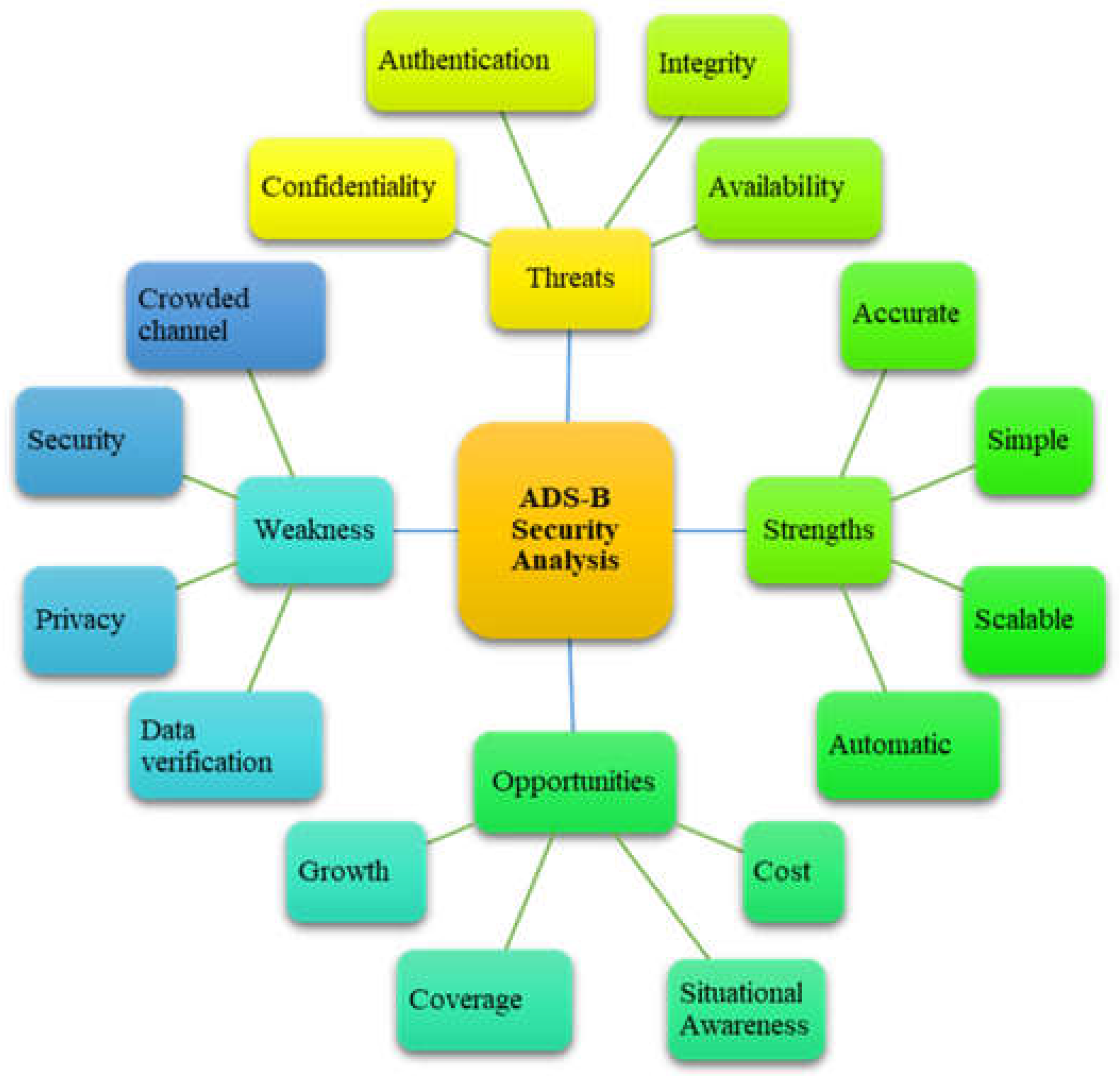
4. Security Analysis of ADS-B
4.1. ADS-B Vulnerabilities
4.2. ADS-B Vulnerabilities Exploits
4.3. ADS-B Attacks
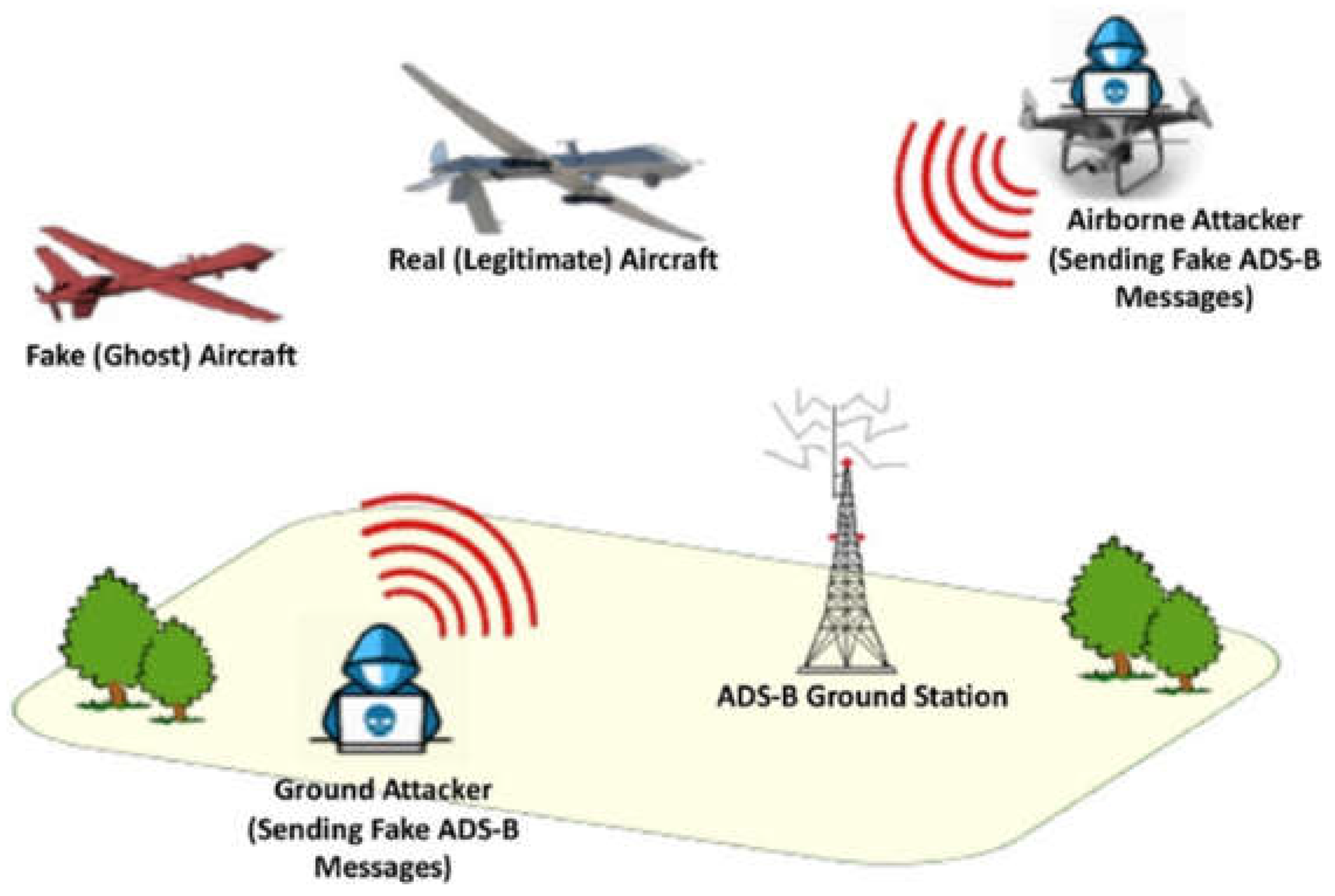
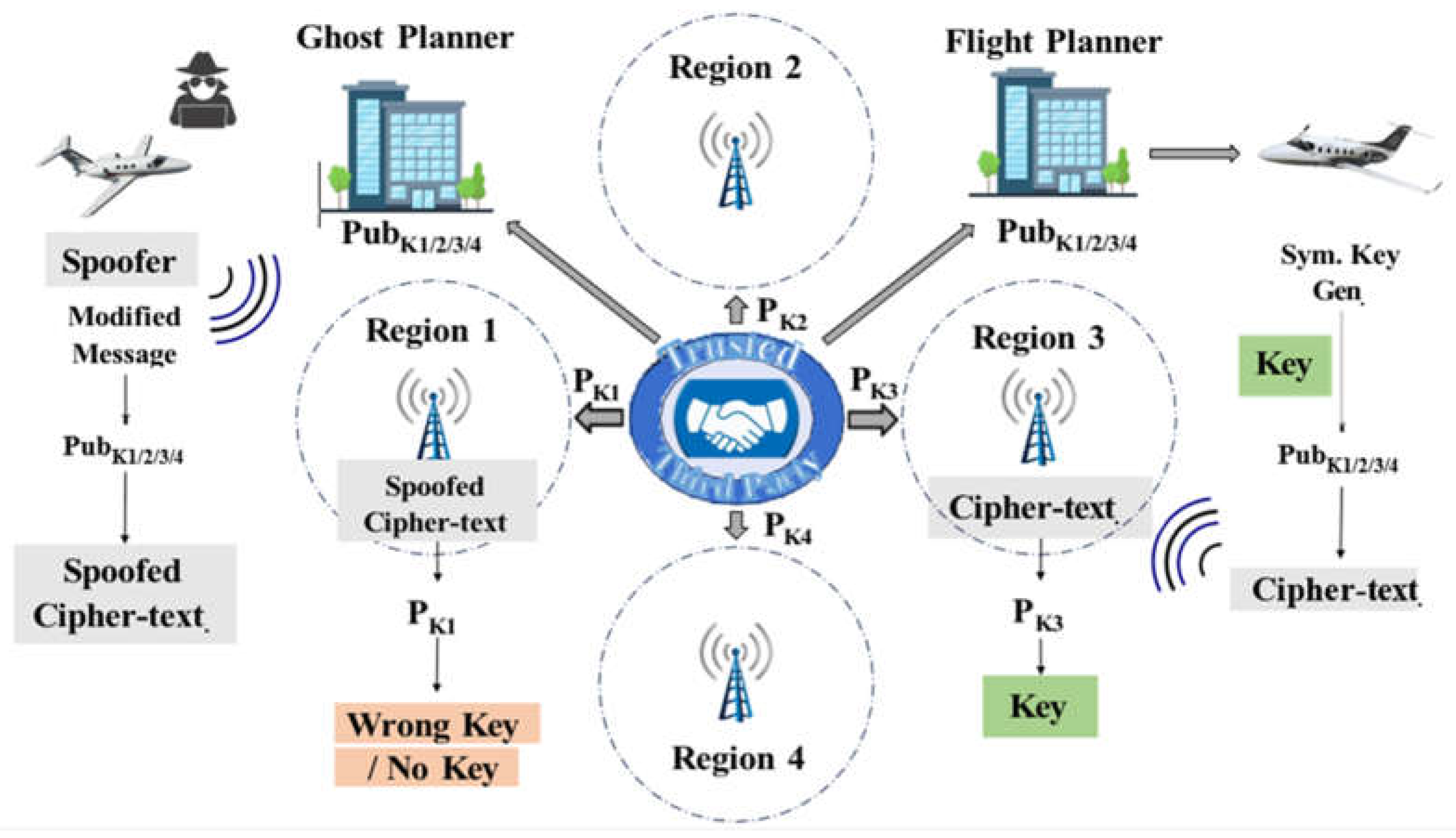
- Message Injection Attack: This is a type of attack in which an attacker sends nonlegitimate ADS-B messages to nearby Aircraft and ATC. These nonlegitimate messages deceive the system into believing that an aircraft is flying at a different altitude or location or on a different course than its original location. This attack can create a dangerous situation and confuse ATC and the pilots. Message injection attacks violate the authentication of the ADS-B protocol. In [49], the authors investigate the impact of message injection and spoofing attacks on ADS-B.
- Message Deletion Attack: An attack in which an attacker intercepts and deletes legitimate messages broadcast by other Aircraft in the surroundings. From an ATC and aircraft point of view, ADS-B messages are critical because they provide real-time information about Aircraft, such as current altitude, speed, and other important information. An attacker can cause accidents or confusion by deleting ADS-B messages and hiding the Aircraft's status and location from ATC. Message deletion attacks violate the Integrity of ADS-B protocol. In [50], the authors discuss two strategies for deleting a legitimate ADS-B message.
