Submitted:
08 April 2024
Posted:
08 April 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Preliminaries
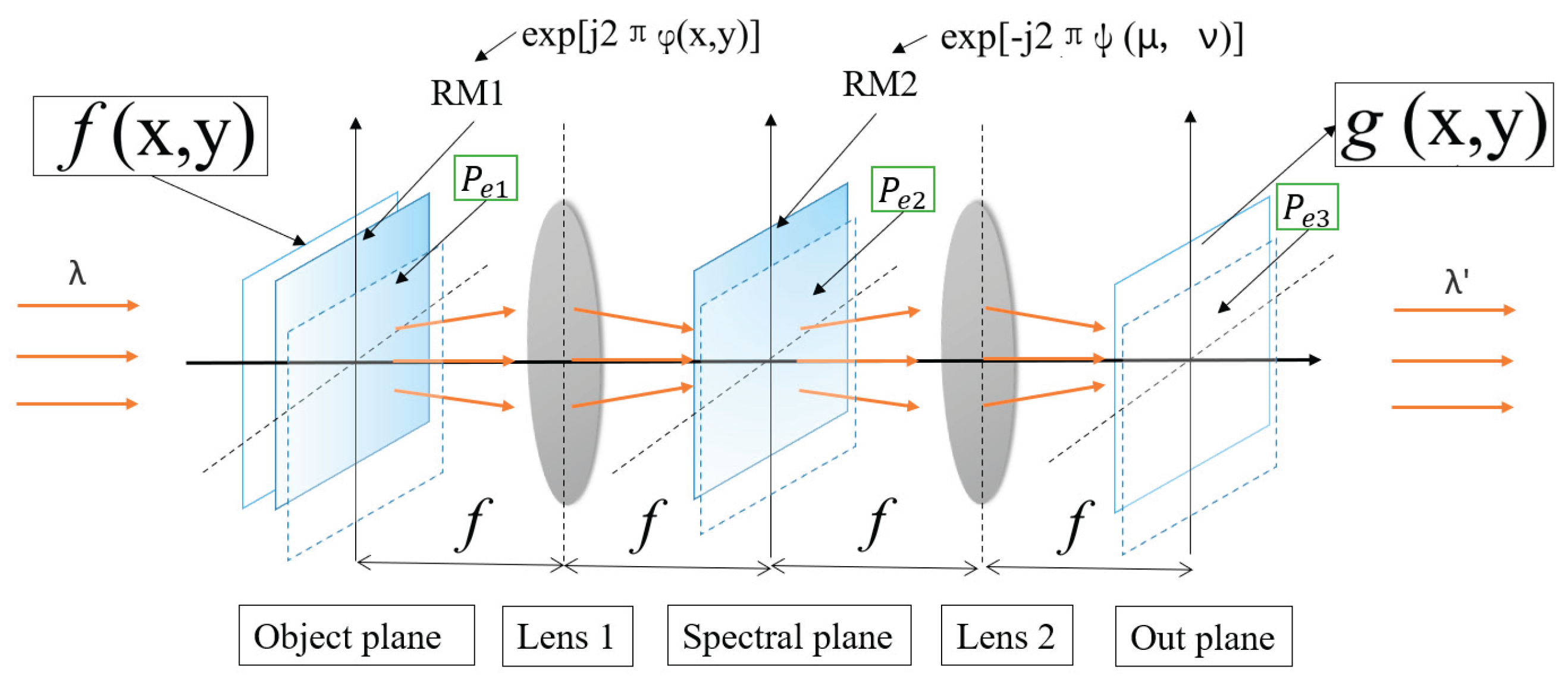
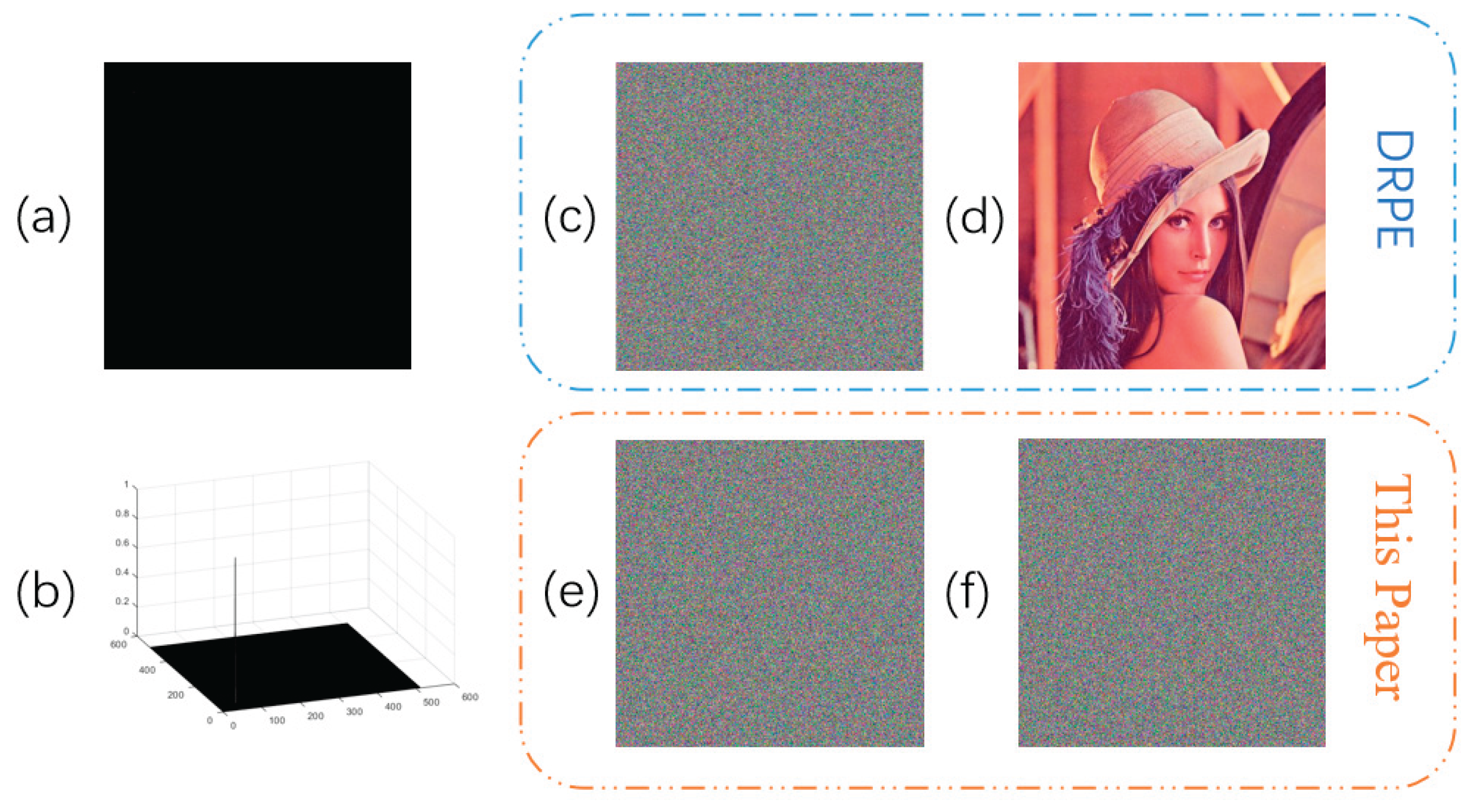
2.1. Double Random Phase Encoding
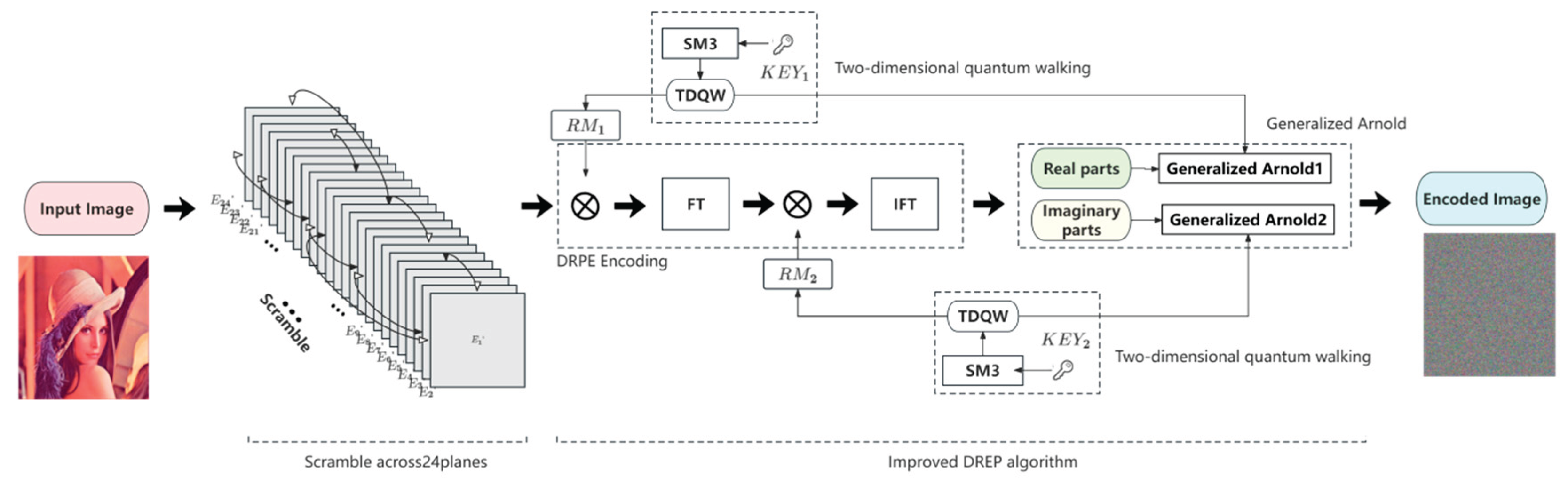
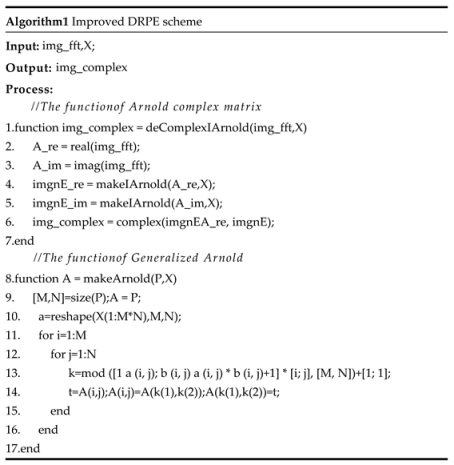
2.2. Improved DREP
2.3. Two Dimensional Quantum Walking (TDQW)
2.4. Bit Layer Scrambling
3. Encryption Algorithm and Decryption Algorithm
3.1. Encryption Algorithm
 |
3.2. Decryption Algorithm
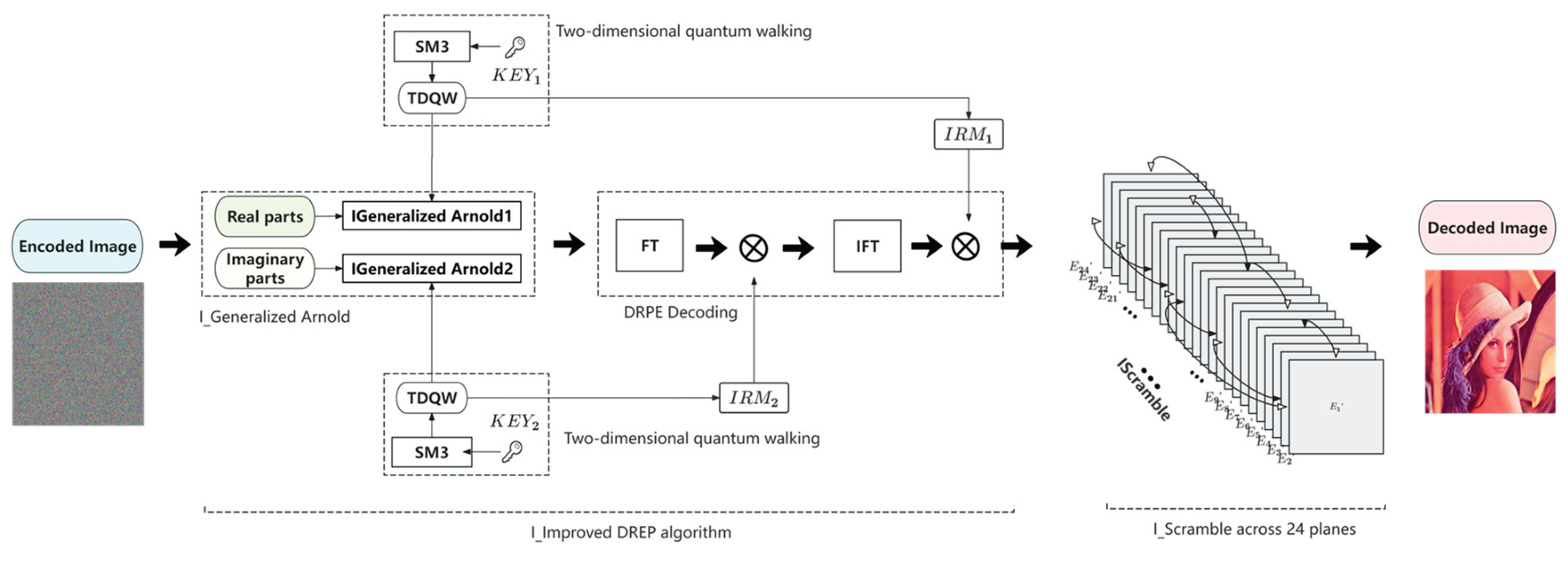
4. Numerical Simulation and Performance Analysis
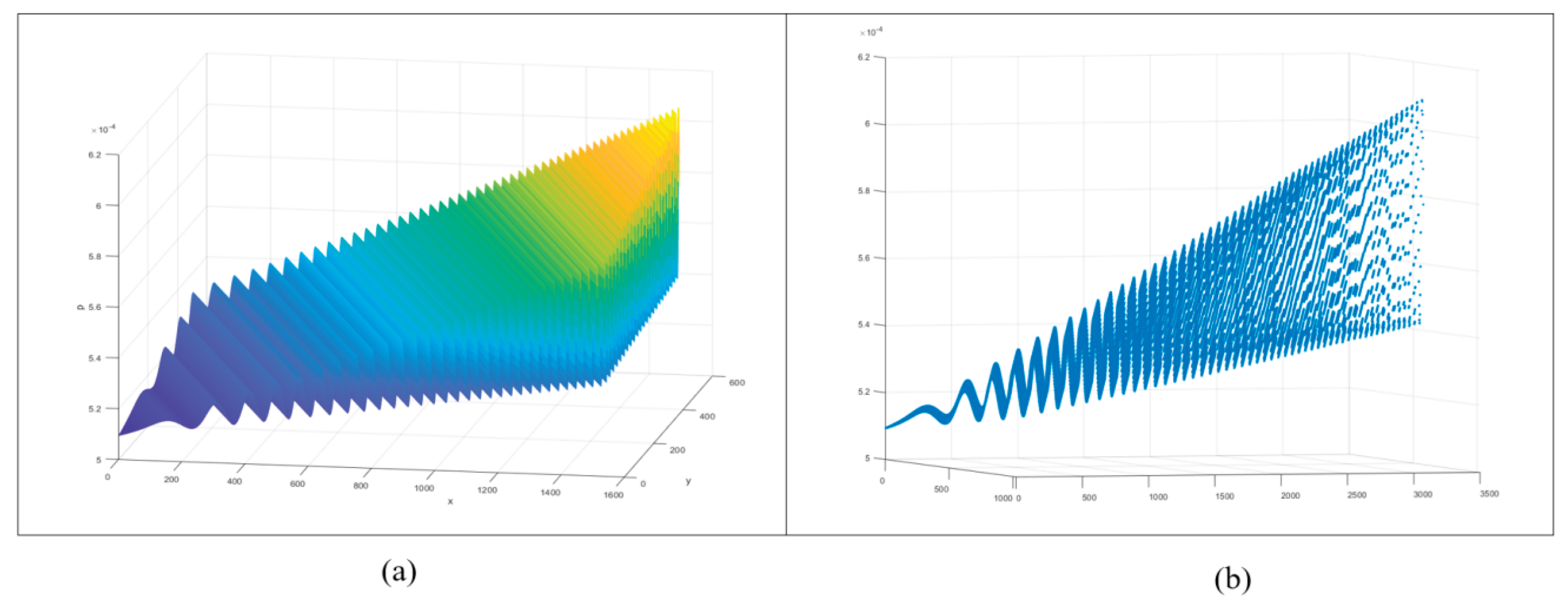
4.1. Correlation Analysis
4.2. Histogram
4.3. Information Entropy
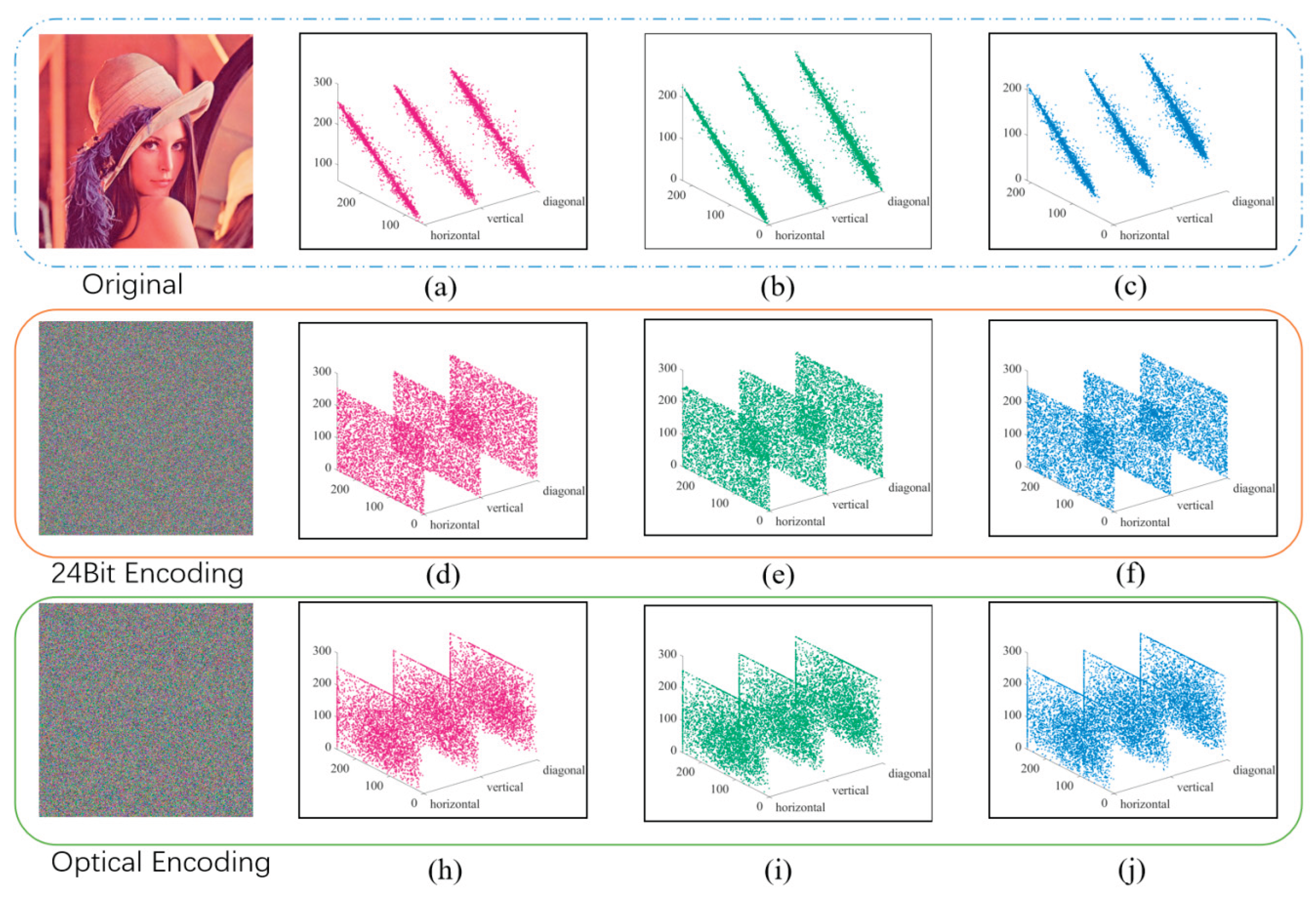
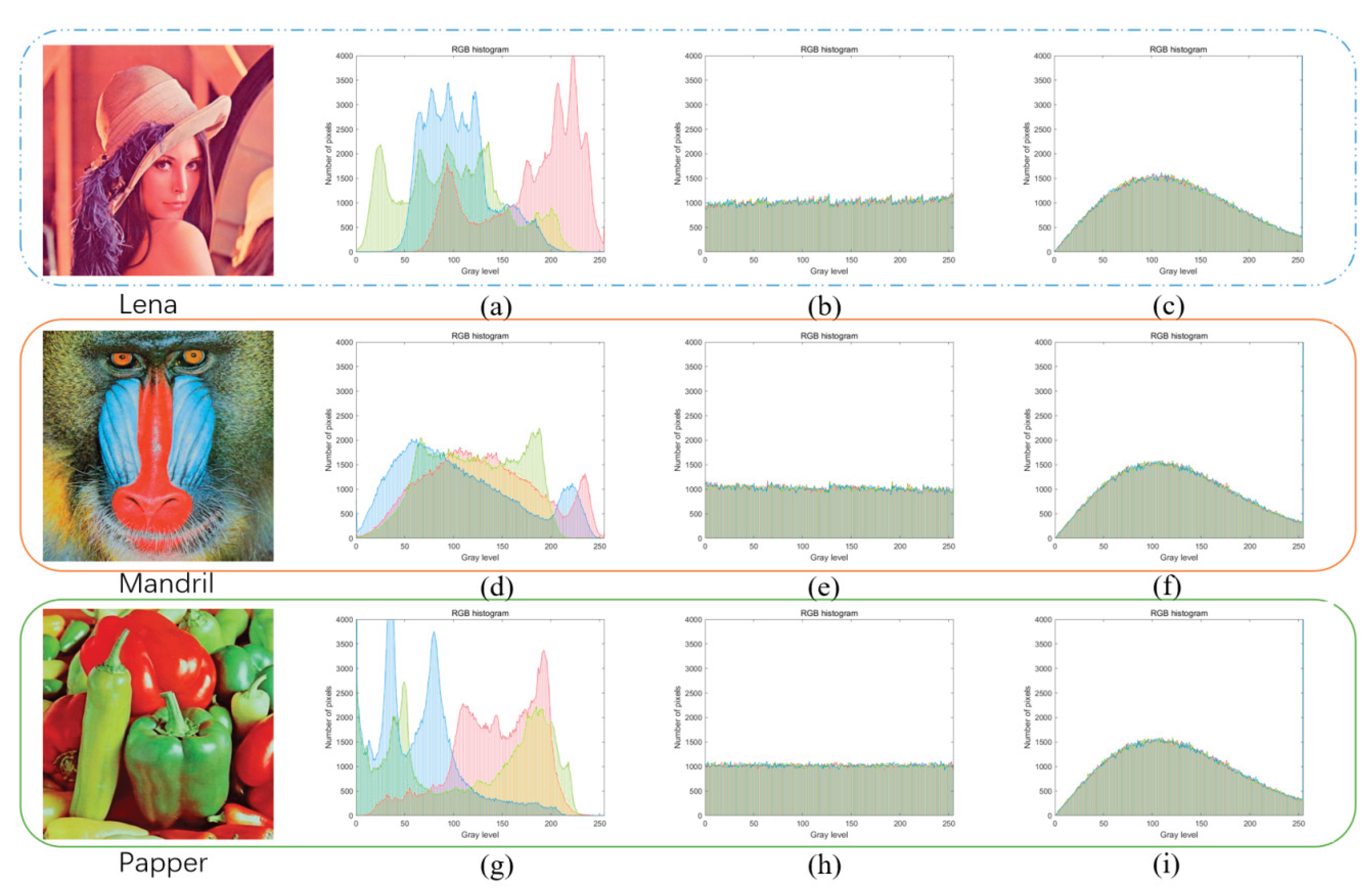
4.4. Key Space and Key Sensitivity
4.5. Known Plaintext Attack (KPA Attack)
4.6. Chosen Plaintext Attack (CPA Attack)
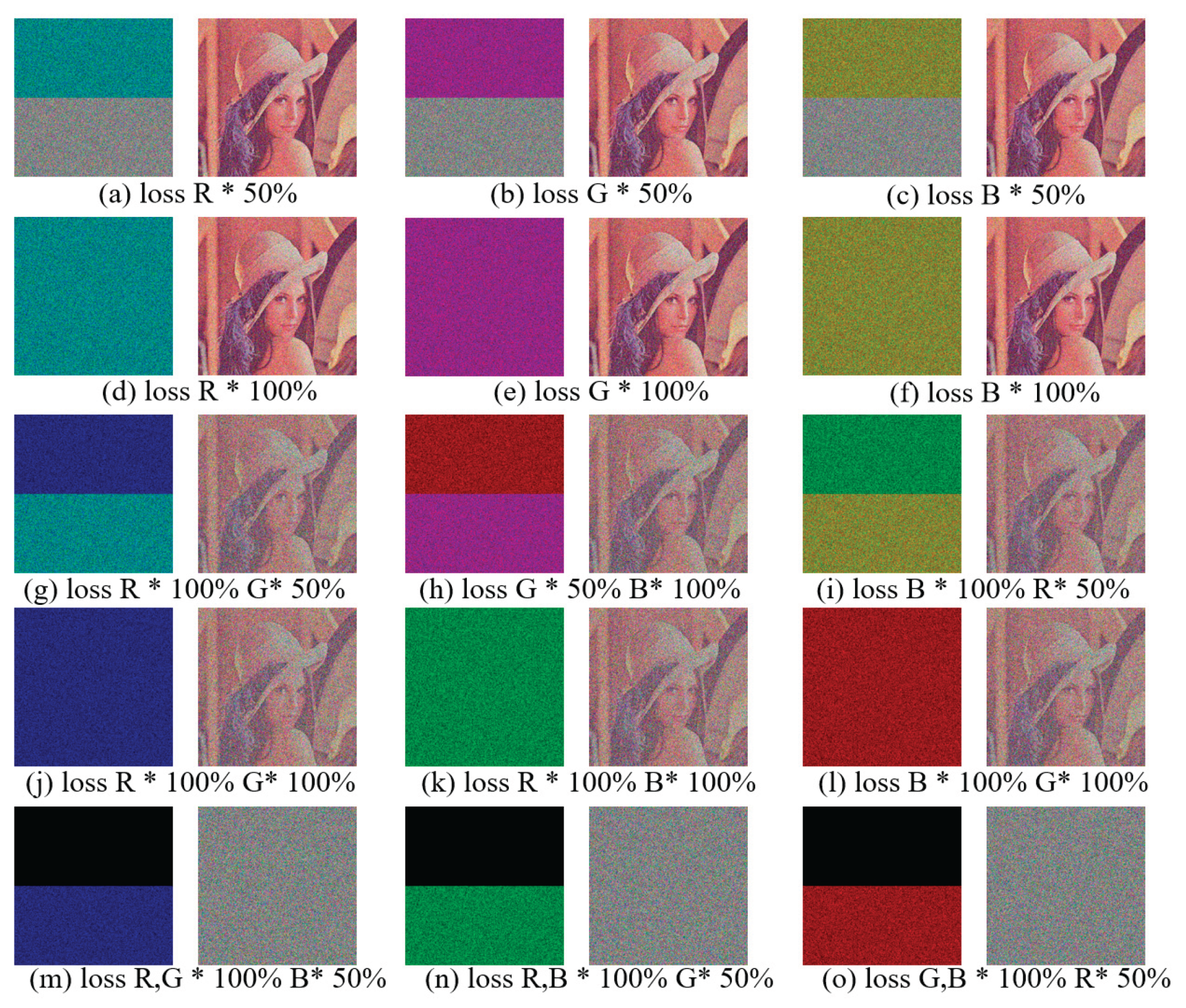
4.7. Noise and Shear Attack Test
4.8. Comparisons of Correlation Coefficient
| REF.# | Cor.R | Cor.G | Cor.B | Entropy.R | Entropy.G | Entropy.B | Key space |
|---|---|---|---|---|---|---|---|
| Original | 0.9794 | 0.9909 | 0.9745 | 7.3484 | 7.5866 | 7.0930 | - |
