Submitted:
05 May 2023
Posted:
06 May 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Information Privacy
1.2. Research Problem
1.3. Cloud computing in healthcare
2. Related Work
3. Proposed Architecture
- Just-enough information disclosure: Disclosing only the right information according to the context in which information is required.
- Accessible location of information: Storing patients’ information in once place for easy access whenever information is required.
- Unified platform: Accessing information through a unified platform is a key characteristic toward improving healthcare services.
- Adherence to the legal privacy-related frameworks: The architecture should adhere to privacy-related regulations and policies such as HIPPA and the information privacy act when using information.
- Patients control: Patients should have a means of control over who can access their information.
- Cloud provider blindness: The cloud provider should not be able to read or access patients’ information that is stored on the cloud.
3.1. Architecture fundamental aspects
3.1.1. Structuring Patients Information
3.1.2. Searchable Symmetric Encryption (SSE)
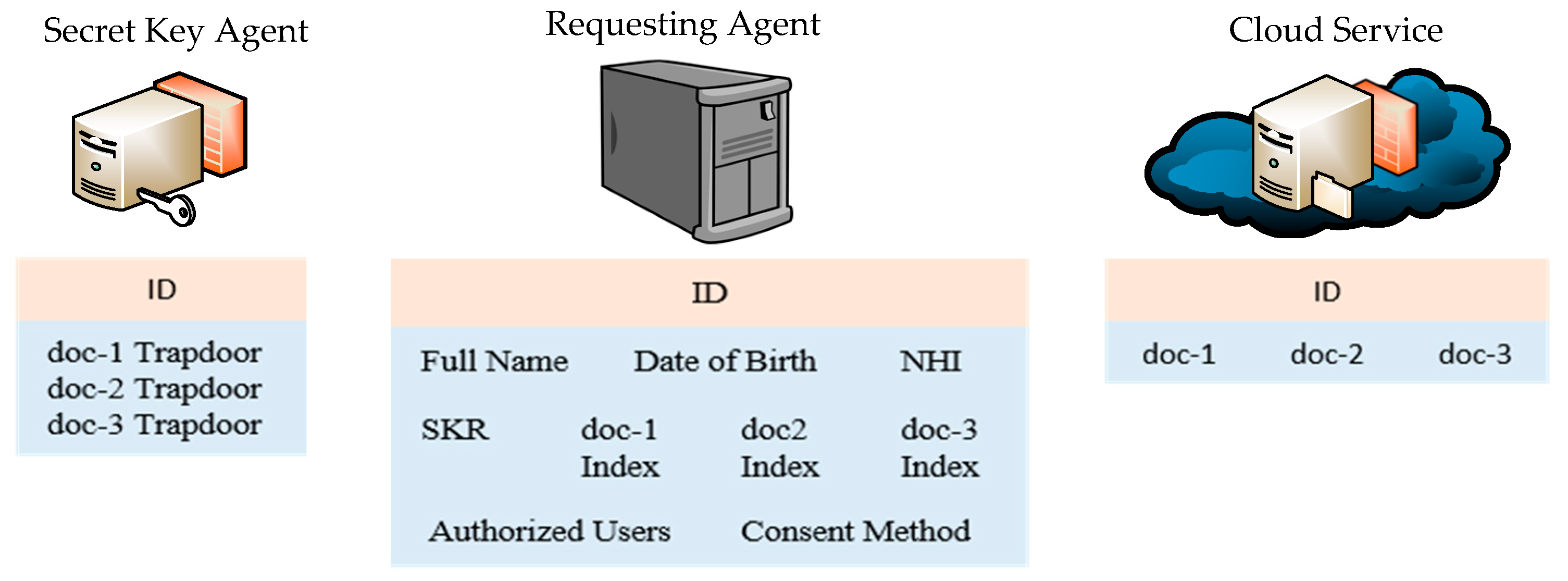
- Generating a secret root key (SKR) for the patient.
- Generating a secret key (SK) for every document of patient information and choosing a keyword of each document.
- Keywords are encrypted using their corresponding secret keys and the resulting ciphertexts are listed to form an encrypted index.
- Trapdoors are then created which involves combining the secret keys with the ciphertexts. Trapdoors will be used to identify and decrypt documents.
- Documents are encrypted using their corresponding secret keys.
3.2. Architectural Design and Components
- Standard presentation and categorization of information
- Information pre-processing, encrypting, and decrypting
- Characteristics related to accessing patients’ information for research purposes
3.3. System Instantiation
- A random secret root key (SkR) is generated for Bob’s information using KeyGen algorithm.
- A number of keywords from each document are selected, and a secret key (Sk) for encrypting them is generated using KeyDer algorithm.
- The IndexGen algorithm encrypts selected keywords for every document using their corresponding Sk. The goal in this step is to create an encrypted index for each document to identify it while encrypted.
- After encrypted indexes are generated for all documents, the ciphertexts of keywords with their corresponding Skfor each document is grouped to be the documents’ trapdoors.
- The last step in the information preparation process involves encrypting the patient’s documents and their corresponding trapdoors. Each document is encrypted using the Sk that is included in its corresponding trapdoor, and trapdoors are encrypted using the SkR which was generated in the first step.
