Submitted:
19 November 2025
Posted:
20 November 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction to Educational ERP Systems
1.1. Evolution of ERP in Academic Institutions
1.2. Challenges in Data Security and Access Management
1.3. Need for Centralized Authentication
2. Literature Survey
| Aspect | Methodology / Article | Key Features | Strengths | Limitations |
|---|---|---|---|---|
| Centralized IAM Architecture | "Cost-Effective IAM Framework" () | Single control point, token-based SSO, policy enforcement | Simplifies management, reduces redundancy, scalable | Potential single point of failure, requires robust infrastructure |
| Multi-Factor Authentication (MFA) | "Multi-Factor Authentication for Improved Enterprise Security" () | Multiple verification factors, adaptive challenge policies | High security, mitigates credential theft | Increased login complexity, user inconvenience |
| Federation Protocols | "Hybrid Cloud Identity" () | SAML, OAuth2, OpenID Connect for cross-system trust | Seamless cross-organizational access, improved interoperability | Implementation complexity, trust management issues |
| Log Analysis & Audit | "Top 8 IAM Metrics" () | Log correlation, anomaly detection, access frequency analysis | Enhances threat detection, compliance monitoring | Data volume management, false positives risk |
| Role-based Access in ERP | "Implementing RBAC in University" () | Role-permission mappings, principle of least privilege | Simplifies permissions, improves security | Rigid roles may limit flexibility, role explosion risk |
| Cloud vs On-Premises IAM | "IAM Architecture - Evolveum" () | Cloud flexibility vs on-premises security control | Cost-effective deployment vs tighter control | Hybrid complexity, data sovereignty concerns |
3. Identity and Access Management (IAM) Fundamentals
3.1. Core Concepts of Identity Management
3.2. Authentication vs Authorization
3.3. IAM Architecture Models
4. Role-Based Access Control (RBAC) in Academic Institutions
4.1. Role Classification: Students, Faculty, Admin, Non-Teaching Staff
- is the set of users,
- is the set of roles,
- is the set of permissions,
- is the set of sessions mapping users to active roles.
4.2. Privilege Mapping and Policy Enforcement
4.3. Preventing Unauthorized Data Exposure
5. Centralized Authentication Frameworks for ERP Systems
- Policy Information Point (PIP): Aggregates attributes for a user .
- Policy Decision Point (PDP): Determines the access decision using input tuples and policy logic .
- Policy Enforcement Point (PEP): Enforces the decision output for resource .
5.1. Single Sign-On (SSO) Integration
5.2. Multi-Factor Authentication Mechanisms
5.3. Directory Services and Federation Protocols
6. Proposed IAM Framework for Educational ERP
6.1. System Architecture
- Identity Repository (): Central database storing all user credentials, attributes, and roles.
- Identity Provider (IdP): Authenticates users and issues signed tokens () for session establishment.
- Policy Decision Point (PDP): Evaluates access requests against a policy set () and identity attributes.
- Policy Enforcement Point (PEP): Gateways in each ERP module enforcing access decisions.
- Access Logs (): Immutable, time-stamped records of all access and authentication events.
6.2. Workflow and Access Flow Diagrams
-
User Authentication: The user submits credentials to the IdP.The IdP validates credentials, and on success, issues a session token ():
- Session Establishment: The user presents to the ERP’s PEP.
- Policy Check: The PEP extracts user role and invokes the PDP to evaluate ifusing role-permission mapping.
- Access Grant/Reject: If authorized, the ERP module grants the requested resource access; otherwise, access is denied.
- Event Logging: All decisions and events are atomically written to the audit log
6.3. Data Logging and Audit Controls
- Periodic Auditing: Automated review scripts calculate statistics such as unauthorized attempts
- Anomaly Detection: Time-series or statistical models flag access patterns deviating from user norms, with equations such as mean-time-between-failures (MTBF) or z-score anomaly detection applied to access frequencies.
