Submitted:
19 April 2024
Posted:
23 April 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
- We propose an algorithm that transforms any Petri net into a CCA process (Sect 2.3). This demonstrates that CCA is at least as expressive as Petri nets, i.e. any system that can be specified in Petri nets can also be specified in CCA.
- We demonstrate that the proposed algorithm is efficient and scalable (Sect 2.3.3). Indeed, the time complexity of the algorithm is quadratic (i.e. the execution time is in the order of the square of the size of the Petri net in input) and the size of the CCA process generated in output grows linearly with the size of the Petri net in input.
- The proposed algorithm is implemented in Python so a Petri net can be translated into a CCA process automatically at a click of a button (Sect. 2.3.3 and Appendix A).
- We show through experiments that a Petri net and its corresponding CCA process behave the same way using the CCA simulator ccaPL. The proposed approach is illustrated using a case study of the dining cryptographers problem (Sect. 3).
2. Materials and Methods
2.1. Overview of Petri Nets
- P is a finite set of places.
- T is a finite set of transitions, such that and .
- is an input function. is the number of directed arcs from the place p to the transition t.
- is an output function. is the number of directed arcs from the transition t to the place p.
- is the initial marking, which defines the initial number of tokens in each place.
2.2. Overview of CCA
2.2.1. Processes
2.2.2. Capabilities
2.2.3. Context Model
2.2.4. Context-Expressions
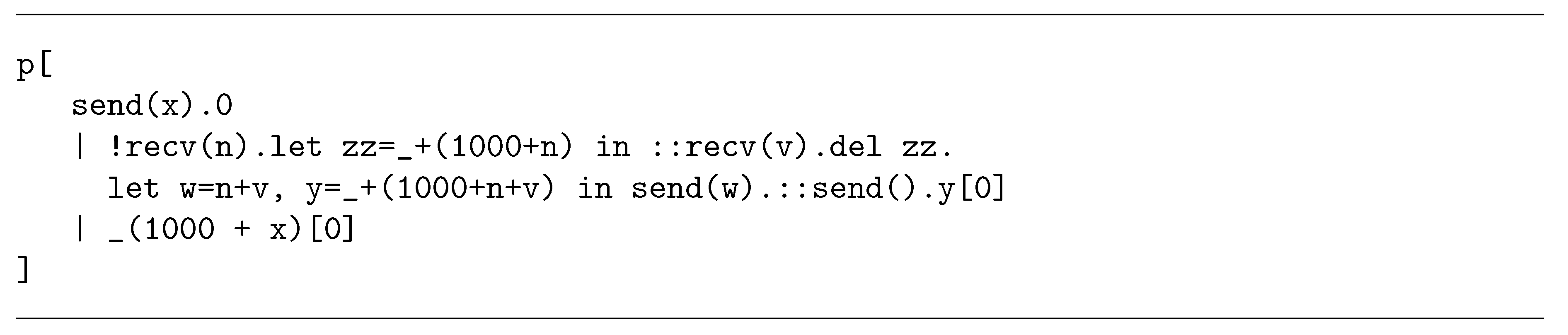
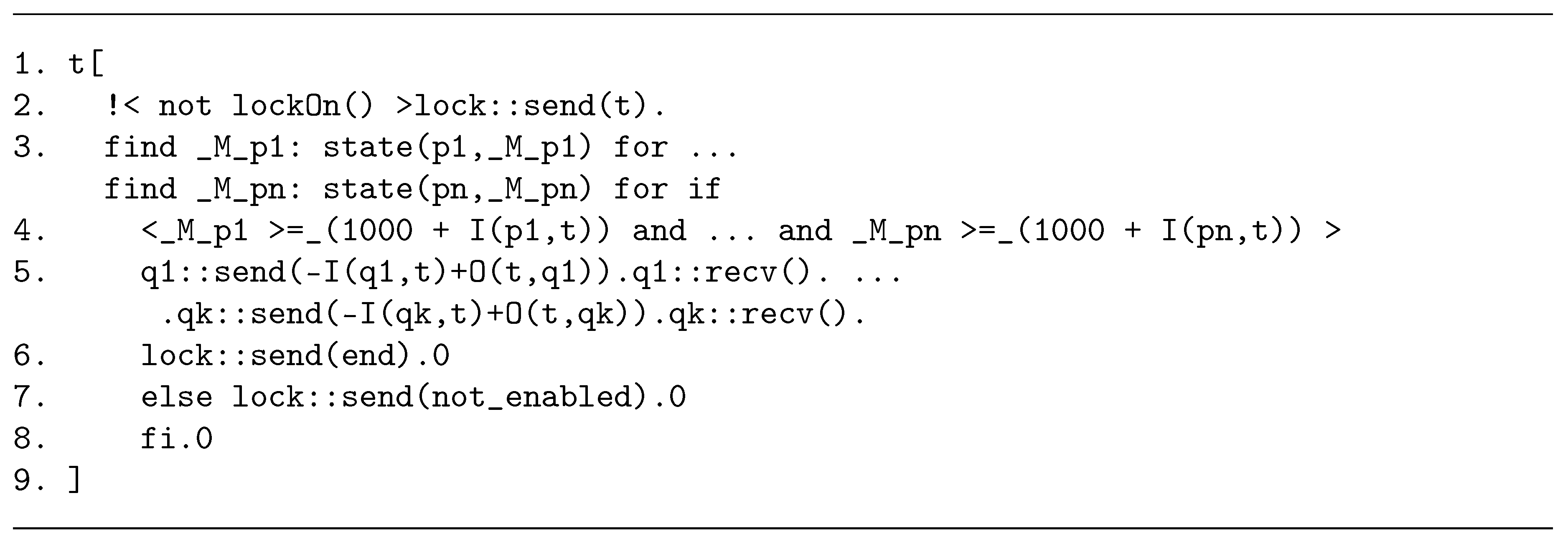
