Submitted:
20 December 2023
Posted:
21 December 2023
You are already at the latest version
Abstract
Keywords:
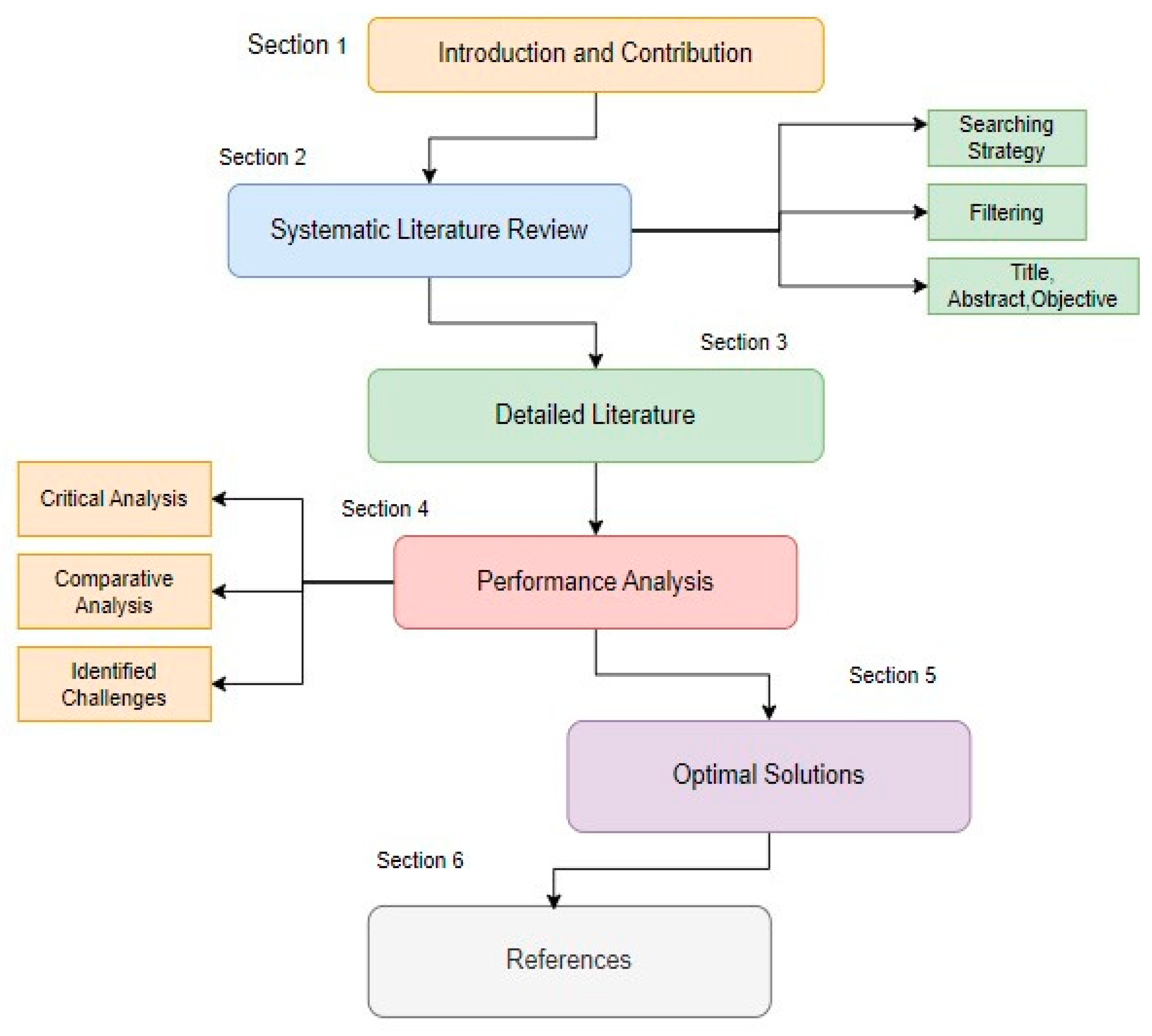
1. Introduction
2. Systematic Literature Review
2.1. String Development
| WORDS | SYNONYM 1 | SYNONYM 2 | SYNONYM 3 |
|---|---|---|---|
| Secure | Protected | Riskless | Encapsulated |
| Logistics | Supply chain | Transportation | Management |
| Monitoring | Observed | Track | Check |
| Secure | Protected | Riskless | Encapsulated |
|---|---|---|---|
| Secure logistics monitoring system based on wireless sensor network. | |||
| Protected logistics monitoring system based on wireless sensor network. | |||
| Encapsulated logistics monitoring system based on wireless sensor network. | |||
| Riskless logistics monitoring system based on wireless sensor network. | |||
| Secure Supply chain monitoring system based on wireless sensor network. | |||
| Secure transportation monitoring system based on wireless sensor network | |||
| Secure management monitoring system based on wireless sensor network. | |||
| Protected transportation system based on wireless sensor network. | |||
| Protected management system based on wireless sensor network. | |||
| Protected supply chain system based on wireless sensor network. | |||
| Encapsulated management consisting the track using wireless sensor network. | |||
| Encapsulated transportation system observed using wireless sensor network. | |||
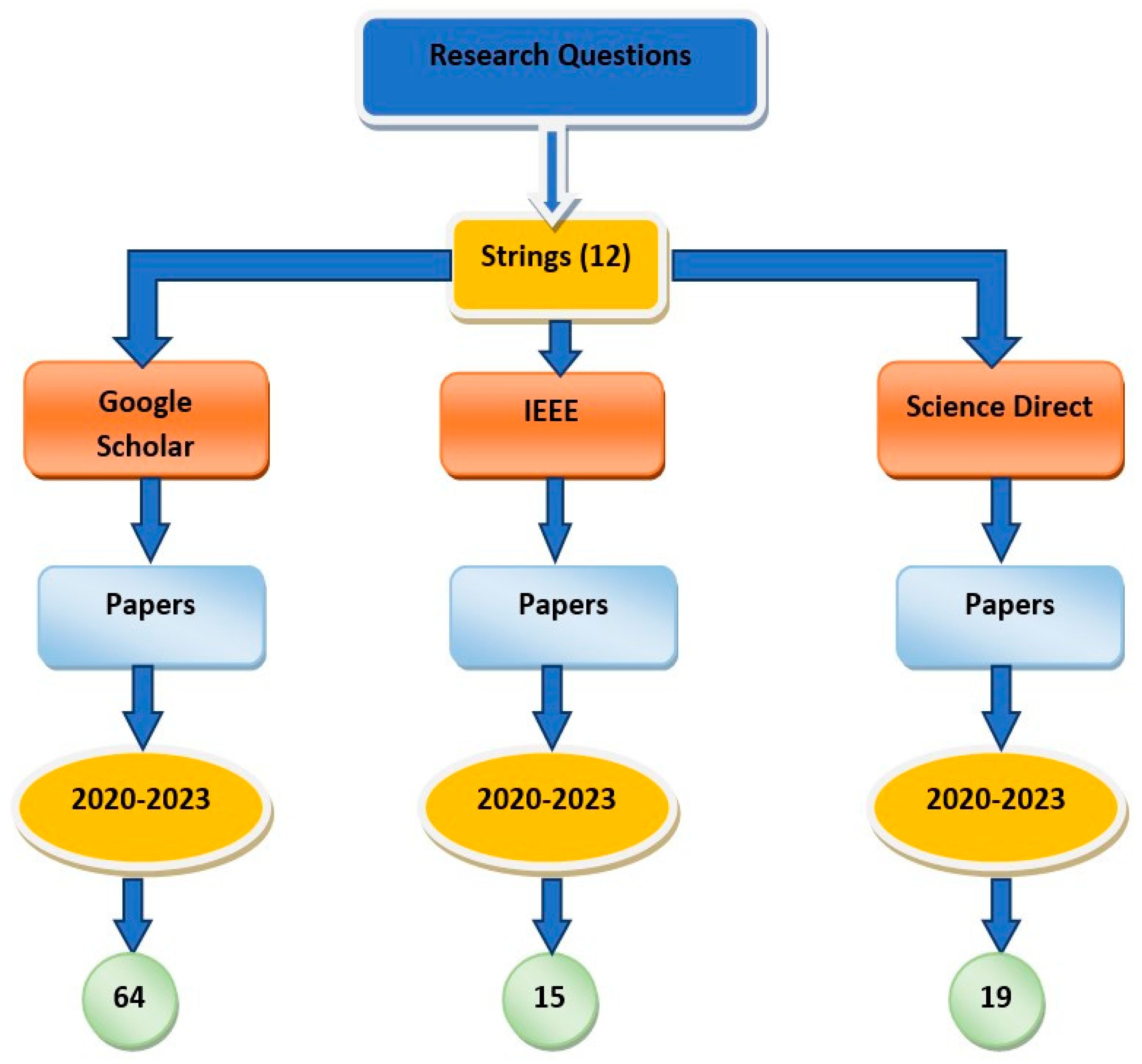
2.2. Searching Protocol:
