1. Introduction
Randomness is the key ingredient of security of any cryptographic protocol, including quantum key distribution (QKD) protocols. To understand the role of randomness in the security of QKD, here we study so-called
detector blinding attack (DBA) [1-9] which injects strong light into the quantum channel and exploits technological weaknesses/features of the single-photon detectors used within, with the purpose of controlling the internal entropy source and thus break the security. This particularly successful attack strategy makes possible not only a completely undetectable eavesdropping, but also a full recovery of the secret key, thus defying two most notable strengths of QKD: 1) the ability to detect eavesdropping, and 2) the information-theoretic unconditional security of the generated secret key. Various adaptations of the DBA have been mounted on a range of scientific and commercial bipartite QKD systems [
1,
2] rendering them completely unusable even though their manufacturers have previously claimed them provable and unbreakably secure for years before the blinding attack has become publicly known.
Each instance of DBA is specifically tailored for a detector feature that is being exploited, for example: passive quenching [
5], active quenching [
4], superlinearity [
5], thermal effects [1, 2, 5] etc. as well as specific architecture of the receiving station, such as passive or semi-active base control. In the demonstrated attacks the optical power of the incoming blinding light ranges from up to 28 mW one-time pulse [
3], 8 mW continuous [
4], all the way down to a few pW continuous [
5] or even less than 120 photons per pulse [
6], which is a power span of over 15 decades! Most of scientific and research works propose to defend against a detector blinding attack by upgrading hardware so as to be able to detect strong light incoming from the quantum channel [10-14]. Apart from being technologically challenging, the main problem with that approach is that while it may prevent a particular attack, it does not guarantee restoring of provable security, as noted in Ref. [
4] and experimentally demonstrated in [
14]. Repelling the attack by "brute force. i.e. without a deeper understanding of how and why it works, leaves a metallic aftertaste that a clever modification of the attack could make it work again.
In this paper we investigate the information-theoretic background of this devastating attack strategy on so called "discrete variable QKD" that is, QKD protocols which communicate single qubits. We show that success of a blinding attack relies on the attacker's ability to obtain information on the receiver’s choice of detection base. In a detector blinding attack it is done by active sending a combination of a blinding light and a multi-qubit message with a purpose to take control over the internal entropy source which selects the base. Based on this insight, an elegant defense strategy is developed for preventing the whole family of multi-qubit attacks on receiver's entropy source, which restores the unconditional security of a QKD protocol. On top of that, by monitoring an additional parameter of the communication over the quantum channel, it is possible to detect a general entropy source attack at no further cost in hardware.
Even though blinding attack works well on virtually any QKD protocol [
8], for the sake of simplicity and without the loss of generality, we will study attacks on two implementations of the BB84 protocol [15-16], which were broken in Refs. [
4] and [
5].
2. BB84 protocol in a nutshell
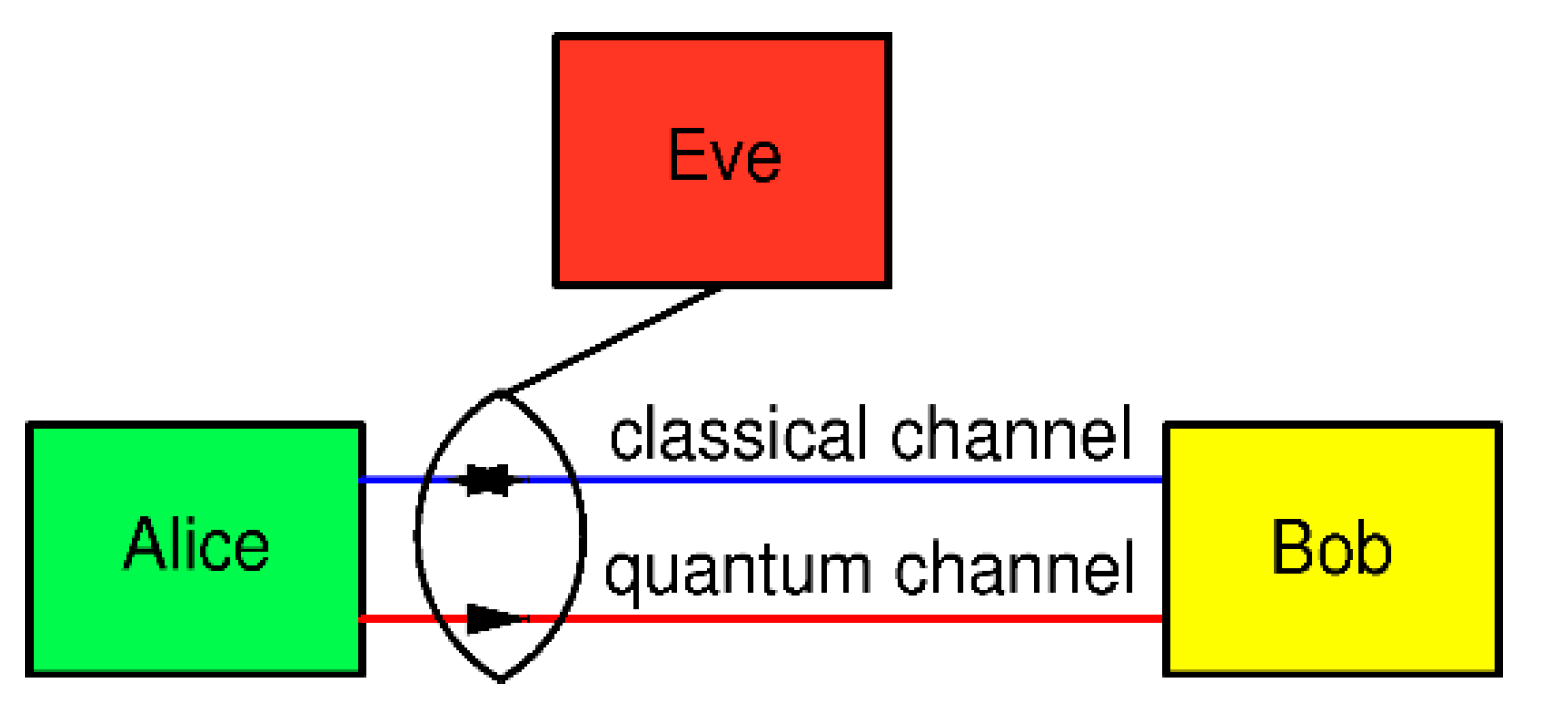
In the BB84 QKD protocol, two legitimate parties who wish to establish a secure communication, usually named Alice and Bob, are linked by one quantum channel and one authenticated (but not necessarily encrypted) classical channel, while an eavesdropper Eve has a physical access to both channels, as shown in Fig. 1.
Figure 1.
BB84 protocol scenario. Alice, the sending station, generates qubits and sends them to Bob through the one-way quantum channel (originally it was a 30 cm long air gap). Bob, the receiving station, receives and measures qubits. To accomplish the secret key generation, an authenticated, but not necessarily secret, two-way classical communication channel between them is necessary. It is assumed that an eavesdropper Eve has a physical access to both channels and any equipment allowed by the laws of Nature.
Figure 1.
BB84 protocol scenario. Alice, the sending station, generates qubits and sends them to Bob through the one-way quantum channel (originally it was a 30 cm long air gap). Bob, the receiving station, receives and measures qubits. To accomplish the secret key generation, an authenticated, but not necessarily secret, two-way classical communication channel between them is necessary. It is assumed that an eavesdropper Eve has a physical access to both channels and any equipment allowed by the laws of Nature.
It is assumed that classical communication channel is bidirectional and information-theoretic authenticated: Alice can be sure that she is talking to Bob, and vice versa. The messages exchanged between Alice and Bob over this channel need not be encrypted, which means that Eve can read them but cannot change them. The quantum channel is unidirectional: Alice uses it to send qubits to Bob.
