Submitted:
06 November 2023
Posted:
08 November 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
- we elaborated the SLR protocol, which can be used to replicate or update this study in the future;
- we selected and reviewed 142 papers considering they explore security threats, vulnerabilities, or solutions for 5G-IoT environments;
- we analyzed and presented the information extracted from the selected papers, classifying threats, vulnerabilities, and solutions;
- we present the state-of-the-art related to security issues in 5G-IoT scenarios.
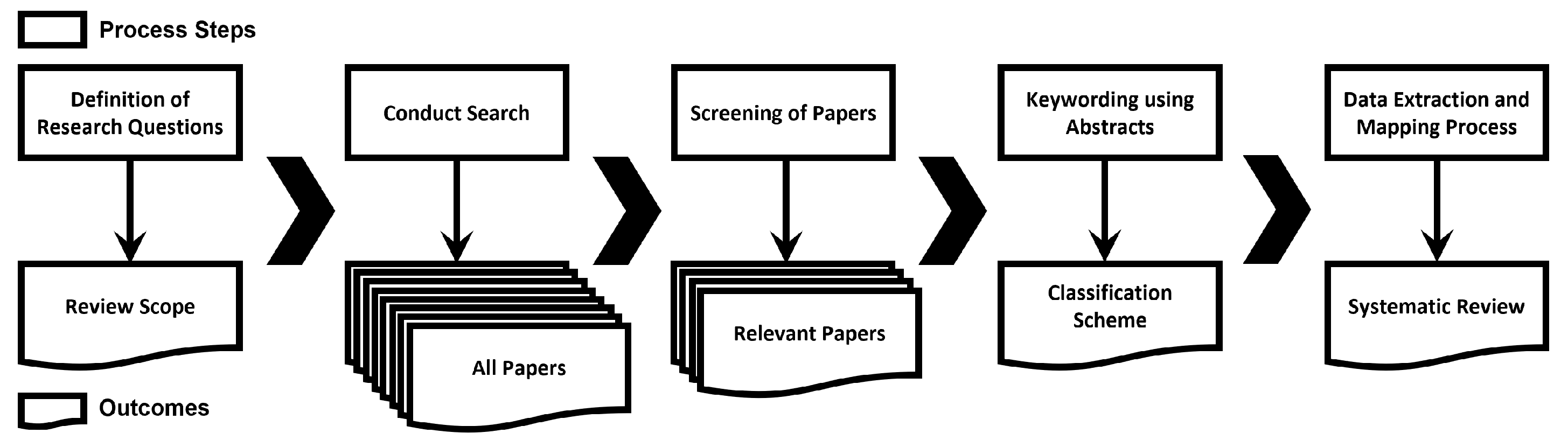
2. Research Protocol
2.1. Research Questions
- RQ1: What are the known vulnerabilities in the 5G-IoT context? Rationale: This question seeks to identify the vulnerabilities listed in the literature in the context of 5G-IoT applications.
- RQ2: What are the known threats in the 5G-IoT context? Rationale: We seek to classify the known threats in the 5G-IoT context and understand how they affect these environments.
- RQ3: What are the recommendations and proposed solutions to mitigate the vulnerabilities and threats listed in the literature? Rationale: This question aims to present the recommendations and proposed solutions to mitigate the known vulnerabilities and threats in IoT and 5G environments and the best practices to build secure applications in these contexts.
2.2. Search Strategy
2.3. Search String
( “Internet of Everything” OR “Internet of Things” OR “IoE” OR “IoT” )
AND
( “Solution” OR “Architecture” OR “Framework” OR “Platform” OR “System” OR “Threat” OR “Vulnerability” )
AND
( “Confidentiality” OR “Integrity” OR “Privacy” OR “Protection” OR “Security” OR “Trustworthiness” )
AND
( “5G” )
2.4. Search Repositories
2.5. Selection Criteria
- IC1: Papers that present vulnerabilities in 5G-IoT context;
- IC2: Papers that present threats in 5G-IoT context;
- IC3: Papers that present solutions to mitigate vulnerabilities and threats in 5G-IoT context;
- IC4: Papers that present recommendations to improve the security of applications in 5G-IoT contexts;
- IC5: When several papers show similar studies, only the most recent is included;
- IC6: If there are versions of the same paper, the most complete must be included.
- EC1: Posters, short articles, and expanded abstracts (articles with less than three pages);
- EC2: Book chapters;
- EC3: Articles not written in English;
- EC4: Articles that do not focus on security;
- EC5: Duplicate results;
- EC6: Articles published before the year 2010 (beginning of work for 5G development).
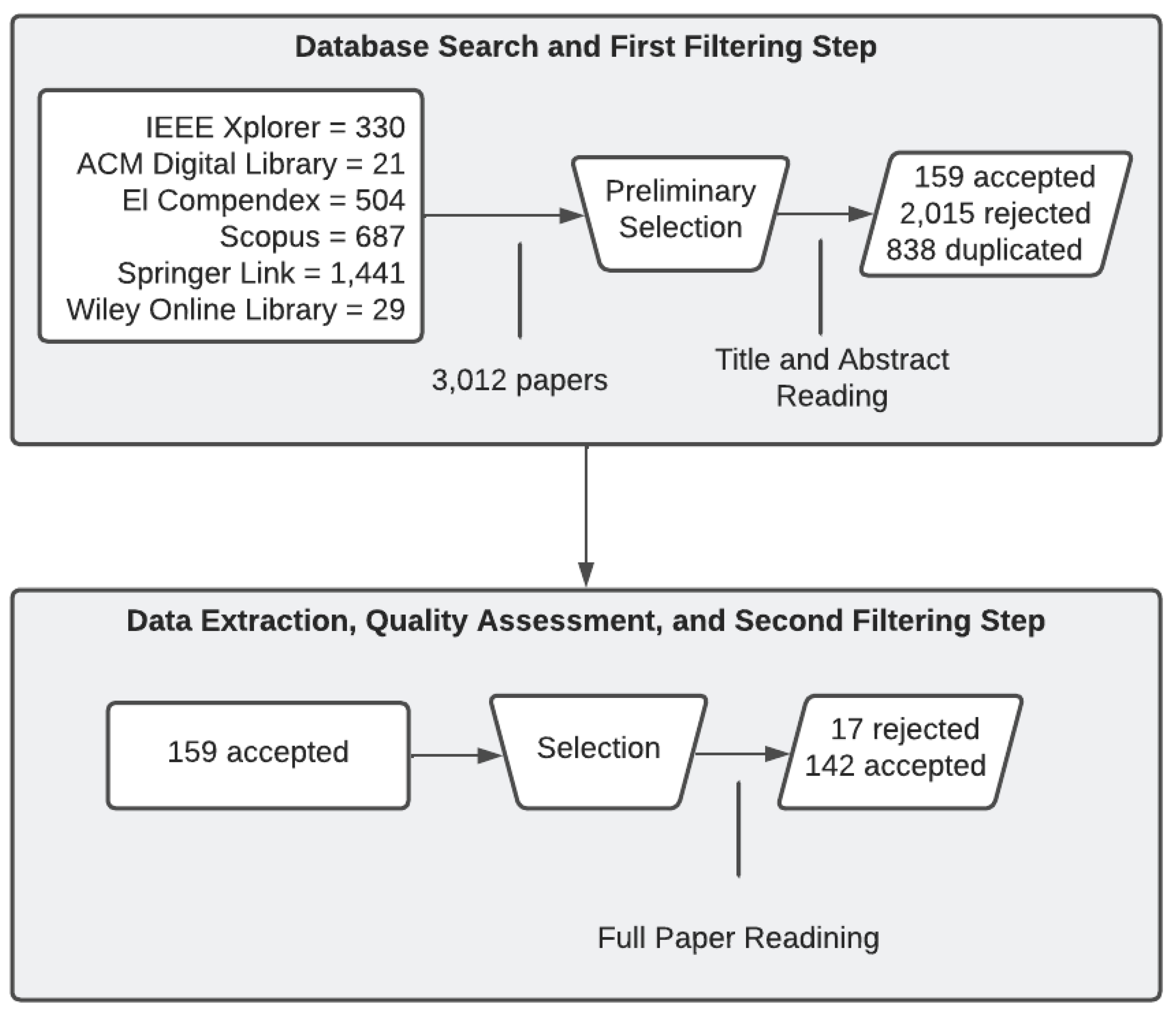
2.6. Selection Procedure
- Delete duplicate documents;
- Exclude documents published before the year 2010 or documents not written in English;
- Exclude documents not published in journals or conferences;
- Exclude dissertations and theses, expanded abstracts, summary articles, and posters;
- Exclude irrelevant documents, i.e., documents that do not help to answer the research questions.
- Each reviewer classifies the document as relevant, irrelevant, or undefined;
- Documents classified as relevant by two reviewers are kept;
- Documents classified as irrelevant by two reviewers are excluded;
- Documents classified as undefined by two reviewers are better analyzed through a quick reading of the complete document, and then they are reclassified as relevant or irrelevant;
- Documents classified as relevant or undefined by one reviewer and irrelevant by another are discussed between both until they reach a consensus on one of the previous classifications.
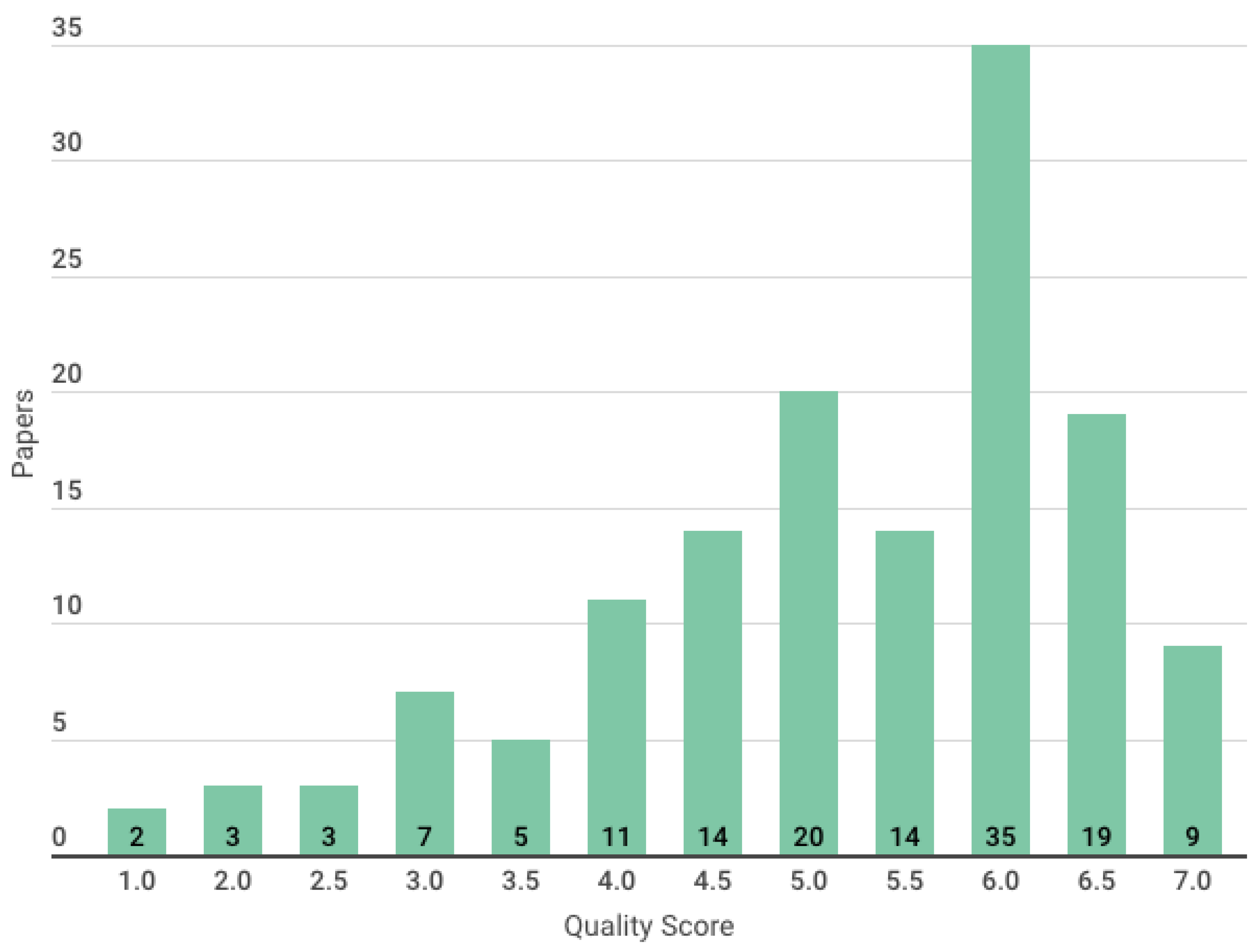
2.7. Quality Assessment
- Is the text well organized and clear (easy to understand)?
- Are motivation and goals well described?
- Is the methodology clear (easy to understand and replicate)?
- Is the document well-referenced, and does it present good related work?
- Does the document present threats, vulnerabilities, or solutions?
- Do the authors present a good discussion of the topics covered in the document?
- Are there any suggestions for future work?
- Yes 1;
- Moderate - 0.5;
- No - 0.