- Message Modification Attack: In a message modification attack, the attacker intercepts a legitimate broadcast message by violating ADS-B confidentiality and modifying different message values, such as altitude, speed, etc. The modified message is transferred to ATC, making it difficult for ATC to track the Aircraft's updated location and status. Message modification attacks violate the Integrity of the ADS-B protocol. In [51], authors proposed a mechanism for injecting and verifying a modified message in the ATC system.
- Eavesdropping Attack: An attack in which an attacker intercepts and listens to legitimate messages broadcast by Aircraft. These messages contain critical data related to Aircraft, such as altitude, position, etc. The intercept messages also provide sensitive information to the attacker, such as flight status and path. In [52], the authors discuss and implement multiple methods of passive attacks, such as eavesdropping. Eavesdropping violates the confidentiality of ADS-B protocol.
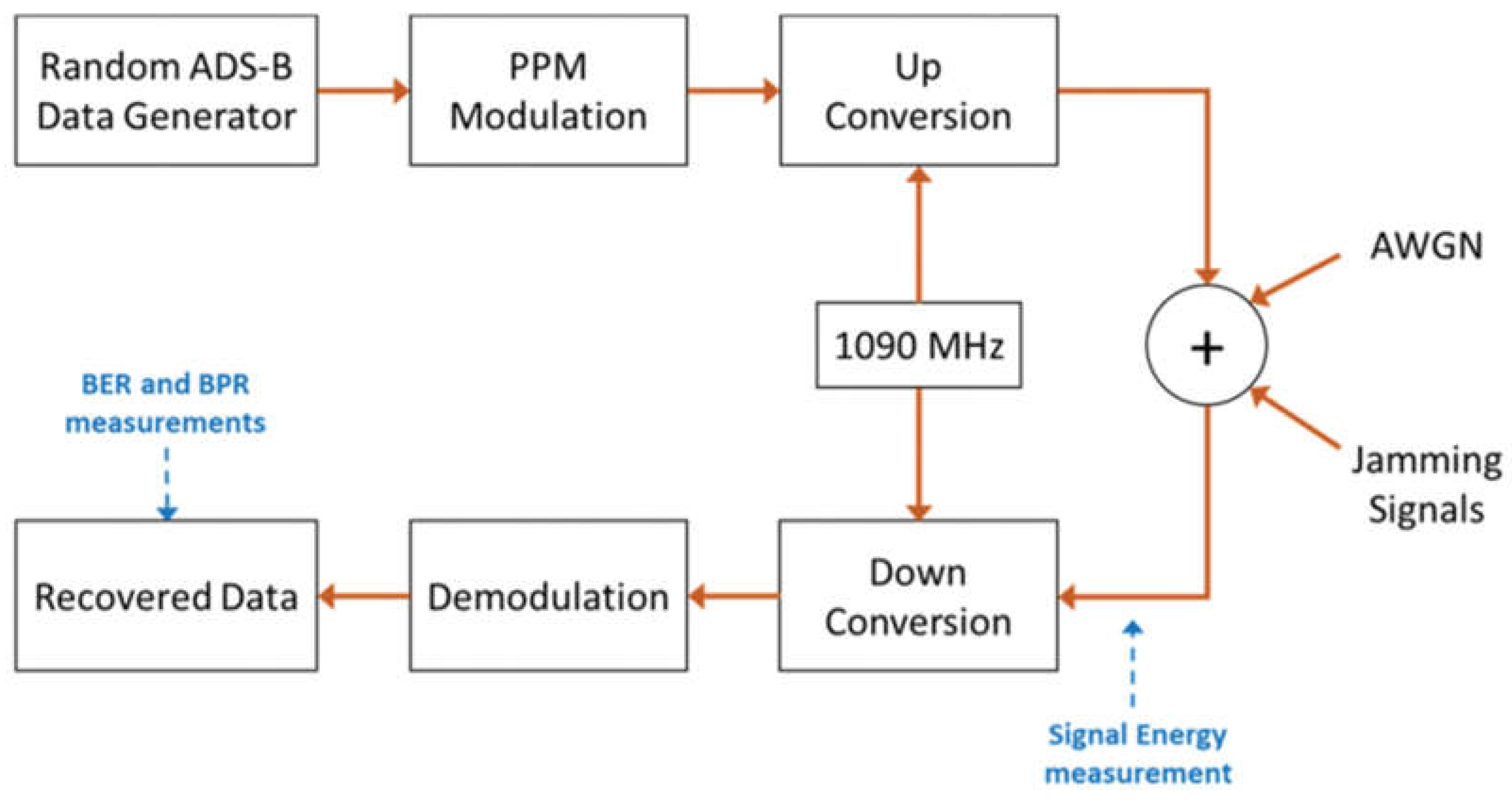
- Jamming Attack: Transmitting similar high-power radio signals on a frequency similar to that used by aircraft for communication can prevent air traffic controllers from receiving legitimate ADS-B messages. This attack will disrupt communication between air traffic control and air, creating difficulties for pilots in receiving instructions from air traffic controllers. Message jamming attacks violate the availability of ADS-B protocol. In [52], the authors discuss and implement multiple methods of active attacks, such as eavesdropping. Table 3 presents a summary of ADS-B Attacks.
