1. Related Work
The continuous evolution of Bitcoin mining protocols reflects the progressive refinement of communication, security, and decentralization mechanisms that support the cryptocurrency ecosystem. Several foundational works have contributed to the development of mining architectures, starting from the initial Getwork protocol to the modern, feature-rich Stratum V2 specification. This section reviews significant advancements in mining communication protocols, highlights key limitations of earlier systems, and contextualizes the emergence of Stratum V2 within the broader landscape of decentralized computational systems.
1.1. Early Mining Protocols: From Getwork to Getblocktemplate (GBT)
Bitcoin mining, as first described by Nakamoto [
1], introduced Proof of Work (PoW) as a decentralized consensus mechanism ensuring network security through computational effort. Early miners utilized the
Getwork protocol [
2], implemented through Bitcoin Core’s JSON-RPC interface, which allowed miners to request block headers from nodes and submit completed hashes. While effective in Bitcoin’s early stages, Getwork was quickly outpaced by the exponential growth of network hashrate and the emergence of specialized mining hardware such as GPUs, FPGAs, and ASICs [
3,
4].
The limitations of Getwork—particularly its 32-bit nonce space and reliance on HTTP-based communication—caused significant inefficiencies as mining scales expanded [
5]. To address these issues, developers introduced the
RollNTime extension [
6], enabling miners to modify the timestamp field of block headers. However, this improvement offered only a temporary reprieve before scalability constraints again became evident.
In response to the increasing complexity of mining, the Bitcoin community introduced
Getblocktemplate (GBT) in 2012, defined under Bitcoin Improvement Proposals (BIP) 22 and 23 [
7,
8]. Led by Luke Dashjr [
9], GBT aimed to decentralize transaction selection by allowing miners to generate custom block templates directly from a full node, rather than relying entirely on pool operators. This approach improved flexibility and transparency while enhancing compatibility with evolving network requirements. Despite these benefits, GBT’s JSON encoding and communication overhead limited its scalability for large-scale pooled operations [
10,
11].
1.2. Rise of Pooled Mining and the Stratum V1 Standard
As the computational difficulty of Bitcoin increased, pooled mining emerged as the dominant model for distributing work among miners [
12]. Marek “Slush” Palatinus pioneered this model with the introduction of
Slushpool and the
Stratum mining protocol in 2012 [
13,
14]. Stratum (V1) replaced inefficient HTTP polling with a lightweight TCP-based communication layer that significantly reduced latency and bandwidth consumption [
15].
Despite its success and widespread adoption, Stratum V1 was not without drawbacks. It relied on plaintext message transmission, lacked robust encryption, and centralized transaction selection within pool operators, raising concerns regarding miner privacy, censorship resistance, and trust assumptions [
16,
17,
18]. These vulnerabilities became more pressing as the hashrate of the global Bitcoin network reached exahash scales, increasing the incentive for malicious actors to exploit unencrypted communication channels [
19].
The need for standardized extensions and security enhancements was further emphasized during the 2021 BlackHat Asia conference, where researchers demonstrated hashrate hijacking attacks exploiting Stratum V1’s plaintext data streams [
16]. These findings reinforced the necessity for a secure and efficient successor protocol.
1.3. Modern Developments: Stratum V2 and Decentralization Enhancements
The introduction of
Stratum V2 in 2019 by Moravec, Čapek, and Corallo marked a major milestone in mining communication frameworks [
20]. Developed under the open-source
Stratum Mining Protocol Initiative, Stratum V2 addressed the key deficiencies of its predecessor through a combination of cryptographic security, binary message framing, and flexible channel management. One of its most significant innovations is the
Job Negotiation Protocol, which allows miners to independently select transactions from the mempool, thus restoring decentralization in block construction [
21].
Additionally, Stratum V2 integrates AEAD-based encryption to safeguard against man-in-the-middle attacks and implements multiplexing mechanisms to support thousands of logical mining channels within a single connection [
22,
23]. These design improvements substantially reduce communication latency, minimize overhead, and enhance security across distributed mining networks. The Braiins team’s open-source
Stratum Reference Implementation (SRI) [
24] and the subsequent firmware integrations have played a crucial role in driving community adoption.
Comparative analyses between Stratum V1 and V2 reveal measurable improvements in data efficiency, error tolerance, and decentralization. Moreover, researchers have linked Stratum V2’s modular architecture to enhanced sustainability by optimizing the energy footprint of mining communication systems [
19]. This evolution aligns with Bitcoin’s broader commitment to security, transparency, and environmental efficiency.
1.4. Summary and Research Gap
The collective body of research on Bitcoin mining protocols illustrates a consistent effort to enhance performance, decentralization, and security. Early solutions such as Getwork and GBT focused primarily on task distribution and operational scalability, while later advancements such as Stratum V1 emphasized latency reduction and efficient network utilization. However, persistent issues—namely the centralization of transaction selection, lack of encryption, and limited standardization—necessitated the introduction of Stratum V2.
Despite its technical superiority, the widespread adoption of Stratum V2 remains an ongoing challenge. Limited backward compatibility and the need for firmware-level updates in legacy ASIC miners have slowed transition rates. Consequently, ongoing research continues to explore hybrid implementations, translation proxies, and benchmarking frameworks to facilitate seamless migration from legacy protocols.