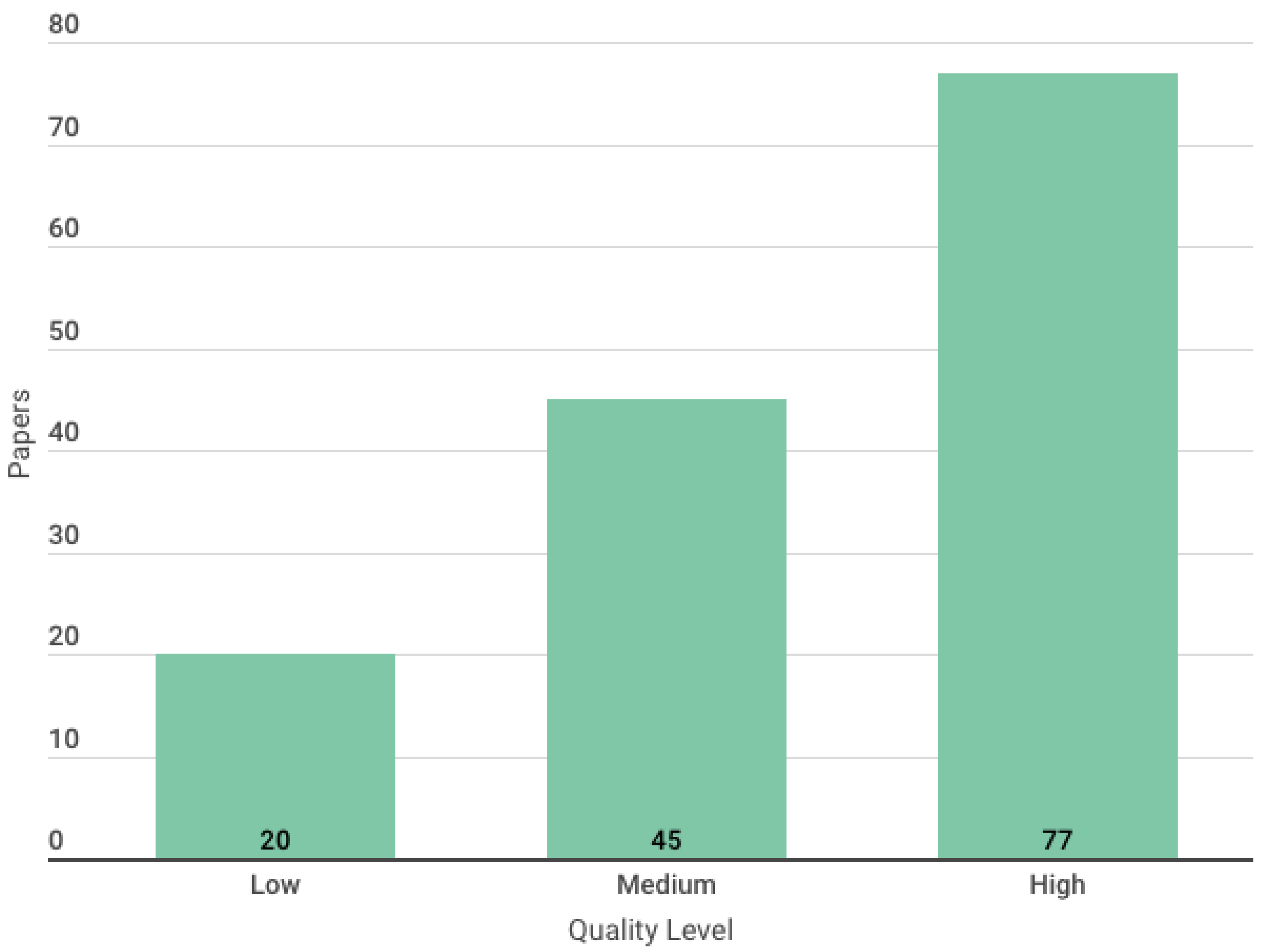
- High quality, if the score is 5.5 or higher;
- Medium quality, if the score is between 3.5 and 5.5;
- Low quality if the score is less than or equal to 3.5.
2.8. Data Extraction
- Title
- Authors
- Abstract
- Year
- Article type
- Name of Conference/Journal
- Country(s) where the research was performed
- Number of pages
- Number of citations
- Quality
- List of threats
- List of vulnerabilities
- List of solutions
- List of essential definitions/terms
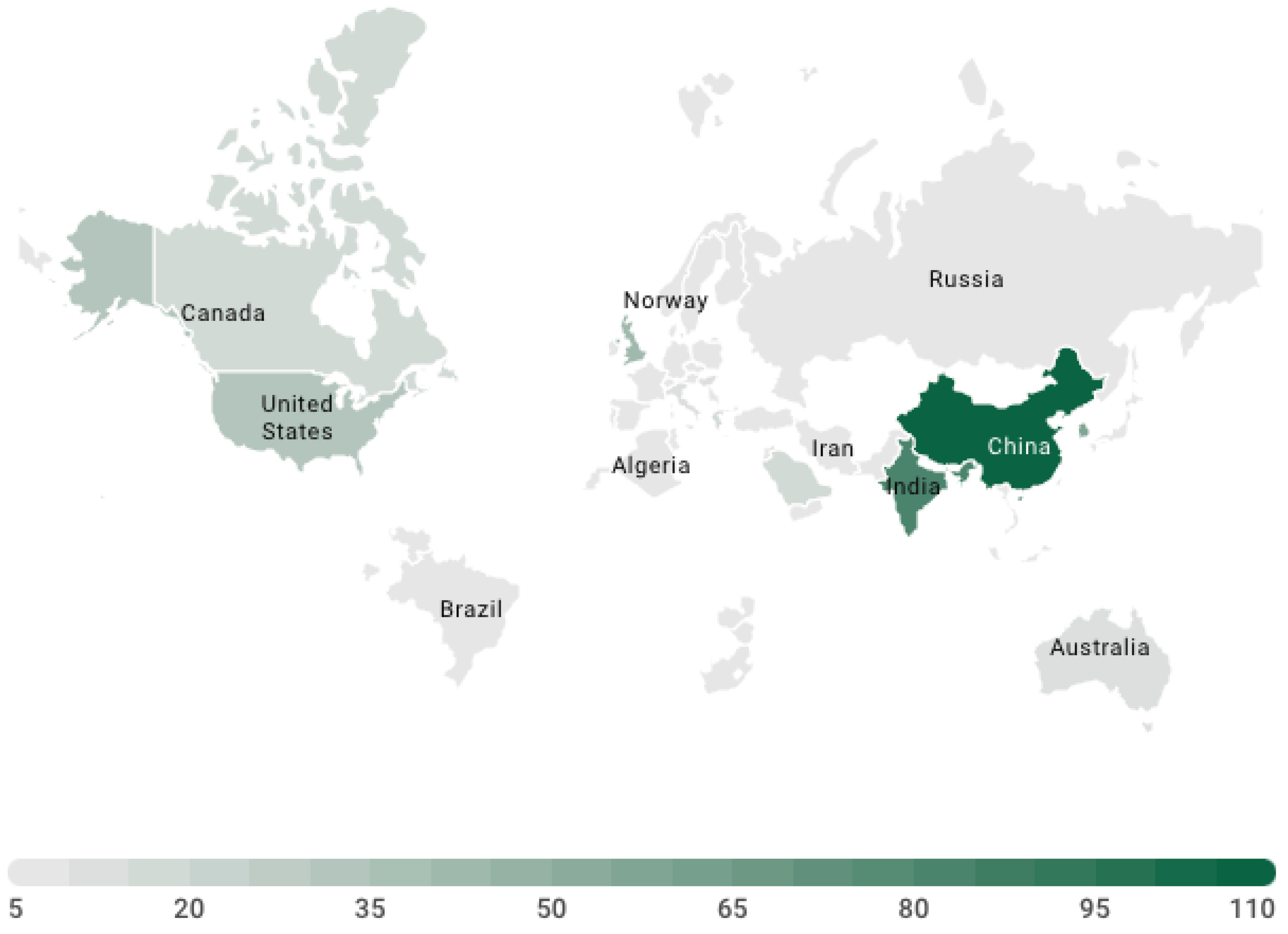
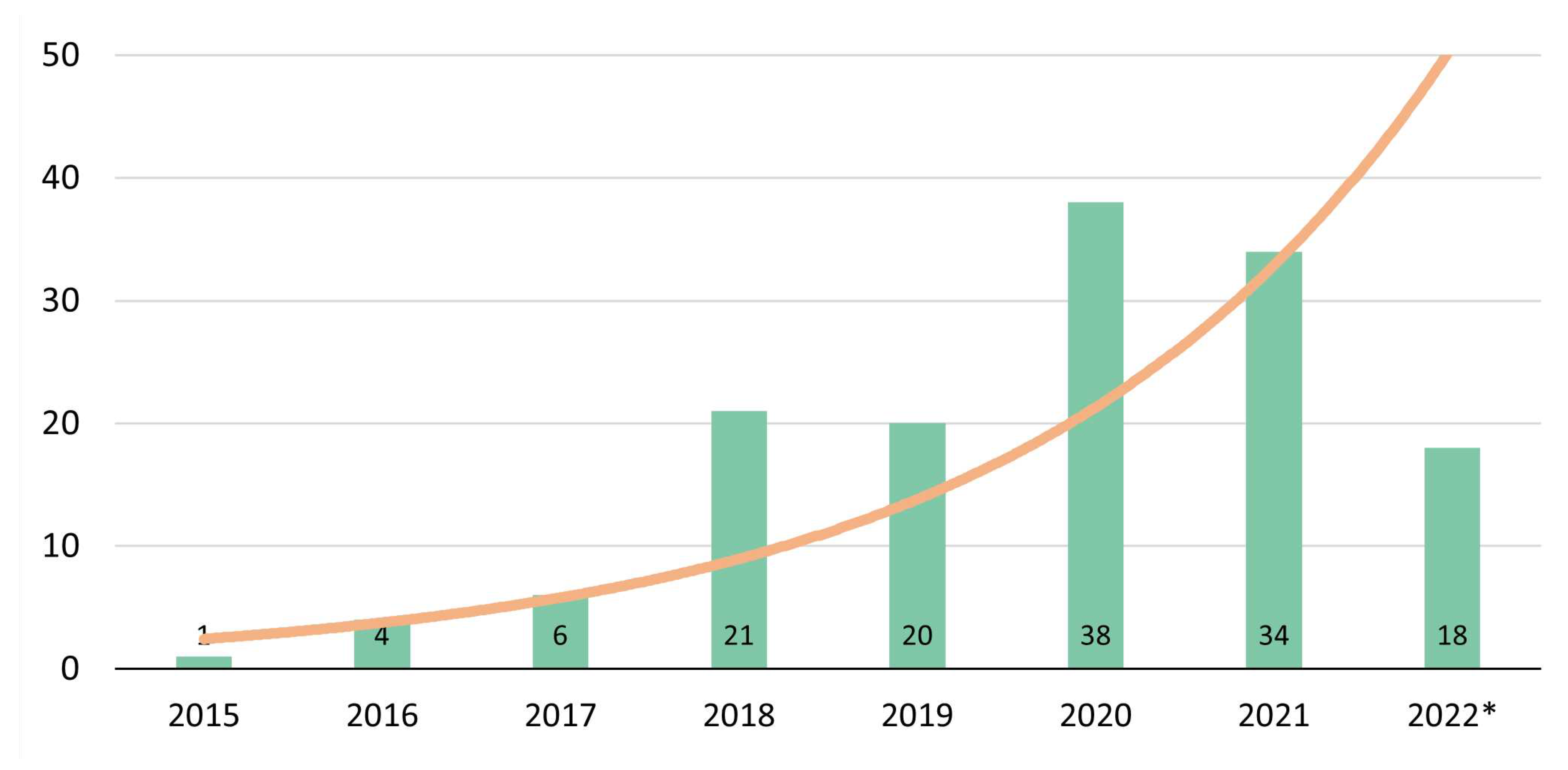
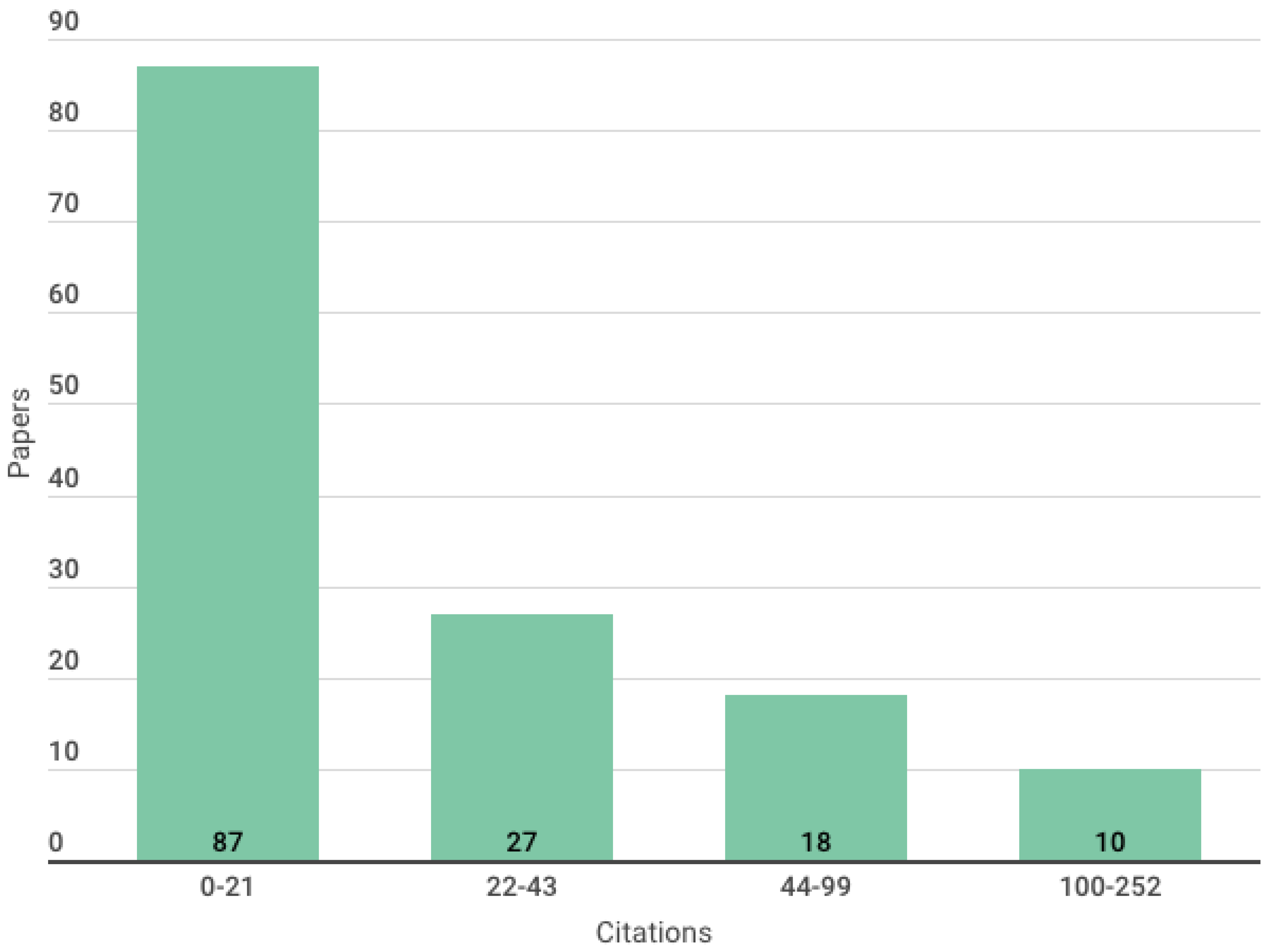
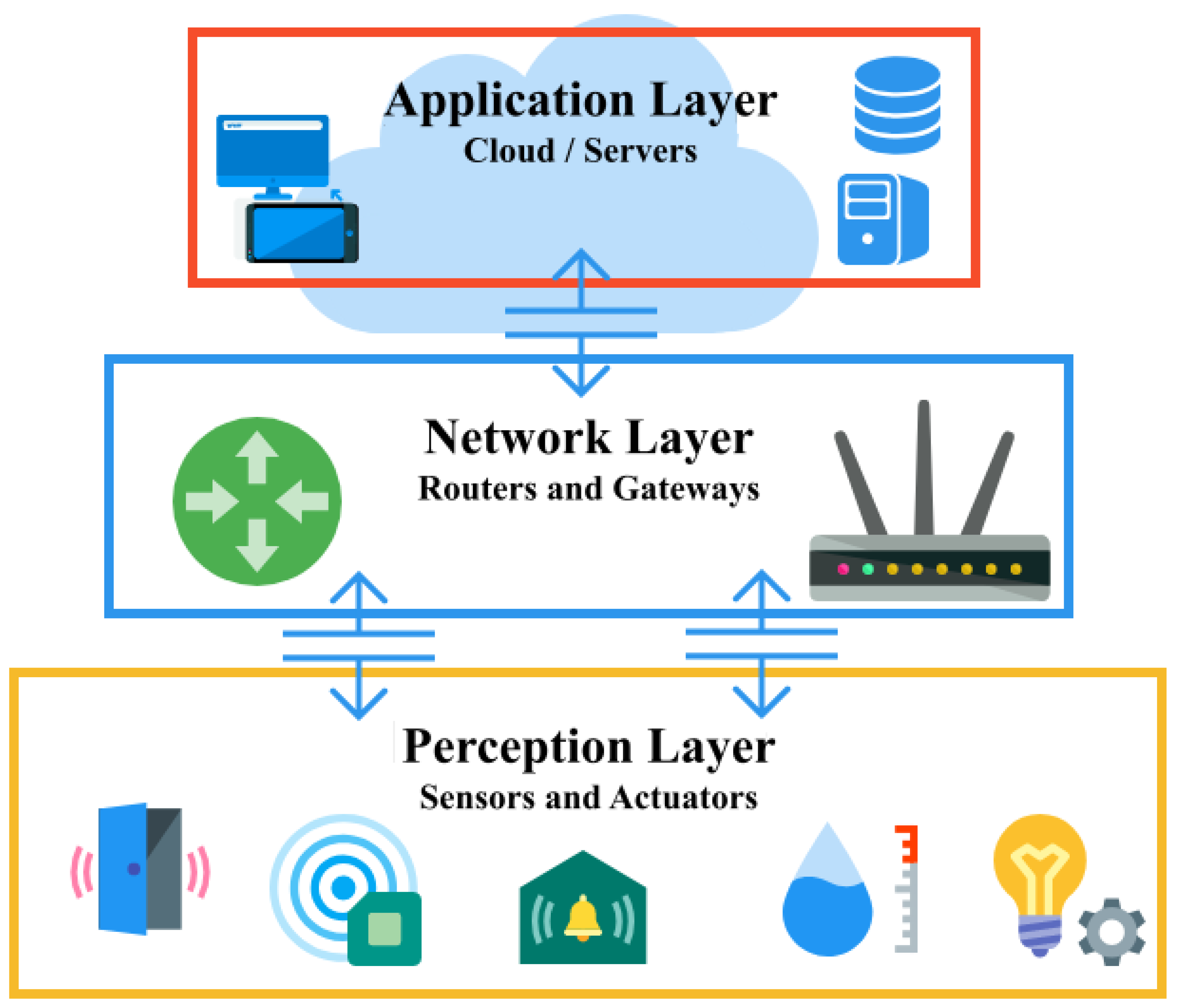
3. General Results
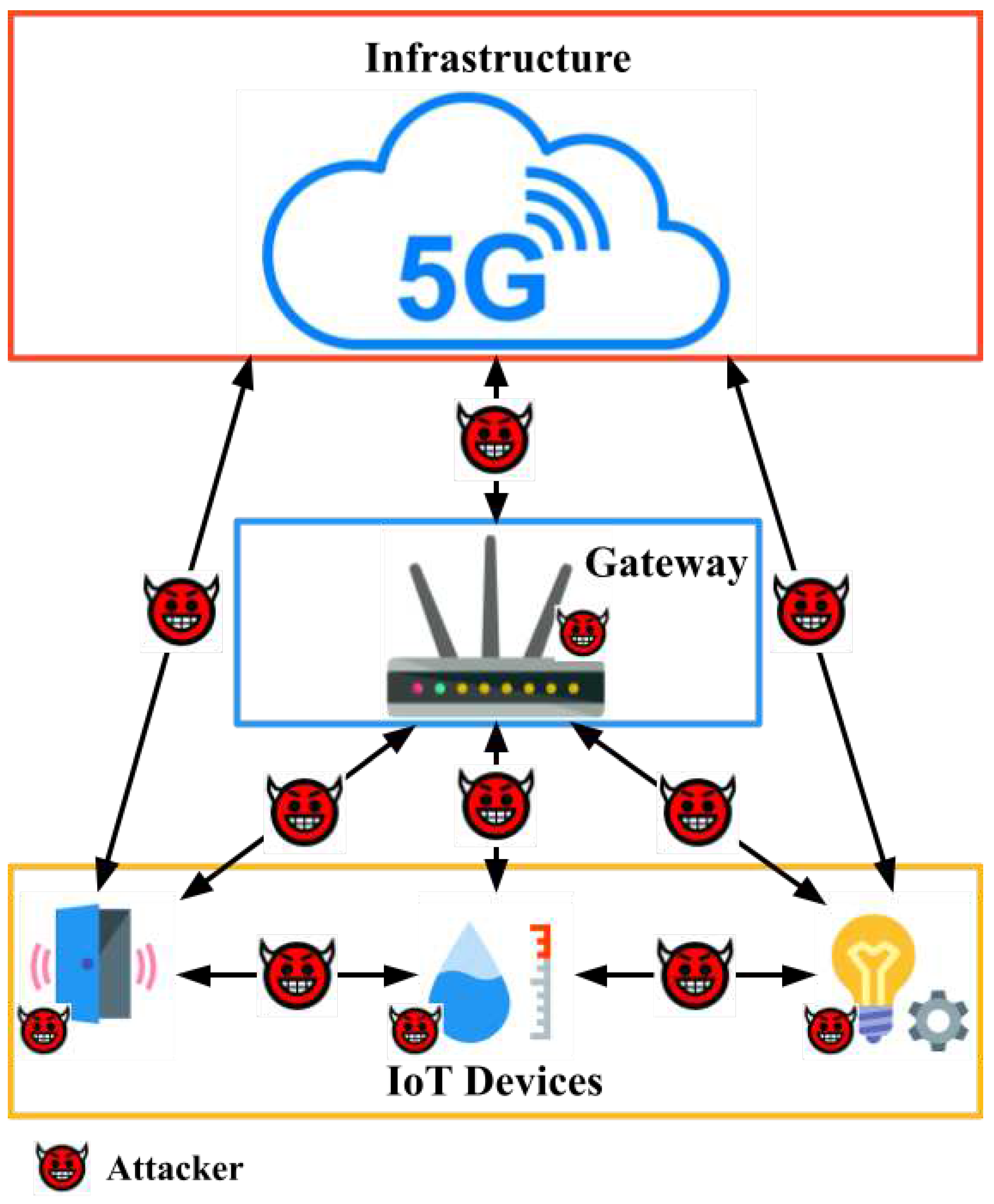
4. Threat Model
- Device: Each device can be targeted by attackers and, when compromised, allows communication with the 5G infrastructure or gateways, expanding the attack surface to other targets. The attacker can co-opt the device into a botnet frequently used for DDoS attacks. The captured device can also be used to listen to communication, extract sensitive information from the system, or even send fake data.
- Gateway: Gateways concentrate communication in IoT systems, enabling communication with devices and the 5G infrastructure. If an attacker takes control of the gateway, all the devices connected to it can be targeted to be co-opted. The gateway can also become unavailable due to a successful attack, and the devices connected to it will be unreachable. Finally, since gateways serve as an aggregation point in IoT systems, sensitive information can be leaked or even manipulated by the attacker.