| [18] | −0.00006 | 0.0367 | 0.0247 | 7.7771 | 7.7190 | 7.7150 | - |
| [23] | -0.0016 | -0.0077 | -0.0002 | 7.9968(Modulo and XOR ) | |||
| [24] | -0.0014 | 0.0023 | 0.0015 | 7.9988(DNA) | - | ||
| [22] | -0.0053 | -0.0012 | 0.005 | 7.9973 | 2372 | ||
| [13] | -0.0119 | -0.0087 | -0.0045 | 7.7317 | 7.7864 | 7.6481 | (1015)16 |
| Bit24 | 0.00133 | 0.00191 | -0.0036 | 7.9994 | 7.9994 | 7.9993 | ∞ |
| OCT | -0.00177 | -0.00168 | -0.000499 | 7.7590 | 7.7503 | 7.7514 | ∞ |
| Theoretical value | 0 | 0 | 0 | 8 | 8 | 8 | ∞ |
5. Conclusions
References
- Zhang, Y.; Chen, A.; Tang, Y.; et al. plain-text-related image encryption algorithm based on perceptron-like network. Inf. Sci. 2020, 526, 180–202. [Google Scholar] [CrossRef]
- Hu, W.W.; Zhou, R.G.; Luo, J.; et al. Quantum image encryption algorithm based on Arnold scrambling and wavelet transforms. Quantum Inf. Process. 2020, 19, 1–29. [Google Scholar] [CrossRef]
- Farah, M.A.B.; Farah, A.; Farah, T. An image encryption scheme based on a new hybrid chaotic map and optimized substitution box. Nonlinear Dyn. 2020, 99, 3041–3064. [Google Scholar] [CrossRef]
