1. Introduction
1.1. Rise of Distributed and Remote-First Enterprises
In recent years, enterprises have rapidly shifted toward distributed and remote-first models, driven by technological advances and changing workforce expectations. By 2025, about 22% of the U.S. workforce works remotely, reflecting a lasting cultural transformation. Hybrid work models, favored by over 80% of employees globally, combine flexibility with collaboration and have become a dominant operational paradigm. This shift has expanded the enterprise perimeter, increasing dependence on cloud services and necessitating new security and networking approaches that accommodate distributed user bases and locations.
1.2. Challenges of Traditional Network Security Architecture
Traditional network security designs, which rely heavily on well-defined perimeters, struggle to cope with the dissolving network boundaries of distributed enterprises. Such architectures typically require backhauling traffic through fixed data centers for inspection, causing latency and hampering user experience. They also face challenges in scaling and adapting to dynamic cloud environments, leaving gaps in security coverage and creating bottlenecks. The shift to mobile and remote work exacerbates these limitations, exposing enterprises to increasing risks from unmonitored endpoints and cloud applications.
1.3. Evolution Toward Cloud-Centric Security Models
The inadequacies of perimeter-centric models have accelerated the adoption of cloud-centric security frameworks that inherently support distributed architectures. These models emphasize direct-to-cloud connectivity, centralized visibility, and layered security controls that travel with data and users independently of location. The move to Software-Defined Wide Area Networking (SD-WAN), cloud-native security services, and identity-based access control reflects this evolution, offering improved scalability, agility, and comprehensive threat protection aligned with cloud service consumption.
1.4. Need for SASE in Modern Enterprise Environments
Secure Access Service Edge (SASE) emerges as a unifying framework combining comprehensive networking and security services delivered from the cloud. SASE addresses the complexity of securing distributed enterprises by integrating SD-WAN, cloud access security broker (CASB), firewall-as-a-service (FWaaS), zero trust network access (ZTNA), and secure web gateways into a single service. This convergence reduces latency, enhances user experience, and provides consistent, context-aware security policies across all access points, whether remote or on-premises. Therefore, SASE is essential for modern enterprises aiming to protect cloud applications and optimize network performance within a unified security architecture.
2. Literature Survey
The Secure Access Service Edge (SASE) has gained significant attention as enterprises increasingly embrace cloud-first and distributed architectures. SASE represents a converged approach, integrating networking and security functions into a unified, cloud-delivered platform that addresses the complex demands of modern enterprise environmentsenabling optimized performance, consistent security, and simplified management. Research and industry solution comparisons reveal a spectrum of methodologies, deployment strategies, and technological focuses ranging from vendor-specific implementations to hybrid integration models. Understanding these approaches is essential to evaluating the best paths for effective SASE adoption.
Table 1.
Comparison of SASE Implementation Methodologies and Solutions.
Table 1.
Comparison of SASE Implementation Methodologies and Solutions.
| Solution/Vendor |
Deployment Model |
Key Features |
Strengths |
Limitations |
| Cato Networks |
Cloud-native, single vendor |
AI-driven operations, global private cloud, unified management |
Reduced complexity, automation, good performance |
Vendor lock-in concerns |
| Fortinet FortiSASE |
Cloud or hybrid |
ZTNA, Secure SD-WAN, AI security |
Flexible deployment, strong enterprise security |
Complexity in hybrid setups |
| Palo Alto Prisma SASE |
Cloud-native |
AI-powered threat detection, ZTNA, CASB, SD-WAN |
High scalability, comprehensive threat protection |
Higher cost |
| Versa Networks |
Cloud-delivered |
Unified SASE platform, AI, flexible deployment |
Improved user experience, cost-efficient |
Limited advanced DLP features |
| Zscaler Zero Trust |
Cloud-native |
Security Service Edge (SSE), global Zero Trust Exchange |
Strong cloud focus, streamlined management |
Smaller support for legacy apps |
| Cisco SASE |
Cloud and on-premises |
SD-WAN, FWaaS, CASB, ZTNA |
Integration with Cisco products, robust threat protection |
Complex integration |
| Cloudflare SASE |
Cloud-native, edge-based |
Identity-based access, global PoPs, SD-WAN |
Low latency, strong web protection |
Less coverage in traditional enterprise segments |
| Netskope |
Cloud-native |
AI-powered visibility, CASB, ZTNA |
Flexible, strong cloud data security |
Newer player, evolving ecosystem |
| VMware VeloCloud |
Cloud and on-premises |
SD-WAN, ZTNA, CASB, centralized management |
Seamless VMware ecosystem integration |
Deployment complexity |
This table summarizes key aspects of various SASE solutions, highlighting favored deployment models, advanced features like AI-driven security, unified management capabilities, and strengths such as reduced operational complexity and network optimization. The limitations indicate areas like integration challenges, cost implications, or feature gaps. Evaluating these factors helps enterprises select appropriate SASE strategies aligned with their network complexity, security requirements, and growth objectives.
3. Fundamentals of Secure Access Service Edge (SASE) with Formulaic Insights
3.1. Core Principles and Architectural Overview
SASE integrates networking and security into a single cloud-native architecture designed to provide secure access regardless of user location or device. This is achieved by converging essential security functions with software-defined wide area networking (SD-WAN) across distributed cloud points of presence (PoPs). The architectural principle follows a layered plane modelwith separate data, control, and management planesenabling centralized policy enforcement and decentralized traffic inspection close to users. Network availability
in SASE architectures with multiple redundant PoPs can be mathematically expressed as:
where is the availability of each PoP and is the total number of PoPs. This redundancy ensures high resilience and minimal latency.
