Submitted:
26 November 2025
Posted:
28 November 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Evolution of Hybrid Cloud Security Challenges
1.2. Limitations of Perimeter-Based Security Models
1.3. Need for Zero Trust in Hybrid Cloud Environments
2. Literature Review
| Study/Article | Methodology | Key Features | Advantages | Limitations |
|---|---|---|---|---|
| "Implementing a Zero Trust Architecture in Hybrid Cloud Environments" (2024) | Case study and literature review | Focus on micro-segmentation, continuous monitoring, and policy enforcement in hybrid clouds | Enhanced security posture, operational efficiencies | Technical complexity, organizational resistance |
| "Advanced cloud security framework based on Zero Trust and Adaptive Deep Learning" (2025) | Integration of ZTA with adaptive deep learning (ADL) | Real-time anomaly detection, predictive threat analysis, adaptive response | Superior threat detection and adaptive control | Requires advanced ML infrastructure, integration challenges |
| "Roadmap to Zero Trust Implementation in Hybrid Clouds" (2025) | Conceptual framework and best practices | Continuous verification, least privilege access, risk assessment | Addresses compliance complexity, consistent policy enforcement | Implementation costs, learning curve for teams |
| "Zero Trust Architecture: A Systematic Literature Review" (2024) | Systematic review of ZTA research | Emphasis on "never trust, always verify," microservice architecture integration | Demonstrated security improvements in healthcare and other sectors | Performance trade-offs in some use cases |
3. Foundational Concepts of Zero Trust Security
3.1. Principle of Least Privilege
3.2. Continuous Authentication and Verification
3.3. Micro-Segmentation and Identity-Centric Control
3.4. Zero Trust Network Access (ZTNA) vs Traditional VPN
4. Hybrid Cloud Architecture and Attack Surface
4.1. Cloud-On-Prem Integration Challenges
4.2. Shared Responsibility Model and Security Boundaries
4.3. Common Threat Vectors Leading to Lateral Movement
5. Framework for Deploying Zero Trust in Hybrid Cloud
5.1. Identity and Access Management Integration
5.2. Policy Enforcement Points and Control Plane Design
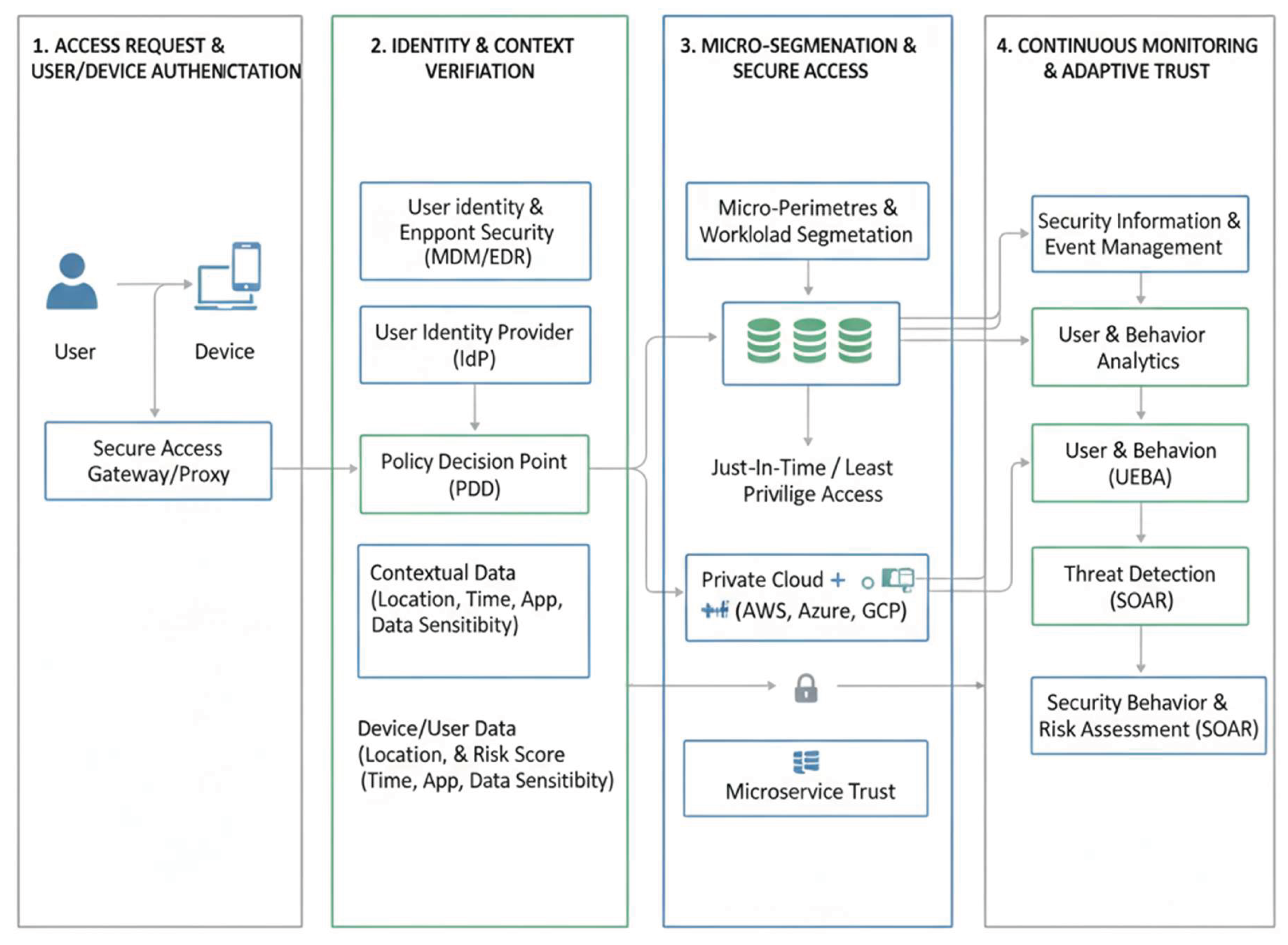
5.3. Role of Multi-Factor and Risk-Based Authentication
5.4. Encryption, Tokenization & Secure API Gateways
6. Continuous Verification Mechanisms
6.1. Behavioral Analytics and Access Scoring
6.2. Device Posture Validation and Endpoint Security
6.3. Session-Based Privilege Management
6.4. Real-Time Monitoring & Telemetry
7. Minimizing Lateral Movement through Micro-Segmentation
7.1. Segmentation Strategies for Hybrid Environments
7.2. Zero Trust Workload Isolation Models
7.3. Role of Software-Defined Perimeters (SDP)
7.4. Case Evaluation: Preventing East-West Attacks
8. Implementation of Zero Trust in Hybrid Cloud Environments
8.1. Assessment and Maturity Model
8.2. Policy-Driven Deployment Approach
8.3. Technology Stack and Tools for Zero Trust
8.4. Best Practices and Governance