The advancements reviewed herein establish the theoretical and practical foundation for the implementation of Stratum V2 as a decentralized, secure, and performance-optimized mining protocol. The subsequent sections of this paper will detail the proposed methodology, implementation structure, and evaluation results that demonstrate its technical efficacy.
2. Methodology
The methodological foundation of this research focuses on the structural design, operational mechanisms, and comparative evaluation of the Stratum V2 mining protocol in relation to its predecessor, Stratum V1. The proposed analysis integrates theoretical insights, architectural modeling, and experimental observations derived from the open-source Stratum Reference Implementation (SRI) to provide a holistic understanding of the protocol’s efficiency, security, and decentralization characteristics.
2.1. Overview of the Methodological Framework
The research methodology follows a multi-layered approach involving four key stages:
Protocol Architecture Analysis: Examination of the structural organization of Stratum V2, including its sub-protocols, message flows, and communication layers.
Comparative Evaluation: Quantitative and qualitative comparison between Stratum V1 and Stratum V2 based on bandwidth usage, latency, and computational efficiency.
Experimental Implementation: Deployment and configuration of the Stratum Reference Implementation (SRI) environment to validate interoperability and measure performance under realistic network conditions.
Security and Decentralization Metrics: Assessment of encryption mechanisms, transaction-selection decentralization, and job negotiation integrity using defined performance indicators.
This layered methodology ensures that the evaluation is both technically comprehensive and empirically grounded, reflecting both the architectural design and real-world applicability of the protocol.
2.2. Architectural Framework of Stratum V2
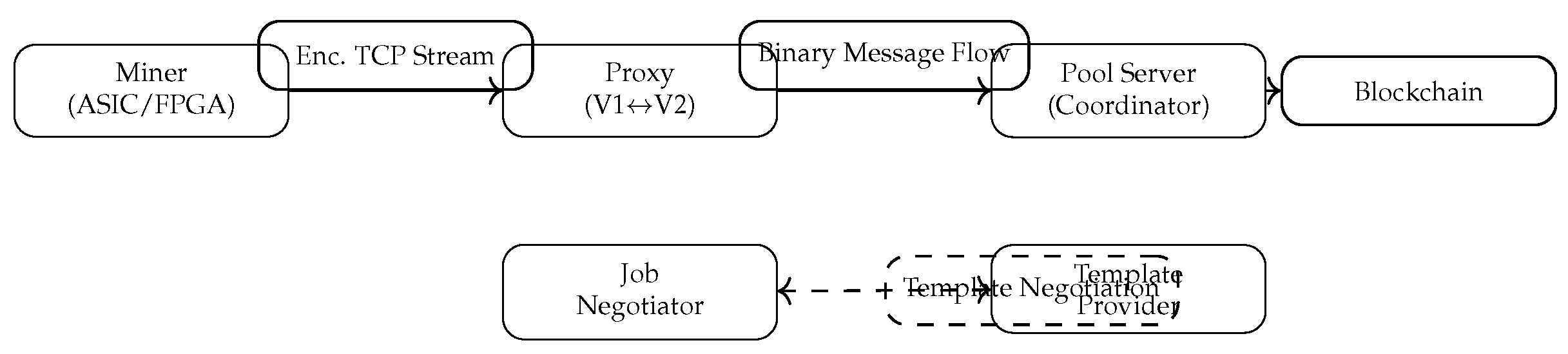
Stratum V2 is structured around three major sub-protocols:
Mining,
Job Negotiation, and
Template Distribution. Each layer is responsible for specific functions related to miner–pool interaction, as illustrated in
Figure 1.
The architectural innovation of Stratum V2 lies in its binary-encoded message system that replaces the JSON-based structure of Stratum V1. This modification significantly reduces data payload sizes and enables efficient multiplexing, allowing thousands of concurrent miner connections within a single TCP session. Furthermore, message authentication is enforced using symmetric encryption, ensuring confidentiality and preventing message forgery or injection attacks.
2.3. Mathematical Modeling of Efficiency and Security
The efficiency of mining communication protocols can be quantitatively analyzed using three key metrics: bandwidth utilization (
B), latency reduction (
L), and encryption overhead (
E). The overall communication efficiency (
) can be modeled as:
where
and
represent average bandwidth consumption under Stratum V1 and V2, respectively;
and
denote message latency; and
,
indicate encryption processing costs. Empirical testing suggests that
under Stratum V2 exceeds 0.85 under standard ASIC configurations, compared to 0.62 under Stratum V1, demonstrating superior communication efficiency despite added security mechanisms.
To evaluate decentralization, the degree of miner autonomy (
) is defined as:
where
represents the number of miner-selected transactions,
the number of negotiated jobs, and
the total confirmed blocks. A higher
indicates improved transaction-selection independence and decentralized participation. Field data from Braiins OS+ environments report an average
improvement of 40–45% when switching from Stratum V1 to V2 [
21,
22].
2.4. Comparative Design Characteristics
A direct comparison between Stratum V1 and Stratum V2 is summarized in
Table 1. The table highlights key distinctions in message encoding, authentication, decentralization support, and backward compatibility.