2.3. An Algorithm for Mapping a Petri Net onto a CCA Process
| Algorithm 1: Mapping a Petri net onto a CCA process |
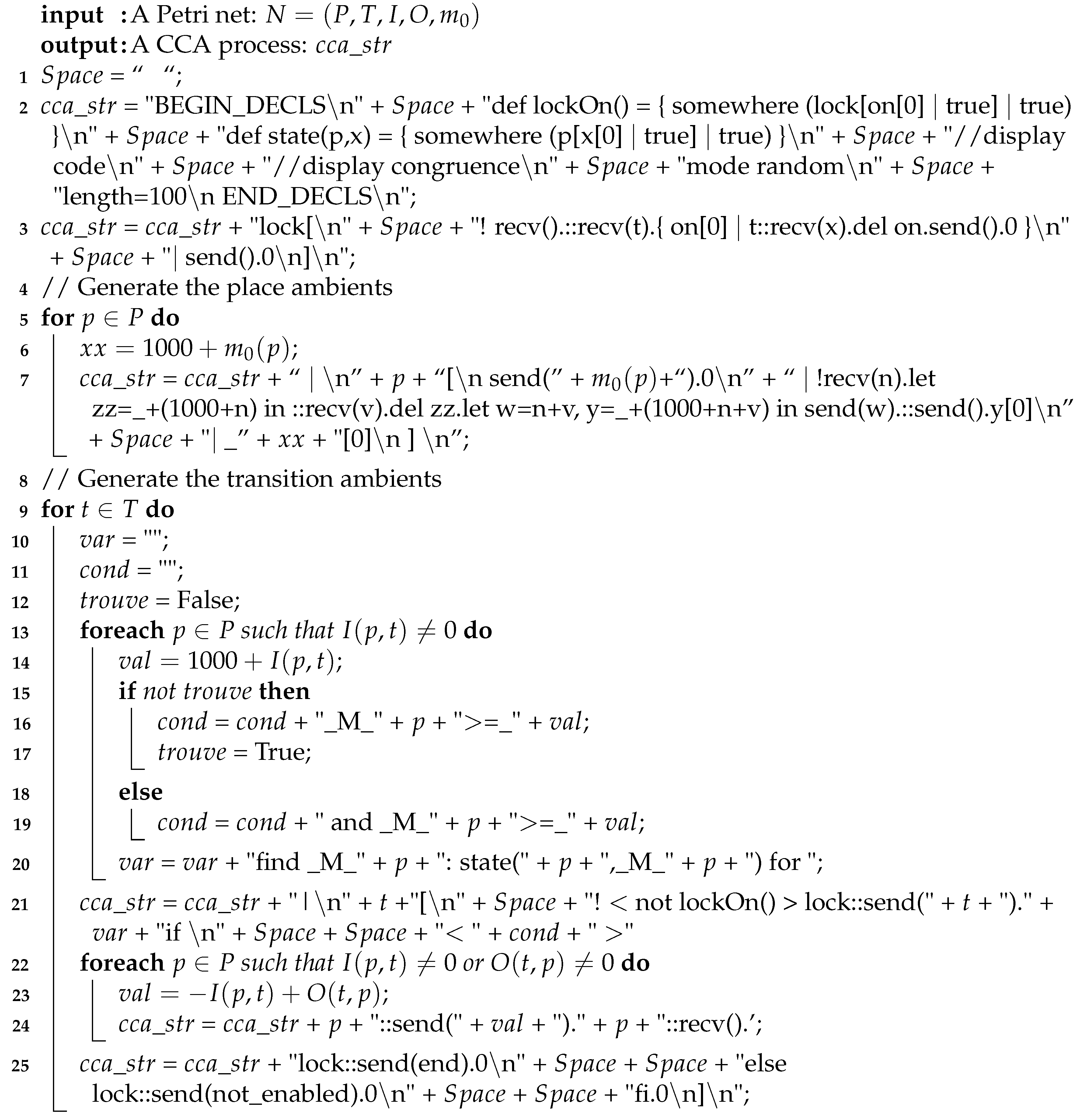 |
2.3.1. Modelling Places
- If , and , then , and . Let “” and “”, for some strings and . It follows that “” and “”. In string comparison, “” ≥ “” ⇔ “”≥ “”. We conclude that
- If , and , then . Let “” and “”, for some digit and strings and of equal length n. Since , “” ≥ “” is always true. Therefore we conclude that
-
If , and , then let and , for some integers and , and digits and . There are 2 cases: or .