In the first phase of the BB84 protocol, Alice sends to Bob, over the quantum channel, a random classical bit equiprobably valued 0 or 1, encoded in a linearly polarized qubit as follows: bit value 0 is randomly and equiprobably encoded as either 0o or 45o polarization, while bit value 1 is randomly and equiprobably encoded as either 90o or 135o. Alice typically uses an electronic quantum random number generator (QRNG) [17-22] in order to generate a qubit. Bob randomly selects one out of the two orthogonal bases in which the qubit is measured: (0o, 90o) or (45o, 135o). With probability of 1/2, namely when his base happens to match the polarization of the qubit, Bob obtains the exact bit value that Alice sent, while in the other case Bob obtains a random bit. To figure out which is the case, Bob discloses his base to Alice over the authenticated classical channel. Knowing which qubit she sent, Alice replies either "keep" in which case they keep the bit, or "discard" in which case they both discard their bits. This communication is repeated until Alice and Bob collect a sufficiently long raw key, for example until the length of bits, agreed beforehand, is reached. The repeated communication of qubits is performed periodically with frequency , which technically allows Bob to define a short period of time (henceforth gate time) around the expected time of arrival of qubits and in that manner reduce the effect of noise (dark counts). Note that, by listening to the communication over the classical channel alone, Eve is not able to figure out the value of the bit that is kept. Furthermore, she cannot fake any of the communication over the classical channel because it is authenticated. All she can do is to intervene in the quantum channel and listen to the classical channel. Ideally, after this initial phase, Alice and Bob end up with the same stream of bits, namely their secret common key. However, due to inevitable hardware imperfections such as: noise (dark counts and afterpulses in single-photon detectors), losses, bases misalignment, etc. as well as Eve's tampering with the quantum channel, there will be some differences (errors). In order to correct them, they need two further classical communication phases, namely information reconciliation and privacy amplification, which are performed over the authenticated classical channel.
The blinding attack is performed entirely in the initial phase in which the quantum channel is used, so we do not need to analyze the leftover two classical phases of the BB84 protocol. Furthermore, in a DBA Alice is never under attack, so her setup will not be discussed either.
3. Detector blinding attack on BB84 with passive base selection
In the receiving station (Bob), which has been broken in Ref. [
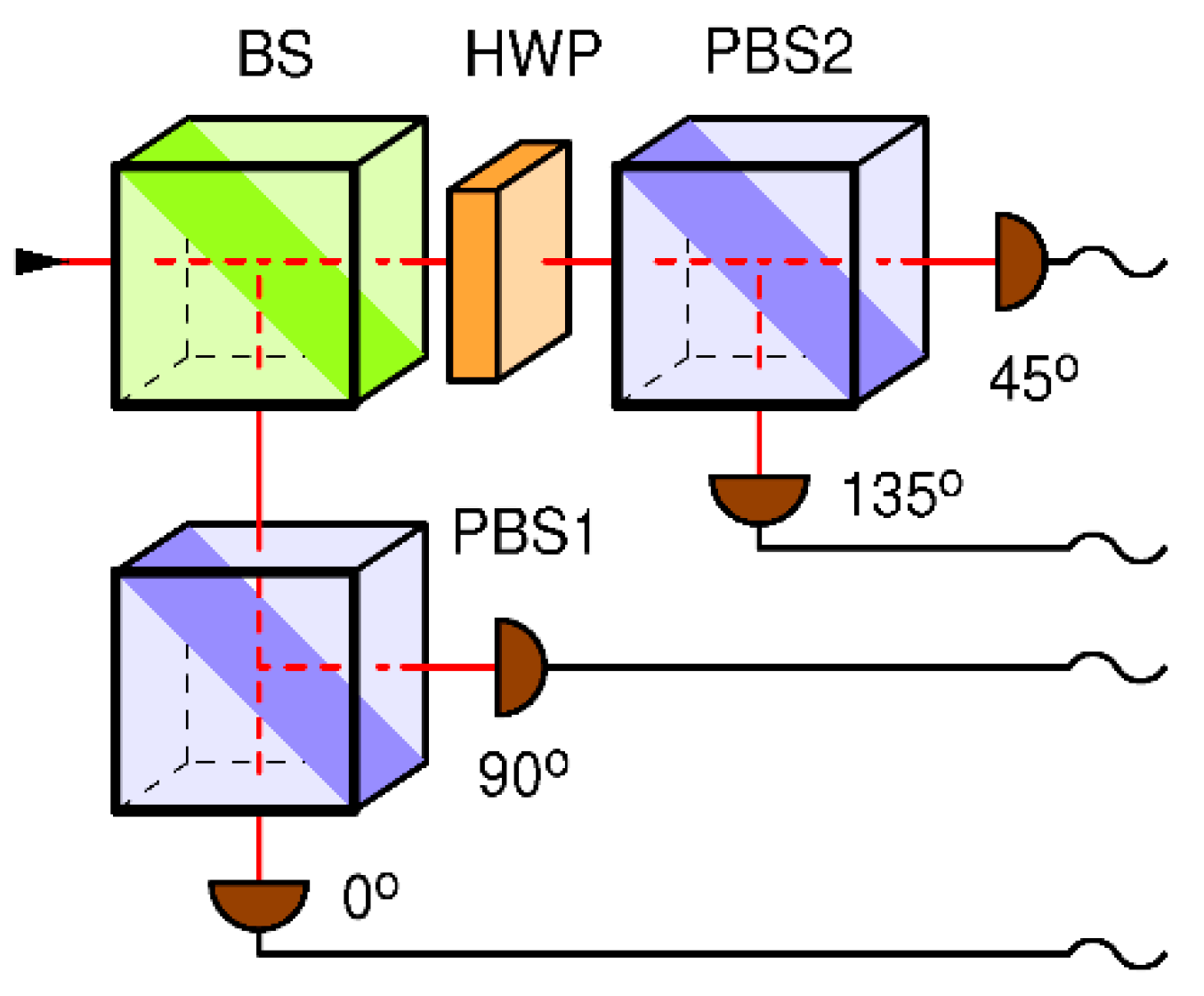
4], random selection of bases is performed passively, by help of a non-polarizing beam splitter (BS), as shown in Fig 2. Note that the sender (Alice) needs an equivalent of 2 random bits to generate the qubit state (namely to choose 1 out of 4 possible qubit states), while Bob needs an equivalent of 1 bit of entropy per received qubit to randomly choose its measurement basis (1 out of 2 possible bases), which mandates that each station must have a private random number generator or something equivalent of it. In the Bob setup, show in Fig. 2, the random selection of the receiving base is obtained through the use of the beam splitter BS.
Figure 2.
Receiver for BB84 with a passive random number generator: measurement basis is selected randomly by means of the first, polarization insensitive beam splitter (BS). Each base consists of a polarizing beam splitter (PBS) and two detectors. The (45o, 135o) base is realized by placing a properly rotated half-wave plate (HWP) in front of it.
Figure 2.
Receiver for BB84 with a passive random number generator: measurement basis is selected randomly by means of the first, polarization insensitive beam splitter (BS). Each base consists of a polarizing beam splitter (PBS) and two detectors. The (45o, 135o) base is realized by placing a properly rotated half-wave plate (HWP) in front of it.
The detector blinding attack (DBA), on this setup, works as follows. Eve cuts the quantum channel between Alice and Bob (e.g. an optic fiber or aerial link) and blinds simultaneously all four detectors in Bob by shining strong pulsed circularly polarized light of high enough intensity, as explained in Ref. [
4]. Each detector in Bob receives ¼ of the incident power of the blinding light. Pulses are powerful and frequent enough (~70 kHz repetition rate, 8 mW per pulse) to keep the detectors thermally blinded at all times during the qubit exchange. According to Ref. [
4], this blinding strategy generates a four-fold coincidence among all detectors upon every blinding pulse.
