Submitted:
15 November 2025
Posted:
18 November 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
- Contributions
- Proposed a Sybil Attack Prevention and Detection Mechanism in VANET (SAPDMV) based on multi-factor authentication, integrating identification number, status, security key, and both minimum and maximum speed thresholds for node verification.
- Enhanced detection accuracy by using precise threshold values, resulting in a high detection rate and reduced false positive and false negative rates compared to existing schemes.
- Implemented and tested the mechanism using Network Simulator-2.35, demonstrating superior performance in key network metrics such as end-to-end delay, throughput, and packet delivery ratio.
- Addressed limitations of previous approaches by allowing nodes without identification numbers to reattempt registration and by verifying both minimum and maximum speed thresholds to prevent misclassification of legitimate and malicious nodes.
- Provided a robust and scalable solution for securing vehicular networks against Sybil attacks, making it suitable for real-world intelligent transportation systems.
2. Related Work
| Author/Reference | Simulation | Method | Strength | Weakness |
| Soyoung Park[7] | NS2/Custom | Time Stamp Series | Detects Sybil nodes using time stamp similarity | Detection slow if RSUs are far apart; ineffective if attacker stays under one RSU |
| Pareek et al.[8] | NS2/Custom | MAC Address Check | Prevents duplicate MAC addresses | MAC addresses can be spoofed by attackers |
| P. Gu et al. [9] | NS2/Custom | Machine Learning (KNN, SVM) | High accuracy in classification | High runtime complexity; limited to light traffic and rational model attacks |
| Hamed et al.[10] | NS2/Custom | Infrastructure Observation | Observes moving dynamics for detection | Requires RSU synchronization; soft identification reduces efficiency |
| Reddy et al.[11] | NS2/Custom | Digital Signatures | Uses encrypted signatures for identity verification | Does not consider vehicle mobility; limited in high mobility/density |
| Sharma et al.[12] | NS2/Custom | Short-lived Pseudo Certificates | Provides privacy and anonymity | Depends on vehicle feedback; does not consider vehicle behavior |
| Eziama et al.[13] | NS2/Custom | Bayesian Neural Network | Probabilistic modeling for node identification | Does not consider mobility patterns; lacks adaptability |
| Saggi & Kaur[6] | NS2/Custom | Neighboring Information | Uses identification and speed threshold | Does not check vehicle status; cannot detect internal malicious nodes |
3. Methodology
3.1. Design and Development of the Proposed Algorithm
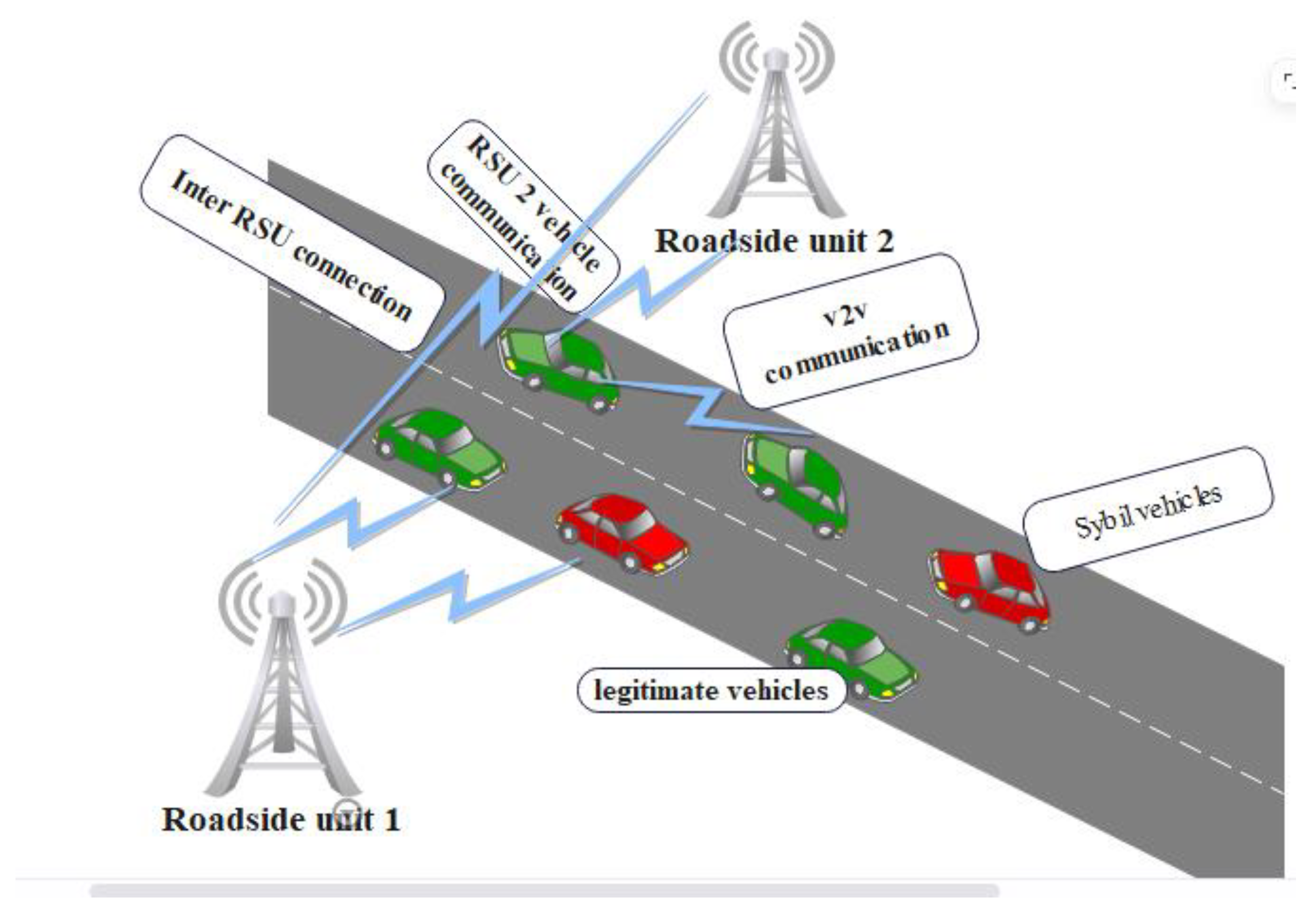
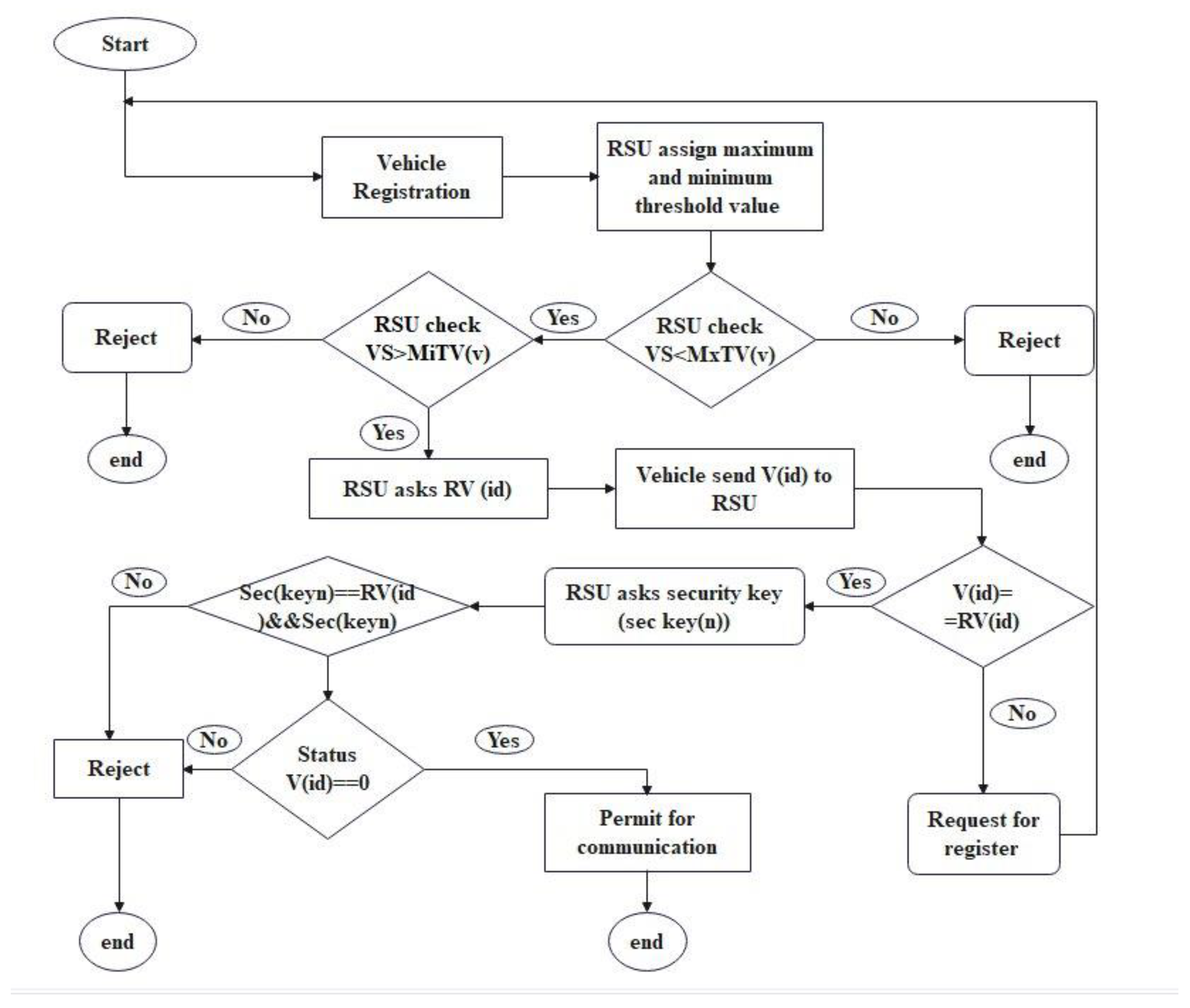
- Each vehicle and Roadside Unit (RSU) is registered by a trusted authority, ensuring only registered vehicles are considered legitimate.
- During registration, the RSU assigns each vehicle an identification number, status, security key, and both minimum and maximum speed threshold values.
- Vehicles must register with the RSU before joining the network, and their legitimacy is verified based on these multi-factor criteria.
- When a vehicle requests to join the network, the RSU checks its identification number, status, security key, and speed against stored values.
- If all criteria are met, the vehicle is permitted to communicate; otherwise, it is rejected as a potential Sybil node.
- The mechanism is implemented and tested using Network Simulator-2.35, with simulation parameters including varying numbers of nodes, malicious nodes, and vehicle speeds.
- The performance of the proposed system is compared with existing schemes and AODV with Sybil attack, focusing on detection rate, false positive rate, false negative rate, end-to-end delay, throughput, and packet delivery ratio.
- 1.
- Vehicle sends a Hello message to the RSU to request network access.
- 2.
- RSU sets maximum and minimum speed threshold values for the vehicle.
- 3.
- RSU compares the vehicle’s speed with the stored threshold values.
- 4.
- RSU requests the vehicle’s identification number and checks it against registered IDs.
- 5.
- RSU asks for the vehicle’s security key and verifies it.
- 6.
- RSU checks the vehicle’s status to determine if it is offline (legitimate) or online (duplicate).
- 7.
- If all checks pass, the vehicle is permitted to communicate; otherwise, it is rejected as a Sybil node.
