1. Introduction
The 5th Generation Mobile Network (5G) offers a stable, fast, reliable, and secure foundational network for digital information transformation across various domains. By integrating innovative technologies such as Software-Defined Network (SDN), Network Function Virtualization (NFV), and Cloud-Native, 5G achieves high flexibility with deployment customization and scalability [
1]. It demonstrates unprecedented capabilities in high-speed data transmission, low-latency communication, and massive device connectivity, thereby driving innovations and developments in applications such as the Internet of things (IoT), industrial Internet, smart cities, augmented reality, and virtual reality.
The 5G core network (5GC) is designed based on a "cloud-native" Service-based Architecture (SBA). In 5G SBA core network, Network Elements (NEs) evolve into software-based, modular Network Functions (NFs) composed of multiple microservices. NFs communicate with each other via Service-based Interfaces (SBIs), combined in a bus-like topology. Each NF supports providing services to other NFs, enhancing load balance, fault tolerance, scalability, and maintainability of the 5GC [
2].
However, while the 5GC adopts SBA to enhance network capacity and service quality, it also exposes a large attack surface compared to past networks, inevitably facing many new security and privacy challenges [
3]. First, the centralized management of NFs presents drawbacks such as single points of failure and performance bottlenecks. The centralized Network Repository Function (NRF) in the 5GC is responsible for the registration, updating, deregistration, and authorization of NFs, carrying a significant communication load. If the NRF is broken through, the service interaction of the entire core network is greatly affected. Second, during the service authorization process, there are vulnerabilities in access control and identity authentication. Attackers can impersonate NF service consumers, hijack access tokens, and then carry out replay attacks and MITM attacks, achieving unauthorized access to services and malicious service invocation. Third, insufficient privacy protection measures for NFs could lead to such risks as core network service and resource leakage, exposure of network topology, and even theft of user-sensitive data.
Current research on the security of the 5GC mainly focuses on the security of key 5G technologies and improvements in UE authentication and key agreement [
4,
5]. However, research on NF management and service authorization security is relatively scarce. Issues such as the single point of failure of NRF, cross-domain service authorization security, and NF privacy protection urgently need to be addressed. The security and reliability of the 5GC are fundamental to ensuring the stable operation of 5G network services.
To address the security and privacy issues in 5G NF services management, in this paper, we propose 5G-DAuth, a decentralized secure and trustworthy NF service management scheme for 5G networks. 5G-DAuth offers trusted registration, authentication, authorization, and access control for cross-domain NF services sharing, built on a blockchain and an off-chain TEE-based security management platform. 5G-DAuth leverages the consortium blockchain to build a cross-domain authorization network among 5G public land mobile networks (PLMNs), and use smart contracts for NF management and service authorization. The computational tasks of smart contracts are offloaded to off-chain TEEs based on Intel SGX, achieving secure and efficient cross-domain NF service authorization and access control while supporting NF data privacy protection. Our contributions can be summarized as follows:
- •
We propose 5G-DAuth, a cross-domain 5G NF service authorization scheme based on a consortium blockchain and off-chain TEE. Our scheme constructs the consortium blockchain for NF communication between multiple PLMNs, utilizing smart contracts to provide NF management and service authorization, thereby addressing the single point of failure of NRF.