3.2. Key Components: SD-WAN, CASB, SWG, ZTNA, FWaaS
The key SASE components collaborate to establish secure, optimized connectivity:
SD-WAN routes traffic dynamically, optimizing paths based on latency, bandwidth, and policy, modeled by a dynamic routing function
selecting the path
minimizing cost
:
Cloud Access Security Broker (CASB) provides visibility and policy enforcement on cloud app usage.
Secure Web Gateway (SWG) inspects and filters internet traffic for threats and policy compliance.
Zero Trust Network Access (ZTNA) enforces granular, identity-based access continuously verified by authentications and device posture checks.
Firewall as a Service (FWaaS) offers scalable firewall protections in the cloud, enforcing uniform policies.
Together these components allow for a unified security policy evaluated dynamically based on user , device , resource , and time .
3.3. SASE vs Traditional Perimeter-Based Security Models
Traditional perimeter security follows a hard boundary model, often resulting in the equation:
where
denotes implicit trust. However, with distributed architectures, this trust model collapses. SASE replaces this with zero trust principles, where trust
is a continuous function of user authentication
, device compliance
, and risk
:
eliminating implicit trust and enforcing dynamic validation.
3.4. Role of Identity, Context and Policy Enforcement
Identity functions as the cornerstone of access decisions in SASE. Policies are enforced through a centralized policy decision point that evaluates context
—user role, location, device state, and threat intelligence—in real time as a function
:
This dynamic evaluation enables consistent, granular control reducing attack surfaces and adapting to environmental changes.
4. Distributed Enterprise Network Requirements
4.1. Multi-Branch and Hybrid Workforce Connectivity
Distributed enterprises often operate across numerous branches with hybrid workforces requiring seamless and secure connectivity. The network must accommodate diverse access points, balancing direct cloud connections and on-premises integration. The connectivity model typically involves multiple WAN links and cloud access points with redundancy to ensure uninterrupted service. Network availability
over multiple paths can be quantified as:
where
is the availability of each individual connection or path, ensuring higher overall service reliability through parallel redundant links.
4.2. Cloud-Native Application Workloads and SaaS Adoption
Modern enterprises increasingly rely on cloud-native applications and SaaS offerings that demand high bandwidth and low latency. Network infrastructure must support rapid, secure access to distributed cloud resources while maintaining user experience. Load balancing dynamically selects optimal routes
minimizing latency
across available paths in the cloud fabric:
This ensures efficient resource utilization while conforming to security policies.
4.3. Bandwidth Efficiency and Network Performance Needs
Optimizing bandwidth usage is critical as distributed enterprises contend with growing volumes of data and transactions. Technologies such as SD-WAN enable path selection based on performance metrics (latency, jitter, loss) optimizing throughput
. The total throughput
aggregates over
paths:
where each
corresponds to throughput over link
. Effective traffic shaping and prioritization further enhance performance under varying network conditions.
4.4. Security Challenges in Distributed Environments
Distributed architectures expand the security perimeter, increasing attack surfaces and complicating policy enforcement. Challenges include securing multiple access points, maintaining consistent identity and access control, and detecting lateral movements across segments. Zero Trust principles embodied in frameworks like SASE enforce continuous verification modeled as a function based on user , device , resource , and time , mitigating risks dynamically and uniformly. Interoperability between heterogeneous systems and cloud providers remains complex, requiring integrated policy orchestration and telemetry for comprehensive visibility.
5. Unified Security Framework in SASE Architecture
5.1. Converging Networking and Security as a Service
At the heart of SASE lies the convergence of networking and security functions into a unified, cloud-delivered service. This integration dissolves traditional silos, combining SD-WAN’s dynamic connectivity with comprehensive security capabilities such as firewall-as-a-service (FWaaS), secure web gateway (SWG), cloud access security broker (CASB), and zero trust network access (ZTNA). The unified framework ensures consistent policy enforcement regardless of user or application location, optimizing both security and network performance. Network availability
in such converged infrastructures can be represented mathematically as:
where
are individual node availabilities, capturing the resilience afforded by distributed cloud points of presence.
5.2. Identity-Centric Access and Continuous Validation
Identity serves as the cornerstone of access control within SASE architectures. Through continuous validation mechanisms, access decisions
evaluate multiple factors including user identity
, device posture
, location
, and behavioral context
in real time:
This dynamic function ensures least privilege principles, adapting permissions based on risk assessments and contextual changes, drastically minimizing attack surfaces.
5.3. Content Filtering, Threat Prevention, and DLP
Content inspection and threat prevention functions embedded within SASE inspect traffic for malware, phishing, and policy violations. Data Loss Prevention (DLP) enforces controls over sensitive data flow. These capabilities collectively define a threat mitigation function
operating on data packets
:
Automated quarantine or blocking actions follow detections, ensuring proactive risk management.
5.4. Secure API Access & Micro-Segmentation Policies
SASE extends protection to API traffic by authenticating API clients and enforcing granular access policies. Micro-segmentation within SASE isolates workloads into secure segments
, controlling east-west traffic and preventing lateral attacks. The security posture gain
from micro-segmentation can be modeled as:
where
is the number of segments, and
is the probability of compromise in segment
. This segmentation reduces risk by compartmentalizing the environment.