- Trujillo-Toledo, D.A.; López-Bonilla, O.R.; García-Guerrero, E.E.; et al. Real-time RGB image encryption for IoT applications using enhanced sequences from chaotic maps. Chaos Solitons Fractals 2021, 153, 111506. [Google Scholar] [CrossRef]
- Xiong, Y.; Wang, Y. Cryptoanalysis on the optical image encryption scheme based on full phase encoding and equal modulus decomposition. Appl. Opt. 2022, 61, 2743–2749. [Google Scholar] [CrossRef]
- Inoue, K.; Cho, M. Amplitude based keyless optical encryption system using deep neural network. J. Vis. Commun. Image Represent. 2021, 79, 103251. [Google Scholar] [CrossRef]
- Guo, X.; Zhong, J.; Li, B.; et al. Full-color holographic display and encryption with full-polarization degree of freedom. Adv. Mater. 2022, 34, 2103192. [Google Scholar] [CrossRef]
- Wang, H.L.; Ma, H.F.; Cui, T.J. A Polarization-Modulated Information Metasurface for Encryption Wireless Communications. Adv. Sci. 2022, 9, 2204333. [Google Scholar] [CrossRef]
- Abuturab, M.R.; Alfalou, A. Multiple color image fusion, compression, and encryption using compressive sensing, chaotic-biometric keys, and optical fractional Fourier transform. Opt. Laser Technol. 2022, 151, 108071. [Google Scholar] [CrossRef]