2.3. Inclusion Criteria
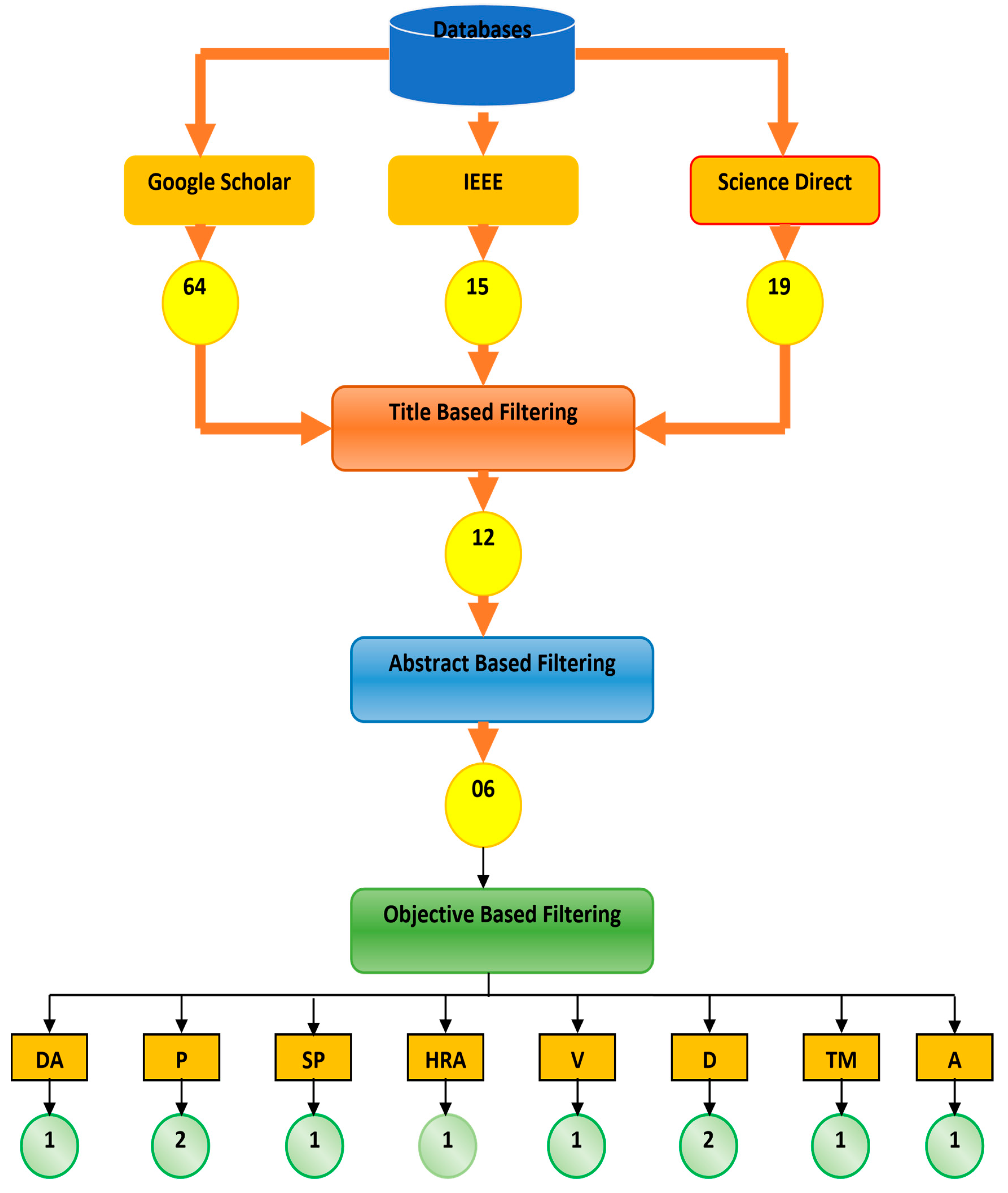
2.4. Filtering
| Ref. | DA | P | SP | HRA | V | D | TM | A |
|---|---|---|---|---|---|---|---|---|
| [1] | ✔ | ▪ | ▪ | ▪ | ▪ | ▪ | ▪ | ▪ |
| [2] | ▪ | ✔ | ▪ | ▪ | ▪ | ▪ | ▪ | ▪ |
| [3] | ▪ | ▪ | ✔ | ✔ | ▪ | ▪ | ▪ | ▪ |
| [4] | ▪ | ▪ | ▪ | ▪ | ✔ | ✔ | ▪ | ▪ |
| [5] | ▪ | ▪ | ▪ | ▪ | ▪ | ✔ | ✔ | ✔ |
| [6] | ▪ | ✔ | ▪ | ▪ | ▪ | ▪ | ▪ | ▪ |
3. Detailed Literature
| Ref. | Technique | Methodology |
|---|---|---|
| [5] | Intrusion Detection System (IDS) | IDS strategies for WSN are categorized according to the method used to identify attacks. the classification of security threats, several IDS detection methods, and performance criteria for evaluating the IDS algorithm for WSNs. |
| [6] | Entropy weight fuzzy comprehensive evaluation method |
To evaluate the platform planning scheme, use a fuzzy, comprehensive evaluation approach with entropy weight. The wireless network uses a multizone network networking technique to segment the overall coverage area into several smaller regions. Control of a sub-area is the responsibility of each wireless access point. Each wireless access point will also transform into a mobile terminal and the backbone of the network at the same time. |
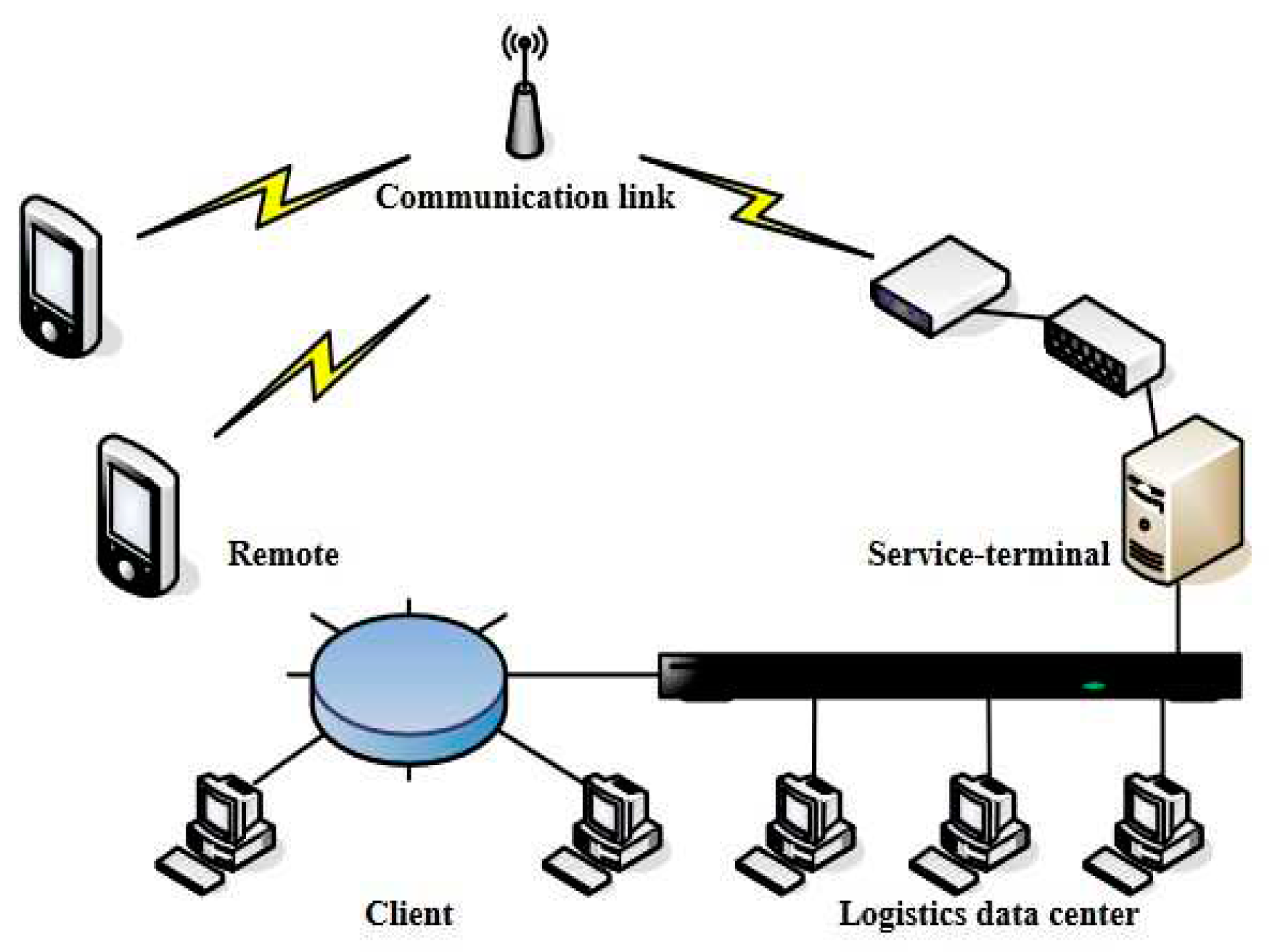
