Submitted:
06 May 2024
Posted:
07 May 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Background
1.2. Motivation
1.3. Main Work
- 1.
- To address the performance shortcomings of traditional PSI-CA protocols in the face of significant differences in dataset sizes between participants, this paper introduces the first protocol, which is the unbalanced PSI-CA protocol based on Cuckoo filter. This protocol successfully constructs the first unbalanced private intersection cardinality protocol of this article by integrating exchange encryption technologies with Cuckoo filter functionalities for private information retrieval, followed by experimental analysis.
- 2.
- To alleviate the computational and storage burden on small health app developer in the first protocol, the paper further proposes an unbalanced PSI-CA protocol based on single cloud assistance and conducts experimental analysis. This strategy effectively migrates computational and storage tasks to cloud services, significantly optimizing resource utilization efficiency.
- 3.
- To safeguard against data leakage risks inherent in the unbalanced PSI-CA protocol based on single cloud assistance which cannot resist collusion attacks, the paper further designs an unbalanced PSI-CA protocol based on dual cloud assistance. By employing homomorphic encryption and other security technologies, this scheme resolves potential data leakage risks in the single-cloud protocol while effectively preventing potential collusion attacks.
- 4.
- Based on the unbalanced PSI-CA protocol based on dual cloud assistance, this paper also designs the PSI-CA network and establishes corresponding data update strategies, significantly enhancing the practicality of the protocol.
2. Related Works
2.1. Design Framework of Private Set Intersection Protocol
2.1.1. Design Framework Based on Public Key Encryption
- 1.
- Based on Diffie-Hellman (DH) theory: Meadows [5] used the DH key exchange mechanism, which is based on the discrete logarithm problem, to implement a PSI protocol. In contrast, Huberman [6] and his team explored the use of elliptic curve cryptography in PSI, noting its significant advantages in security and efficiency compared to traditional discrete logarithm-based PSI methods.
- 2.
- Based on the RSA assumption: DeCristofaro and others [7] developed a semi-honest PSI protocol using RSA blind signature technology based on the integer factorization problem. Another study [8] showed that PSI schemes based on discrete logarithm cryptography demonstrated higher efficiency compared to those based on integer factorization cryptography.
- 3.
- Based on homomorphic encryption: Freedman and his team [9] innovatively represented elements as roots of polynomials and encrypted the coefficients of these polynomials using Paillier homomorphic encryption technology, combined with zero-knowledge proofs, to implement a two-party PSI protocol resistant to malicious attacks. In 2016, Freedman et al. [10] further improved computational efficiency through the ElGamal encryption mechanism and reduced the protocol’s computational complexity using Cuckoo Hash technology [4]. Abadi et al. [11] introduced a set representation method based on point-value pairs of d-degree polynomials, implemented through the Paillier encryption scheme, reducing the multiplication complexity from O() to O(d) [4]. Kissner and other researchers [12] adopted different polynomial representation methods, significantly reducing computational costs to be linearly proportional to the number of participants. Jarecki and others [13] used additive homomorphic encryption and zero-knowledge proofs to implement pseudorandom functions (PRF). Hazay and others [14] developed an additive homomorphic encryption scheme that supports threshold decryption for implementing multi-party semi-honest PSI protocols. Dou Jiawei and others [15] combined Paillier encryption to propose a PSI protocol based on the formula for calculating the area of triangles and rational number encoding.
2.1.2. Design Framework Based on Garbled Circuits
2.1.3. Design Framework Based on Oblivious Transfer
2.2. PSI-CA
3. Related Theories and Technologies
3.1. Multi-Party Secure Computation Security Model
- 1.
- Semi-honest model: In this model, participants adhere to the protocol’s execution rules but may attempt to gather other participants’ inputs, outputs, and any accessible information during the execution of the protocol. This model assumes that the participants do not deviate from the established procedural rules but will use all available information to deduce the private data of others.
- 2.
- Malicious adversary model: Unlike the semi-honest model, the malicious adversary model accounts for the possibility that attackers may manipulate a subset of the participants to perform illicit actions, such as submitting incorrect input data or maliciously altering data to steal the private information of honest participants. Malicious adversaries might also disrupt the protocol by intentionally terminating its execution or by refusing to participate, thus preventing the protocol’s completion.
3.2. Cuckoo Filter
3.3. Paillier Homomorphic Encryption
- 1.
- Additive Homomorphism: If and , then . This allows for performing addition operations on ciphertexts without needing to decrypt them first.
- 2.
- Scalar Multiplication Homomorphism: If , then . This means that it is possible to perform multiplication operations between a ciphertext and a plaintext scalar without decryption.
4. PSI-CA Protocol Constructed Based on DH Key Exchange Mechanism
4.1. Protocol Process
4.1.1. Exchange and Computation Stage
- 1.
- Receiver Data Encryption: The receiver encrypts with its private key , obtaining and sends it to the sender.
- 2.
- Sender Computation: Upon receiving , the sender applies its private key to compute and shuffles it before sending it back to the receiver.
- 3.
- Sender Data Encryption: The sender encrypts with its private key , resulting in and sends it to the receiver to facilitate the computation of the intersection cardinality.
4.1.2. Cardinality Calculation Stage
- 1.
- Receiver Decryption and Computation: The receiver uses the inverse of to decrypt to retrieve . By comparing with , the receiver can calculate the cardinality of the intersection between the two sets.