- Zhang, Y.; Zhang, L.; Zhong, Z.; et al. Hyperchaotic image encryption using phase-truncated fractional Fourier transform and DNA-level operation. Opt. Lasers Eng. 2021, 143, 106626. [Google Scholar] [CrossRef]
- Li, Y.M.; Wei, D.; Zhang, L. Double-encrypted watermarking algorithm based on cosine transform and fractional Fourier transform in invariant wavelet domain. Inf. Sci. 2021, 551, 205–227. [Google Scholar] [CrossRef]
- Peng, D.; Huang, Z.; Liu, Y.; et al. Optical coherence encryption with structured random light. PhotoniX 2021, 2, 1–15. [Google Scholar] [CrossRef] [PubMed]
- Liu, Q.; Liu, L. Color image encryption algorithm based on DNA coding and double chaos system. IEEE Access 2020, 8, 83596–83610. [Google Scholar] [CrossRef]
- Javidi, B.; Zhang, G.; Li, J. Experimental demonstration of the random phase encoding technique for image encryption and security verification. Opt. Eng. 1996, 35, 2506–2512. [Google Scholar] [CrossRef]
- Javidi, B.; Sergent, A.; Zhang, G.; et al. Fault tolerance properties of a double phase encoding encryption technique. Opt. Eng. 1997, 36, 992–998. [Google Scholar] [CrossRef]