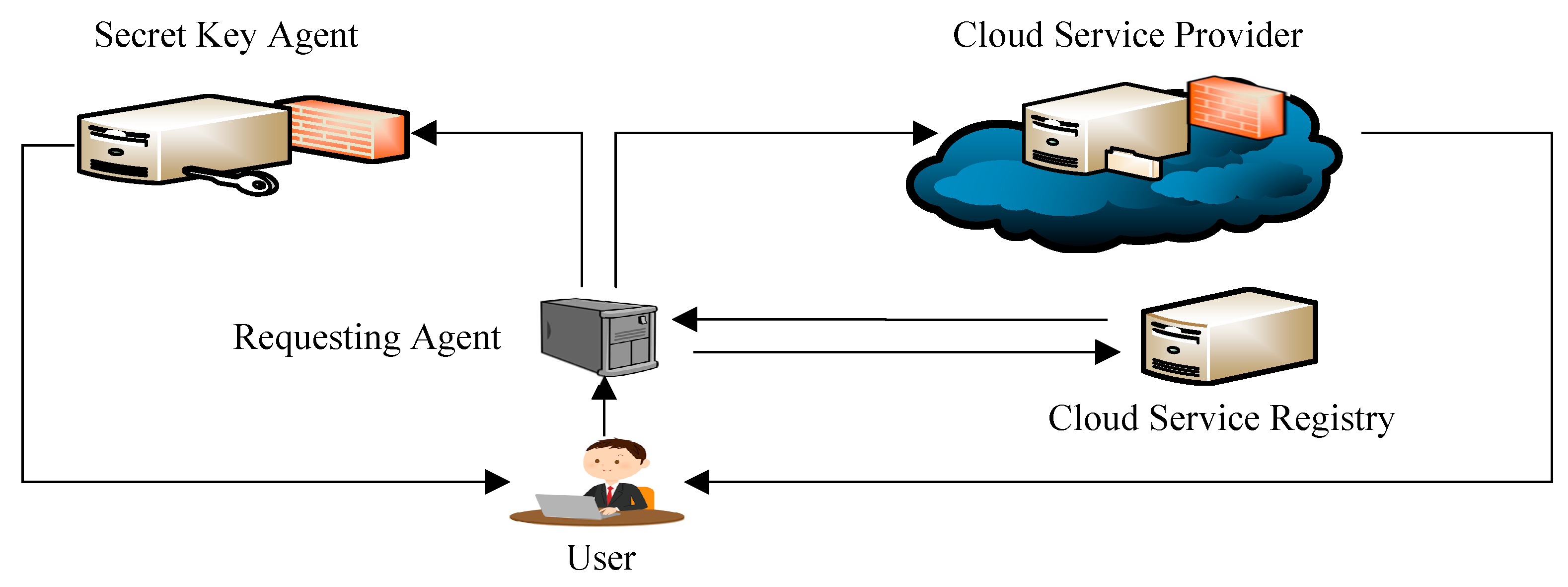
- 1.
- Generates a unique code for the patient referred to as (System ID).
- 2.
- Sends Bob’s encrypted information labelled by Bob’s system ID to the cloud service provider (CSP).
- 3.
- Sends the encrypted trapdoors to the secret key agent (SKA) for storage. Information sent to the SKA is also labelled by Bob’s system ID.
- 4.
- The information sent to both CSP and SKA is deleted from the RA.
- 5.
- The RA stores the following information:
- Bob’s identification information
- Bob’s system ID,
- Bob’s SkR,
- Document indexes
- Names of users who have permanent consent to access Bob’s information (if Bob has provided any)
- Information required for obtaining Bob’s temporary consent
- Bob’s information is stored in encrypted form and labelled by Bob’s system-generated ID. The cloud provider is not able to learn the content of the information.
- The trapdoors are encrypted using Bob’s SkR and stored on the SKA labelled by Bob’s system ID. The SKA is unable to learn the content of the trapdoors without having Bob’s SkR that is stored on the RA.
- The RA is the only entity in the system that can identify Bob in the system and his SkR. The RA stores all the information that is required to access Bob’s information as presented in Figure 2.
- Accessing stored patient information – Scenario
3.3.1. Protocol to access information stored in the cloud
- 1.