- Continuous staff training and awareness
- Automated policy enforcement and audit trails
- Incident response integration with Zero Trust telemetry
- Periodic policy reviews aligned with evolving threats
9. Use Cases & Industry Applications
9.1. Financial Services and Compliance-Driven Clouds
9.2. Healthcare Data Protection Under Zero Trust
9.3. Secure DevOps and CI/CD Pipelines
9.4. Government Digital Infrastructure
10. Performance Evaluation and Security Metrics
10.1. Quantifying Access Control Effectiveness
| Metric | Description | Typical Value / Range | Purpose |
|---|---|---|---|
| Authorization Failure Rate | % of access requests denied due to lack of permission | 1% - 5% | Measures strictness and enforcement of least privilege principle |
| Access Review Frequency | How often access rights are reviewed/updated | Quarterly to Annually | Ensures access remains appropriate and reduces stale rights |
| Authentication Success Rate | % of successful authentications (MFA, Password, SSO) | 95% - 99.9% | Reflects reliability of authentication mechanisms |
| Access Revocation Success | % of access revocations applied effectively and timely | ≥ 95% | Metrics on how quickly unauthorized access is removed |
| Separation of Duties (SoD) | % compliance with SoD policies | 90% - 100% | Prevents conflicts of interest and unauthorized privilege escalation |
| Mean Time to Detect (MTTD) | Average time taken to detect unauthorized access | Hours to Days | Indicates responsiveness to detect policy violations |
| False Positive Rate (FPR) | % of legitimate access flagged as unauthorized | < 5% | Measures precision of access control monitoring systems |
| False Negative Rate (FNR) | % of unauthorized access that goes undetected | < 1% | Critical for identifying undetected security risks |
10.2. Measuring Reduction in Lateral Movement
| Metric | Description | Typical Range / Target | Purpose |
|---|---|---|---|
| Time to Detect (TTD) | Average time to detect lateral movement attempts | Minutes to hours | Measures speed of threat detection |
| Number of Lateral Movement Attempts | Count of detected lateral movement incidents | Lower is better | Tracks frequency of adversary lateral movement |
| Percentage Reduction in Lateral Movement | Percent decrease in lateral movement attempts after controls | 50%-90% reduction | Evaluates effectiveness of security improvements |
| Microsegmentation Coverage | % of network segmented to prevent lateral access | 80%-100% | Measures granularity of network segmentation |
| Mean Time to Contain (MTC) | Average time to contain/block lateral movement | Minutes to hours | Shows responsiveness in limiting attacker spread |
| Privilege Escalation Attempts | Number of detected privilege escalations enabling movement | Lower is better | Indicator sensitive to lateral movement vectors |
| Endpoint Detection Rate | % of lateral movement attempts detected on endpoints | ≥ 90% | Reflects strength of endpoint monitoring |
| False Positive Rate | % of false alerts classified as lateral movement | < 5% | Balances detection accuracy and alert noise |