4.2. Experimental Analysis
4.3. Summary of This Chapter
5. Unbalanced PSI-CA Protocol Based on Cuckoo Filter
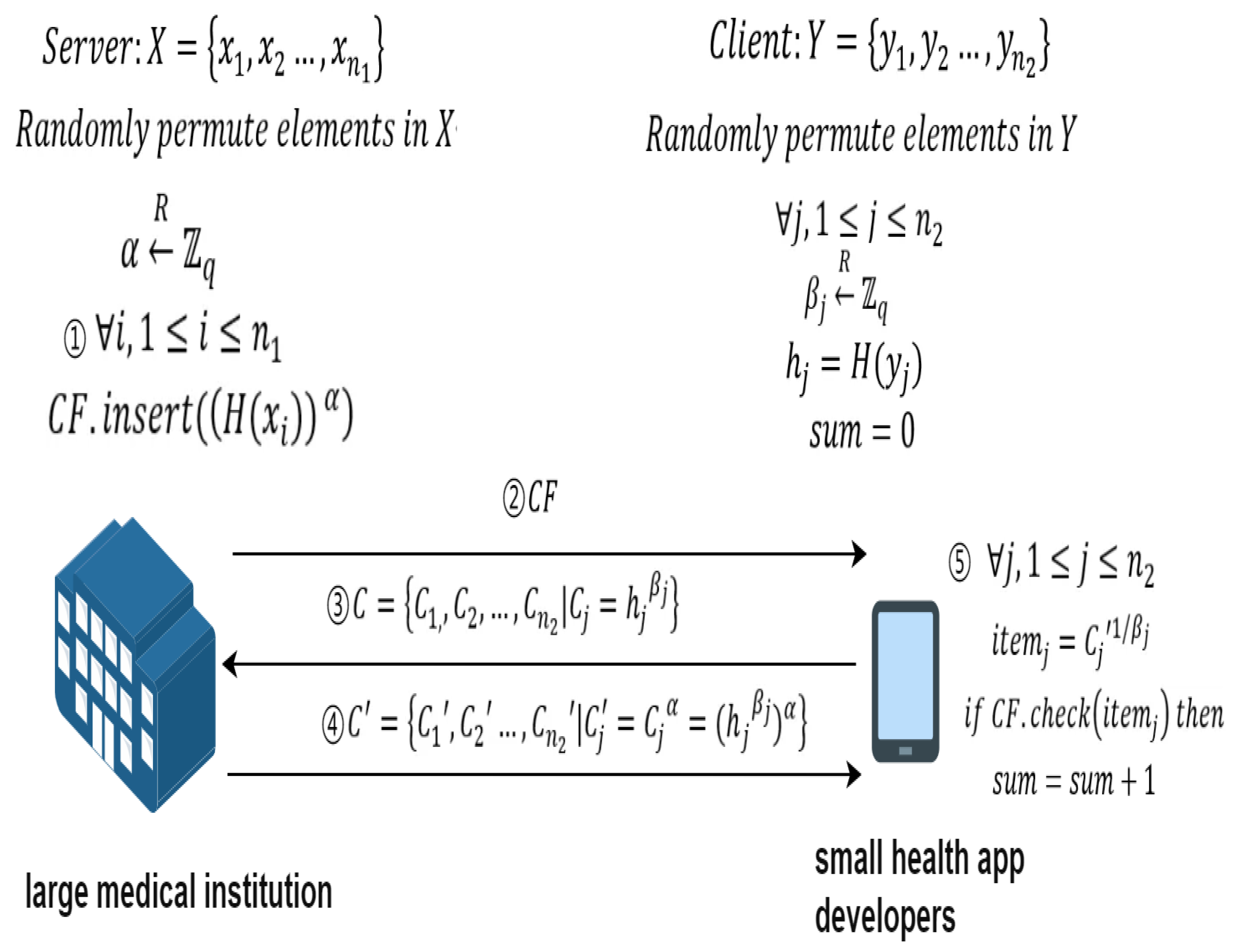
5.1. Definition of Main Participants and Related Symbols
- 1.
- large medical institution represents the party with a larger dataset and greater computational and storage capabilities.
- 2.
- small health app developer represents the party with a smaller dataset and lesser computational and storage capabilities.
- 3.
- X and Y represent the dataset of the large medical institution and the small health app developer respectively.
- 4.
- represents the private key of the large medical institution in the Diffie-Hellman encryption algorithm.
- 5.
- represents the random number generated by the small health app developer for the Diffie-Hellman encryption algorithm.
- 6.
- H represents the hash function negotiated by the small health app developer and large medical institution for use.
- 7.
- represents Cuckoo Filter, represents the operation of adding an element to the Cuckoo filter, represents the operation of checking whether a specific element exists in the filter.
- 8.
- represents the i-th element of set X. Similarly, , , etc., also represent similar meanings.
- 9.
- represents the set containing ciphertexts sent by the small health app developer to the large medical institution.
- 10.
- represents the set containing ciphertexts sent by the large medical institution to the small health app developer.
- 11.
- represents the result obtained through a series of exchange and decryption operations, used to retrieve the filter.
- 12.
- represents the cardinality of the intersection between the two parties.
5.2. Protocol Process
5.2.1. Preprocessing
- 1.
- Security parameter negotiation: The small health app developer and the large medical institution agree on the large prime number q used in the DH encryption algorithm and the hash function H used.
- 2.
- Large Medical Institution Generates Private Key: The large medical institution generates its own private key , used for the Diffie-Hellman (DH) encryption algorithm.
- 3.
- Data Scrambling: The small health app developer and the large medical institution scramble their own datasets Y and X for randomization, enhancing data privacy and security.
- 4.
- Small Health App Developer Data Preprocessing: The small health app developer calculates and generates random numbers , used for the Diffie-Hellman (DH) encryption algorithm.
- 5.
- Creation of Cuckoo Filter: The large medical institution generates a Cuckoo filter by using the operation , and sends the filter to the small health app developer for private set intersection queries with privacy protection.
5.2.2. Cardinality Calculation
- 1.
- Element Blinding and Interactive Encryption Operations: The small health app developer and the large medical institution interact through a series of asymmetric encryption and decryption operations to blind the small health app developer’s elements. Specifically, the small health app developer calculates and sends C to the large medical institution. The large medical institution uses its private key to compute and sends back to the small health app developer.
- 2.
- Cardinality Computation: After receiving , the small health app developer checks whether they belong to the filter through the check operation , thereby calculating the cardinality of the intersection of the sets. Specifically, after receiving sent by the large medical institution, the small health app developer computes and uses the result to query the filter to obtain the intersection’s cardinality .