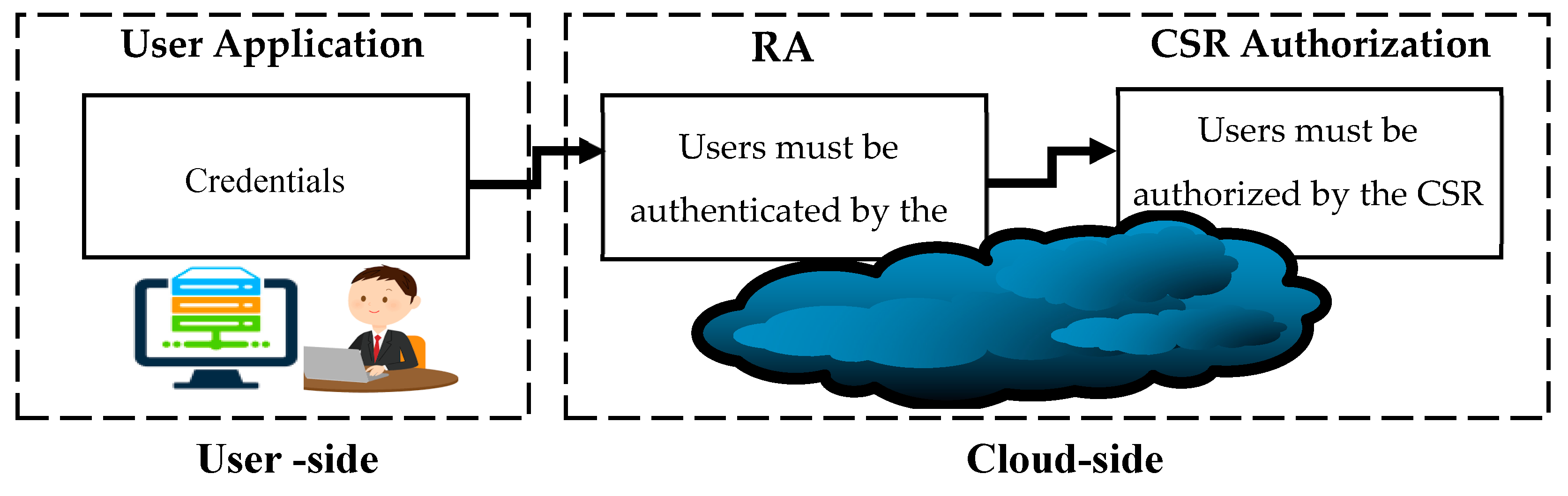
- It searches for Bob’s information using his basic information and finds his System ID.
- 2.
- It sends a request of authorization to the CSR. The request includes the following information:
- Information that is required to identify the nurse (user ID);
- List of users who have permanent consent to access Bob’s information;
- Bob’s mobile number for requesting his consent if required in this particular instance.
- It searches for the nurse information to identify her access rights to patient information. This happens by searching through the list of users that is stored locally on the CSR.
- It checks if the nurse is permanently consented to access Bob’s information using the list of users who have permanent consent to access Bob’s information.
- The CSR finds out that the nurse is allowed access doc-1 and doc-2 (Em_V) of patients’ information, but she is not permanently consented to access Bob’s information, therefore, Bob’s consent is required.