- •
We design an off-chain TEE based on Intel SGX to reduce block synchronization waiting time, enhance the computational efficiency of smart contracts, and ensure security and privacy for both smart contracts and on-chain data.
- •
We conduct serious security analysis and performance evaluation on 5G-DAuth to demonstrate that it meets security and privacy protection requirements while offering certain performance advantages.
The rest of this paper is organized as follows. Section II reviews related works with comparison. Section III presents the system model and security model of 5G-DAuth. Section IV describes the details of the 5G-DAuth design. Section V provides security analysis and performance evaluation. Finally, Section VI concludes the whole paper.
4. 5D-DAuth Design
In this section, we present a detailed description of 5G-DAuth. We first give a design overview and then introduce the key steps of 5G-DAuth, specifically system initialization, NF management, service authorization, and service access.
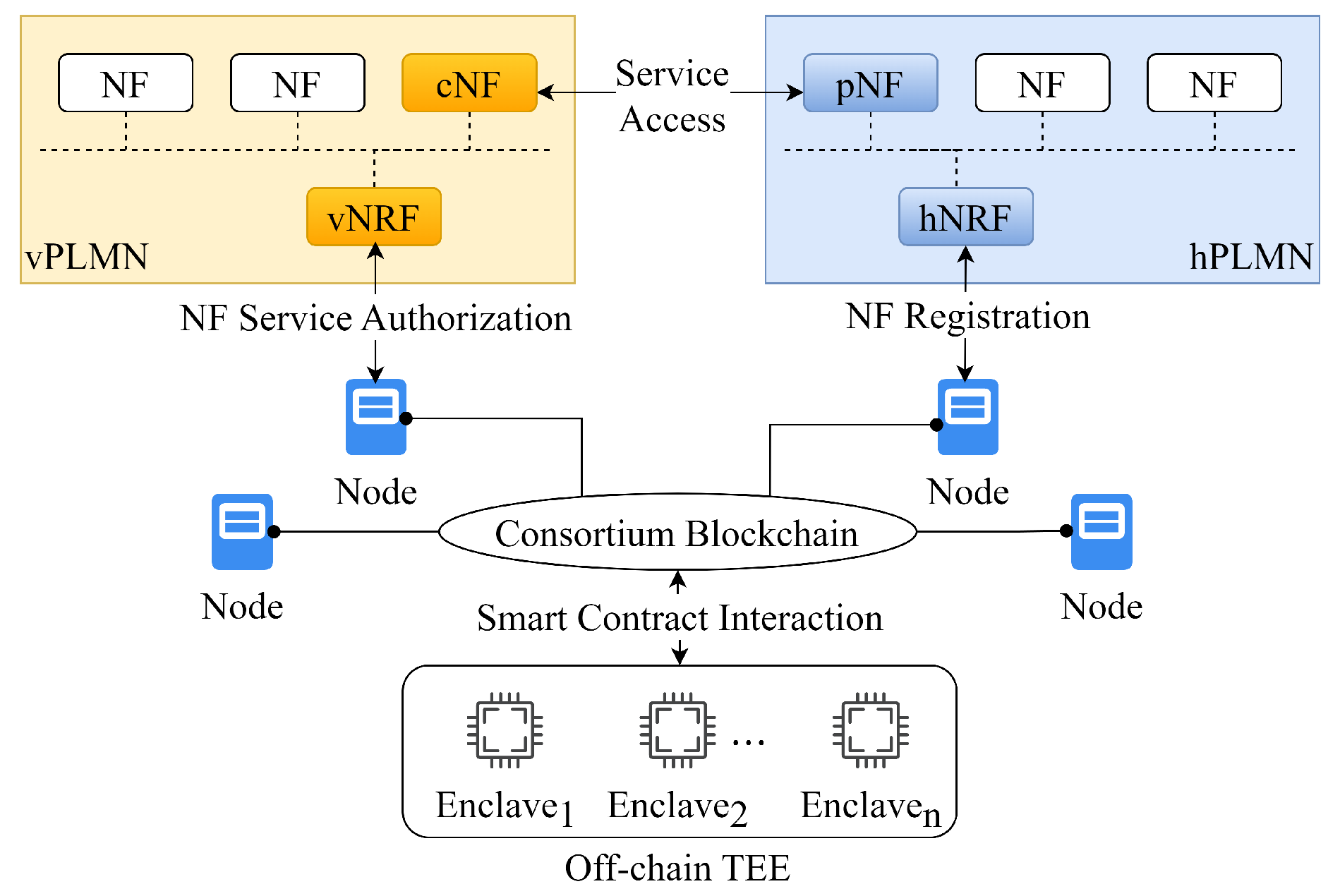
4.1. 5G-DAuth Overview
5G-DAuth is a decentralized network function service security management system that integrates consortium blockchain technology and off-chain TEEs within a 5G SBA core network. It leverages consortium blokchain and smart contract to construct a decentralized platform for cross-domain NF management and automatic service authorization and access control. Mobile operators or third-party service providers can deploy smart contracts on the blockchain to automate the processes of NF service registration, authentication, authorization, and access control. Additionally, 5G-DAuth maintains an off-chain TEE pool to execute these smart contracts and safeguard data off-chain. This approach ensures the confidentiality of NF profiles and policy information while reducing synchronization time and computational costs. With its well-thought-out design, 5G-DAuth eliminates the single point of failure associated with the NRF, protects the privacy of NF service information, and enhances the overall execution efficiency of the system.
4.2. System Setup
Consortium Blockchain Initialization: 5G-DAuth is composed of multiple PLMNs owned by different mobile operators. Each operator registers several nodes on a consortium blockchain. A subset of nodes invokes smart contracts, while others handle transaction packaging and block synchronization. Within each PLMN, an NRF is associated with one of the consortium blockchain nodes and responsible for invocating smart contracts on the blockchain as an external client. During the initialization phase, each NRF generates a public-private key pair (), which is used to sign smart contract transaction proposals and negotiate a session key with the associated consortium blockchain node. After the initialization of the consortium blockchain network, an on-chain smart contract M is deployed on the blockchain. M is responsible for creating off-chain enclaves and deploying NF management smart contracts. In the scenario of two PLMNs’ cross-domain service invocation, the consortium blockchain establishes a specific channel between the associated blockchain nodes of PLMNS and creates a private ledger for this channel. The configuration and service authorization information of NFs are recorded in this ledger.
Enclave Initialization and Smart Contract Deployment: PLMN sends the enclave creation and smart contract deployment requests to the associated consortium blockchain node via the NRF. The request includes the code of a smart contract and its hash value , as well as the public key of the NRF . The consortium blockchain node invokes M to generate a for the smart contract, initialize an enclave (i.e., Executor) within the off-chain TEE, and deploy the code of the smart contract into the enclave. The Executor generates an enclave identifier and an attestation report , as well as a session key and a public-private key pair (). After the enclave is initialized, it sends , , , and back to M. Subsequently, M stores the Enclave’s , , , and the smart contract’s and in the consortium blockchain ledger. The consortium blockchain node sends , , , , and to the NRF, enabling it to invoke the smart contract. The NRF subsequently decrypts the session key using its private key and uses to encrypt the messages between NRF and the enclave.