| [7] | RFID technology | Wireless sensor network software and hardware are the foundation upon which WSN and RFID are constructed, and it is here that the intricate design of the logistics supply chain management system business process is mostly completed. The information management process of conventional logistics company, including access, storage positioning and monitoring, and distribution monitoring and management, is realized when the two primary approaches suggested in this article are combined. The management system is tested on this basis. |
| [8] |
Radio frequency identification (RFID) technology and Service (DaaS) billing scheme |
To detect and trace the conditions of food while it is being transported, the RFID layer incorporates temperature sensors inside RFID tags. The cost implementation difficulties are handled using the Data as a Service (DaaS) pricing model, which avoids the significant initial investment that these high-tech solutions frequently need by charging customers only for the data they use, rather than for the installed equipment. |
| [9] | JAVA technology | For design and development, the JAVA technology platform is chosen, the SQL Server database is chosen for the system's backend, and a straightforward and user-friendly WEB interface is built for the system's user service side to satisfy the demands of a userfriendly environment. The system's implementation also contributes in certain theoretical and practical ways to the design and advancement of related logistics tracking information management systems based on wireless sensor networks. |
| [10] | Wolf group algorithm | We gather and compute logistics data using the wolf group algorithm's hunting and siege formula, and then we examine how well the logistics supervision system really performs in practice. |