5.3. Correctness Analysis
5.4. Security Analysis
5.5. Experimental Analysis
5.6. Summary of This Chapter
6. Unbalanced PSI-CA Protocol Based on Single Cloud Assistance
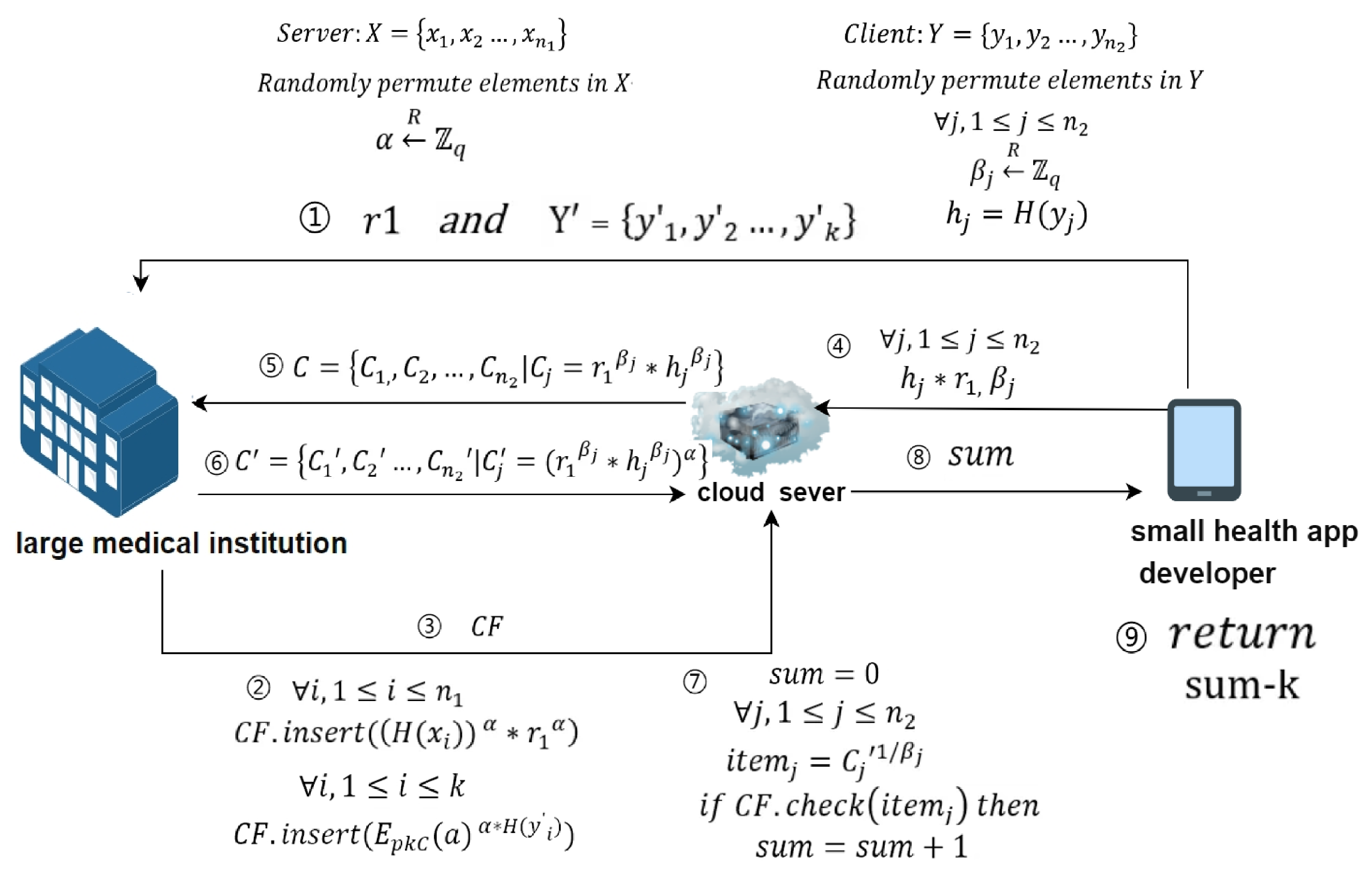
6.1. Definition of Main Participants and Related Symbols
- 1.
- large medical institution represents the party with a larger dataset and greater computational and storage capabilities.
- 2.
- small health app developer represents the party with a smaller dataset and lesser computational and storage capabilities.
- 3.
- cloud server: Represents an auxiliary server that assists the receiver in obtaining intersection’s cardinality operations, undertaking most of the computational and storage pressures.
- 4.
- X and Y represent the dataset of the large medical institution and the small health app developer respectively.
- 5.
- represents the obfuscated dataset sent by the small health app developer to the large medical institution, used to confuse the cloud server and prevent it from obtaining the accurate cardinality of the intersection.k represents the cardinality of the set .
- 6.
- represents the private key of the dlarge medical institution in the Diffie-Hellman encryption algorithm.
- 7.
- represents the random number generated by the small health app developer, used to blind the data.
- 8.
- represents the random number generated by the small health app developer for the Diffie-Hellman encryption algorithm.
- 9.
- H represents the hash function negotiated for use by the small health app developer and large medical institution.
- 10.
- represents the Cuckoo Filter, represents the operation to add an element to the Cuckoo filter, represents the operation to check if a specified element exists in the filter.
- 11.
- represents the i-th element of the set X. Similarly, , , etc., also represent similar meanings.
- 12.
- represents the set of ciphertexts sent by the small health app developer to the large medical institution.
- 13.
- represents the set of ciphertexts sent by the large medical institution to the small health app developer
- 14.
- represents the result obtained through a series of exchange and decryption operations, used to retrieve the filter to obtain the cardinality of intersection.
- 15.
- represents the variable used to help the small health app developer obtain the cardinality of the intersection, where represents the cardinality of the intersection.
6.2. Protocol Process
6.2.1. Preprocessing
- 1.
- Security parameter negotiation: Each role discusses the necessary security parameters, all parties share the large prime q used in the DH cryptographic algorithm. The small health app developer and the large medical institution negotiate to generate and the hash function H.
- 2.
- The small health app developer negotiates with the large medical institution to create an obfuscated dataset : This data set is completely useless data, which means that its elements cannot belong to either the small health app developer or the large medical institution collection..
- 3.
- Large medical institution generates a private key: The large medical institution generates its own private key , for use in the Diffie-Hellman encryption algorithm.
- 4.
- Data scrambling: The small health app developer and the large medical institution each scramble their own datasets X and Y.
- 5.
- Small health app developer data preprocessing: The small health app developer calculates , generates random numbers , and calculates .
6.2.2. Outsourcing
- 1.
- Large medical institution sends data to the cloud server: The large medical institution uses its private key to perform the operation , creates a Cuckoo filter , and sends it to the cloud server.
- 2.
- Small health app developer sends data to the cloud server: The small health app developer sends the random numbers and to the cloud server. After receiving the data sent by the small health app developer, the cloud server calculates . At this point, the cloud server has saved the small health app developer’s blinded data.
6.2.3. Cardinality Calculation
- 1.
- Cloud server sends data: The cloud server sends the blinded data to the large medical institution.
- 2.
- Large medical institution processes data: Upon receiving , the large medical institution uses its private key to calculate , and sends the result back to the cloud server.
- 3.
- Cloud server processes data: After receiving from the large medical institution, the cloud server calculates and uses the result to search . If exists in , then sum is incremented by 1 (initial value of sum is 0).
- 4.
- Obtaining the intersection cardinality: The small health app developer obtains the cardinality of the intersection by calculating , where k is the cardinality of the set .