In the blind state, detectors are sensitive only to strong pulses of light brighter than some threshold power, superimposed on top of the blinding light, so called "fake states". For example, Eve can shoot a pulse polarized at 45o and of power just over . Half of the power would end up in the 45o detector making it click. The 135o detector will receive a negligible power while detectors in the other base will receive a little bit above each, thus none of the other detectors will click. Note that the success of the attack is not very sensitive to the pulse power as it can be anywhere between just above and just below , leaving quite a wide range for the attack to work on all 4 detectors which, for other security reasons, should be well matched in their specs anyway.
Eve measures Alice's qubit in a randomly selected base (either (0o, 90o) or (45o, 135o)) using a receiving station which is a close copy of Bob. Note that Eve is receiving Alice's qubits using the close copy of Bob's station and using the same protocol as Bob would. After the measurement, Eve sends to Bob a fake state matching her measurement, effectively copying her measurement result to Bob who then measures the same as Alice.
Finally, Eve passively listens to the classical channel between Alice and Bob and does whatever they do in the next two classical phases, namely the information reconciliation and the privacy amplification, in order to arrive to exactly the same "secret" key. Note that the attack does not introduce any extra bit error rate (BER). Since blinded detectors do not produce dark counts, a prudent Eve may send to Bob random fake noise pulses targeting each detector separately (at an individual dark count rate), thus not taking chances in case that Bob is monitoring dark count rates of the detectors. Note that, by Kerchoff's principle of cryptography [
23], Eve knows the dark count rates of Bob's detectors. She could, for example, in quite a realistic scenario, be the vendor of Bob's station and could have measured dark count rates (and all other relevant parameters) prior to selling it.
While it is deemed in Ref. [
4] that detector blindability is what makes the DBA viable, in this work we go a step further and seek for an insight at the level of information theory.
First we note that, in order for the DBA to work, Eve must make sure that Bob's and hers detection bases match, before sending him a light signal that contains an information. In the attack described above, fake states contain the information Eve wants Bob to receive, while continuous circularly polarized blinding light does not contain any.
Next, we note that a fake state pulse is split deterministically at the beamsplitter BS such that exactly one-half of its power hits each detection base. This is in stark contrast with BB84 where Bob receives a single qubit from Alice and where the BS serves as an internal and private entropy source which randomly selects one of the two Bob's detection bases. Apparently, due to the deterministic splitting of a fake state under DBA, entropy of this internal randomness generator is zero - the entropy source it effectively disabled. But, without the random selection of bases, Bob is unable to run the BB84 protocol. Whatever Bob is actually running, it is not the BB84. But he does not know that because he does not realize his entropy source has been compromised.
In the BB84 protocol, random base selection of the receiving station is a pivotal and indispensable ingredient of the security. Let us investigate this in more detail. As explained above, as per original BB84, Bob must calculate his reception base in order to be able send this information to Alice. He does that based upon his detections. Namely, if either detector 0o or 90o fires then Bob concludes that his random base is 0, if any the other two detectors fire then the base is 1, and finally if no detector fires or more than two detectors fire (e.g. due to the noise) then the communication instance is inconclusive and must be discarded. If Bob is monitoring randomness of the sequence of bases (even though this is not a part of BB84), he would notice a perfect randomness. But how can this be when his own entropy source is incapacitated? Obviously, the randomness of his detection bases can be traced back to the beampslitter BS in Eve's station, which is still functioning in the quantum regime because it is receiving single qubits from Alice. This means that Eve and Bob are now logically united into one receiving station. Eve-Bob. which performs a correct BB84 protocol with Alice. In effect, Eve has sneaked into Bob's station (even though she might be physically far away) and is able to obtain enough information to arrive to the exact same key as Alice and Bob.
What information Eve obtains? The DBA allows Eve to directly set the detection outcome of any of the four detectors in Bob thus she knows everything that Bob knows. Indirectly, she also gains knowledge of Bob's bases. It is tempting to conjecture that if Bob is monitoring proper operation of his detectors, e.g. by making sure they are not blinded and are sensitive to single photons, then devastating attacks like DBA are impossible.
But, could Eve mount a successful attack without blinding the detectors? To answer that, we consider two scenarios.
In the first scenario let us suppose Eve is able to set Bob's receiving base by some means other than detector blinding. Then, her best strategy would be to set Bob's base so as to match hers, but this time she would send to Bob a single qubit matching her measurement. Bob would detect the same bit as Eve, without any increased loss or error with respect to when Eve is absent. Thus, Eve would obtain all the information as in the DBA and would stay invisible.
In the second scenario Eve succeeds without having a control over Bob's bases. Let us suppose that Bob himself is choosing his reception base randomly (e.g. by help of a true random number generator or equivalent), but that Eve somehow gets the information about the base before receiving Alice's qubit. Now, Eve may set her base to match Bob's, receive Alice's qubit and send to Bob a qubit that matches her measurement. Eve would again obtain the key and would stay invisible. Note that in both of those scenarios, communication is performed via single qubits and thus Bob's BS will operate in the quantum regime and will introduce a 3 dB loss of useful signal. However, this amount of loss is not a problem for Eve, as will be clarified later.
From this discussion one can see that if Eve has the information on Bob's bases on time, the whole QKD protocol is doomed - it would give no security whatsoever with or without blinding of detectors. We conclude that Eve's success relies in DBA solely on the fact that her mutual information with Bob's choice of bases is maximal:
where
is a random variable describing Eve's knowledge on Bob's receiving bases during all
rounds of the initial phase of BB84, and
is a random variable describing Bob's knowledge on his receiving bases. The base codes
and
have a value 0 for (0, 90) base and 1 for (45, 135) base.
The DBA is just a technique by which Eve obtains the mutual information of Eq. (1) in full.
4. Detector blinding attack on BB84 with semi-active base selection
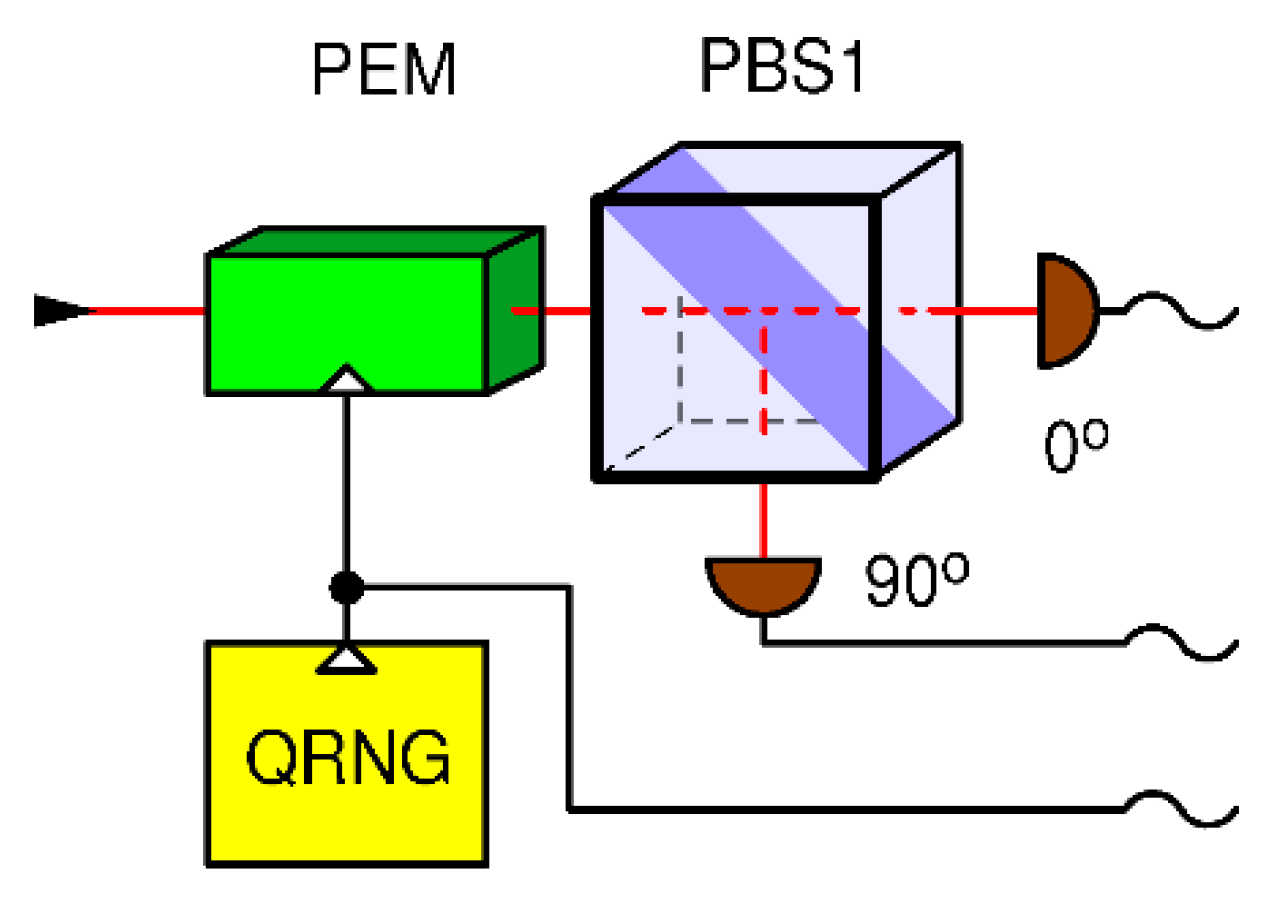
In the receiving station (Bob) which has been broken in Ref. [
5], random choice of detection bases is performed actively by means of a phase electro modulator (PEM) driven by an explicit electronic QRNG, as shown in Fig. 3. The state of the QRNG (0 or 1) determines the receiving base. According to the above discussion, we assume that the QRNG is private meaning that it cannot be manipulated nor predicted by Eve. This base choice technique functions exactly as required by BB84 for single qubits. It also diverts all the incoming power of a strong fake state to the selected base.