- Communication Between Device and Gateway: Since IoT devices have computational constraints, the communication between devices and gateways can be targeted by eavesdroppers, who can steal sensitive data. Even when using encryption, the attacker can derive the original data by collecting enough encrypted data in transmission [17].
- Communication Between Gateway and Infrastructure: Attackers can exploit the communication channel between gateways and the 5G infrastructure.
- Communication Between Device and Infrastructure: Attackers can exploit the communication channel between the devices and the 5G infrastructure in the case of direct connection of the devices (e.g., using the 5G mMTC).
- Device-to-Device Communication: An important feature in 5G is the Device-to-Device (D2D) communication, which increases network coverage by enabling direct communication between devices without traversing the core network. This feature opens the door to propagating attacks in a multi-hop scenario, i.e., hop by hop to reach a vulnerable device. Using a compromised device, the attacker can access critical parts of the infrastructure [18].
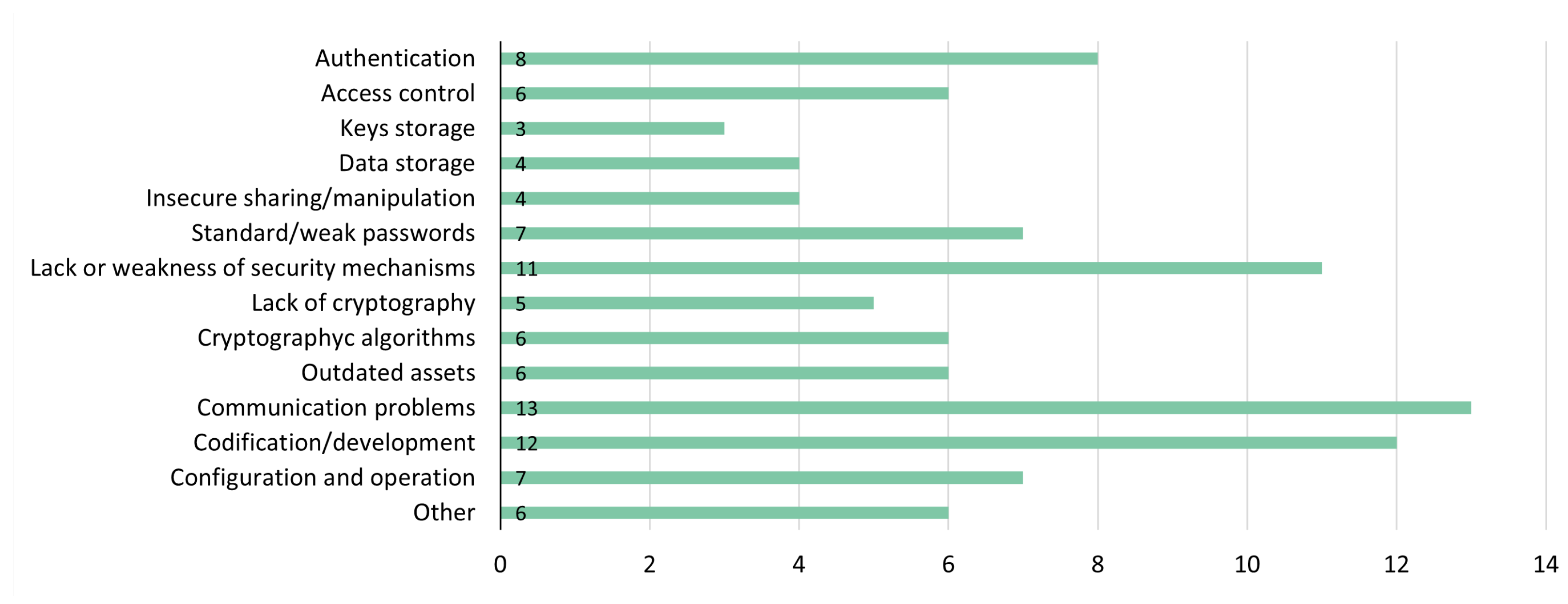
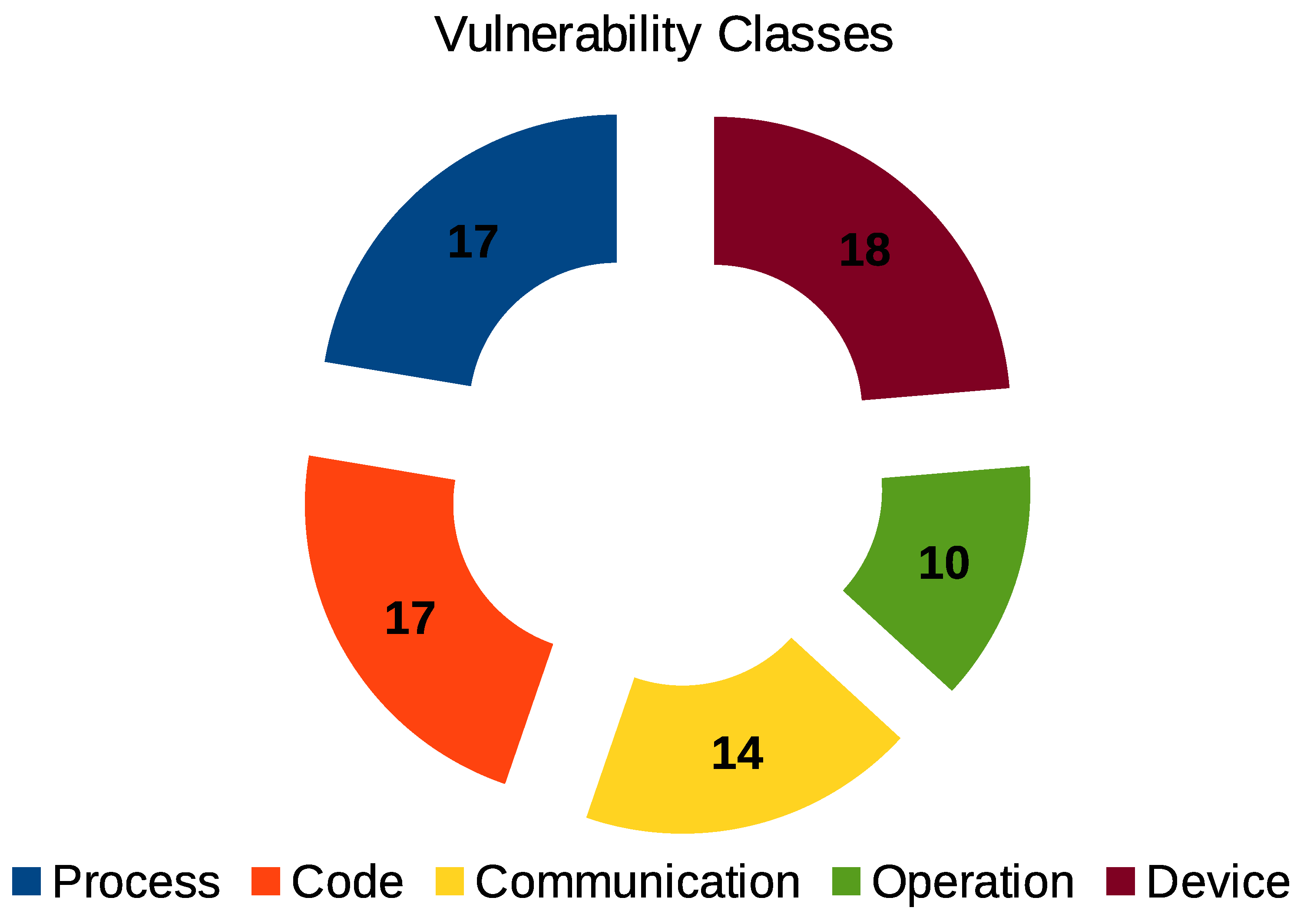
5. Known Vulnerabilities
- process, when related to common processes such as authentication, attestation, or manipulation;
- code, when related to development processes, including code practices and used technologies;
- communication, when related to protocols and data transmission;
- operation, when related to the device’s use or configuration by the user;
- and device, when related to some characteristic of the devices.