6.3. Correctness Analysis
6.4. Security Analysis
6.5. Experimental Analysis
6.5.1. Data Storage Volume
6.5.2. Protocol Running Time
6.6. Summary of This Chapter
7. Unbalanced PSI-CA Protocol Based on Dual cloud Assistance
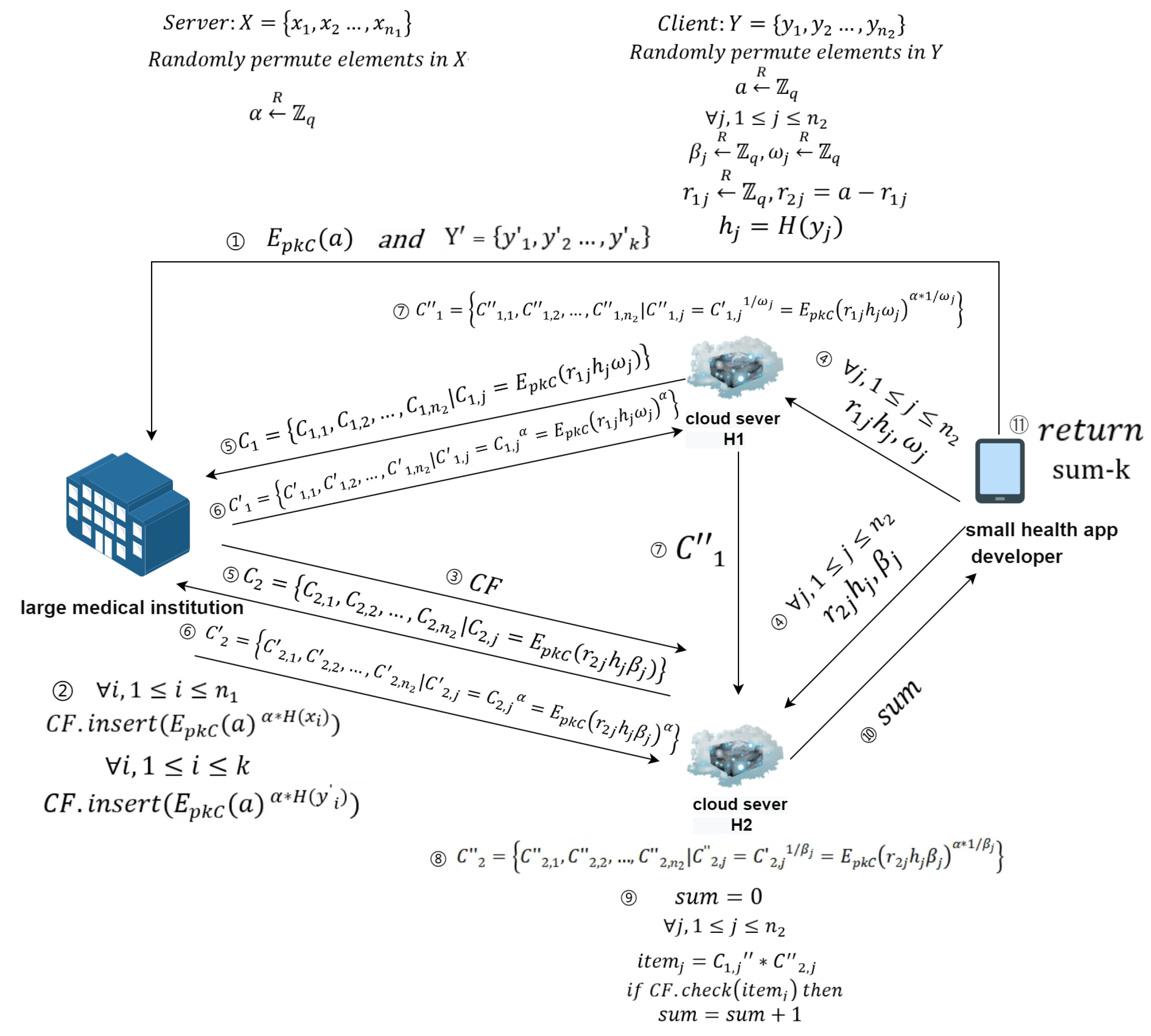
7.1. Definition of Main Participants and Related Symbols
- 1.
- large medical institution represents the party with a larger dataset and greater computational and storage capabilities.
- 2.
- small health app developer represents the party with a smaller dataset and lesser computational and storage capabilities.
- 3.
- cloud server : Acts as an auxiliary server for the small health app developer, handling the majority of computation and storage pressures.
- 4.
- cloud server : Another auxiliary server handling substantial computational and storage demands.
- 5.
- X and Y: Represent the dataset of the large medical institution and the small health app developer, respectively.
- 6.
- represents the obfuscated dataset sent by the small health app developer to the large medical institution, used to confuse the cloud server and prevent it from obtaining the accurate cardinality of the intersection.k represents the cardinality of the set .
- 7.
- : Represents the private key of the large medical institution used in the Diffie-Hellman encryption algorithm.
- 8.
- H: The hash function agreed upon by the small health app developer and the large medical institution for use.
- 9.
- : Represents the Cuckoo Filter, where denotes the operation to add elements, and checks for the presence of specific elements.
- 10.
- : Random exponentials generated by the small health app developer for cloud server , for cloud server .
- 11.
- a: A secret value held by the small health app developer.
- 12.
- : Random numbers used by the small health app developer for sending obfuscated data to cloud server , and for where .
- 13.
- : The ciphertext collection sent from cloud server to the large medical institution, and from ; and are specific elements within these collections.
- 14.
- and : Processed ciphertext collections returned to and from the large medical institution; and are specific elements within these collections.
- 15.
- and : Final processed ciphertext collections at and after receiving data from the large medical institution; and are specific elements within these collections.
- 16.
- : Represents the result of multiplying and used to query the filter.
- 17.
- represents the variable used to help the small health app developer obtain the cardinality of the intersection, where represents the cardinality of the intersection.
7.2. Protocol Process
7.2.1. Preprocessing
- 1.
- Discuss security parameters: Each party discusses the necessary security parameters—the large prime q used in DH encryption and the small health app developer’s public key required for the Paillier encryption system. The small health app developer and the large medical institution negotiate the creation of hash function H.
- 2.
- The small health app developer negotiates with the large medical institution to create an obfuscated dataset : This data set is completely useless data, which means that its elements cannot belong to either the small health app developer or the large medical institution collection.
- 3.
- small health app developer sends : The small health app developer generates its private secret number a and sends to the large medical institution.
- 4.
- large medical institution generates private key: The large medical institution creates its private key , used for the DH encryption algorithm.
- 5.
- Data scrambling: The small health app developer and the large medical institution each shuffle their respective datasets.
- 6.
- small health app developer calculates hashes and generates random numbers: The small health app developer computes and generates random numbers , , , , and computes , where .
7.2.2. Outsourcing
- 1.
- small health app developer sends data to cloud servers: The small health app developer sends , to cloud server , and , to cloud server . computes , and computes . At this point, and hold the small health app developer’s obfuscated data.
- 2.
- large medical institution sends data to cloud servers: Using , the large medical institution performs the filter insertion operation to generate a Cuckoo filter and sends it to cloud server . stores the filter sent by the large medical institution.
7.2.3. Intersection
- 1.
- and send data: and each send their respective collections and to the large medical institution.
- 2.
- large medical institution processes data: Upon receiving the data, the large medical institution uses its private key to compute and sends the results back to . It also processes and sends the results back to .
- 3.
- processes data: After receiving data from the large medical institution, uses the random number to calculate and sends the results to .
- 4.
- processes data: Upon receiving data from and the large medical institution, calculates . checks if exists in . If exists in , then sum is incremented by 1 (initial value of sum is 0).
- 5.
- Obtaining the intersection cardinality: The small health app developer obtains the cardinality of the intersection by calculating , where k is the cardinality of the set .