4. Performance Analysis
4.1. Critical Analysis
|
Detection Algorithm |
Effort Year |
Technique | Short coming |
|---|---|---|---|
| [5] | 2020 | Intrusion Detection System (IDS) | Inability to respond or stop attacks upon detection [11] Scalability issue [12] |
| [6] | 2021 | Entropy weight fuzzy comprehensive evaluation method | Difficulty in determining weights and limited to quantitative data [13] Security Vulnerabilities [14] |
| [7] | 2023 | RFID technology | Not as accurate, reliable expensive or Compatibility issues [15] Cost and Scalability [16] |
| [8] | 2023 | Radio frequency identification (RFID) technology and Service (DaaS) billing scheme | RFID is less precise and reliable. Expensive. The cost of the service (DaaS) pricing model is greater, and there is less customization and control [17]. To prevent unauthorized access and data breaches in such systems, security and privacy safeguards must be developed [18]. |
| [9] | 2023 | JAVA technology | It is very slow and has restrictions on platforms [19] The algorithm may still spend a lot of energy if it is not energy-efficient, which might shorten the life of WSN nodes and decrease the efficiency of the system [20]. |
| [10] | 2021 | Wolf group algorithm | Lack of privacy and security. Cost-effectiveness [21] To defend the system from cyber- attacks, it is crucial to establish strong security measures including encryption, access control, and data backup. [22] |
