Submitted:
12 July 2023
Posted:
13 July 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Methodology
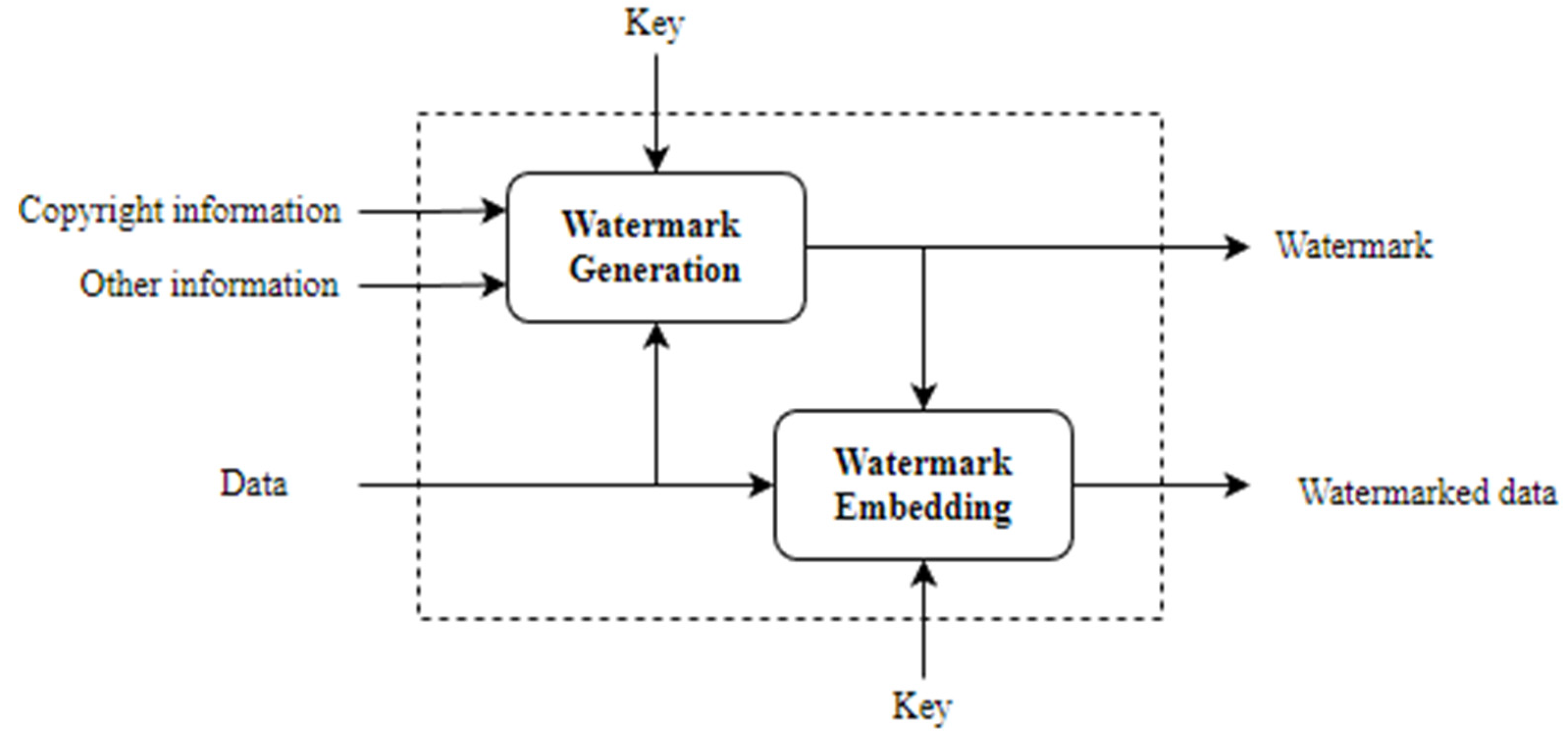
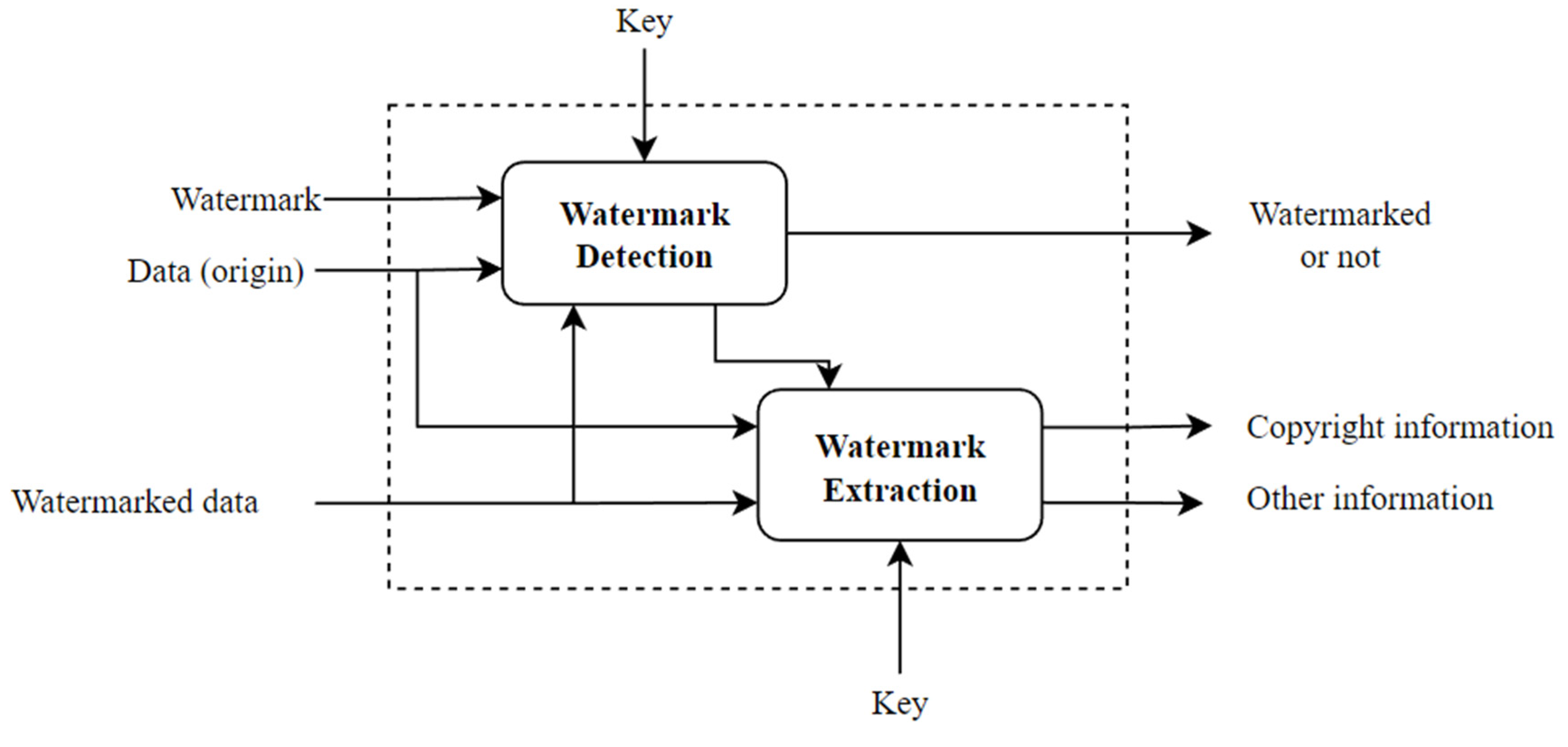
2.1. Watermarking Process for Copyright Protection
2.2. Analysis of Watermarking Techniques
2.2.1. Spatial Domain-Based Techniques
2.2.2. Frequency Domain-Based Techniques
2.2.3. Lossless Watermarking Techniques
2.2.4. Zero-Watermarking Technique
3. Integrated Watermarking Algorithm
3.1. Short, Pseudo-Random, and Meaningful Watermark Generation
3.2. Watermark Embedded in the Vertices
3.2.1. Watermark Embedding
3.2.2. Watermark Detection
3.3. Zero-Watermark Based on Statistical Properties
3.3.1. Zero-Watermark Embedding
3.3.2. Zero-Watermark Extraction
3.4. Integrate Watermarking Algorithm to Protect Copyright
3.4.1. Watermark Embedding Steps
3.4.2. Steps to Extract Watermark to Prove Copyright.
4. Experiments
4.1. Generate Pseudo-Random Meaningful Watermark
4.2. Embedding and Detecting Watermark
4.2.1. Experiment with a Polygon Vector Geographic Data
4.2.2. Experiment with Polyline Vector Geographic Data
4.2.3. Experiment with Point Vector Geographic Data
4.3. Embedding and Detecting Zero-Watermark
5. Conclusions
Acknowledgments
References
- Wang, X.; Yan, H.; Zhang, L.; Zhang, X.; Li, P. An encryption algorithm for vector maps based on the Gaussian random and Haar transform. Journal of Spatial Science 2021, 1–16. [Google Scholar] [CrossRef]
- Mondal, B. Cryptographic image scrambling techniques. In Cryptographic and Information Security (pp. 37–65). CRC Press (2018).