5.1. Process
- diversity of authentication modes may generate high network traffic [34];
- lack of authentication and authorization in SDN [13];
- broken access control [23];
- Evolved Packet System Authentication and Key Agreement (EPS-AKA) protocol is vulnerable to several well-known attacks, such as man-in-the-middle (MITM) and denial of service (DoS), and suffers from the disclosure of user identity on first access to the network [39];
- 5G-AKA allows for replay attacks since authentication and synchronization failure messages are sent to the device in plain text [40];
- other messages, such as RRC (Radio Resource Control) and NAS (Non-access stratum), are sent to the device in plain text, which can generate DoS and other attacks that compromise the confidentiality, as already happens with 4G [40];
- lack of attestation to know if a device is compromised [13];
- lack of certificate validation or incorrect validation [22];
- lack of data integrity verification [7];
- insecure deserialization [23];
- management of large numbers of devices [26].
5.2. Code
- memory buffer overflow can crash the system, allow control of program execution flow, or execute arbitrary code [22];
- XML external entity (XXE) injection [23];
- processing overload can facilitate replay attacks and RPL (routing protocol for low power and lossy networks) routing [26];
- non-standard protocol stacks, easily accessed physically or remotely [29];
- insecure pseudo-random generators [22];
- symmetric key algorithms are vulnerable to cryptographic attacks (e.g., known text, chosen text, and cryptanalysis) [46];
- asymmetric key algorithms are vulnerable to MitM and chosen text attacks [46];
- classic encryption algorithms, such as those based on the elliptic curve, are easily compromised when considering eventual advances in quantum computing [46];
- Diffie-Hellman (DH) algorithm is vulnerable to man-in-the-middle (MITM) attacks when exchanging public DH values between two devices [47];
- RSA algorithm (supports point-to-point communication and multicast routing in low power networks) is vulnerable to attacks such as forwarding, sinkhole, Sybil, Hello flooding, wormhole, black hole, and DoS [23];
- vulnerable web interfaces [48];
- single master key for software update [37];
- use of third-party libraries without proper security [43].
5.3. Communication
- vulnerabilities in infrastructure and edge devices [26];
- unreliable communication channel and medium access collisions [31];
- wireless sensor networks allow for easier device duplication [44];
- massive access is susceptible to eavesdropping due to the broadcast nature of wireless channels [50];
- TLS and SSL are vulnerable to attacks such as resource exhaustion, flooding, replay, amplification attacks, BEAST (Browser Exploit Against SSL/TLS), CRIME (Compression Ratio Info-leak Made Easy), Heartbleed, and RC4 (Rivest Cipher 4) [23];
- insecure TLS/SSL version or configuration [22];
- cross-site scripting (XSS) [23];
- Access Stratum (AS) keys’ stream reuse and NAS null encryption [28];
- 5G NSA (non-standalone) inherits vulnerabilities from 4G (network core) [30];
- simple HTTP communication [32];
- insecure pairing procedures [19].
5.4. Operation
- incorrect OS and software configuration [26];
- node interruption [26];
- deployment site exposure can facilitate attacks [29];
- translation between security protocols of different networks can be a weakness [49];
- bad user practices [30];
- frequent topology change in the Internet of Vehicles (IoV) networks [27].
5.5. Device
- vulnerable hosts can create multi-host and multi-stage vulnerabilities [24];
- weak physical security and insecure communication interfaces - given the resource restrictions - can lead to spoofing and sleep deprivation attacks [26];
- easy device access enables malicious code execution [44];
- lighter security technologies due to resource constraints [29];
- weak encryption [4];
- wearable devices have a high probability of losing confidential information in case of theft or loan [55];
- device location can be changed [57];
- rogue or compromised edge nodes and log files can be monitored by attackers [58];
- private keys can be compromised due to node security flaw [59];
- SIM card contents and functions can be remotely modified by sending a text message through OTA (Over-The-Air) technology [33];
- easy access to devices that do not require human interaction [21];
- lack of digital identity on devices [32];
- poorly designed devices allow easy execution of commands that can cause failures, or unauthorized access [10];
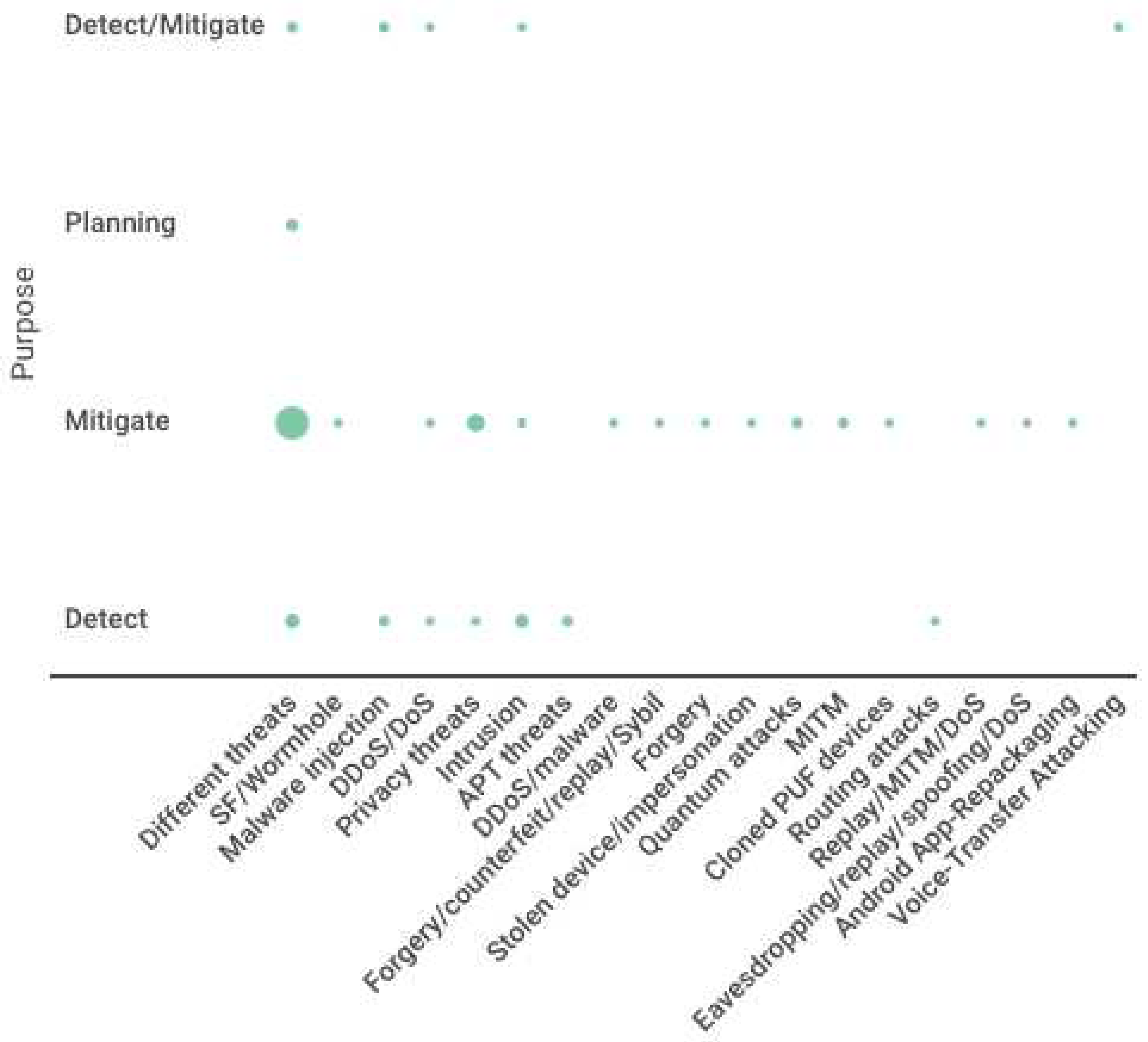
6. Threats In 5G-IoT Environments
6.1. Attacks on Data
6.2. Access Attacks
6.3. Masquerade Attacks
6.4. Routing Attacks
6.5. Availability Attacks
6.6. Summary
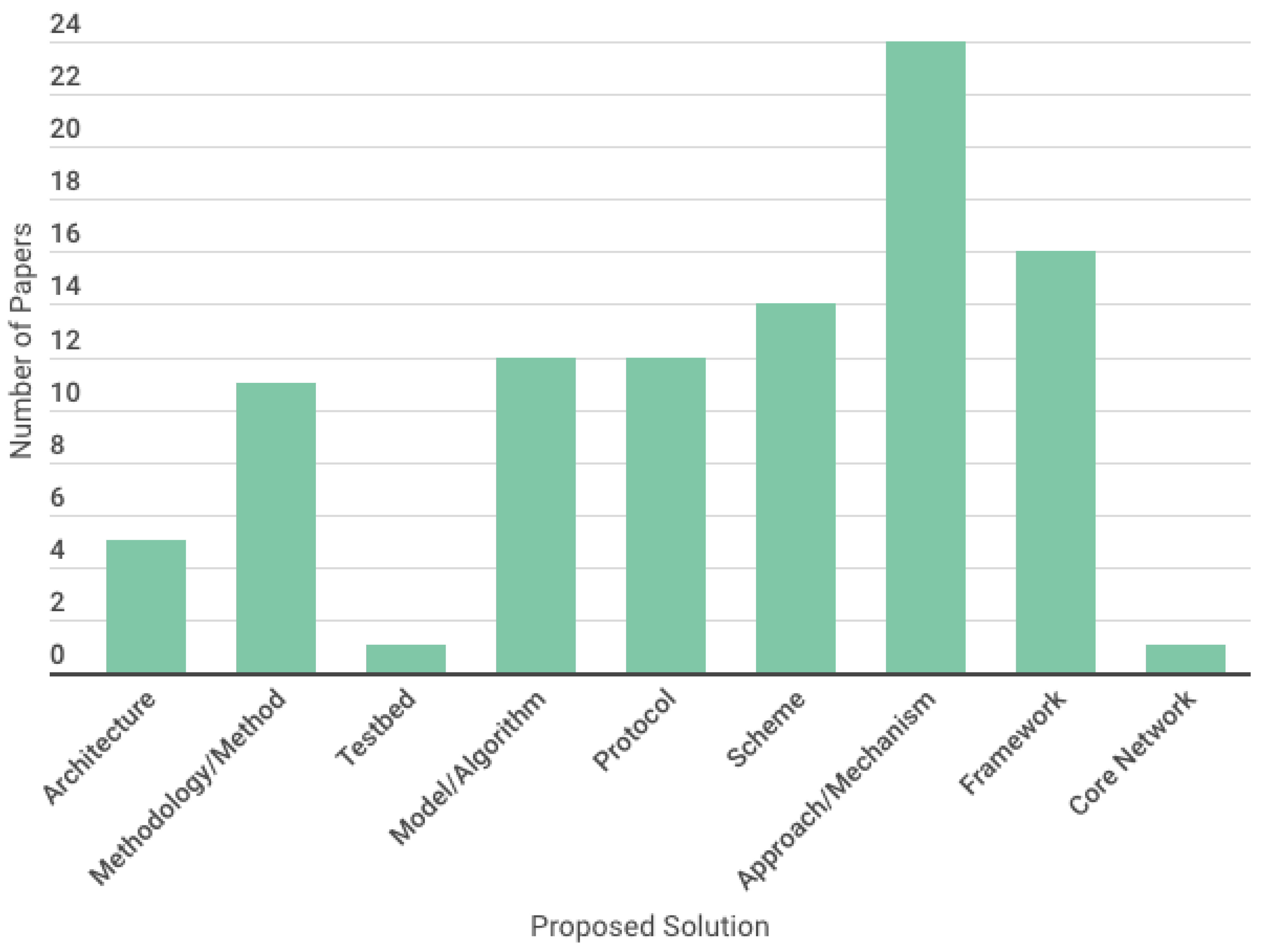
7. Proposed Solutions
8. Recommendations
- users should not use default passwords;
- users should keep software updated;
- developers should ensure secure communication;
- developers should simplify the installation and maintenance of devices;
- developers should ensure software integrity;
- developers should ensure that personal data protection; and
- developers should prevent interruptions.