4.3. NF Management
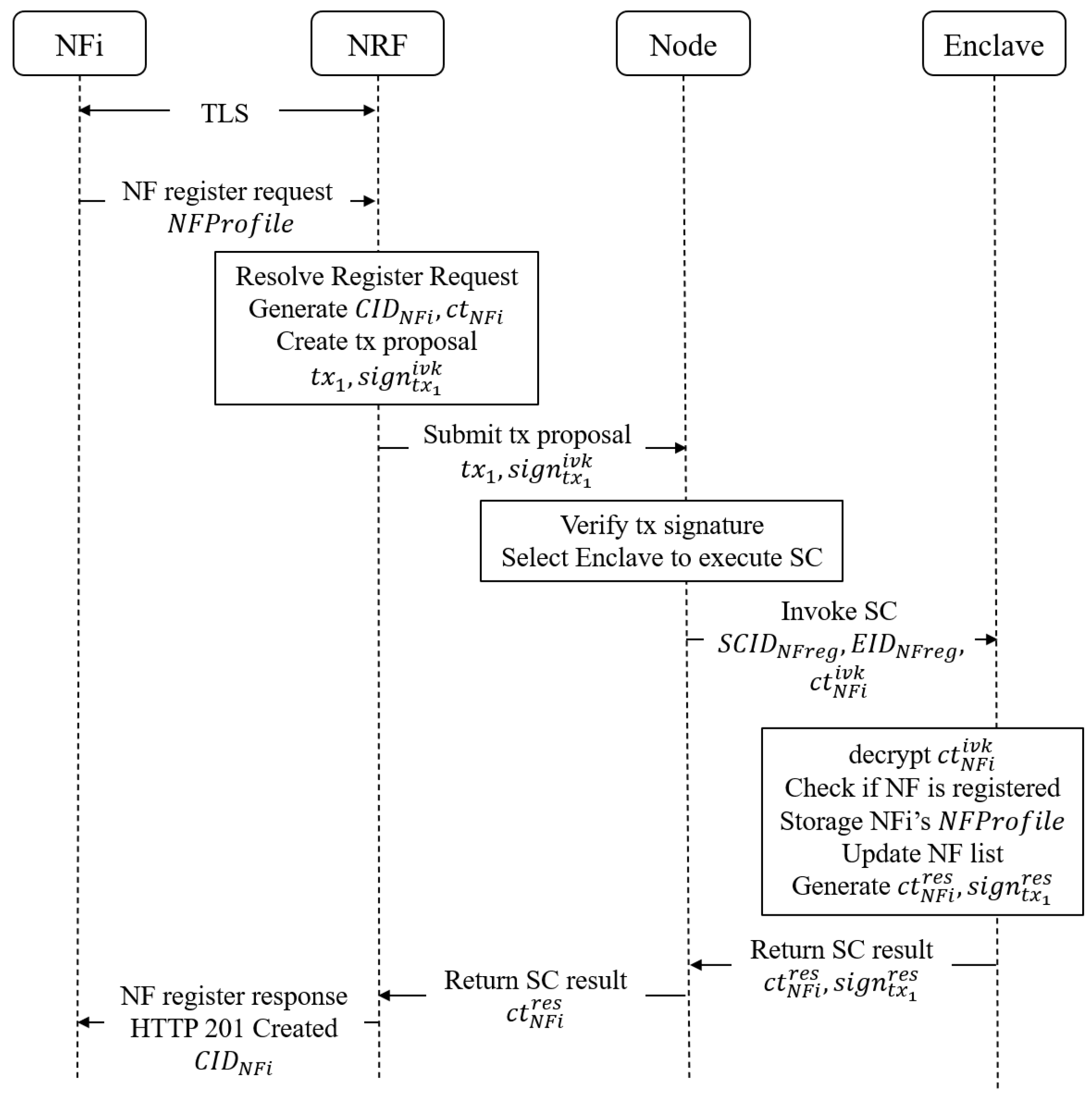
In the 5G-DAuth system, the management of the NF life cycle is facilitated through smart contracts under the oversight of the NRF. The NRF invokes smart contracts to implement the registration, updating, and deregistration of NFs. Before providing and consuming services, an NF first registers to the NRF by submitting NF configuration information
. The
is stored on the consortium blockchain, facilitating decentralized NF management and cross-domain NF service discovery. The detailed process of NF registration is illustrated in
Figure 2 and described as follows:
Step 1: NF sends registration request to NRF. Before initiating a registration request, a network function instance first engages in TLS mutual authentication with the NRF to establish a secure transport channel between and NRF. Subsequently, invokes the NRF’s service API Nnrf_NFManagement/nf-instances/nfinstanceID with a PUT request. The registration request message from carries data that constitutes the configuration information of the NF instance. The includes both standard and optional configurations. The standard configurations are attributes that must be submitted upon NF instance registration, such as NF instance ID , NF type , NF status , PLMN ID , FQDN or IP address, NF service set , and NF load information , among others. Optional configurations are properties that are customized for specific NF functionalities, such as the GUAMI in the AMF or the SMF region ID in the UPF.
Step 2: NRF invokes smart contracts to blockchain nodes. Upon receiving registration information from NF, NRF further processes the NF instance information. Firstly, NRF conducts a hash operation on the instance ID of to generate a hidden ID to conceal the identity of the registered NF. Subsequently, NRF encrypts using the session key between NRF and Enclave to obtain . Then, NRF constructs a transaction proposal for invoking the smart contract for NF registration. Then, NRF signs the transaction with NRF’s private key and sends the transaction proposal and transaction signature to the consortium blockchain nodes.
Step 3: Blockchain node invokes enclave to execute smart contract. Upon receiving the transaction proposal from NRF, consortium blockchain nodes first validate the signature using . Subsequently, they invoke the NF registration smart contract within Enclave based on and . The Enclave utilizes the session key to decrypt and obtain plaintext , parses its attributes, and performs further processing. It retrieves the and of the NF instance, encrypts using the Enclave’s sealing key , initiates a write request to the consortium blockchain, and stores the key-value pair (, ) in the consortium blockchain ledger. Additionally, a registered NF list for NF service discovery is maintained on the consortium blockchain. When a new NF is registered, a new entry is added to this list in the form of a key-value pair (, ) , encrypted using as well. Upon completion of the execution of the smart contract , the Enclave encrypts the execution result using to obtain , signs it using to obtain , and returns them to the consortium blockchain nodes.
Step 4: NF receives registration success response. The consortium blockchain nodes validate the signature of the ciphertext execution result using , return the ciphertext execution result to NRF, and perform transaction packaging and ledger synchronization between nodes. NRF decrypts the execution result using to obtain the registration status of , and then sends an HTTP 201 response to along with , informing of the successful registration.