- -
- If , then .
- -
- If , let “ ” and “”, for some strings and . It follows that “” > “” .
Therefore, we conclude that .
2.3.2. Modelling Transitions
2.3.3. Complexity of the Algorithm
3. Results
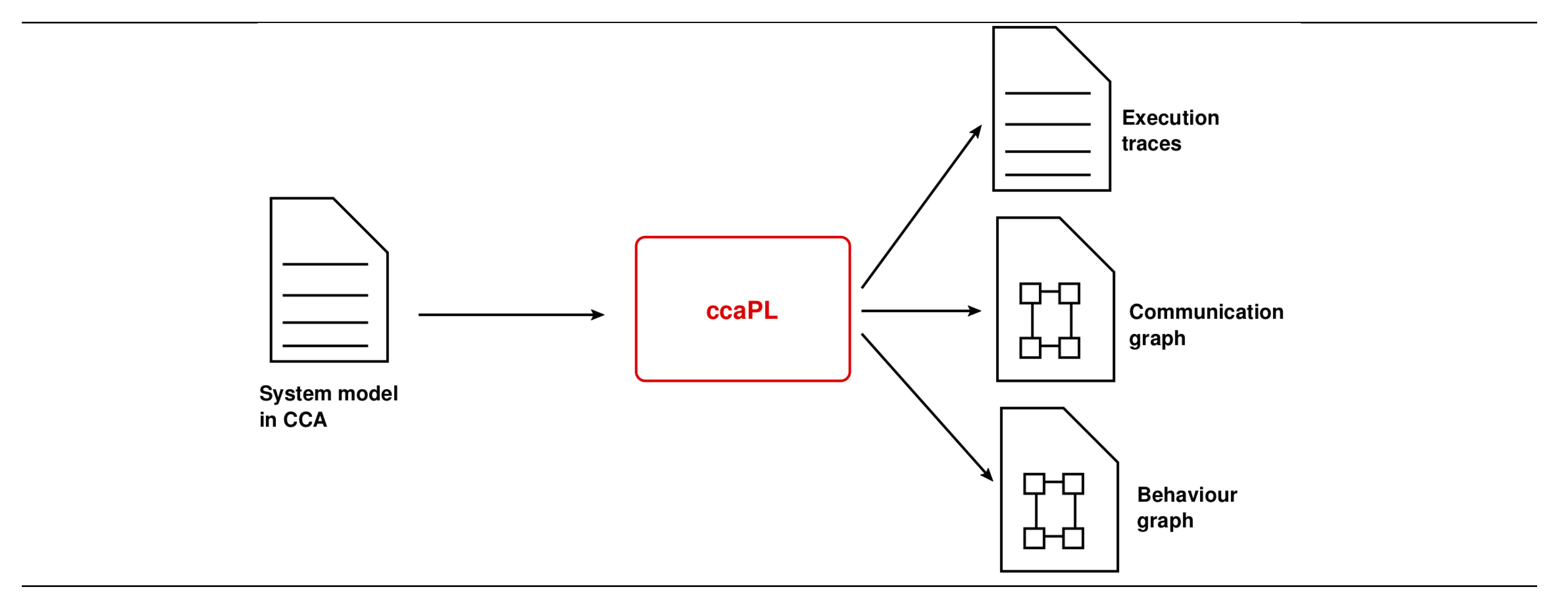
3.1. Overview of the CCA Simulator ccaPL
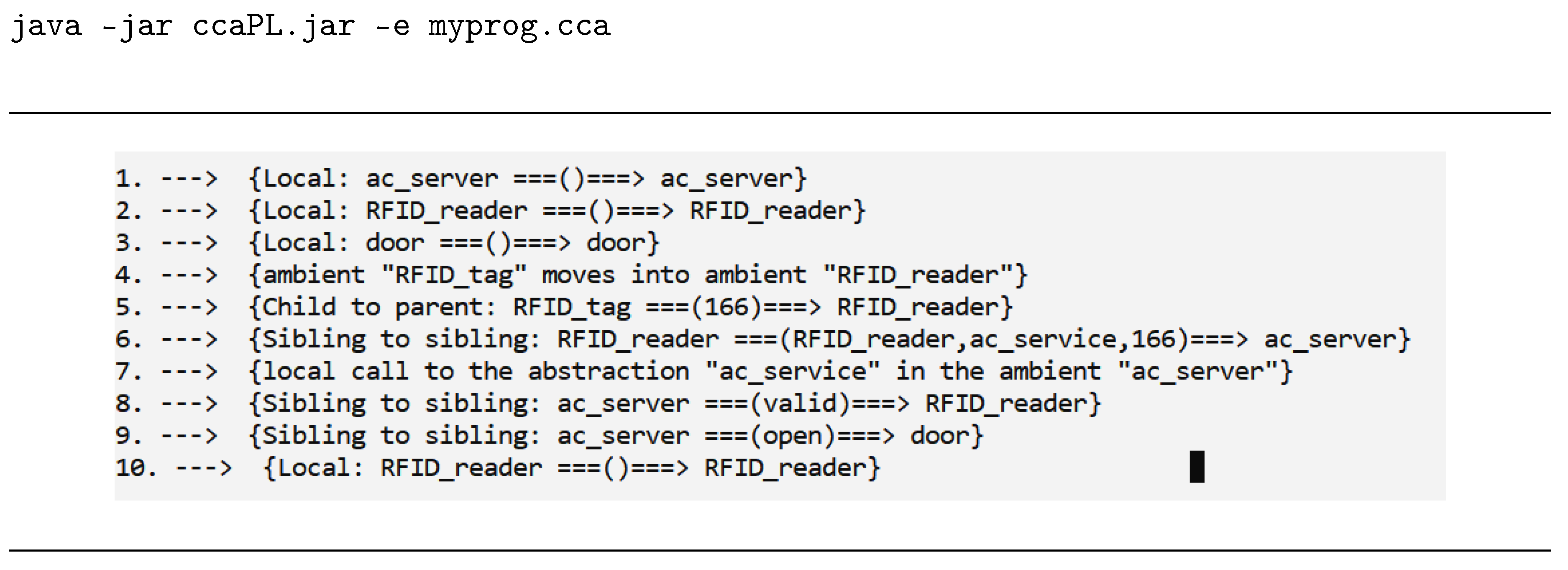
3.1.1. Textual Execution Trace
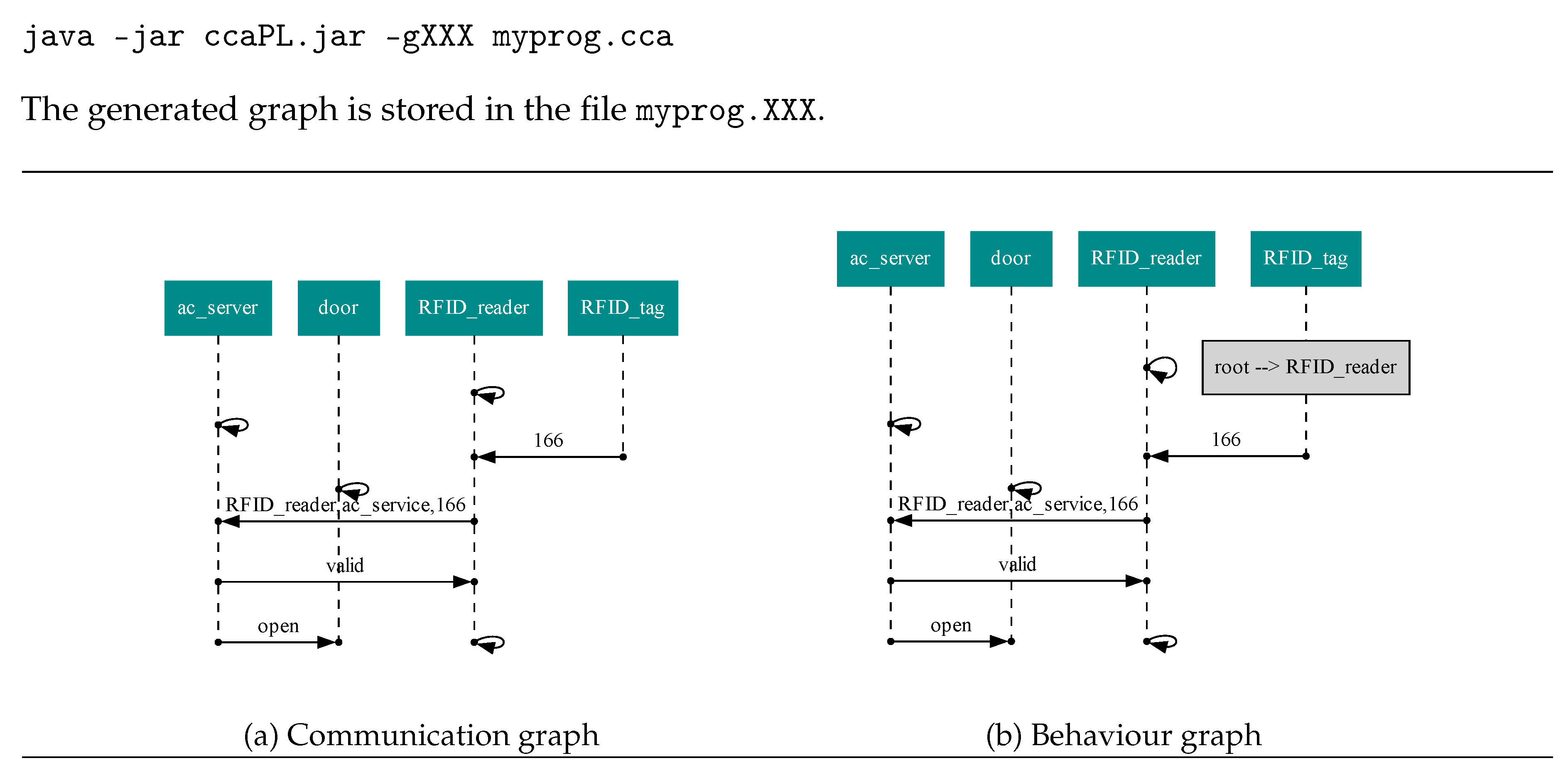
3.1.2. Communication Graph
3.1.3. Behaviour Graph
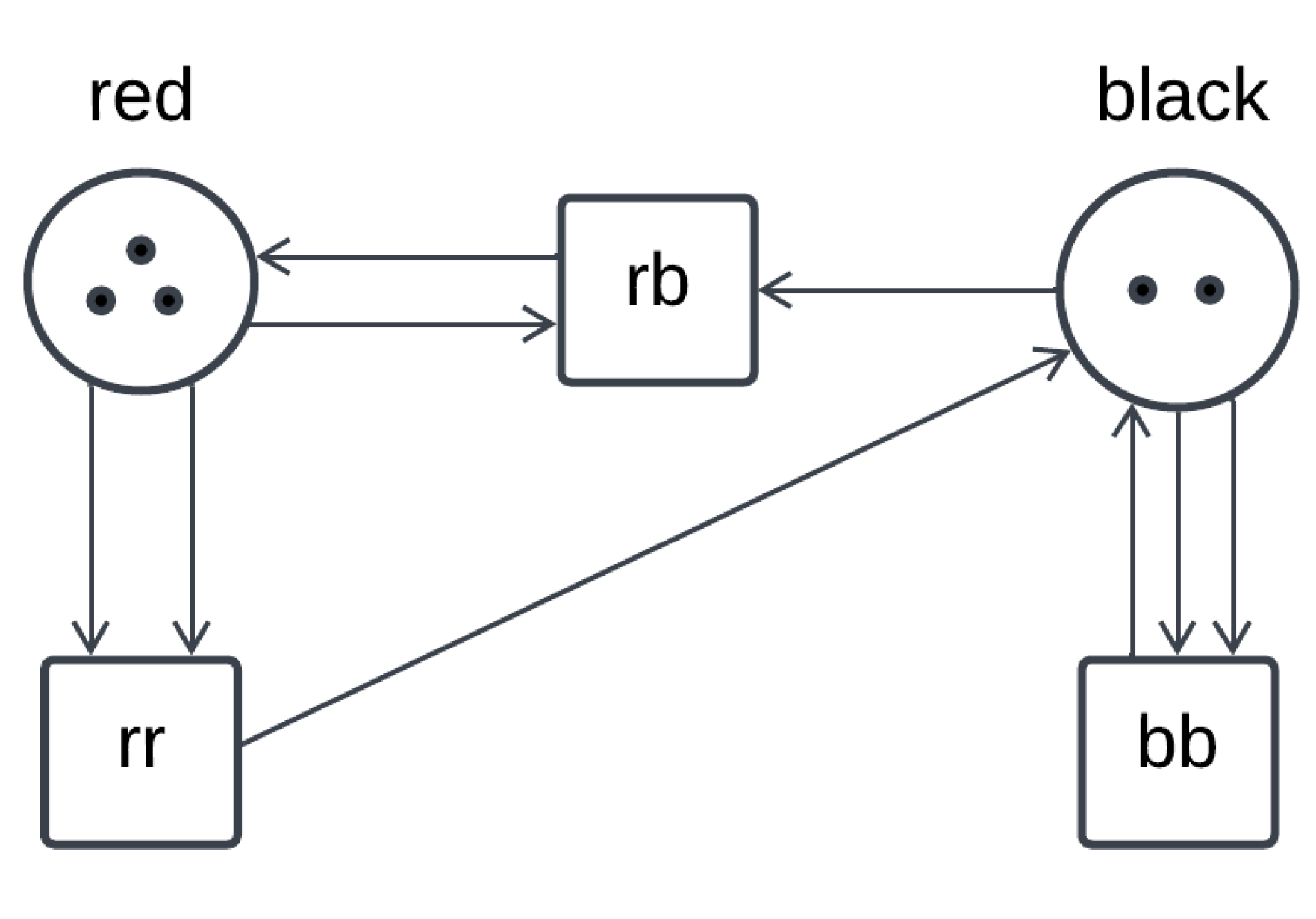
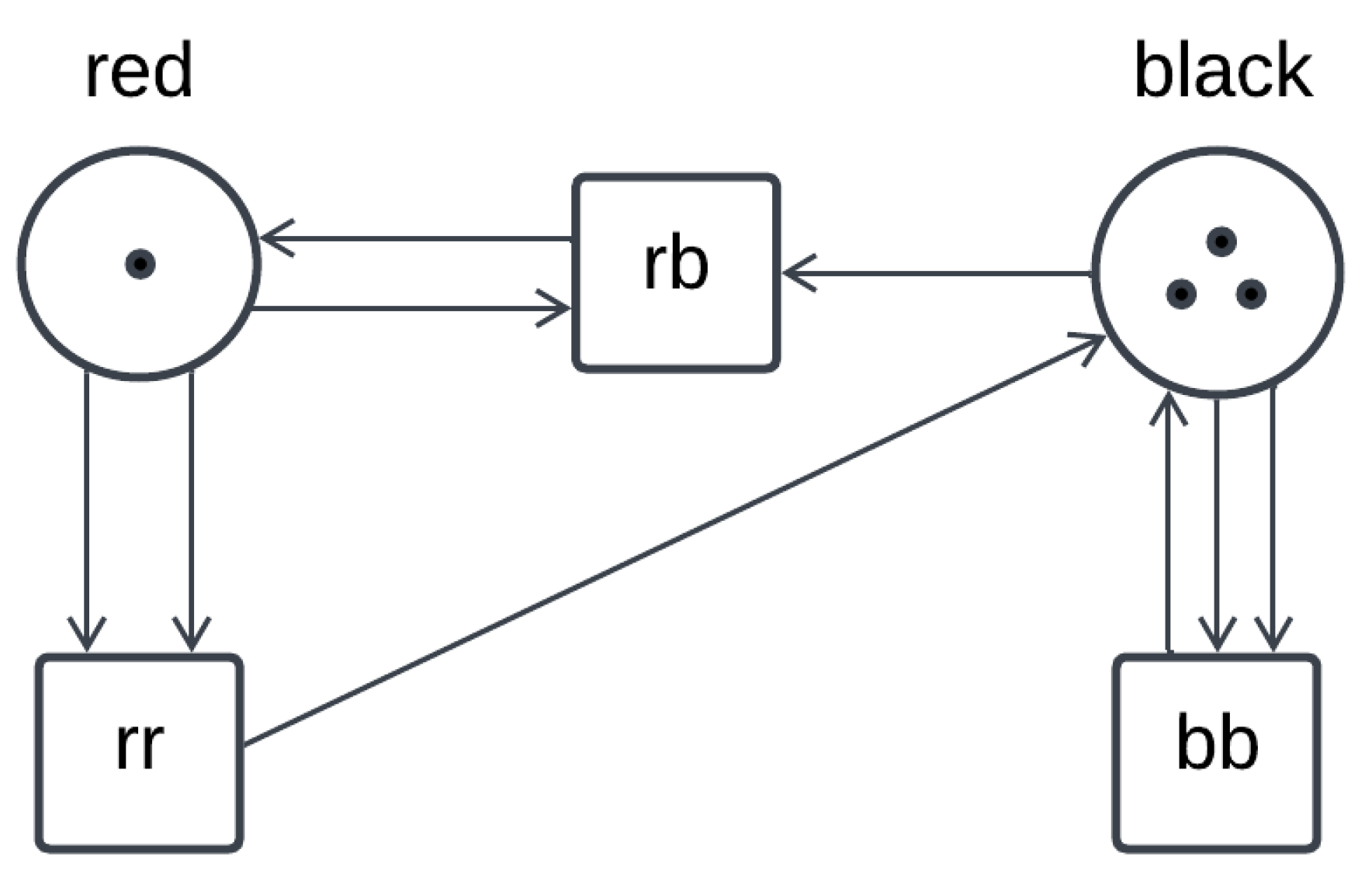
