Submitted:
30 January 2024
Posted:
31 January 2024
You are already at the latest version
Abstract
Keywords:
0.Introduction
1. Related work
1.1. Our contribution
- Search results validation: The scheme allows the signature to be attached to each file to verify the accuracy of the search results.
- No bilinear pairing: The calculation of bilinear pairing needs more time, and the scheme’s efficiency will significantly improve without bilinear pairing.
- We prove that the new scheme can resist offline keyword guessing attacks, file injection attacks, and choose keyword attacks (CKA) under the standard model.
1.2. Organization
2. Preliminaries
- Elliptic curve discrete logarithm problem (ECDLP): given , where P is the generator of the group, and Q is the element in . It is difficult to calculate the integer k such that , where .
- Elliptic curve Computational Diffie-Hellman problem (ECDCHP): for any given in , it is difficult to calculate , where .
- Elliptic curve Decisional Diffie-Hellman problem (ECDDDH): Given where unknown. The DDH (Decisional Diffie-Hellman) problem is to decide whether X equals or a random element in G.
3. The System Model and Attack Model of CLVPFCKS
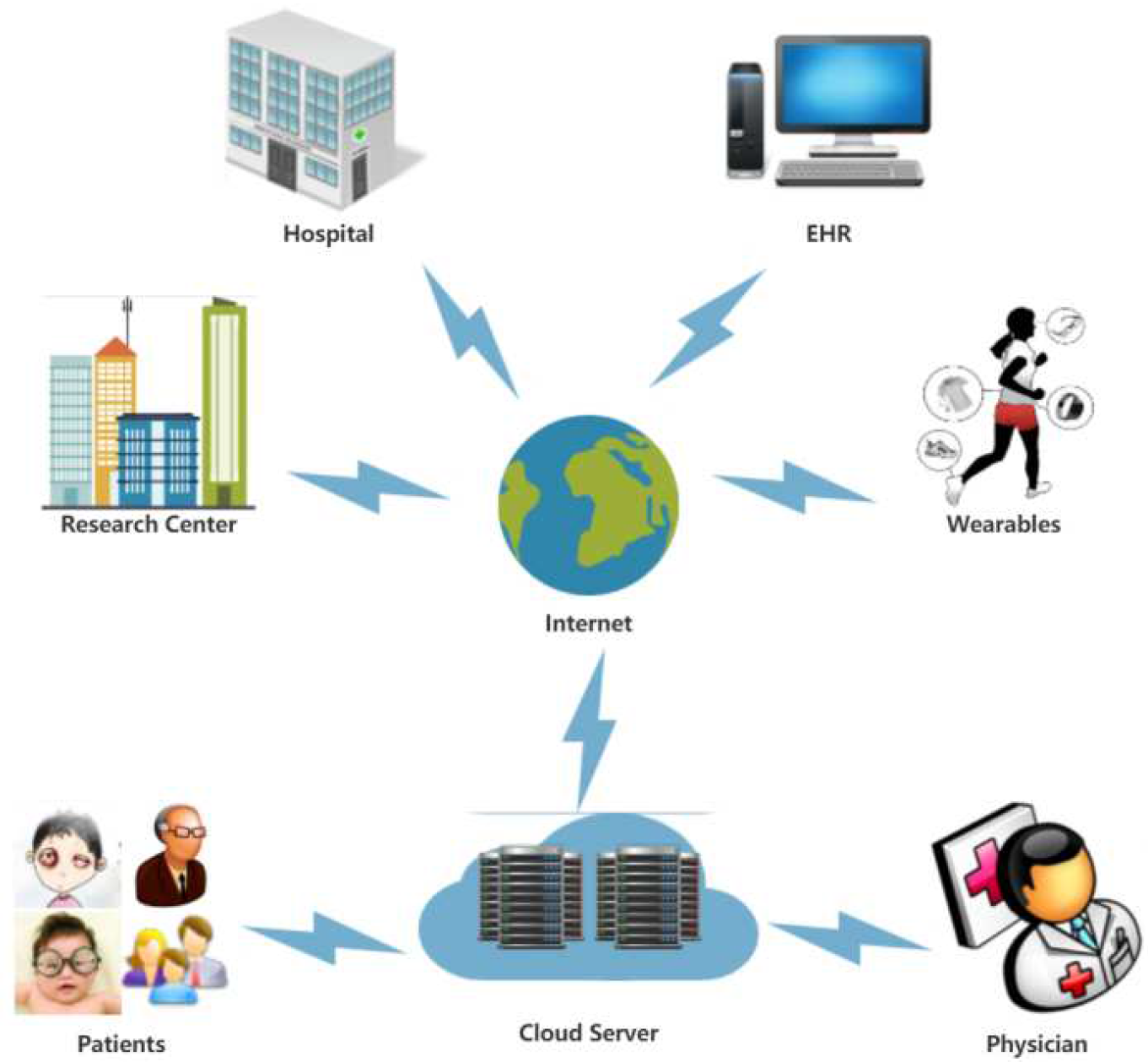
3.1. System model
3.2. Design Goals
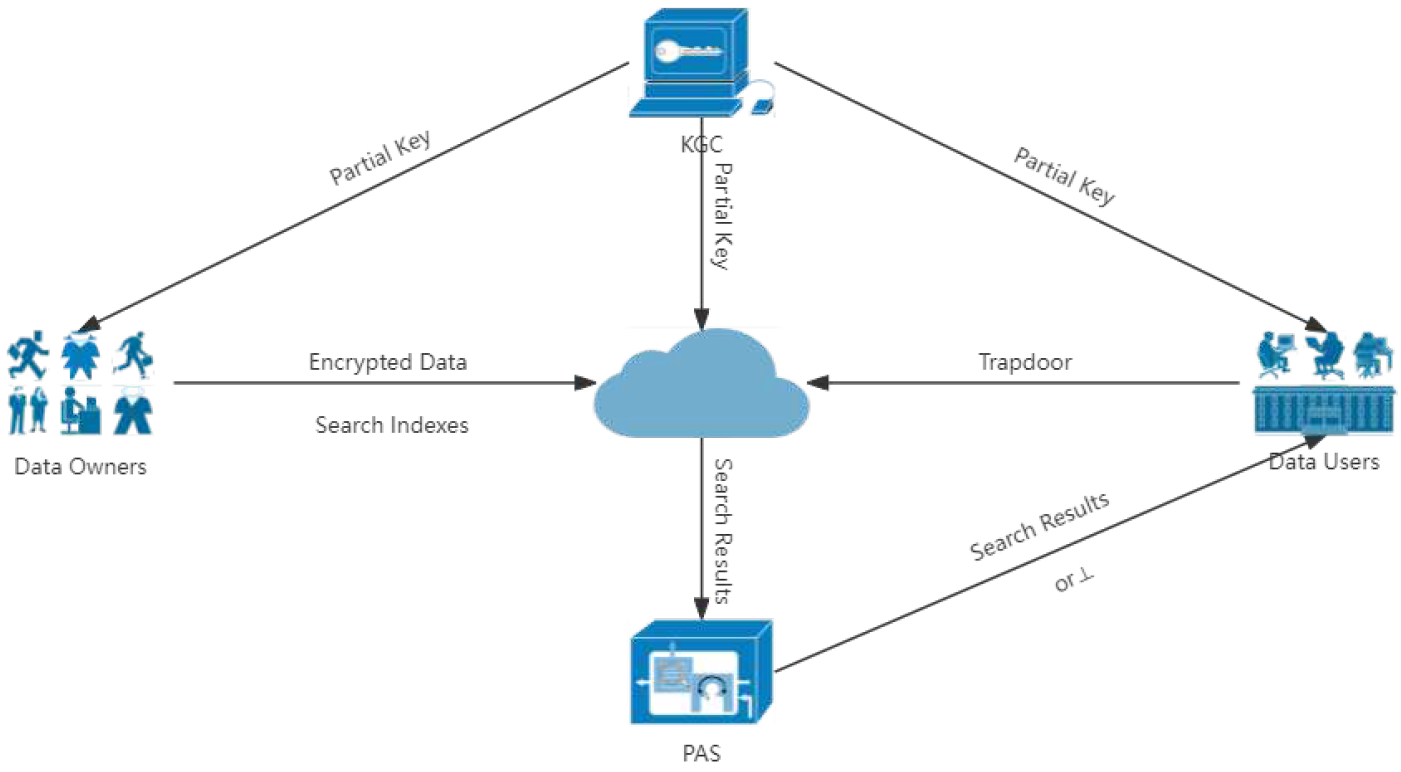
3.3. Solution Framework
3.4. Security Model
4. the proposed CLVPFCKS
| Notations | DESCRIPTIONS |
| x | Master key |
| system public key | |
| Data Owner Collection | |
| identity set for data owner | |
| identity set for CSP | |
| identity set for data user | |
| Public/secret key pair for CSP | |
| Public/secret key pair for data owner | |
| Public/secret key pair for data user | |
| File set F | |
| ciphertext set | |
| identity set for F | |
| Collection of keywords | |
| Data owner signature for | |
| Data owners’ multi-signatures for | |
| F’s multi-signature | |
| Index of | |
| Index set for F | |
| Search keyword set | |
| The trapdoor of | |
| Search results | |
| Identity set for |
4.1. Specific construction of CLVPFCKS
- , and the index set is , where . Finally send I to CSP.