6. Cloud Application Protection Mechanisms in SASE
6.1. Zero Trust Network Access (ZTNA) for SaaS/Cloud Apps
ZTNA is foundational in SASE frameworks for securing cloud and SaaS applications by enforcing strict identity- and context-based access controls without relying on network perimeter trust. Access decisions are continuously reevaluated based on real-time attributes such as user identity, device posture, location, and behavioral analytics. This dynamic trust function
is modeled as:
where
represents user credentials,
device security state,
location context, and
behavioral indicators. ZTNA minimizes exposure by granting access only to verified and compliant entities, preventing lateral movement and unauthorized intrusions.
6.2. Cloud Access Security Broker (CASB) Integration
CASB extends visibility and control over cloud service usage, acting as a policy enforcement point between users and cloud applications. It facilitates data governance, compliance monitoring, and threat detection specifically tailored for cloud environments. CASB’s policy enforcement
operates on observed cloud traffic
to allow, block, or quarantine requests:
CASB integration within SASE ensures unified risk management across multiple SaaS and IaaS platforms.
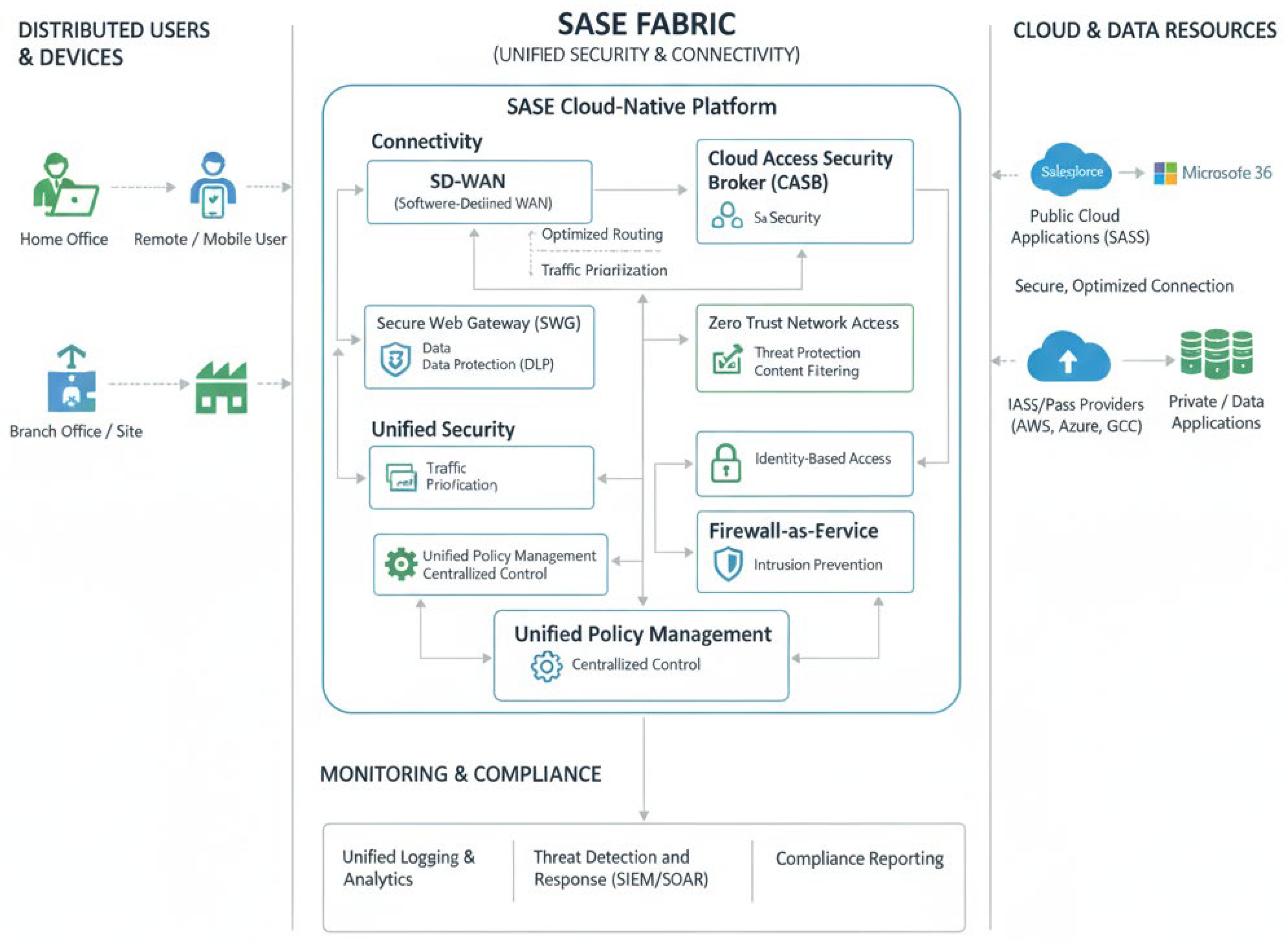
Figure 1.
Cloud Application Protection and Network Optimization using SASE.
Figure 1.
Cloud Application Protection and Network Optimization using SASE.
6.3. Data Encryption, Tokenization & Key Management
Protecting sensitive cloud data requires strong cryptographic controls. Encryption converts plaintext
to ciphertext
with key
:
Tokenization replaces sensitive data elements with non-sensitive tokens
, decoupling actual data from usage contexts. Effective key management
governs generation, distribution, and rotation:
These mechanisms ensure data confidentiality and integrity across cloud transit and storage.
6.4. Runtime Risk Analysis and Adaptive Policy Enforcement
SASE platforms perform continuous runtime risk evaluation combining telemetry, anomaly detection, and contextual insights. Risk score
at time
integrates multiple signals
weighted by importance
:
Adaptive policies adjust authorization and monitoring based on
, enabling real-time response to emerging threats and dynamic environments.