- Jeong, O.; Moon, I. Adaptive transfer learning-based cryptanalysis on double random phase encoding. Opt. Laser Technol. 2024, 168, 109916. [Google Scholar] [CrossRef]
- Zhang, R.; Xiao, D. Double image encryption scheme based on compressive sensing and double random phase encoding. Mathematics 2022, 10, 1242. [Google Scholar] [CrossRef]
- Faragallah, O.S.; Afifi, A.; Elashry, I.F.; et al. Efficient optical double image cryptosystem using chaotic mapping-based Fresnel transform. Opt. Quantum Electron. 2021, 53, 305. [Google Scholar] [CrossRef]
- Abd-El-Atty, B.; Iliyasu, A.M.; Alanezi, A.; et al. Optical image encryption based on Quantum walks. Opt. Lasers Eng. 2021, 138, 106403. [Google Scholar] [CrossRef]
- Wang, Y.; et al. Optical single-channel color image encryption based on chaotic fingerprint phase mask and diffractive imaging. Appl. Opt. 2023, 62.4, 1009–1018. [Google Scholar] [CrossRef]
- Hu, W.; Dong, Y. Quantum color image encryption based on a novel 3D chaotic system. J. Appl. Phys. 2022, 131, 114402. [Google Scholar] [CrossRef]
- Tian, P.; Su, R. A Novel Virtual Optical Image Encryption Scheme Created by Combining Chaotic S-Box with Double Random Phase Encoding. Sensors 2022, 22, 5325. [Google Scholar] [CrossRef] [PubMed]