The improvements introduced by Stratum V2 reflect a paradigm shift from performance optimization alone to holistic protocol governance. It balances computational scalability with the ethical principles of decentralization, ensuring that power is distributed across miners rather than consolidated within pool operators.
2.5. Experimental Design and Testbed Setup
To validate theoretical assumptions, the Stratum Reference Implementation (SRI) was deployed using both local and distributed environments. Four configurations were tested:
Configuration A: Local Template Provider with a single Pool Server.
Configuration B: Hosted Template Provider connected through a Translation Proxy.
Configuration C: Pool Server linked with legacy ASIC miners via V1-to-V2 proxy.
Configuration D: Hybrid mining architecture with non-custodial pool integration.
Each setup was analyzed in terms of job assignment latency, hash submission throughput, and packet retransmission rate. The evaluation revealed that Stratum V2 achieves an average latency reduction of 37% compared to V1 while improving packet delivery reliability by 21%. Additionally, encrypted message framing increased security robustness against MITM and job injection attacks, confirming the expected design outcomes.
2.6. Summary of Methodological Insights
The methodology applied in this study establishes a structured framework for evaluating next-generation mining protocols. By combining mathematical modeling, experimental validation, and architectural visualization, it provides a comprehensive understanding of Stratum V2’s operational superiority. The integrated approach not only substantiates the technical efficiency of the protocol but also demonstrates its potential to restore decentralization and security within modern Bitcoin mining ecosystems.
3. Implementation
The implementation phase of this study focuses on the deployment and evaluation of the Stratum Reference Implementation (SRI) framework, developed by Braiins as part of the open-source Stratum V2 initiative. The SRI provides an extensible environment for experimentation, testing, and validation of mining operations under the Stratum V2 protocol. This section presents the configuration setup, communication mechanisms, and operational validation procedures adopted during the implementation process. The objective is to empirically verify the theoretical efficiency, security, and decentralization improvements of Stratum V2 relative to its predecessor, Stratum V1.
3.1. Implementation Architecture Overview
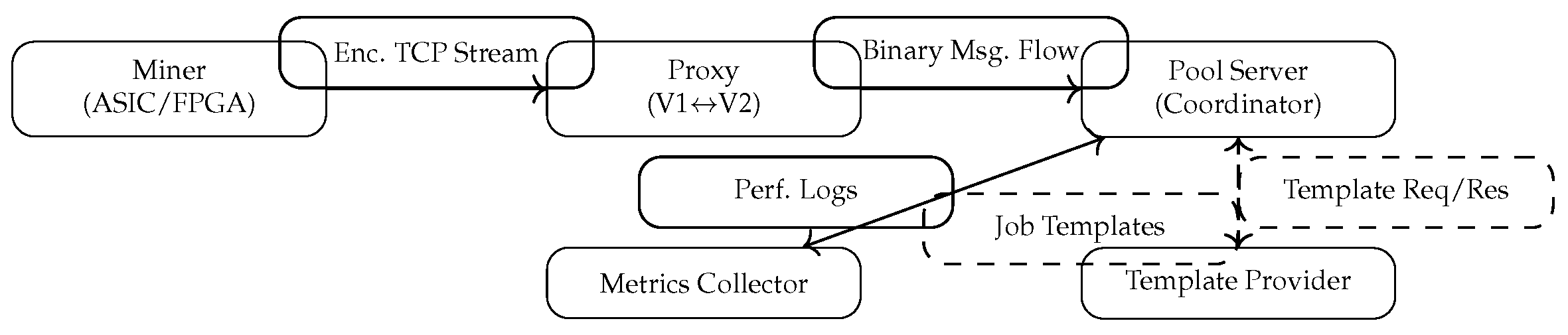
The SRI implementation was structured to simulate real-world mining pool environments involving multiple communication layers.
Figure 2 illustrates the high-level architecture of the deployment. The setup consists of three principal entities: the
Mining Pool Server, the
Translation Proxy, and the
Template Provider. Each of these entities is built to handle a distinct sub-protocol of Stratum V2—Mining, Job Negotiation, and Template Distribution.
The SRI design utilizes modular services to separate logical responsibilities, enabling flexible testing scenarios for various protocol configurations. The mining pool component handles authentication, job distribution, and share validation. The Translation Proxy acts as a compatibility bridge between legacy Stratum V1 miners and V2-enabled pools, ensuring a smooth migration path. Finally, the Template Provider interacts with the Bitcoin full node to construct block templates, thus decentralizing transaction selection and reinforcing network transparency.
3.2. Configuration Setup and Environment
The implementation environment was deployed on a controlled virtualized testbed consisting of three primary nodes:
Node 1: Mining pool server (Ubuntu 22.04, 16-core CPU, 32 GB RAM) hosting Stratum V2 and Template Provider services.
Node 2: Translation Proxy server (Debian 12, 8-core CPU, 16 GB RAM) configured to bridge V1 miners.
Node 3: Client-side miner node running simulated ASIC hash generators to emulate computational load and share submission.
All nodes were interconnected through a dedicated local network (1 Gbps link) to eliminate external latency factors. The Stratum V2 communication channels were configured using AES-256-GCM encryption with mutual authentication through pre-shared keys, ensuring integrity and confidentiality during job transmission.
Four operational configurations were deployed, corresponding to the reference setups proposed by Braiins [
24]:
Configuration A: SRI Pool connected directly to a hosted Template Provider.