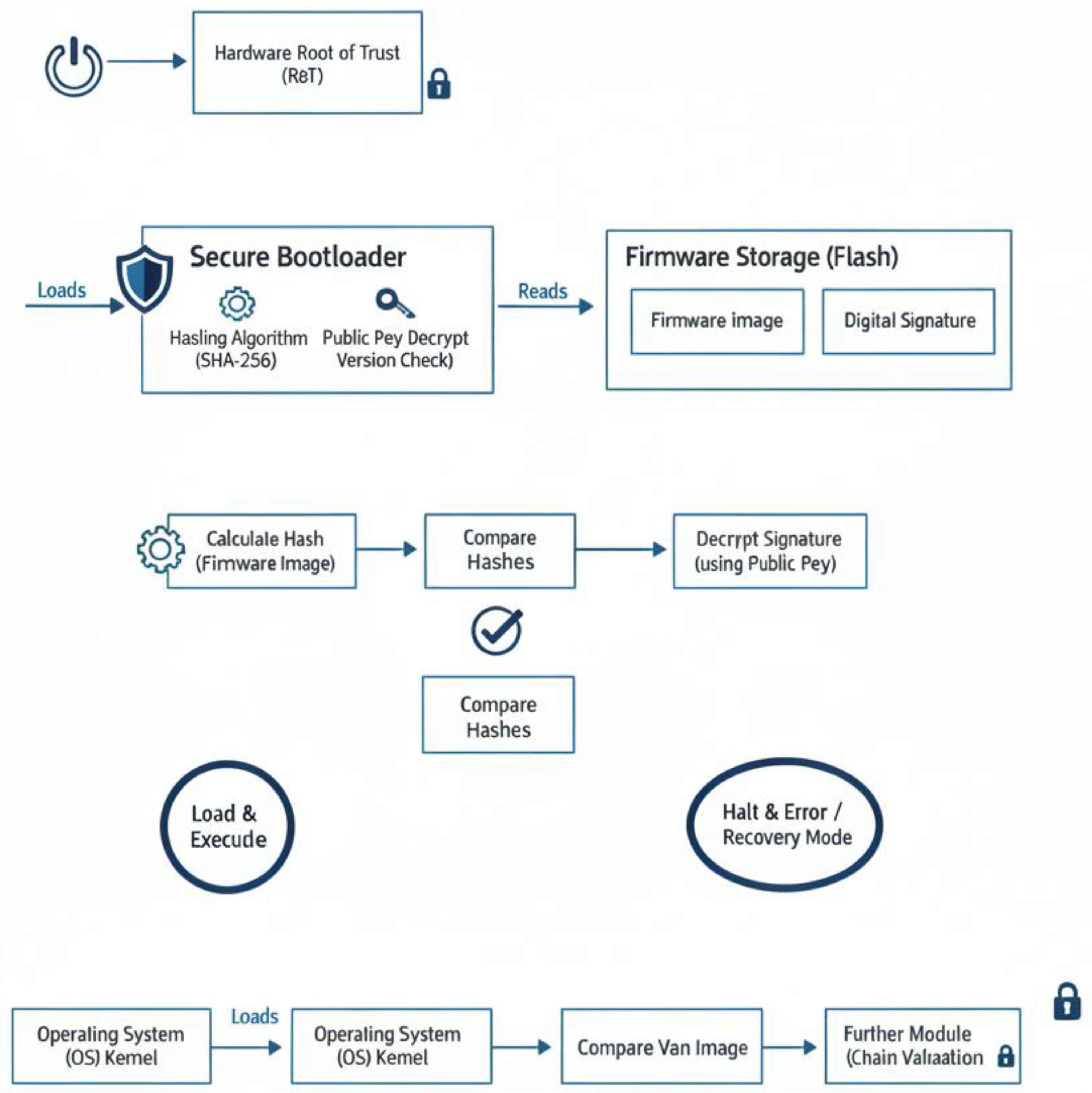
7. Implementation Strategies
7.1. Integration with Existing ERP Modules
7.2. Cloud-Based IAM vs On-Premises IAM
7.3. Identity Provisioning and Lifecycle Management
8. Performance Evaluation and Results
8.1. Metrics for IAM Efficiency
-
User Authentication Success Rate (UASR):High UASR indicates reliable user access without unnecessary disruptions.