- Yildirim, M. A color image encryption scheme reducing the correlations between R, G, B components. Optik 2021, 237, 166728. [Google Scholar] [CrossRef]
- Yildirim, M. Optical color image encryption scheme with a novel DNA encoding algorithm based on a chaotic circuit. Chaos Solitons Fractals 2022, 155, 111631. [Google Scholar] [CrossRef]
- Qin, W.; Peng, X. Asymmetric cryptosystem based on phase-truncated Fourier transforms. Opt. Lett. 2010, 35, 118–120. [Google Scholar] [CrossRef] [PubMed]
- Wang, X.; Zhao, D. A special attack on the asymmetric cryptosystem based on phase-truncated Fourier transforms. Opt. Commun. 2012, 285, 1078–1081. [Google Scholar] [CrossRef]
- Li, M.; et al. On the security of image cryptosystems using DRPE based on scrambling and diffusion. Opt. Quantum Electron. 2024, 56.2, 241. [Google Scholar] [CrossRef]
- Zhou, Q.; et al. Optical image encryption based on two-channel detection and deep learning. Opt. Lasers Eng. 2023, 162, 107415. [Google Scholar] [CrossRef]
- Singh, P.; Kumar, R.; Yadav, A.K.; et al. Security analysis and modified attack algorithms for a nonlinear optical cryptosystem based on DRPE. Optics and Lasers in Engineering, 2021, 139, 106501.