7.3. Correctness Analysis
7.4. Security Analysis
- 1.
- The small health app developer runs the preprocessing algorithm, sharing the cryptographic hash function H and the large prime q used in the protocol with the adversary.
- 2.
- The small health app developer simulates the outsourcing algorithm and sends their (encrypted) input to the adversary.
- 3.
- The small health app developer and the adversary simulate the intersection algorithm and discard any output.
- 4.
- The adversary is asked to output a guess of the small health app developer’s input y.
- 1.
- In step four of Figure 3, since and are unknown to the adversary, cannot be derived. The adversary can only attempt exhaustive guessing, thus making negligible.
- 2.
- In subsequent steps, as A does not know the small health app developer’s private key for the Paillier encryption system, it is impractical to decrypt the ciphertexts, making it even more challenging to derive . For instance, , and since the private key used in Paillier’s system by the small health app developer is unknown, decrypting this compound is complex and hence remains secure.
7.5. Experimental Analysis
7.5.1. Data Computation Volume
- 1.
- unbalanced PSI-CA protocol based on Cuckoo filter: Two rounds of modular exponentiation operations and filter retrieval.
- 2.
- unbalanced PSI-CA protocol based on single cloud assistance: A single round of multiplication operations .
- 3.
- unbalanced PSI-CA protocol based on dual cloud assistance: Two rounds of multiplication operations .
- 1.
- Modular Exponentiation Operation: Representing computation-intensive operations, modular exponentiation becomes particularly time-consuming. On a standard hardware setup, the time required for a single modular exponentiation operation depends primarily on the size of the numbers involved and the efficiency of the algorithm.
- 2.
- Multiplication Operation: Compared to modular exponentiation, multiplication operations execute much faster on modern computing systems, even when involving large numbers. Therefore, whether it’s a single round of multiplication in the single-cloud protocol or two rounds in the dual-cloud protocol, the processing times are relatively short.
- 3.
- Cuckoo Filter Retrieval: Although relatively quick, the retrieval operation for a Cuckoo filter involves memory access, which may make it slightly slower than simple arithmetic operations. The exact time required for this operation depends on the size of the filter and the efficiency of the implementation.
- 1.
- Unbalanced PSI-CA Protocol Based On Cuckoo Filter: Primarily relies on two rounds of modular exponentiation and, which are computation-intensive, especially when dealing with large numbers, making it the most time-consuming of all the operations reviewed.Additionally, the filter retrieval operation is also involved.
- 2.
- Unbalanced PSI-CA Protocol Based On Single Cloud Assistance: By executing a single round of multiplication, it significantly alleviates the computational burden on the small health app developer. Multiplication operations, even for large numbers, can be done quickly.
- 3.
- Unbalanced PSI-CA Protocol Based On Dual cloud Assistance: Includes two rounds of multiplication operations, also aiming to distribute the computational pressure on the small health app developer. Although it involves two rounds of multiplication, due to the inherent efficiency of the operation, the total processing time remains within an acceptable range.
7.5.2. Protocol Running Time
7.6. Summary of This Chapter
7.7. Extensions
7.7.1. PSI-CA Network
- Access and Authentication of Cloud Servers: Any server can apply to become a cloud server, also known as a server assistant. These servers must undergo a series of certification processes (including hardware performance verification, security vulnerability scanning, and compliance checks) to ensure they meet security and performance standards. Servers that pass the certification but later violate regulations will be blacklisted and removed. The system maintains platform security and trust through mechanisms such as regular security scans and real-time monitoring, with any violations leading to immediate removal and further investigation of the server.
- Mechanism for Selecting Server Assistants: When needing to perform PSI-CA, small health app developers choose two cloud servers based on their performance (such as processing power, storage capacity, and network bandwidth), stability, security capabilities, and compliance with regulations, among other hard and soft factors. Cloud servers with high availability promises are preferred to minimize the risk of failures.
- Execution Mechanism for PSI-CA Operations: The PSI-CA network supports small health app developer flexibility and system scalability; small health app developers can execute PSI-CA on different large medical institutions by merely changing and obfuscated dataset , without needing to redesign the entire system. This design enhances small health app developer flexibility and the system’s efficiency, reliability, and security.
7.7.2. Data Updates
-
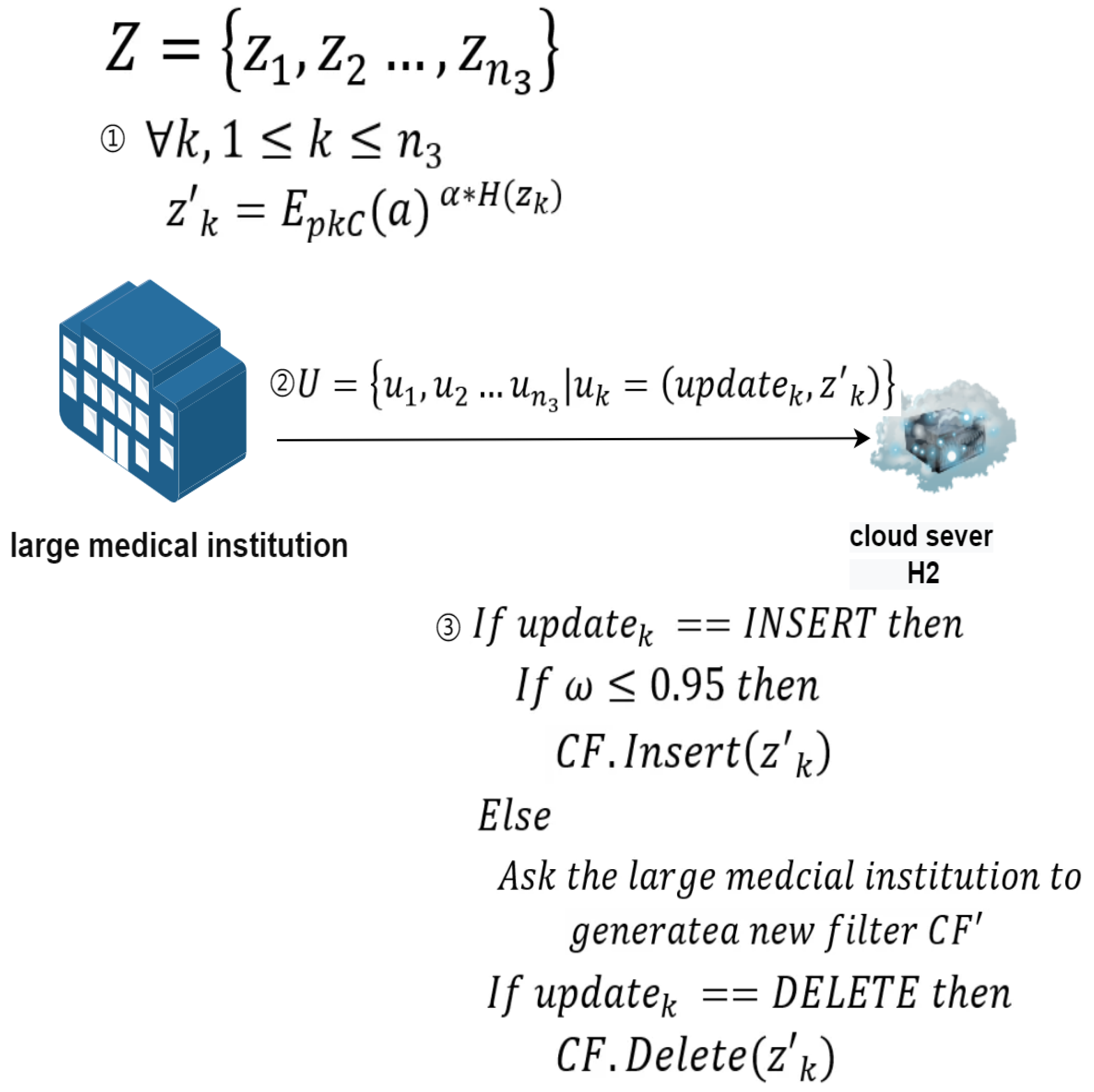
Data Updates on the Large Medical Institution’s Side:As shown in Figure 4, the update details of the large medical institution are as follows:Definition of main participants and related symbols:
- 1.