- Wang, Y.; Yang, C.; Ren, N.; Zhu, C.; Rui, T.; Wang, D. An adaptive watermark detection algorithm for vector geographic data. KSII Transactions on Internet and Information Systems (TIIS) 2020, 14, 323–343. [Google Scholar] [CrossRef]
- Yan, H.; Zhang, L.; Yang, W. A normalization-based watermarking scheme for 2D vector map data. Earth Science Informatics 2017, 10, 471–481. [Google Scholar] [CrossRef]
- Wang, C.; Peng, Z.; Peng, Y.; Yu, L. Watermarking 2D vector maps on spatial topology domain. In 2009 International Conference on Multimedia Information Networking and Security (Vol. 2, pp. 71–74). IEEE (2009).
- Wang, Y.; Yang, C.; Zhu, C.; Ding, K. An efficient robust multiple watermarking algorithm for vector geographic data. Information 2018, 9, 296. [Google Scholar] [CrossRef]
- Voigt, M.; Busch, C. Feature-based watermarking of 2D vector data. In Security and Watermarking of Multimedia Contents V; SPIE, 2003; Volume 5020, pp. 359–366.
- Ren, N.; Wang, Q. S.; Zhu, C. Q. Selective authentication algorithm based on semi-fragile watermarking for vector geographical data. In 2014 22nd International Conference on Geoinformatics (pp. 1–6). IEEE (2014). [CrossRef]
- Wang, C.; Peng Z., Peng; Y., Yu; L., Wang, J.; Zhao, Q. Watermarking geographical data on spatial topological relations. Multimedia Tools and Applications 2012, 57, 67–89. [CrossRef]
- Zope-Chaudhari, S.; Venkatachalam, P.; Buddhiraju, K. M. Copyright protection of vector data using vector watermark. In 2017 IEEE International Geoscience and Remote Sensing Symposium (IGARSS) (pp. 6110–6113). IEEE (2017).