- Average Time to Provision (ATP): Measures the average time taken to grant access from the moment a user is onboarded.
- Access Request Response Time (ARRT): Time taken by the IAM system to evaluate and respond to access requests.
- Compliance Rate: Percentage of access requests conforming to policy rules and regulatory requirements.
- IAM User Satisfaction Score: Collected through surveys reflecting ease of use, reliability, and support quality.
8.2. Access Log Analysis
- Frequency Analysis: Identifying common access patterns and peak usage times.
- Anomaly Detection: Flagging abnormal access attempts using statistical models or machine learning techniques, such as z-score analysis or clustering.
- Trend Identification: Tracking repeated failed access or sudden spikes in denied requests that might indicate attempted breaches.
8.3. Reduction in Unauthorized Access Attempts
- Unauthorized Access Attempt Rate (UAAR):
- Incident Response Time (IRT): Time between detection of unauthorized attempts and activation of remediation protocols.
Conclusion and Future Enhancements
References
- Sharma, T., Reddy, D. N., Kaur, C., Godla, S. R., Salini, R., Gopi, A., & Baker El-Ebiary, Y. A. (2024). Federated Convolutional Neural Networks for Predictive Analysis of Traumatic Brain Injury: Advancements in Decentralized Health Monitoring. International Journal of Advanced Computer Science & Applications, 15(4).
- Palaniappan, S., Joshi, S. S., Sharma, S., Radhakrishnan, M., Krishna, K. M., & Dahotre, N. B. (2024). Additive manufacturing of FeCrAl alloys for nuclear applications-A focused review. Nuclear Materials and Energy, 40, 101702.
- Prabhu Kavin, B., Karki, S., Hemalatha, S., Singh, D., Vijayalakshmi, R., Thangamani, M., ... & Adigo, A. G. (2022). Machine learning-based secure data acquisition for fake accounts detection in future mobile communication networks. Wireless Communications and Mobile Computing, 2022(1), 6356152.
- Thamilarasi, V., & Roselin, R. (2021, February). Automatic classification and accuracy by deep learning using cnn methods in lung chest X-ray images. In IOP Conference Series: Materials Science and Engineering (Vol. 1055, No. 1, p. 012099). IOP Publishing.
- Vidyabharathi, D., Mohanraj, V., Kumar, J. S., & Suresh, Y. (2023). Achieving generalization of deep learning models in a quick way by adapting T-HTR learning rate scheduler. Personal and Ubiquitous Computing, 27(3), 1335-1353.
- Arul Selvan, M. (2025). Detection of Chronic Kidney Disease Through Gradient Boosting Algorithm Combined with Feature Selection Techniques for Clinical Applications.
- Kuchukuntla, M., Palanivel, V., & Madhubabu, A. (2023). Tofacitinib citrate-loaded nanoparticle gel for the treatment of alopecia areata: Response surface design, formulation and in vitro-in vivo characterization. Recent Advances in Drug Delivery and Formulation: Formerly Recent Patents on Drug Delivery & Formulation, 17(4), 314-331.
- Selvaraj, G., Kuppusamy, S., & Aswathanarayanan, M. (2025). Sustainable crop recommendation system using seasonally adaptive recursive spectral convolutional neural network for responsible agricultural production. Geomatics, Natural Hazards and Risk, 16(1), 2509619.
- Raja, A. S., Peerbasha, S., Iqbal, Y. M., Sundarvadivazhagan, B., & Surputheen, M. M. (2023). Structural Analysis of URL For Malicious URL Detection Using Machine Learning. Journal of Advanced Applied Scientific Research, 5(4), 28-41.
- Kalaiselvi, B., & Thangamani, M. (2020). An efficient Pearson correlation based improved random forest classification for protein structure prediction techniques. Measurement, 162, 107885.