10.3. Incident Response and Forensic KPIs
| KPI Name | Description | Typical Value / Target | Purpose |
|---|---|---|---|
| Mean Time to Detect (MTTD) | Average time from incident occurrence to detection | Minutes to hours | Measures how quickly incidents are identified |
| Mean Time to Acknowledge (MTTA) | Average time to acknowledge an incident alert | Minutes | Indicates responsiveness of the incident response team |
| Mean Time to Contain (MTTC) | Average time to halt incident spread or impact | Minutes to hours | Measures effectiveness in limiting damage |
| Mean Time to Resolve (MTTR) | Time from detection to full incident resolution | Hours to days | Indicates overall efficiency in incident handling |
| Incident Volume | Number of incidents within a period | Varies by organization | Measures workload and trends |
| First Response Time | Time from incident creation to initial response | Minutes | Reflects responsiveness at incident start |
| Reopen Rate | % of incidents reopened after being marked resolved | < 5% | Indicates quality of initial resolution |
| Incident Severity Distribution | Breakdown of incidents by severity (Critical, High, etc.) | N/A | Helps prioritize resources and improve planning |
| Forensic Investigation Time | Average time taken for forensic analysis | Hours to days | Measures depth and efficiency of incident investigation |
| Root Cause Identification Rate | % of incidents with identified root cause | > 90% | Indicates thoroughness of analysis and understanding |
| Post-Incident Review Rate | % of incidents with documented post-incident reviews | > 90% | Represents commitment to learning and process improvement |
| Cost per Incident | Average financial impact of incidents | Varies | Quantifies economic impact and helps prioritize investments |
11. Challenges & Limitations
11.1. Interoperability Between Cloud Providers
11.2. Legacy System Constraints
11.3. Overhead in Monitoring and Policy Enforcement
11.4. Cost, Skills, and Operational Complexity
12. Conclusion and Future Enhancements
References
- Arora, A. (2025). THE SIGNIFICANCE AND ROLE OF AI IN IMPROVING CLOUD SECURITY POSTURE FOR MODERN ENTERPRISES. Available at SSRN 5268192.
- Singh, B. (2025). Building Secure Software Faster with DevSecOps Principles, Practices, and Implementation Strategies. Practices, and Implementation Strategies (May 23, 2025), 23 May.
- Akat, G.B.; Magare, B.K. (2023). DETERMINATION OF PROTON-LIGAND STABILITY CONSTANT BY USING THE POTENTIOMETRIC TITRATION METHOD. MATERIAL SCIENCE, 22(07).
- Siddiqui, A.; Chand, K.; Shahi, N.C. (2021). Effect of process parameters on extraction of pectin from sweet lime peels. Journal of The Institution of Engineers (India): Series A, 102(2), 469-478.
- Kumar, J.D.S.; Subramanyam, M.V.; Kumar, A.S. (2024). Hybrid Sand Cat Swarm Optimization Algorithm-based reliable coverage optimization strategy for heterogeneous wireless sensor networks. International Journal of Information Technology, 1-19.