3.2. Legitimate and Sybil Vehicle Detection
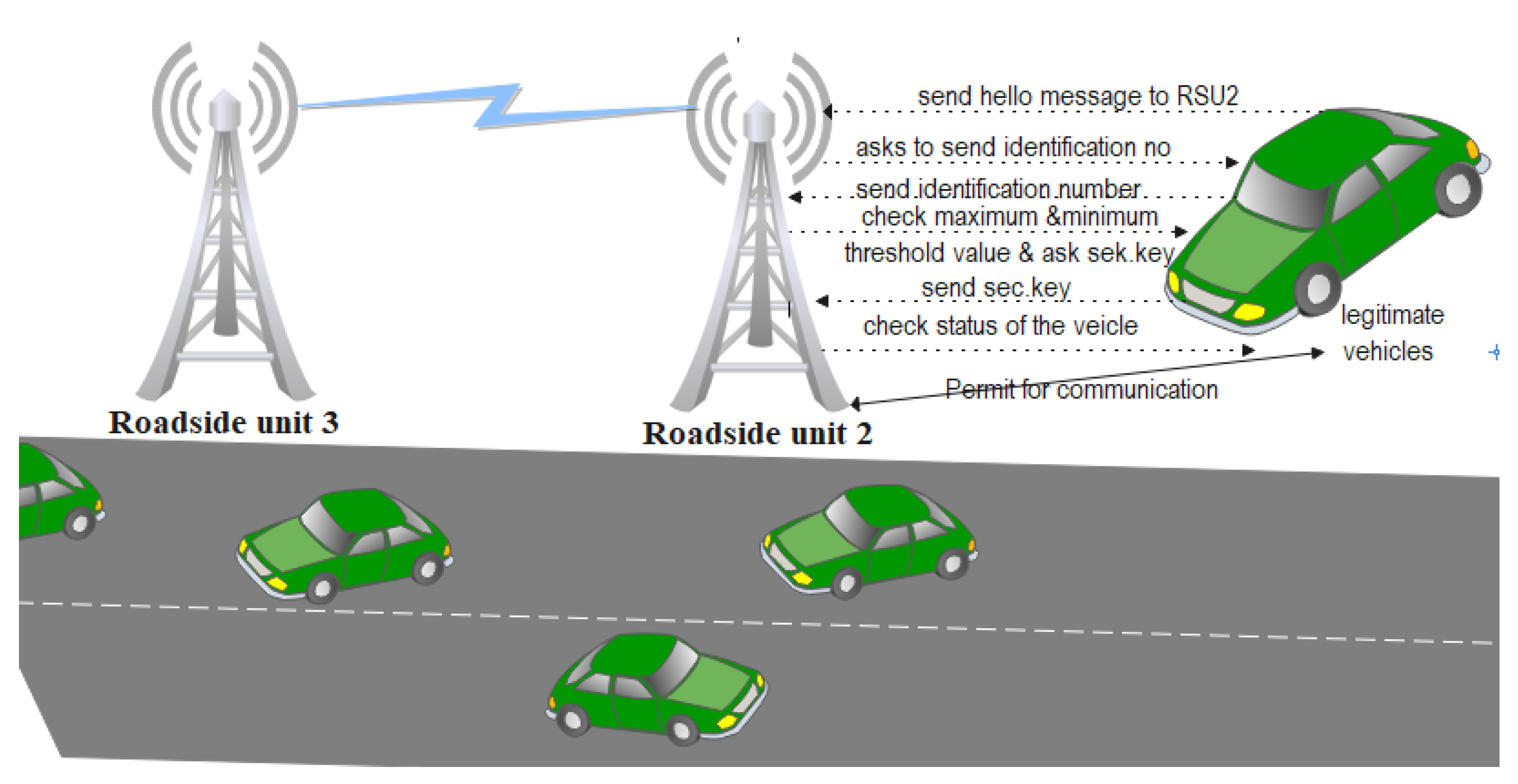
- A vehicle sends a Hello message to the Roadside Unit (RSU) to request network access.
- The RSU sets the maximum and minimum speed threshold values for the vehicle.
- The RSU compares the vehicle’s speed with the stored threshold values.
- If the speed is within the allowed range, the RSU requests the vehicle’s identification number and checks it against the registered vehicle IDs.
- The RSU asks for the vehicle’s security key and verifies it.
- The RSU checks the vehicle’s status to determine if it is offline (legitimate) or online (duplicate).
- If all checks pass identification matches, status is offline, security key is correct, and speed is within the threshold the vehicle is recognized as legitimate and permitted to communicate within the network.