8.1. Machine Learning
8.2. Blockchain
8.3. Lightweight Solutions
8.4. Perception Layer Security
9. Related Work
10. Conclusions
Acknowledgments
References
- Bockelmann, C.; Pratas, N.K.; Wunder, G.; Saur, S.; Navarro, M.; Gregoratti, D.; Vivier, G.; De Carvalho, E.; Ji, Y.; StefanoviC, C.; Popovski, P.; Wang, Q.; Schellmann, M.; Kosmatos, E.; Demestichas, P.; Raceala-Motoc, M.; Jung, P.; Stanczak, S.; Dekorsy, A. Towards Massive Connectivity Support for Scalable mMTC Communications in 5G Networks. IEEE Access 2018, 6, 28969–28992. [Google Scholar] [CrossRef]
- Chen, Y.; Sambo, Y.A.; Onireti, O.; Imran, M.A. A Survey on LPWAN-5G Integration: Main Challenges and Potential Solutions. IEEE Access 2022, 10, 32132–32149. [Google Scholar] [CrossRef]
- Sadique, K.M.; Rahmani, R.; Johannesson, P. Enhancing Data Privacy in the Internet of Things (IoT) Using Edge Computing. Proceedings of the 2nd International Conference on Computational Intelligence, Security and Internet of Things; Springer: Agartala, India, 2020; pp. 231–243. [CrossRef]
- Ghorbani, H.; Mohammadzadeh, M.S.; Ahmadzadegan, M.H. DDoS Attacks on the IoT Network with the Emergence of 5G. Proceedings of the International Conference on Technology and Entrepreneurship; IEEE: San Jose, CA, USA, 2020; pp. 1–5. [CrossRef]
- Valadares, D.C.G.; Will, N.C.; Sobrinho, A.A.C.C.; Lima, A.C.D.; Morais, I.S.; Santos, D.F.S. Security Challenges and Recommendations in 5G-IoT Scenarios. To appear in AINA 2023 Proceedings.
- Lohachab, A.; Karambir, B. Critical Analysis of DDoS — An Emerging Security Threat over IoT Networks. Journal of Communications and Information Networks 2018, 3, 57–78. [Google Scholar] [CrossRef]
- Miloslavskaya, N.; Tolstoy, A. Internet of Things: Information Security Challenges and Solutions. Cluster Computing 2019, 22, 103–119. [Google Scholar] [CrossRef]
- Khalid, M.; Mujahid, U.; ul Islam Muhammad, N. Ultralightweight RFID Authentication Protocols for Low-Cost Passive RFID Tags. Security and Communication Networks 2019, 2019, 1–25. [Google Scholar] [CrossRef]
- Borgaonkar, R.; Anne Tøndel, I.; Zenebe Degefa, M.; Gilje Jaatun, M. Improving Smart Grid Security Through 5G Enabled IoT and Edge Computing. Concurrency and Computation: Practice and Experience 2021, 33, e6466. [Google Scholar] [CrossRef]
- Mogadem, M.M.; Li, Y.; Meheretie, D.L. A Survey on Internet of Energy Security: Related Fields, Challenges, Threats and Emerging Technologies. Cluster Computing 2021, 25, 2449–2485. [Google Scholar] [CrossRef]
- Kitchenham, B.A.; Charters, S. Guidelines for performing Systematic Literature Reviews in Software Engineering. Technical Report EBSE 2007-001, Keele University and Durham University Joint Report, 2007.
- Petersen, K.; Feldt, R.; Mujtaba, S.; Mattsson, M. Systematic Mapping Studies in Software Engineering. Proceedings of the 12th International Conference on Evaluation and Assessment in Software Engineering; British Computer Society: Bari, Italy, 2008.
- Ramezan, G.; Leung, C.; Wang, Z.J. A Survey of Secure Routing Protocols in Multi-Hop Cellular Networks. IEEE Communications Surveys & Tutorials 2018, 20, 3510–3541. [Google Scholar] [CrossRef]
- Kitchenham, B.A.; Charters, S. Guidelines for performing Systematic Literature Reviews in Software Engineering. Technical Report EBSE 2007-001, School of Computer Science and Mathematics, Keele University, 2007.
- Burhan, M.; Rehman, R.A.; Khan, B.; Kim, B.S. IoT Elements, Layered Architectures and Security Issues: A Comprehensive Survey. Sensors 2018, 18, 2796. [Google Scholar] [CrossRef]
- Sharma, S.; Satapathy, S.; Singh, S.; Sahu, A.K.; Obaidat, M.S.; Saxena, S.; Puthal, D. Secure Authentication Protocol for 5G Enabled IoT Network. Proceedings of the 5th International Conference on Parallel, Distributed and Grid Computing; IEEE: Solan Himachal Pradesh, India, 2018; pp. 621–626. [CrossRef]
- Liao, C.H.; Shuai, H.H.; Wang, L.C. Eavesdropping Prevention for Heterogeneous Internet of Things Systems. Consumer Communications & Networking Conf; IEEE: Las Vegas, NV, USA, 2018; pp. 1–2. [CrossRef]
- Nieto, A.; Acien, A.; Fernandez, G. Crowdsourcing Analysis in 5G IoT: Cybersecurity Threats and Mitigation. Mob. Netw. Appl. 2019, 24, 881–889. [Google Scholar] [CrossRef]
- Shim, J.P.; Sharda, R.; French, A.M.; Syler, R.A.; Patten, K.P. The Internet of Things: Multi-faceted Research Perspectives. Communications of the Association for Information Systems. [CrossRef]
- Salim, M.M.; Rathore, S.; Park, J.H. Distributed Denial of Service Attacks and its Defenses in IoT: A Survey. The Journal of Supercomputing 2020, 76, 5320–5363. [Google Scholar] [CrossRef]
- Šarac, M.; Pavlović, N.; Bacanin, N.; Al-Turjman, F.; Adamović, S. Increasing Privacy and Security by Integrating a Blockchain Secure Interface Into an IoT Device Security Gateway Architecture. Energy Reports 2021, 7, 8075–8082. [Google Scholar] [CrossRef]
- Mathas, C.M.; Vassilakis, C.; Kolokotronis, N.; Zarakovitis, C.C.; Kourtis, M.A. On the Design of IoT Security: Analysis of Software Vulnerabilities for Smart Grids. Energies 2021, 14, 2818. [Google Scholar] [CrossRef]
- Mrabet, H.; Belguith, S.; Alhomoud, A.; Jemai, A. A Survey of IoT Security Based on a Layered Architecture of Sensing and Data Analysis. Sensors 2020, 20, 3625. [Google Scholar] [CrossRef]
- Yadav, G.; Paul, K.; Allakany, A.; Okamura, K. IoT-PEN: A Penetration Testing Framework for IoT. Proceedings of the International Conference on Information Networking; IEEE: Barcelona, Spain, 2020; pp. 196–201. [CrossRef]
- Osman, A.; Wasicek, A.; Kopsell, S.; Strufe, T. Transparent Microsegmentation in Smart Home IoT Networks. Proceedings of the 3rd USENIX Workshop on Hot Topics in Edge Computing; USENIX Association: Virtual Event, 2020; pp. 1–6.
- Saleem, K.; Alabduljabbar, G.M.; Alrowais, N.; Al-Muhtadi, J.; Imran, M.; Rodrigues, J.J.P.C. Bio-Inspired Network Security for 5G-Enabled IoT Applications. IEEE Access 2020, 8, 229152–229160. [Google Scholar] [CrossRef]
- He, Y.; Kong, M.; Du, C.; Yao, D.; Yu, M. Communication Security Analysis of Intelligent Transportation System Using 5G Internet of Things From the Perspective of Big Data. IEEE Transactions on Intelligent Transportation Systems 2023, 24, 2199–2207. [Google Scholar] [CrossRef]
- Kwon, S.; Park, S.; Cho, H.; Park, Y.; Kim, D.; Yim, K. Towards 5G-based IoT Security Analysis Against Vo5G Eavesdropping. Computing 2021, 103, 425–447. [Google Scholar] [CrossRef]
- Lee, B.; Lee, I.G.; Kim, M. Design and Implementation of Secure Cryptographic System on Chip for Internet of Things. IEEE Access 2022, 10, 18730–18742. [Google Scholar] [CrossRef]
- Vaezi, M.; Azari, A.; Khosravirad, S.R.; Shirvanimoghaddam, M.; Azari, M.M.; Chasaki, D.; Popovski, P. Cellular, Wide-Area, and Non-Terrestrial IoT: A Survey on 5G Advances and the Road Toward 6G. IEEE Communications Surveys & Tutorials 2022, 24, 1117–1174. [Google Scholar] [CrossRef]
- Qadri, Y.A.; Ali, R.; Musaddiq, A.; Al-Turjman, F.; Kim, D.W.; Kim, S.W. The Limitations in the State-of-the-Art Counter-Measures Against the Security Threats in H-IoT. Cluster Computing 2020, 23, 2047–2065. [Google Scholar] [CrossRef]
- Ozdemir, D.; Cibulka, J.; Stepankova, O.; Holmerova, I. Design and Implementation Framework of Social Assistive Robotics for People with Dementia - A Scoping Review. Health and Technology 2021, 11, 367–378. [Google Scholar] [CrossRef]
- Qiu, Q.; Du, X.; Yu, S.; Wang, C.; Liu, S.; Zhao, B.; Chang, L. Research on IoT Security Technology and Standardization in the 5G Era. Proceedings of the International Conference on Security and Privacy in New Computing Environments; Springer: Virtual Event, 2021; pp. 77–90. [CrossRef]
- Rahimi, H.; Zibaeenejad, A.; Rajabzadeh, P.; Safavi, A.A. On the Security of the 5G-IoT Architecture. Proceedings of the International Conference on Smart Cities and Internet of Things; ACM: Mashhad, Iran, 2018. [CrossRef]
- Mo, X. The Development Direction of Industrial Internet of Things based on 5G Communication. Journal of Physics: Conference Series 2020, 1648, 042121. [Google Scholar] [CrossRef]
- Touqeer, H.; Zaman, S.; Amin, R.; Hussain, M.; Al-Turjman, F.; Bilal, M. Smart Home Security: Challenges, Issues and Solutions at Different IoT Layers. The Journal of Supercomputing 2021, 77, 14053–14089. [Google Scholar] [CrossRef]
- Gong, G. Securing Internet-of-Things. Proceedings of the 11th International Symposium on Foundations and Practice of Security; Springer: Montreal, Canada, 2018; pp. 3–16. [CrossRef]
- Xingzhong, J.; Qingshui, X.; Haifeng, M.; Jiageng, C.; Haozhi, Z. The Research on Identity Authentication Scheme of Internet of Things Equipment in 5G Network Environment. Proceedings of the 19th International Conference on Communication Technology; IEEE: Xi’an, China, 2019; pp. 312–316. [CrossRef]
- Lopes, A.P.G.; Hilgert, L.O.; Gondim, P.R.; Lloret, J. Secret Sharing-Based Authentication and Key Agreement Protocol for Machine-Type Communications. International Journal of Distributed Sensor Networks 2019, 15, 1550147719841003. [Google Scholar] [CrossRef]
- Behrad, S.; Bertin, E.; Tuffin, S.; Crespi, N. A New Scalable Authentication and Access Control Mechanism for 5G-Based IoT. Future Generation Computer Systems 2020, 108, 46–61. [Google Scholar] [CrossRef]
- Chitroub, S.; Blaid, D.; Aouadia, H.; Laouar, R. Securing Mobile IoT Deployment Using Embedded SIM: Concerns and Solutions. Proceedings of the International Conference on Internet of Things, Embedded Systems and Communications; IEEE: Tunis, Tunisia, 2019; pp. 75–79. [CrossRef]
- Chopra, G.; Kumar Jha, R.; Jain, S. A Survey on Ultra-Dense Network and Emerging Technologies: Security Challenges and Possible Solutions. Journal of Network and Computer Applications 2017, 95, 54–78. [Google Scholar] [CrossRef]
- Anisetti, M.; Asal, R.; Ardagna, C.A.; Comi, L.; Damiani, E.; Gaudenzi, F. A Knowledge-Based IoT Security Checker. Proceedings of the European Conference on Parallel Processing; Springer: Turin, Italy, 2018; pp. 299–311. [CrossRef]
- Zhang, H.; Sakurai, K. A Survey of Software Clone Detection From Security Perspective. IEEE Access 2021, 9, 48157–48173. [Google Scholar] [CrossRef]
- Srinivasu, P.N.; Bhoi, A.K.; Nayak, S.R.; Bhutta, M.R.; Woźniak, M. Blockchain Technology for Secured Healthcare Data Communication Among the Non-Terminal Nodes in IoT Architecture in 5G Network. Electronics 2021, 10, 1437. [Google Scholar] [CrossRef]
- Althobaiti, O.S.; Dohler, M. Cybersecurity Challenges Associated With the Internet of Things in a Post-Quantum World. IEEE Access 2020, 8, 157356–157381. [Google Scholar] [CrossRef]
- Jung, Y.; Agulto, R. Virtual IP-Based Secure Gatekeeper System for Internet of Things. Sensors 2021, 21, 38. [Google Scholar] [CrossRef] [PubMed]
- Rim, K.; Lim, D. DoS Attack Control Design of IoT System for 5G Era. Journal of Information and Communication Convergence Engineering 2018, 16, 93–98. [Google Scholar] [CrossRef]
- Chen, S.; Ma, R.; Chen, H.H.; Zhang, H.; Meng, W.; Liu, J. Machine-to-Machine Communications in Ultra-Dense Networks — A Survey. IEEE Communications Surveys & Tutorials 2017, 19, 1478–1503. [Google Scholar] [CrossRef]
- Qi, Q.; Chen, X.; Zhong, C.; Zhang, Z. Physical Layer Security for Massive Access in Cellular Internet of Things. Science China Information Sciences 2020, 63, 1–12. [Google Scholar] [CrossRef]
- Yussuf Ahmed, A. Taufiq Asyhari, M.A.R. A Cyber Kill Chain Approach for Detecting Advanced Persistent Threats. Computers, Materials & Continua 2021, 67, 2497–2513. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Shetty, S.; Gope, P.; Rodrigues, J.J.P.C. Security in 5G-Enabled Internet of Things Communication: Issues, Challenges, and Future Research Roadmap. IEEE Access 2021, 9, 4466–4489. [Google Scholar] [CrossRef]
- Khumalo, P.; Nleya, B.; Gomba, A.; Mutsvangwa, A. Services and Applications Security in IoT Enabled Networks. Proc. of the Intl. Conf. on Intelligent and Innovative Computing Applications; IEEE: Mon Tresor, Mauritius, 2018. [CrossRef]