- The SCR sends a request of consent to Bob in the form of a text message. The content of the message includes:
- Bob’s system ID
- Indexes of doc-1 and doc-2
- The nurse’s application address
- Bob’s system ID and SkR
- Trapdoor-1 and Trapdoor-2 tags
- The nurse’s application address
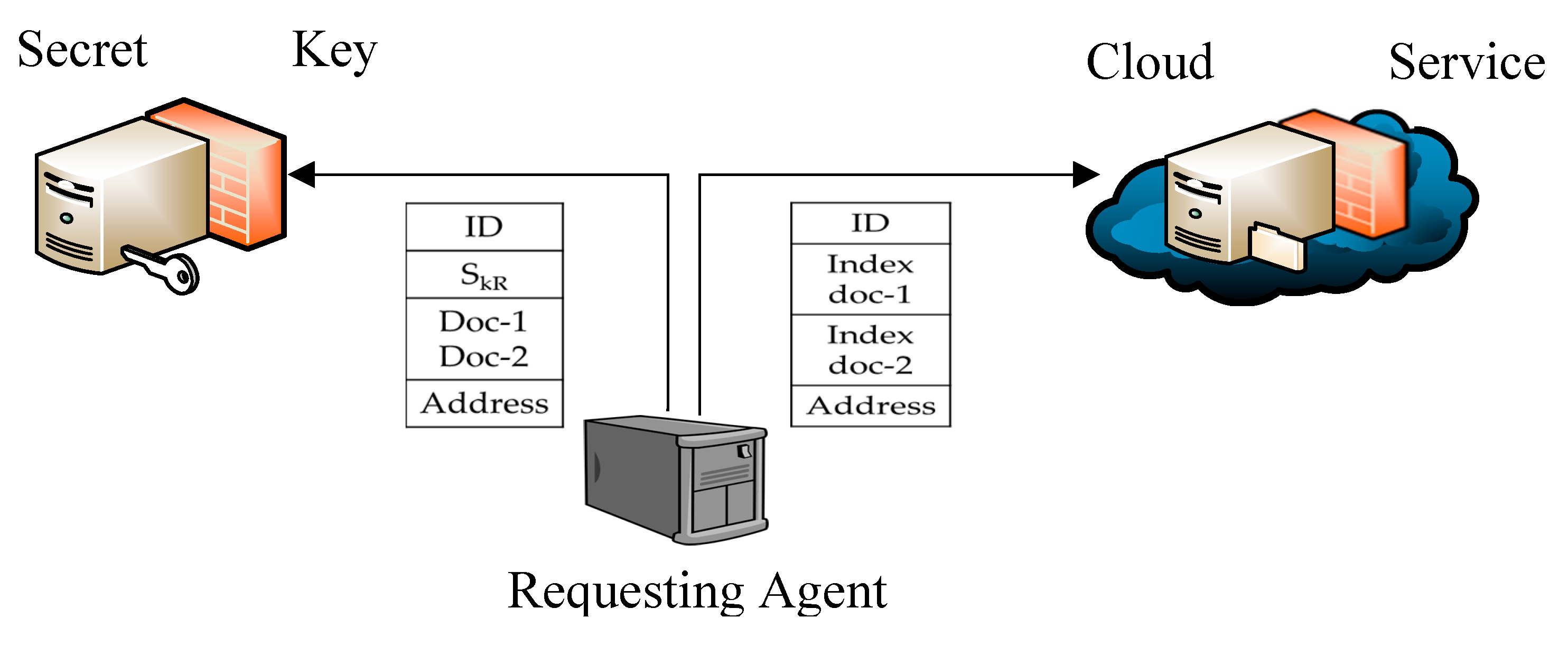
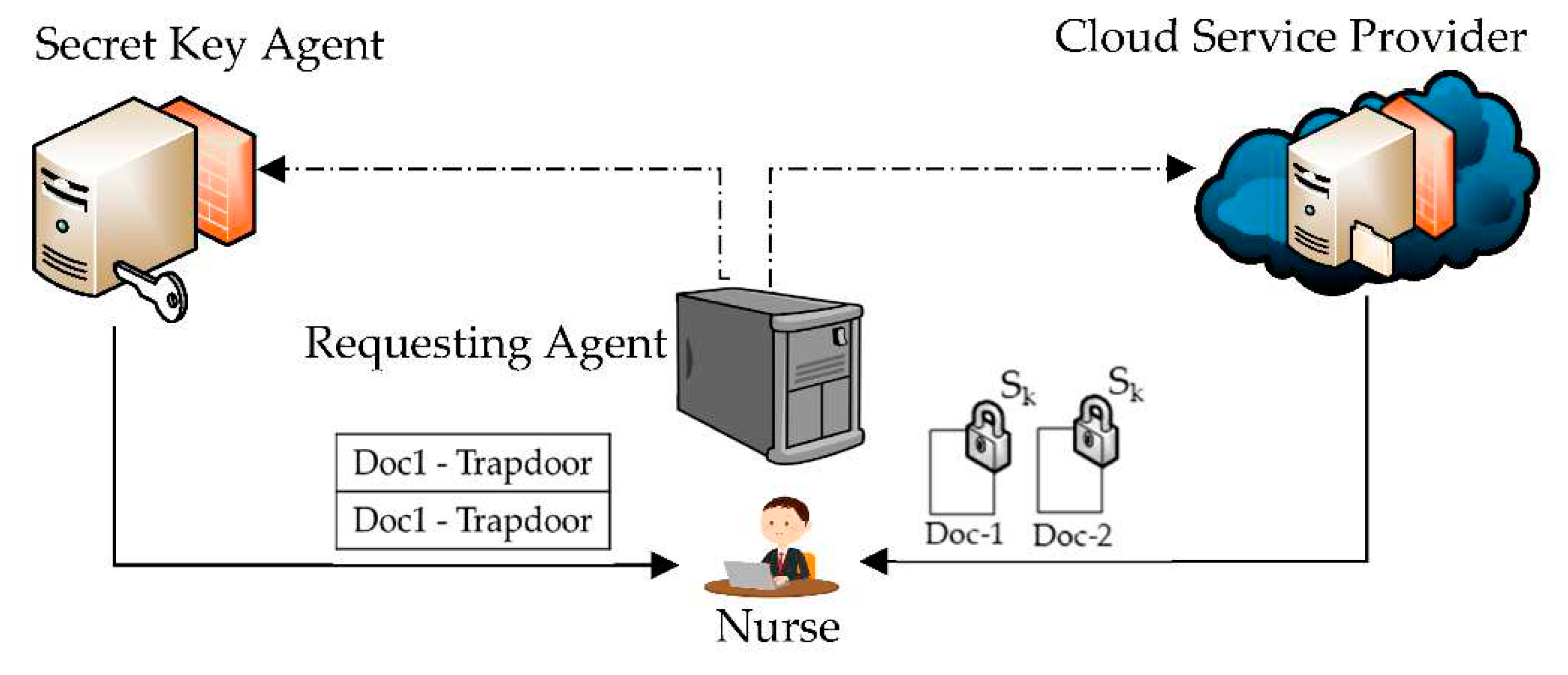
- Searches for Bob’s information using Bob’s system ID
- Searches for the doc-1 and doc-2 using their indexes.
- Sends the identified documents (doc-1 and doc-2) to the nurse using her application physical address.
- Searches for the encrypted trapdoors using Bob’s system ID
- Decrypts the trapdoors using Bob’s SkR
- Sends trapdoors for doc-1 and doc-2 to the nurse application using her application physical address.
- Re-encrypts the trapdoors using the same SkR and drops the SkR (deletes it).