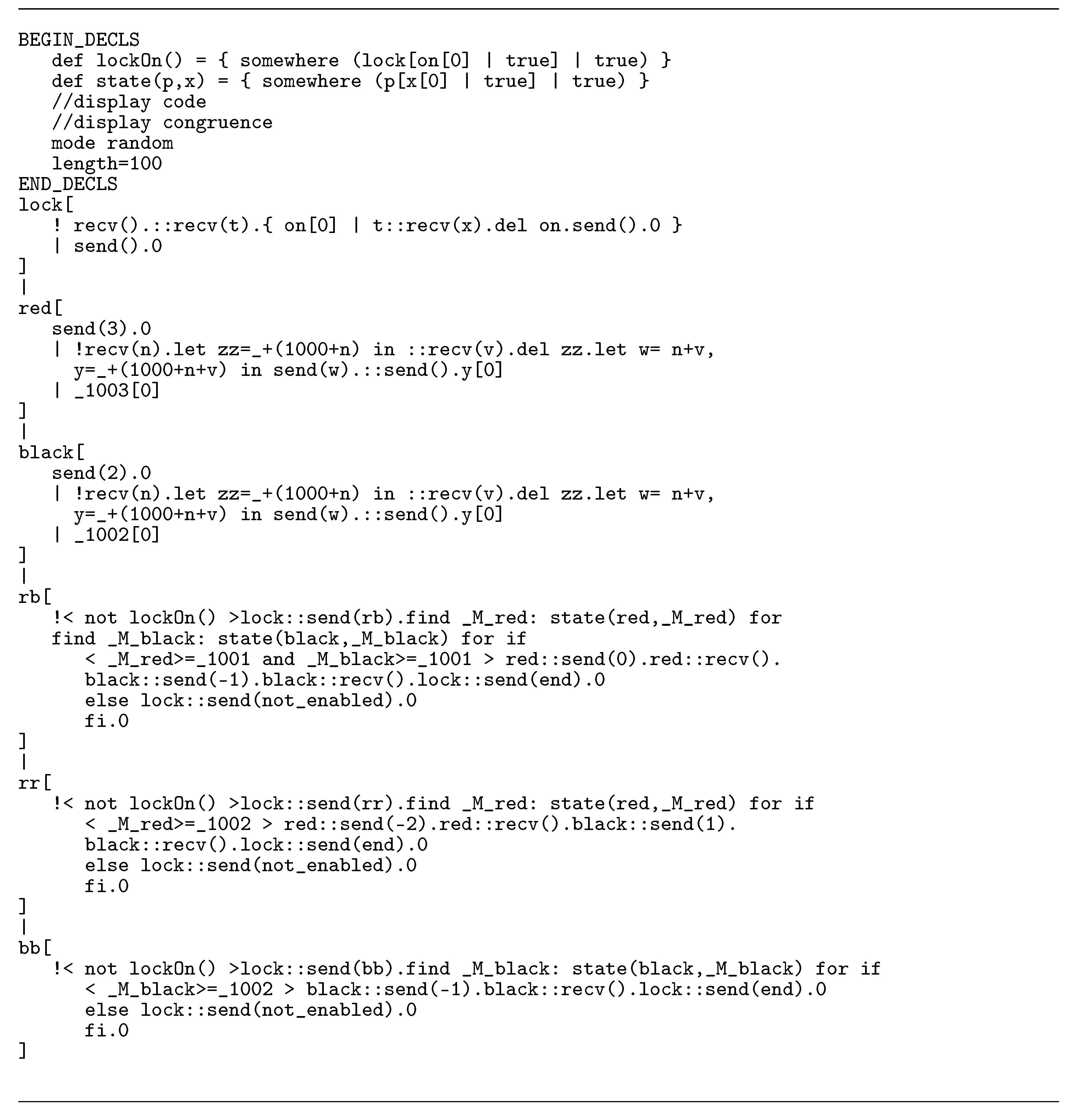
3.2. A Case Study: The Dining Cryptographers Problem
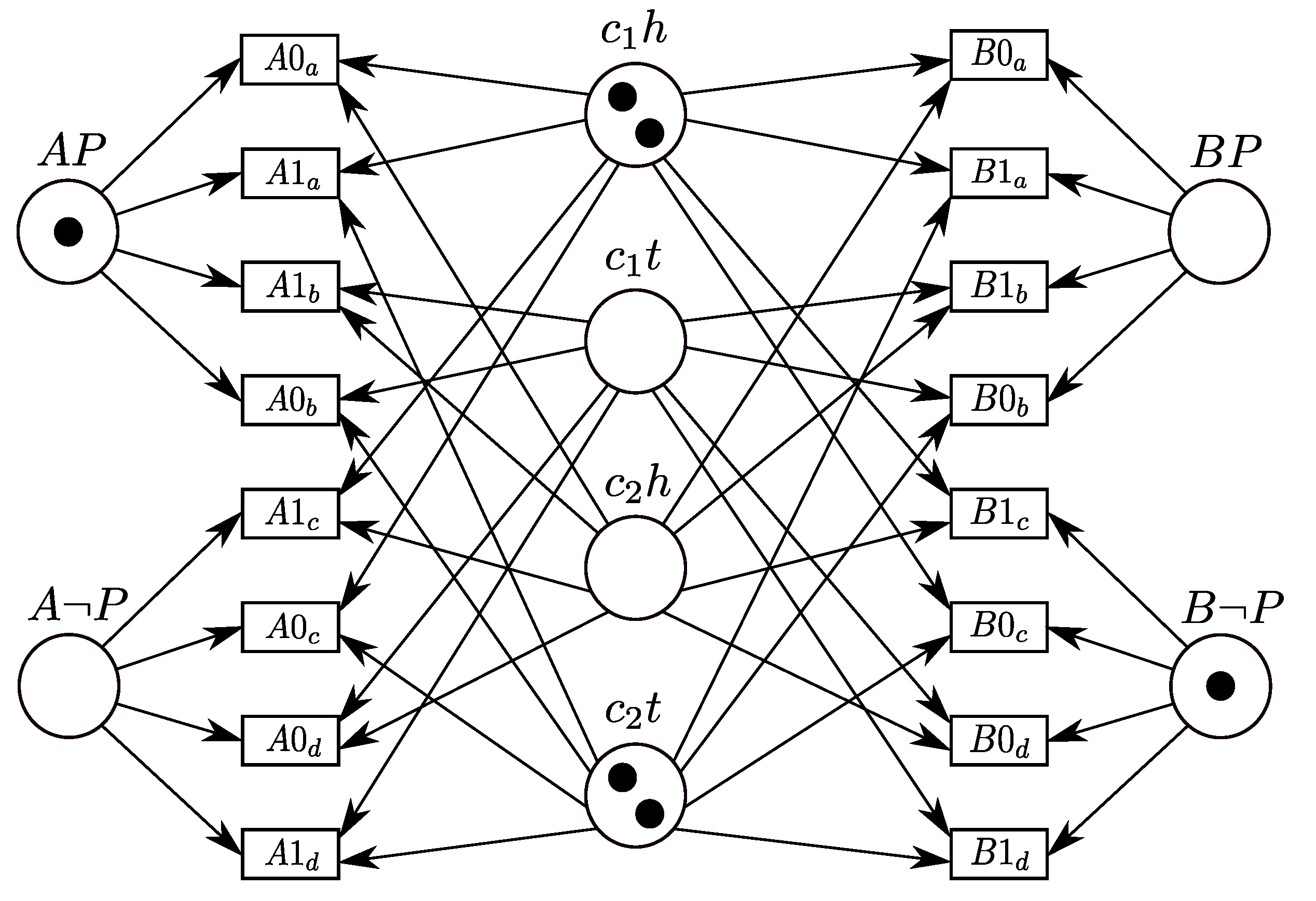
3.2.1. A Dining Cryptographers Protocol
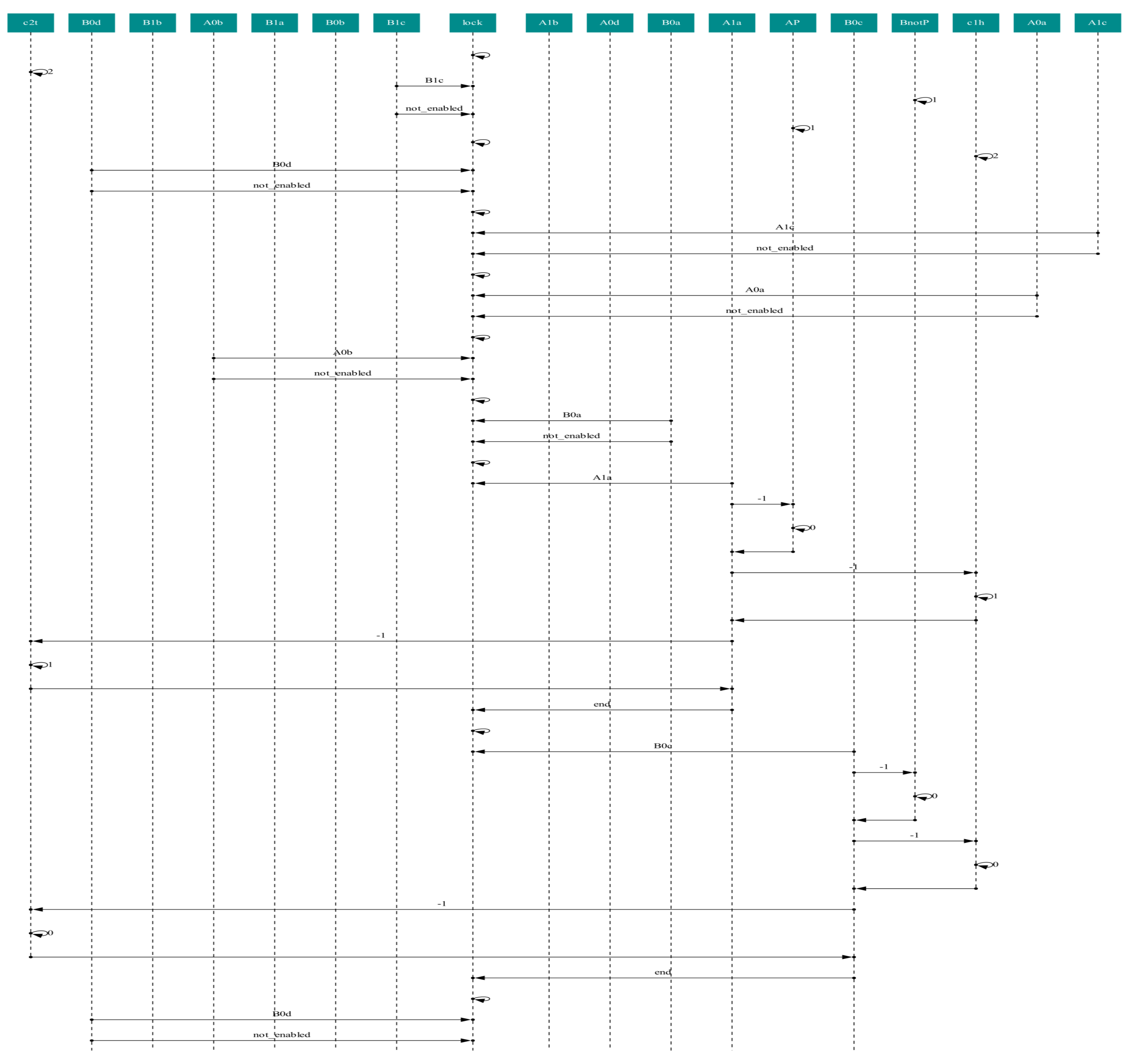
3.2.2. Mapping the Petri Net of the Dining Cryptographers Protocol onto a CCA Process
4. Discussion
5. Conclusion
Author Contributions
Funding
Conflicts of Interest
Appendix A. An implementation of Algorithm 1 in Python
References
- Petri, C.A. Kommunikation mit Automaten (Communication with Automata). Phd thesis, University of Bonn, 1962.