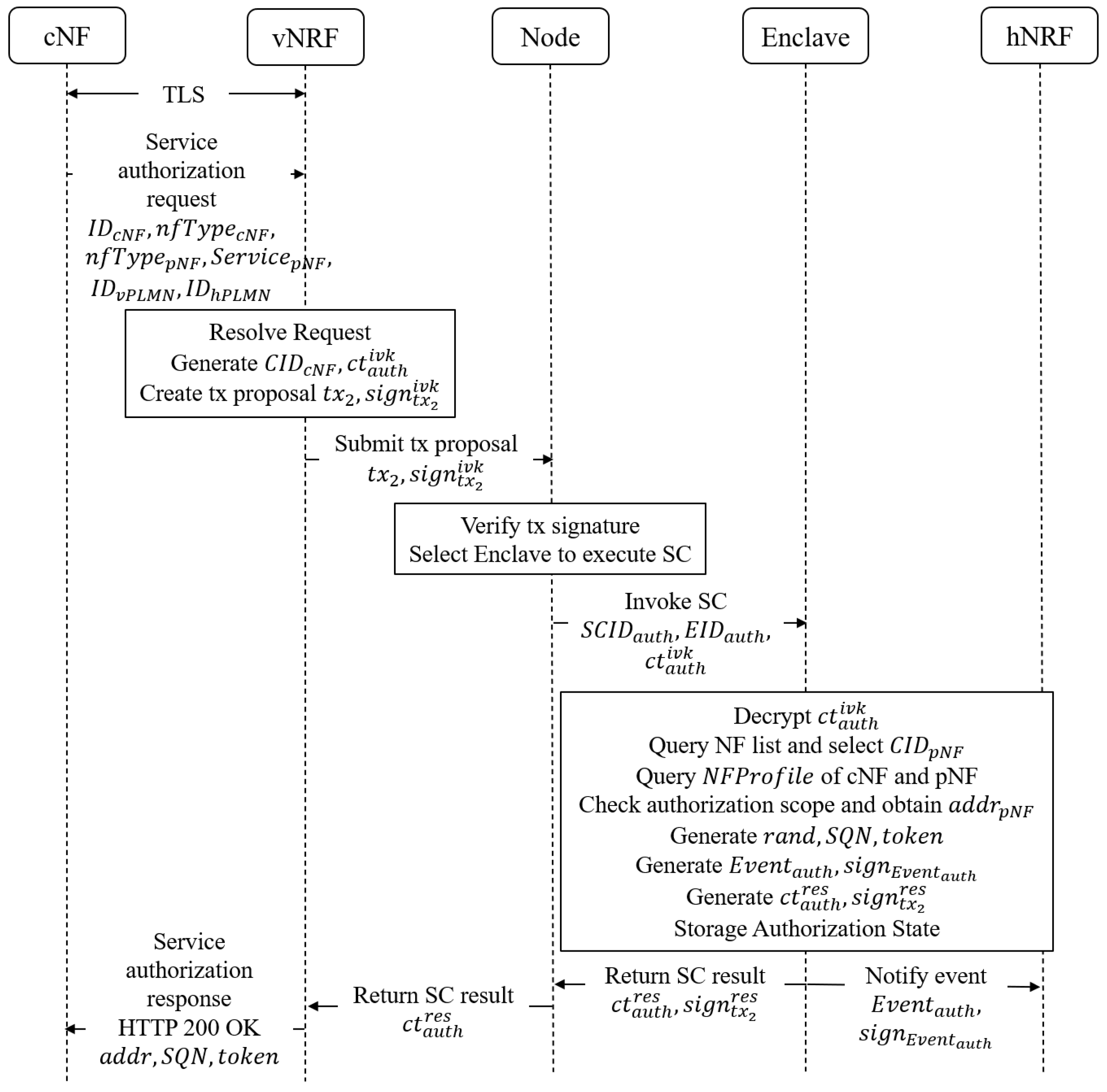
4.4. Service Authorization
When a cNF from vPLMN intends to access a service provided by a pNF in hPLMN, a service discovery and authorization request must be initiated for vNRF. The authorization operation is carried out by the smart contract
, which is responsible for service discovery and authorization. Based on the cNF request, the smart contract
queries the target service access address and issues the corresponding authorization token. The service authorization process is illustrated in
Figure 3.
Step 1: cNF initiates a service discovery and authorization request to vNRF. Firstly, cNF and vNRF establish a secure communication channel through TLS mutual authentication. Subsequently, cNF invokes the API Nnrf_AccessToken provided by vNRF, initiating a GET request. The request message includes the cNF instance ID, cNF type, vPLMN ID where cNF is located, target pNF type, target service type, and hPLMN ID where the pNF is located.
Step 2: vNRF initiates smart contract invocation to consortium blockchain nodes. Upon receiving the request from cNF, vNRF further processes the request. Firstly, it computes the for cNF, then encrypts the parameters of the service authorization request using the session key between vNRF and Enclave to obtain . Next, vNRF constructs a transaction proposal for invoking the authorization smart contract . Then, vNRF signs the transaction and sends the transaction proposal along with the signature to the consortium blockchain nodes.
Step 3: Consortium blockchain nodes invoke Enclave to execute smart contract. Upon receiving the transaction proposal from vNRF, the consortium blockchain nodes validate the signature of the transaction proposal. Then, they invoke the smart contract within Enclave . Enclave utilizes the session key to decrypt and obtain the service authorization request information from cNF. Firstly, Enclave searches for the registration status of cNF based on . If cNF is registered, the authorization process continues; otherwise, the authorization is aborted. Then, based on the pNF type , Enclave queries the NF registration list to select a suitable pNF in hPLMN and retrieve its . Subsequently, the Enclave queries the of pNF on the consortium blockchain based on . It extracts configuration information from including service name, service access address, service authorization scope, resource authorization scope, etc., and determines if the corresponding service can be provided to cNF within the authorization scope specified by the pNF. If cNF falls within the specified authorization scope of the pNF, Enclave generates a random number and a sequence number , and creates an access token for cNF. The attributes of the access token include the CID and type of cNF, the CID and type of pNF, the service provided by pNF, the expiration time of authorization, and the random number. The Enclave signs these attributes using the Enclave private key to obtain . Upon completion of the smart contract execution, the Enclave sends the access token , the target service access address , and the sequence number as the contract execution result. These are encrypted and signed, then sent to the consortium blockchain nodes. The authorization information is sealed using and stored on the consortium blockchain. Utilizing the smart contract event listening mechanism, an event is predefined to apply for service authorization to pNF in hPLMN and generate an access token. When this event is triggered during the smart contract execution, encrypted event notifications and signatures are generated and sent to the hPLMN consortium blockchain nodes subscribed to this event.
Step 4: cNF receives authorization success response. The consortium blockchain nodes validate the signature of the ciphertext execution result using , then send the ciphertext execution result to vNRF and perform transaction packaging and ledger synchronization between nodes. vNRF decrypts the ciphertext execution result using the session key , and sends the target service access address and access token to cNF. It informs cNF of the successful service authorization via an HTTP 200 response. Subsequently, cNF can initiate service access requests to pNF using the target service access address and access token.