- Ramesh, T. R., & Kavitha, C. (2013). Web user interest prediction framework based on user behavior for dynamic websites. Life Sci. J, 10(2), 1736-1739.
- Jawaharlal, S., Subramanian, S., Palanivel, V., Devarajan, G., & Veerasamy, V. (2024). Cyclodextrin-based nanosponges as promising carriers for active pharmaceutical ingredient. Journal of Biochemical and Molecular Toxicology, 38(1), e23597.
- Raja, M. W., & Nirmala, D. K. (2016). Agile development methods for online training courses web application development. International Journal of Applied Engineering Research ISSN, 0973-4562.
- Kumar, R. D., Saravanan, K., Nallusamy, C., & Sakthivel, K. (2025, April). Transformative Ai-Driven Tamil Sign Language Recognition and Speech Synthesis Using ViT-CNN. In 2025 3rd International Conference on Artificial Intelligence and Machine Learning Applications Theme: Healthcare and Internet of Things (AIMLA) (pp. 1-6). IEEE.
- Thamilarasi, V., & Roselin, R. (2019). Lung segmentation in chest X-ray images using Canny with morphology and thresholding techniques. Int. j. adv. innov. res, 6(1), 1-7.
- Geeitha, S., & Thangamani, M. (2018). Incorporating EBO-HSIC with SVM for gene selection associated with cervical cancer classification. Journal of medical systems, 42(11), 225.
- Inbaraj, R., & Ravi, G. (2020). A survey on recent trends in content based image retrieval system. Journal of Critical Reviews, 7(11), 961-965.
- Ramesh, T. R., Raghavendra, R., Vantamuri, S. B., Pallavi, R., & Easwaran, B. (2023). IMPROVING THE QUALITY OF VANET COMMUNICATION USING FEDERATED PEER-TO-PEER LEARNING. ICTACT Journal on Communication Technology, 14(1).
- Kumar, J., Radhakrishnan, M., Palaniappan, S., Krishna, K. M., Biswas, K., Srinivasan, S. G., ... & Dahotre, N. B. (2024). Cr content dependent lattice distortion and solid solution strengthening in additively manufactured CoFeNiCrx complex concentrated alloys–a first principles approach. Materials Today Communications, 40, 109485.
- Sakthivel, K., Arularasi, S., Gopinath, S., Vinoth, M., Kowsalya, G., & Lalitha, S. (2025, April). Deep Learning-Based Approach for Accurate Plant Disease Identification Using Image Analysis. In 2025 3rd International Conference on Artificial Intelligence and Machine Learning Applications Theme: Healthcare and Internet of Things (AIMLA) (pp. 1-6). IEEE.
- Thangamani, M., & Thangaraj, P. (2010). Integrated Clustering and Feature Selection Scheme for Text Documents. Journal of Computer Science, 6(5), 536.
- Boopathy, D., & Balaji, P. (2023). Effect of different plyometric training volume on selected motor fitness components and performance enhancement of soccer players. Ovidius University Annals, Series Physical Education and Sport/Science, Movement and Health, 23(2), 146-154.
- Venkatesan, P., Subrahmanyam, P. V. R. S., & Pratap, D. R. (2010). Spectrophotometric determination of pure amitriptyline hydrochloride through ligand exchange on mercuric ion. Int J ChemTech Res, 2(1), 54-56.
- Jaishankar, B., Ashwini, A. M., Vidyabharathi, D., & Raja, L. (2023). A novel epilepsy seizure prediction model using deep learning and classification. Healthcare analytics, 4, 100222.
- Ramesh, T. R., Sreevani, N., Babu, G. J. S., Singh, N., & Kareem, A. (2024, November). Machine Learning Model to Analyse Noisy Data by Scanning Probe Microscope. In 2024 Second International Conference Computational and Characterization Techniques in Engineering & Sciences (IC3TES) (pp. 1-6). IEEE.
- Ramya, K., Vaidyanathan, V., Suriyaa, M., Senthilselvi, A., & Selvan, M. A. (2025, August). Automated Attendance Monitoring System using Real-Time Facial Recognition and Python based Computer Vision Techniques. In 2025 8th International Conference on Circuit, Power & Computing Technologies (ICCPCT) (pp. 1703-1708). IEEE.