5. Security of scheme
5.1. Correctness
- If , then
5.2. Security
6. Performance analysis
| scheme | CKCA-CIND | IND-KGA | insider-KGA | FIA | SCF | VER |
| VCKSM[18] | No proof | yes | no | no | yes | yes |
| VMKS[46] | yes | yes | No proof | No proof | yes | yes |
| VMKDO[33] | yes | yes | no | no | yes | yes |
| VCSE[46] | yes | No proof | no | no | yes | yes |
| CLPAEKS[12] | No proof | No proof | yes | yes | yes | No proof |
| CL-dPAEKS[11] | No proof | No proof | yes | yes | yes | No proof |
| our | yes | yes | yes | yes | yes | yes |
| symbols | Definition |
| Running time required for a bilinear pairing operation, | |
| Running time required for a hash-to-operation, | |
| Running time required for a scalar multiplication operation in | |
| Running time required for an exponentiation operation in | |
| Running time required for a scalar multiplication operation in | |
| u | Number of data users |
| d | Number of data owners |
| m | Number of keywords in ciphertext |
| n | Number of ciphertext |
| s | Number of search keywords |
| scheme | keyGen | Enc | Trap | search | verify |
| VCKSM[18] | [2nd + n(m + 2)] | ||||
| VMKS[46] | |||||
| our |
| scheme | keyGen(ms) | Enc(ms) | Trap(ms) | search(ms) | verify(ms) | Total |
| VCKSM[18] | 2024.155 | 4151817 | 1380.715 | 3305426.428 | 3098.481 | 7463746.779 |
| VMKS[46] | 8043 | 1382126 | 737.275 | 130.852 | 2474.349 | 1393511.476 |