- Sun, G.; et al. A novel optical video cryptosystem based on improved 3D arnold transform in gyrator domains. Opt. Laser Technol. 2024, 168, 109891. [Google Scholar] [CrossRef]
- Hao, W.; Zhang, T.; Chen, X.; et al. A hybrid NEQR image encryption cryptosystem using two-dimensional Quantum walks and Quantum coding. Signal Process. 2023, 205, 108890. [Google Scholar] [CrossRef]
- Aharonov, D.; Ambainis, A.; Kempe, J.; et al. Quantum walks on graphs[C]//Proceedings of the thirty-third annual ACM symposium on Theory of computing. 2001: 50-59.
- Simonson, S. Public Key Cryptography. MAA NOTES 2005, 68, 109. [Google Scholar]
- Farah, M.A.B.; Farah, A.; Farah, T. An image encryption scheme based on a new hybrid chaotic map and optimized substitution box. Nonlinear Dyn. 2020, 99, 3041–3064. [Google Scholar] [CrossRef]
- Zhang, Y. A unified image cryptography based on a perceptron-like network. The Visual Computer, 2022: 1-16.
- Man, Z.; Li, J.; Di, X., et al. Double image encryption algorithm based on neural network and chaos. Chaos, solitons & fractals, 2021, 152, 111318.
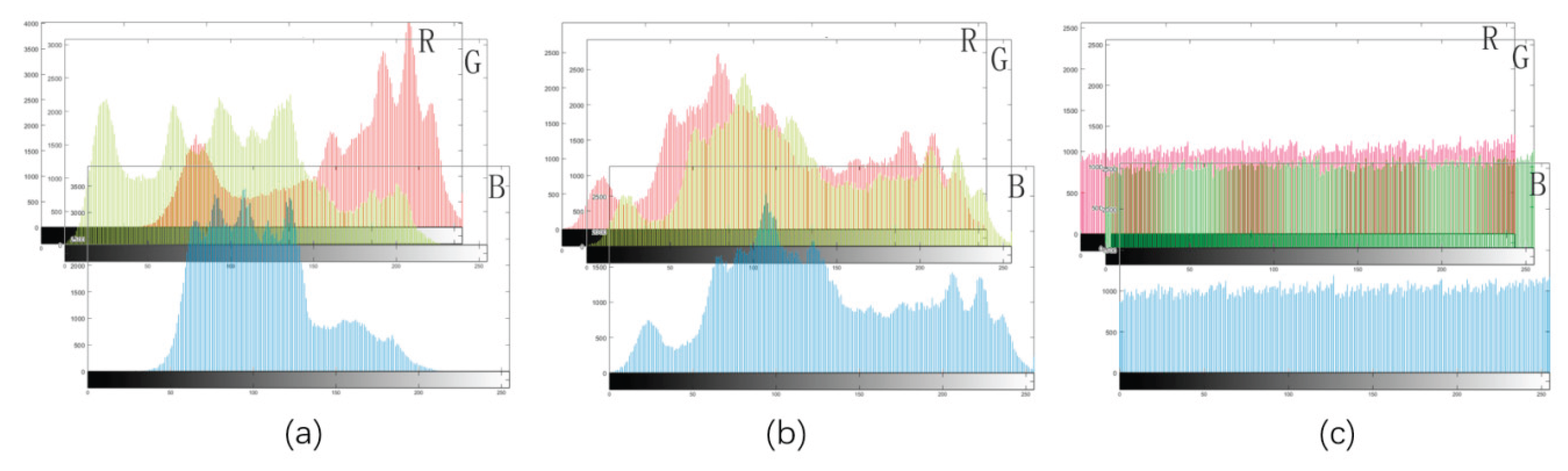
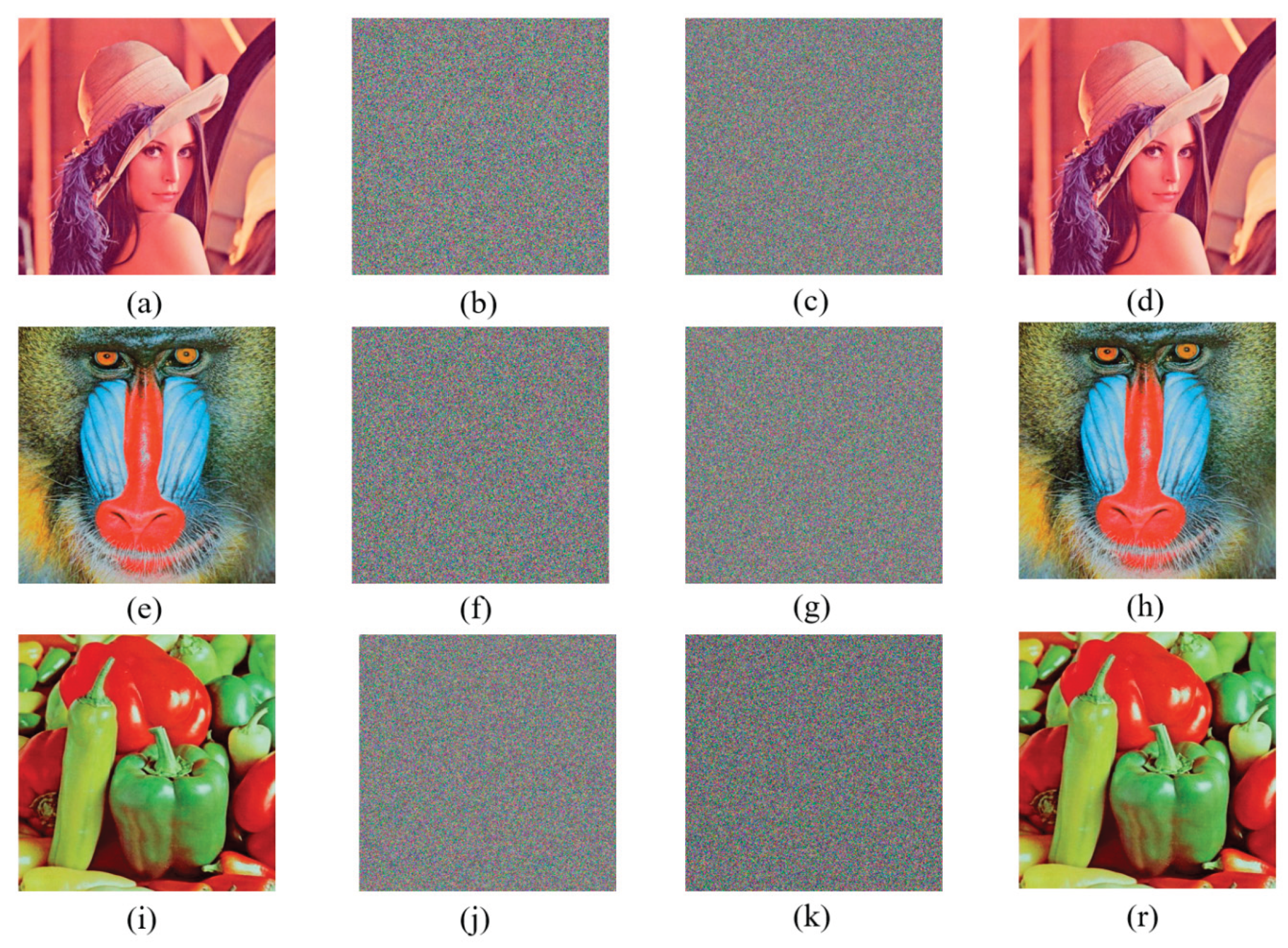



 |
| Fig | Correlation.R | Correlation.G | Correlation.B | ||||||
|---|---|---|---|---|---|---|---|---|---|
| H | V | D | H | V | D | H | V | D | |
| Figure 6(a) | 0.9811 | 0.9811 | 0.9677 | 0.9830 | 0.9703 | 0.9516 | 0.9592 | 0.9362 | 0.8999 |
| Figure 6(b) | -0.0075 | -0.0083 | 0.0036 | -0.0050 | 0.0003 | -0.0052 | -0.0016 | 0.0020 | -0.0140 |