- Murata, T. Petri nets: Properties, analysis and applications. Proceedings of the IEEE 1989, 77, 541–580.
- Hoare, C. Communicating Sequential Processes; Prentice Hall, 1985.
- Milner, R. Communication and Mobile Systems: The π-Calculus; Cambridge University Press, 1999.
- Fournet, C.; Gonthier, G. The reflexive CHAM and the join-calculus, New York, NY, USA, 1996; POPL ’96, p. 372–385. [CrossRef]
- Siewe, F.; Zedan, H.; Cau, A. The Calculus of Context-aware Ambients. Journal of Computer and System Sciences 2011, 77, 597–620.
- Siewe, F. ccaPL: A CCA Programming Environment. https://fsiewe.afrilocode.net/CCA/index.html (accessed: 23 November 2023).
- Cardelli, L.; Gordon, A.D. Mobile Ambients. Theoretical Computer Science 2000, 240, 177–213.
- Alfakeeh, A.S.; Al-Bayatti, A.H.; Siewe, F.; Baker, T. Agent-based negotiation approach for feature interactions in smart home systems using calculus of the context-aware ambient. Transactions on Emerging Telecommunications Technologies 2022, 33, e3808.
- Siewe, F.; Yang, H. Privacy protection by typing in ubiquitous computing systems. Journal of Systems and Software 2016, 120, 133–153. [CrossRef]
- Atbaiga, N.; Siewe, F. Formal Specification of a Context-aware Whiteboard System in CCA. In Proceedings of the In Proceedings of the Libyan International Conference on Electrical Engineering and Technology (LICEET 2018), Tripoli, Libya, 2018.
- Mennicke, S. A Petri Net Semantics for the Join-Calculus. Technical report, Technical Report, TU Braunschweig. Available at https://www. tu-braunschweig …, 2012.
- Yao, W.; He, X. Mapping Petri nets to concurrent programs in CC++. Information and Software Technology 1997, 39, 485–495. [CrossRef]
- Korečko, t.; Sobota, B. Petri Nets to B-Language Transformation in Software Development. Acta Polytechnica Hungarica 2014, 11, 187–206.
- Boukelkoul, S.; Redjimi, M. Mapping between Petri nets and DEVS models. In Proceedings of the 2013 3rd International Conference on Information Technology and e-Services (ICITeS), 2013, pp. 1–6. [CrossRef]
- Marsan, M.A.; Balbo, G.; Conte, G.; Donatelli, S.; Franceschinis, G. Modelling with generalized stochastic Petri nets. ACM SIGMETRICS performance evaluation review 1998, 26, 2.
- van der Aalst, W.M.P. Putting high-level Petri nets to work in industry. Computers in Industry 1994, 25, 45–54. [CrossRef]
- AT&T Labs-Research. Graphviz Distribution. http://www.research.att.com/sw/tools/graphviz/download.html (accessed: 23 November 2023).
- Chaum, D. The Dining Cryptographers Problem: Unconditional Sender and Recipient Untraceability. J. Cryptol. 1988, 1, 65–75.
- Mazaré, L. Using unification for opacity properties. In Proceedings of the In Proceedings of the Workshop on Issues in the Theory of Security (WITS’04), 2004, pp. 165–176.
- Bryans, J.W.; Koutny, M.; Ryan, P.Y.A. Modelling Opacity Using Petri Nets. Electr. Notes Theor. Comput. Sci. 2005, 121, 101–115.
- Best, E.; Devillers, R.; Hall, J.G. The box calculus: A new causal algebra with multi-label communication. In Proceedings of the Advances in Petri Nets 1992; Rozenberg, G., Ed., Berlin, Heidelberg, 1992; pp. 21–69.
- Koutny, M.; Esparza, J.; Best, E. Operational Semantics for the Petri Box Calculus. In Proceedings of the CONCUR ’94: Concurrency Theory; Jonsson, B.; Parrow, J., Eds., Berlin, Heidelberg, 1994; pp. 210–225.
- Cerone, A. Implementing Condition/Event Nets in the Circal Process Algebra. In Proceedings of the 5th International Conference on Fundamental Approaches to Software Engineering, FASE `02; Jonsson, B.; Parrow, J., Eds., Springer-Verlag, 2002; pp. 49–63.
- Milner, R. Bigraphs for Petri nets. In Proceedings of the Advanced Course on Petri Nets. Springer, 2003, pp. 686–701.
- Sassone, V.; Sobociński, P. A congruence for Petri nets. Electronic Notes in Theoretical Computer Science 2005, 127, 107–120.
- Leifer, J.J.; Milner, R. Transition systems, link graphs and Petri nets. Mathematical Structures in Computer Science 2006, 16, 989–1047.