7. Network Optimization Using SASE
7.1. Intelligent Routing Through SD-WAN
SASE integrates Software-Defined Wide Area Networking (SD-WAN) to optimize routing by dynamically selecting the best available path for network traffic based on real-time conditions such as latency, bandwidth, and link quality. SD-WAN routing selects a path
that minimizes a cost function
, typically a measure of latency and loss:
This capability ensures optimal performance for critical applications by adapting traffic flows dynamically, enhancing user experience while efficiently utilizing network resources.
7.2. Latency Reduction Techniques for Multi-Cloud Workloads
To address latency in multi-cloud environments, SASE employs edge-based processing and direct cloud access, avoiding backhauling traffic through centralized data centers. Latency
for a given cloud workload routing can be modeled as:
SASE reduces
by leveraging distributed points of presence (PoPs) close to users and cloud data centers, minimizing core network transit times and improving responsiveness.
7.3. Edge-Based Traffic Optimization and Load Balancing
SASE pushes traffic inspection and optimization closer to users at the network edge, combining traffic shaping and load balancing to maximize throughput and reliability. Aggregate throughput
over multiple links is:
where
is throughput on link
. Load balancing algorithms distribute traffic loads to avoid congestion, improving availability and performance consistency.
7.4. Performance Metrics and QoS Enforcement
SASE platforms enforce Quality of Service (QoS) by prioritizing traffic according to business policies and application requirements. Metrics such as latency
, jitter
, packet loss
, and throughput
are continuously monitored. The overall QoS score
can be expressed as:
where
are weights reflecting the importance of each metric. This quantitative assessment guides adaptive traffic management to maintain service levels.
8. Implementation Roadmap for SASE Adoption
8.1. Readiness Assessment and Architecture Evaluation
The initial step involves assessing the current network and security infrastructure to identify gaps relative to desired SASE capabilities. This readiness assessment
can be represented as a composite score:
where
is the score for each security/network capability
, and
its relative importance. Architecture evaluation focuses on compatibility with cloud-native frameworks and identifies legacy components requiring modernization or integration.
8.2. Migration Strategy from Legacy Networking
Transitioning from traditional MPLS or legacy VPN systems involves phased migration minimizing disruption. The migration plan prioritizes critical applications and user groups, iteratively shifting traffic to SASE services. Risk
during migration can be modeled to ensure it remains below tolerance
:
Traffic steering gradually diverts flows based on monitoring feedback, preserving service continuity while validating policy effectiveness.
8.3. Integration with IAM, SIEM, and SOC Platforms
SASE adoption requires seamless integration with Identity and Access Management (IAM) for enforcing zero trust principles, Security Information and Event Management (SIEM) for consolidated telemetry, and Security Operations Centers (SOC) for real-time incident response. The integration overhead
balances performance impact and security improvement:
Optimization targets maximizing threat detection while minimizing latency and complexity, achieved through API-based interoperability and automated workflows.
8.4. Organizational Policies, Compliance & Governance
Implementing SASE demands alignment with organizational security policies, regulatory compliance, and governance frameworks. Governance effectiveness
can be tracked using compliance metrics
and audit frequencies
:
Ongoing policy reviews, employee training, and risk assessment ensure continuous adherence and adaptation to evolving compliance landscapes.
9. Use Cases and Industry Applications
9.1. Remote Workforce and Secure Teleworking
The rise of remote work demands secure, seamless access to corporate resources from diverse locations and devices. SASE enables organizations to replace legacy VPNs with a cloud-native security framework that authenticates users via Zero Trust Network Access (ZTNA), enforcing continuous validation while optimizing network paths through distributed points of presence (PoPs). This ensures consistent security and user experience regardless of location, supporting high productivity and protecting sensitive data in teleworking scenarios.
9.2. Multi-Cloud Enterprise Ecosystems
Enterprises increasingly utilize multiple cloud providers for flexibility and resilience, creating complexity in connectivity and security. SASE unifies networking and security across heterogeneous cloud environments, providing centralized policy enforcement and real-time threat detection. It simplifies multi-cloud access by leveraging Cloud Access Security Brokers (CASB), firewall-as-a-service (FWaaS), and secure web gateways (SWG) that collectively monitor and control cloud traffic, reducing risk in complex cloud ecosystems.
9.3. BFSI and Compliance-Driven Infrastructure
The Banking, Financial Services, and Insurance (BFSI) sector requires stringent compliance with regulations such as PCI DSS, SOX, and GDPR. SASE provides end-to-end encryption, data loss prevention, and continuous monitoring to ensure adherence to these frameworks. Its identity-centric policies and micro-segmentation capabilities guard against advanced threats, protect sensitive financial information, and support auditability, enabling BFSI institutions to meet compliance without compromising business agility.
9.4. Educational Institutions and Public Sector Networks
Educational and public sector organizations often have distributed campuses and remote users requiring secure access to digital learning platforms and government services. SASE enhances these networks by enabling secure, scalable, and manageable connectivity, integrating identity-based access controls with threat prevention measures. This ensures data privacy for students and citizens while maintaining compliance with applicable public data protection regulations.
10. Performance Evaluation and Security Metrics
10.1. Application Access Performance Benchmarks
Evaluating SASE performance includes measuring throughput, latency, and user experience to ensure seamless access to applications, especially cloud-native and SaaS platforms. Latency (
) is a critical factor and can be modeled as:
where
is the network propagation delay,
is the time for security inspection and policy enforcement, and
accounts for delays due to traffic congestion. Metrics like Mean Opinion Score (MoS) or Quality of Experience (QoE) combine these to quantify user satisfaction.