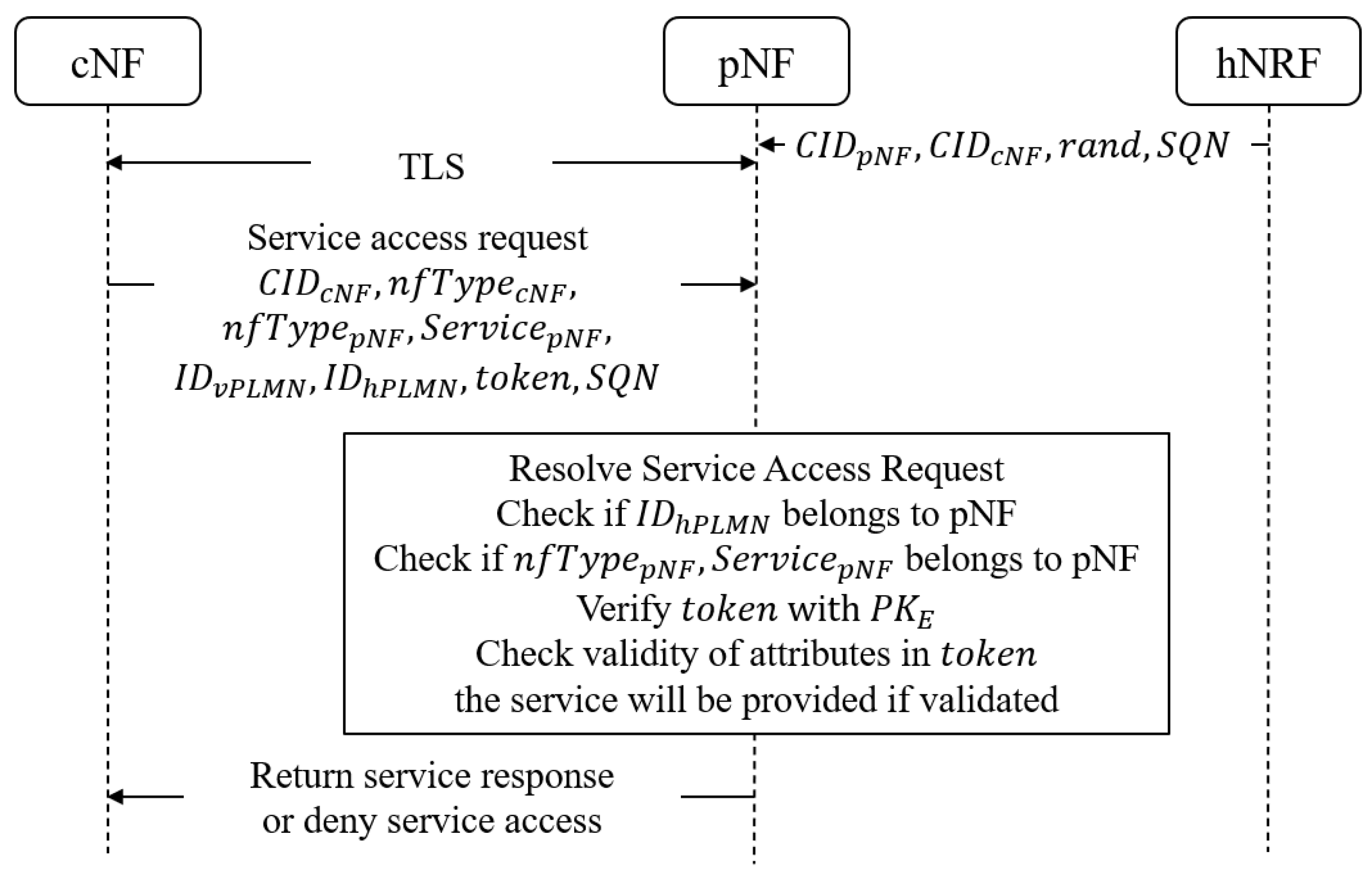
4.5. Service Access
After obtaining service authorization, cNF can initiate service access requests to the target service address of pNF while carrying an access token. Upon successful validation of the request by pNF, the corresponding service can be provided. During the service authorization phase, hNRF retrieves event notifications from the alliance chain nodes. Using
to decrypt the notification,
,
,
, and
are obtained. hNRF forwards
,
,
, and
to pNF, which stores them for subsequent access token verification during cNF service access. The NF service access process is illustrated in
Figure 4.
Step 1: cNF initiates service access request to pNF. cNF and pNF first establish TLS mutual authentication for eligibility verification. cNF initiates a service access request to the target service address of pNF. The request message includes the CID of cNF, cNF type, pNF type, target service type, vPLMN ID where cNF is located, hPLMN ID where pNF is located, access token, sequence number, and specific parameters required for invoking the service.
Step 2: pNF validates the service access request. Upon receiving the service invocation request from cNF, pNF utilizes the Enclave public key to verify the token. It extracts the attributes from the token and compares them with the cNF request parameters. If the service requested by cNF is in an authorized state, the random number and sequence number correspond one-to-one, and the access token is within its validity period, pNF executes the service operation and returns the service response to cNF. Subsequently, pNF increments .
Step 3: cNF obtains the service access result. pNF determines the legitimacy of cNF’s service access based on the access token, then decides whether to execute the service or refuse it. Upon receiving the response message from pNF, if cNF receives a service response, it proceeds with subsequent operations and updates . If cNF receives a refusal of service, it needs to request service authorization again.
5. Security and Performance Evaluation
This section provides a comprehensive security analysis, details the experiment design and implementation, and reports the performance evaluation results of f D5G-NFAu in terms of latency, throughput, CPU cost, and memory cost by comparing with a baseline.
5.1. Security Analysis
We analyze the security of 5G-DAuth from the perspective of security requirements and use AVISPA to formally verify the service authorization protocol.
Mutual Authentication: During the system initialization phase, public and private keys and digital certificates are generated for NF, NRF, and the consortium blockchain nodes. At the beginning of communication, the TLS protocol is used to authenticate the identities of both parties.
Confidentiality and Integrity: The communications between NFs and between NFs and NRF are both encrypted with a session key generated after identity authentication through the TLS protocol, ensuring secure and reliable transmission. For the communication between NRF and the consortium blockchain nodes, transaction proposals sent by NRF are signed with , allowing the consortium blockchain nodes to verify that the transactions originated from the correct sender. The smart contract invocation information sent by NRF is encrypted using the session key negotiated during the Enclave initialization.
Privacy Protection: On the data privacy protection level, the data sealing function provided by SGX is used to achieve encrypted storage of NF configuration information and service authorization information in the consortium blockchain ledger, ensuring that only authenticated Enclaves can decrypt the data, thus preventing unauthorized access to NF data. On the identity privacy protection level, before registration, the pNF of hPLMN generates a concealed identity identifier through hNRF, ensuring that when the cNF of vPLMN accesses services and authorizations, it only obtains anonymized pNF information. This prevents attackers from reconstructing the network topology through enumeration or other means.
Access Control Security: During the service authorization phase, the smart contracts check the registration status of both cNF and pNF, verify cNF request information against the service provision scope of pNF, specify the authorization expiration time, sign the access token with the Enclave’s private key , and encrypt the authorization information with for storage in the consortium blockchain ledger. This ensures strict permission control and traceability of authorization information for cNF service authorization. During the service access phase, cNF must provide an access token to request services, while pNF verifies the legitimacy of the service request using the cNF identity information and the access token. The token is verified with the Enclave’s public key to retrieve the service authorization scope, which is then compared with the cNF’s service request information to prevent unauthorized access by cNF.