Figure 3.
Receiver for BB84 with an active receiver with phase electro-modulator (PEM): measurement basis is determined by the quantum random number generator (QRNG) controlling the PEM.
Figure 3.
Receiver for BB84 with an active receiver with phase electro-modulator (PEM): measurement basis is determined by the quantum random number generator (QRNG) controlling the PEM.
The version of DBA used against this setup works as follows. Eve again cuts the quantum channel between Alice and Bob. She blinds simultaneously all four detectors in Bob by shining strong continuous (CW) circularly polarized light of a carefully tailored intensity, as explained in Ref. [
5]. Note that circularly polarized light distributes evenly among the detectors regardless of the state of the PEM, and thus Eve is able to simultaneously blind, and keep blinded forever (or at least during the qubit exchange phase), both of the detectors, and thus both bases. Note that while the active control of PEM works correctly for qubits and fake states, it has no effect on the blinding light. Therefore, we name the setup in Fig. 3 "semi-active". As in the previous DBA, blinded detectors are sensitive only to fake states pulses brighter than a threshold power
, superimposed on top of the blinding CW light, which confines the fake state power to the range between slightly above
and slightly below
.
The difference to the previous setup (shown in Fig. 2) is that, here, Eve is able to copy her measurement to Bob with only 50% success, namely in those instances where her base coincides with Bob's by a chance. In the other 50% Bob's blinded detectors receive nothing and the bit is lost. Next, by passively listening to the classical communication between Alice and Bob in the next phases of the BB84 protocol, Eve is able to figure out which bits were lost, sift the same bits as Alice and Bob do and recover 100% of the key. While this attack reduces the key rate by a factor of 2 (equivalent of channel loss of 3 dB) with respect to when Eve is not there, the security situation is not satisfactory because Eve still obtains the full key and, in the presence of other losses or a strongly varying loss, she might just get away undetected. In fact, Eve might place her away from Bob, such that the channel loss between them is at least 3 dB, in which case the loss would be compensated because her fake states Bob detects with no loss. In fact, if the channel loss between Eve and Bob is greater than 3 dB, Eve will have to fake an additional loss, not to raise suspicion, which is technically quite easy. On top of that, note that Alice and Bob have no secure way of calibrating the key rate because Eve might decide to be present all the time and introduce the 3 dB loss when not eavesdropping and remove it when she does. This architecture of receiving station (Fig. 3) has also been shown vulnerable to the weak pulse (~120 photons) attack with an early test prototype of superconducting nanowire single-photon detectors exploiting their superlinear behavior and/or their great sensitivity to thermal effects [
6].
The technical reason for this relative success of Eve even with the "semi active" control of bases is that regardless of the state of the PEM, incident circularly polarized light is equally distributed among the 4 detectors which enables Eve to keep them blinded all at all times. The theoretical problem is that it does not satisfy assumptions under which the BB84 protocol has been proven secure (e.g. [16, 24]) namely that a light received by Bob's station must hit not more than one base at a time, which is an implicit assumption of a single-qubit communication. This assumption is violated in the setup in Fig. (3).
5. Improved setup with a fully-active base selection
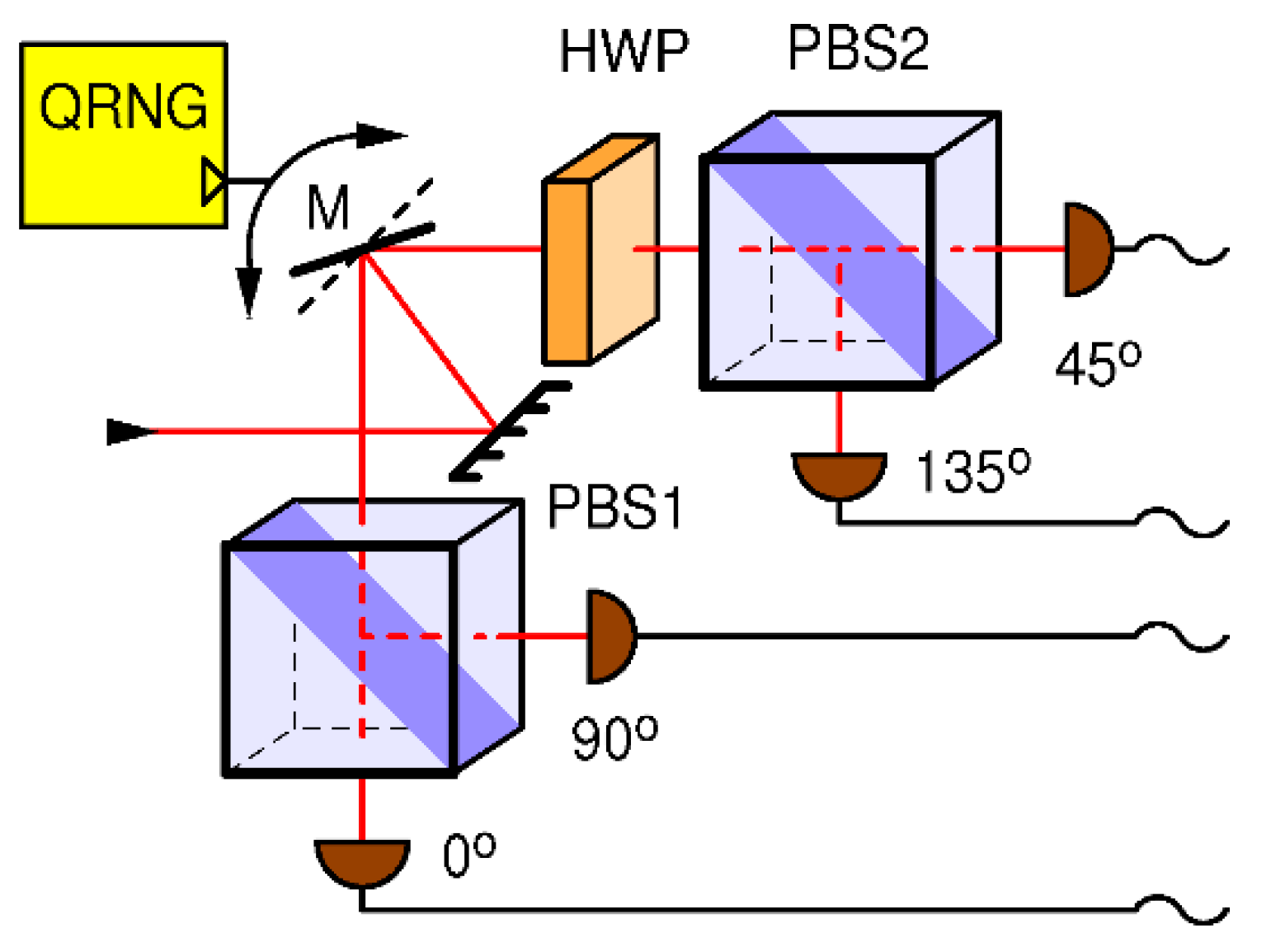
Following the discussion above, we propose an improved receiving station, shown in Fig. 4. It consists of two physically distinct detection bases and a mirror which directs all incoming light to one and only one base under control of a local and private QRNG.