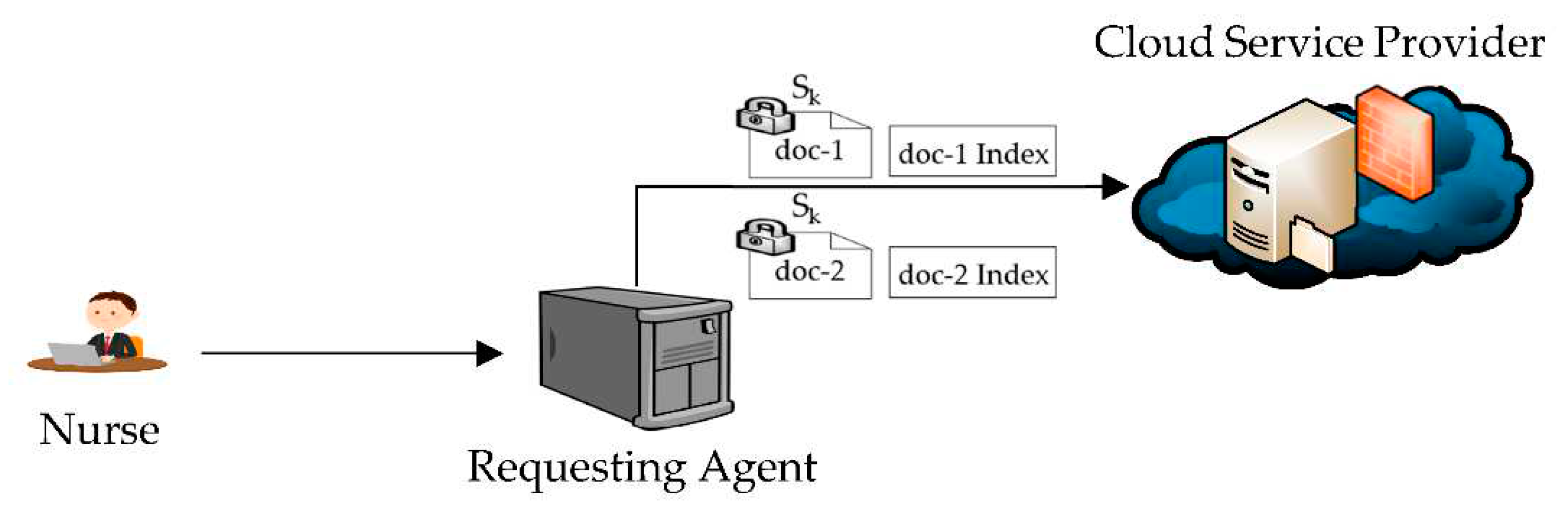
3.3.2. Updating patient information
- It searches for Bob’s information to identify him.
- It searches through the list of authorized users to access Bob’s information and finds the nurse listed as temporarily authorized users to access doc-1 and doc-2 of patients’ information.
- It forwards the encrypted information, indexes for doc-1 and doc-2, and Bob’s system ID to the CSP.
- It searches for Bob’s encrypted documents using indexes and system ID.
- It identifies the documents using the indexes and replaces them by the new ones
- It deletes the indexes received from the RA.
3.4. Architecture Implementation
- The ability of the cloud provider to access and read the information that is stored in the cloud
- The ability of unauthorized users to access patients’ information stored in the cloud
3.4.1. Implementation setup
- It sends Bob’s system ID and indexes of Doc-1 and Doc-2 to the CSP.
- It sends Bob’s system ID and trapdoor tags to the SKA.
3.4.2. Testing the architecture
| Test | Description | Result | Pass/Fail |
|---|---|---|---|
| Unauthorized System Access | Un authorized user made request to download a trapdoor that is stored on the cloud | Access Denied | Pass |
| Getting access to documents stored on the cloud | A document downloaded without having the secret key. | Document was viewed in its encrypted form | Pass |
| Unauthorized operations | Attempt made to access the server or the database by sending queries | Access Denied | Pass |
| Unknown users | Unregistered user attempted to log in to the system | Login failed | Pass |
4. Discussion
4.1. Privacy-preservation
4.2. Security Analysis
4.3. Architecture Limitation
- Network congestion: Healthcare organizations may experience network congestion when multiple users are accessing cloud-based services simultaneously. This can cause slowdowns, latency, or even complete loss of service.
- Geographic location: Healthcare providers located in remote or rural areas may not have access to high-speed internet, which can make accessing cloud-based services difficult.
- Data-intensive applications: Certain healthcare applications, such as EHRs or medical imaging systems, generate large amounts of data that need to be transferred over the internet. This can be a bandwidth-intensive process, which can lead to slowdowns and performance issues.
- Security: High-bandwidth applications may require additional security measures to protect patient data. This can further slowdown the data transfer process and add to the bandwidth requirements.
- Cost: Higher bandwidth requirements can result in increased costs for healthcare organizations, which may make cloud adoption less feasible.
- Assessing their current bandwidth requirements and planning for future needs. This can help ensure that their network infrastructure can handle the bandwidth requirements of cloud-based applications.
- Investing in high-speed internet connections and upgrading network infrastructure, including routers and switches.
- Considering cloud providers that offer content delivery networks (CDNs) to minimize latency and speed up data transfer times.
- Implementing data compression and deduplication techniques to reduce the amount of data that needs to be transferred over the internet.
- Prioritizing network traffic to ensure that bandwidth-intensive applications are given priority over less critical applications.
5. Conclusion
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- M. Gupta, M. Thirumalaisamy, S. Shamsher, A. Pandey, D. Muthiah and N. Suvarna, "Patient Health Monitoring using Feed Forward Neural Network with Cloud Based Internet of Things," in 2022 2nd International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE), Greater Noida, India, 2022.