- Wang, X.; Huang, D. J.; Zhang, Z. Y. A DCT-based blind watermarking algorithm for vector digital maps. In Advanced Materials Research (Vol. 179, pp. 1053–1058). Trans Tech Publications Ltd. (2011). [CrossRef]
- Liang, B.; Rong, J.; Wang, C. A vector maps watermarking algorithm based on dct domain. ISPRS Congr 2010, 38, 3. [Google Scholar]
- Hou, X.; Min, L.; Yang, H. A reversible watermarking scheme for vector maps based on multilevel histogram modification. Symmetry 2018, 10, 397. [Google Scholar] [CrossRef]
- Cao, L.; Men, C.; Ji, R. High-capacity reversible watermarking scheme of 2D-vector data. Signal, Image and Video Processing 2015, 9, 1387–1394. [Google Scholar] [CrossRef]
- Lin, Z. X.; Peng, F.; Long, M. A low-distortion reversible watermarking for 2D engineering graphics based on region nesting. IEEE Transactions on Information Forensics and Security 2018, 13, 2372–2382. [Google Scholar] [CrossRef]
- Qiu, Y. , Duan, H., Sun, J., & Gu, H. (2019). Rich-information reversible watermarking scheme of vector maps. Multimedia Tools and Applications 2019, 78, 24955–24977. [Google Scholar] [CrossRef]
- Qiu, Y.; Gu, H.; Sun, J. High-payload reversible watermarking scheme of vector maps. Multimedia Tools and Applications 2018, 77, 6385–6403. [Google Scholar] [CrossRef]
- Peng, F.; Yan, Z. J.; Long, M. A reversible watermarking for 2D vector map based on triple differences expansion and reversible contrast mapping. In International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage (pp. 147–158). Springer, Cham (2017). [CrossRef]