- Niasi, K. S. K., Kannan, E., & Suhail, M. M. (2016). Page-level data extraction approach for web pages using data mining techniques. International Journal of Computer Science and Information Technologies, 7(3), 1091-1096.
- Karthikeyan, K., Geetha, B. G., Sakthivel, K., Vignesh, S., Hemalatha, S., & Meena, M. (2025, April). Exploring Machine Learning Algorithms for Identifying Optimal Features to Predict Childbirth Modes. In 2025 3rd International Conference on Artificial Intelligence and Machine Learning Applications Theme: Healthcare and Internet of Things (AIMLA) (pp. 1-5). IEEE.
- Thamilarasi, V., & Roselin, R. (2019). Automatic thresholding for segmentation in chest X-ray images based on green channel using mean and standard deviation. International Journal of Innovative Technology and Exploring Engineering (IJITEE), 8(8), 695-699.
- Hamed, S., Mesleh, A., & Arabiyyat, A. (2021). Breast cancer detection using machine learning algorithms. International Journal of Computer Science and Mobile Computing, 10(11), 4-11.
- Saravanan, V., Sumalatha, A., Reddy, D. N., Ahamed, B. S., & Udayakumar, K. (2024, October). Exploring Decentralized Identity Verification Systems Using Blockchain Technology: Opportunities and Challenges. In 2024 5th IEEE Global Conference for Advancement in Technology (GCAT) (pp. 1-6). IEEE.
- Boopathy, D., & Balaji, D. P. Training outcomes of yogic practices and aerobic dance on selected health related physical fitness variables among tamilnadu male artistic gymnasts. Sports and Fitness, 28.
- Valliappan, K., Vaithiyanathan, S. J., & Palanivel, V. (2013). Direct chiral HPLC method for the simultaneous determination of warfarin enantiomers and its impurities in raw material and pharmaceutical formulation: application of chemometric protocol. Chromatographia, 76(5), 287-292.
- Asaithambi, A., & Thamilarasi, V. (2023, March). Classification of lung chest X-ray images using deep learning with efficient optimizers. In 2023 IEEE 13th Annual Computing and Communication Workshop and Conference (CCWC) (pp. 0465-0469). IEEE.
- Marimuthu, M., Mohanraj, G., Karthikeyan, D., & Vidyabharathi, D. (2023). RETRACTED: Safeguard confidential web information from malicious browser extension using Encryption and Isolation techniques. Journal of Intelligent & Fuzzy Systems, 45(4), 6145-6160.
- Inbaraj, R., & Ravi, G. (2021). Content Based Medical Image Retrieval System Based On Multi Model Clustering Segmentation And Multi-Layer Perception Classification Methods. Turkish Online Journal of Qualitative Inquiry, 12(7).
- Ramya, K., Rithwik, R., VIjaay, E. M., Kumar, S., Senthilselvi, A., & Selvan, M. A. (2025, August). Climate-Aware Plant Phenotyping and Crop Suitability Prediction Using CNN+ XGBoost. In 2025 8th International Conference on Circuit, Power & Computing Technologies (ICCPCT) (pp. 1921-1925). IEEE.
- Thamilarasi, V., & Roselin, R. (2021). U-NET: convolution neural network for lung image segmentation and classification in chest X-ray images. INFOCOMP: Journal of Computer Science, 20(1), 101-108.
- Gangadhar, C., Chanthirasekaran, K., Chandra, K. R., Sharma, A., Thangamani, M., & Kumar, P. S. (2022). An energy efficient NOMA-based spectrum sharing techniques for cell-free massive MIMO. International Journal of Engineering Systems Modelling and Simulation, 13(4), 284-288.
- Ramesh, T. R., Kumar, K., Asha, V., Kumar, S. N., Kumar, M., & Kareem, A. (2024, November). Implementing RNN and LSTM Models to Electrical Load Predictions. In 2024 Second International Conference Computational and Characterization Techniques in Engineering & Sciences (IC3TES) (pp. 1-6). IEEE.