- Shinkar, A.R.; Joshi, D.; Praveen, R.V.S.; Rajesh, Y.; Singh, D. (2024, December). Intelligent solar energy harvesting and management in IoT nodes using deep self-organizing maps. In 2024 International Conference on Emerging Research in Computational Science (ICERCS) (pp. 1-6). IEEE.
- Vikram, A.V.; Arivalagan, S. (2017). Engineering properties on the sugar cane bagasse with sisal fibre reinforced concrete. International Journal of Applied Engineering Research, 12(24), 15142-15146.
- Reddy, D.N.; Venkateswararao, P.; Vani, M.S.; Pranathi, V.; Patil, A. (2025). HybridPPI: A Hybrid Machine Learning Framework for Protein-Protein Interaction Prediction. Indonesian Journal of Electrical Engineering and Informatics (IJEEI), 13(2).
- Atheeq, C.; Sultana, R.; Sabahath, S.A.; Mohammed, M.A.K. (2024). Advancing IoT Cybersecurity: adaptive threat identification with deep learning in Cyber-physical systems. Engineering, Technology & Applied Science Research, 14(2), 13559-13566.
- Arora, A. (2025). Zero Trust Architecture: Revolutionizing Cybersecurity for Modern Digital Environments. Available at SSRN 5268151.
- Mohammed Nabi Anwarbasha, G.T.; Chakrabarti, A.; Bahrami, A.; Venkatesan, V.; Vikram, A.S.V.; Subramanian, J.; Mahesh, V. (2023). Efficient finite element approach to four-variable power-law functionally graded plates. Buildings, 13(10), 2577.
- Kumar, N.; Kurkute, S.L.; Kalpana, V.; Karuppannan, A.; Praveen, R.V.S.; Mishra, S. (2024, August). Modelling and Evaluation of Li-ion Battery Performance Based on the Electric Vehicle Tiled Tests using Kalman Filter-GBDT Approach. In 2024 International Conference on Intelligent Algorithms for Computational Intelligence Systems (IACIS) (pp. 1-6). IEEE.
- Singh, H. (2025). Securing High-Stakes Digital Transactions: A Comprehensive Study on Cybersecurity and Data Privacy in Financial Institutions. Available at SSRN 5267850.
- Singh, B. (2025). Integrating Threat Modeling In Devsecops For Enhanced Application Security. Available at SSRN 5267976.
- Akat, G.B. (2023). Structural Analysis of Ni1-xZnxFe2O4 Ferrite System. MATERIAL SCIENCE, 22(05).
- Vijay Vikram, A.S.; Arivalagan, S. (2017). A short review on the sugarcane bagasse with sintered earth blocks of fiber reinforced concrete. Int J Civil Eng Technol, 8(6), 323-331.
- Yamuna, V.; Praveen, R.V.S.; Sathya, R.; Dhivva, M.; Lidiya, R.; Sowmiya, P. (2024, October). Integrating AI for Improved Brain Tumor Detection and Classification. In 2024 4th International Conference on Sustainable Expert Systems (ICSES) (pp. 1603-1609). IEEE.
- Sultana, R.; Ahmed, N.; Sattar, S.A. (2018). HADOOP based image compression and amassed approach for lossless images. Biomedical Research, 29(8), 1532-1542.
- Kumar, T.V. (2024). Enhanced Kubernetes Monitoring Through Distributed Event Processing.
- Boopathy, D.; Balaji, P. (2023). Effect of different plyometric training volume on selected motor fitness components and performance enhancement of soccer players. Ovidius University Annals, Series Physical Education and Sport/Science, Movement and Health, 23(2), 146-154.
- Rao, A.S.; Reddy, Y.J.; Navya, G.; Gurrapu, N.; Jeevan, J.; Sridhar, M.; Anand, D. High-performance sentiment classification of product reviews using GPU (parallel)-optimized ensembled methods.
- Arora, A. (2025). Securing Multi-Cloud Architectures using Advanced Cloud Security Management Tools. Available at SSRN 5268184.
- Singh, B. (2025). Mastering Oracle Database Security: Best Practices for Enterprise Protection. Available at SSRN 5267920.