| Ref. | Research Gaps | Solutions |
|---|---|---|
| [5] | Low Scalability issue | Hierarchical IDS architecture that uses a clustering algorithm |
| [13] | Difficult weight determination | Load cell sensor and a calibration method |
| [14] | High Security Vulnerabilities | Advanced Encryption Standard (AES) to secure |
| [20] | Low optimization and reduced effectiveness | Integration with other systems |
| [21] | Issue of security and privacy | Wolf group algorithm |
Conclusion
References
- Elsisi, M.; Mahmoud, K.; Lehtonen, M.; Darwish, M.M.F. Reliable Industry 4. 0 Based on Machine Learning and IoT for Analyzing, Monitoring, and Securing Smart Meters. Sensors 2021, 21, 487. [Google Scholar]
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- WSN based Online Parameter Monitoring in Cold Storage Warehouses in Cloud using IOT concepts Bindu J, Nikitha, Namitha, Pradeep H, International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 05 Issue: 07 | July-2018 www.irjet.net p-ISSN: 2395-0072.
- Li, F. R. Yu, G. Deng, C. Luo, Z. Ming, and Q. Yan, “Industrial Internet: A survey on the enabling technologies, applications, and challenges,” IEEE Commun. Surveys Tuts. 2017, 19, 1504–1526.
- S. Godala, R. Prasad, and V. Vaddella, “An Intrusion Detection System in Wireless Sensor Networks,” Int. J. Commun. Netw. Inf. Secur. IJCNIS 2020, 12, 127–141. [CrossRef]
- “Intelligent Logistics Tracking System Based on Wireless Sensor Network,” Int. J. Front. Eng. Technol.; 2021, 3. [CrossRef]