10.2. Threat Detection and Security Posture Metrics
Security effectiveness in SASE deployments is measured by detection rates, false positive rates, and incident containment times. The detection accuracy
is often evaluated as:
while false positive rate
is:
These metrics help balance vigilance with usability, optimizing policy tuning and resource allocation to maintain a strong security posture.
10.3. Incident Response Time and Policy Enforcement KPIs
Key performance indicators for incident response include Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) to threats, critical for minimizing damage. These are calculated as:
where
is the number of incidents. Additionally, policy enforcement effectiveness can be tracked by access violation rates and enforcement latency, ensuring timely and consistent application of security controls.
11. Challenges and Limitations of SASE Adoption
11.1. Vendor Lock-In and Interoperability Issues
One significant challenge in SASE adoption is vendor lock-in caused by proprietary technologies and data formats. Organizations that choose a single vendor for the entire SASE stack may face difficulties switching providers due to data extraction complexities and restrictive contracts. Interoperability issues also arise when integrating SASE solutions with existing legacy systems and heterogeneous cloud environments, complicating seamless policy enforcement and telemetry sharing.
11.2. Networking Overhead and Configuration Complexity
SASE architectures rely on cloud Points of Presence (PoPs) for security and optimization, but poorly distributed or overloaded PoPs introduce latency impacting performance. Configuration complexity grows as enterprises must orchestrate policies across diverse endpoints, cloud services, and network segments, often requiring specialized expertise. The intricate setups may result in misconfigurations increasing security risks or service disruptions.
11.3. Cost and Skillset Challenges in Deployment
Implementing SASE can be costly upfront, with investments needed for new infrastructure, licenses, and operational changes. Additionally, there exists a skill gap in IT teams lacking experience with SASE’s unified approach, causing delays or inefficiencies. Organizational resistance to change and the need for thorough user training also present adoption barriers.
11.4. Scalability and Data Localization Constraints
Although SASE solutions promise scalability, growth may reveal limitations in handling increased traffic volumes, diverse geographies, and regulatory compliance mandates related to data residency. Enterprises must ensure their chosen SASE providers can adapt to workload expansion without performance degradation while conforming to local data governance policies.
Recognizing these challenges enables informed planning and mitigation strategies, such as choosing interoperable solutions, investing in talent development, phased deployment approaches, and vendor collaboration to ensure SASE adoption delivers its full potential securely and efficiently.
Conclusion and Future Enhancements
Secure Access Service Edge (SASE) stands as a transformative paradigm for enterprise networking and security, combining cloud-native architecture with zero trust principles to address the complexity of modern distributed and cloud-first infrastructures. By unifying networking and security services such as SD-WAN, CASB, SWG, ZTNA, and FWaaS into a single framework, SASE enables consistent policy enforcement, reduced latency, and enhanced security posture across diverse access points and cloud environments.
Future enhancements in SASE technology will be driven by the integration of artificial intelligence (AI) and machine learning (ML) to elevate threat detection and automate responses adaptively. Predictive analytics will enable proactive risk mitigation, while AI-powered behavioral analysis will refine access decisions in real time. Advancements in edge computing and 5G integration will further optimize network performance and extend secure connectivity to the growing edge device ecosystem.
Concurrently, SASE platforms will evolve to offer deeper API integrations, facilitating seamless orchestration with existing IAM, SIEM, and SOC tools, thus streamlining operations and accelerating incident response. Enhanced data privacy and localization capabilities will address regulatory challenges across global deployments.
Overall, SASE is poised to become foundational for secure, agile, and scalable enterprise architectures in the coming years, enabling organizations to balance performance demands with robust security governance in an increasingly complex digital landscape.
References
- Arora, A. (2025). THE SIGNIFICANCE AND ROLE OF AI IN IMPROVING CLOUD SECURITY POSTURE FOR MODERN ENTERPRISES. Available at SSRN 5268192.
- Singh, B. (2025). Building Secure Software Faster with DevSecOps Principles, Practices, and Implementation Strategies. Practices, and Implementation Strategies (May 23, 2025).
- Akat, G. B., & Magare, B. K. (2023). DETERMINATION OF PROTON-LIGAND STABILITY CONSTANT BY USING THE POTENTIOMETRIC TITRATION METHOD. MATERIAL SCIENCE, 22(07).
- Siddiqui, A., Chand, K., & Shahi, N. C. (2021). Effect of process parameters on extraction of pectin from sweet lime peels. Journal of The Institution of Engineers (India): Series A, 102(2), 469-478. [CrossRef]
- Kumar, J. D. S., Subramanyam, M. V., & Kumar, A. S. (2024). Hybrid Sand Cat Swarm Optimization Algorithm-based reliable coverage optimization strategy for heterogeneous wireless sensor networks. International Journal of Information Technology, 1-19. [CrossRef]
- Shinkar, A. R., Joshi, D., Praveen, R. V. S., Rajesh, Y., & Singh, D. (2024, December). Intelligent solar energy harvesting and management in IoT nodes using deep self-organizing maps. In 2024 International Conference on Emerging Research in Computational Science (ICERCS) (pp. 1-6). IEEE.
- Vikram, A. V., & Arivalagan, S. (2017). Engineering properties on the sugar cane bagasse with sisal fibre reinforced concrete. International Journal of Applied Engineering Research, 12(24), 15142-15146.