- Lopez, S.; Sarada, V.; Praveen, R.V.S.; Pandey, A.; Khuntia, M.; Haralayya, D.B. (2024). Artificial intelligence challenges and role for sustainable education in india: Problems and prospects. Sandeep Lopez, Vani Sarada, RVS Praveen, Anita Pandey, Monalisa Khuntia, Bhadrappa Haralayya (2024) Artificial Intelligence Challenges and Role for Sustainable Education in India: Problems and Prospects. Library Progress International, 44(3), 18261-18271.
- Akat, G.B. (2022). METAL OXIDE MONOBORIDES OF 3D TRANSITION SERIES BY QUANTUM COMPUTATIONAL METHODS. MATERIAL SCIENCE, 21(06).
- Kumar, T.V. (2019). Cloud-Based Core Banking Systems Using Microservices Architecture.
- Kumar, J.D.S.; Subramanyam, M.V.; Kumar, A.P.S. (2023). Hybrid Chameleon Search and Remora Optimization Algorithm-based Dynamic Heterogeneous load balancing clustering protocol for extending the lifetime of wireless sensor networks. International Journal of Communication Systems, 36(17), e5609.
- Arora, A. (2025). Analyzing Best Practices and Strategies for Encrypting Data at Rest (Stored) and Data in Transit (Transmitted) in Cloud Environments. Available at SSRN 5268190.
- Sharma, S.; Vij, S.; Praveen, R.V.S.; Srinivasan, S.; Yadav, D.K.; VS; RK (2024, October). Stress Prediction in Higher Education Students Using Psychometric Assessments and AOA-CNN-XGBoost Models. In 2024 4th International Conference on Sustainable Expert Systems (ICSES) (pp. 1631-1636). IEEE.
- Arora, A. (2025). Transforming Cybersecurity Threat Detection and Prevention Systems using Artificial Intelligence. Available at SSRN 5268166.
- Nizamuddin, M.K.; Raziuddin, S.; Farheen, M.; Atheeq, C.; Sultana, R. (2024). An MLP-CNN Model for Real-time Health Monitoring and Intervention. Engineering, Technology & Applied Science Research, 14(4), 15553-15558.
- Arora, A. (2025). Evaluating Ethical Challenges in Generative AI Development and Responsible Usage Guidelines. Available at SSRN 5268196.
- Kamatchi, S.; Preethi, S.; Kumar, K.S.; Reddy, D.N.; Karthick, S. (2025, May). Multi-Objective Genetic Algorithm Optimised Convolutional Neural Networks for Improved Pancreatic Cancer Detection. In 2025 3rd International Conference on Data Science and Information System (ICDSIS) (pp. 1-7). IEEE.
- Sivakumar, S.; Prakash, R.; Srividhya, S.; Vikram, A.V. (2023). A novel analytical evaluation of the laboratory-measured mechanical properties of lightweight concrete. Structural engineering and mechanics: An international journal, 87(3), 221-229.
- Praveen, R.V.S.; Hemavathi, U.; Sathya, R.; Siddiq, A.A.; Sanjay, M.G.; Gowdish, S. (2024, October). AI Powered Plant Identification and Plant Disease Classification System. In 2024 4th International Conference on Sustainable Expert Systems (ICSES) (pp. 1610-1616). IEEE.
- Akat, G.B. (2022). OPTICAL AND ELECTRICAL STUDY OF SODIUM ZINC PHOSPHATE GLASS. MATERIAL SCIENCE, 21(05).
- Singh, B. (2025). Oracle Database Vault: Advanced Features for Regulatory Compliance and Control. Available at SSRN 5267938.
- Kumar, T.V. (2018). Event-Driven App Design for High-Concurrency Microservices.
- Arora, A. (2025). Integrating Dev-Sec-Ops Practices to Strengthen Cloud Security in Agile Development Environments. Available at SSRN 5268194.
- Singh, B. (2025). Integrating Security Seamlessly into DevOps Development Pipelines through DevSecOpsA Holistic Approach to Secure Software Delivery. Available at SSRN 5267955.
- Kumar, T.V. (2016). Layered App Security Architecture for Protecting Sensitive Data.
- Charanya, J.; Sureshkumar, T.; Kavitha, V.; Nivetha, I.; Pradeep, S.D.; Ajay, C. (2024, June). Customer Churn Prediction Analysis for Retention Using Ensemble Learning. In 2024 15th International Conference on Computing Communication and Networking Technologies (ICCCNT) (pp. 1-10). IEEE.