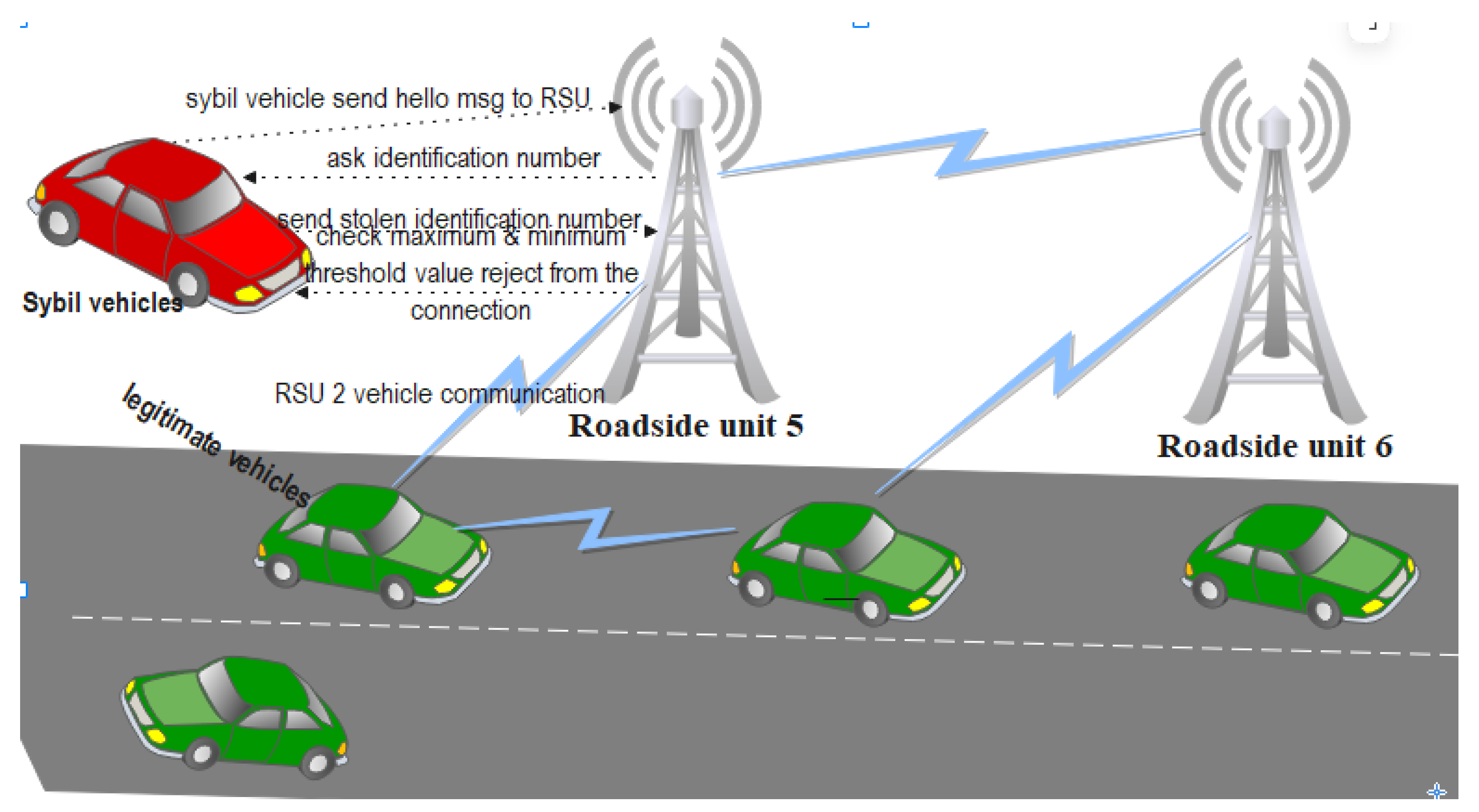
- A vehicle sends a Hello message to the Roadside Unit (RSU) to request network access.
- The RSU sets the maximum and minimum speed threshold values for the vehicle.
- The RSU compares the vehicle’s speed with the stored threshold values.
- If the speed is within the allowed range, the RSU requests the vehicle’s identification number and checks it against the registered vehicle IDs.
- The RSU asks for the vehicle’s security key and verifies it.
- The RSU checks the vehicle’s status to determine if it is offline (legitimate) or online (duplicate).
- If all checks pass identification matches, status is offline, security key is correct, and speed is within the threshold the vehicle is permitted to communicate.
- If any check fails (e.g., fake or stolen identification, speed outside threshold, status online, or incorrect security key), the vehicle is detected as a Sybil node and rejected from the network.
3.3. Experimental Setup
Simulation
4. Result and Discussions
4.1. Analyzing Trace Files
4.2. Performance Metrics
- Detection Rate: The proportion of Sybil attacks correctly identified by the system.
- False Positive Rate: The ratio of legitimate vehicles incorrectly flagged as Sybil nodes.
- False Negative Rate: The ratio of Sybil vehicles that are not detected by the system.
- End-to-End Delay: The time taken for a packet to travel from source to destination, indicating network responsiveness.