Resisting Replay and MITM Attacks: After cNF requests service authorization, it obtains an access token signed by the Enclave’s private key, with a unique value added to the token to ensure its uniqueness. When cNF requests service access, it must carry the access token and synchronize with pNF for each request, preventing attackers from intercepting and replaying messages to gain unauthorized access. Additionally, since the communication between NFs uses the TLS protocol and SEPP-based cross-PLMN signaling transmission, the authenticity of identities and communication security are ensured. This prevents attackers from decrypting or tampering with communication messages during NF service authorization and access processes, thereby mitigating MITM attacks.
Preventing Single Points of Failure: Leveraging the decentralized nature of the consortium blockchain, the NF management and service authorization functions of NRF are implemented via smart contracts on the consortium blockchain. This decentralization prevents service disruptions in NF registration or access token generation caused by NRF attacks or failures, thereby achieving decentralized cross-domain NF management and service authorization.
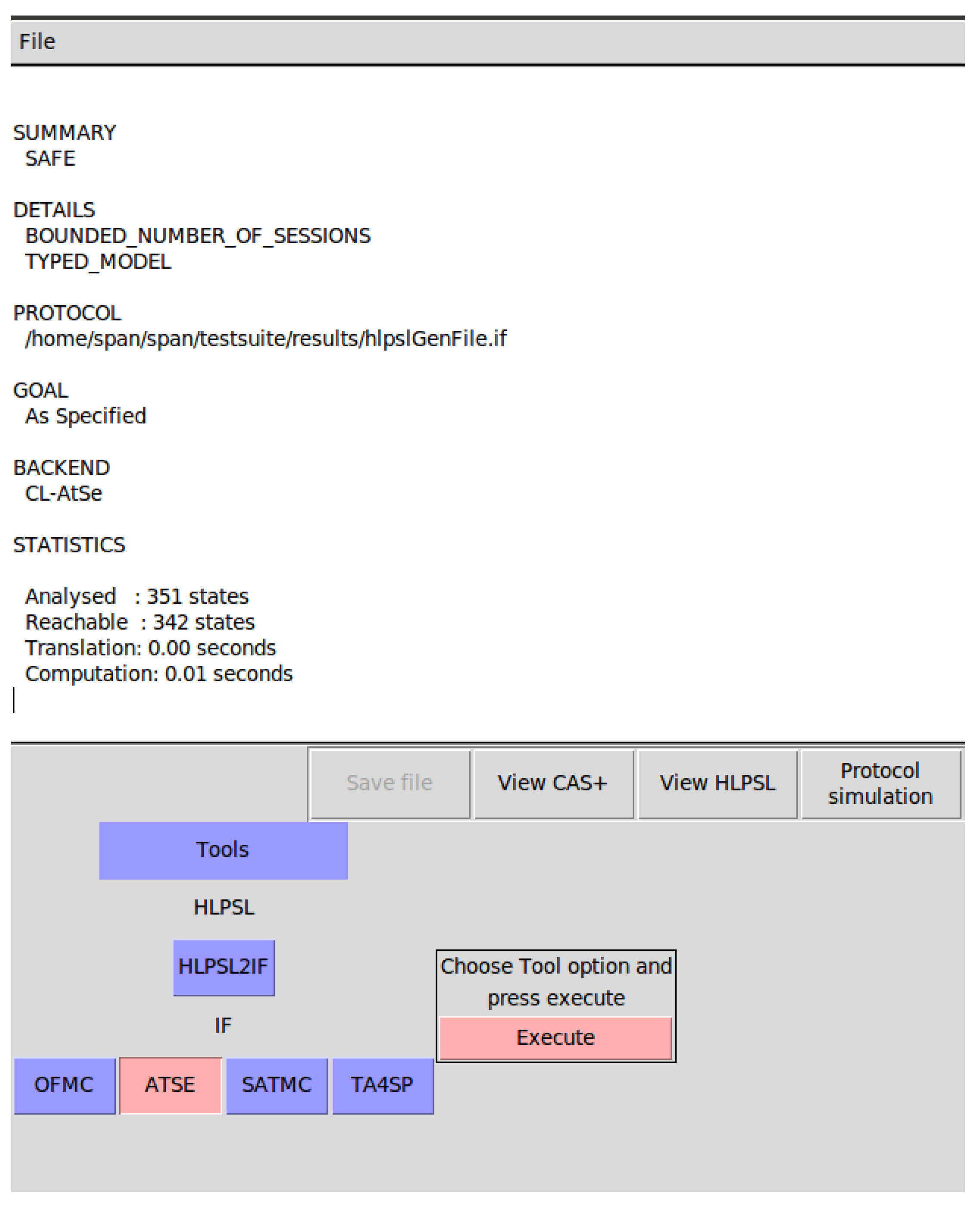
We utilize AVISPA for the formal analysis of the NF service authorization protocol [
16]. The protocol is modeled based on the Dolev-Yao model, and the verification result confirms that the NF service authorization process meets the specified security requirements. The formal verification result is shown in
Figure 5.
5.2. Experimental Setup
Experiment Environment: 5G-DAuth utilizes the Hyperledger Fabric as the consortium blockchain, deploying relevant Enclaves using drivers and SDK provided by Intel SGX, and implementing the system on the Ubuntu Linux platform. Smart contracts for NF management and service authorization are developed using C++ and Intel SGX library functions. A Docker container is employed to construct a 5G SBA core network simulation environment, simulating NF communication across PLMNs based on the inter-container communication mechanism of Docker containers. 5G SBA network functions are developed using Go and GIN framework, with each PLMN containing both cNF and pNF. Following the specifications of the 3GPP standard, message transmission between network functions is based on the HTTP/2 protocol, while service interfaces are provided in the form of RESTful Open API, with message data structured in JSON format. The digital signature algorithm utilized in the experiment is 256-bit ECDSA, the hashing algorithm is SHA-256, and the symmetric encryption algorithm used for Enclave sealing is 128-bit AES-GCM.