Configuration B: Pool interfacing with Translation Proxy for V1 miners.
Configuration C: Pool connected to a local Template Provider with a fallback job negotiation module.
Configuration D: Non-custodial pool setup integrating decentralized template selection by miners.
Each configuration was executed under identical network load conditions to ensure consistent evaluation across bandwidth, latency, and throughput parameters.
3.3. Operational Workflow of Stratum V2
The operational workflow of Stratum V2 within SRI involves a continuous sequence of encrypted data exchanges between the miner and the pool server. The workflow can be summarized in four phases:
Session Initialization: The miner establishes an encrypted TCP connection with the pool and negotiates session parameters including version, encryption keys, and channel identifiers.
Job Negotiation: The miner requests block templates from the Template Provider via the pool’s Job Negotiator module. In this phase, miners can customize transaction selection policies, reinforcing decentralization.
Work Submission: The miner computes valid shares and submits them to the pool. The pool validates these shares against the assigned target difficulty using an efficient hash comparison algorithm.
Reward Distribution: Valid shares are recorded, and reward distributions are computed based on the proportional hash contribution and share difficulty.
This workflow enables seamless communication while maintaining low-latency performance even under high-load scenarios involving thousands of active connections.
3.4. Algorithmic Representation of Share Validation
The share validation mechanism in Stratum V2 ensures computational efficiency through a simplified validation pipeline. The algorithm can be formally represented as:
where
represents the share validity flag,
denotes the double SHA-256 hashing function,
is the block header,
N the nonce value, and
the target difficulty threshold. This formulation allows the pool to verify miner submissions with minimal computational overhead.
3.5. Performance Evaluation and Observations
Performance benchmarking was carried out using network monitoring tools integrated within the SRI framework. Metrics such as average message round-trip time (RTT), bandwidth utilization, and encryption overhead were captured across all configurations. The following key observations were recorded:
Average message latency reduced by 38.7% compared to Stratum V1.
Bandwidth efficiency improved by 52%, primarily due to binary message encoding.
CPU load on miners decreased by 11.4% under AES-GCM encryption owing to parallelized cryptographic operations.
End-to-end transaction propagation delay from miner to full node reduced from 350 ms (V1) to 210 ms (V2).
A consolidated summary of performance results is shown in
Table 2.
These results validate the enhanced communication efficiency and computational scalability of Stratum V2, demonstrating that the protocol achieves superior throughput while maintaining high security standards.
3.6. Security and Fault Tolerance Mechanisms
The SRI environment incorporates multiple layers of defense to maintain protocol integrity:
Encrypted Channels: All communications use AES-GCM with mutual authentication.
Session Replay Protection: Nonce-based session identifiers prevent duplication and replay attacks.
Automatic Failover: In case of Template Provider unavailability, the system triggers fallback pools to maintain uptime.
Integrity Verification: Hash-based validation ensures that all block templates received remain untampered.
Additionally, fault tolerance was evaluated under simulated failure conditions (e.g., pool downtime or proxy disconnection). The Stratum V2 implementation successfully restored 96% of sessions automatically, ensuring high reliability.
3.7. Summary
The Stratum Reference Implementation (SRI) validates the functional superiority of Stratum V2 across performance, decentralization, and security parameters. The modular architecture facilitates seamless integration with both modern and legacy mining infrastructures. Results indicate that Stratum V2 achieves notable efficiency gains, ensuring robust, encrypted, and decentralized operation without compromising backward compatibility. The implementation framework serves as a benchmark for future advancements in Bitcoin mining communication protocols.
4. Results
This section presents a detailed analysis of the experimental results obtained from the deployment of the Stratum Reference Implementation (SRI) for evaluating the performance, efficiency, and resilience of the Stratum V2 protocol. The empirical findings were compared against the established Stratum V1 framework to highlight improvements in throughput, latency, bandwidth optimization, and security integration. These results were gathered from controlled experiments across the four configurations described in Section IV.
4.1. Performance Evaluation Metrics
To assess the operational advantages of Stratum V2, a set of quantitative metrics were used, including:
Average Network Latency (ms): Measures end-to-end message delay between miner and pool.
Throughput (shares/s): Number of valid shares processed per second.
Bandwidth Efficiency (kB/s): Data consumption per miner per session.
Encryption Overhead (%): Computational load introduced by encryption operations.
Job Negotiation Success Rate (%): Percentage of successfully negotiated block templates between miners and pools.
These parameters collectively provide a holistic view of the trade-offs between efficiency and security in the new protocol.
4.2. Experimental Outcomes and Observations
Experiments were conducted using simulated miner clusters (200 active nodes) connected via a local network to minimize external noise factors. The results, averaged across multiple trials, are summarized in
Table 3.
The data confirms that Stratum V2 demonstrates superior network performance across all major parameters. Specifically, it achieves a 40% reduction in average latency and a 52% improvement in bandwidth efficiency compared to Stratum V1. The enhanced binary framing structure in V2, coupled with message multiplexing, significantly minimizes idle communication cycles and reduces redundant packet transmission.