- Ren, N.; Zhou, Q.; Zhu, C.; Zhu, A. X.; Chen, W. A Lossless Watermarking Algorithm Based on Line Pairs for Vector Data. Ieee Access 2020, 8, 156727–156739. [Google Scholar] [CrossRef]
- Zhou, Q.; Ren, N.; Zhu, C.; Tong, D. Storage feature-based watermarking algorithm with coordinate values preservation for vector line data. KSII Transactions on Internet and Information Systems (TIIS) 2018, 12, 3475–3496. [Google Scholar] [CrossRef]
- Li, A. B.; Zhu, A. X. Copyright authentication of digital vector maps based on spatial autocorrelation indices. Earth Science Informatics 2019, 12, 629–639. [Google Scholar] [CrossRef]
- Rani, A.; Bhullar, A. K.; Dangwal, D.; Kumar, S. A zero-watermarking scheme using discrete wavelet transform. Procedia Computer Science 2015, 70, 603–609. [Google Scholar] [CrossRef]
- Liu, Y.; Yang, F.; Gao, K.; Dong, W.; Song, J. A zero-watermarking scheme with embedding timestamp in vector maps for Big Data computing. Cluster Computing 2017, 20, 3667–3675. [Google Scholar] [CrossRef]
- Peng, Y. , & Yue, M. (2015). A zero-watermarking scheme for vector map based on feature vertex distance ratio. Journal of Electrical and Computer Engineering 2015, 2015, 35. [Google Scholar] [CrossRef]
- Xun, W. A. N. G.; Huang, D.; Zhang, Z. A robust zero-watermarking algorithm for vector digital maps based on statistical characteristics. Softw. Appl. Econ. Anal. Bus. Manag 2012, 7, 2349. [Google Scholar] [CrossRef]