- Mamlin, B.W.; Tierney, W.M. The Promise of Information and Communication Technology in Healthcare: Extracting Value From the Chaos. Am. J. Med Sci. 2016, 351, 59–68. [CrossRef]
- Neves, A.L.; Carter, A.W.; Freise, L.; Laranjo, L.; Darzi, A.; Mayer, E.K. Impact of sharing electronic health records with patients on the quality and safety of care: a systematic review and narrative synthesis protocol. BMJ Open 2018, 8, e020387. [CrossRef]
- Kalkman, S.; van Delden, J.; Banerjee, A.; Tyl, B.; Mostert, M.; van Thiel, G. Patients’ and public views and attitudes towards the sharing of health data for research: a narrative review of the empirical evidence. J. Med Ethic- 2019, 48, 3–13. [CrossRef]
- Kim, E.; Rubinstein, S.M.; Nead, K.T.; Wojcieszynski, A.P.; Gabriel, P.E.; Warner, J.L. The Evolving Use of Electronic Health Records (EHR) for Research. Semin. Radiat. Oncol. 2019, 29, 354–361. [CrossRef]
- Kitamura, T.; Kiyohara, K.; Matsuyama, T.; Hatakeyama, T.; Shimamoto, T.; Izawa, J.; Nishiyama, C.; Iwami, T. Is Survival After Out-of-Hospital Cardiac Arrests Worse During Days of National Academic Meetings in Japan? A Population-Based Study. J. Epidemiology 2016, 26, 155–162. [CrossRef]
- Gray, C.S.; Barnsley, J.; Gagnon, D.; Belzile, L.; Kenealy, T.; Shaw, J.; Sheridan, N.; Nji, P.W.; Wodchis, W.P. Using information communication technology in models of integrated community-based primary health care: learning from the iCOACH case studies. Implement. Sci. 2018, 13, 87. [CrossRef]
- W. Oude, L. v. Velsen, M. Huygens and H. Hermens, "Requirements for and Barriers towards Interoperable eHealth Technology in Primary Care," IEEE Internet Computing , pp. 10-19, 2015.
- Bélanger, F.; Crossler, R.E. Privacy in the Digital Age: A Review of Information Privacy Research in Information Systems. MIS Q. 2011, 35, 1017-1041.
- T. White, E. Blok and V. D. Calhoun, "Data sharing and privacy issues in neuroimaging research: Opportunities, obstacles, challenges, and monsters under the bed," Special Issue: The ENIGMA Consortium: the first 10 years, pp. 278-291, 2022.
- Wirth, F.N.; Meurers, T.; Johns, M.; Prasser, F. Privacy-preserving data sharing infrastructures for medical research: systematization and comparison. BMC Med Informatics Decis. Mak. 2021, 21, 1–13. [CrossRef]
- Public Law , "HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT OF 1996," Public Law 104-191, 104th Congress, 1996.
- Gunasekara, G.; Dillon, E. Data Protection Litigation in New Zealand: Processes and Outcomes. Vic. Univ. Wellingt. Law Rev. 2008, 39, 457–486. [CrossRef]
- A. Gkoulalas-Divanis and G. Loukides, "Introduction to Medical Data Privacy," in Medical Data Privacy Handbook, Switzerland, Springer International Publishing, 2015, pp. 1-14.
- Meng, S.; Fan, S.; Li, Q.; Wang, X.; Zhang, J.; Xu, X.; Qi, L.; Alam Bhuiyan, Z. Privacy-Aware Factorization-Based Hybrid Recommendation Method for Healthcare Services. IEEE Trans. Ind. Informatics 2022, 18, 5637–5647. [CrossRef]
- Gürsoy, G.; Li, T.; Liu, S.; Ni, E.; Brannon, C.M.; Gerstein, M.B. Functional genomics data: privacy risk assessment and technological mitigation. Nat. Rev. Genet. 2021, 23, 245–258. [CrossRef]
- Tanriverdi, M. A Systematic Review of Privacy Preserving Healthcare Data Sharing on Blockchain. 2020, ume 4, 31–37. [CrossRef]
- S. M. Blackman, "Towards a Conceptual Framework for Persistent Use: A Technical Plan to Achieve Semantic Interoperability within Electronic Health Record Systems," in Proceedings of the 50th Hawaii International Conference on System Sciences, 2017.
- Shahid, J.; Ahmad, R.; Kiani, A.K.; Ahmad, T.; Saeed, S.; Almuhaideb, A.M. Data Protection and Privacy of the Internet of Healthcare Things (IoHTs). Appl. Sci. 2022, 12, 1927. [CrossRef]
- Priyanga.P and MuthuKumar.V.P, "Cloud computing for healthcare organisation," International Journal of Multidisciplinary Research and Development , pp. 487-493, 2015.
- Casola, V.; Castiglione, A.; Choo, K.-K.R.; Esposito, C. Healthcare-Related Data in the Cloud: Challenges and Opportunities. IEEE Cloud Comput. 2016, 3, 10–14. [CrossRef]
- Svensson, A. Challenges in Using IT Systems for Collaboration in Healthcare Services. Int. J. Environ. Res. Public Heal. 2019, 16, 1773. [CrossRef]
- E. Griffith, "What Is Cloud Computing?," 03 May 2016. [Online]. Available: http://au.pcmag.com/networking-communications-software-products/29902/feature/what-is-cloud-computing. [Accessed 21 March 2017].