- Cao, J.; Yu, P.; Xiang, X.; Ma, M.; Li, H. Anti-Quantum Fast Authentication and Data Transmission Scheme for Massive Devices in 5G NB-IoT System. IEEE Internet of Things Journal 2019, 6, 9794–9805. [Google Scholar] [CrossRef]
- Uddin, H.; Gibson, M.; Safdar, G.A.; Kalsoom, T.; Ramzan, N.; Ur-Rehman, M.; Imran, M.A. IoT for 5G/B5G Applications in Smart Homes, Smart Cities, Wearables and Connected Cars. Proceedings of the 24th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks; IEEE: Limassol, Cyprus, 2019; pp. 1–5. [CrossRef]
- Yu, P.; Cao, J.; Ma, M.; Li, H.; Niu, B.; Li, F. Quantum-Resistance Authentication and Data Transmission Scheme for NB-IoT in 3GPP 5G Networks. Proceedings of the Wireless Communications and Networking Conference; IEEE: Marrakesh, Morocco, 2019; pp. 1–7. [CrossRef]
- Tang, Z.; Keoh, S.L. An Efficient Scheme to Secure Data Provenance in Home Area Networks. Proceedings of the 3rd 5G World Forum; IEEE: Bangalore, India, 2020; pp. 115–120. [CrossRef]
- Shen, S.; Zhang, K.; Zhou, Y.; Ci, S. Security in edge-assisted Internet of Things: challenges and solutions. Science China Information Sciences 2020, 63, 1–14. [Google Scholar] [CrossRef]
- Alvarenga, I.D.; Camilo, G.F.; De Souza, L.A.C.; Duarte, O.C.M.B. DAGSec: A Hybrid Distributed Ledger Architecture for the Secure Management of the Internet of Things. Proceedings of the International Conference on Blockchain; IEEE: Melbourne, Australia, 2021; pp. 266–271. [CrossRef]
- Holik, F. Protecting IoT Devices with Software-Defined Networks. Proceedings of the International Conference on Intelligent Technologies and Applications; Springer: Grimstad, Norway, 2021; pp. 41–52. [CrossRef]
- Sharma, P.; Jain, S.; Gupta, S.; Chamola, V. Role of Machine Learning and Deep Learning in Securing 5G-Driven Industrial IoT Applications. Ad Hoc Networks 2021, 123, 102685. [Google Scholar] [CrossRef]
- Wu, T.Y.; Lee, Z.; Obaidat, M.S.; Kumari, S.; Kumar, S.; Chen, C.M. An Authenticated Key Exchange Protocol for Multi-Server Architecture in 5G Networks. IEEE Access 2020, 8, 28096–28108. [Google Scholar] [CrossRef]
- Xiao, L.; Xu, H.; Zhu, F.; Wang, R.; Li, P. SKINNY-Based RFID Lightweight Authentication Protocol. Sensors 2020, 20, 1366. [Google Scholar] [CrossRef] [PubMed]
- Anand, A.; Rani, S.; Anand, D.; AljahThe Development Direction ofdali, H.M.; Kerr, D. An Efficient CNN-Based Deep Learning Model to Detect Malware Attacks (CNN-DMA) in 5G-IoT Healthcare Applications. Sensors 2021, 21, 6346. [Google Scholar] [CrossRef]
- Gafurov, K.; Chung, T.M. Comprehensive Survey on Internet of Things, Architecture, Security Aspects, Applications, Related Technologies, Economic Perspective, and Future Directions. Journal of Information Processing Systems 2019, 15, 797–819. [Google Scholar] [CrossRef]
- Taimoor, N.; Rehman, S. Reliable and Resilient AI and IoT-Based Personalised Healthcare Services: A Survey. IEEE Access 2022, 10, 535–563. [Google Scholar] [CrossRef]
- Ni, J.; Lin, X.; Shen, X.S. Efficient and Secure Service-Oriented Authentication Supporting Network Slicing for 5G-Enabled IoT. IEEE Journal on Selected Areas in Communications 2018, 36, 644–657. [Google Scholar] [CrossRef]
- Qiu, Q.; Wang, D.; Du, X.; Yu, S.; Liu, S.; Zhao, B. Security Standards and Measures for Massive IoT in the 5G Era. Mobile Networks and Applications 2022, 27, 392–403. [Google Scholar] [CrossRef]
- Seyhan, K.; Nguyen, T.N.; Akleylek, S.; Cengiz, K. Lattice-Based Cryptosystems for the Security of Resource-Constrained IoT Devices in Post-Quantum World: A Survey. Cluster Computing 2022, 25, 1729–1748. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Shu, L.; Choo, K.K.R. Fighting COVID-19 and Future Pandemics With the Internet of Things: Security and Privacy Perspectives. IEEE/CAA Journal of Automatica Sinica 2021, 8, 1477–1499. [Google Scholar] [CrossRef]
- Zidková, N.; Maryska, M. Threat Analysis of 5G Technology Within IIoT Sensors. Proceedings of the Future Technologies Conference; Springer: Vancouver, BC, Canada, 2022; pp. 389–402. [CrossRef]
- Ambareen, J.; Prabhakar, M.; Ara, T. LEES: A Hybrid Lightweight Elliptic ElGamal-Schnorr-Based Cryptography for Secure D2D Communications. Journal of Telecommunications and Information Technology 2021, 2, 24–30. [Google Scholar] [CrossRef]
- Shin, S.; Kwon, T. A Privacy-Preserving Authentication, Authorization, and Key Agreement Scheme for Wireless Sensor Networks in 5G-Integrated Internet of Things. IEEE Access 2020, 8, 67555–67571. [Google Scholar] [CrossRef]
- Yujia, H.; Yongfeng, H.; Fu, C. Research on Node Authentication of MQTT Protocol. Proceedings of the 11th International Conference on Software Engineering and Service Science; IEEE: Beijing, China, 2020; pp. 405–410. [CrossRef]
- Zenger, C.T.; Zimmer, J.; Pietersz, M.; Driessen, B.; Paar, C. Constructive and Destructive Aspects of Adaptive Wormholes for the 5G Tactile Internet. Proceedings of the 9th Conference on Security & Privacy in Wireless and Mobile Networks; ACM: Darmstadt, Germany, 2016; pp. 109–120. [CrossRef]
- Montaño-Blacio, M.; Briceño-Sarmiento, J.; Pesántez-Bravo, F. 5G Network Security for IoT Implementation: A Systematic Literature Review. Proceedings of the International Conference on Innovation and Research; Springer: Sangolquí, Ecuador, 2021; pp. 28–40. [CrossRef]
- Rezvy, S.; Luo, Y.; Petridis, M.; Lasebae, A.; Zebin, T. An Efficient Deep Learning Model for Intrusion Classification and Prediction in 5G and IoT Networks. Proceedings of the 53rd Annual Conference on Information Sciences and Systems; IEEE: Baltimore, MD, USA, 2019; pp. 1–6. [CrossRef]
- Varga, P.; Peto, J.; Franko, A.; Balla, D.; Haja, D.; Janky, F.; Soos, G.; Ficzere, D.; Maliosz, M.; Toka, L. 5G Support for Industrial IoT Applications — Challenges, Solutions, and Research Gaps. Sensors 2020, 20, 828. [Google Scholar] [CrossRef] [PubMed]
- Sharma, A.; Balasubramanian, V.; Jolfaei, A. Security Challenges and Solutions for 5G HetNet. Proceedings of the 19th International Conference on Trust, Security and Privacy in Computing and Communications; IEEE: Guangzhou, China, 2020; pp. 1318–1323. [CrossRef]
- Vassilakis, V.; Chochliouros, I.P.; Spiliopoulou, A.S.; Sfakianakis, E.; Belesioti, M.; Bompetsis, N.; Wilson, M.; Turyagyenda, C.; Dardamanis, A. Security Analysis of Mobile Edge Computing in Virtualized Small Cell Networks. Proceedings of the International Conference on Artificial Intelligence Applications and Innovations; Springer: Thessaloniki, Greece, 2016; pp. 653–665. [CrossRef]
- Mohammed, T.; Albeshri, A.; Katib, I.; Mehmood, R. UbiPriSEQ — Deep Reinforcement Learning to Manage Privacy, Security, Energy, and QoS in 5G IoT HetNets. Applied Sciences 2020, 10, 7120. [Google Scholar] [CrossRef]
- Li, S.; Iqbal, M.; Saxena, N. Future Industry Internet of Things with Zero-Trust Security. Information Systems Frontiers 2022. [Google Scholar] [CrossRef]
- Huang, X.; Craig, P.; Lin, H.; Yan, Z. SecIoT: A Security Framework for the Internet of Things. Security and Communication Networks 2016, 9, 3083–3094. [Google Scholar] [CrossRef]
- Lagkas, T.; Argyriou, V.; Bibi, S.; Sarigiannidis, P. UAV IoT Framework Views and Challenges: Towards Protecting Drones as “Things”. Sensors 2018, 18, 4015. [Google Scholar] [CrossRef] [PubMed]
- Miloslavskaya, N.; Tolstoy, A. IoTBlockSIEM for Information Security Incident Management in the Internet of Things Ecosystem. Cluster Computing 2020, 23, 1911–1925. [Google Scholar] [CrossRef]
- Mansour, C.; Chasaki, D. Multi-layer Security Mechanism for Networked Embedded Devices. Proceedings of the 11th International Conference on Ubiquitous Computing and Ambient Intelligence; Springer: Philadelphia, PA, USA, 2017; pp. 3–14. [CrossRef]
- Rathee, G.; Iqbal, R.; Waqar, O.; Bashir, A.K. On the Design and Implementation of a Blockchain Enabled E-Voting Application Within IoT-Oriented Smart Cities. IEEE Access 2021. [Google Scholar] [CrossRef]
- Hellaoui, H.; Koudil, M.; Bouabdallah, A. Energy Efficiency in Security of 5G-Based IoT: An End-to-End Adaptive Approach. IEEE Internet of Things Journal 2020, 7, 6589–6602. [Google Scholar] [CrossRef]
- Bordel, B.; Alcarria, R.; Robles, T.; Iglesias, M.S. Data Authentication and Anonymization in IoT Scenarios and Future 5G Networks Using Chaotic Digital Watermarking. IEEE Access 2021, 9, 22378–22398. [Google Scholar] [CrossRef]
- Torroglosa-Garcia, E.M.; Calero, J.M.A.; Bernabe, J.B.; Skarmeta, A. Enabling Roaming Across Heterogeneous IoT Wireless Networks: LoRaWAN Meets 5G. IEEE Access 2020, 8, 103164–103180. [Google Scholar] [CrossRef]
- Al-Aqrabi, H.; Johnson, A.P.; Hill, R.; Lane, P.; Alsboui, T. Hardware-Intrinsic Multi-Layer Security: A New Frontier for 5G Enabled IIoT. Sensors 2020, 20, 1963. [Google Scholar] [CrossRef]
- Sharma, V.; Kim, J.; Kwon, S.; You, I.; Chen, H.C. Fuzzy-Based Protocol for Secure Remote Diagnosis of IoT Devices in 5G Networks. Proceedings of the International Conference on Internet of Things as a Service; Springer: Taichun, Taiwan, 2018; pp. 54–63. [CrossRef]
- Azad, M.A.; Bag, S.; Perera, C.; Barhamgi, M.; Hao, F. Authentic Caller: Self-Enforcing Authentication in a Next-Generation Network. IEEE Transactions on Industrial Informatics 2020. [Google Scholar] [CrossRef]
- Shin, S.; Kwon, T. Two-Factor Authenticated Key Agreement Supporting Unlinkability in 5G-Integrated Wireless Sensor Networks. IEEE Access 2018, 6, 11229–11241. [Google Scholar] [CrossRef]
- Liu, W.; Wang, X.; Peng, W. Secure Remote Multi-Factor Authentication Scheme Based on Chaotic Map Zero-Knowledge Proof for Crowdsourcing Internet of Things. IEEE Access 2020, 8, 8754–8767. [Google Scholar] [CrossRef]
- Khalid, M.; Khokhar, U.; Najam-ul Islam, M. Advance Strong Authentication Strong Integrity (ASASI) Protocol for Low Cost Radio Frequency Identification. Proceedings of the International Conference on Smart Computing and Electronic Enterprise; IEEE: Shah Alam, Malaysia, 2018; pp. 1–6. [CrossRef]
- Fan, K.; Song, P.; Yang, Y. ULMAP: Ultralightweight NFC Mutual Authentication Protocol with Pseudonyms in the Tag for IoT in 5G. Mobile Information Systems 2017, 2017, 1–7. [Google Scholar] [CrossRef]
- Fan, K.; Gong, Y.; Liang, C.; Li, H.; Yang, Y. Lightweight and Ultralightweight RFID Mutual Authentication Protocol with Cache in the Reader for IoT in 5G. Security and Communication Networks 2016, 9, 3095–3104. [Google Scholar] [CrossRef]
- Das, M.L. Privacy and Security Challenges in Internet of Things. Proceedings of the 11th International Conference on Distributed Computing and Internet Technology; Springer: Bhubaneswar, India, 2015; pp. 33–48. [CrossRef]
- Duguma, D.G.; Kim, J.; Lee, S.; Jho, N.S.; Sharma, V.; You, I. A Lightweight D2D Security Protocol with Request-Forecasting for Next-Generation Mobile Networks. Connection Science 2022, 34, 362–386. [Google Scholar] [CrossRef]
- Shin, D.; Yun, K.; Kim, J.; Astillo, P.V.; Kim, J.N.; You, I. A Security Protocol for Route Optimization in DMM-Based Smart Home IoT Networks. IEEE Access 2019, 7, 142531–142550. [Google Scholar] [CrossRef]
- Rajawat, A.S.; Bedi, P.; Goyal, S.B.; Shukla, P.K.; Jamal, S.S.; Alharbi, A.R.; Aljaedi, A. Securing 5G-IoT Device Connectivity and Coverage Using Boltzmann Machine Keys Generation. Mathematical Problems in Engineering 2021, 2021, 1–10. [Google Scholar] [CrossRef]
- Rawal, B.S.; Peter, A. Introduction of Interstitial Model and a Sumkey to Address the Key Challenges with Blockchain. Proceedings of the IEEE Globecom Workshops; IEEE: Waikoloa, HI, USA, 2019. [CrossRef]
- Ravi, N.; Selvaraj, M.S. TeFENS: Testbed For Experimenting Next-Generation-Network Security. Proceedings of the IEEE 5G World Forum; IEEE: Silicon Valley, CA, USA, 2018; pp. 204–209. [CrossRef]
- Wang, K.; Liu, X.; Chen, C.M.; Kumari, S.; Shojafar, M.; Hossain, M.S. Voice-Transfer Attacking on Industrial Voice Control Systems in 5G-Aided IIoT Domain. IEEE Trans. on Industrial Informatics 2021. [Google Scholar] [CrossRef]