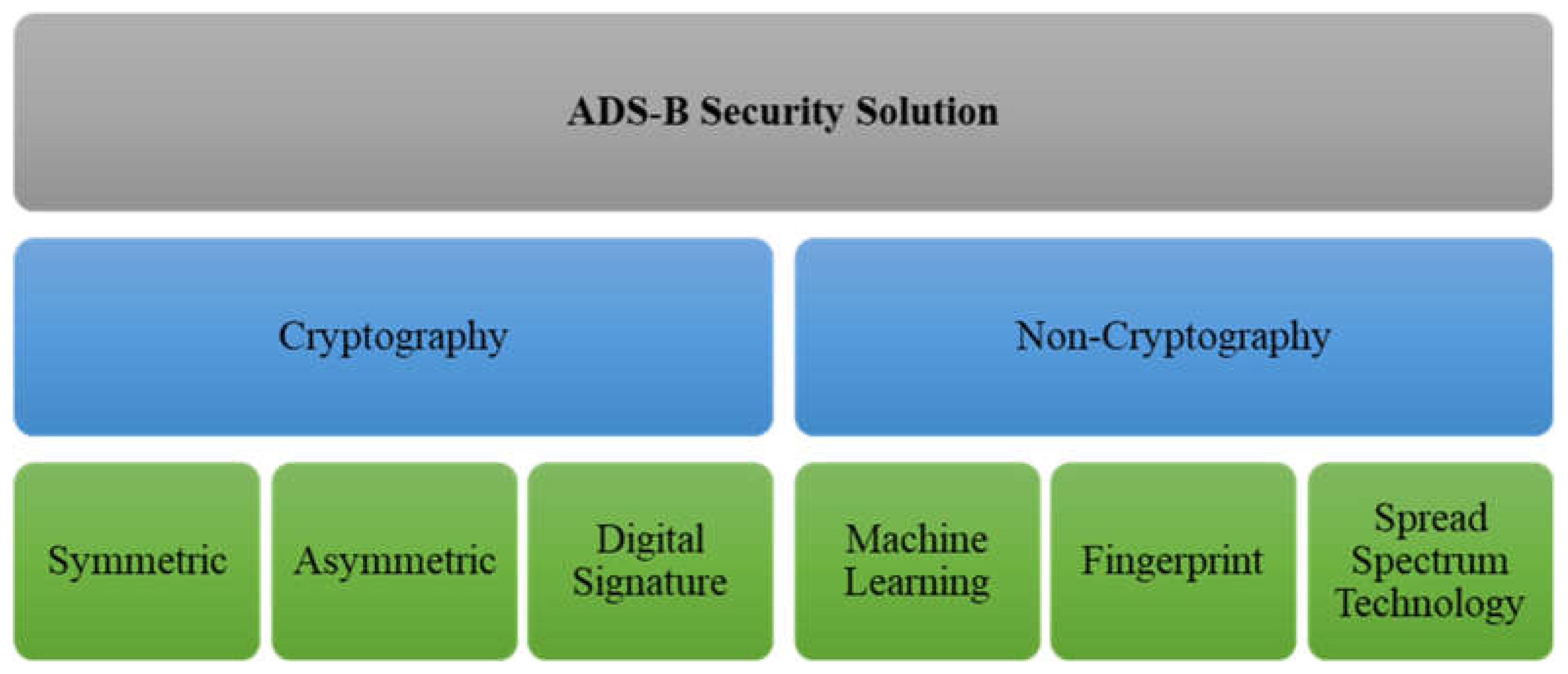
5. Analysis of Existing Solutions
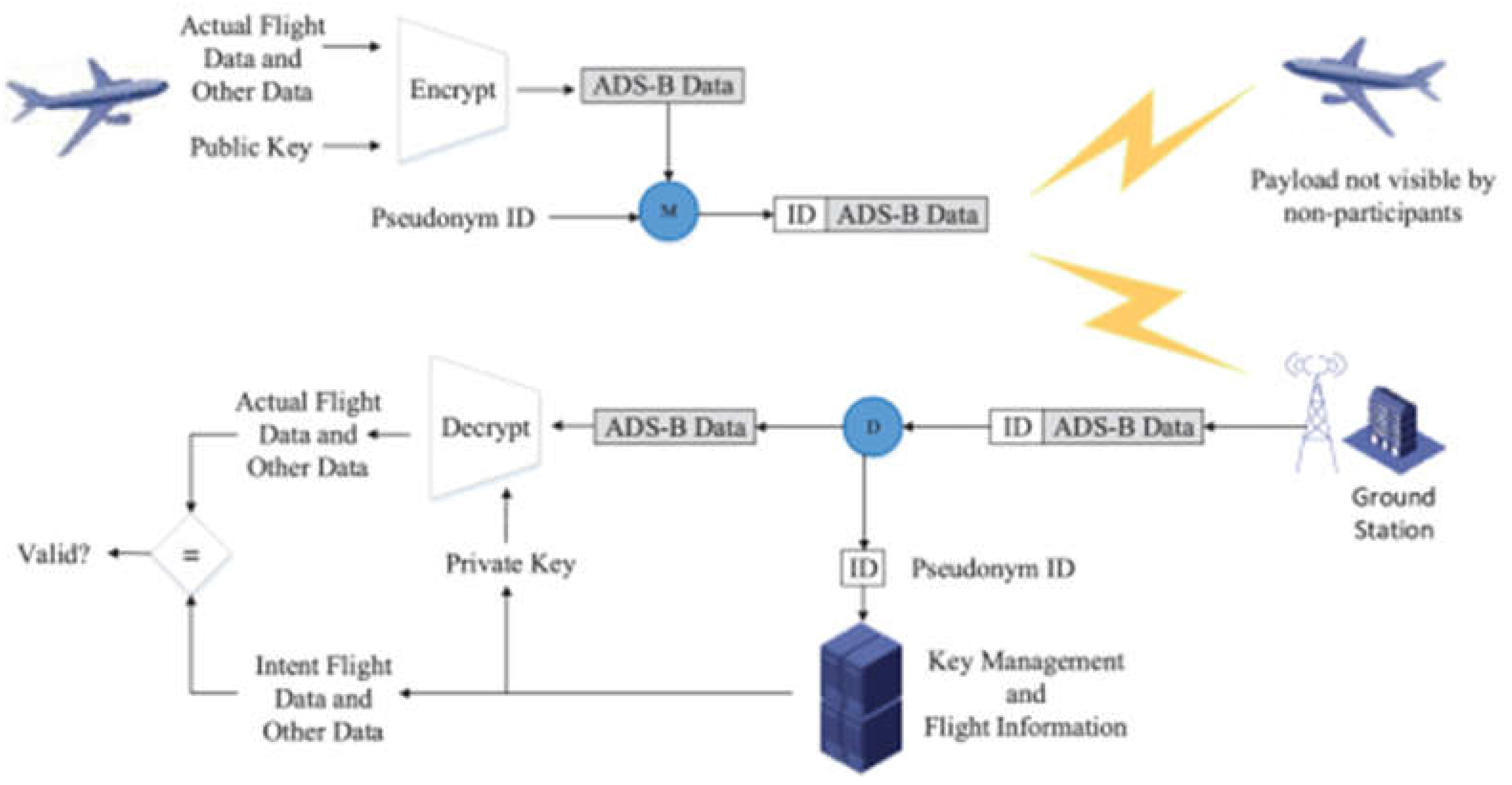
5.1. Cryptography Schemes
5.1.1. Symmetric Cryptography
5.1.2. Asymmetric Cryptography
5.1.3. Digital Signature
5.2. Non-Cryptography Schemes
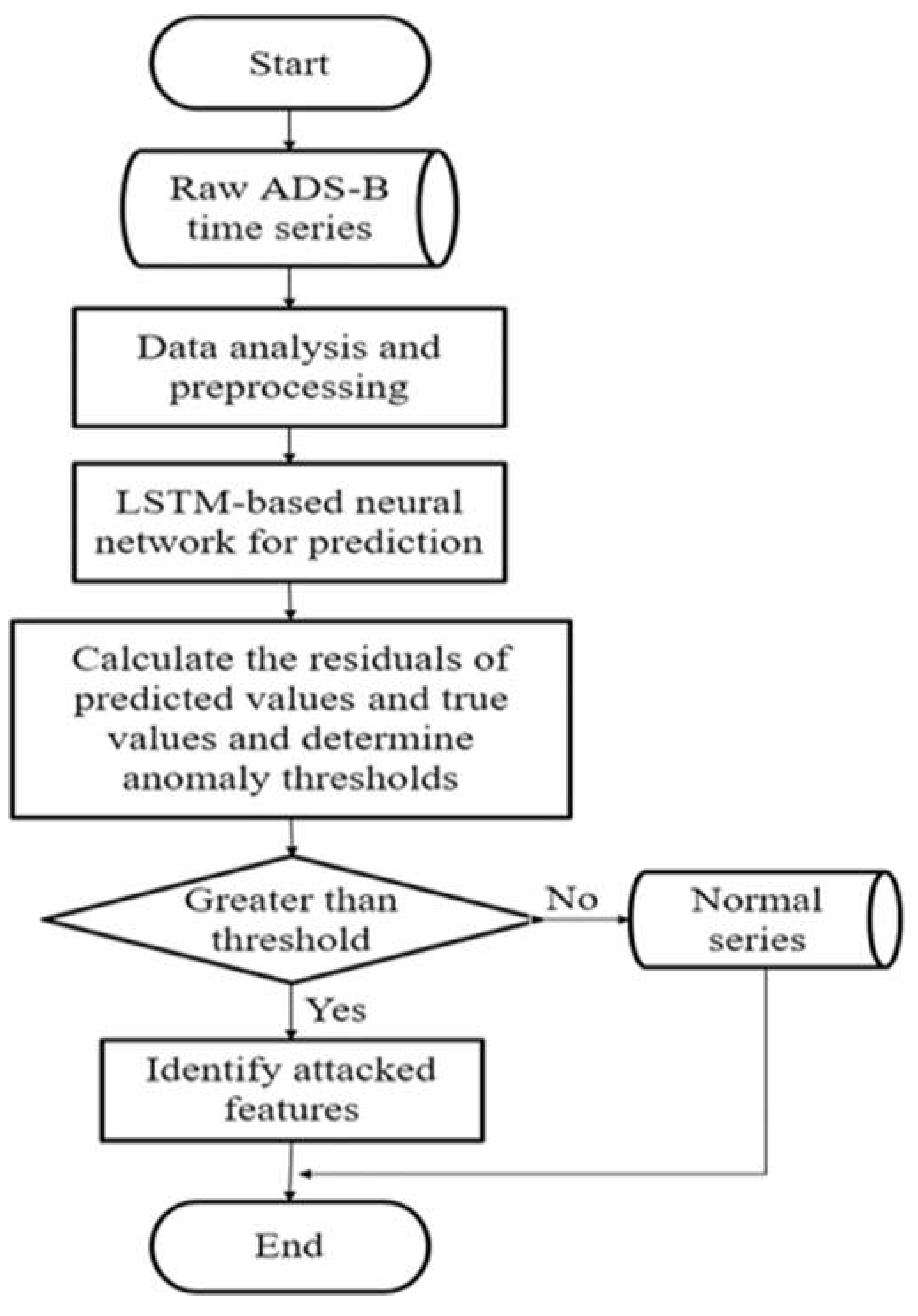
5.2.1. Machine Learning-Based Security Solutions
5.2.2. Fingerprint
5.2.3. Spread Spectrum Technology
6. Security Requirements
- ▪
- Standard Compliance: Security solutions must align with the updated version of the ADS-B protocol to ensure compliance with message format and communication logic.
- ▪
- Backward compatibility: New security solutions should seamlessly integrate with existing systems, allowing aircraft that have yet to update their systems to continue operating.
- ▪
- No Modifications in Hardware: The proposed security solution should require a simple software update without requiring hardware modifications in terms of maintenance and cost.
- ▪
- Limited Message Overhead: Security techniques must introduce minimal additional message overhead to avoid congestion on the 1090ES frequency band.
- ▪
- Cryptography Elements: Despite the limited message size in standard ADS-B packets, the solution's security level should not be compromised.
- ▪
- Packet Loss Events: Given the prevalent packet loss phenomena in the 1090ES frequency band, effective security solutions should demonstrate resilience against incomplete packet reception caused by obstacles and other factors.
7. Challenges and Future Research Directions
- ▪
- Blockchain Integration: Blockchain, a composite system incorporating P2P (peer-to-peer) networks, smart contracts, consensus mechanisms, and cryptography, emerges as a promising solution for secure data sharing in an untrusted network. Blockchain is an exceptional public trust technique that applies to ADS-B protocol, using group certification techniques for ADS-B message integrity and authentication. The researchers should focus on the blockchain's usability in forthcoming research endeavors in ADS-B security. Pioneering work by authors in [21] introduced blockchain technology for identity recognition employing P2P technology for distributed data storage and authentication. This technique showcases high security, reliability, and scalability, offering identity authentication across different infrastructures [104]. Articles such as "Aviation Blockchain Infrastructure" (ABI) propose leveraging blockchain for effective, secure, and private communication between Aircraft and authorized individuals [100].
- ▪
- Machine Learning Applications: Given the importance of abnormal data detection, particularly in a non-encrypted and open protocol like ADS-B, machine learning (ML) provides a compelling solution. In recent years, a surge in anomaly detection techniques based on ML has been witnessed, with deep learning gaining prominence in various domains. Deep learning and machine learning applications will play vital roles in anomaly detection in the ADS-B system. The time series algorithm can enhance detection efficacy by augmenting feature dimensions by leveraging the qualities of rapid ADS-B message updates with accurate time correlation and utilizing deep learning and machine learning models for detecting malicious ADS-B messages. This approach ensures compatibility with existing ADS-B protocols without additional sensors. Numerous articles, including works by [101]–[103], illustrate using deep learning techniques or LSTM networks to enhance ADS-B system security.