| Figure 6(c) | 0.0006 | -0.0023 | -0.0016 | -0.0004 | -0.0017 | -0.0019 | -0.0003 | 0.0009 | 0.0020 |
| Figure 6(e) | 0.7707 | 0.8563 | 0.7524 | 0.7465 | 0.8443 | 0.7311 | 0.8567 | 0.9081 | 0.8369 |
| Figure 6(f) | -0.0097 | 0.0236 | -0.0036 | 0.0086 | -0.0125 | 0.0015 | 0.0051 | -0.0084 | -0.0230 |
| Figure 6(g) | 0.0025 | 0.0074 | 0.0019 | 0.0026 | -0.0014 | 0.0070 | 0.0275 | 0.0036 | -0.0025 |
| Figure 6(i) | 0.9772 | 0.9738 | 0.9587 | 0.9920 | 0.9892 | 0.9800 | 0.9749 | 0.9691 | 0.9427 |
| Figure 6(j) | 0.0013 | -0.0037 | 0.0045 | 0.0191 | 0.0066 | -0.002 | -0.0036 | 0.0200 | -0.0058 |
| Figure 6(k) | -0.0101 | 0.0055 | -0.0030 | -0.0320 | 0.0003 | 0.0040 | -0.0059 | 0.0016 | 0.0248 |
| Numble | Lena | Mandril | Papper | ||||||
|---|---|---|---|---|---|---|---|---|---|
| Figure 6(a) | Figure 6(b) | Figure 6(c) | Figure 6(e) | Figure 6(f) | Figure 6(g) | Figure 6(i) | Figure 6(j) | Figure 6(k) | |
| Entropy.R | 7.3484 | 7.9994 | 7.7590 | 7.7593 | 7.9994 | 7.7249 | 7.3484 | 7.9994 | 7.7191 |
| Entropy.G | 7.5866 | 7.9994 | 7.7503 | 7.4594 | 7.9993 | 7.7222 | 7.5866 | 7.9994 | 7.7215 |
| Entropy.B | 7.0930 | 7.9992 | 7.7514 | 7.7556 | 7.9994 | 7.7213 | 7.093 | 7.9992 | 7.7209 |
| Numble | Lena | Mandril | Papper | ||||||
| R | G | B | R | G | B | R | G | B | |
| UACI | 99.6217 | 99.6016 | 99.5987 | 99.6033 | 99.5867 | 99.5865 | 99.5986 | 99.5879 | 99.5942 |
| NPCR | 33.6643 | 33.3611 | 33.3695 | 33.5258 | 33.3890 | 33.3780 | 33.4928 | 33.3977 | 33.4915 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