| our | 683.675 | 680340 | 353.51 | 336838.335 | 6.67 | 1018222.19 |
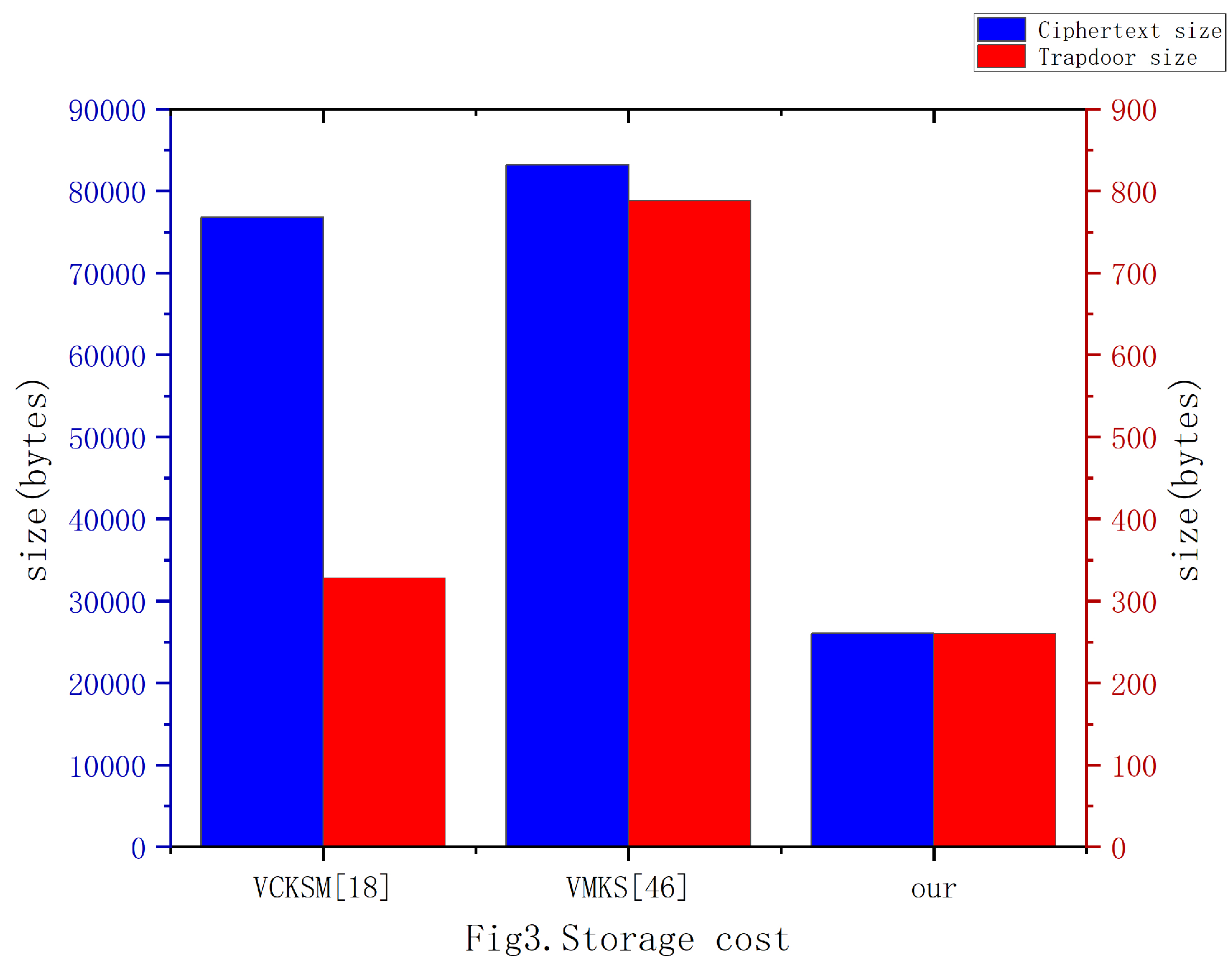
| scheme | Ciphertext size(bytes) | Trapdoor size(bytes) |
| VCKSM[18] | ||
| VMKS[46] | ||
| our |
7. Conclusion
References
- L. AtzoriA. Iera and G. Morabito, "The Internet of Things: A survey," Comput. Netw., vol. 54, no. 15, pp. 2787-2805, 2010. [CrossRef]
- A. Zanella, N. Bui, A. Castellani, L. Vangelista and M. Zorzi, "Internet of Things for Smart Cities," Ieee Internet of Things Journal, vol. 1, no. 1, pp. 22-32, 2014. [CrossRef]
- P. Bellavista, G. Cardone, A. Corradi and L. Foschini, "Convergence of MANET and WSN in IoT Urban Scenarios," Ieee Sens. J., vol. 13, no. 10, pp. 3558-3567, 2013. [CrossRef]
- V. Jagadeeswari, V. Subramaniyaswamy, R. Logesh and V. Vijayakumar, "A study on medical Internet of Things and Big Data in personalized healthcare system," Health Information Science and Systems, vol. 6, no. 1, 2018. [CrossRef]
- D.J. He, R. Ye, S. Chan, M. Guizani and Y.P. Xu, "Privacy in the Internet of Things for Smart Healthcare," Ieee Commun. Mag., vol. 56, no. 4, pp. 38-44, 2018. [CrossRef]
- Y.Y. ChenJ.C. Lu and J.K. Jan, "A Secure EHR System Based on Hybrid Clouds," J. Med. Syst., vol. 36, no. 5, pp. 3375-3384, 2012. [CrossRef]
- D.X. SongD. Wagner and A. Perrig, Practical Techniques for Searches on Encrypted Data, Proc. IEEE Symposium on Security & Privacy, 2002, pp. 44-55.