- ▪
- Multi-layered Security Framework: The existing security solutions proposed by researchers failed to protect ADS-B from attack as they only provide a certain level of security. Researchers must design and test a security framework based on multi-layered security that can detect and defend ADS-B systems from different attacks.
- ▪
- High Attack Detection with Low False Alarm: Researchers face challenges in developing an attack detection method with low false alarms and high attack detection probabilities. The existing security solutions published by researchers have fundamental implementation limitations. To implement existing methods, researchers have to modify the infrastructure of the ADS-B system or the ADS-B message format. Most importantly, the developed solutions are not tested in a real-time environment, which will affect the method's efficiency. ADS-B system requires a security solution that overcomes the mentioned limitations.
8. Conclusions
References
- Wu, Z.; Shang, T.; Guo, A. Security Issues in Automatic Dependent Surveillance-Broadcast (ADS-B): A Survey. IEEE Access 2020, 8, 122147–122167. [Google Scholar] [CrossRef]
- Jacob, P.; Sirigina, R.P.; Madhukumar, A.S.; Prasad, V.A. Cognitive Radio for Aeronautical Communications: A Survey. IEEE Access 2016, 4, 3417–3443. [Google Scholar] [CrossRef]
- S. Sciancalepore and R. Di Pietro, "SOS: Standard-compliant and packet loss tolerant security framework for ADS-B communications," IEEE Trans Dependable Secure Comput, vol. 18, no. 4, pp. 1681–1698, 2019.
- C. Yang, J. Mott, and D. M. Bullock, "Leveraging aircraft transponder signals for measuring aircraft fleet mix at non-towered airports," International Journal of Aviation, Aeronautics, and Aerospace, vol. 8, no. 2, p. 1, 2021.
- Baek, J.; Hableel, E.; Byon, Y.-J.; Wong, D.S.; Jang, K.; Yeo, H. How to Protect ADS-B: Confidentiality Framework and Efficient Realization Based on Staged Identity-Based Encryption. IEEE Trans. Intell. Transp. Syst. 2016, 18, 690–700. [Google Scholar] [CrossRef]
- R. (Firm). SC-186, Minimum Operational Performance Standards for Universal Access Transceiver (UAT) Automatic Dependent Surveillance Broadcast (ADS-B). RTCA, 2004.
- P. J. Martone and G. E. Tucker, "Candidate requirements for multilateration and ADS-B systems to serve as alternatives to secondary radar," in 20th DASC. 20th Digital Avionics Systems Conference (Cat. No. 01CH37219), IEEE, 2001, pp. 7C2-1.
- C. Rekkas and M. Rees, "Towards ADS-B implementation in Europe," in 2008 Tyrrhenian International Workshop on Digital Communications-Enhanced Surveillance of Aircraft and Vehicles, IEEE, 2008, pp. 1–4.