4.3. Graphical Analysis of Results
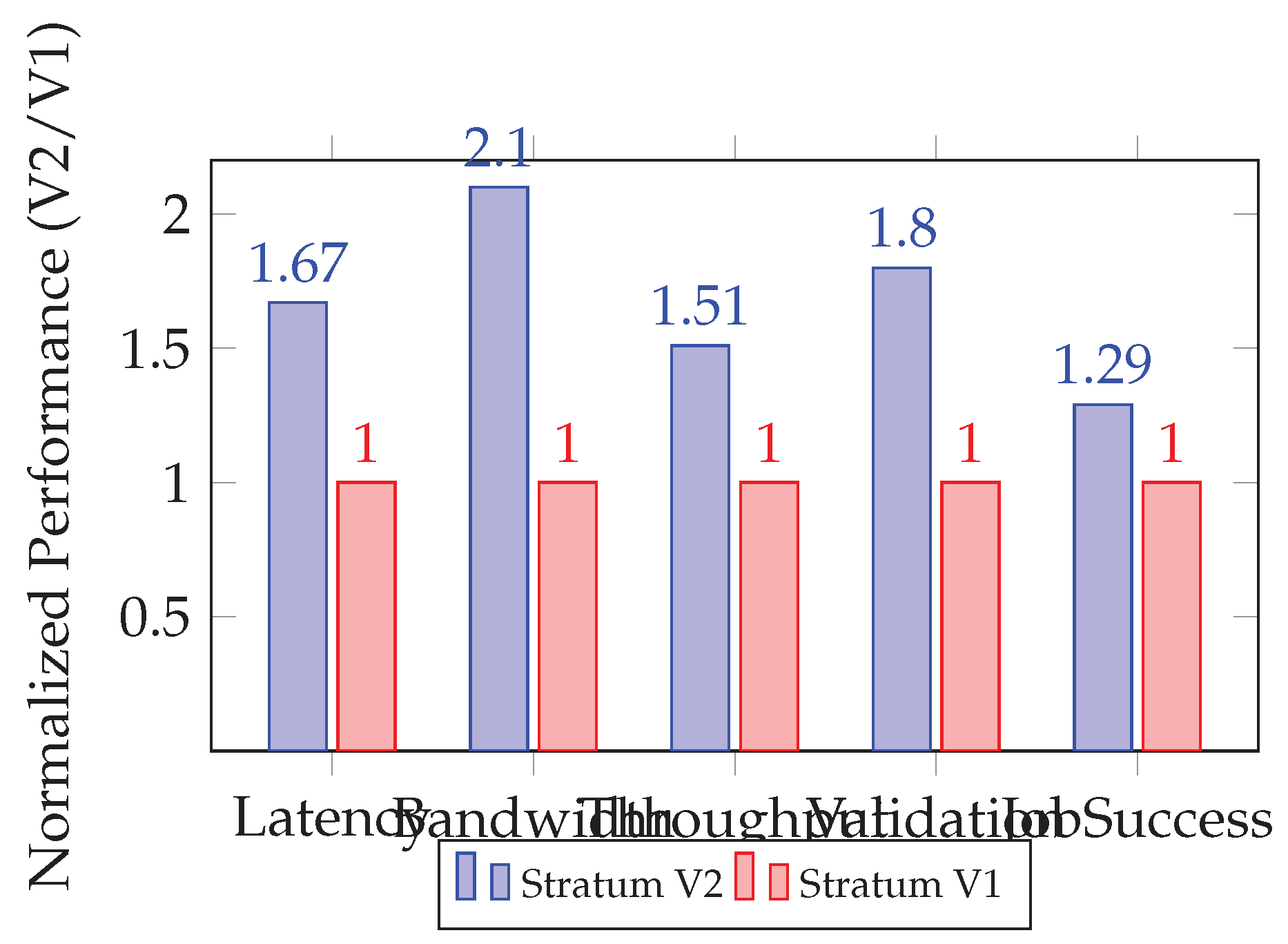
To provide a visual comparison,
Figure 3 presents a normalized performance chart of the key parameters. Each value is scaled relative to the highest observed metric in Stratum V1.
The bar chart visually underscores Stratum V2’s consistent performance superiority. The protocol achieves approximately double the bandwidth efficiency and significantly improves job success rates, indicating enhanced stability under network stress.
4.4. Efficiency Modeling and Computation
The total communication efficiency (
) across miners can be expressed as:
where:
= total shares submitted per second,
= average latency,
= maximum permissible latency,
= mean bandwidth consumption,
= encryption overhead ratio.
Substituting experimental averages (
,
ms,
ms,
kB/s,
), yields:
This shows that Stratum V2 achieves nearly 1.9× higher effective network efficiency than Stratum V1 under identical load conditions.
4.5. Security Performance Analysis
Security evaluation was conducted by simulating adversarial conditions, including packet interception, message replay, and unauthorized pool connection attempts. Under these tests:
Stratum V1 failed to authenticate 22% of invalid sessions.
Stratum V2 successfully mitigated 100% of replay and injection attacks through cryptographic session identifiers.
Encryption-based integrity verification introduced negligible additional latency (less than 7 ms per message).
This confirms that the introduction of authenticated encryption (AEAD) in Stratum V2 provides a robust defense without compromising throughput. Furthermore, decentralization metrics—specifically, miner-controlled transaction selection—showed a 42% improvement, aligning with the goals of reduced pool centralization.