- D. Boneh, G.D. Crescenzo, R. Ostrovsky and G. Persiano, "Public Key Encryption with Keyword Search," Eurocrypt 2004, pp. 506-522, 2004. [CrossRef]
- J. BaekR. Safiavinaini and W. Susilo, Public Key Encryption with Keyword Search Revisited, Proc. International Conference on Computational Science and Its Applications (ICCSA 2008), 2008, pp. 1249-1259. [CrossRef]
- H.S. Rhee, J.H. Park, W. Susilo and D.H. Lee, Improved searchable public key encryption with designated tester, Proc. International Symposium on Information, 2009, pp. 376. [CrossRef]
- L. Wu, Y. Zhang, M. Ma, N. Kumar and D. He, "Certificateless searchable public key authenticated encryption with designated tester for cloud-assisted medical Internet of Things," Ann. Telecommun., vol. 74, no. 7-8, pp. 423-434, 2019. [CrossRef]
- D. He, M. Ma, S. Zeadall, N. Kumar and K. Liang, "Certificateless Public Key Authenticated Encryption with Keyword Search for Industrial Internet of Things," Ieee T. Ind. Inform., pp. 1, 2017. [CrossRef]
- M.M. A, D.H.B. C, M.K.K. D and J.C. A, "Certificateless searchable public key encryption scheme for mobile healthcare system," Comput. Electr. Eng., vol. 65, pp. 413-424, 2018. [CrossRef]
- M. Ma, D. He, S. Fan and D. Feng, "Certificateless searchable public key encryption scheme secure against keyword guessing attacks for smart healthcare," Journal of Information Security and Applications, vol. 50, 2020. [CrossRef]
- Y. Lu and J. Li, "Constructing pairing-free certificateless public key encryption with keyword search," Frontiers of Information Technology & Electronic Engineering, vol. 20, no. 8, pp. 1049-1060, 2019. [CrossRef]
- P. GolleJ. Stadon and B. Waters, Secure conjunctive keyword search over encrypted data,3089, M. Jakobsson, et al., eds., 2004, pp. 31-45. [CrossRef]
- Y.H. Hwang and P.J. Lee, Public key encryption with conjunctive keyword search and its extension to a multi-user system, Book Public key encryption with conjunctive keyword search and its extension to a multi-user system, Series Public key encryption with conjunctive keyword search and its extension to a multi-user system 4575,ed., Editor ed., 2007, pp. 2. [CrossRef]
- Y.B. Miao, et al., "VCKSM: Verifiable conjunctive keyword search over mobile e-health cloud in shared multi-owner settings," Pervasive Mob. Comput., vol. 40, pp. 205-219, 2017. [CrossRef]
- Y. Yang and M.D. Ma, "Conjunctive Keyword Search With Designated Tester and Timing Enabled Proxy Re-Encryption Function for E-Health Clouds," Ieee T. Inf. Foren. Sec., vol. 11, no. 4, pp. 746-759, 2016. [CrossRef]
- S.H. Heng and K. Kurosawa, k-resilient identity-based encryption in the standard model,2964, T. Okamoto, ed., 2004, pp. 67-80. [CrossRef]
- D. Khader, Public key encryption with keyword search based on K-resilient IBE,3982, M. Gavrilova, et al., eds., 2006, pp. 298-308.
- H.M. YangC.X. Xu and H.T. Zhao, An Efficient Public Key Encryption with Keyword Scheme Not Using Pairing, Proc. First International Conference on Instrumentation, 2011.
- T.F. Vallent and H. Kim, A Pairing-Free Public Key Encryption with Keyword Searching for Cloud Storage Services, Book A Pairing-Free Public Key Encryption with Keyword Searching for Cloud Storage Services, Series A Pairing-Free Public Key Encryption with Keyword Searching for Cloud Storage Services 135,ed., Editor ed., 2014, pp. 70.
- N.B. YangS.M. Xu and Z. Quan, "An Efficient Public Key Searchable Encryption Scheme for Mobile Smart Terminal," Ieee Access, vol. 8, pp. 77940-77950, 2020. [CrossRef]
- M. Ma, M. Luo, S. Fan and D. Feng, "An Efficient Pairing-Free Certificateless Searchable Public Key Encryption for Cloud-Based IIoT," Wirel. Commun. Mob. Com., vol. 2020, 2020. [CrossRef]
- M.R. Senouci, I. Benkhaddra, A. Senouci and F.G. Li, "A provably secure free-pairing certificateless searchable encryption scheme," Telecommun. Syst., vol. 80, no. 3, pp. 383-395, 2022. [CrossRef]
- Z.Y. Hu, L.Z. Deng, Y.Y. Wu, H.Y. Shi and Y. Gao, "Secure and Efficient Certificateless Searchable Authenticated Encryption Scheme Without Random Oracle for Industrial Internet of Things," Ieee Syst. J., vol. 17, no. 1, pp. 1304-1315, 2023. [CrossRef]
- J.W. Byun, H.S. Rhee, H.A. Park and D.H. Lee, Off-line keyword guessing attacks on recent keyword search schemes over encrypted data,4165, W. Jonker and M. Petkovic, eds., 2006, pp. 75-83.