- A. Costin and A. Francillon, "Ghost in the Air (Traffic): On insecurity of ADS-B protocol and practical attacks on ADS-B devices," black hat USA, vol. 1, pp. 1–12, 2012.
- B. Haines, "Hackers+ airplanes," No good can come of this. Defcon, vol. 20, pp. 26–29, 2012.
- H. Kelly, "Researcher: New air traffic control system is hackable. CNN." 2012.
- Marks, P. Air traffic system vulnerable to cyber attack. New Sci. 2011, 211, 22–23. [Google Scholar] [CrossRef]
- A. Greenberg, "Next-gen air traffic control vulnerable to hackers spoofing planes out of thin air," Forbes Magazine. Retrieved September, vol. 10, p. 2014, 2012.
- M. Schäfer, V. Lenders, and I. Martinovic, "Experimental analysis of attacks on next generation air traffic communication," in Applied Cryptography and Network Security: 11th International Conference, ACNS 2013, Banff, AB, Canada, June 25-28, 2013. Proceedings 11, Springer, 2013, pp. 253–271.
- G. Dave, G. Choudhary, V. Sihag, I. You, and K.-K. R. Choo, "Cyber security challenges in aviation communication, navigation, and surveillance," Comput Secur, vol. 112, p. 102516, 2022.
- T. L. Kraus, "Celebrating a history of excellence: the Federal Aviation Administration and Space Education Outreach Program.," 2011.
- D. I. N. U. EQUIPAGE, “Audit Report,” 2014.
- G. Dave, G. Choudhary, V. Sihag, I. You, and K.-K. R. Choo, "Cyber security challenges in aviation communication, navigation, and surveillance," Comput Secur, vol. 112, p. 102516, 2022.
- H. Ahmed, H. Khan, and M. A. Khan, "A survey on security and privacy of automatic dependent surveillance-broadcast (ads-b) protocol: Challenges, potential solutions and future directions," Authorea Preprints, 2023.
- Pennapareddy, S.; Natarajan, K. Securing ADS-B data transmissions using blockchain: a comprehensive survey and analysis. Aircr. Eng. Aerosp. Technol. 2022, 95, 452–463. [Google Scholar] [CrossRef]
- Wu, Z.; Shang, T.; Guo, A. Security Issues in Automatic Dependent Surveillance-Broadcast (ADS-B): A Survey. IEEE Access 2020, 8, 122147–122167. [Google Scholar] [CrossRef]
- Manesh, M.R.; Kaabouch, N. Analysis of vulnerabilities, attacks, countermeasures and overall risk of the Automatic Dependent Surveillance-Broadcast (ADS-B) system. Int. J. Crit. Infrastruct. Prot. 2017, 19, 16–31. [Google Scholar] [CrossRef]
- Strohmeier, M.; Lenders, V.; Martinovic, I. On the Security of the Automatic Dependent Surveillance-Broadcast Protocol. IEEE Commun. Surv. Tutorials 2014, 17, 1066–1087. [Google Scholar] [CrossRef]
- Strohmeier, M.; Schafer, M.; Lenders, V.; Martinovic, I. Realities and challenges of nextgen air traffic management: the case of ADS-B. IEEE Commun. Mag. 2014, 52, 111–118. [Google Scholar] [CrossRef]
- M. Strohmeier, V. Lenders, and I. Martinovic, "Security of ADS− B: State of the Art and Beyond," DCS, 2013.
- McCallie, D.; Butts, J.; Mills, R. Security analysis of the ADS-B implementation in the next generation air transportation system. Int. J. Crit. Infrastruct. Prot. 2011, 4, 78–87. [Google Scholar] [CrossRef]
- Stastny, P.; Stoica, A.-M. Protecting aviation safety against cybersecurity threats. IOP Conf. Series: Mater. Sci. Eng. 2022, 1226. [Google Scholar] [CrossRef]
- Lu, X.; Dong, R.; Wang, Q.; Zhang, L. Information Security Architecture Design for Cyber-Physical Integration System of Air Traffic Management. Electronics 2023, 12, 1665. [Google Scholar] [CrossRef]
- Paraschi, E.P.; Georgopoulos, A.; Papanikou, M. Safety and security implications of crisis-driven austerity HRM practices in commercial aviation: A structural equation modelling approach. Saf. Sci. 2021, 147, 105570. [Google Scholar] [CrossRef]
- Dave, G.; Choudhary, G.; Sihag, V.; You, I.; Choo, K.-K.R. Cyber security challenges in aviation communication, navigation, and surveillance. Comput. Secur. 2021, 112, 102516. [Google Scholar] [CrossRef]
- Ukwandu, E.; Ben-Farah, M.A.; Hindy, H.; Bures, M.; Atkinson, R.; Tachtatzis, C.; Andonovic, I.; Bellekens, X. Cyber-Security Challenges in Aviation Industry: A Review of Current and Future Trends. Information 2022, 13, 146. [Google Scholar] [CrossRef]
- Jun, J.T.; Gang, G.L.; Qingtao, Q.P. Review on artificial intelligence techniques for improving representative air traffic management capability. J. Syst. Eng. Electron. 2022, 33, 1123–1134. [Google Scholar] [CrossRef]
- Rezo, Z.; Steiner, S.; Mihetec, T.; Čokorilo, O. Strategic planning and development of Air Traffic Management system in Europe: A capacity-based review. Transp. Res. Procedia 2023, 69, 5–12. [Google Scholar] [CrossRef]
- Maurer, N.; Guggemos, T.; Ewert, T.; Graupl, T.; Schmitt, C.; Grundner-Culemann, S. Security in Digital Aeronautical Communications A Comprehensive Gap Analysis. Int. J. Crit. Infrastruct. Prot. 2022, 38. [Google Scholar] [CrossRef]
- Valovage, E. Enhanced ADS-B Research. 2006 ieee/aiaa 25TH Digital Avionics Systems Conference. LOCATION OF CONFERENCE, USADATE OF CONFERENCE; pp. 1–7.
- Boyen, X. A tapestry of identity-based encryption: practical frameworks compared. Int. J. Appl. Cryptogr. 2008, 1, 3. [Google Scholar] [CrossRef]
- E. Chan-Tin, D. Feldman, N. Hopper, and Y. Kim, "The frog-boiling attack: Limitations of anomaly detection for secure network coordinate systems," in Security and Privacy in Communication Networks: 5th International ICST Conference, SecureComm 2009, Athens, Greece, September 14-18, 2009, Revised Selected Papers 5, Springer, 2009, pp. 448–458.
- Finke, C.; Butts, J.; Mills, R.; Grimaila, M. Enhancing the security of aircraft surveillance in the next generation air traffic control system. Int. J. Crit. Infrastruct. Prot. 2013, 6, 3–11. [Google Scholar] [CrossRef]
- N. S. Joseph, C. Banerjee, E. Pasiliao, and T. Mukherjee, "FlightSense: A Spoofer Detection and Aircraft Identification System using Raw ADS-B Data," Proceedings - 2020 IEEE International Conference on Big Data, Big Data 2020, pp. 3885–3894, Dec. 2020. [CrossRef]
- Manesh, M.R.; Kaabouch, N. Cyber-attacks on unmanned aerial system networks: Detection, countermeasure, and future research directions. Comput. Secur. 2019, 85, 386–401. [Google Scholar] [CrossRef]
- FAA Reauthorization Act: Progress and Challenges Implementing Various Provisions of the 2012 Act." Accessed: Dec. 23, 2023. [Online]. Available: https://apps.dtic.mil/sti/citations/AD1102097.
- S. Gorman, Y. J. Dreazen, and A. Cole, "Insurgents hack US drones. The Wall Street Journal." Upd. Dec, 2009.
- Y. Katz, "IDF encrypting drones after Hezbollah accessed footage," Jerusalem Post, 2010.
- A. Wood, "After ADS-B launch, security concerns raised," Aviation International News, vol. 38, no. 16, Jul. 2006.
- INDIA’S NATIONAL SECURITY: ISSUES AND CHALLENGES - Dr. NASIR AHMAD GANAIE - Google Books.” Accessed: Dec. 23, 2023. [Online]. Available: https://books.google.com.pk/books?hl=en&lr=&id=adWmEAAAQBAJ&oi=fnd&pg=PA59&dq=NDTV,+A+phone+application+that+threatens+security,+Press+Trust+of+India,+New+Delhi,+India,+October+4,+2010.&ots=F5jZB7KOW6&sig=heSBl1Bmq6nbxSXXql1snctwwQc&redir_esc=y#v=onepage&q&f=false.
- M. Unnikrishnan, “ITT Calls on AT&T for ADS-B infrastructure,” Aviation Week, 2007.