- Zhou, Q.; Zhu, C.; Ren, N.; Chen, W.; Gong, W. Zero Watermarking Algorithm for Vector Geographic Data Based on the Number of Neighboring Features. Symmetry 2021, 13, 208. [Google Scholar] [CrossRef]
- Moulin, P.; Koetter, R. Data-hiding codes. Proceedings of the IEEE 2005, 93, 2083–2126. [Google Scholar] [CrossRef]


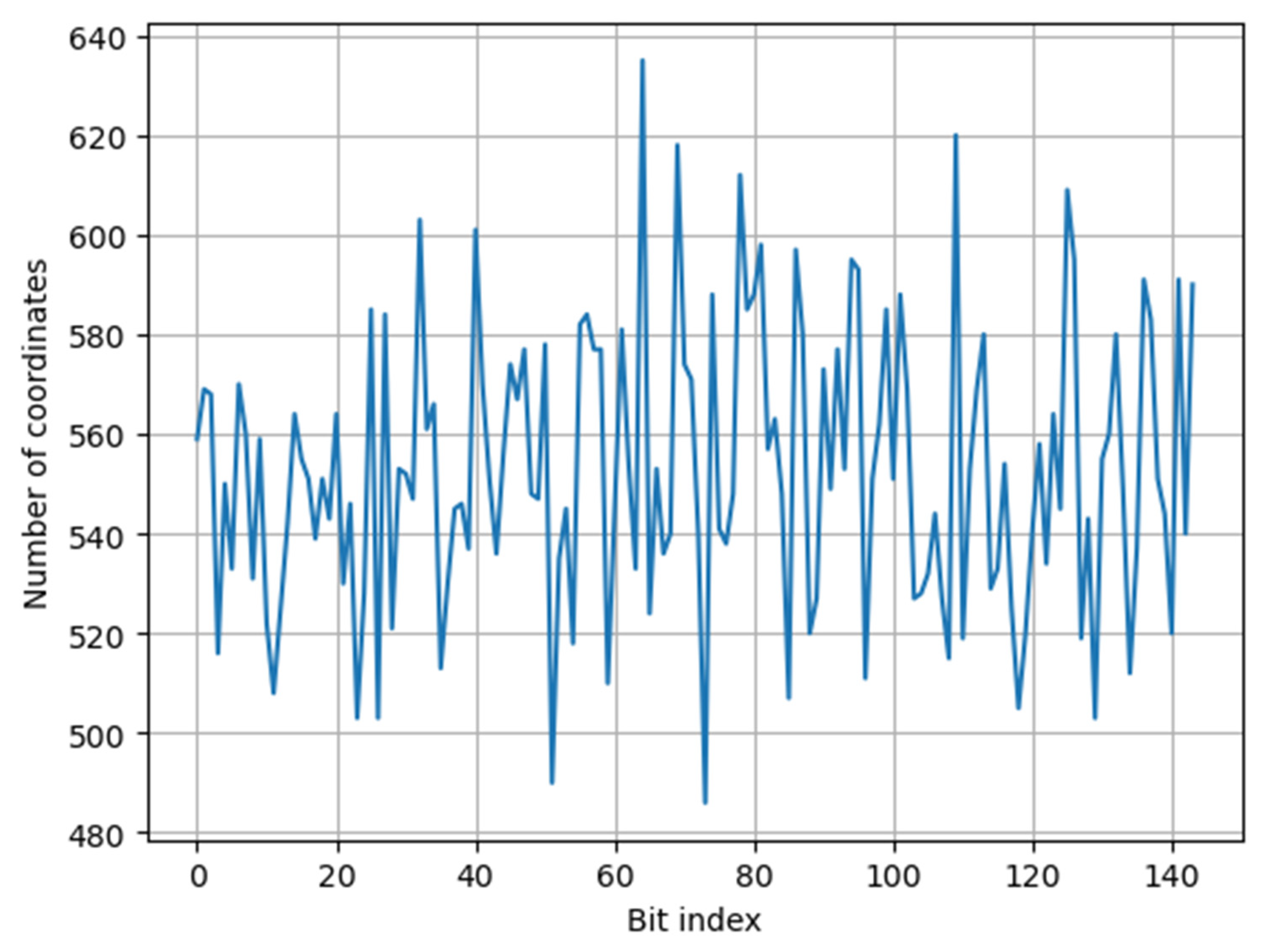
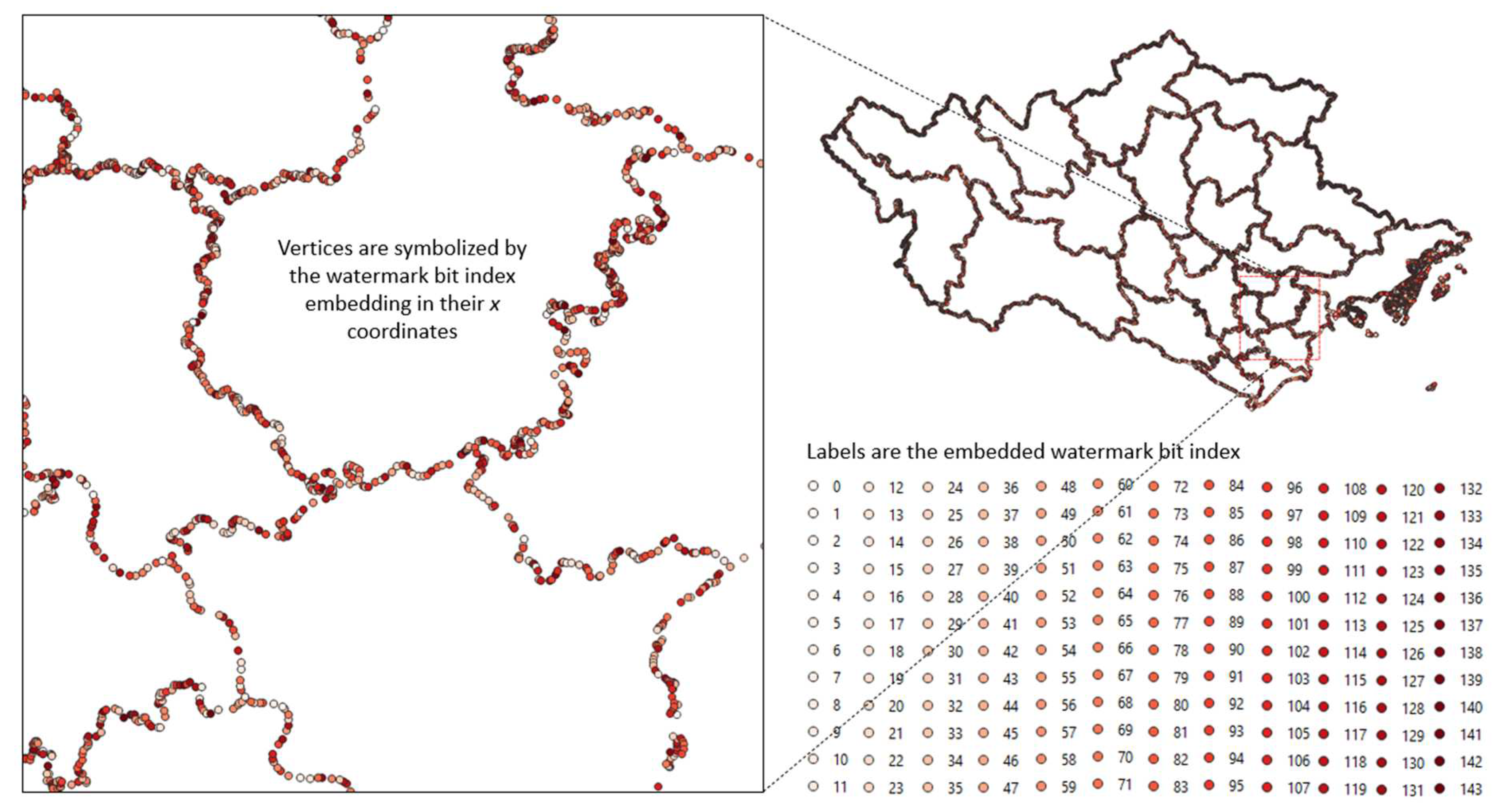
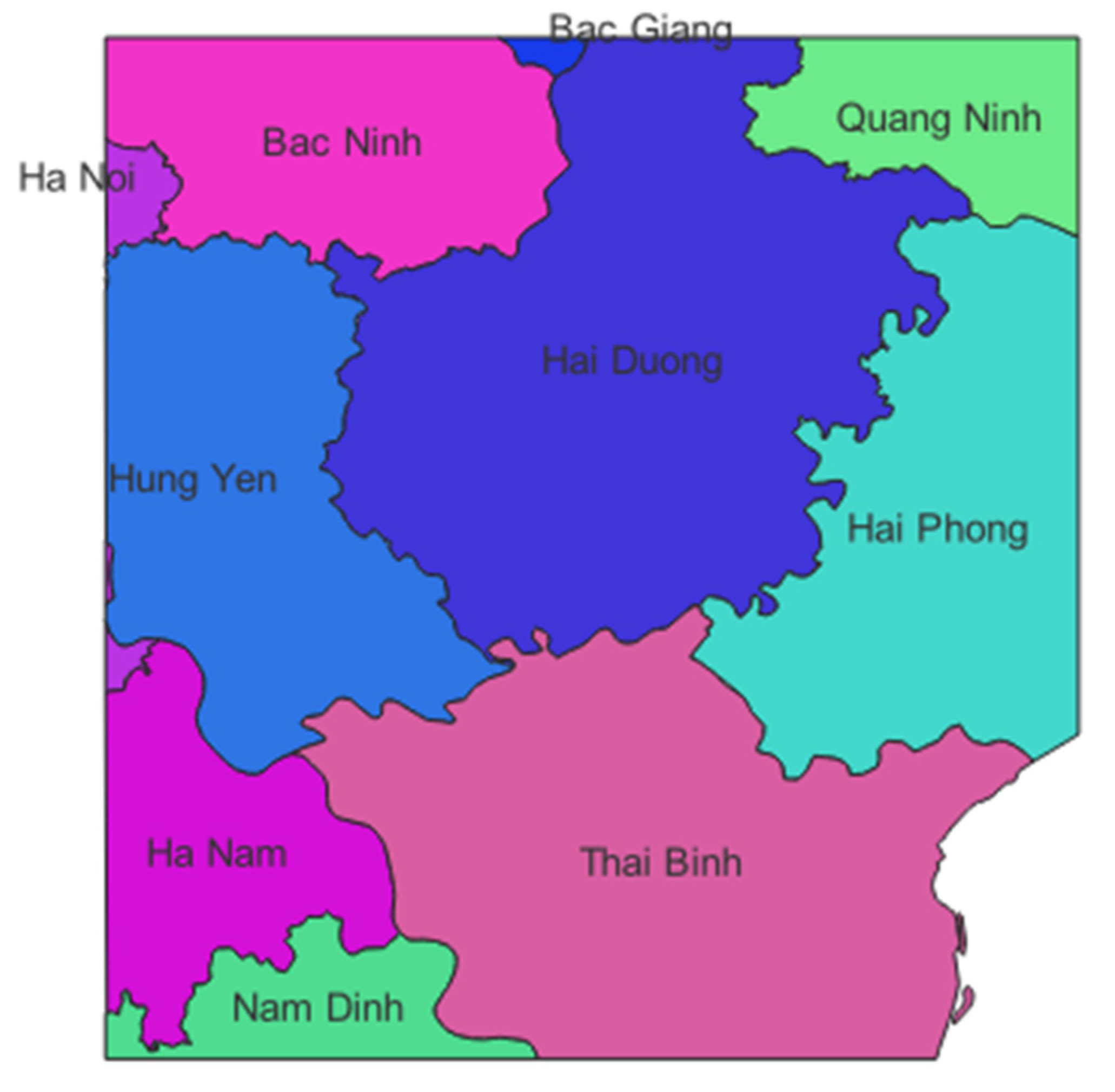
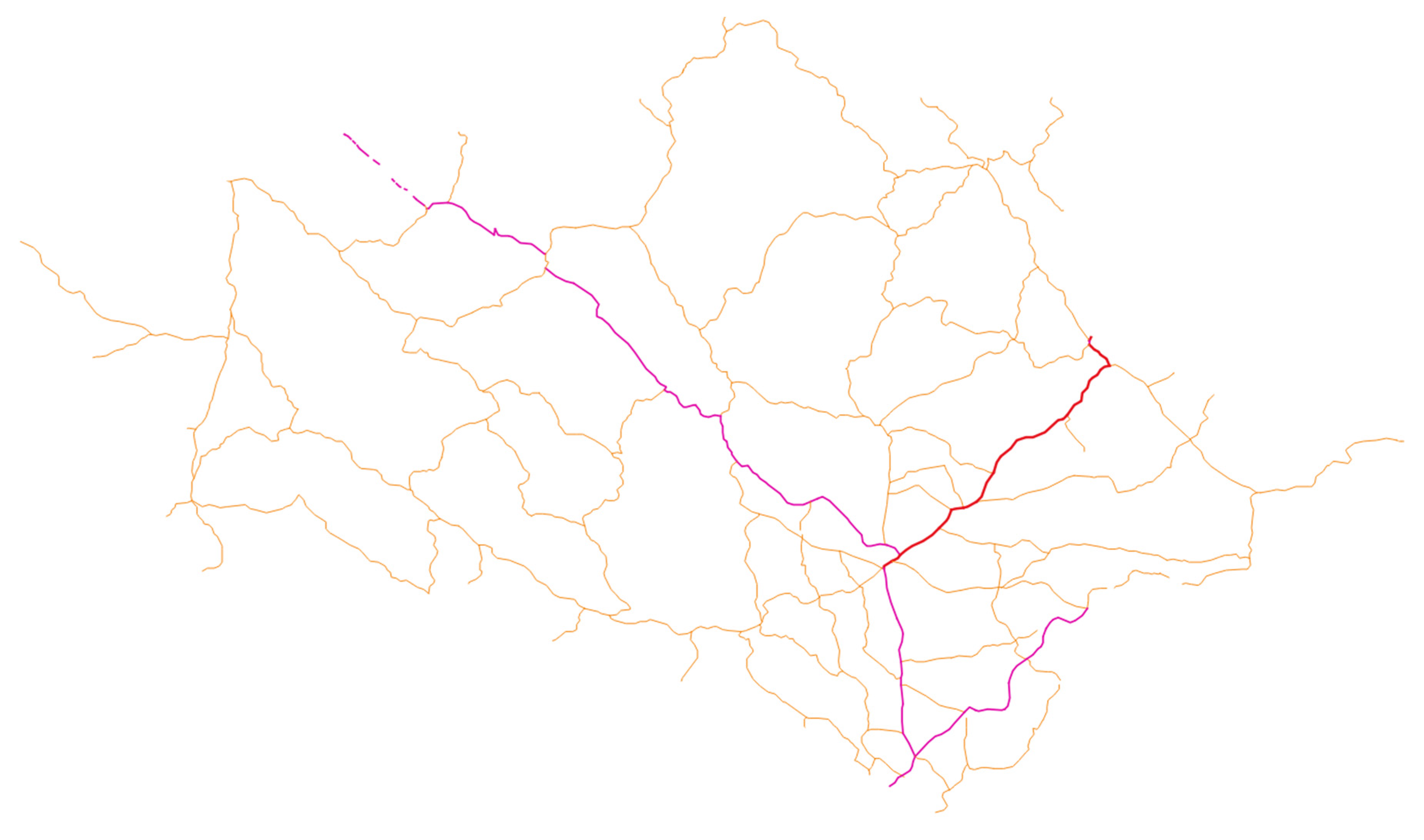
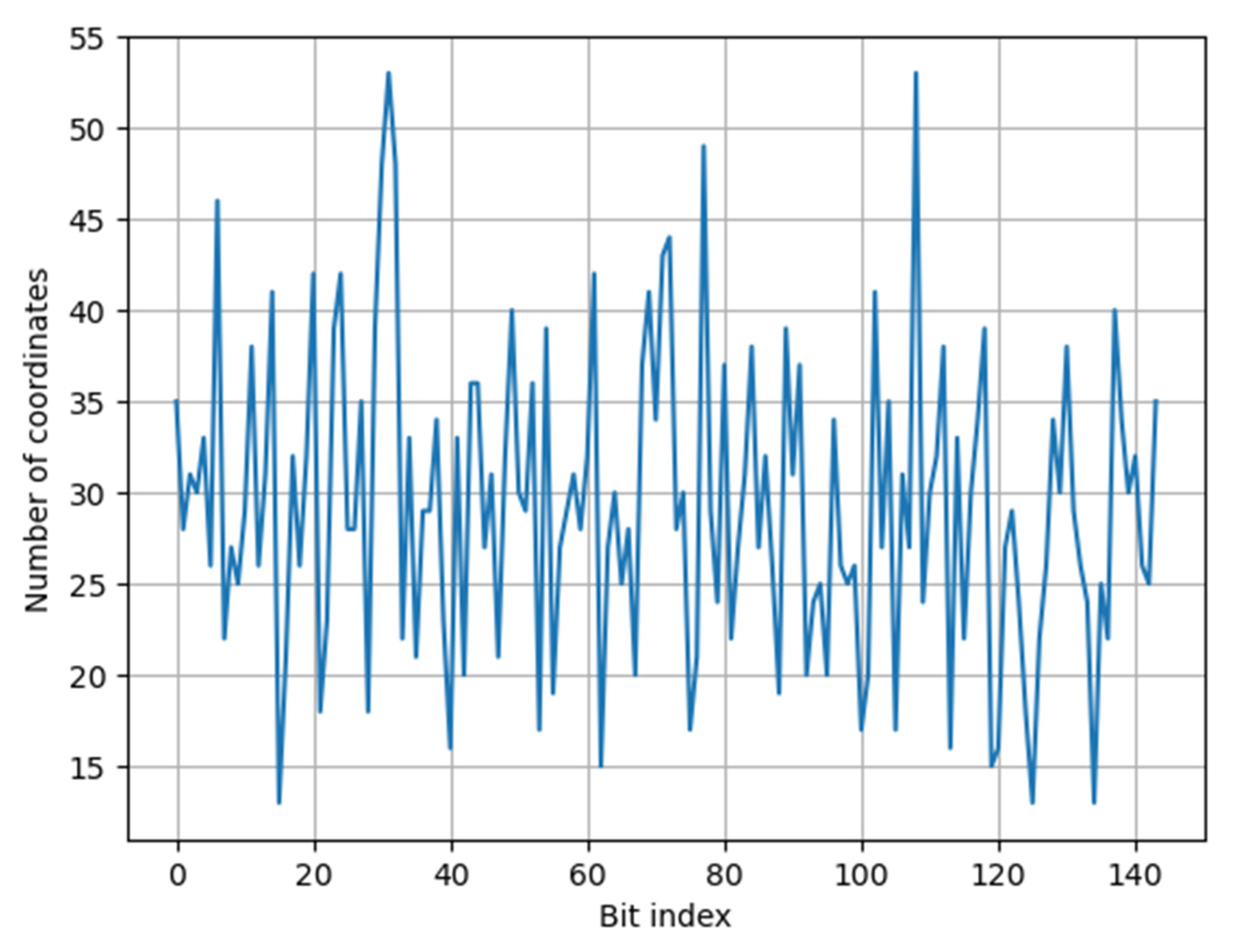
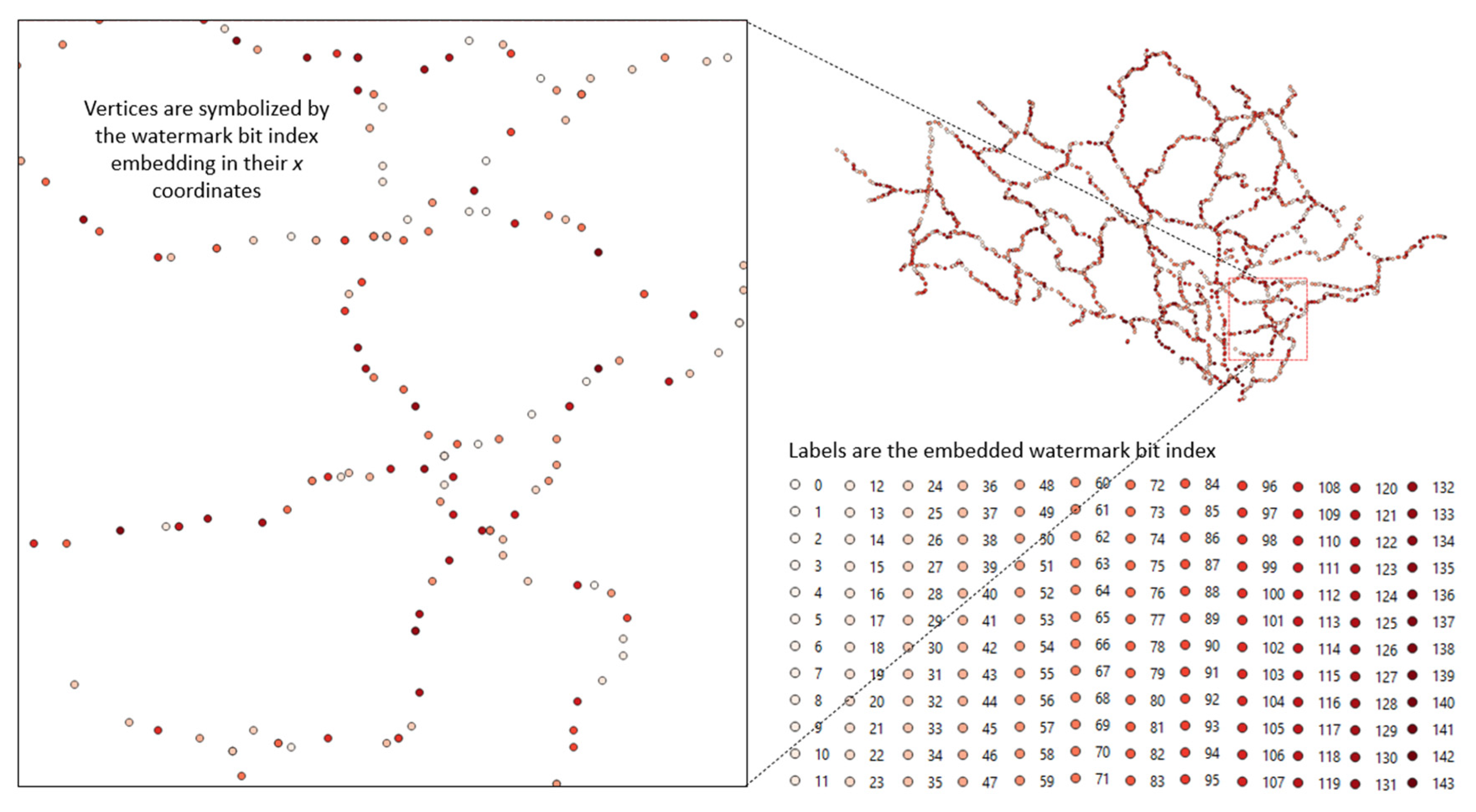
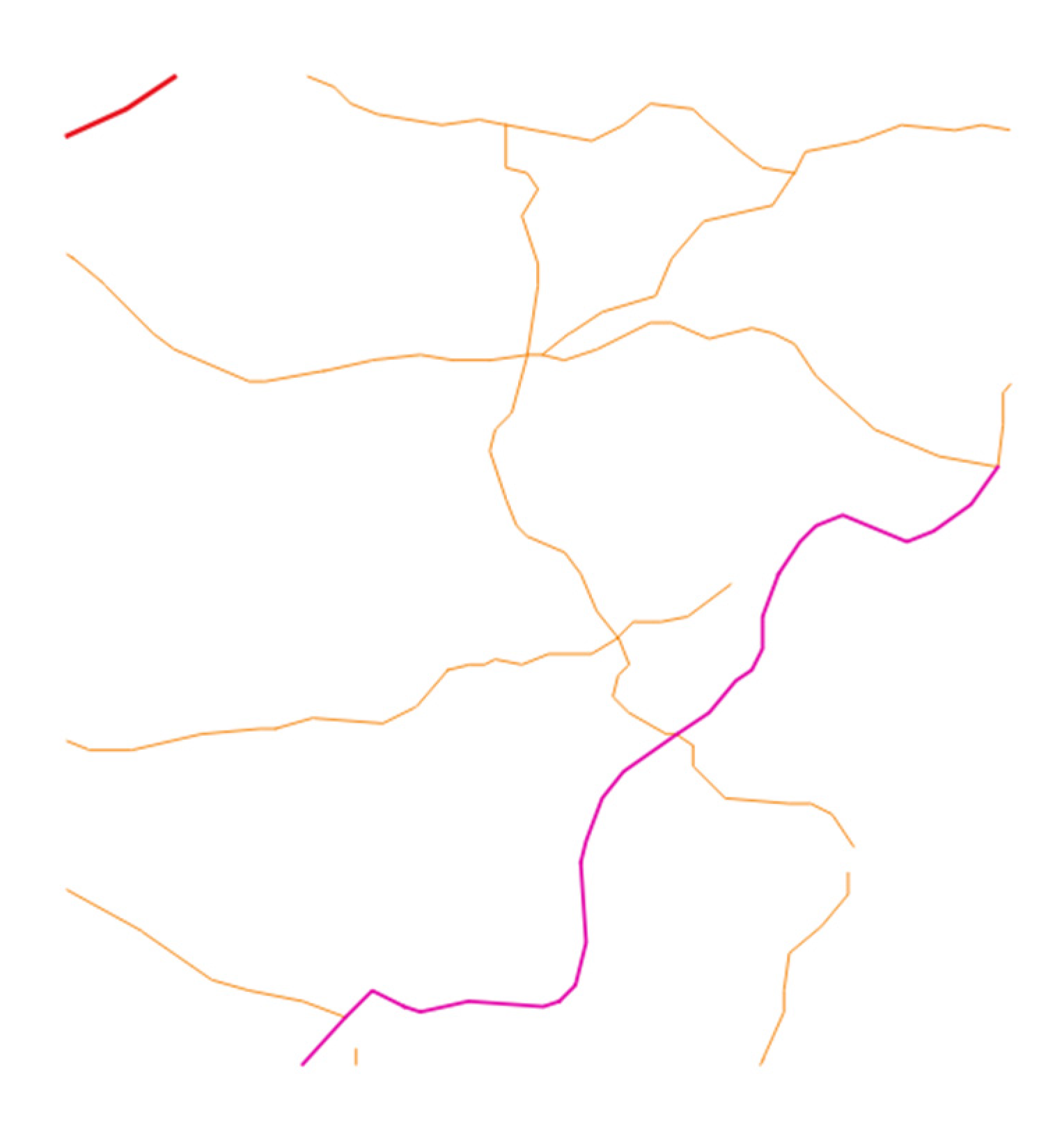

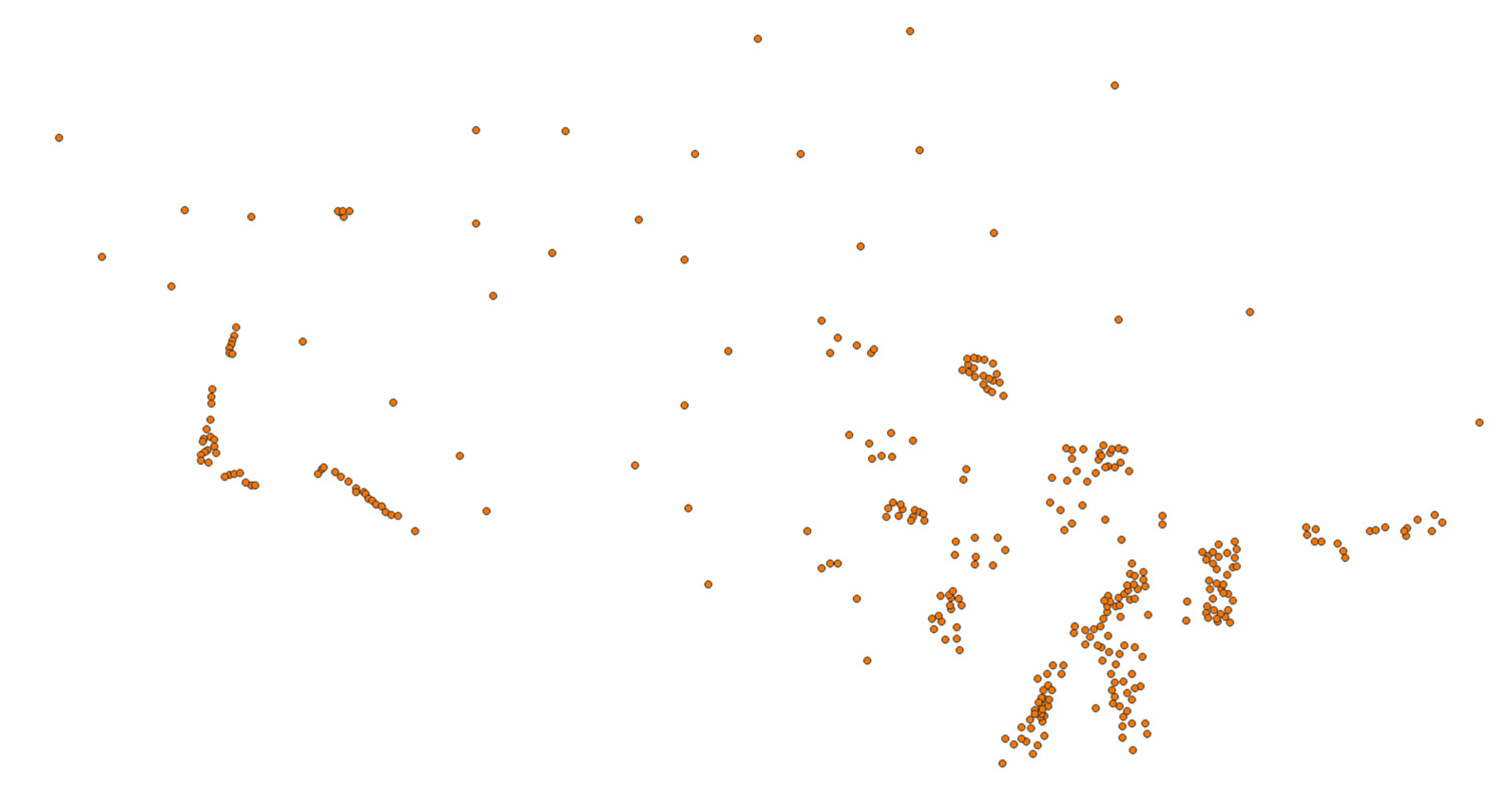
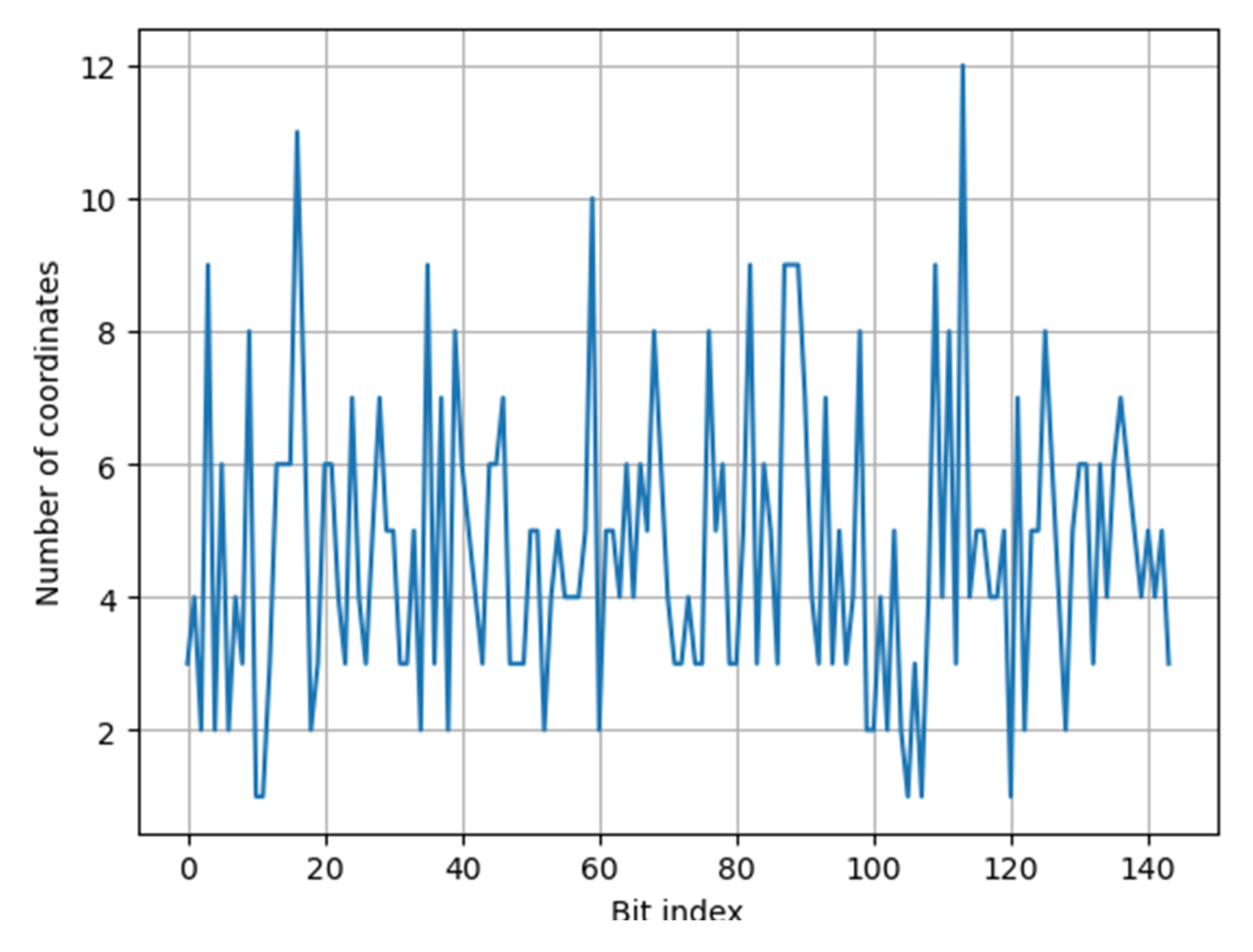
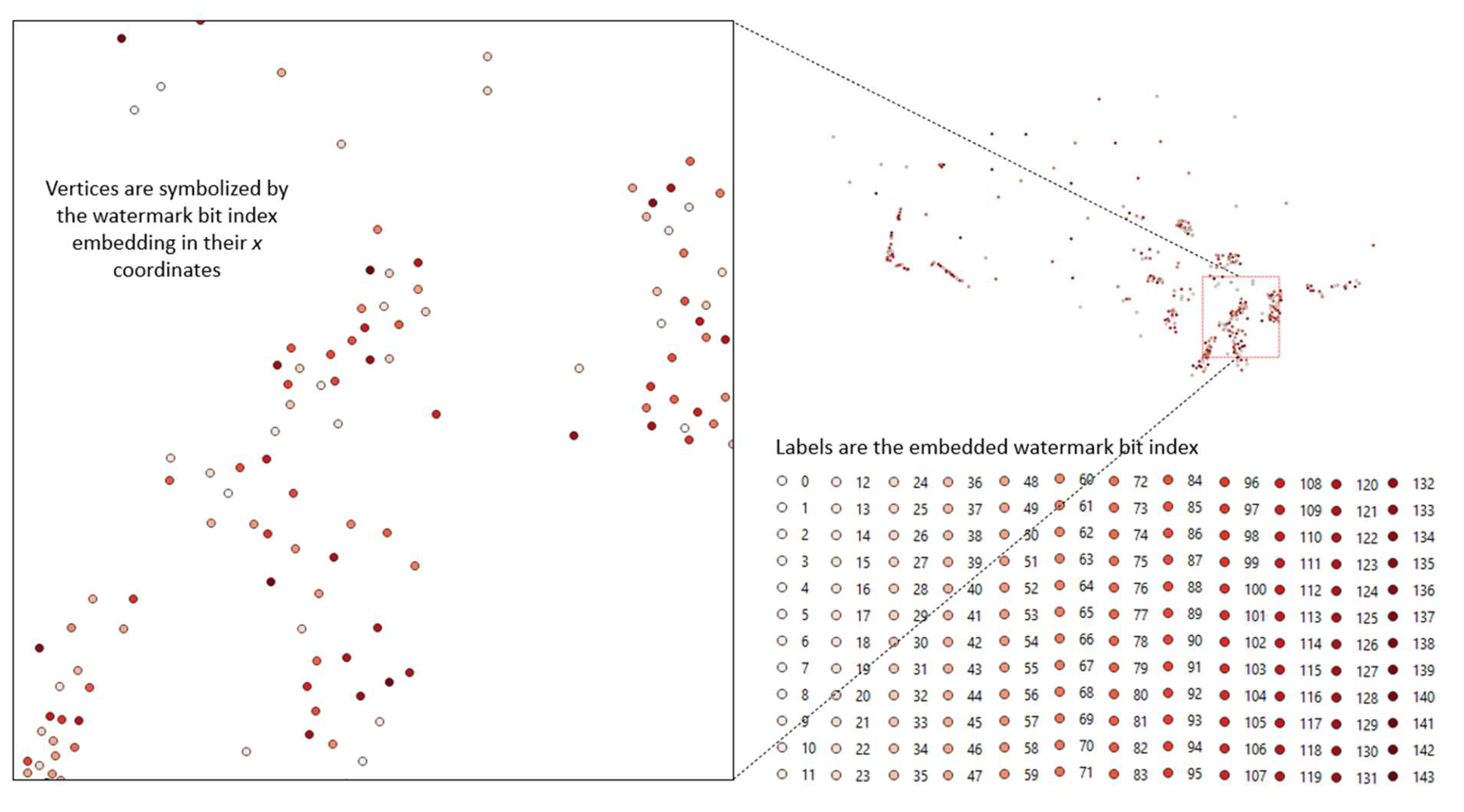


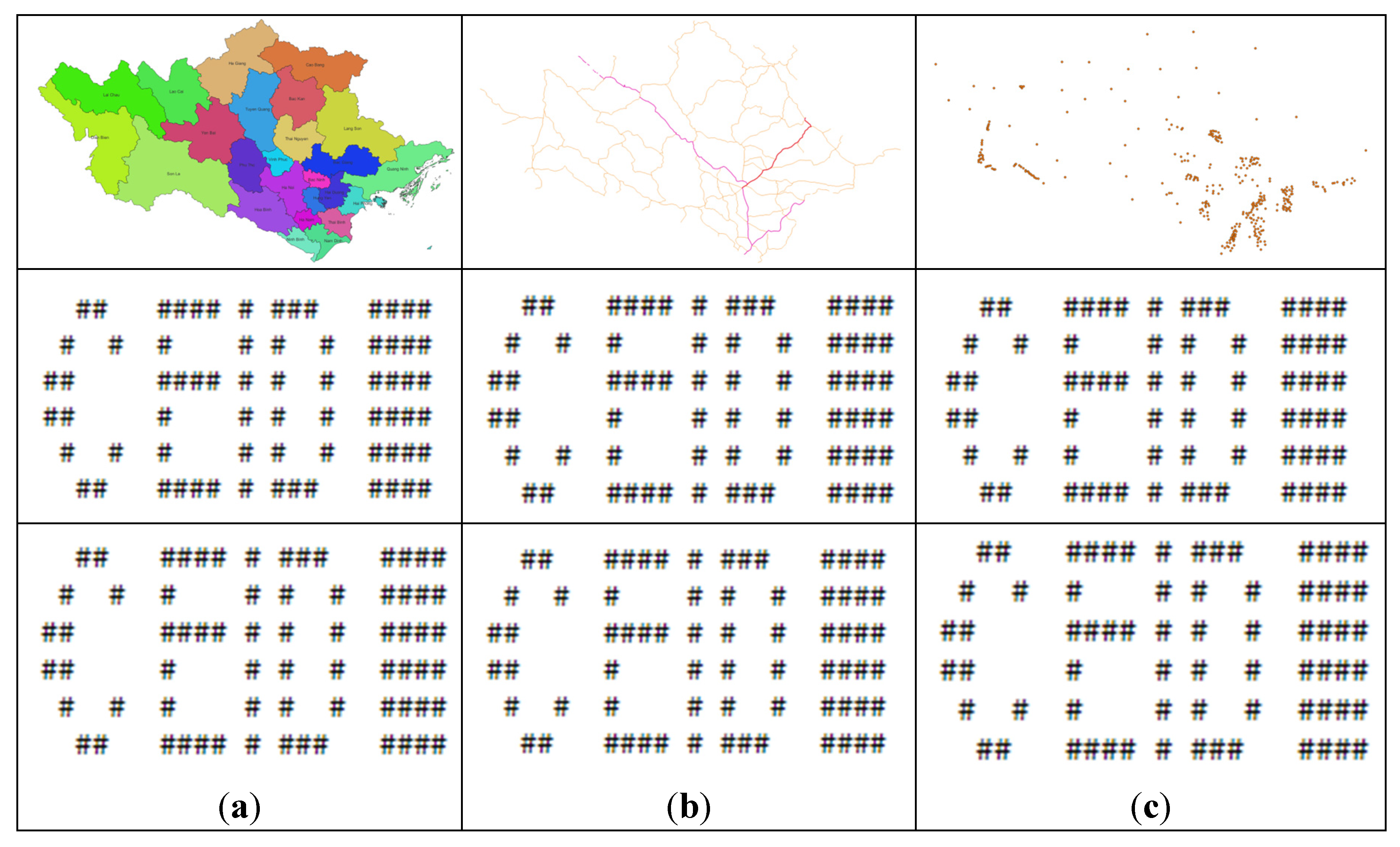
| Bit index | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 |
| No | 559 | 569 | 568 | 516 | 550 | 533 | 570 | 560 | 531 | 559 | 522 | 508 |
| Bit index | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 | 20 | 21 | 22 | 23 |
| No | 525 | 542 | 564 | 555 | 551 | 539 | 551 | 543 | 564 | 530 | 546 | 503 |
| Bit index | 24 | 25 | 26 | 27 | 28 | 29 | 30 | 31 | 32 | 33 | 34 | 35 |
| No | 528 | 585 | 503 | 584 | 521 | 553 | 552 | 547 | 603 | 561 | 566 | 513 |
| Bit index | 36 | 37 | 38 | 39 | 40 | 41 | 42 | 43 | 44 | 45 | 46 | 47 |
| No | 530 | 545 | 546 | 537 | 601 | 570 | 551 | 536 | 556 | 574 | 567 | 577 |
| Bit index | 48 | 49 | 50 | 51 | 52 | 53 | 54 | 55 | 56 | 57 | 58 | 59 |