Figure 4.
Receiver for BB84 with an exclusive active receiver: receiving basis is determined by the quantum random number generator QRNG, which flips the mirror (M) between two possible angles each of which reflects all light into one and only one measurement basis.
Figure 4.
Receiver for BB84 with an exclusive active receiver: receiving basis is determined by the quantum random number generator QRNG, which flips the mirror (M) between two possible angles each of which reflects all light into one and only one measurement basis.
Such a switching mechanism is allowed by laws of quantum mechanics and could be implemented for example by a motorized mirror, a MEMS router [25, 31], a mechanical switch inside optical fibers [
26] or electro-optically controlled Mach-Zehnder interferometer (MZI) 2x2 port switch [
32]. While micro mechanical mirror switches offer switching times down to a microsecond, MZI offers sub-nanosecond switching times and is suitable for photonics integration. Whatever the technique would be used, it is imperative that it is polarization insensitive and does not introduce high losses. For all of these techniques, insertion loses of a fraction of a dB have been demonstrated which is quite acceptable given the total loss budget of a typical quantum channel. For simplicity of discussion, but without the loss of generality, we assume that the four detectors operate in the free-running mode, meaning they are ready to detect at all times except when in the dead time. In particular that means that gating is assumed to be implemented at the level of data analysis, not at the level of disabling the optical sensors. If the latter is preferred, for example to reduce noise, a modification with double-gating can be implemented that would preserve sensitivity to out-of-gate thermal blinding. We will now analyze how this setup operates under a DBA attack.
The DBA attack requires careful tailoring of characteristics of the blinding light (e.g. its power, polarization, whether it should be a CW or a pulsed light, etc.) as well as precise modeling of single-photon detectors, in order to arrive to a reliable blinding technique for a particular receiving station. The difference of the proposed receiver (shown in Fig. 4), with respect to the two previous receivers (shown in Figs. 2 and 3), is that here only one (randomly selected) base receives light, while the other base is in darkness. Following the previous discussion, we will differ two cases: the continuous blinding light and the pulsed blinding light.
In case of the continuous blinding light attack on the new receiver Eve cannot keep blinded both bases at all times nor is her attack invisible. Namely, whenever the QRNG changes the receiving base, the two detectors that were previously in dark get both simultaneously hit by a strong blinding light. One is able to predict what happens then without any modeling of a particular detector. When a single-photon sensitive detector, which was previously in the dark and ready to detect, gets hit by a strong light, it will detect, that is produce a "click. an output pulse signifying a detection, at least once. This is because the sensor will do exactly what it is supposed to do when a single photon is detected: for example, an avalanche photodiode will become highly conductive while a superconductive nanowire will become highly resistant. Such transitions will necessarily generate a detection signal. The detector(s) in question may become blinded, but that will happen only after that initial detection. As explained before, because not being able to decide which state was sent, Bob will have to announce such events discarded: this will happen in 50% of gates. In the other 50% of gates Eve is able to send her measurement to Bob with probability of 1/2 (in total 25% of gates) namely in those instances where her base coincides with Bob's randomly selected base by a chance, while in the remaining 25% gates Bob will receive nothing (his detectors will remain silent), resulting in 4-fold drop of the effective key rate with respect to no eavesdropper. Even though this higher loss, equivalent of 6 dB, introduced by Eve, is in principle easier to detect by Alice and Bob, this is still not satisfactory because: a) Eve may be able to compensate for the loss (as explained before); and b) Eve can obtain a complete knowledge of the key without being detected.
In case of the pulsed blinding light, very strong laser pulses keep detectors thermally blinded. In the original DBA described in Refs. [4, 7], performed on the setup shown in Fig. 2, it is noted that such strong pulses will cause simultaneous detection in all affected detectors. Because of that, Eve keeps the blinding pulses outside of gate so that they do not generate extra in-gate coincidences, and shoots them frequent enough to keep all the detectors blinded at all times. However, when this attack is applied to the setup in Fig. 4, Eve is not sure which base gets blinded, because bases are selected at random with probability 1/2, therefore she needs to rise the blinding rate by at least twice. Even so, because of the binomial statistics of base selection, occasionally a base might get out of blinding and generate an extra in-gate coincidence when hit by a fake state. While details of this behavior would have to be investigated further, it is safe to assume that, in her best scenario, Eve will be able to achieve blinding and retrieve the full key, albeit at the expense of 6 dB loss caused merely by the random base choice. The un-avoidable price paid for the pulsed blinding is causing the out-of-gate coincidences between the two detectors in the active (selected) base.
5.1. Attack analysis
From the discussion above, it would naively seem that Eve can successfully eavesdrop on the receiver in Fig. 4 using blinding techniques. However, this particular setup enables yet another lever arm available to Alice and Bob to defeat Eve, which relies on monitoring in-gate and out-of-gate coincidences.
Let us first discuss a regular quantum communication with single qubits, in which Bob knows the arrival time of Alice's qubit and opens a short detection time window
, named "gate. around it, to detect the qubit. In order to have a non-zero secret key rate of the BB84 protocol, the bit error rate of the first phase must be
% [
27]. The dark count occurrence probability during the gate for a single detector is:
where
is the dark count rate (DCR) of the detector and
is duration of the gate. The right-hand approximation is valid for
, which is often the case. Bob can confidently determine the dark count rates for all four detectors by disconnecting the receiver from the quantum channel and performing measurements in the dark. To simplify calculation, we will henceforth assume equal DCR for all detectors. DCR-caused "accidental" coincident detection between a pair of detectors belonging to the same base is a Poissonian random event. Its probability during the gate-open period
, or "in gate" probability, is given by:
When receiving qubits, the coincidence rate between two detectors forming a base, is described by the Hong-Ou-Mandel (HOM) effect, which characterizes the probability of simultaneous photon detection at the two outputs of a beamsplitter [
28]. By considering a coherent input state qubit, emitted from Alice with an average photon number
within a gate-open period
, the per-gate-coincidence-probability measured by Bob in any of its two bases is given by [
29]:
where
is Bob's system quantum efficiency, which includes effects of finite detector quantum efficiency, optics imperfections and other losses in Bob, while quantum channel efficiency
is a fraction of qubits that survive through the quantum channel connecting Alice and Bob. The right-hand approximation is valid for
, which holds true in a practical QKD where typically
and
while loses can be anywhere between a few dB and few tens of dB. The overall factor
equals probability that the qubit is in a "wrong" base. In the case that the base is "right" for the given qubit, there will be no coincidence in principle because photon will end up in only one detector. Here we neglect a possible imperfection in Bob's polarizers, which in may allow for a small probability of coincidence (typically less than 0.01). The coincidence probability is composed of both the accidental coincidences and qubit-related coincidences. Both being Poisson random processes, the total in-gate coincidence probability
, for the regular BB84 protocol in setup in Fig. 4, is given by:
As an example, assuming the following realistic values: gate time ns, the dark count rate cps, average photon number in a qubit , Bob's system quantum efficiency , and the quantum channel transfer efficiency (-8 dB), one arrives to .