- Spainhower, M.; Butts, J.; Guernsey, D.; Shenoi, S. Security analysis of RSVP-TE signaling in MPLS networks. Int. J. Crit. Infrastruct. Prot. 2008, 1, 68–74. [Google Scholar] [CrossRef]
- Wu, Z.; Guo, A.; Yue, M.; Liu, L. An ADS-B Message Authentication Method Based on Certificateless Short Signature. IEEE Trans. Aerosp. Electron. Syst. 2020, 56, 1742–1753. [Google Scholar] [CrossRef]
- M. R. Manesh, M. Mullins, K. Foerster, and N. Kaabouch, “A preliminary effort toward investigating the impacts of ADS-B message injection attack,” in 2018 IEEE Aerospace Conference, IEEE, 2018, pp.
- K. F. Mirzaei, B. P. De Carvalho, and P. Pschorn, “Security of ADS-B: Attack scenarios,” EasyChair, Tech. Rep, 2019.
- Shang, F.; Wang, B.; Yan, F.; Li, T. Multidevice False Data Injection Attack Models of ADS-B Multilateration Systems. Secur. Commun. Networks 2019, 2019, 1–11. [Google Scholar] [CrossRef]
- Costin and, A. Francillon, “Ghost in the Air (Traffic): On insecurity of ADS-B protocol and practical attacks on ADS-B devices,” black hat USA, vol. 1, pp. 1–12, 2012.
- H. Yang, H. Li, and X. S. Shen, “Modern Cryptography for ADS-B Systems,” in Secure Automatic Dependent Surveillance-Broadcast Systems, Springer, 2022, pp.
- R. Bavdekar, E. J. Chopde, A. Agrawal, A. Bhatia, and K. Tiwari, “Post Quantum Cryptography: A Review of Techniques, Challenges and Standardizations,” International Conference on Information Networking, vol. 2023-January, pp. 146–151, 2023. [CrossRef]
- L. R. John Jochum, “Encripted mode select ADS-B for tactical military situational awareness,” 2001, Accessed: Dec. 25, 2023. [Online]. Available: https://dspace.mit.edu/bitstream/handle/1721.1/86721/49223652-MIT.
- H. Yang, M. Yao, Z. Xu, and B. Liu, “LHCSAS: A Lightweight and Highly-Compatible Solution for ADS-B Security,” 2017 IEEE Global Communications Conference, GLOBECOM 2017 - Proceedings, vol. 2018-January, pp. 1–7, Jul. 2017. [CrossRef]
- R. Agbeyibor, “Secure ADS-B: Towards Airborne Communications Security in the Federal Aviation Administration’s Next Generation Air Transportation System,” Theses and Dissertations, Mar. 2014, Accessed: Dec. 25, 2023. [Online]. Available: https://scholar.afit.
- K. D. Wesson, T. E. Humphreys, and B. L. Evans, “Can cryptography secure next generation air traffic surveillance?,” IEEE Security and Privacy Magazine, 2014.
- Zhang, S.; Li, H.; Dai, Y.; Li, J.; He, M.; Lu, R. Verifiable Outsourcing Computation for Matrix Multiplication With Improved Efficiency and Applicability. IEEE Internet Things J. 2018, 5, 5076–5088. [Google Scholar] [CrossRef]
- Li, H.; Yang, Y.; Dai, Y.; Yu, S.; Xiang, Y. Achieving Secure and Efficient Dynamic Searchable Symmetric Encryption over Medical Cloud Data. IEEE Trans. Cloud Comput. 2020, 8, 484–494. [Google Scholar] [CrossRef]
- Z. Feng, W. Pan, and Y. Wang, “A data authentication solution of ADS-B system based on X. 509 certificate,” in 27th International Congress of the Aeronautical Sciences, ICAS, 2010, pp. 1–6.
- C. Gentry and A. Silverberg, “Hierarchical id-based cryptography,” Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), vol. 2501, pp. 548–566, 2002. [CrossRef]
- S. S. M. Chow, L. C. K. Hui, S. M. Yiu, and K. P. Chow, “Secure hierarchical identity based signature and its application,” Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), vol. 3269, pp. 480–494, 2004. [CrossRef]
- E. Cook, “ADS-B, friend or foe: ADS-B message authentication for NextGen aircraft,” in 2015 IEEE 17th International Conference on High Performance Computing and Communications, 2015 IEEE 7th International Symposium on Cyberspace Safety and Security, and 2015 IEEE 12th International Conference on Embedded Software and Systems, IEEE, 2015, pp. 1256–1261.
- H. Khan, H. Khan, and S. Ghafoor, “Securing ADS-B Communications through a Novel Authentication Framework,” 2023.
- W. Pan, Z. Feng, Y. W.-J. of E. S. and, and undefined 2012, “ADS-B data authentication based on ECC and X. 509 certificate,” journal.uestc.edu.cnWJ Pan, ZL Feng, Y WangJournal of Electronic Science and Technology, 2012•journal.uestc.edu.cn. [CrossRef]
- J. Baek, Y. J. Byon, E. Hableel, and M. Al-Qutayri, “An authentication framework for Automatic Dependent Surveillance-Broadcast based on online/offline identity-based signature,” Proceedings - 2013 8th International Conference on P2P, Parallel, Grid, Cloud and Internet Computing, 3PGCIC 2013, pp. 358–363, 2013. [CrossRef]
- Yang, H.; Huang, R.; Wang, X.; Deng, J.; Chen, R. EBAA: An efficient broadcast authentication scheme for ADS-B communication based on IBS-MR. Chin. J. Aeronaut. 2014, 27, 688–696. [Google Scholar] [CrossRef]
- Markani, J.H.; Amrhar, A.; Gagné, J.-M.; Landry, R.J. Security Establishment in ADS-B by Format-Preserving Encryption and Blockchain Schemes. Appl. Sci. 2023, 13, 3105. [Google Scholar] [CrossRef]
- EBSCOhost | 100818950 | An Efficient Broadcast Authentication Scheme with Batch Verification for ADS-B Messages.” Accessed: Dec. 26, 2023. [Online]. Available: https://web.s.ebscohost.com/abstract?direct=true&profile=ehost&scope=site&authtype=crawler&jrnl=19767277&AN=100818950&h=TvZ4Ne1ukku%2fhD0aeo%2b%2f09%2fGkYyBFZcpHy%2bND%2bDGPvpW.
- Yang, A.; Tan, X.; Baek, J.; Wong, D.S. A New ADS-B Authentication Framework Based on Efficient Hierarchical Identity-Based Signature with Batch Verification. IEEE Trans. Serv. Comput. 2015, 10, 165–175. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Choo, K.-K.R.; Wu, W. Efficient Hierarchical Identity-Based Signature With Batch Verification for Automatic Dependent Surveillance-Broadcast System. IEEE Trans. Inf. Forensics Secur. 2016, 12, 454–464. [Google Scholar] [CrossRef]
- Wu, Z.; Shang, T.; Guo, A. Security Issues in Automatic Dependent Surveillance-Broadcast (ADS-B): A Survey. IEEE Access 2020, 8, 122147–122167. [Google Scholar] [CrossRef]
- Finke, C.; Butts, J.; Mills, R.; Grimaila, M. Enhancing the security of aircraft surveillance in the next generation air traffic control system. Int. J. Crit. Infrastruct. Prot. 2013, 6, 3–11. [Google Scholar] [CrossRef]
- H. Yang, M. Yao, Z. Xu, and B. Liu, “LHCSAS: A Lightweight and Highly-Compatible Solution for ADS-B Security,” 2017 IEEE Global Communications Conference, GLOBECOM 2017 - Proceedings, vol. 2018-January, pp. 1–7, Jul. 2017. [CrossRef]
- H. Yang, H. Li, and X. S. Shen, “Secure Automatic Dependent Surveillance-Broadcast Systems,” 2023. [CrossRef]
- D. Boneh and M. Franklin, “Identity-Based Encryption from the Weil Pairing,” https://doi.org/10.1137/S0097539701398521, vol. 32, no. 3, pp. 586–615, Feb. 2012. [CrossRef]
- Yi, P.; Li, J.; Zhang, Y.; Chen, Y. Efficient Hierarchical Signature Scheme with Batch Verification Function Suitable for ADS-B System. IEEE Trans. Aerosp. Electron. Syst. 2022, PP, 1–9. [Google Scholar] [CrossRef]
- Asari, A.; Alagheband, M.R.; Bayat, M.; Asaar, M.R. A new provable hierarchical anonymous certificateless authentication protocol with aggregate verification in ADS-B systems. Comput. Networks 2020, 185, 107599. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Choo, K.-K.R.; Wu, W. Efficient Hierarchical Identity-Based Signature With Batch Verification for Automatic Dependent Surveillance-Broadcast System. IEEE Trans. Inf. Forensics Secur. 2016, 12, 454–464. [Google Scholar] [CrossRef]
- B. Burfeind, R. Mills, S. Nykl, J. A. Betances, and C. Sielski, “Confidential ADS-B,” IEEE Aerospace Conference Proceedings, vol. 2019-March, Mar. 2019. [CrossRef]
- Braeken, A. Holistic Air Protection Scheme of ADS-B Communication. IEEE Access 2019, 7, 65251–65262. [Google Scholar] [CrossRef]
- M. R. Manesh, M. S. Velashani, E. Ghribi, and N. Kaabouch, “Performance comparison of machine learning algorithms in detecting jamming attacks on ADS-B devices,” in 2019 IEEE International Conference on Electro Information Technology (EIT), IEEE, 2019, pp.