- Cresswell, K.; Hernández, A.D.; Williams, R.; Sheikh, A. Key Challenges and Opportunities for Cloud Technology in Health Care: Semistructured Interview Study. JMIR Hum. Factors 2022, 9, e31246. [CrossRef]
- P. Mell and T. Grance, "The NIST Definition of Cloud Computing," in National Institute of Standards and Technology , 2011.
- Doukas, C.; Pliakas, T.; Maglogiannis, I. Mobile healthcare information management utilizing Cloud Computing and Android OS. 2010 32nd Annual International Conference of the IEEE Engineering in Medicine and Biology Society (EMBC 2010). LOCATION OF CONFERENCE, ArgentinaDATE OF CONFERENCE; pp. 1037–40.
- Griebel, L.; Prokosch, H.-U.; Köpcke, F.; Toddenroth, D.; Christoph, J.; Leb, I.; Engel, I.; Sedlmayr, M. A scoping review of cloud computing in healthcare. BMC Med Informatics Decis. Mak. 2015, 15, 1–16. [CrossRef]
- R. Zhang and L. Liu, "Security Models and Requirements for Healthcare Application Clouds," in IEEE 3rd International Conference on Cloud Computing (CLOUD) ,, 2010.
- Sharma, M.; Sehrawat, R. A hybrid multi-criteria decision-making method for cloud adoption: Evidence from the healthcare sector. Technol. Soc. 2020, 61, 101258. [CrossRef]
- B. Yüksel, A. Küpçü and Ö. Özkasap, "Research issues for privacy and security of electronic health services," Future Generation Computer Systems, pp. 1-17, 2017.
- H. Raj, M. Kumar, P. Kumar, A. Singh and O. P. Verma, "Issues and Challenges Related to Privacy and Security in Healthcare Using IoT, Fog, and Cloud Computing," in Advanced Healthcare Systems: Empowering Physicians with IoT-Enabled Technologies, Scrivener Publishing LLC, 2022.
- H. Aziz and A. Guled, "Cloud Computing and Healthcare Services," Journal of Biosensors & Bioelectronics, 2016.
- Chenthara, S.; Ahmed, K.; Wang, H.; Whittaker, F. Security and Privacy-Preserving Challenges of e-Health Solutions in Cloud Computing. IEEE Access 2019, 7, 74361–74382. [CrossRef]
- Weir, C.R.; Hammond, K.W.; Embi, P.J.; Efthimiadis, E.N.; Thielke, S.M.; Hedeen, A.N. An exploration of the impact of computerized patient documentation on clinical collaboration. Int. J. Med Informatics 2011, 80, e62–e71. [CrossRef]
- E Dixon, B.; Embi, P.J.; A Haggstrom, D. Information technologies that facilitate care coordination: provider and patient perspectives. Transl. Behav. Med. 2018, 8, 522–525. [CrossRef]
- Bertagnolli, M.M.; Anderson, B.; Quina, A.; Piantadosi, S. The electronic health record as a clinical trials tool: Opportunities and challenges. Clin. Trials 2020, 17, 237–242. [CrossRef]
- Liu, X.; Wang, Z.; Jin, C.; Li, F.; Li, G. A Blockchain-Based Medical Data Sharing and Protection Scheme. IEEE Access 2019, 7, 118943–118953. [CrossRef]
- G. Cordovano and S. N. Shah, "Requesting Medical Records," Journal of Ahima, 2020.
- D. Gupta, S. Malik and A. Rana, "Adopting Semantic Interoperability for Improved Healthcare," SSRN, 2022.
- Rajkumar, N.; Muzoora, M.; Thun, S. Dentistry and Interoperability. J. Dent. Res. 2022, 101, 1258–1262. [CrossRef]
- L. Devadass, S. S. Sekaran and R. Thinakaran, "Cloud Computing in Healthcare," International Journal of Students’ Research In Technology & Management, vol. 5, no. 1, pp. 25-31, 2017.
- T. Quatrani, "Introduction to the Unified Modeling Language," IBM, 2003.
- T. Górski, "UML Profile for Messaging Patterns in Service-Oriented Architecture, Microservices, and Internet of Things," Applied Sciences, vol. 12, no. 24, 2022.
- Thramboulidis, K.; Christoulakis, F. UML4IoT—A UML-based approach to exploit IoT in cyber-physical manufacturing systems. Comput. Ind. 2016, 82, 259–272. [CrossRef]
- R. J. Petrasch and R. R. Petrasch, "Data Integration and Interoperability: Towards a Model-Driven and Pattern-Oriented Approach," Modelling, pp. 105-126, 2022.