Baseline Method: Due to the lack of relevant research on blockchain-based cross-domain NF service authorization schemes in the literature and industry, we construct a baseline scheme for NF service authorization based on consortium blockchain and on-chain TEE for performance evaluation and comparison. The NF service authorization mechanism of the baseline is implemented on FPC[
17]. By comparing with the baseline, we validate that applying off-chain smart contract TEE for cross-domain NF service authorization in 5G-DAuth has higher efficiency than the on-chain TEE solutions.
Evaluation Metrics: To evaluate the performance of the consortium blockchain with off-chain SGX for secure privacy protection, we compare 5G-DAuth with the on-chain TEE approach, mainly focusing on the latency and throughput of the consortium blockchain transactions. Additionally, we also compare 5G-DAuth with two other NF service authorization schemes based on access tokens proposed by Zhang [
8] and Zhu [
9]. The comparison includes the latency and resource utilization (CPU and memory), and security performance of access token generation and validation.
5.3. Experimental Results
This section details the prototype implementation of 5G-DAuth and presents its performance evaluation through experiments, focusing on the latency and throughput of various system operations, as well as the CPU and memory utilization under different volumes of token acquisition requests.
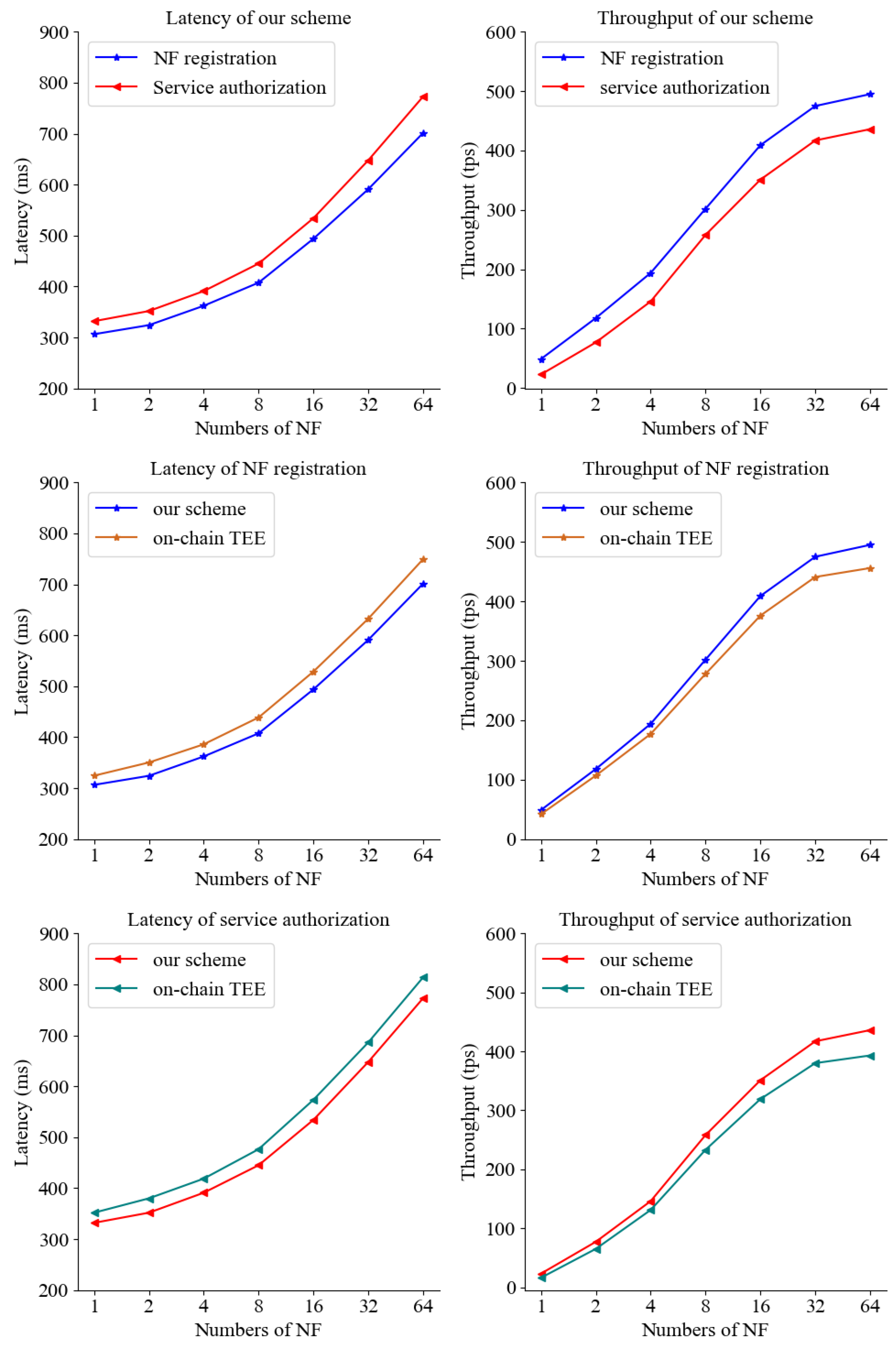
Figure 6 illustrates the variation trend of latency with the increase of NF number during the process of network function registration and service authorization. It can be observed from the figure that the latency gradually increases as the number of NFs increases. The numbers of read and write operations on the state data of the consortium blockchain ledger involved in the smart contracts for NF registration and service authorization, as well as the specific computations, vary. During the execution process of smart contracts, the state data that needs to be written is encrypted using the Enclave sealing key
. In the NF registration smart contract, there is one read operation and two write operations on the state database. Firstly, it checks whether the NF instance has been registered based on
and
. If the NF instance is not registered, it writes the NF configuration information into the state database and appends a
record to the NF registration list. In the service authorization smart contract execution process, there are two read operations and one write operation on the state database, as well as signature computations and event notification generation. Firstly, it searches the NF registration list based on
and selects a suitable
. It retrieves pNF configuration information and generates an access token signed with the Enclave private key based on the authorization request parameters and the service authorization scope in the pNF configuration information. Then it stores the authorization information in the consortium blockchain ledger and generates an authorization event notification to hNRF.
5G-DAuth and the baseline with on-chain TEEs have the same processes of network function registration and service authorization. It can be observed that 5G-DAuth has a lower time overhead compared to the baseline. The main reason is that 5G-DAuth moves the execution of smart contracts to off-chain TEE, where they run within Enclaves. By providing authentication reports from the Enclaves and the signatures on the execution results of smart contracts, the endorsing nodes can trust the execution results of off-chain TEE. This reduces the time overhead caused by the need for multiple endorsing nodes to execute smart contracts, as in the baseline.