- Reddy, D. N., Venkateswararao, P., Vani, M. S., Pranathi, V., & Patil, A. (2025). HybridPPI: A Hybrid Machine Learning Framework for Protein-Protein Interaction Prediction. Indonesian Journal of Electrical Engineering and Informatics (IJEEI), 13(2). [CrossRef]
- Atheeq, C., Sultana, R., Sabahath, S. A., & Mohammed, M. A. K. (2024). Advancing IoT Cybersecurity: adaptive threat identification with deep learning in Cyber-physical systems. Engineering, Technology & Applied Science Research, 14(2), 13559-13566.
- Arora, A. (2025). Zero Trust Architecture: Revolutionizing Cybersecurity for Modern Digital Environments. Available at SSRN 5268151.
- Mohammed Nabi Anwarbasha, G. T., Chakrabarti, A., Bahrami, A., Venkatesan, V., Vikram, A. S. V., Subramanian, J., & Mahesh, V. (2023). Efficient finite element approach to four-variable power-law functionally graded plates. Buildings, 13(10), 2577. [CrossRef]
- Kumar, N., Kurkute, S. L., Kalpana, V., Karuppannan, A., Praveen, R. V. S., & Mishra, S. (2024, August). Modelling and Evaluation of Li-ion Battery Performance Based on the Electric Vehicle Tiled Tests using Kalman Filter-GBDT Approach. In 2024 International Conference on Intelligent Algorithms for Computational Intelligence Systems (IACIS) (pp. 1-6). IEEE.
- Singh, H. (2025). Securing High-Stakes Digital Transactions: A Comprehensive Study on Cybersecurity and Data Privacy in Financial Institutions. Available at SSRN 5267850.
- Singh, B. (2025). Integrating Threat Modeling In Devsecops For Enhanced Application Security. Available at SSRN 5267976.
- Akat, G. B. (2023). Structural Analysis of Ni1-xZnxFe2O4 Ferrite System. MATERIAL SCIENCE, 22(05).
- Vijay Vikram, A. S., & Arivalagan, S. (2017). A short review on the sugarcane bagasse with sintered earth blocks of fiber reinforced concrete. Int J Civil Eng Technol, 8(6), 323-331.
- Yamuna, V., Praveen, R. V. S., Sathya, R., Dhivva, M., Lidiya, R., & Sowmiya, P. (2024, October). Integrating AI for Improved Brain Tumor Detection and Classification. In 2024 4th International Conference on Sustainable Expert Systems (ICSES) (pp. 1603-1609). IEEE.
- Sultana, R., Ahmed, N., & Sattar, S. A. (2018). HADOOP based image compression and amassed approach for lossless images. Biomedical Research, 29(8), 1532-1542.
- Kumar, T. V. (2024). Enhanced Kubernetes Monitoring Through Distributed Event Processing.
- Boopathy, D., & Balaji, P. (2023). Effect of different plyometric training volume on selected motor fitness components and performance enhancement of soccer players. Ovidius University Annals, Series Physical Education and Sport/Science, Movement and Health, 23(2), 146-154.
- Rao, A. S., Reddy, Y. J., Navya, G., Gurrapu, N., Jeevan, J., Sridhar, M., ... & Anand, D. High-performance sentiment classification of product reviews using GPU (parallel)-optimized ensembled methods. [CrossRef]
- Arora, A. (2025). Securing Multi-Cloud Architectures using Advanced Cloud Security Management Tools. Available at SSRN 5268184.
- Singh, B. (2025). Mastering Oracle Database Security: Best Practices for Enterprise Protection. Available at SSRN 5267920.
- Lopez, S., Sarada, V., Praveen, R. V. S., Pandey, A., Khuntia, M., & Haralayya, D. B. (2024). Artificial intelligence challenges and role for sustainable education in india: Problems and prospects. Sandeep Lopez, Vani Sarada, RVS Praveen, Anita Pandey, Monalisa Khuntia, Bhadrappa Haralayya (2024) Artificial Intelligence Challenges and Role for Sustainable Education in India: Problems and Prospects. Library Progress International, 44(3), 18261-18271.
- Akat, G. B. (2022). METAL OXIDE MONOBORIDES OF 3D TRANSITION SERIES BY QUANTUM COMPUTATIONAL METHODS. MATERIAL SCIENCE, 21(06).
- Kumar, T. V. (2019). Cloud-Based Core Banking Systems Using Microservices Architecture.
- Kumar, J. D. S., Subramanyam, M. V., & Kumar, A. P. S. (2023). Hybrid Chameleon Search and Remora Optimization Algorithm-based Dynamic Heterogeneous load balancing clustering protocol for extending the lifetime of wireless sensor networks. International Journal of Communication Systems, 36(17), e5609. [CrossRef]
- Arora, A. (2025). Analyzing Best Practices and Strategies for Encrypting Data at Rest (Stored) and Data in Transit (Transmitted) in Cloud Environments. Available at SSRN 5268190.
- Sharma, S., Vij, S., Praveen, R. V. S., Srinivasan, S., Yadav, D. K., & VS, R. K. (2024, October). Stress Prediction in Higher Education Students Using Psychometric Assessments and AOA-CNN-XGBoost Models. In 2024 4th International Conference on Sustainable Expert Systems (ICSES) (pp. 1631-1636). IEEE.
- Arora, A. (2025). Transforming Cybersecurity Threat Detection and Prevention Systems using Artificial Intelligence. Available at SSRN 5268166.