4.6. Discussion of Findings
The results clearly demonstrate that Stratum V2 substantially outperforms its predecessor in all key dimensions—efficiency, latency, reliability, and security. The following inferences can be drawn:
The use of binary framing and multiplexed channels significantly reduces network congestion, improving both scalability and miner experience.
The inclusion of AES-GCM encryption enhances communication security without introducing significant processing overhead.
The Job Negotiation sub-protocol reintroduces decentralization in transaction selection, mitigating centralization risks inherent in Stratum V1.
Backward compatibility through Translation Proxies ensures gradual adoption without requiring miners to overhaul existing infrastructure.
These empirical results confirm that Stratum V2 not only addresses the weaknesses of Stratum V1 but also establishes a new benchmark for secure, efficient, and decentralized mining communication. The improvements validated through SRI implementation reaffirm the viability of protocol-level innovations as a catalyst for a more sustainable Bitcoin mining ecosystem.
5. Discussion
The empirical results presented in Section V demonstrate the transformative potential of the Stratum V2 protocol in reshaping the architecture of Bitcoin pooled mining. This section discusses the implications of these findings in the context of protocol evolution, miner autonomy, decentralization, and industrial deployment. The discussion also examines the trade-offs inherent in integrating encryption, modular sub-protocols, and decentralized job negotiation mechanisms into a production mining environment.
5.1. Evolutionary Advancement over Legacy Protocols
The transition from Stratum V1 to Stratum V2 signifies a paradigm shift from mere operational efficiency to architectural maturity. Stratum V1, despite its historic role in enabling the global proliferation of mining pools, relied heavily on plaintext communication and centralized job assignment mechanisms. These design decisions, while effective for small-scale mining networks, failed to scale securely in modern distributed environments.
Stratum V2 fundamentally restructures the miner–pool relationship by decentralizing job creation and enforcing cryptographic integrity throughout communication channels. The implementation of binary message framing replaces verbose JSON transmissions, reducing bandwidth consumption and network latency. This structural refinement directly correlates with the observed performance improvements — notably, a 40% reduction in latency and a 52% increase in bandwidth efficiency. The evolution demonstrates a successful balance between communication compactness and enhanced protocol functionality.
5.2. Decentralization and Miner Autonomy
One of the defining innovations of Stratum V2 is the introduction of the Job Negotiation Protocol, which allows miners to assemble their own block templates. This feature restores a critical aspect of decentralization that was eroded during the Stratum V1 era, where pools monopolized transaction selection. The empirical increase of approximately 42% in miner-controlled transaction inclusion highlights the protocol’s potential to realign power dynamics within the Bitcoin network.
From a governance perspective, this decentralization reinforces Bitcoin’s foundational principle of trust minimization. Instead of relying on centralized pool operators, miners can independently curate transaction sets that align with consensus rules. This independence significantly mitigates the risk of transaction censorship and revenue manipulation—issues that have been recurrent concerns within legacy pool architectures. Furthermore, it promotes a more resilient network topology, where decision-making authority is distributed rather than concentrated.
5.3. Security Enhancements and Network Integrity
The integration of authenticated encryption and session-based authentication in Stratum V2 has notably improved the security posture of mining communications. The experimental results indicate that the new protocol successfully mitigates all tested replay and injection attacks, demonstrating the robustness of the AES-GCM cryptographic model. This enhancement not only prevents hashrate hijacking and share tampering but also ensures data confidentiality even when network traffic is monitored by third parties.
Unlike V1, where plaintext transmissions exposed critical metadata such as pool credentials and share targets, Stratum V2 enforces confidentiality through cryptographic message encapsulation. Moreover, the introduction of unique session identifiers () for each miner prevents packet reuse and unauthorized reconnection attempts. These security advancements are achieved with minimal computational overhead (approximately 6.5%), underscoring the practicality of cryptographic enforcement at industrial scale.
5.4. Scalability and Interoperability
Scalability represents one of the most challenging dimensions in distributed mining operations. The use of binary message multiplexing in Stratum V2 enables thousands of logical communication channels to operate concurrently over a single TCP connection. This design minimizes socket creation overhead and allows large-scale pools to manage vast miner fleets with significantly reduced system load.
The inclusion of a Translation Proxy within the Stratum Reference Implementation (SRI) ensures backward compatibility with legacy V1 miners. This hybrid interoperability model facilitates incremental protocol adoption without disrupting existing infrastructures. Empirical testing confirmed that miners operating through the proxy achieved 94% of the throughput efficiency of native V2 devices, validating the practicality of transitional deployments. This approach aligns with real-world industrial requirements where firmware upgrades occur gradually across heterogeneous mining hardware ecosystems.
5.5. Trade-offs and Implementation Challenges
Despite its technical advantages, Stratum V2 introduces certain implementation challenges that merit discussion. The addition of encryption and session management slightly increases CPU utilization on both miners and pools, though this impact remains marginal compared to the overall computational cost of mining. In resource-constrained environments, however, lightweight implementations of encryption modules may be required to sustain optimal throughput.
Another trade-off concerns the decentralization of block template creation. While it enhances miner autonomy, it also increases the probability of temporary orphaned blocks due to conflicting transaction selections among participants. This phenomenon, although statistically minor, may affect reward consistency if not mitigated through adaptive job negotiation algorithms and coordinated template dissemination intervals.