The variation trend of throughput with the increase of the number of NFs during the process of network function registration and service authorization is shown in
Figure 6. As the number of NFs increases, the throughput also increases, and when the number of NFs reaches 16, the rate of increase in throughput begins to slow down. The concurrent processing capacity of NRF, as well as the number of blockchain nodes and Enclaves, can impose limitations on throughput scalability. However, by increasing the number of concurrent connections supported by NRF and augmenting the number of blockchain nodes and Enclaves, this constraint can be mitigated, leading to enhanced throughput.
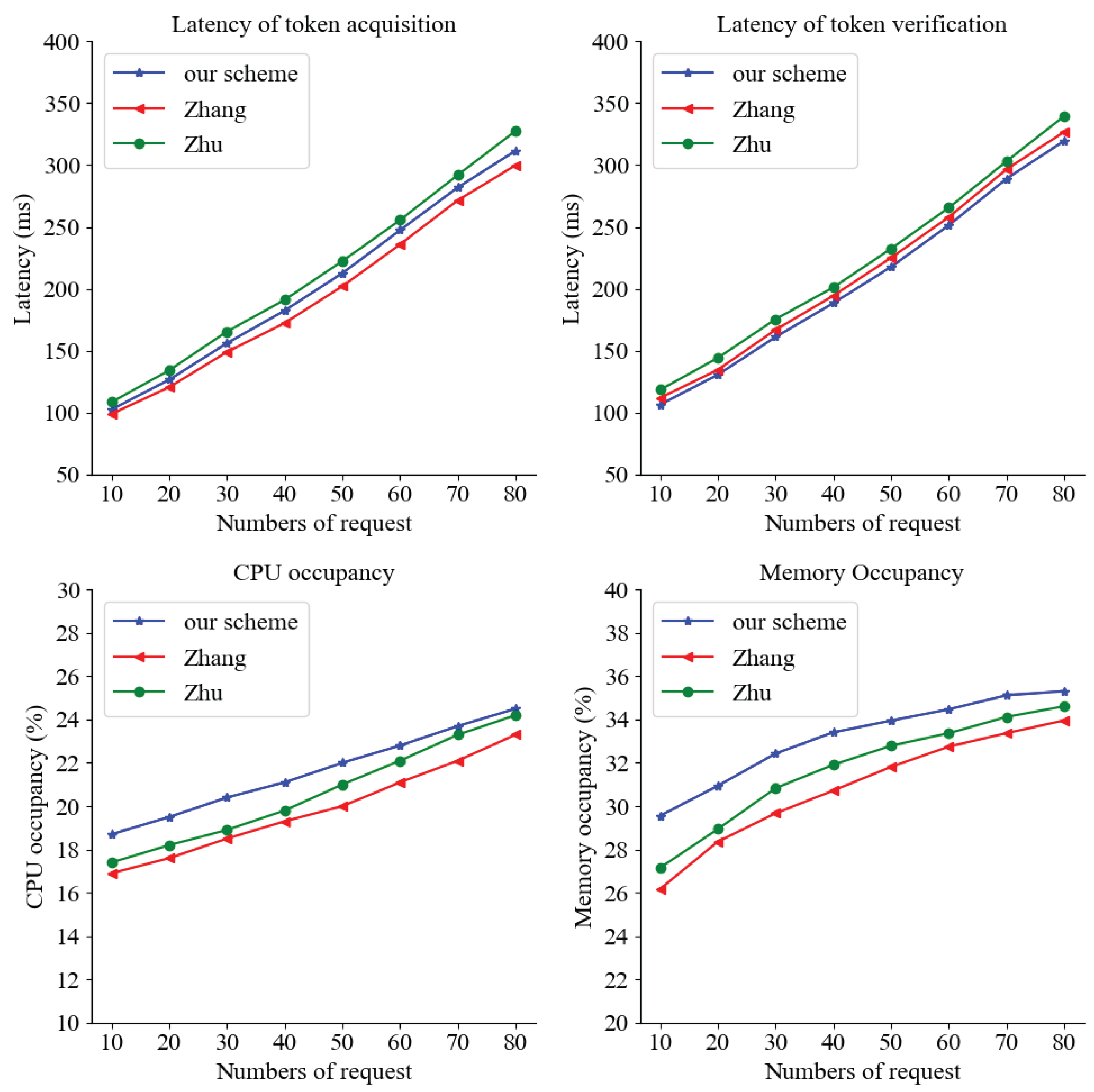
Specifically, we compare 5G-DAuth with two existing access token-based service authorization schemes proposed by Zhang [
8] and Zhu [
9]. The evaluation includes the token acquisition latency during the service authorization process, the token verification latency during service access, and the system CPU and memory utilization during service authorization execution. The results are shown in
Figure 7.
In 5G-DAuth, the token acquisition latency is lower than Zhu’s scheme, mainly because Zhu’s scheme introduces a business process table and a shared token repository. The NRF generates JSON web token (JWT) tokens after verifying whether the cNF service request complies with the business process relationship. Since 5G-DAuth utilizes Intel SGX to provide a trusted execution environment for token generation, there is a certain time overhead when decrypting the NF configuration information for privacy protection. Compared to Zhang’s scheme, which generates access tokens in a less secure execution environment, the latency of 5G-DAuth is higher. The token verification process during service access is performed by the pNF in all three schemes. The token verification latency of 5G-DAuth is superior to both Zhang’s and Zhu’s schemes. Zhang’s scheme requires two different hash function operations in addition to token verification, while Zhu’s scheme requires token verification, storage, and re-signing upon the receipt of the token by the pNF. In contrast, 5G-DAuth utilizes smart contract event notifications to allow the pNF to obtain partial attributes of cNF service authorization in advance, enabling direct token verification upon the receipt of the access token.
Regarding CPU and memory utilization, 5G-DAuth incurs additional CPU and memory consumption due to the context switching between the trusted and untrusted memory regions created by Intel SGX, as well as the memory swapping. While Intel SGX provides robust security and privacy protection capabilities, it comes with a performance cost to provide these security features. Despite the incurred performance overhead, experimental data indicates that the related overhead remains within the machine’s normal operational range.