- “Optimization of Intelligent Logistics Supply Chain Management System Based on Wireless Sensor Network and RFID Technology.” Available online:. Available online: https://www.hindawi.com/journals/js/2021/8111909/ (accessed on 28 February 2023).
- “Sensors | Free Full-Text | Cost-Effective Implementation of a Temperature Traceability System Based on Smart RFID Tags and IoT Services.” Available online:. Available online: https://www.mdpi.com/14248220/20/4/1163 (accessed on 28 February 2023).
- “Using Wireless Sensor Network to Remote Real-Time Monitoring and Tracking of Logistics Status Based on Difference Transmission Algorithm.” Available online: https://www.hindawi. 28 February 2021.
- “Construction of a Supply Chain Financial Logistics Supervision System Based on Internet of Things Technology.” https://www.hindawi.com/journals/mpe/2021/9980397/ (accessed Mar. 04, 2023).
- Wang, C.; Li, J.; Zhang, H. An Intrusion Detection System in Wireless Sensor Networks. Journal of Physics: Conference Series, 2018, 1101, 012027. [Google Scholar]
- Kshetri, N.; Voas, J.; An, Y. Intrusion detection in wireless sensor networks: A comprehensive review. Journal of Network and Computer Applications 2019, 125, 60–78. [Google Scholar] [CrossRef]
- Jing, Z.; Li, J.; Li, J.; Li, X. Design and Implementation of Intelligent Logistics Tracking System Based on Wireless Sensor Network. 2016 IEEE 2nd International Conference on Big Data Analysis (ICBDA), 2016, 16-19.