- Sakthivel, K., Ashwin, J., Poongodi, K., & Oviya, S. (2025, March). Image Analysis for Historical Knowledge Discovery and Preservation. In 2025 International Conference on Visual Analytics and Data Visualization (ICVADV) (pp. 895-900). IEEE.
- Raja, M. W. (2024). Artificial intelligence-based healthcare data analysis using multi-perceptron neural network (MPNN) based on optimal feature selection. SN Computer Science, 5(8), 1034.
- Lavanya, R., Vidyabharathi, D., Kumar, S. S., Mali, M., Arunkumar, M., Aravinth, S. S., ... & Tesfayohanis, M. (2023). [Retracted] Wearable Sensor-Based Edge Computing Framework for Cardiac Arrhythmia Detection and Acute Stroke Prediction. Journal of Sensors, 2023(1), 3082870.
- Surendiran, R., Aarthi, R., Thangamani, M., Sugavanam, S., & Sarumathy, R. (2022). A systematic review using machine learning algorithms for predicting preterm birth. International Journal of Engineering Trends and Technology, 70(5), 46-59.
- Thamilarasi, V., Naik, P. K., Sharma, I., Porkodi, V., Sivaram, M., & Lawanyashri, M. (2024, March). Quantum computing-navigating the frontier with Shor's algorithm and quantum cryptography. In 2024 International conference on trends in quantum computing and emerging business technologies (pp. 1-5). IEEE.
- Juliet, P. S., & Janani, V. (2025, May). Detecting Apple and Maize Plant Diseases using GAN and GNN. In 2025 Global Conference in Emerging Technology (GINOTECH) (pp. 1-6). IEEE.
- Radhakrishnan, M., Sharma, S., Palaniappan, S., Pantawane, M. V., Banerjee, R., Joshi, S. S., & Dahotre, N. B. (2024). Influence of thermal conductivity on evolution of grain morphology during laser-based directed energy deposition of CoCrxFeNi high entropy alloys. Additive Manufacturing, 92, 104387.
- Arunachalam, S., Kumar, A. K. V., Reddy, D. N., Pathipati, H., Priyadarsini, N. I., & Ramisetti, L. N. B. (2025). Modeling of chimp optimization algorithm node localization scheme in wireless sensor networks. Int J Reconfigurable & Embedded Syst, 14(1), 221-230.
- Ramesh, T. R., Sharma, A. K., Balaji, T., & Umamaheswari, S. (2025). Utilizing Quantum Networks to Ensure the Security of AI Systems in Healthcare. In AI and Quantum Network Applications in Business and Medicine (pp. 353-370). IGI Global Scientific Publishing.
- Venkatesan, P., Manavalan, R., & Valliappan, K. (2011). Preparation and evaluation of sustained release loxoprofen loaded microspheres. Journal of basic and clinical pharmacy, 2(3), 159.
- Inbaraj, R., & Ravi, G. (2021). Multi Model Clustering Segmentation and Intensive Pragmatic Blossoms (Ipb) Classification Method based Medical Image Retrieval System. Annals of the Romanian Society for Cell Biology, 25(3), 7841-7852.
- Thamilarasi, V., & Roselin, R. (2019). Survey on Lung Segmentation in Chest X-Ray Images. The International Journal of Analytical and Experimental Modal Analysis, 1-9.
- Selvam, P., Faheem, M., Dakshinamurthi, V., Nevgi, A., Bhuvaneswari, R., Deepak, K., & Sundar, J. A. (2024). Batch normalization free rigorous feature flow neural network for grocery product recognition. IEEE Access, 12, 68364-68381.
- Sakthivel, K., Kowsalya, A., Durgadevi, M., & Dhaneswar, R. C. (2025, January). Hybrid Deep Learning for Proactive Driver Risk Prediction and Safety Enhancement. In 2025 International Conference on Multi-Agent Systems for Collaborative Intelligence (ICMSCI) (pp. 1572-1577). IEEE.