- Large medical institution: Represents the large medical institution that wants to encrypt and upload updated data to cloud server .
- 2.
- Cloud server : Represents the cloud-assisted server that assists the large medical institution in completing update operations.
- 3.
- Z represents the set of data to be updated, represents the k-th element of Z.
- 4.
- represents the load factor of the filter.
- 5.
- represents the data after encryption processing.
- 6.
- represents the operation index, used to determine whether the update operation is an insertion or deletion.
- 7.
- U represents the set of data sent by the large medical institution to the cloud-assisted server , represents the k-th element of U.
Update process:- 1.
- The large medical institution has a set of elements Z it wants to insert or delete. These elements are blinded before being sent to cloud server . Specifically, .
- 2.
- In addition to sending the blinded elements, the large medical institution also sends an identifier variable to inform the small health app developer whether the operation is an insertion or a deletion.
- 3.
- During an insertion operation, first checks whether the current filter’s load factor exceeds 0.95.
- 4.
- If the load factor is greater than 0.95, then must request the large medical institution to generate a new filter using all elements to maintain high spatial and lookup efficiency of the filter.
- 5.
- If the load factor is less than or equal to 0.95, then can directly insert the element into the current filter .
- 6.
- In a deletion operation, removes the specified element from the filter , a process that does not require generating a new filter.
-
Data Updates on the Small Health App Developer’s Side:As shown in Figure 5, the update details of the small health app developer are as follows:Definition of main participants and related symbols:
- 1.
- Small health app developer: Represents the small health app developer who wants to perform data updates.
- 2.
- Cloud server : Represents the cloud-assisted server that assists the small health app developer in completing update operations.
- 3.
- Cloud server Represents the cloud-assisted server that assists the small health app developer in completing update operations.
- 4.
- Z represents the set of data to be updated, represents the k-th element of Z.
- 5.
- represents the data after being processed by the hash function H.
- 6.
- k represents the data index, used to determine the type of update, either insertion or deletion, and to retrieve the updated data based on the index.
- 7.
- When adding data, represents the data processed through the dual-cloud scheme and sent to the two cloud-assisted servers. When deleting, is null.
- 8.
- V represents the set of data sent by the small health app developer to the cloud-assisted server , represents the k-th element of V.
- 9.
- represents the set of data sent by the small health app developer to the cloud-assisted server , represents the k-th element of .
Update process:- 1.
- The small health app developer has a set of elements Z it wants to insert or delete. In both cases, the small health app developer blinds each element and sends them to and respectively.
- 2.
- The small health app developer sends a data index K to inform the cloud servers about the type of update, whether it is an insertion or a deletion. If the index is less than , it indicates a deletion operation. In this case, is null, and and delete the corresponding data based on the index.
- 3.
- If the index is greater than , it indicates an addition operation, and the corresponding calculation results and index are saved.
- 4.
- After completing a batch of deletion and addition operations, the relative order of the indices also needs to be adjusted. The update process is illustrated in Figure 5.
8. Conclusions and Future Work
8.1. Work Summary
- 1.
- Addressing the shortcomings of traditional PSI-CA protocols when dealing with significant data size disparities among participants, this paper proposes the first protocol, namely the unbalanced PSI-CA protocol based on Cuckoo filter.
- 2.
- Given the complexities of cryptographic operations and storage demands of the small health app developer in the unbalanced PSI-CA protocol based on Cuckoo filter, this paper introduces a unbalanced PSI-CA protocol based on single cloud assistance. This protocol effectively transfers the majority of computational and storage burdens from the small health app developer to the cloud.
- 3.
- In response to potential collusion between the cloud and large medical institution in the unbalanced PSI-CA protocol based on single cloud assistance, this paper proposes a unbalanced PSI-CA protocol based on dual cloud assistance with security mechanisms like homomorphic encryption, which effectively prevents collusion attacks while offloading computational and storage burdens.
- 4.
- In view of the practical problems of the unbalanced PSI-CA protocol based on dual cloud assistance, this paper also designs a PSI-CA network and a data update mode tailored for the unbalanced PSI-CA protocol based on dual cloud assistance.
8.2. Protocol Summary
8.3. Future Outlook
- 1.
- All protocols are designed for two-party unbalanced PSI-CA. Extending these protocols to multi-party scenarios is an important future direction, given the practical needs for multi-party computations.
- 2.
- The protocols are developed under a semi-honest security model. Extending their robustness to malicious models, where adversaries may actively attempt to undermine the protocols, represents a crucial area for further research.
- 3.
- The current protocols are focused exclusively on PSI-CA. In practical applications, there may be a need to carry out other types of computations, such as PSI-SUM, etc. Expanding the protocols to support a variety of computational types is another significant direction for future work.