| No | 548 | 547 | 578 | 490 | 535 | 545 | 518 | 582 | 584 | 577 | 577 | 510 |
| Bit index | 60 | 61 | 62 | 63 | 64 | 65 | 66 | 67 | 68 | 69 | 70 | 71 |
| No | 546 | 581 | 554 | 533 | 635 | 524 | 553 | 536 | 540 | 618 | 574 | 571 |
| Bit index | 72 | 73 | 74 | 75 | 76 | 77 | 78 | 79 | 80 | 81 | 82 | 83 |
| No | 540 | 486 | 588 | 541 | 538 | 548 | 612 | 585 | 588 | 598 | 557 | 563 |
| Bit index | 84 | 85 | 86 | 87 | 88 | 89 | 90 | 91 | 92 | 93 | 94 | 95 |
| No | 548 | 507 | 597 | 580 | 520 | 527 | 573 | 549 | 577 | 553 | 595 | 593 |
| Bit index | 96 | 97 | 98 | 99 | 100 | 101 | 102 | 103 | 104 | 105 | 106 | 107 |
| No | 511 | 551 | 562 | 585 | 551 | 588 | 569 | 527 | 528 | 532 | 544 | 527 |
| Bit index | 108 | 109 | 110 | 111 | 112 | 113 | 114 | 115 | 116 | 117 | 118 | 119 |
| No | 515 | 620 | 519 | 553 | 569 | 580 | 529 | 533 | 554 | 525 | 505 | 520 |
| Bit index | 120 | 121 | 122 | 123 | 124 | 125 | 126 | 127 | 128 | 129 | 130 | 131 |
| No | 541 | 558 | 534 | 564 | 545 | 609 | 595 | 519 | 543 | 503 | 555 | 560 |
| Bit index | 132 | 133 | 134 | 135 | 136 | 137 | 138 | 139 | 140 | 141 | 142 | 143 |
| No | 580 | 549 | 512 | 537 | 591 | 583 | 551 | 544 | 520 | 591 | 540 | 590 |
| Bit index | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 |
| No | 35 | 28 | 31 | 30 | 33 | 26 | 46 | 22 | 27 | 25 | 29 | 38 |
| Bit index | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 | 20 | 21 | 22 | 23 |
| No | 26 | 31 | 41 | 13 | 21 | 32 | 26 | 32 | 42 | 18 | 23 | 39 |
| Bit index | 24 | 25 | 26 | 27 | 28 | 29 | 30 | 31 | 32 | 33 | 34 | 35 |