- Banu, S. S., Niasi, K. S. K., & Kannan, E. (2019). Classification Techniques on Twitter Data: A Review. Asian Journal of Computer Science and Technology, 8(S2), 66-69.
- Saravanan, V., Upender, T., Ruby, E. K., Deepalakshmi, P., Reddy, D. N., & SN, A. (2024, October). Machine Learning Approaches for Advanced Threat Detection in Cyber Security. In 2024 5th IEEE Global Conference for Advancement in Technology (GCAT) (pp. 1-6). IEEE.
- Reddy, D. N., Venkateswararao, P., Vani, M. S., Pranathi, V., & Patil, A. (2025). HybridPPI: A Hybrid Machine Learning Framework for Protein-Protein Interaction Prediction. Indonesian Journal of Electrical Engineering and Informatics (IJEEI), 13(2).
- Radhakrishnan, M., Sharma, S., Palaniappan, S., & Dahotre, N. B. (2024). Evolution of microstructures in laser additive manufactured HT-9 ferritic martensitic steel. Materials Characterization, 218, 114551.
- Boopathy, D., Singh, S. S., & PrasannaBalaji, D. EFFECTS OF PLYOMETRIC TRAINING ON SOCCER RELATED PHYSICAL FITNESS VARIABLES OF ANNA UNIVERSITY INTERCOLLEGIATE FEMALE SOCCER PLAYERS. EMERGING TRENDS OF PHYSICAL EDUCATION AND SPORTS SCIENCE.
- Thamilarasi, V., Asaithambi, A., & Roselin, R. (2025). ENHANCED ENSEMBLE SEGMENTATION OF LUNG CHEST X-RAY IMAGES BY DENOISING AUTOENCODER AND CLAHE. ICTACT Journal on Image & Video Processing, 15(3).
- Saraswathi, R. J., Mahalingam, T., Devikala, S., Ramesh, T. R., & Sivakumar, K. (2024). Beyond the Current State of the Art in Electric Vehicle Technology in Robotics and Automation. J. Electrical Systems, 20(4s), 2282-2291.
- Inbaraj, R., & Ravi, G. (2020). Content Based Medical Image Retrieval Using Multilevel Hybrid Clustering Segmentation with Feed Forward Neural Network. Journal of Computational and Theoretical Nanoscience, 17(12), 5550-5562.
- Satheesh, N., & Sakthivel, K. (2024, December). A Novel Machine Learning-Enhanced Swarm Intelligence Algorithm for Cost-Effective Cloud Load Balancing. In 2024 International Conference on Innovative Computing, Intelligent Communication and Smart Electrical Systems (ICSES) (pp. 1-7). IEEE.
- Sivakumar, T., Venkatesan, P., Manavalan, R., & Valliappan, K. (2007). Development of a HPLC method for the simultaneous determination of losartan potassium and atenolol in tablets. Indian journal of pharmaceutical sciences, 69(1).
- Narmatha, C., Thangamani, M., & Ibrahim, S. J. A. (2020). Research scenario of medical data mining using fuzzy and graph theory. International Journal of Advanced Trends in Computer Science and Engineering, 9(1), 349-355.
- Vidyabharathi, D., & Mohanraj, V. (2023). Hyperparameter Tuning for Deep Neural Networks Based Optimization Algorithm. Intelligent Automation & Soft Computing, 36(3).
- Mubsira, M., & Niasi, K. S. K. (2018). Prediction of Online Products using Recommendation Algorithm.
- Sureshkumar, T. (2015). Usage of Electronic Resources Among Science Research Scholars in Tamil Nadu Universities A Study.
- RAJA, M. W., PUSHPAVALLI, D. M., BALAMURUGAN, D. M., & SARANYA, K. (2025). ENHANCED MED-CHAIN SECURITY FOR PROTECTING DIABETIC HEALTHCARE DATA IN DECENTRALIZED HEALTHCARE ENVIRONMENT BASED ON ADVANCED CRYPTO AUTHENTICATION POLICY. TPM–Testing, Psychometrics, Methodology in Applied Psychology, 32(S4 (2025): Posted 17 July), 241-255.