References
- Bald, P.; Baronio, R.; Cristofaro, E.; Gasti, P.; Tsudik, G. Efficient and secure testing of fully-sequenced human genomes. Biological Sciences Initiative 2000, 470, 7–10. [Google Scholar]
- Chen, H.; Laine, K.; Rindal, P. Fast private set intersection from homomorphic encryption. In Proceedings of the Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security; 2017; pp. 1243–1255. [Google Scholar]
- Nagaraja, S.; Mittal, P.; Hong, C.Y.; Caesar, M.; Borisov, N. {BotGrep}: Finding {P2P} Bots with Structured Graph Analysis. In Proceedings of the 19th USENIX Security Symposium (USENIX Security 10); 2010. [Google Scholar]
- Li, W.; Liu, J.; Zhang, L.; Wang, Q.; He, C. A Survey on Set Intersection Computation for Privacy Protection. Journal of Computer Research and Development 2022, 59, 1782–1799. [Google Scholar]
- Meadows, C. A More Efficient Cryptographic Matchmaking Protocol for Use in the Absence of a Continuously Available Third Party. In Proceedings of the Proc. of the 7th IEEE Symposium on Security and Privacy, Los Alamitos, CA; 1986; pp. 134–134. [Google Scholar]
- Huberman, B.; Franklin, M.; Hogg, T. Enhancing Privacy and Trust in Electronic Communities. In Proceedings of the Proc. of the 1st ACM Conference on Electronic Commerce, New York; 1999; pp. 78–86. [Google Scholar]
- DeCristofaro, E.; Tsudik, G. Experimenting with Fast Private Set Intersection. In Proceedings of the Proc. of Int. Conf. on Trust and Trustworthy Computing, Berlin; 2012; pp. 55–73. [Google Scholar]
- Pinkas, B.; Schneider, T.; Zohner, M. Faster Private Set Intersection Based on OT Extension. In Proceedings of the Proc. of the 23rd USENIX Security Symposium, Berkeley, CA; 2014; pp. 797–812. [Google Scholar]
- Freedman, M.; Nissim, K.; Pinkas, B. Efficient Private Matching and Set Intersection. In Proceedings of the Proc. of the 23rd Int. Conf. on the Theory and Applications of Cryptographic Techniques, Accessed: 2020-10-16. Berlin, 2004. [Google Scholar]
- Freedman, M.J.; Hazay, C.; Nissim, K.; et al. Efficient Set Intersection with Simulation-Based Security. Journal of Cryptology 2016, 29, 115–155. [Google Scholar] [CrossRef]
- Abadi, A.; Terzis, S.; Dong, C. O-PSI: Delegated Private Set Intersection on Outsourced Datasets. In Proceedings of the Proc of the 27th IFIP International Information Security and Privacy Conference, Berlin; 2015; pp. 3–17. [Google Scholar]
- Kissner, L.; Song, D. Privacy-Preserving Set Operations. In Proceedings of the Proc of the 25th Annual International Cryptology Conference, Berlin; 2005; pp. 241–257. [Google Scholar]
- Jarecki, S.; Liu, X. Efficient Oblivious Pseudorandom Function with Applications to Adaptive OT and Secure Computation of Set Intersection. In Proceedings of the LNCS 5444: Proc of the 6th Theory of Cryptography Conference, Berlin; 2009; pp. 577–594. [Google Scholar]
- Hazay, C.; Venkitasubramaniam, M. Scalable Multi-party Private Set-Intersection. In Proceedings of the Proc of the 20th IACR International Workshop on Public Key Cryptography, Berlin; 2017; pp. 175–203. [Google Scholar]
- Dou, J.; Liu, X.; Wang, W.; et al. Efficient and Secure Calculation of Two-Party Sets in the Field of Rational Numbers. Chinese Journal of Computers 2020, 43, 1397–1413. [Google Scholar]
- Damgård, I.; Pastro, V.; Smart, N.; et al. Multiparty Computation from Somewhat Homomorphic Encryption. In Proceedings of the 32nd Annual Cryptology Conference; Berlin, 2012; Name, E., Ed.; Lecture Notes in Computer Science; pp. 643–662.
- Yao, A.C. Protocols for Secure Computations. In Proceedings of the Proc of the 23rd Annual Symposium on Foundations of Computer Science (SFCS 1982), Piscataway, NJ; 1982; pp. 160–164. [Google Scholar]
- Micali, S.; Goldreich, O.; Wigderson, A. How to Play Any Mental Game. In Proceedings of the Proc of the 19th ACM Symposium on Theory of Computing, New York; 1987; pp. 218–229. [Google Scholar]
- Pinkas, B.; Schneider, T.; Segev, G.; et al. Phasing: Privateset intersectionusing permutation-basedhashing. In Proceedings of the Proceedings of the 24th USENIX Security Symposium, USENIX Association, Berkeley, CA; 2015; pp. 515–530. [Google Scholar]
- Pinkas, B.; Schneider, T.; Weinert, C.; et al. Efficient circuit-based PSI via cuckoo hashing. In Proceedings of the 38th Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin, 2018; pp. 125–157. [Google Scholar]
- Pinkas, B.; Schneider, T.; Tkachenko, O.; et al. Efficient circuit-based PSI with linear communication. In Proceedings of the 39th Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin, 2019; pp. 122–153. [Google Scholar]
- Huang, Y.; Evans, D.; Katz, J. Private Set Intersection: Are Garbled Circuits Better Than Custom Protocols? In Proceedings of the 19th Network and Distributed System Security Symposium, Accessed: 2020-10-21. Reston, VA, 2012. [Google Scholar]
- Naor, M.; Pinkas, B. Efficient oblivious transfer protocols. In Proceedings of the SODA, Vol. 1; 2001; pp. 448–457. [Google Scholar]
- Dong, C.; Chen, L.; Wen, Z. When private set intersection meets big data: an efficient and scalable protocol. In Proceedings of the Proceedings of the 2013 ACM SIGSAC conference on Computer & communications security; 2013; pp. 789–800. [Google Scholar]
- Rindal, P.; Rosulek, M. Improved private set intersection against malicious adversaries. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques. Springer International Publishing; Springer International Publishing, 2017; pp. 235–259. [Google Scholar]
- Zhang, E.; Liu, F.H.; Lai, Q.; et al. Efficient multi-party private set intersection against malicious adversaries. In Proceedings of the Proceedings of the 2019 ACM SIGSAC conference on cloud computing security workshop; 2019; pp. 93–104. [Google Scholar]
- Pinkas, B.; Rosulek, M.; Trieu, N.; et al. PSIfrom PaXoS: Fast, malicious private set intersection. In Proceedings of the Proceedings of the 39th Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer, 2020; pp. 739–767. [Google Scholar]
- Orrù, M.; Orsini, E.; Scholl, P. Actively secure 1-out-of-n OT extension with application to private set intersection. In Proceedings of the Proceedings of Cryptographers’ Track at the RSA Conference; Springer, 2017; pp. 381–396. [Google Scholar]
- Rindal, P.; Schoppmann, P. VOLE-PSI: Fast OPRF and circuit-PSI from vector-OLE. IACR Cryptology ePrint Archive, 2021. https://eprint.iacr.org/2021/266.
- Schoppmann, P.; Gascón, A.; Reichert, L.; et al. Distributed vector-OLE: Improved constructions and implementation. In Proceedings of the Proceedings of the 26th ACM SIGSAC Conference on Computer and Communications Security; ACM, 2019; pp. 1055–1072. [Google Scholar]
- Weng, C.; Yang, K.; Katz, J.; et al. Wolverine: Fast, scalable, and communication-efficient zero-knowledge proofs for Boolean and arithmetic circuits. Cryptology ePrint Archive, 2020. https://eprint.iacr.org/2020/925.