| No | 42 | 28 | 28 | 35 | 18 | 39 | 48 | 53 | 48 | 22 | 33 | 21 |
| Bit index | 36 | 37 | 38 | 39 | 40 | 41 | 42 | 43 | 44 | 45 | 46 | 47 |
| No | 29 | 29 | 34 | 23 | 16 | 33 | 20 | 36 | 36 | 27 | 31 | 21 |
| Bit index | 48 | 49 | 50 | 51 | 52 | 53 | 54 | 55 | 56 | 57 | 58 | 59 |
| No | 32 | 40 | 30 | 29 | 36 | 17 | 39 | 19 | 27 | 29 | 31 | 28 |
| Bit index | 60 | 61 | 62 | 63 | 64 | 65 | 66 | 67 | 68 | 69 | 70 | 71 |
| No | 32 | 42 | 15 | 27 | 30 | 25 | 28 | 20 | 37 | 41 | 34 | 43 |
| Bit index | 72 | 73 | 74 | 75 | 76 | 77 | 78 | 79 | 80 | 81 | 82 | 83 |
| No | 44 | 28 | 30 | 17 | 21 | 49 | 29 | 24 | 37 | 22 | 27 | 31 |
| Bit index | 84 | 85 | 86 | 87 | 88 | 89 | 90 | 91 | 92 | 93 | 94 | 95 |
| No | 38 | 27 | 32 | 26 | 19 | 39 | 31 | 37 | 20 | 24 | 25 | 20 |
| Bit index | 96 | 97 | 98 | 99 | 100 | 101 | 102 | 103 | 104 | 105 | 106 | 107 |
| No | 34 | 26 | 25 | 26 | 17 | 20 | 41 | 27 | 35 | 17 | 31 | 27 |
| Bit index | 108 | 109 | 110 | 111 | 112 | 113 | 114 | 115 | 116 | 117 | 118 | 119 |
| No | 53 | 24 | 30 | 32 | 38 | 16 | 33 | 22 | 30 | 34 | 39 | 15 |
| Bit index | 120 | 121 | 122 | 123 | 124 | 125 | 126 | 127 | 128 | 129 | 130 | 131 |
| No | 16 | 27 | 29 | 24 | 18 | 13 | 22 | 26 | 34 | 30 | 38 | 29 |
| Bit index | 132 | 133 | 134 | 135 | 136 | 137 | 138 | 139 | 140 | 141 | 142 | 143 |
| No | 26 | 24 | 13 | 25 | 22 | 40 | 34 | 30 | 32 | 26 | 25 | 35 |
| Bit index | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 |
| No | 3 | 4 | 2 | 9 | 2 | 6 | 2 | 4 | 3 | 8 | 1 | 1 |