- Nizamuddin, M. K., Raziuddin, S., Farheen, M., Atheeq, C., & Sultana, R. (2024). An MLP-CNN Model for Real-time Health Monitoring and Intervention. Engineering, Technology & Applied Science Research, 14(4), 15553-15558. [CrossRef]
- Arora, A. (2025). Evaluating Ethical Challenges in Generative AI Development and Responsible Usage Guidelines. Available at SSRN 5268196.
- Kamatchi, S., Preethi, S., Kumar, K. S., Reddy, D. N., & Karthick, S. (2025, May). Multi-Objective Genetic Algorithm Optimised Convolutional Neural Networks for Improved Pancreatic Cancer Detection. In 2025 3rd International Conference on Data Science and Information System (ICDSIS) (pp. 1-7). IEEE.
- Sivakumar, S., Prakash, R., Srividhya, S., & Vikram, A. V. (2023). A novel analytical evaluation of the laboratory-measured mechanical properties of lightweight concrete. Structural engineering and mechanics: An international journal, 87(3), 221-229.
- Praveen, R. V. S., Hemavathi, U., Sathya, R., Siddiq, A. A., Sanjay, M. G., & Gowdish, S. (2024, October). AI Powered Plant Identification and Plant Disease Classification System. In 2024 4th International Conference on Sustainable Expert Systems (ICSES) (pp. 1610-1616). IEEE.
- Akat, G. B. (2022). OPTICAL AND ELECTRICAL STUDY OF SODIUM ZINC PHOSPHATE GLASS. MATERIAL SCIENCE, 21(05).
- Singh, B. (2025). Oracle Database Vault: Advanced Features for Regulatory Compliance and Control. Available at SSRN 5267938.
- Kumar, T. V. (2018). Event-Driven App Design for High-Concurrency Microservices.
- Arora, A. (2025). Integrating Dev-Sec-Ops Practices to Strengthen Cloud Security in Agile Development Environments. Available at SSRN 5268194.
- Singh, B. (2025). Integrating Security Seamlessly into DevOps Development Pipelines through DevSecOpsA Holistic Approach to Secure Software Delivery. Available at SSRN 5267955.
- Kumar, T. V. (2016). Layered App Security Architecture for Protecting Sensitive Data.
- Charanya, J., Sureshkumar, T., Kavitha, V., Nivetha, I., Pradeep, S. D., & Ajay, C. (2024, June). Customer Churn Prediction Analysis for Retention Using Ensemble Learning. In 2024 15th International Conference on Computing Communication and Networking Technologies (ICCCNT) (pp. 1-10). IEEE.
- Nimma, D., Rao, P. L., Ramesh, J. V. N., Dahan, F., Reddy, D. N., Selvakumar, V., ... & Jangir, P. (2025). Reinforcement Learning-Based Integrated Risk Aware Dynamic Treatment Strategy for Consumer-Centric Next-Gen Healthcare. IEEE Transactions on Consumer Electronics. [CrossRef]
- Arora, A. (2025). The Future of Cybersecurity: Trends and Innovations Shaping Tomorrow's Threat Landscape. Available at SSRN 5268161.
- Akat, G. B. (2022). STRUCTURAL AND MAGNETIC STUDY OF CHROMIUM FERRITE NANOPARTICLES. MATERIAL SCIENCE, 21(03).
- Singh, H. (2025). The Role of Multi-Factor Authentication and Encryption in Securing Data Access of Cloud Resources in a Multitenant Environment. Available at SSRN 5267886.
- Raja, M. W., & Nirmala, D. K. (2016). Agile development methods for online training courses web application development. International Journal of Applied Engineering Research ISSN, 0973-4562.
- Anuprathibha, T., Praveen, R. V. S., Sukumar, P., Suganthi, G., & Ravichandran, T. (2024, October). Enhancing Fake Review Detection: A Hierarchical Graph Attention Network Approach Using Text and Ratings. In 2024 Global Conference on Communications and Information Technologies (GCCIT) (pp. 1-5). IEEE.
- Jeyaprabha, B., & Sundar, C. (2021). The mediating effect of e-satisfaction on e-service quality and e-loyalty link in securities brokerage industry. Revista Geintec-gestao Inovacao E Tecnologias, 11(2), 931-940.
- Arora, A. (2025). Comprehensive Cloud Security Strategies for Protecting Sensitive Data in Hybrid Cloud Environments.
- Sultana, R., Ahmed, N., & Basha, S. M. (2011). Advanced Fractal Image Coding Based on the Quadtree. Computer Engineering and Intelligent Systems, 2 3, 129, 136.
- Singh, H. (2025). Cybersecurity for Smart Cities Protecting Infrastructure in the Era of Digitalization. Available at SSRN 5267856.
- Kemmannu, P. K., Praveen, R. V. S., & Banupriya, V. (2024, December). Enhancing Sustainable Agriculture Through Smart Architecture: An Adaptive Neuro-Fuzzy Inference System with XGBoost Model. In 2024 International Conference on Sustainable Communication Networks and Application (ICSCNA) (pp. 724-730). IEEE.
- Singh, B. (2017). Enhancing Real-Time Database Security Monitoring Capabilities Using Artificial Intelligence. International Journal of Current Engineering and Scientific Research (IJCESR).
- Singh, H. (2025). STRATEGIES TO BALANCE SCALABILITY AND SECURITY IN CLOUD-NATIVE APPLICATION DEVELOPMENT. Available at SSRN 5267890.
- RAJA, M. W., PUSHPAVALLI, D. M., BALAMURUGAN, D. M., & SARANYA, K. (2025). ENHANCED MED-CHAIN SECURITY FOR PROTECTING DIABETIC HEALTHCARE DATA IN DECENTRALIZED HEALTHCARE ENVIRONMENT BASED ON ADVANCED CRYPTO AUTHENTICATION POLICY. TPM–Testing, Psychometrics, Methodology in Applied Psychology, 32(S4 (2025): Posted 17 July), 241-255.