- Nimma, D.; Rao, P.L.; Ramesh, J.V.N.; Dahan, F.; Reddy, D.N.; Selvakumar, V.; Jangir, P. (2025). Reinforcement Learning-Based Integrated Risk Aware Dynamic Treatment Strategy for Consumer-Centric Next-Gen Healthcare. IEEE Transactions on Consumer Electronics.
- Arora, A. (2025). The Future of Cybersecurity: Trends and Innovations Shaping Tomorrow's Threat Landscape. Available at SSRN 5268161.
- Akat, G.B. (2022). STRUCTURAL AND MAGNETIC STUDY OF CHROMIUM FERRITE NANOPARTICLES. MATERIAL SCIENCE, 21(03).
- Singh, H. (2025). The Role of Multi-Factor Authentication and Encryption in Securing Data Access of Cloud Resources in a Multitenant Environment. Available at SSRN 5267886.
- Raja, M.W.; Nirmala, D.K. (2016). Agile development methods for online training courses web application development. International Journal of Applied Engineering Research ISSN, 0973-4562.
- Anuprathibha, T.; Praveen, R.V.S.; Sukumar, P.; Suganthi, G.; Ravichandran, T. (2024, October). Enhancing Fake Review Detection: A Hierarchical Graph Attention Network Approach Using Text and Ratings. In 2024 Global Conference on Communications and Information Technologies (GCCIT) (pp. 1-5). IEEE.
- Jeyaprabha, B.; Sundar, C. (2021). The mediating effect of e-satisfaction on e-service quality and e-loyalty link in securities brokerage industry. Revista Geintec-gestao Inovacao E Tecnologias, 11(2), 931-940.
- Arora, A. (2025). Comprehensive Cloud Security Strategies for Protecting Sensitive Data in Hybrid Cloud Environments.
- Sultana, R.; Ahmed, N.; Basha, S.M. (2011). Advanced Fractal Image Coding Based on the Quadtree. Computer Engineering and Intelligent Systems, 2 3, 129, 136.
- Singh, H. (2025). Cybersecurity for Smart Cities Protecting Infrastructure in the Era of Digitalization. Available at SSRN 5267856.
- Kemmannu, P.K.; Praveen, R.V.S.; Banupriya, V. (2024, December). Enhancing Sustainable Agriculture Through Smart Architecture: An Adaptive Neuro-Fuzzy Inference System with XGBoost Model. In 2024 International Conference on Sustainable Communication Networks and Application (ICSCNA) (pp. 724-730). IEEE.
- Singh, B. (2017). Enhancing Real-Time Database Security Monitoring Capabilities Using Artificial Intelligence. International Journal of Current Engineering and Scientific Research (IJCESR).
- Singh, H. (2025). STRATEGIES TO BALANCE SCALABILITY AND SECURITY IN CLOUD-NATIVE APPLICATION DEVELOPMENT. Available at SSRN 5267890.
- RAJA; MW; PUSHPAVALLI; DM; BALAMURUGAN; DM; SARANYA; K (2025). ENHANCED MED-CHAIN SECURITY FOR PROTECTING DIABETIC HEALTHCARE DATA IN DECENTRALIZED HEALTHCARE ENVIRONMENT BASED ON ADVANCED CRYPTO AUTHENTICATION POLICY. TPM–Testing, Psychometrics, Methodology in Applied Psychology, 32(S4 (2025): Posted 17 July), 241-255.
- Akat, G.B.; Magare, B.K. (2022). Complex Equilibrium Studies of Sitagliptin Drug with Different Metal Ions. Asian Journal of Organic & Medicinal Chemistry.
- Kumar, T.V. (2020). Generative AI Applications in Customizing User Experiences in Banking Apps.
- Jeyaprabha, B.; Catherine, S.; Vijayakumar, M. (2024). Unveiling the Economic Tapestry: Statistical Insights Into India's Thriving Travel and Tourism Sector. In Managing Tourism and Hospitality Sectors for Sustainable Global Transformation (pp. 249-259). IGI Global Scientific Publishing.
- Arora, A. (2025). Understanding the Security Implications of Generative AI in Sensitive Data Applications.
- JEYAPRABHA; B; SUNDAR; C (2022). The Psychological Dimensions Of Stock Trader Satisfaction With The E-Broking Service Provider. Journal of Positive School Psychology, 6(5).