Using the same approach, we can calculate out-of-gate coincidence rate for DCR:
The qubits do not fall outside of gate and therefore do not cause out-of-gate coincidences:
The total out-of-gate coincidence probability, for the regular BB84 protocol in setup in Fig. 4, equals:
where
is rate at which Alice emits qubits. Using the same set of communication parameters as in the previous example and
MHz, one arrives to
.
Our defense strategy relies on the fact that both in-gate and out-of-gate coincidence probabilities, described by Eq. (5) and Eq. (8), are dramatically enhanced under a strong-light attack, as will be shown below.
The case of the CW DBA. Let
be the number of photons arriving during a gate onto a detector. Then the probability
that the detector, having a quantum efficiency
, will detect at least once is given by [
29]:
or even closer to unity in case of superlinear detectors [
6]. Considering a coherent blinding light, with an average photon number
arriving on Bob during a gate, the overall coincidence probability, according to Eq. (9), is:
Assuming an attack using as few as photons incident on Bob per gate, and assuming that , then the coincidence probability is about and it would quickly approach theoretical maximum of for a larger . This is about 6 orders of magnitude higher than in-gate coincidence probability of the regular BB84 protocol, , as calculated above, even though the incident optical power considered in this example is much smaller than required for an actual detector blinding attack.
In the case of the pulsed DBA, which operates upon the principle of thermal blinding with a strong out-of-gate pulses, such an attack will not enlarge in-gate coincidences between detectors in the same base. However, as explained above, each blinding light pulse will create one out-of-gate coincident pair of detections in two detectors belonging to the base which is currently selected by the QRNG. The coincidence probability for either detection base, per gate, is given by:
where
is a minimum required blinding pulse rate being 70 kHz according to [
4] and, as explained above, this needs to be at least doubled by Eve because of the active base selection in this setup. As justified above, we do not add dark counts to that rate.
Assuming kHz and other parameters the same as in the previous examples, we obtain . On the other hand, the coincidence probability of the undisturbed QKD , as calculated above, is more than 6 orders of magnitude smaller.
This demonstrates that, both in the in-gate and in the out-of-gate DBA, the corresponding coincidence probabilities will be strongly enhanced with respect to the undisturbed BB84, when using the setup shown in Fig. 4. This fact is the basis for our defense strategy, which should work for any type of strong light attack, DBA included.
The high ratio of coincidence probabilities under the DBA attack and in the normal communication is robust across a realistic range of communication parameters. For example, in an extreme state-of-the-art communication having qubit rate GHz and the gate time ps, the in-gate ratio stays the same while the out-of-gate ratio gets 100 times greater. In fact, given all other parameters constant, the in-gate ratio is almost independent of and , while the out-of-gate ratio is roughly proportional to in the range between 1 and 1000 MHz.
5.2. Proposed defense strategy against strong-light attacks
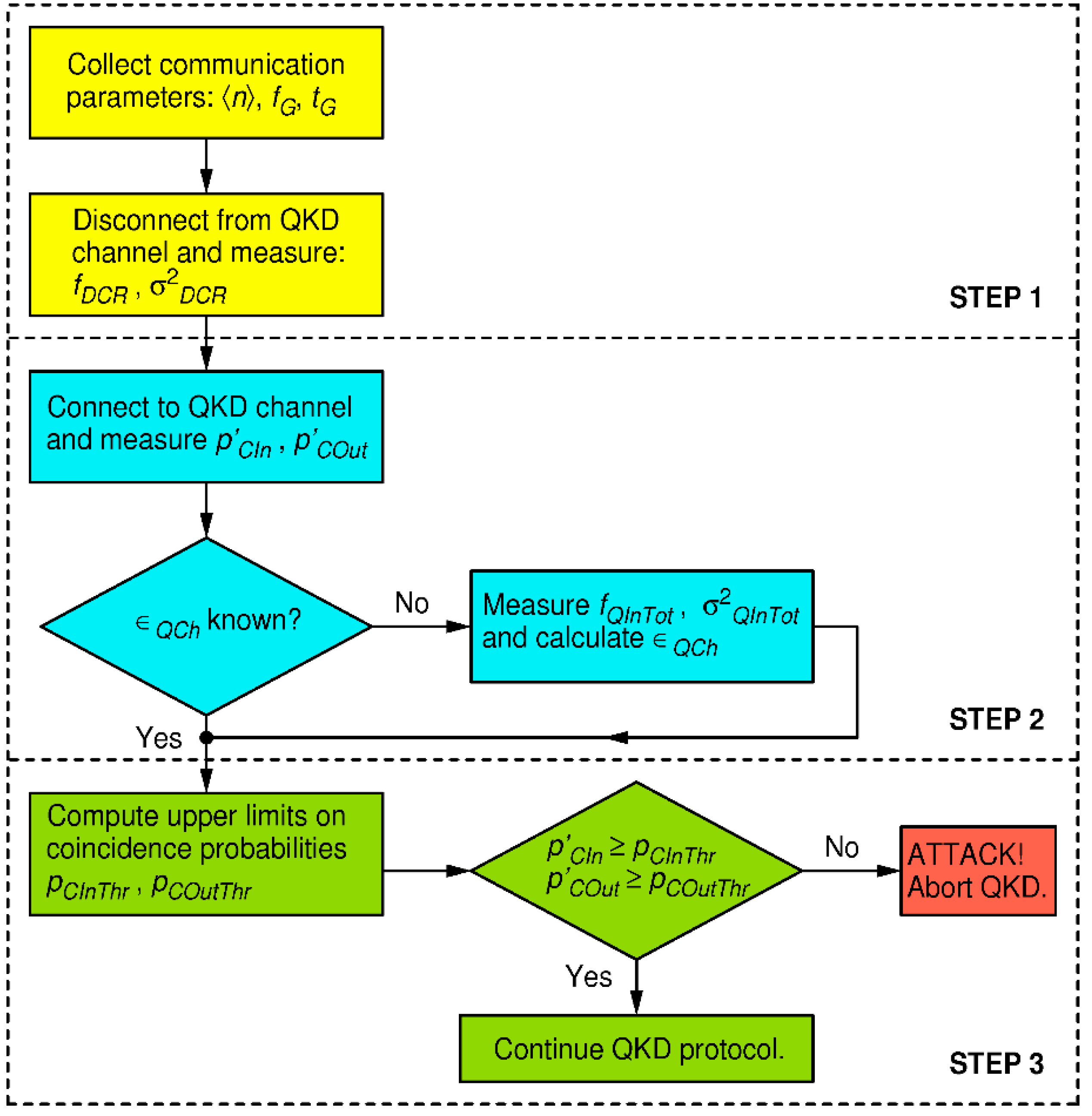
To defend from strong light attacks, we focus on two pairs of equations: on one hand Eq. (5) and Eq. (8) which model in- and out- of-gate coincidence probabilities during execution of a pristine BB84 QKD protocol, and on the other hand Eq. (10) and Eq. (11) which model the same coincidence probabilities, but under a strong-light attack. The huge rise in coincidence probabilities under a strong-light attack, even for injected light level far less than required to mount an actual blinding attack, presents a robust figure of merit for discerning the undisturbed quantum communication from an attack condition. In modern QKD systems, output of each detector is connected to a dedicated channel of a time-tagger and time stamps are recorded, thus the above probabilities can be evaluated by a simple data analysis. The defense strategy, valid for the receiver in Fig. (4), is outlined by the flow chart in Fig. 5, while the details are worked out below.