- T. Kacem, A. Kaya, A. S. Keceli, C. Catal, D. Wijsekera, and P. Costa, “ADS-B Attack Classification using Machine Learning Techniques,” in 2021 IEEE Intelligent Vehicles Symposium Workshops (IV Workshops), IEEE, 2021, pp. 7–12.
- H. Yang, H. Li, and X. S. Shen, “Complete ADS-B Security Solution,” in Secure Automatic Dependent Surveillance-Broadcast Systems, Springer, 2022, pp.
- S. Khan, J. Thorn, A. Wahlgren, and A. Gurtov, “Intrusion detection in automatic dependent surveillance-broadcast (ADS-B) with machine learning,” in 2021 IEEE/AIAA 40th Digital Avionics Systems Conference (DASC), IEEE, 2021, pp.
- Mink, D.M.; McDonald, J.; Bagui, S.; Glisson, W.B.; Shropshire, J.; Benton, R.; Russ, S. Near-Real-Time IDS for the U.S. FAA’s NextGen ADS-B. Big Data Cogn. Comput. 2021, 5, 27. [Google Scholar] [CrossRef]
- R. Karam, M. Salomon, and R. Couturier, “A comparative study of deep learning architectures for detection of anomalous ADS-B messages,” in 2020 7th International Conference on Control, Decision and Information Technologies (CoDIT), IEEE, 2020, pp.
- Wang, J.; Zou, Y.; Ding, J. ADS-B spoofing attack detection method based on LSTM. EURASIP J. Wirel. Commun. Netw. 2020, 2020, 1–12. [Google Scholar] [CrossRef]
- R. Karam, M. Salomon, and R. Couturier, “Supervised ADS-B Anomaly Detection Using a False Data Generator,” in 2022 2nd International Conference on Computer, Control and Robotics (ICCCR), IEEE, 2022, pp.
- X. Guo, C. Zhu, J. Yang, and Y. Xiao, “An Anomaly Detection Model for ADS-B Systems Based on Improved GAN and LSTM Networks,” in 2021 IEEE 21st International Conference on Communication Technology (ICCT), IEEE, 2021, pp.
- N. S. Joseph, C. Banerjee, E. Pasiliao, and T. Mukherjee, “FlightSense: A spoofer detection and aircraft identification system using raw ADS-B data,” in 2020 IEEE International Conference on Big Data (Big Data), IEEE, 2020, pp. 3885–3894.
- X. Ying, J. Mazer, G. Bernieri, M. Conti, L. Bushnell, and R. Poovendran, “Detecting ADS-B spoofing attacks using deep neural networks,” in 2019 IEEE conference on communications and network security (CNS), IEEE, 2019, pp. 187–195.
- Habler, E.; Shabtai, A. Using LSTM encoder-decoder algorithm for detecting anomalous ADS-B messages. Comput. Secur. 2018, 78, 155–173. [Google Scholar] [CrossRef]
- Danev, B.; Zanetti, D.; Capkun, S. On physical-layer identification of wireless devices. ACM Comput. Surv. 2012, 45, 1–29. [Google Scholar] [CrossRef]
- Zeng, K.; Govindan, K.; Mohapatra, P. Non-cryptographic authentication and identification in wireless networks [Security and Privacy in Emerging Wireless Networks. IEEE Wirel. Commun. 2010, 17, 56–62. [Google Scholar] [CrossRef]
- Y. Liu, P. Ning, H. Dai, and A. Liu, “Randomized differential DSSS: Jamming-resistant wireless broadcast communication,” in 2010 Proceedings IEEE INFOCOM, IEEE, 2010, pp.
- C. Pöpper, M. Strasser, and S. Capkun, “Jamming-resistant broadcast communication without shared keys.,” in USENIX security Symposium, 2009, pp. 231–248.
- M. Strasser, C. Popper, S. Capkun, and M. Cagalj, “Jamming-resistant key establishment using uncoordinated frequency hopping,” in 2008 IEEE Symposium on Security and Privacy (sp 2008), IEEE, 2008, pp.
- R. J. Reisman, “Air traffic management blockchain infrastructure for security, authentication, and privacy,” AIAA Scitech 2019 Forum, 2019. [CrossRef]
- Habler, E.; Shabtai, A. Using LSTM encoder-decoder algorithm for detecting anomalous ADS-B messages. Comput. Secur. 2018, 78, 155–173. [Google Scholar] [CrossRef]
- S. Akerman, E. Habler, and A. Shabtai, “VizADS-B: Analyzing Sequences of ADS-B Images Using Explainable Convolutional LSTM Encoder-Decoder to Detect Cyber Attacks,” Jun. 2019, Accessed: Dec. 24, 2023. [Online]. Available: https://arxiv.org/abs/1906.07921v1.
- Chen, S.; Zheng, S.; Yang, L.; Yang, X. Deep Learning for Large-Scale Real-World ACARS and ADS-B Radio Signal Classification. IEEE Access 2019, 7, 89256–89264. [Google Scholar] [CrossRef]

| Ref. & Year | Aviation Security | Security Analysis | Security Analysis Diagram | Security Solution Analysis | Security Requirements | Research Direction | ||
|---|---|---|---|---|---|---|---|---|
| Cryptography | Non-Cryptography | ML/DL | ||||||
| [1] 2023 |
✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ |
| [2] 2022 |
✓ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ |
| [3] 2020 |
✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ |
| [4] 2017 |
✓ | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ | ✓ |
| [5] 2015 |
✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ |
| [6] 2014 |
✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ |
| [7] 2013 |
✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ |
| [8] 2011 |
✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ |
| Proposed Survey | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Abbreviation | Description | Abbreviation | Description |
|---|---|---|---|
| ADS-B | Automatic Dependent Surveillance-Broadcast | ICT | Information and Communications Technology |
| NextGen | Next Generation | ATC | Air Traffic Control |
| FAA | Federal Aviation Administration | RF | Radio Frequency |
| ACAS | Automatic Collision Avoidance System | RTC | Radio Technical Committee |
| CPDLC | Controlled Pilot Data-Link Communication | VHF | Very High-Frequency |
| HF | High-Frequency | DL | Deep Learning |
| ILS | Instrument Landing System | ICAO | International Civil Aviation Organization |
| PSR | Primary Surveillance Radar | SSR | Secondary Surveillance Radar |
| ATM | Air Traffic Management | DSCN | Digital Satellite Communication Networks |
| NIST | National Institute of Standards and Technology | MPLS | Multiprotocol Labeled Switching |
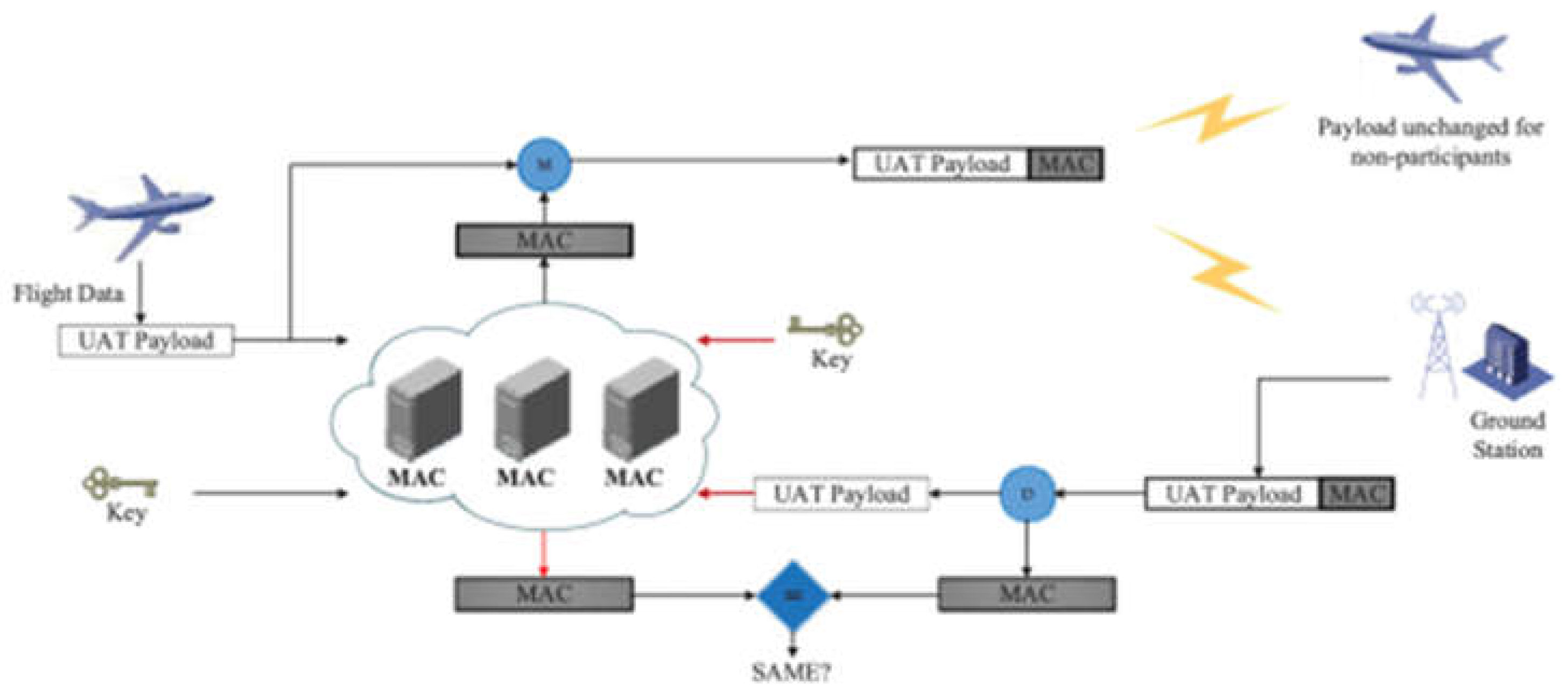
| CA | Certification Authority | MAC | Message Authentication Code |
| ECDSA | Elliptic Curve Digital Signature Algorithm | IBE | Identity-Based Encryption |
| HAP | Holistic Air Protection | LSTM | Short-Term Long Memory |
| CNN | Conventional Neural Network | P2P | Peer-to-Peer |
| Sr# | Attack | Sub-Attacks | Attack Purpose | Attack Method |
|---|---|---|---|---|
| 1. | Eavesdropping | Reconnaissance attack | Getting aircraft information is also called aircraft reconnaissance. | Using an ADS-B receiver, obtain the corresponding airspace data. |