- Khomenko, V.; Meyer, R.; Hüchting, R. A polynomial translation of pi-calculus FCPs to safe Petri nets. Logical Methods in Computer Science 2013, 9.
- Khomenko, V.; Germanos, V. Modelling and Analysis Mobile Systems Using-calculus (EFCP). In Transactions on Petri Nets and Other Models of Concurrency X; Springer, 2015; pp. 153–175.
- Degano, P.; De Nicola, R.; Montanari, U. A distributed operational semantics for CCS based on condition/event systems. Acta Informatica 1988, 26, 59–91.
- Goltz, U. CCS and Petri nets. In LITP Spring School on Theoretical Computer Science; Springer, 1990; pp. 334–357.
- Busi, N.; Gorrieri, R. Distributed semantics for the π-calculus based on Petri nets with inhibitor arcs. The Journal of Logic and Algebraic Programming 2009, 78, 138–162.
- Dam, M. Model Checking Mobile Processes. Information and Computation 1996, 129, 35–51.
- Sangiorgi, D.; Walker, D. The π-calculus: A Theory of Mobile Processes; Cambridge University Press, 2001.
- van Glabbeek, R.; Vaandrager, F. Petri net models for algebraic theories of concurrency. In Proceedings of the PARLE Parallel Architectures and Languages Europe; de Bakker, J.W.; Nijman, A.J.; Treleaven, P.C., Eds. Springer Berlin Heidelberg, 1987, pp. 224–242.
- Degano, P.; Nicola, R.D.; Montanari, U. A distributed operational semantics for CCS based on condition/event systems. Acta Informatica 1988, 26, 59–91.
- Siewe, F.; Germanos, V.; Zeng, W. Analysing Petri Nets in a Calculus of Context-Aware Ambients. In Proceedings of the 2020 IEEE 44th Annual Computers, Software, and Applications Conference (COMPSAC). IEEE Computer Society, 2020, pp. 1647–1652.
- Gorrieri, R.; Montanari, U. On the implementation of concurrent calculi in net calculi: two case studies. Theoretical Computer Science 1995, 141, 195–252.
- Taubner, D.A. Finite Representations of CCS and TCSP Programs by Automata and Petri Nets; Springer Berlin, Heidelberg, 1989.
| 1 | First in First out |
| Processes | Context-expressions | ||||||
| inactivity | empty context | ||||||
| parallel composition | true | ||||||
| block | false | ||||||
| name restriction | name match | ||||||
| replication | hole | ||||||
| ambient | location context | ||||||
| context-guarded prefix | parallel composition | ||||||
| if-then | conjunction | ||||||
| … | disjunction | ||||||
| negation | |||||||
| if-then-else | spatial next modality | ||||||
| somewhere modality | |||||||
| arithmetic | |||||||
| search | |||||||
| process abstraction | |||||||
| M | Capabilities | Locations | |||||
| one transition | @ | any parent | |||||
| move into ambient n | specific parent n | ||||||
| move out of parent | # | any child | |||||
| delete ambient n | specific child n | ||||||
| receive data from | any sibling | ||||||
| send data to | specific sibling n | ||||||
| process abstraction call | locally |
| C |
| ⊧ | ||||
| C | ⊧ | iff | ||
| C | ⊧ | iff | ||
| C | ⊧ | iff | ||
| C | ⊧ | iff | ||
| C | ⊧ | iff | ||
| C | ⊧ | iff | ||
| C | ⊧ | iff | ||
| C | ⊧ | iff | ||
| C | ⊧ | iff | or |
| = | n is located at self. | ||
| = | self is located at n. | ||
| = | m is located at n. | ||
| = | self is with n. | ||
| = | n is with m. | ||
| = | the current state of p is x. | ||
| = | the lock is on. |
| (R1) | if |
| (R2) | |
| , for some i, . | |
| (R3) | |
| (R4) | |
| if . | |
| (R5) | |
| if |
 |
 |
 |
 |
 |
 |
| Inputs | Outputs | |||
|---|---|---|---|---|
| Coin | Cryptographer | Petri net | CCA process | |
| markings | markings | Enabled transitions | Executed ambients | # |
| , | A0a, B1c | 1 | ||
| , | A1c, B0a | 2 | ||
| , | A1c, B1c | 3 | ||
| , | A1a, B0c | 4 | ||
| , | A0c, B1a | 5 | ||
| , | A0c, B0c | 6 | ||
| , | A1b, B0b | 7 | ||
| , | A0d, B1b | 8 | ||
| , | A0d, B0d | 9 | ||
| , | A0b, B1d | 10 | ||
| , | A1d, B0b | 11 | ||
| , | A1d, B1d | 12 | ||
Short Biography of Authors
 |
Dr. François Siewe is a Reader in Software Engineering in the School of Computer Science and Informatics at De Montfort University (DMU) in Leicester in the UK. He received a Ph.D. degree in Computer Science from De Montfort University in 2005. He obtained a B.Sc. degree in Mathematics and Computer Science in 1990, a M.Sc. degree in 1991, a Diplome d’Etude Approfondie (DEA) degree in Computer Science in 1992, and a Doctorat de Troisième Cycle degree in Computer Science in 1997 from the University of Yaoundé I in Yaoundé, Cameroon. Prior to joining DMU, he was a Fellow at the United Nations University International Institute for Software Technology (UNU-IIST) in Macua in China, and a Lecturer at the University of Dschang in Cameroon. His research interests include software engineering, formal methods, cyber security, context-aware and pervasive computing, and Internet of Things (IoT). |
 |
Dr. Vasileios Germanos is a Senior Lecturer in Computer Science in the Scholl of Computer Science and Informatics at De Montfort University, in Leicester in the UK. He obtained his MSc and PhD, both in Computing Science, from Newcastle University, UK. His research include formal methods, concurrent systems and cyber security. |
 |
Dr. Wen Zeng is an Associate Professor in the School of Computer and Information Engineering at Shanghai Polytechnic University. She is an Honorary Senior Research Fellow at De Montfort University, U.K., and a Guest Member of Staff at Newcastle University, U.K. She received her PhD and MSc both from Newcastle University, U.K. After that, she became a Post-doc Research Associate at Newcastle University. In 2017, she joined the School of Computer Science and Informatics at De Montfort University to work as a Tenured Senior Lecturer in Cybersecurity. Her current research interests center on the system design and optimization, including distributed systems, Internet of Things with Cloud computing systems, information flow, Cybersecurity, data privacy and risk management, and big data. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