Figure 5.
Flow chart of the defense strategy for the proposed receiver of Fig. 4.
Figure 5.
Flow chart of the defense strategy for the proposed receiver of Fig. 4.
In the first step, one collects information about Bob's system quantum efficiency , dark count rates of all four detectors, where index marks the detector dedicated for measuring of the k-th polarization (namely linear polarization of angle ), and estimate their respective statistical uncertainties . As before, in order to simplify treatment, but with an obvious extension to the general case, we henceforth assume that all detectors exhibit the same dark count parameters: and . All these parameters may be known in advance. Alternatively, one may disconnect Bob from the quantum channel and perform an appropriate set of measurements (calibration) to obtain them. We also assume that parameters , , are known or negotiated before the start of QKD protocol. While Eve may know all of these parameters (by Kerchoff's principle), she may not influence them.
In the second step, during the quantum communication session (namely the first phase of BB84), one measures Bob's in-gate and out-of-gate coincidence probabilities related to reception of qubits, namely
and
. For example,
is evaluated as the sum of rates of coincidences between pairs of detectors (0, 2) and (1, 3) that happen only during gates, divided by the rate of gates
. Similarly is evaluated
except that said coincidences are now counted out of gates. Furthermore, if the quantum channel transmissivity
is not known/calibrated beforehand, it should be estimated. To that end, one measures the total rate of detections of all four detectors within coincidence windows,
and estimates its variance
. The qubit reception probability is then equal to:
According to Eq. (10), for undisturbed BB84, it should be equal to:
Solving for
gives:
Note that Eve does not control nor , but she can manipulate apparent to a certain extent. On one hand, she could make lower by randomly omitting qubits from Alice, but that would not enable her to increase her information on the resulting key, while the key would only get shorter for all three parties. On top of that, communication-induced coincidence probabilities would became smaller, thus ratio of probability of blinding-induced coincidences would rise in comparison to ones from the communication. That would make Eve's attack more easily discoverable. On the other hand, she could make higher, by removing a (part of) loss she induced beforehand, as explained before, if any. In that case, she must "invent" new qubits for Bob that would cause rising of BER, causing Alice and Bob to remove this extra information in the privacy amplification so Eve will not gain any new knowledge on the key, nor would the effective key length change. By doing so, her discoverability would get smaller by a factor she enlarged , but that is not a significant gain, as will be shown below.
Before going to the final step, one needs to estimate the statistical uncertainty of
. To that end we assume that predominant uncertainty of
comes from statistical uncertainties of
and dark count rates. We further assume that qubit detection and dark counts are Poissonian events. It is then straightforward to show, using standard statistical theory of propagation of uncertainty, that its variance is given by:
At the end of this step, following parameters, pertaining to the hardware and the quantum communication, are known: , , , , , , , , , and . These are input to the final step.
In the third and final step, one calculates upper limits on probabilities of in- and out- of gate coincidence probabilities for undisturbed QKD communication ( and , and compares them to the directly measured probabilities of in- and out- of gate coincidence ( and ) in order to detect whether the QKD system is under attack, at a desired (arbitrary) level of confidence.
The in- and out- of gate undisturbed coincidence probabilities
and
can be estimated using Eqs. (5) and (8) respectively and parameters available from the previous step. Their respective variances are:
Next, without any assumption on the statistical distribution(s) governing their values, one can find the respective upper limits on those probabilities, using Chebyshev's inequality [
30]:
Having in mind that all variables in the above equation are positive, an upper limit on
is given by:
which can be interpreted as:
where
is an arbitrarily chosen probability (confidence level) that inequality
holds. Equivalently we obtain:
Finally, we define the following security criterion. If both inequalities below hold:
one is to conclude that the QKD session is not under a DBA with confidentiality level of
. On the other hand, if any of the two inequalities fail, then the session is insecure and should be aborted.
Let us now work out one numerical example. We assume the same realistic parameters as above for easier comparison, namely: , MHz, ns, , kcps, on top of that cps, total in-gate detection rate cps, and kcps. From Eqs. (12), (14) and (15) we obtain: , and . Then, Eqs. (16) and (17) yield: and . Finally, even requiring a very high confidence level of 99.9999% , Eqs.(20) and (21) give a rather small/strict threshold values on coincidence probabilities: and .
The criterion in Eq. (22) tells us that as soon as or one concludes, with 99.9999% confidence, that the session has been compromised. To appreciate the discerning capability of this defense, we should recall that for the DBA attacks described in the previous section, using the same values of communication parameters, we got and which is several orders of magnitude higher than their respective thresholds and . We conclude that it is very unlikely that any multi-photon attack strategy would pass the criterion Eq. (22) in conjunction with the setup of Fig. 4.
6. Discussion and conclusion
In this work we investigate the merit of internal entropy sources on security of QKD. To that end we study a particularly vicious "detector blinding attack" (DBA) which was successfully demonstrated on the most frequently used architectures of QKD receivers used for the BB84 protocol, as described in the literature. By virtue of DBA, an attacker (Eve) is able to obtain a perfect copy of the key agreed upon between the two legitimate parties (Alice and Bob) while staying undetected. While most of the defenses described in literature consist essentially in detecting a strong light incoming from the quantum channel, authors of DBA have shown that such counter-measured can be defeated, as discussed in the introduction. Therefore we took a different path. Noting that the necessary condition for success of a DBA is Eve's ability to gain control over the internal entropy source of the receiver station (Bob), we modified the setup such that the mentioned condition cannot be met.
We show that even though the successfully attacked passive (Fig. 2) and semi-active (Fig. 3) receiver configurations, as well as here proposed fully-active (Fig. 4) one, are all seemingly functionally equivalent, only the latter is secure against attacks on the internal entropy source. Namely, a circularly polarized light incident on the passive or the semi-active setup will distribute its power evenly between all detectors present in the setup. This gives Eve an opportunity to blind the detectors and consequently manipulate their detections. On the other hand, in the proposed fully-active receiver, light never falls on all detectors simultaneously: it can only hit one detection base at a time. Whenever the blinding light is switched from one base to another which was previously in the dark, the two detectors belonging to that base will generate a coincident detection with a very high probability, orders of magnitude higher than in the normal (undisturbed) quantum communication where correlations of that sort are highly suppressed by design. In essence, our attack defense consists in comparing the measured coincidence probability to the level expected from the undisturbed quantum communication: if it is higher then the system is under attack.
In the passive and the semi-active setups, an information-theoretically perfect random number generator (QRNG), required for selecting the receiving base, is realized by the front-end non-polarizing beam splitter which can be directly accessed by Eve via the quantum channel. A subtle difference of our proposed setup is that it makes use of an explicit QRNG which within itself collapses the wave function and outputs entropy in form of a classical information. Such an entropy source does not accept any information from communication channels and consequently cannot be controlled nor predicted by Eve. Thus, we deter the DBA, in fact any strong-light attack, at the conceptual level, by disabling for Eve the possibility of manipulating or reading-out the internal entropy source of Bob.
The modified receiver setup and the statistical criterion for recognizing a strong-light attack, are the main contributions of this work. From the rigorous mathematical treatment and examples, it is clear that the proposed statistical criterion has an overwhelming discerning power between a genuine quantum communication and an attack by a strong light. We believe that our approach of ensuring the provable security, being non-specific to any particular version of a DBA, should have a higher resilience against modifications of DBA that may be conceived in the future.
But even so, we think that neither this, nor any other defense strategy, voids the necessity of monitoring of the proper functioning of the single-photon detectors, as well as all other active or passive components of both QKD stations: Alice and Bob alike, as well as the characteristics of the quantum channel. All this is needed to keep the whole system compliant with security proofs at all times. The absence of such a monitoring, as well as laconic use of an exposed beam splitter as an entropy source in the receiving station, opens a possibility for devastating attacks, as has been demonstrated on a number of scientific and commercial QKD systems. The lesson learned from this is that real-world implementation of a QKD protocol should be done with utmost care and constant monitoring of compliance with its theoretical idealization.