| 2. | Jamming | Denial of service, flooding attack | Jam ADS-B communicates for a certain amount of time in a specific airspace. | Transmit high-frequency signal on the targeted frequency band (1090ES) |
| 3. | Message Injection | Ghost injection | To mislead ATC in the targeted airspace, inject fake aircraft. | Using a power transmitting device generates and injects fake messages using relevant frequency. |
| 4. | Message deletion | Aircraft disappearance | Deleted target field or complete message | At physical layers, flip the bits in the ADS-B message. |
| 5. | Message modification | Virtual trajectory modification | Modify the content of the message | Implemented by combining message injection and deletion attack. |
| Threat | Impact on System |
|---|---|
| Interception | Protocol-insignificant but perhaps useful for malicious tracking |
| Data Manipulation | Message Integrity is compromised, leading to misleading or omitted collision avoidance alerts, confusion, and incorrect controller actions; Safety Hazard. |
| Identity Spoofing | The integrity of the message is undermined by fraudulent tracks utilized for deceiving air traffic control; Risk to Safety |
| Ghost Flights | False flight information is transmitted with the intention of perplexing controllers or overloading receiver processing capacity, compromising its dependability. Prudence for Safety |
| Disappearance ofOriginal Flight | This is accomplished by replaying the Aircraft's previous flight data before its presence in the coverage area, thus preventing the dissemination of the most recent flight information. |
| Ref. Year |
Cryptographic Technique | Research Contribution | Strengths | Challenges |
|---|---|---|---|---|
| [9] 2006 |
Symmetric Cryptography |
The authors proposed research surveys on the ADS-B potential solutions and security concerns. | Symmetric cryptography-based solutions are suitable for bulk data, with less overhead, speed and efficiency. | Challenges included data integrity, message authentication, key management, and exchange. |
| [5] 2014 | ||||
| [10] 2020 | ||||
| [11] 2013 |
The authors proposed an encryption algorithm based on FFX-A2 (Format Preserving) | |||
| [12] 2017 |
Using Vector Homomorphic and FFX encryption, the authors proposed solutions for ADS-B message integrity and privacy. | |||
| [13] 2022 | ||||
| [14] 2012 |
Using IBE (Identity-Based Encryption) for key encryption and sharing and hybrid technique with symmetric cryptography for data. | |||
| [15] 2017 |
Proposed a technique to address the problems of key sharing and authentication. | |||
| [16] 2023 |
Asymmetric Cryptography |
The authors proposed a solution based on a hierarchical signature technique based on a certificate-less signature technique utilizing aggregate signatures to reduce the processing time using key validation and setup processes through various communication components. | Asymmetric cryptography-based solutions are suitable for ADS-B message integrity, privacy, cryptography key distribution, message confidentiality and authentication. | Challenges included message overhead, increase in computational cost, performance, and key management. |
| [17] 2021 | ||||
| [18] 2017 | ||||
| [19] 2019 |
The authors proposed a lightweight protocol based on symmetric and asymmetric encryption for ADS-B message confidentiality. ATC plays the role of TTP in the proposed protocol to manage the session data and the encryption keys. | |||
| [20] 2014 |
From the ADS-B security point of view, the authors discussed the suitability of ECDSA (Elliptic Curve Digital Signature Algorithm) from the perspectives of signature length and standard constraints. | |||
| [21] 2019 |
To protect ADS-B message confidentiality and authentication, the author proposed a technique based on HAP (Holistic Air Protection) using an elliptic curve and certificates-based encryption. | |||
| [22] 2019 |
Digital Signature | Based on the certificated less signature, the authors presented the ADS-B message authentication technique. The proposed technique is performance efficient and does not need any certificate management authority. | Digital signatures provide integrity, authentication, and non-repudiation to ADS-B message data. | Challenges included complexity, interoperability, algorithm performance and key management in a large space. |
| Year & Ref. | Dataset Description | ML Models | Accuracy |
|---|---|---|---|
| 2022 [23] | Opensky (20 randomly chosen flights are downloaded from the OpenSky Network) | LSTM | 98% |
| 2021 [24] | FlightRadar24 (authors used a dataset containing messages of 1 flight from Lisbon to Paris) | SVM DT RF |
91% 92% 90% |
| 2021 [25] | OpenSky (the dataset containing 26000) | LR NB K-NN |
52.10% 82.10% 99.57% |
| 2021 [26] | Flightradar24 (authors didn't mention the details of the dataset) | LSTM with GAN | 97% |
| 2021 [27] | OpenSky (dataset with 20,000 messages, 10,000 legitimate and 10,000 nonlegitimate) | SVM | 80% |
| 2020 [28] | Simulated (authors didn't mention the details of the dataset) | LSTM | 93% |
| 2020 [29] | Simulated (18675 messages are collected for experiments) | GAN CNN |
98.87 % 99% |
| 2020 [30] | OpenSky (the author didn't mention the number of legitimate and nonlegitimate messages) | LSTM | 91.59% |
| 2019 [31] | Simulated (authors didn't mention the details of the dataset and number of messages used in the experiments) | LR SVM KNN ANN DT |
65.6% 67.3% 74.6% 81% 74.2% |
| 2019 [32] | Simulated (the dataset contains only 18675 messages, and the author didn't mention the number of legitimate and nonlegitimate messages) | DNN | 96.66% |
| 2018 [33] | Simulated (authors didn't mention the details of the dataset) | LSTM | 95.50% |
| Category | Compatibility | Scalability | Difficulty | Cost |
|---|---|---|---|---|
| Symmetric Cryptography | Key management and sharing | Medium | High | High |
| Asymmetric Cryptography | Key generation, sharing, and storing | Medium | High | High |
| Message Authentication Code (MAC) | Key management and change message format | Medium | Low | Low |
| Machine Learning | Need to add software | High | Low | Low |
| Spread Spectrum | Change the system and add hardware | Medium | High | High |
| Fingerprinting | We need to add hardware, but there is no need to modify the system | Medium | Medium | High |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