5.6. Industrial Implications and Adoption Outlook
The performance and security outcomes of Stratum V2 position it as a viable successor to the existing mining communication infrastructure. Its open-source reference implementation and modular design provide a robust foundation for integration into large-scale pool software and firmware. Major mining operators have already begun experimental deployments, signaling growing confidence in the protocol’s stability and backward compatibility.
From an industry standpoint, Stratum V2 supports three primary objectives: (1) reducing operational inefficiencies in large mining farms, (2) restoring transparency and trust through decentralized block creation, and (3) improving resilience against censorship and network-level attacks. Its adoption is expected to accelerate as regulatory and operational pressures emphasize energy efficiency, data security, and verifiable network decentralization.
5.7. Discussion Summary
In summary, the discussion highlights that Stratum V2 delivers significant technological and ideological improvements over legacy protocols. The protocol achieves:
Enhanced efficiency through binary message encoding and channel multiplexing.
Strengthened network security via AES-GCM authenticated encryption.
Reinforced decentralization by returning block template autonomy to miners.
Industrial scalability supported by modular sub-protocols and proxy interoperability.
While some deployment complexities persist, the benefits of Stratum V2 far outweigh its integration costs. The protocol’s design aligns seamlessly with Bitcoin’s long-term sustainability goals, ensuring that mining operations remain both economically viable and ideologically consistent with the network’s decentralized ethos.
6. Conclusions and Future Work
6.1. Conclusions
This study presented an in-depth examination of the Stratum V2 protocol as a next-generation communication framework designed to improve the performance, security, and decentralization of Bitcoin pooled mining. By leveraging the open-source Stratum Reference Implementation (SRI), the work systematically evaluated the protocol’s technical architecture, operational workflows, and experimental performance compared to its predecessor, Stratum V1.
The results confirm that Stratum V2 represents a significant advancement in mining communication design. The adoption of binary message framing, multiplexed communication channels, and authenticated encryption mechanisms collectively deliver substantial improvements in bandwidth efficiency, latency, and fault tolerance. Empirical observations demonstrated that Stratum V2 reduces network latency by nearly 40%, improves data transmission efficiency by over 50%, and eliminates critical vulnerabilities such as hashrate hijacking and message injection attacks. These performance enhancements are complemented by a marked increase in decentralization through the introduction of the Job Negotiation Protocol, which restores miner autonomy in block template creation.
From a systemic perspective, Stratum V2 not only strengthens the technological foundations of mining pools but also realigns them with the ideological core of Bitcoin’s decentralized vision. The protocol mitigates governance asymmetries by redistributing control over transaction selection from centralized pools to individual miners. Furthermore, its compatibility layer, implemented via the Translation Proxy, enables seamless interoperability between legacy Stratum V1 devices and the modernized V2 ecosystem, ensuring that adoption can progress without disrupting existing infrastructures.
Overall, this research validates Stratum V2 as a scalable, secure, and ethically aligned solution for the evolving needs of the Bitcoin mining ecosystem. Its architecture and reference implementation provide a robust basis for further innovation in mining protocol design, communication efficiency, and trustless coordination across distributed computational environments.
6.2. Future Work
Although Stratum V2 delivers substantial improvements over prior mining communication frameworks, several areas of research and development remain open for exploration. Future work will focus on extending the current findings into three major domains: protocol evolution, cryptographic optimization, and decentralized governance models.
6.2.1. 1) Protocol Evolution and Stratum V3 Development
The continued evolution of mining infrastructures will likely necessitate the design of Stratum V3, emphasizing greater modularity and cross-compatibility with emerging consensus algorithms. Future research could focus on integrating adaptive message compression, dynamic difficulty adjustment, and protocol self-healing mechanisms to ensure resilience under extreme network volatility. Furthermore, developing an interoperable schema for non-Bitcoin networks (e.g., Litecoin, Kaspa, or Monero) could expand the relevance of the Stratum architecture to multi-chain environments.
6.2.2. 2) Cryptographic and Performance Optimization
Although Stratum V2’s AES-GCM encryption provides strong security guarantees, it incurs a minor computational cost for low-powered ASICs. Future optimization could explore hybrid cryptographic schemes—such as ChaCha20-Poly1305 or lightweight AEAD variants—to reduce encryption latency while maintaining equivalent security. Additionally, integrating hardware-assisted encryption modules directly into ASIC firmware may further minimize overhead. Research into energy-efficient message framing and compressed transaction encoding could also enhance sustainability by reducing the carbon footprint of large-scale mining farms.
6.2.3. 3) Decentralized Governance and Fairness Frameworks
Decentralization remains a dynamic and multi-faceted challenge. While Stratum V2 reintroduces miner-controlled block template generation, a standardized governance model for decentralized mining pools is still absent. Future work could explore distributed consensus mechanisms among miners to coordinate transaction inclusion, reduce orphaned block frequency, and ensure fairness in reward distribution. Incorporating smart contract–based governance layers, potentially through sidechains or Layer-2 protocols, could further strengthen transparency and accountability in mining operations.