- Pufahl, L.; Zerbato, F.; Weber, B.; Weber, I. BPMN in healthcare: Challenges and best practices. Inf. Syst. 2022, 107, 102013. [CrossRef]
- Schmidt, M.-T.; Hutchison, B.; Lambros, P.; Phippen, R. The Enterprise Service Bus: Making service-oriented architecture real. IBM Syst. J. 2005, 44, 781–797. [CrossRef]
- Niknejad, N.; Ismail, W.; Ghani, I.; Nazari, B.; Bahari, M.; Hussin, A.R.B.C. Understanding Service-Oriented Architecture (SOA): A systematic literature review and directions for further investigation. Inf. Syst. 2020, 91, 101491. [CrossRef]
- Aziz, O.; Farooq, M.S.; Abid, A.; Saher, R.; Aslam, N. Research Trends in Enterprise Service Bus (ESB) Applications: A Systematic Mapping Study. IEEE Access 2020, 8, 31180–31197. [CrossRef]
- Agbo, C.C.; Mahmoud, Q.H.; Eklund, J.M. Blockchain Technology in Healthcare: A Systematic Review. Healthcare 2019, 7, 56. [CrossRef]
- Jin, H.; Luo, Y.; Li, P.; Mathew, J. A Review of Secure and Privacy-Preserving Medical Data Sharing. IEEE Access 2019, 7, 61656–61669. [CrossRef]
- Abdellatif, A.A.; Al-Marridi, A.Z.; Mohamed, A.; Erbad, A.; Chiasserini, C.F.; Refaey, A. ssHealth: Toward Secure, Blockchain-Enabled Healthcare Systems. IEEE Netw. 2020, 34, 312–319. [CrossRef]
- Guo, R.; Shi, H.; Zheng, D.; Jing, C.; Zhuang, C.; Wang., Z. Flexible and Efficient Blockchain-Based ABE Scheme With Multi-Authority for Medical on Demand in Telemedicine System. IEEE Access 2019, 7, 88012–88025. [CrossRef]
- Xi, P.; Zhang, X.; Wang, L.; Liu, W.; Peng, S. A Review of Blockchain-Based Secure Sharing of Healthcare Data. Appl. Sci. 2022, 12, 7912. [CrossRef]
- J. Qu, "Blockchain in medical informatics," Journal of Industrial Information Integration, vol. 25, 2022.
- F. Alhaddadin, J. A. Gutiérrez and W. Liu, "Privacy-aware cloud-based architecture for sharing healthcare information," Auckland University of Technology, Auckland, New Zealand, 2020.
- R. Curtmola, J. Garay, S. Kamara and R. Ostrovsky, "Searchable Symmetric Encryption: Improved Definitions and Efficient Constructions," in 13th ACM Conference on Computer and Communications Security, 2006.
- D. Boneh, G. D. Crescenzo, R. Ostrovsky and G. Persiano, "Public Key Encryption with keyword Search," in International Conference on the Theory and Applications of Cryptographic Techniques, Berlin, Heidelberg, 2004.
- Y.-C. Chang, "Single Database Private Information Retrieval with Logarithmic Communication," in The 9th Australasian Conference on Information Security and Privacy, Sydney, Australia, 2004.
- E. Goh, "Secure Indexes," IACR ePrint Cryptography Archive, 2003.
- Eludiora, S.; Abiona, O.; Oluwatope, A.; Oluwaranti, A.; Onime, C.; Kehinde, L. A User Identity Management Protocol for Cloud Computing Paradigm. Int. J. Commun. Netw. Syst. Sci. 2011, 04, 152–163. [CrossRef]
- Amazon, "aws," 2019. [Online]. Available: https://aws.amazon.com.
- Marwaha, J.S.; Landman, A.B.; Brat, G.A.; Dunn, T.; Gordon, W.J. Deploying digital health tools within large, complex health systems: key considerations for adoption and implementation. npj Digit. Med. 2022, 5, 1–7. [CrossRef]
| Doc-1 | Doc-2 | Doc-3 |
|---|---|---|
| Full Name Date of Birth Gender Ethnicity Significant Conditions NHI Number Current Medication |
Drug Allergies Discharge, Summaries Blood Type Laboratory Results Next Kin |
All the information that is not contained in doc-1 and doc-2 |
| Doc-1 Encrypted Index | Doc-1 Trapdoor | ||||
|---|---|---|---|---|---|
| Basic Info | JK^78Uo8361KL$#VWL | Sk | JK^78Uo8361KL$#VWL | ||
| Significant | RM*#%H)GIDU784K2% | RM*#%H)GIDU784K2% | |||
| Medication | B&0*9QOVPI(068B%#O | B&0*9QOVPI(068B%#O | |||
| Doc-1 | APV*89&@JE)<I@DO$ | APV*89&@JE)<I@DO$ | |||
| Full Name | D.O. Birth | NHI Number |
| ID | SKR | doc-1 Index doc-2 Index doc-3 Index |
| User ID User ID User ID |
Email Phone Number |
|
| ID# | Role | Access Privilege |
|---|---|---|
| 29930894 | Nurse | doc-1 | doc-2 |
| 29930804 | Doctor | doc-1 | doc-2 | doc-3 |
| 29930832 | Receptionist | doc-1 |
| 29930930 | Doctor | doc-1 | doc-2 | doc-3 |
| Section 1 | Section 2 | Section 3 | |
|---|---|---|---|
| Organization ID Practitioner ID Patient Name Patient DOB Patient NHI Consent Method: Phone# |
SKR |
Encrypted information doc-1 doc-2 doc-3 |
|
| doc-1 Index doc-2 Index doc-3 Index |
doc-1 Trapdoor doc-1 Trapdoor doc-1 Trapdoor |
||
| SysId# | UserId | Role | Access Privilege |
|---|---|---|---|
| 29930894 | 7777 | Receptionist | doc-1 |
| 29930804 | 8888 | Nurse | doc-1 | doc-2 |
| 29930832 | 9999 | Specialist | doc-1 | doc-2 | doc-3 |
| 29930930 | 6666 | Receptionist | doc-1 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