- Singh, H. (2025). How Generative AI is Revolutionizing Scientific Research by Automating Hypothesis Generation. Available at SSRN 5267912.
- Singh, B. (2025). Advanced Oracle Security Techniques for Safeguarding Data Against Evolving Cyber Threats. Available at SSRN 5267951.
- Praveen, R.V.S. (2024). Data Engineering for Modern Applications. Addition Publishing House.
- Akat, G.B.; Magare, B.K. (2022). Mixed Ligand Complex Formation of Copper (II) with Some Amino Acids and Metoprolol. Asian Journal of Organic & Medicinal Chemistry.
- Singh, B. (2025). DevSecOps: A Comprehensive Framework for Securing Cloud-Native Applications. Available at SSRN 5267982.
- Singh, H. (2025). The Future Of Generative Ai: Opportunities, Challenges, And Industry Disruption Potential. Challenges, And Industry Disruption Potential (May 23, 2025), 23 May.
- Chand, K. (2013). Effect of pre-cooling treatments on shelf life of tomato in ambient condition.
- Rahman, Z.; Mohan, A.; Priya, S. (2021). Electrokinetic remediation: An innovation for heavy metal contamination in the soil environment. Materials Today: Proceedings, 37, 2730-2734.
- Singh, B. (2025). Enhancing Oracle Database Security with Transparent Data Encryption (TDE) Solutions. Available at SSRN 5267924.
- Singh, B. (2025). Challenges and Solutions for Adopting DevSecOps in Large Organizations. Available at SSRN 5267971.
- Singh, H. (2025). Key Cloud Security Challenges for Organizations Embracing Digital Transformation Initiatives. Available at SSRN 5267894.
- Kumar, T.V. (2022). AI-Powered Fraud Detection in Real-Time Financial Transactions.
- Raja, M.W. (2024). Artificial intelligence-based healthcare data analysis using multi-perceptron neural network (MPNN) based on optimal feature selection. SN Computer Science, 5(8), 1034.
- Akat, G.B. (2021). EFFECT OF ATOMIC NUMBER AND MASS ATTENUATION COEFFICIENT IN Ni-Mn FERRITE SYSTEM. MATERIAL SCIENCE, 20(06).
- Thakur, R.R.; Shahi, N.C.; Mangaraj, S.; Lohani, U.C.; Chand, K. (2021). Development of an organic coating powder and optimization of process parameters for shelf life enhancement of button mushrooms (Agaricus bisporus). Journal of Food Processing and Preservation, 45(3), e15306.
- Kumar, T.V. (2015). ANALYSIS OF SQL AND NOSQL DATABASE MANAGEMENT SYSTEMS INTENDED FOR UNSTRUCTURED DATA.
- Kumar, T.V. (2023). REAL-TIME DATA STREAM PROCESSING WITH KAFKA-DRIVEN AI MODELS.
- Nasir, G.; Chand, K.; Azaz Ahmad Azad, Z.R.; Nazir, S. (2020). Optimization of Finger Millet and Carrot Pomace based fiber enriched biscuits using response surface methodology. Journal of Food Science and Technology, 57(12), 4613-4626.
- Singh, H. (2025). Enhancing Cloud Security Posture with AI-Driven Threat Detection and Response Mechanisms. Available at SSRN 5267878.
- Praveen, R.V.S.; Hundekari, S.; Parida, P.; Mittal, T.; Sehgal, A.; Bhavana, M. (2025, February). Autonomous Vehicle Navigation Systems: Machine Learning for Real-Time Traffic Prediction. In 2025 International Conference on Computational, Communication and Information Technology (ICCCIT) (pp. 809-813). IEEE.
- Kumar, T.V. (2021). NATURAL LANGUAGE UNDERSTANDING MODELS FOR PERSONALIZED FINANCIAL SERVICES.
- Chand, K.; Shahi, N.C.; Lohani, U.C.; Garg, S.K. (2011). Effect of storage conditions on keeping qualities of jaggery. Sugar Tech, 13(1), 81-85.
- Kumar, T.V. (2019). BLOCKCHAIN-INTEGRATED PAYMENT GATEWAYS FOR SECURE DIGITAL BANKING.
- Arunmohan, A.M.; Lakshmi, M. (2018). Analysis of modern construction projects using montecarlo simulation technique. International Journal of Engineering & Technology, 7(2.19), 41-44.
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