- Akat, G. B., & Magare, B. K. (2022). Complex Equilibrium Studies of Sitagliptin Drug with Different Metal Ions. Asian Journal of Organic & Medicinal Chemistry.
- Kumar, T. V. (2020). Generative AI Applications in Customizing User Experiences in Banking Apps.
- Jeyaprabha, B., Catherine, S., & Vijayakumar, M. (2024). Unveiling the Economic Tapestry: Statistical Insights Into India's Thriving Travel and Tourism Sector. In Managing Tourism and Hospitality Sectors for Sustainable Global Transformation (pp. 249-259). IGI Global Scientific Publishing.
- Arora, A. (2025). Understanding the Security Implications of Generative AI in Sensitive Data Applications.
- JEYAPRABHA, B., & SUNDAR, C. (2022). The Psychological Dimensions Of Stock Trader Satisfaction With The E-Broking Service Provider. Journal of Positive School Psychology, 6(5).
- Singh, H. (2025). How Generative AI is Revolutionizing Scientific Research by Automating Hypothesis Generation. Available at SSRN 5267912.
- Singh, B. (2025). Advanced Oracle Security Techniques for Safeguarding Data Against Evolving Cyber Threats. Available at SSRN 5267951.
- Praveen, R. V. S. (2024). Data Engineering for Modern Applications. Addition Publishing House.
- Akat, G. B., & Magare, B. K. (2022). Mixed Ligand Complex Formation of Copper (II) with Some Amino Acids and Metoprolol. Asian Journal of Organic & Medicinal Chemistry.
- Singh, B. (2025). DevSecOps: A Comprehensive Framework for Securing Cloud-Native Applications. Available at SSRN 5267982.
- Singh, H. (2025). The Future Of Generative Ai: Opportunities, Challenges, And Industry Disruption Potential. Challenges, And Industry Disruption Potential (May 23, 2025).
- Chand, K. (2013). Effect of pre-cooling treatments on shelf life of tomato in ambient condition.
- Rahman, Z., Mohan, A., & Priya, S. (2021). Electrokinetic remediation: An innovation for heavy metal contamination in the soil environment. Materials Today: Proceedings, 37, 2730-2734. [CrossRef]
- Singh, B. (2025). Enhancing Oracle Database Security with Transparent Data Encryption (TDE) Solutions. Available at SSRN 5267924.
- Singh, B. (2025). Challenges and Solutions for Adopting DevSecOps in Large Organizations. Available at SSRN 5267971.
- Singh, H. (2025). Key Cloud Security Challenges for Organizations Embracing Digital Transformation Initiatives. Available at SSRN 5267894.
- Kumar, T. V. (2022). AI-Powered Fraud Detection in Real-Time Financial Transactions.
- Raja, M. W. (2024). Artificial intelligence-based healthcare data analysis using multi-perceptron neural network (MPNN) based on optimal feature selection. SN Computer Science, 5(8), 1034. [CrossRef]
- Akat, G. B. (2021). EFFECT OF ATOMIC NUMBER AND MASS ATTENUATION COEFFICIENT IN Ni-Mn FERRITE SYSTEM. MATERIAL SCIENCE, 20(06).
- Thakur, R. R., Shahi, N. C., Mangaraj, S., Lohani, U. C., & Chand, K. (2021). Development of an organic coating powder and optimization of process parameters for shelf life enhancement of button mushrooms (Agaricus bisporus). Journal of Food Processing and Preservation, 45(3), e15306.
- Kumar, T. V. (2015). ANALYSIS OF SQL AND NOSQL DATABASE MANAGEMENT SYSTEMS INTENDED FOR UNSTRUCTURED DATA.
- Kumar, T. V. (2023). REAL-TIME DATA STREAM PROCESSING WITH KAFKA-DRIVEN AI MODELS.
- Nasir, G., Chand, K., Azaz Ahmad Azad, Z. R., & Nazir, S. (2020). Optimization of Finger Millet and Carrot Pomace based fiber enriched biscuits using response surface methodology. Journal of Food Science and Technology, 57(12), 4613-4626. [CrossRef]
- Singh, H. (2025). Enhancing Cloud Security Posture with AI-Driven Threat Detection and Response Mechanisms. Available at SSRN 5267878.
- Praveen, R. V. S., Hundekari, S., Parida, P., Mittal, T., Sehgal, A., & Bhavana, M. (2025, February). Autonomous Vehicle Navigation Systems: Machine Learning for Real-Time Traffic Prediction. In 2025 International Conference on Computational, Communication and Information Technology (ICCCIT) (pp. 809-813). IEEE.
- Kumar, T. V. (2021). NATURAL LANGUAGE UNDERSTANDING MODELS FOR PERSONALIZED FINANCIAL SERVICES.
- Chand, K., Shahi, N. C., Lohani, U. C., & Garg, S. K. (2011). Effect of storage conditions on keeping qualities of jaggery. Sugar Tech, 13(1), 81-85. [CrossRef]
- Kumar, T. V. (2019). BLOCKCHAIN-INTEGRATED PAYMENT GATEWAYS FOR SECURE DIGITAL BANKING.
- Arunmohan, A. M., & Lakshmi, M. (2018). Analysis of modern construction projects using montecarlo simulation technique. International Journal of Engineering & Technology, 7(2.19), 41-44. [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).