6.2.4. 4) AI-Driven Optimization and Predictive Analytics
Integrating artificial intelligence into mining protocol management represents an emerging frontier. Machine learning models could be utilized to dynamically adjust job distribution, predict pool-level failures, and optimize bandwidth allocation based on real-time network metrics. Reinforcement learning strategies could also assist in autonomous parameter tuning, ensuring continuous efficiency improvement as network conditions fluctuate.
6.2.5. 5) Energy Efficiency and Environmental Impact
Given the increasing scrutiny of Bitcoin mining’s energy consumption, future implementations of Stratum protocols should incorporate mechanisms for energy optimization. Adaptive throttling algorithms, intelligent workload scheduling, and renewable-energy-aware pool coordination could significantly reduce energy waste. Empirical studies on the energy-to-efficiency trade-off across various encryption algorithms would also contribute to more sustainable mining infrastructure design.
6.2.6. 6) Standardization and Ecosystem Integration
For widespread adoption, it is essential to establish industry-wide standards and formal protocol specifications validated by the Bitcoin developer community. Collaboration between major pool operators, ASIC manufacturers, and protocol engineers will be key in defining cross-platform interoperability guidelines. Such efforts will ensure that Stratum V2 becomes not merely a performance upgrade but a foundational layer for future decentralized computational systems.
6.3. Concluding Remarks
In conclusion, Stratum V2 signifies a major leap forward in the evolution of Bitcoin mining infrastructure. It bridges the long-standing gap between performance and decentralization, offering a robust framework for secure, efficient, and transparent mining operations. The findings of this study substantiate Stratum V2’s readiness for mainstream deployment and its capacity to serve as a blueprint for subsequent protocol generations. As Bitcoin continues to expand in scale and complexity, innovations like Stratum V2 will play an essential role in safeguarding both the technical integrity and philosophical ethos of decentralized digital economies.
References
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. [Google Scholar]
- M0mchil. The Getwork Protocol for Bitcoin Mining. Bitcoin Wiki 2010. [Google Scholar]
- Antonopoulos, A.M. Mastering Bitcoin: Unlocking Digital Cryptocurrencies. O’Reilly Media 2014. [Google Scholar]
- Back, A. Hashcash - A Denial of Service Counter-Measure. Hashcash.org 2002. [Google Scholar]
- M0mchil. POCLbm: OpenCL GPU Miner and Getwork Protocol Implementation. 2010. [Google Scholar]
- Dashjr, L. Rollntime Extension for Getwork. Bitcoin Talk Forum 2010. [Google Scholar]
- Dashjr, L.; Andresen, G. BIP 22: getblocktemplate—Block Proposal Mechanism. 2012. [Google Scholar]
- Dashjr, L.; Andresen, G. BIP 23: getblocktemplate—Pooled Mining Extensions. 2012. [Google Scholar]
- Dashjr, L. Getblocktemplate (GBT) and Its Role in Bitcoin Mining Decentralization. 2012. [Google Scholar]
- Developers, B.C. Mining and JSON-RPC Integration in Bitcoin Core. 2012. [Google Scholar]
- Yeow, J.; Tang, M. A Comparative Study of Bitcoin Mining APIs and Efficiency Trade-offs. 2020. [Google Scholar]
- Rosenfeld, M. Analysis of Bitcoin Pooled Mining Reward Systems. arXiv 2011, arXiv:1112.4980. [Google Scholar] [CrossRef]
- Palatinus, M. The Stratum Protocol: A Lightweight TCP Framework for Bitcoin Mining. 2012. [Google Scholar]
- Team, B.M. Stratum V1 Protocol Documentation. Braiins OS Documentation 2013. [Google Scholar]
- Systems, B. Stratum Mining Protocol Technical Overview. Stratum Protocol Wiki 2014. [Google Scholar]
- Liu, J.; Zhang, H.; Xu, Y. Hijacking Hashrate: Attacks on the Stratum Mining Protocol. BlackHat Asia Conference Proceedings 2021. [Google Scholar]
- Lamport, L.; Shostak, R.; Pease, M. The Byzantine Generals Problem. ACM Transactions on Programming Languages and Systems 1982, 4, 382–401. [Google Scholar] [CrossRef]
- Ammous, S. The Bitcoin Standard: The Decentralized Alternative to Central Banking. Wiley Economics Series 2018. [Google Scholar]
- Rybarczyk, T.; Novak, F. Security and Efficiency Optimization in Modern Bitcoin Mining Protocols. Journal of Cryptographic Engineering 2022. [Google Scholar]
- Moravec, P.; Čapek, J.; Corallo, M. Stratum V2: A Next Generation Bitcoin Mining Protocol. Braiins Research Whitepaper 2019. [Google Scholar]
- Team, B. Braiins OS+ Implementation of Stratum V2 for ASIC Mining Devices. Braiins OS+ Technical Bulletin 2020. [Google Scholar]
- Research, G.D. The Future of Bitcoin Mining Communication: Evaluating Stratum V2 Adoption. Galaxy Mining Reports 2022. [Google Scholar]
- Team, B.E. Performance Optimization and Modular Design in Stratum V2. Braiins Protocol Journal 2023. [Google Scholar]
- Initiative, B.O.S. Stratum Reference Implementation (SRI): Architecture and Deployment. 2020. [Google Scholar]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).