- Szymanski, T.H. Securing the Industrial-Tactile Internet of Things With Deterministic Silicon Photonics Switches. IEEE Access 2016. [Google Scholar] [CrossRef]
- Deebak, B.; AL-Turjman, F. A Robust and Distributed Architecture for 5G-Enabled Networks in the Smart Blockchain Era. Computer Communications 2022, 181, 293–308. [Google Scholar] [CrossRef]
- Vangala, A.; Das, A.K.; Chamola, V.; Korotaev, V.; Rodrigues, J.J.P.C. Security in IoT-Enabled Smart Agriculture: Architecture, Security Solutions and Challenges. Cluster Computing 2022. [Google Scholar] [CrossRef]
- Dib, M.; Torabi, S.; Bou-Harb, E.; Assi, C. A Multi-Dimensional Deep Learning Framework for IoT Malware Classification and Family Attribution. IEEE Transactions on Network and Service Management 2021, 18, 1165–1177. [Google Scholar] [CrossRef]
- Rey, V.; Sánchez Sánchez, P.M.; Huertas Celdrán, A.; Bovet, G. Federated Learning for Malware Detection in IoT Devices. Computer Networks 2022, 204, 108693. [Google Scholar] [CrossRef]
- Krishnan, P.; Duttagupta, S.; Achuthan, K. SDN/NFV Security Framework for Fog-to-Things Computing Infrastructure. Software: Practice and Experience 2020, 50, 757–800. [Google Scholar] [CrossRef]
- Lawal, M.A.; Shaikh, R.A.; Hassan, S.R. A DDoS Attack Mitigation Framework for IoT Networks using Fog Computing. Procedia Computer Science 2021, 182, 13–20. [Google Scholar] [CrossRef]
- Jaiswal, A.; Kumar, S.; Kaiwartya, O.; Kumar, N.; Song, H.; Lloret, J. Secrecy Rate Maximization in Virtual-MIMO Enabled SWIPT for 5G Centric IoT Applications. IEEE Systems Journal 2021, 15, 2810–2821. [Google Scholar] [CrossRef]
- Jain, A.; Singh, T.; Sharma, S.K.; Prajapati, V. Implementing Security in IoT Ecosystem Using 5G Network Slicing and Pattern Matched Intrusion Detection System: A Simulation Study. Interdisciplinary Journal of Information, Knowledge, and Management 2021, 16, 001–038. [Google Scholar] [CrossRef] [PubMed]
- Khan, N.A. PKI-Based Security Enhancement for IoT in 5G Networks. Proceedings of the 3rd International Conference on Inventive Computation and Information Technologies; Springer: Virtual Event, 2022. [CrossRef]
- Lee, H.; Kang, D.; Ryu, J.; Won, D.; Kim, H.; Lee, Y. A Three-Factor Anonymous User Authentication Scheme for Internet of Things Environments. Journal of Information Security and Applications 2020. [Google Scholar] [CrossRef]
- Li, X.; Liu, S.; Wu, F.; Kumari, S.; Rodrigues, J.J.P.C. Privacy Preserving Data Aggregation Scheme for Mobile Edge Computing Assisted IoT Applications. IEEE Internet of Things Journal 2019, 6, 4755–4763. [Google Scholar] [CrossRef]
- Choudhury, H. HashXor: A Lightweight Scheme for Identity Privacy of IoT Devices in 5G Mobile Network. Computer Networks 2021, 186, 107753. [Google Scholar] [CrossRef]
- Zhang, P.; Sun, H.; Situ, J.; Jiang, C.; Xie, D. Federated Transfer Learning for IIoT Devices With Low Computing Power Based on Blockchain and Edge Computing. IEEE Access 2021, 9, 98630–98638. [Google Scholar] [CrossRef]
- Krundyshev, V.; Kalinin, M. Hybrid Neural Network Framework for Detection of Cyber Attacks at Smart Infrastructures. Proceedings of the 12th International Conference on Security of Information and Networks; ACM: Sochi, Russia, 2019; pp. 1–7. [CrossRef]
- Lee, Y.; Woo, S.; Lee, J.; Song, Y.; Moon, H.; Lee, D.H. Enhanced Android App-Repackaging Attack on In-Vehicle Network. Wireless Communications and Mobile Computing 2019, 2019, 1–13. [Google Scholar] [CrossRef]
- Kang, J.J.; Fahd, K.; Venkatraman, S.; Trujillo-Rasua, R.; Haskell-Dowland, P. Hybrid Routing for Man-in-the-Middle (MITM) Attack Detection in IoT Networks. Proceedings of the 29th International Telecommunication Networks and Applications Conference; IEEE: Auckland, New Zealand, 2019; pp. 1–6. [CrossRef]
- Zhang, B.; Li, J.; Zheng, X.; Ge, J.; Sun, J. A Blockchain-Based Mobile IoT Network Interconnection Security Trusted Protocol Model. Proceedings of the 11th International Symposium on Cyberspace Safety and Security; Springer: Guangzhou, China, 2019; pp. 372–381. [CrossRef]
- Fu, Y.; Yan, Z.; Cao, J.; Koné, O.; Cao, X. An Automata Based Intrusion Detection Method for Internet of Things. Mobile Information Systems 2017, 2017, 1–13. [Google Scholar] [CrossRef]
- Laguduva, V.R.; Katkoori, S.; Karam, R. Machine Learning Attacks and Countermeasures for PUF-based IoT Edge Node Security. SN Computer Science 2020, 1. [Google Scholar] [CrossRef]
- Cheng, X.; Luo, Q.; Pan, Y.; Li, Z.; Zhang, J.; Chen, B. Predicting the APT for Cyber Situation Comprehension in 5G-Enabled IoT Scenarios Based on Differentially Private Federated Learning. Security and Communication Networks 2021, 2021, 1–14. [Google Scholar] [CrossRef]
- Lee, K.; Yim, K. Study on the Transaction Linkage Technique Combined with the Designated Terminal for 5G-Enabled IoT. Digital Communications and Networks 2022, 8, 124–131. [Google Scholar] [CrossRef]
- Catania, E.; La Corte, A. IoT Privacy in 5G Networks. Proceedings of the 3rd International Conference on Internet of Things, Big Data and Security; SciTePress: Funchal, Madeira, Portugal, 2018; pp. 123–131. [CrossRef]
- Sankar, S.P.; Subash, T.D.; Vishwanath, N.; Geroge, D.E. Security Improvement in Blockchain Technique Enabled Peer to Peer Network for Beyond 5G and Internet of Things. Peer-to-Peer Networking and Applications 2020, 14, 392–402. [Google Scholar] [CrossRef]
- Baniata, H.; Almobaideen, W.; Kertesz, A. A Privacy Preserving Model for Fog-Enabled MCC Systems Using 5G Connection. Proceedings of the 5th International Conference on Fog and Mobile Edge Computing; IEEE: Paris, France, 2020; pp. 223–230. [CrossRef]
- Nie, X.; Yang, L.T.; Feng, J.; Zhang, S. Differentially Private Tensor Train Decomposition in Edge-Cloud Computing for SDN-Based Internet of Things. IEEE Internet of Things Journal 2020, 7, 5695–5705. [Google Scholar] [CrossRef]
- Lu, N.; Du, Q.; Sun, L.; Ren, P. Traffic-Driven Intrusion Detection for Massive MTC Towards 5G Networks. Proceedings of the IEEE Conference on Computer Communications Workshops; IEEE: Honolulu, HI, USA, 2018; pp. 426–431. [CrossRef]
- Wang, F.; Lu, Y.; Wang, C.; Li, Q. Binary Black-Box Adversarial Attacks with Evolutionary Learning Against IoT Malware Detection. Wireless Communications and Mobile Computing 2021. [Google Scholar] [CrossRef]
- Celik, A.; Tetzner, J.; Sinha, K.; Matta, J. 5G Device-to-Device Communication Security and Multipath Routing Solutions. Applied Network Science 2019, 4, 1–24. [Google Scholar] [CrossRef]
- Tsimenidis, S.; Lagkas, T.; Rantos, K. Deep Learning in IoT Intrusion Detection. Journal of Network and Systems Management 2022. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Coen-Porisini, A. 5G In the Internet of Things Era: An Overview on Security and Privacy Challenges. Computer Networks 2020, 179, 107345. [Google Scholar] [CrossRef]
- Dhirani, L.L.; Armstrong, E.; Newe, T. Industrial IoT, Cyber Threats, and Standards Landscape: Evaluation and Roadmap. Sensors 2021. [Google Scholar] [CrossRef] [PubMed]
- Ahmad, A.; Bhushan, B.; Sharma, N.; Kaushik, I.; Arora, S. Importunity & Evolution of IoT for 5G. Proc. of the Intl. Conf. on Comm. Systems and Network Technologies; IEEE: Gwalior, India, 2020. [CrossRef]
- Pahlevanzadeh, B.; Koleini, S.; Fadilah, S.I. Security in IoT: Threats and Vulnerabilities, Layered Architecture, Encryption Mechanisms, Challenges and Solutions. Proc. of the 2nd Intl. Conference on Advances in Cyber Security; Springer: Penang, Malaysia, 2021. [CrossRef]
- Sallam, S.; Beheshti, B.D. A Survey on Lightweight Cryptographic Algorithms. TENCON 2018–2018 IEEE Region 10 Conference; IEEE: Jeju, South Korea, 2018; pp. 1784–1789. [CrossRef]
- Zhang, S.; Wang, Y.; Zhou, W. Towards Secure 5G networks: A Survey. Computer Networks 2019, 162, 106871. [Google Scholar] [CrossRef]
- Atharvan, G.; Koolikkara Madom Krishnamoorthy, S.; Dua, A.; Gupta, S. A Way Forward Towards a Technology-Driven Development of Industry 4.0 Using Big Data Analytics in 5G-Enabled IIoT. International Journal of Communication Systems 2022, 35, e5014. [Google Scholar] [CrossRef]
- Liang, W.; Ji, N. Privacy Challenges of IoT-Based Blockchain: A Systematic Review. Cluster Computing 2022, 25. [Google Scholar] [CrossRef]
- Sathish, C.; Rubavathi, C.Y. A survey on Blockchain Mechanisms (BCM) Based on Internet of Things (IoT) Applications. Multimedia Tools and Applications 2022, 81, 33419–33458. [Google Scholar] [CrossRef]
- Hewa, T.M.; Kalla, A.; Nag, A.; Ylianttila, M.E.; Liyanage, M. Blockchain for 5G and IoT: Opportunities and Challenges. Proceedings of the 8th International Conference on Communications and Networking; IEEE: Hammamet, Tunisia, 2020; pp. 1–8. [CrossRef]
- Rath, D.K.; Kumar, A. A Primer on Internet of Things Ecosystem and 5G Networks. Proceedings of the International Conference on Information Technology; IEEE: Bhubaneswar, India, 2018. [CrossRef]
- Wang, N.; Wang, P.; Alipour-Fanid, A.; Jiao, L.; Zeng, K. Physical-Layer Security of 5G Wireless Networks for IoT: Challenges and Opportunities. IEEE Internet of Things Journal 2019. [Google Scholar] [CrossRef]
- Tan, Y.a.; Zhang, X.; Sharif, K.; Liang, C.; Zhang, Q.; Li, Y. Covert Timing Channels for IoT over Mobile Networks. IEEE Wireless Communications 2018, 25, 38–44. [Google Scholar] [CrossRef]
- Akhunzada, A.; Islam, S.u.; Zeadally, S. Securing Cyberspace of Future Smart Cities with 5G Technologies. IEEE Network 2020. [Google Scholar] [CrossRef]
- Gupta, S.; Parne, B.L.; Chaudhari, N.S. Security Vulnerabilities in Handover Authentication Mechanism of 5G Network. Proc. of the Intl. Conf. on Secure Cyber Computing and Communication; IEEE: Jalandhar, India, 2018. [CrossRef]
- Ziani, A.; Medouri, A. A Survey of Security and Privacy for 5G Networks. In Emerging Trends in ICT for Sustainable Development; Springer: Cham, Switzerland, 2021; pp. 201–208. [Google Scholar] [CrossRef]
- Cao, J.; Ma, M.; Li, H.; Ma, R.; Sun, Y.; Yu, P.; Xiong, L. A Survey on Security Aspects for 3GPP 5G Networks. IEEE Communications Surveys & Tutorials 2020, 22, 170–195. [Google Scholar] [CrossRef]
- Chettri, L.; Bera, R. A Comprehensive Survey on Internet of Things (IoT) Toward 5G Wireless Systems. IEEE IoT Journal 2020. [Google Scholar] [CrossRef]
- Li, S.; Xu, L.D.; Zhao, S. 5G Internet of Things: A Survey. Journal of Industrial Information Integration 2018, 10, 1–9. [Google Scholar] [CrossRef]
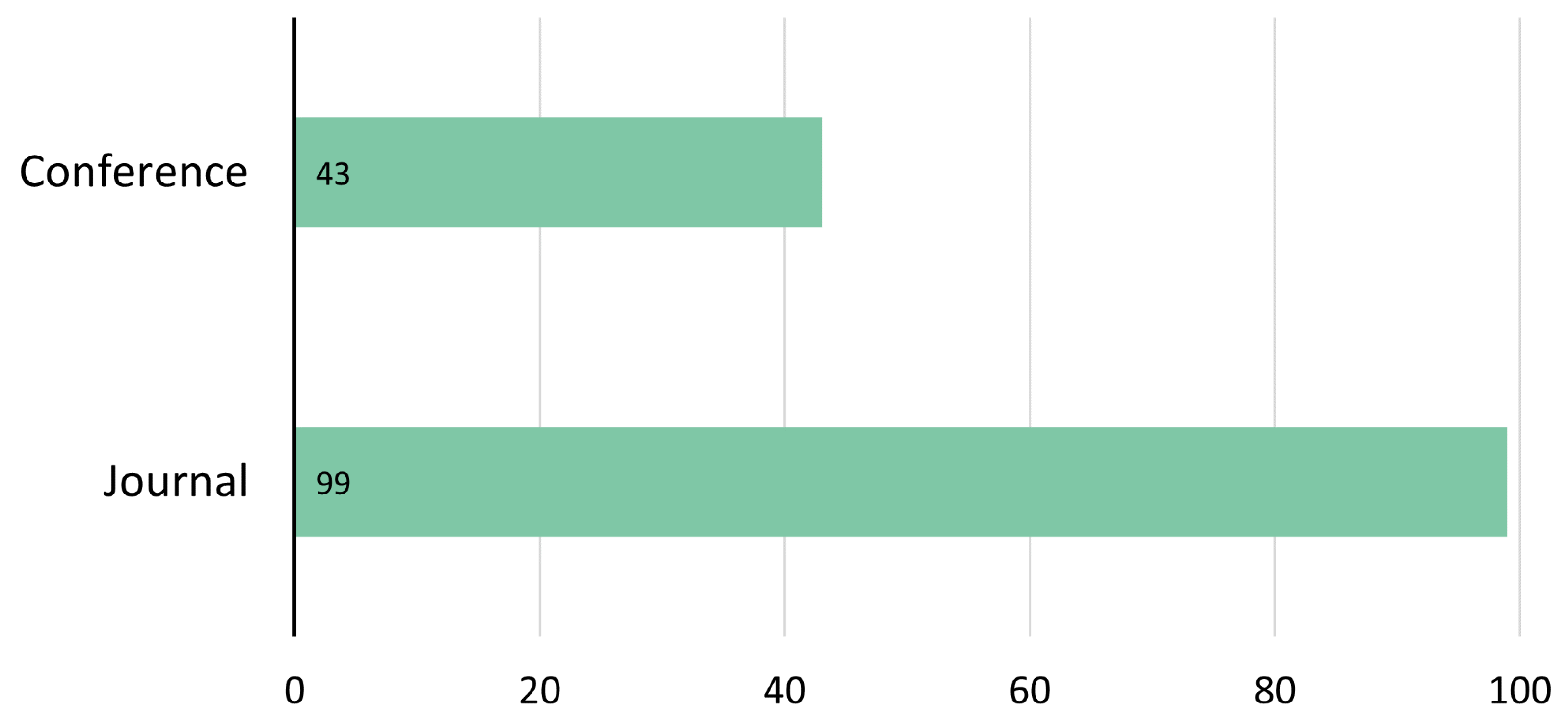
| Population | Internet of Things, Internet of Everything, IoT, IoE |
| Intervention | threat, vulnerability, solution |
| Context | 5G |
| Outcome | security, privacy, confidentiality, integrity, trustworthiness, protection |
| Scientific Repository | URL |
|---|---|
| ACM Digital Library | http://dl.acm.org |
| El Compendex | http://www.engineeringvillage.com |
| IEEE Digital Library | http://ieeexplore.ieee.org |
| Wiley Online Library | http://onlinelibrary.wiley.com |
| Scopus | http://www.scopus.com |
| Springer Link | http://link.springer.com |
| Reference | Problem | Main Objective | Proposed Solution |
|---|---|---|---|
| Qiao et al. [50] | IoT security in the context of massive spectrum sharing. | Secure massive access. | A framework for securing cellular IoT networks. |
| Qadri et al. [31] | SF and wormhole in the context of healthcare-IoT. | Secure patients’ data. | A blockchain-based cryptographic framework. |
| Ozdemir et al. [32] | Security of social assistive robotics. | Secure implementation. | A framework of social assistive robotics. |
| Vassilakis et al. [80] | Security in the context of multi-tenant MEC services. | Security analysis for virtualized small cell networks. | A framework for MEC in virtualised small cell networks. |
| Dib et al. [109] | Emergence of IoT malware. | IoT malware classification. | A multi-dimensional deep learning framework. |
| Ni et al. [67] | Security of network slicing and fog computing for 5G-IoT. | Authentication | Service-oriented authentication framework. |