| Bit index | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 | 20 | 21 | 22 | 23 |
| No | 3 | 6 | 6 | 6 | 11 | 7 | 2 | 3 | 6 | 6 | 4 | 3 |
| Bit index | 24 | 25 | 26 | 27 | 28 | 29 | 30 | 31 | 32 | 33 | 34 | 35 |
| No | 7 | 4 | 3 | 5 | 7 | 5 | 5 | 3 | 3 | 5 | 2 | 9 |
| Bit index | 36 | 37 | 38 | 39 | 40 | 41 | 42 | 43 | 44 | 45 | 46 | 47 |
| No | 3 | 7 | 2 | 8 | 6 | 5 | 4 | 3 | 6 | 6 | 7 | 3 |
| Bit index | 48 | 49 | 50 | 51 | 52 | 53 | 54 | 55 | 56 | 57 | 58 | 59 |
| No | 3 | 3 | 5 | 5 | 2 | 4 | 5 | 4 | 4 | 4 | 5 | 10 |
| Bit index | 60 | 61 | 62 | 63 | 64 | 65 | 66 | 67 | 68 | 69 | 70 | 71 |
| No | 2 | 5 | 5 | 4 | 6 | 4 | 6 | 5 | 8 | 6 | 4 | 3 |
| Bit index | 72 | 73 | 74 | 75 | 76 | 77 | 78 | 79 | 80 | 81 | 82 | 83 |
| No | 3 | 4 | 3 | 3 | 8 | 5 | 6 | 3 | 3 | 5 | 9 | 3 |
| Bit index | 84 | 85 | 86 | 87 | 88 | 89 | 90 | 91 | 92 | 93 | 94 | 95 |
| No | 6 | 5 | 3 | 9 | 9 | 9 | 7 | 4 | 3 | 7 | 3 | 5 |
| Bit index | 96 | 97 | 98 | 99 | 100 | 101 | 102 | 103 | 104 | 105 | 106 | 107 |
| No | 3 | 4 | 8 | 2 | 2 | 4 | 2 | 5 | 2 | 1 | 3 | 1 |
| Bit index | 108 | 109 | 110 | 111 | 112 | 113 | 114 | 115 | 116 | 117 | 118 | 119 |
| No | 4 | 9 | 4 | 8 | 3 | 12 | 4 | 5 | 5 | 4 | 4 | 5 |
| Bit index | 120 | 121 | 122 | 123 | 124 | 125 | 126 | 127 | 128 | 129 | 130 | 131 |
| No | 1 | 7 | 2 | 5 | 5 | 8 | 6 | 4 | 2 | 5 | 6 | 6 |
| Bit index | 132 | 133 | 134 | 135 | 136 | 137 | 138 | 139 | 140 | 141 | 142 | 143 |
| No | 3 | 6 | 4 | 6 | 7 | 6 | 5 | 4 | 5 | 4 | 5 | 3 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