- Rao, A. S., Reddy, Y. J., Navya, G., Gurrapu, N., Jeevan, J., Sridhar, M., ... & Anand, D. High-performance sentiment classification of product reviews using GPU (parallel)-optimized ensembled methods.
- Thamilarasi, V. A Detection of Weed in Agriculture Using Digital Image Processing. International Journal of Computational Research and Development, ISSN, 2456-3137.
- Kamatchi, S., Preethi, S., Kumar, K. S., Reddy, D. N., & Karthick, S. (2025, May). Multi-Objective Genetic Algorithm Optimised Convolutional Neural Networks for Improved Pancreatic Cancer Detection. In 2025 3rd International Conference on Data Science and Information System (ICDSIS) (pp. 1-7). IEEE.
- Karuppusamy, C., & Venkatesan, P. (2017). Role of nanoparticles in drug delivery system: a comprehensive review. Journal of Pharmaceutical sciences and Research, 9(3), 318.
- Jayalakshmi, N., & Sakthivel, K. (2024, December). A Hybrid Approach for Automated GUI Testing Using Quasi-Oppositional Genetic Sparrow Search Algorithm. In 2024 International Conference on Innovative Computing, Intelligent Communication and Smart Electrical Systems (ICSES) (pp. 1-7). IEEE.
- Sureshkumar, T., Charanya, J., Kumaresan, T., Rajeshkumar, G., Kumar, P. K., & Anuj, B. (2024, April). Envisioning Educational Success Through Advanced Analytics and Intelligent Performance Prediction. In 2024 10th International Conference on Communication and Signal Processing (ICCSP) (pp. 1649-1654). IEEE.
- Ramesh, T. R., Jackulin, T., Kumar, R. A., Chanthirasekaran, K., & Bharathiraja, M. (2024). Machine learning-based intrusion detection: A comparative analysis among datasets and innovative feature reduction for enhanced cybersecurity. International Journal of Intelligent Systems and Applications in Engineering, 12(12s), 200-206.
- Palaniappan, S., Sharma, S., Radhakrishnan, M., Krishna, K. M., Joshi, S. S., Banerjee, R., & Dahotre, N. B. (2025). Process thermokinetics influenced microstructure and corrosion response in additively in-situ manufactured Ti-Nb-Sn and Ti-Nb alloys. Journal of Manufacturing Processes, 152, 427-441.
- Marimuthu, M., Vidhya, G., Dhaynithi, J., Mohanraj, G., Basker, N., Theetchenya, S., & Vidyabharathk, D. (2021). Detection of Parkinson's disease using Machine Learning Approach. Annals of the Romanian Society for Cell Biology, 25(5), 2544-2550.
- Niasi, K. S. K., & Kannan, E. (2016). Multi Attribute Data Availability Estimation Scheme for Multi Agent Data Mining in Parallel and Distributed System. International Journal of Applied Engineering Research, 11(5), 3404-3408.
- Thangamani, M., & Thangaraj, P. (2013). Fuzzy ontology for distributed document clustering based on genetic algorithm. Applied Mathematics & Information Sciences, 7(4), 1563-1574.
- Nimma, D., Rao, P. L., Ramesh, J. V. N., Dahan, F., Reddy, D. N., Selvakumar, V., ... & Jangir, P. (2025). Reinforcement Learning-Based Integrated Risk Aware Dynamic Treatment Strategy for Consumer-Centric Next-Gen Healthcare. IEEE Transactions on Consumer Electronics.
- Charanya, J., Sureshkumar, T., Kavitha, V., Nivetha, I., Pradeep, S. D., & Ajay, C. (2024, June). Customer Churn Prediction Analysis for Retention Using Ensemble Learning. In 2024 15th International Conference on Computing Communication and Networking Technologies (ICCCNT) (pp. 1-10). IEEE.
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