- Zhang, X.; Wang, K.; Xiang, T.; Zhao, M. A survey on wireless sensor network-based intelligent logistics tracking systems. Journal of Network and Computer Applications 2020, 168, 102711. [Google Scholar] [CrossRef]
- Tang, J.; Yan, X.; Feng, Q. Research on the Interoperability of RFID Technology in Supply Chain Management. In Proceedings of the International Conference on Logistics, Informatics and Service Sciences (LISS) IEEE. 2014; pp. 25–28. [Google Scholar]
- Shi, Y.; Yuan, Q.; Cao, H.; Cui, L. Optimization of logistics supply chain management system based on wireless sensor network and RFID technology: A review. Journal of Ambient Intelligence and Humanized Computing 2021, 12, 2843–2863. [Google Scholar] [CrossRef]
- Kumar, A.; Garg, S. A cost-effective implementation of temperature traceability system based on smart RFID tags and IoT services. Journal of Food Science and Technology 2020, 57, 467–475. [Google Scholar] [CrossRef]
- Xu, S.; Cheng, S.; Zhou, Y. Security and privacy challenges in RFID and IoT-based temperature monitoring systems. Sensors 2021, 21, 745. [Google Scholar] [CrossRef]
- Xu, Q.; Qiu, Y.; Yan, L.; Lu, H. Design of wireless sensor network for remote real-time monitoring and tracking of logistics status based on difference transmission algorithm. International Journal of Distributed Sensor Networks 2017, 13, 1550147717723741. [Google Scholar] [CrossRef]
- Huang, Y.; Yu, H.; Wu, J. An energy-efficient differential data transmission scheme for wireless sensor networks. Sensors 2020, 20, 3739. [Google Scholar] [CrossRef]
- Zhang, Z.; Wang, J.; Zhang, S.; Song, H. Construction of a supply chain financial logistics supervision system based on internet of things technology. International Journal of Distributed Sensor Networks 2020, 16, 1550147720913349. [Google Scholar] [CrossRef]
- Kamble, S. S.; Saini, S.; Patel, R. A review on IoT-based supply chain management system: Challenges, applications, and future scope. Journal of Industrial Integration and Management 2021, 6, 21–40. [Google Scholar] [CrossRef]
- Amin, R.; Islam SK, H.; Biswas, G.P.; et al. Design of an anonymity-preserving threefactor authenticated key exchange protocol for wireless sensor networks[J]. Computer Networks, 2016, 101, 42–62. [Google Scholar] [CrossRef]
- Ding X, Tian Y, Yu Y, A Real-Time Big Data Gathering Algorithm Based on Indoor Wireless Sensor Networks for Risk Analysis of Industrial Operations[J]. IEEE Transactions on Industrial Informatics 2016, 12, 1232–1242. [CrossRef]
- Hussain, K.; Hussain, S.J.; Jhanjhi, N.Z.; Humayun, M. SYN flood attack detection based on bayes estimator (SFADBE) for MANET. In 2019 International Conference on Computer and Information Sciences (ICCIS) IEEE.2019, pp. 1-4.
- Adeyemo Victor Elijah, Azween Abdullah, NZ JhanJhi, Mahadevan Supramaniam and Balogun Abdullateef O, “Ensemble and Deep-Learning Methods for Two-Class and Multi-Attack Anomaly Intrusion Detection: An Empirical Study” International Journal of Advanced Computer Science and Applications(IJACSA) 2019, 10. [CrossRef]
- Lim, M.; Abdullah, A.; Jhanjhi, N. Z. Performance optimization of criminal network hidden link prediction model with deep reinforcement learning. Journal of King Saud University-Computer and Information Sciences 2021, 33, 1202–1210. [Google Scholar] [CrossRef]
- Kumar, T.; Pandey, B.; Mussavi, S.H.A.; Zaman, N. CTHS based energy efficient thermal aware image ALU design on FPGA. Wireless Personal Communications 2015, 85, 671–696. [Google Scholar] [CrossRef]
- Diwaker, C.; Tomar, P.; Solanki, A.; Nayyar, A.; Jhanjhi, N. Z.; Abdullah, A.; Supramaniam, M. A new model for predicting component-based software reliability using soft computing. IEEE Access 2019, 7, 147191–147203. [Google Scholar] [CrossRef]
- Hussain, S. J.; Ahmed, U.; Liaquat, H.; Mir, S.; Jhanjhi, N. Z.; Humayun, M. IMIAD: intelligent malware identification for android platform. In 2019 International Conference on Computer and Information Sciences (ICCIS) IEEE. 2019, pp. 1-6.