- Egert, R.; Fischlin, M.; Gens, D.; Jacob, S.; Senker, M.; Tillmanns, J. Privately Computing Set-Union and Set-Intersection Cardinality via Bloom Filters. European Journal of Operational Research 2015, 139, 371–389. [Google Scholar]
- Ashok, V.; Mukkamala, R. A Scalable and Efficient Privacy Preserving Global Itemset Support Approximation Using Bloom Filters. In Proceedings of the IFIP Conference on Data and Applications Security and Privacy; 2014; pp. 382–389. [Google Scholar]
- Debnath, S.; Dutta, R. Secure and Efficient Private Set Intersection Cardinality Using Bloom Filter. In Proceedings of the International Information Security Conference; 2015; pp. 209–226. [Google Scholar]
- De Cristofaro, E.; Gasti, P.; Tsudik, G. Fast and Private Computation of Cardinality of Set Intersection and Union. In Proceedings of the CANS 2012; Springer, 2012; pp. 218–231. [Google Scholar]
- Jarecki, S.; Liu, X. Fast Secure Computation of Set Intersection. In Proceedings of the SCN 2010, Vol. 6280; Springer, 2010; pp. 418–435. [Google Scholar]
- Su, G.; Xu, M. A Survey on Secure Multi-party Computation Technology and Applications. Information Communication Technologies and Policy 2019, 19–22. [Google Scholar]
- Li, A. Research on Multi-party Statistical Computations Based on Functional Encryption. PhD thesis, Wuhan University of Technology, Wuhan, 2017. [Google Scholar]
- Wang, H.; Dai, H.; Chen, S.; Chen, Z.; Chen, G. A Survey of Filter Data Structures. Computer Science 2024, 51, 35–40. [Google Scholar]
- Yu, M.; Fabrikant, A.; Rexford, J. BUFFALO: Bloom filter forwarding architecture for large organizations. In Proceedings of International Conference on Emerging Networking Experiments and Technologies; 2009; pp. 313–324. [Google Scholar]
- Li, P.; Luo, B.; Zhu, W.; et al. Cluster-based distributed dynamic cuckoo filter system for Redis. International Journal of Parallel, Emergent and Distributed Systems 2020, 35, 340–353. [Google Scholar] [CrossRef]
- Wang, F.; Chen, H.; Liao, L.; et al. The power of better choice: Reducing relocations in cuckoo filter. In Proceedings of the International Conference on Distributed Computing Systems; 2019; pp. 358–367. [Google Scholar]
- Gur, L.; Lis, D.; Dai, H.; et al. Adaptive online cache capacity optimization via lightweight working set size estimation at scale. In Proceedings of the USENIX Annual Technical Conference; 2023; pp. 467–484. [Google Scholar]
- Reviriego, P.; Martínez, J.; Larrabeiti, D.; et al. Cuckoo Filters and Bloom Filters: Comparison and Application to Packet Classification. IEEE Transactions on Network and Service Management 2020, 17, 2690–2701. [Google Scholar] [CrossRef]

| Cardinality of Dataset from Participant One |
Cardinality of Dataset from Participant Two |
Protocol Runtime (seconds) |
| 1.8095 | ||
| 7.3003 | ||
| 56.1277 | ||
| 1859.9520 | ||
| 5.2207 | ||
| 10.0672 | ||
| 63.4835 | ||
| 1886.3966 | ||
| 20.7044 | ||
| 71.9252 | ||
| 1977.5657 | ||
| 170.3074 | ||
| 2054.2694 |
| Cardinality of Dataset from Participant One |
Cardinality of Dataset from Participant Two |
Original Protocol Runtime (seconds) |
New Protocol Runtime (seconds) |
| 1.8095 | 0.1685 | ||
| 7.3003 | 0.1663 | ||
| 56.1277 | 0.1641 | ||
| 1859.9520 | 0.1840 | ||
| 5.2207 | 5.2725 | ||
| 10.0672 | 5.5104 | ||
| 63.4835 | 5.2807 | ||
| 1886.3966 | 5.5166 | ||
| 20.7044 | 21.1474 | ||
| 71.9252 | 21.2865 | ||
| 1977.5657 | 21.9713 | ||
| 170.3074 | 171.5354 | ||
| 2054.2694 | 186.9644 |
| Data Set Count | Size of Cuckoo Filter (MB) |
| 0.535 | |
| 2.363 | |
| 21.678 | |
| 93.645 | |
| 194.436 | |
| 403.201 | |
| 3571.206 | |
| 7372.835 | |
| 15206.421 |
| Small Health App Developer Dataset Size | Large Medical Institution Dataset Size | Protocol 1 Running Time (seconds) | Protocol 2 Running Time (seconds) |
| 0.1685 | 0.1658 | ||
| 0.1663 | 0.1693 | ||
| 0.1641 | 0.1658 | ||
| 0.1840 | 0.1731 | ||
| 5.2725 | 4.0627 | ||
| 5.5104 | 4.2464 | ||
| 5.2807 | 4.3202 | ||
| 5.5166 | 4.6118 | ||
| 21.1474 | 17.056 | ||
| 21.2865 | 16.731 | ||
| 21.9713 | 18.5417 | ||
| 171.5354 | 130.0498 | ||
| 186.9644 | 140.0193 |
| Data Volume | Protocol I Running Time (s) |
Protocol II Running Time (s) |
Protocol III Running Time (s) |
| 0.1539 | 0.1543 | 0.1612 | |
| 0.1569 | 0.1573 | 0.1742 | |
| 0.1616 | 0.1611 | 0.1736 | |
| 0.1693 | 0.1683 | 0.1868 | |
| 4.9239 | 3.8223 | 4.3904 | |
| 5.0232 | 3.9145 | 4.9128 | |
| 5.1709 | 4.0267 | 4.6099 | |
| 5.4172 | 4.2233 | 4.8281 | |
| 20.0930 | 15.6768 | 18.2058 | |
| 20.6841 | 16.1281 | 20.2155 | |
| 21.6690 | 16.8939 | 20.0528 | |
| 165.4731 | 129.0516 | 148.7145 | |
| 173.3531 | 135.2534 | 165.9464 |
| Protocol | Security | Client Storage & Computational Burden | Runtime |
|---|---|---|---|
| Unbalanced PSI-CA Protocol based on Cuckoo Filter | High Security (No collusion attacks) | Requires storing Cuckoo filter and intensive computation | Longest |
| Unbalanced PSI-CA Protocol based on Single Cloud Assistance | Security Risks (Cannot resist collusion attacks) | Shifted to cloud server | Fastest |
| Unbalanced PSI-CA Protocol based on Dual Cloud Assistance | High Security (Can resist collusion attacks) | Shifted to cloud server | Moderate |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