Acknowledgments
Ministry of Science and Education of Republic of Croatia, grant KK.01.1.1.01.0001. Author is indebted to V. Makarov for insightful discussion.
References
- L. Lydersen, C. Wiechers, C. Wittmann, D. Elser, J. Skaar, and V. Makarov. Hacking commercial quantum cryptography systems by bright illumination. Nat. Photonics 2010, 4, 686–689. [CrossRef]
- I. Gerhardt, Q. Liu, A. Lamas-Linares, J. Skaar, C. Kurtsiefer, and V. Makarov. Full-field implementation of a perfect eavesdropper on a quantum cryptography system. Nat. Commun. 2011, 2, 349. [CrossRef] [PubMed]
- Lydersen, L. , Akhlaghi, M. K., Hamed Majedi, A., Skaar, J., & Makarov, V. "Controlling a superconducting nanowire single-photon detector using tailored bright illumination. New J. Phys. 2011, 13, 113042. [Google Scholar] [CrossRef]
-
S. Sauge, L. Lydersen, A. Anisimov, J. Skaar, and V. Makarov. Controlling an actively-quenched single photon detector with bright light. Opt. Express, 2011, 19, 23590–23600. [CrossRef] [PubMed]
- V. Makarov. Controlling passively quenched single photon detectors by bright light. New J. Phys. 2009, 11, 065003. [CrossRef]
- L. Lydersen, N. Jain, C. Wittmann, Ø. Marøy,J. Skaar,C. Marquardt, V. Makarov, and G. Leuchs. Superlinear threshold detectors in quantum cryptography. Phys. Rev. A 2011, 84, 032320. [CrossRef]
- L. Lydersen, C. Wiechers, C. Wittmann, D. Elser, J. Skaar, and V. Makarov. Thermal blinding of gated detectors in quantum cryptography. Opt. Express 2010, 18, 27938–27954. [CrossRef] [PubMed]
- L. Lydersen, J. Skaar, and V. Makarov. Tailored bright illumination attack on distributed-phase-reference protocols. J. Mod. Opt. 2011, 58, 680–685. [CrossRef]
- C. Wiechers, L. Lydersen, C. Wittmann, D. Elser, J. Skaar, C. Marquardt, V. Makarov, and G. Leuchs. After-gate attack on a quantum cryptosystem. New Journal of Physics 2011, 13, 013043. [CrossRef]
- Z. L. Yuan, J. F. Dynes and A. J. Shields. Avoiding the blinding attack in QKD. Nature Photonics 2010, 4, 800–801. [Google Scholar] [CrossRef]
- T. Honjo, M. Fujiwara, K. Shimizu, K. Tamaki, S. Miki, T. Yamashita, H. Terai, Z. Wang, and M. Sasaki. Countermeasure against tailored bright illumination attack for DPS-QKD. Opt. Express 2013, 21, 2667–2673. [Google Scholar] [CrossRef] [PubMed]
- Si, H. , Liu, H., and Ma, H. (2018). "Optical Fiber Communication Network Eavesdropping and Defensive Measures" (2018) 2nd International Forum on Management, Education and Information Technology Application (IFMEITA 2017). [CrossRef]
- Wang, J. , Wang, H., Qin, X. et al. The countermeasures against the blinding attack in quantum key distribution. Eur. Phys. J. D 2016, 70, 5. [Google Scholar] [CrossRef]
- Acheva, P. , Zaitsev, K., Zavodilenko, V. et al. Automated verification of countermeasure against detector-control attack in quantum key distribution. EPJ Quantum Technol. 2023, 10, 22. [Google Scholar] [CrossRef]
- C. H. Bennett and G. Brassard. Quantum public key distribution system. in Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, Bangalore, India, 1984 (IEEE, New York, 1984), pp. 175–179; IBM Tech. Discl. Bull. 1985, 28, 3153–3163. [Google Scholar] [CrossRef]
- C. H. Bennett, F. Bessette, G. Brassard, L. Salvail, J. Smolin. Experimental quantum cryptography. J. Cryptol. 1992, 5, 3–28. [Google Scholar] [CrossRef]
- T. Jennewein, U. Achleitner, G. Weihs, H. Weinfurter, A. Zeilinger. A Fast and Compact Quantum Random Number Generator. Rev. Sci. Instrum. 2000, 71, 1675–1680. [Google Scholar] [CrossRef]
- A. Stefanov, N. Gisin, O. Guinnard, L. Guinnard, H. Zbinden. Optical quantum random number generator. J. Mod. Opt. 2000, 47, 595–598. [Google Scholar] [CrossRef]
- M. Stipčević and B. Medved Rogina. Quantum random number generator based on photonic emission in semiconductors. Rev. Sci. Instrum. 2007, 78, 045104. [Google Scholar] [CrossRef]
- M. A. Wayne, E. R. Jeffrey, G. M. Akselrod and P. G. Kwiat. Photon arrival time quantum random number generation. J. Mod. Opt. 2009, 56, 516–522. [Google Scholar] [CrossRef]
- M. Wahl, M. Leifgen, M. Berlin, T. Roehlicke, H.J. Rahn, O. Benson. An ultrafast quantum random number generator with provably bounded output bias based on photon arrival time measurements. Appl. Phys. Lett. 2011, 98, 171105. [Google Scholar] [CrossRef]
- P. Keshavarzian et al.. A 3.3-Gb/s SPAD-Based Quantum Random Number Generator. IEEE Journal of Solid-State Circuits 2023, 5, 1–16. [CrossRef]
- Kerckhoffs A. La cryptographie militaire. J sci militaires IX url: http://www.petitcolas.net/fabien/kerckhoffs/. 1883, 5–38, 161–191.
- P.W. Shor, J. Preskill. Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett, 2000, 85, 441–444. [CrossRef] [PubMed]
- Luigi Savastano, Guido Maier, Achille Pattavina, and Mario Martinelli. Physical-Parameter Design in 2-D MEMS Optical Switches," J. Lightwave Technol. 2005, 23, 3147–3155. [Google Scholar] [CrossRef]
- Zhenggang Lian, Peter Horak, Xian Feng, Limin Xiao, Ken Frampton, Nicholas White, John A. Tucknott, Harvey Rutt, David N. Payne, Will Stewart, and Wei H. Loh. Nanomechanical optical fiber. Opt. Express 2012, 20, 29386–29394. [Google Scholar] [CrossRef] [PubMed]
- N. Lütkenhaus. Estimates for practical quantum cryptography. Phys. Rev. A 1999, 59, 3301. [Google Scholar] [CrossRef]
- Hong, C. K. , Ou, Z. Y., and Mandel, L.. Measurement of subpicosecond time intervals between two photons by interference. Phys. Rev. Lett. 1987, 59, 2044–2046. [Google Scholar] [CrossRef] [PubMed]
- LaPierre, R. (2022). Coherent State on a Beam Splitter. In: Getting Started in Quantum Optics. Undergraduate Texts in Physics. Springer, Cham. [CrossRef]
- N. Alsmeyer, G. N. Alsmeyer, G. (2011) "Chebyshev’s Inequality". In: Lovric, M. (eds) International Encyclopedia of Statistical Science. Springer, Berlin, Heidelberg. [CrossRef]
- Knoernschild, C. , Kim, C., Liu, B., Lu, F. P., & Kim, J. MEMS-based optical beam steering system for quantum information processing in two-dimensional atomic systems. Optics Letters 2008, 33, 273. [Google Scholar] [CrossRef]
- Yang, J. , Li, X., Yang, J., Liu, J., & Su, X. Polarization-independent bidirectional 4×4 optical switch in free space. Optics & Laser Technology 2010, 42, 927–933. [Google Scholar] [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).