- Humayun, M.; Alsaqer, M. S.; Jhanjhi, N. Energy optimization for smart cities using iot. Applied Artificial Intelligence 2022, 36, 2037255. [Google Scholar] [CrossRef]
- Ghosh, G.; Verma, S.; Jhanjhi, N. Z.; Talib, M. N. Secure surveillance system using chaotic image encryption technique. IOP conference series: materials science and engineering 2020, 993, 012062. [Google Scholar]
- Almusaylim, Z. A.; Zaman, N.; Jung, L. T. Proposing a data privacy aware protocol for roadside accident video reporting service using 5G in Vehicular Cloud Networks Environment. In 2018 4th International conference on computer and information sciences (ICCOINS) IEEE. 2018, pp. 1-5).
- Wassan, S.; Chen, X.; Shen, T.; Waqar, M.; Jhanjhi, N. Z. Amazon product sentiment analysis using machine learning techniques. Revista Argentina de Clínica Psicológica 2021, 30, 695. [Google Scholar]
- Shahid, H.; Ashraf, H.; Javed, H.; Humayun, M.; Jhanjhi, N. Z.; AlZain, M. A. Energy optimised security against wormhole attack in iot-based wireless sensor networks. Comput. Mater. Contin, 2021, 68, 1967–81. [Google Scholar] [CrossRef]
| Years | Main Focus | Major Contribution |
Developments in Our Paper |
|---|---|---|---|
| 2021 | Focus on develop and implement a smart and secure logistics system. | [1] the development and implementation of a smart and secure logistics system based on IoT and cloud technologies, which can optimize logistics processes and enhance supply chain security. However, it may be the need for further evaluation of the economic feasibility and cost- effectiveness of the proposed system and further investigation of the system's scalability and applicability in different logistics contexts. |
Our research could evaluate the scalability of the proposed logistics system by examining its ability to handle increasing volumes of data and users |
| 2020 | Analyze the current state-of-the-art security solutions for IoT systems using a layered architecture approach. |
The study of [2] is proposing a layered security architecture approach for IoT systems that integrates security mechanisms at multiple layers. The gaps identified include lack of standardized security protocols, limited attention to privacy concerns, and inadequate consideration of physical | Our survey presents proposing a layered security architecture approach for IoT systems and evaluating its potential impact on enhancing the security of IoT systems. |
| security measures. | |||
| 2020 | To review and analyze the current state-of-the-art solutions for monitoring the cold chain using IoT technologies. |
The research paper [3] is to provide a comprehensive survey of the existing IoT-based solutions for cold storage monitoring, and to identify the strengths, weaknesses, opportunities, and threats of these solutions. However, it does not provide a detailed analysis of the economic feasibility and cost- effectiveness of these solutions in different practical scenarios. |
Our research presents the use of temperature and humidity sensors to monitor the condition of goods during transportation, and the use of cloud-based systems for data analysis and decision-making. |
| 2021 | To provide a comprehensive review of the applications of IoT in the field of smart logistics, including the challenges, opportunities, and future directions. |
The paper [4] identifies various applications of IoT in smart logistics and discusses their benefits, challenges, and future directions. However, it does not provide a detailed analysis of the technical aspects of these applications. Additionally, it does not cover some important topics such as security and privacy concerns in IoT-based smart logistics systems. | Our survey includes identifying the various applications of IoT in smart logistics, exploring the benefits and challenges of IoT in logistics, and proposing potential solutions for secure logistics monitoring based on IoT technology. |
| Acronyms | Definition |
|---|---|
| DA | Detecting Attack |
| P | Performance |
| SP | Storage positioning |
| HRA | High recognition accuracy |
| V | Validation |
| D | Design |
| TM | Time management |
| A | Accuracy |
| IDS | Intrusion Detection System |
| EWFEM | Entropy weight fuzzy evaluation method |
| RFID | Radio frequency identification |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).