- Y. LuG. Wang and J.G. Li, "Keyword guessing attacks on a public key encryption with keyword search scheme without random oracle and its improvement," Inform. Sciences, vol. 479, pp. 270-276, 2019. [CrossRef]
- M.S. HwangS.T. Hsu and C.C. Lee, "A New Public Key Encryption with Conjunctive Field Keyword Search Scheme," Inf. Technol. Control, vol. 43, no. 3, pp. 277-288, 2014. [CrossRef]
- Q. Chai and G. Gong, Verifiable symmetric searchable encryption for semi-honest-but-curious cloud servers, Proc. IEEE International Conference on Communications, 2012.
- W. Sun, X. Liu, W. Lou, Y.T. Hou and H. Li, Catch You If You Lie to Me: Efficient Verifiable Conjunctive Keyword Search over Large Dynamic Encrypted Cloud Data, Proc. 34th IEEE Conference on Computer Communications (INFOCOM), 2015.
- Y. Miao, J. Ma, X. Liu, Z. Liu and F. Wei, "VMKDO: Verifiable multi-keyword search over encrypted cloud data for dynamic data-owner," Peer Peer Netw. Appl., vol. 11, no. 2, pp. 287-297, 2018. [CrossRef]
- Y. Miao, J. Weng, X. Liu, K. Raymond Choo, Z. Liu and H. Li, "Enabling verifiable multiple keywords search over encrypted cloud data," Inform. Sciences, vol. 465, pp. 21-37, 2018. [CrossRef]
- L. Fang, W. Susilo, C. Ge and J. Wang, "Public key encryption with keyword search secure against keyword guessing attacks without random oracle," Inform. Sciences, vol. 238, pp. 221-241, 2013. [CrossRef]
- Z.Y. Shao and B. Yang, "On security against the server in designated tester public key encryption with keyword search," Inform. Process. Lett., vol. 115, no. 12, pp. 957-961, 2015. [CrossRef]
- C. Hu and P. Liu, "An Enhanced Searchable Public Key Encryption Scheme with a Designated Tester and Its Extensions," Journal of Computers, vol. 7, no. 3, 2012. [CrossRef]
- H.S. Rhee, J.H. Park, W. Susilo and D.H. Lee, "Trapdoor security in a searchable public-key encryption scheme with a designated tester," J. Syst. Software, vol. 83, no. 5, pp. 763-771, 2010. [CrossRef]
- Y. LuG. Wang and J. Li, "On Security of a Secure Channel Free Public Key Encryption with Conjunctive Field Keyword Search Scheme," Inf. Technol. Control, vol. 47, no. 1, pp. 56-62, 2018. [CrossRef]
- I.R. Jeong, J.O. Kwon, D. Hong and D.H. Lee, "Constructing PEKS schemes secure against keyword guessing attacks is possible?" Computer Communications, vol. 32, no. 2, pp. 394-396, 2009. [CrossRef]
- P. Xu, H. Jin, Q. Wu and W. Wang, "Public-Key Encryption with Fuzzy Keyword Search: A Provably Secure Scheme under Keyword Guessing Attack," Ieee T. Comput., vol. 62, no. 11, pp. 2266-2277, 2013. [CrossRef]
- X.J. Lin, L. Sun, H.P. Qu and D.X. Liu, "On the Security of Secure Server-Designation Public Key Encryption with Keyword Search," Comput. J., vol. 61, no. 12, pp. 1791-1793, 2018. [CrossRef]
- Q. Huang and H.B. Li, "An efficient public-key searchable encryption scheme secure against inside keyword guessing attacks," Inform. Sciences, vol. 403, pp. 1-14, 2017. [CrossRef]
- L. Wu, B. Chen, S. Zeadally and D. He, "An efficient and secure searchable public key encryption scheme with privacy protection for cloud storage," Soft Comput., vol. 22, no. 23, pp. 7685-7696, 2018. [CrossRef]
- S.S. Al-Riyami and K.G. Paterson, Certificateless public key cryptography,2894, C. S. Laih, ed., 2003, pp. 452-473.
- Y.M.J.W. Miao, "VCSE: Verifiable conjunctive keywords search over encrypted data without secure-channel," Peer-to-Peer Netw, pp. 995-1007, 2017.
- D.B. He, H.Q. Wang, L.N. Wang, J. Shen and X.Z. Yang, "Efficient certificateless anonymous multi-receiver encryption scheme for mobile devices," Soft Comput., vol. 21, no. 22, pp. 6801-6810, 2017. [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