| Mohammed et al. [81] | Security in the context of 5G IoT HetNets. | Preserve security. | A framework based on deep reinforcement learning. |
| Li et al. [82] | Security in the context of 5G-IoT systems. | Authentication. | Blockchain enabled zero-trust security framework. |
| Krishnan et al. [111] | Security in the context of fog-to-things computing. | Detecting attacks. | An autonomic multilayer security framework. |
| Huang et al. [83] | Security in the context of IoT. | Provide robust and transparent security protection. | A security framework. |
| Lagkas et al. [84] | Security in the context of UAV. | Protect drones as things. | UAV IoT framework. |
| Lawal et al. [112] | DDoS attacks in the context of IoT. | DDoS mitigation. | A framework for IoT using fog computing. |
| Jaiswal et al. [113] | Security in the context of IoT. | Maximize the secrecy rate of IoT systems. | A secure framework. |
| Rey et al. [110] | Malware in the context of IoT. | Malware detection. | A framework based on federated learning. |
| Ramezan et al. [13] | Security in the context of multi-hop cellular networks. | Compare secure routing protocols. | An evaluation framework. |
| Yadav et al. [24] | Vulnerabilities in the context of IoT. | Discover ways an attacker can breach a system. | A penetration testing framework. |
| Lee et al. [29] | Security in the context of industrial IoT. | Improve security. | A method for a secure cryptographic system on a chip. |
| Miloslavskaya et al. [85] | Security in the context of IoT ecosystems. | Information security incident management. | A blockchain-based system. |
| Kwon et al. [28] | Eavesdropping in the context of 5G-IoT. | Detection of eavesdropping. | An intrusion detection system |
| Miloslavskaya et al. [7] | Security in the context of IoT. | Improve security. | Applying the security intelligence approach. |
| Sharma et al. [92] | Security in remote diagnosis of IoT devices. | Secure validation of IoT devices. | Fuzzy logic for safety decisions and remote diagnosis. |
| Rim et al. [48] | DoS attacks in the context of 5G-IoT. | Detection and mitigation. | A system for defending and blocking attacks. |
| Anisetti et al. [43] | Security in the context of IoT. | Security assessment. | IoT security checker. |
| Mansour et al. [86] | Security in the context of smart interconnected networks. | Improve security. | Multi-layer security mechanism. |
| Jain et al. [114] | Security in the context of IoT ecosystem. | Improve security. | An intrusion detection system and network slicing. |
| Chitroub et al. [41] | Security in the context of IoT. | Secure mobile IoT deployment. | A solution based on the blind source separation method. |
| Ahmed et al. [51] | APT in the context of IoT. | Detection of APT. | A data-driven approach to detecting APT stages. |
| Rathee et al. [87] | Security of e-voting within IoT-oriented smart cities. | Improve security. | A secure e-voting mechanism based on blockchain. |
| Srinivasu et al. [45] | Security in the context of 5G-IoT. | Secured healthcare data communication. | A blockchain-based approach. |
| Shen et al. [58] | Security in the context of edge-assisted IoT. | Improve security. | A solution for the tradeoff between security and energy. |
| Osman et al. [25] | Security in the context of smart home IoT networks. | Reduce the attack surface. | A microsegmentation-based approach. |
| Hellaoui et al. [88] | Security in the context of 5G-IoT. | Provide optimized security levels. | An end-to-end adaptive approach. |
| Yujia et al. [74] | Security in the context of IoT. | Improve security. | An authentication mechanism. |
| Bordel et al. [89] | Security in the context of 5G-IoT. | Improve security. | A security mechanism. |
| Garcia et al. [90] | Security in the context of heterogeneous IoT networks. | Improve security. | A handover roaming mechanism. |
| Behrad et al. [40] | Security in the context of 5G-IoT. | Improve authentication and access control. | An authentication and access control mechanism. |
| Aqrabi et al. [91] | Security in the context of industrial IoT. | Improve authentication. | Physically unclonable function and a multi-layer approach. |
| Jung et al. [47] | Security in the context of IoT. | Improve security. | A secure gatekeeper system. |
| He et al. [27] | Security of intelligent transportation systems. | Improve access control. | An access control mechanism based on risk prediction. |
| Azad et al. [93] | Security in the context of IoT. | Improve authentication. | A self-enforcing authentication schema. |
| Tang and Keoh [57] | Security in the context of home area networks. | Improve security. | A scheme to secure data. |
| Lee et al. [116] | Security in the context of IoT. | Improve authentication. | A three-factor anonymous user authentication scheme. |
| Ambareen et al. [72] | Security in the context of 5G-IoT D2D communication. | Protect user information and data. | A secure authentication scheme. |
| Li et al. [117] | Security in the context of IoT applications. | Protect data. | Privacy preserving data aggregation scheme. |
| Shin et al. [73] | Security in the context of 5G-IoT. | Improve security. | Authentication, authorization, and key agreement scheme. |
| Yu et al. [56] | Security in the context of 5G NB-IoT. | Improve security. | Authentication and data transmission scheme. |
| Choudhury [118] | Identity privacy. | Protect identity. | A lightweight scheme. |
| Shin et al. [94] | Security of 5G and wireless sensor networks. | Improve security. | Two-factor authentication and key agreement scheme. |
| Cao et al. [54] | Security in the context of 5G NB-IoT. | Improve security. | Authentication and data distribution scheme. |
| Liu et al. [95] | Authentication in the context of crowdsourcing IoT. | Improve authentication. | Remote multi-factor authentication scheme. |
| Lu et al. [132] | Security in the context of MTC and 5G-IoT. | Improve security. | Traffic-driven intrusion detection scheme. |
| Kang et al. [122] | MITM attack in IoT networks. | Improve the detection. | A scheme using a hybrid routing mechanism. |
| Wu et al. [62] | Authentication in the context of 5G-IoT. | Improve authentication. | An authentication protocol. |
| Fan et al. [97] | Security in the context of 5G-IoT. | Improve authentication. | Ultralightweight NFC mutual authentication protocol. |
| Zhang et al. [123] | Security in the context of mobile IoT. | Improve security. | Security trusted protocol model. |
| Reference | Problem | Main Objective | Proposed Solution |
|---|---|---|---|
| Khumalo et al. [53] | Security in the context of IoT and D2D communication. | Improve security. | Group-based authentication and key agreement protocol. |
| Fan et al. [98] | Authentication in the context of 5G-IoT. | Improve authentication. | RFID mutual authentication protocol. |
| Das [99] | Security in the context of IoT. | Improve security. | Secure protocol for constrained environments. |
| Lopes et al. [39] | Security in the context of MTC and IoT. | Improve security. | Authentication and key agreement protocol. |
| Duguma et al. [100] | Security in the context of D2D and 5G. | Improve security. | Lightweight D2D security protocol. |
| Xiao et al. [63] | Authentication in the context of 5G-IoT. | Improve authentication. | RFID lightweight authentication protocol. |
| Shin et al. [101] | Security in the context of smart home IoT networks. | Improve security. | Security protocol for route optimization. |
| Khalid et al. [8] | Authentication in the context of IoT. | Improve authentication. | Ultralightweight authentication protocol. |
| Khalid et al. [96] | Authentication in the context of IoT. | Improve authentication. | Advance strong authentication strong integrity protocol. |
| Sharma et al. [16] | Authentication in the context of IoT. | Improve authentication. | Secure authentication protocol. |
| Nie et al. [131] | Security in the context of SDN-based IoT. | Improve security. | A differentially private tensor computing model. |
| Anand et al. [64] | Malware attacks in 5G-IoT healthcare applications. | Malware detection. | CNN-based deep learning model. |
| Zhang et al. [119] | Security in the context of industrial IoT. | Improve security. | Federated learning and transfer learning model. |
| Rajawat et al. [102] | Security in the context of 5G-IoT. | Improve security. | Boltzmann machine-based encryption algorithm. |
| Fu et al. [124] | Security in the context of 5G-IoT. | Improve detection. | Automata-based intrusion detection method. |
| Laguduva et al. [125] | IoT edge node security. | Improve security. | A model to identify an original or cloned PUF. |
| Mo [35] | Security in the context of industrial 5G-IoT. | Improve security. | A model for abnormal traffic detection. |
| Krundyshev et al. [120] | Security in the context of smart infrastructures. | Cyber attack detection. | Artificial neural network models. |
| Sadique et al. [3] | Data privacy in the context of IoT. | Protect data. | A model for data privacy enhancement. |
| Rawal et al. [103] | Security in the context of IoT. | Improve security. | An interstitial model. |
| Baniata et al. [130] | Security of fog-enabled mobile cloud computing. | Improve security. | A privacy-preserving model. |
| Rezvy et al. [77] | Security in the context of 5G-IoT. | Intrusion classification and prediction. | A deep learning model. |
| Ravi et al. [104] | Security in the context of 5G-IoT. | Analyze security aspects. | A testbed for security. |
| Taimoor et al. [66] | Security of IoT-based personalized healthcare services. | Improve security. | A methodology for developing health services. |
| Wang et al. [105] | Voice-transfer attack in industrial 5G-IoT. | Detection and mitigation. | A method for addressing voice-transfer attacks. |
| Wang et al. [133] | Binary black-box adversarial attacks. | Improve malware detection. | An adversary sample generation method. |
| Khan [115] | Security in the context of 5G-IoT. | Improve security. | ElGamal with public key infrastructure techniques. |
| Sankar et al. [129] | Security in the context of beyond 5G and IoT. | Improve security. | Private blockchain in SDN and an authentication method. |
| Catania et al. [128] | Privacy threats in the context of 5G-IoT. | Protect privacy. | An analysis methodology. |
| Lee et al. [127] | Security of online identification process in 5G-IoT. | Improve security. | Transaction linkage technique. |
| Sarac et al. [21] | Cyber-attacks on IoT devices. | Improve security. | Integrate security gateway architecture and blockchain. |
| Holik [60] | Security in the context of IoT. | Improve security. | Protection techniques based on SDN. |
| Lee et al. [121] | Android app-repackaging attacks on in-vehicle networks. | Mitigate the Android app-repackaging attacks. | A security technology as a countermeasure. |
| Cheng et al. [126] | APT in the context of 5G-IoT. | Predict APT. | Method based on differentially private federated learning. |
| Deebak et al. [107] | Security and privacy in the context of 5G-IoT. | Security and privacy preservation. | A blockchain-based lightweight distributed architecture. |
| Alvarenga et al. [59] | Security in the context of IoT. | Secure management. | A hybrid distributed ledger architecture. |
| Chopra et al. [42] | Security in the context of ultra-dense networks. | Improve security. | An architecture for security in ultra-dense networks. |
| Mrabet et al. [23] | Security in the context of IoT. | Improve security. | An optimized architecture for IoT. |
| Vangala et al. [108] | Security in IoT-enabled smart agriculture. | Improve security. | An architecture for smart farming. |
| Szymanski [106] | Security in the context of industrial-tactile IoT. | Improve security. | A secure deterministic industrial-tactile IoT core network. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