- Throughput: The amount of data successfully transmitted per unit time, reflecting network efficiency.
- Packet Delivery Ratio (PDR): The percentage of packets successfully delivered to their destination, measuring reliability.
- Computation Time: The time required for authentication and verification processes, affecting real-time performance.
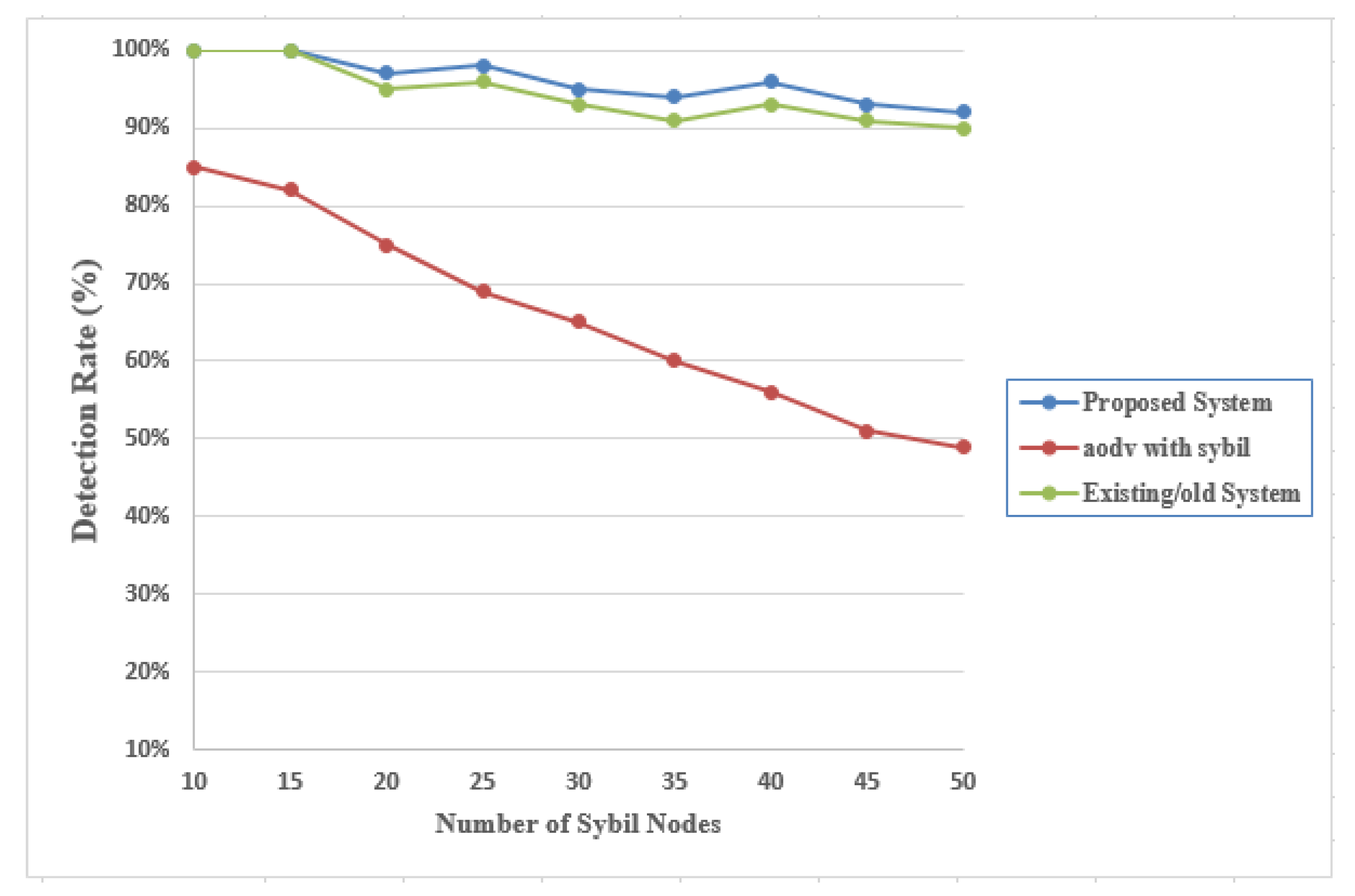
4.2.1. Malicious Node Detection Rate (DR)
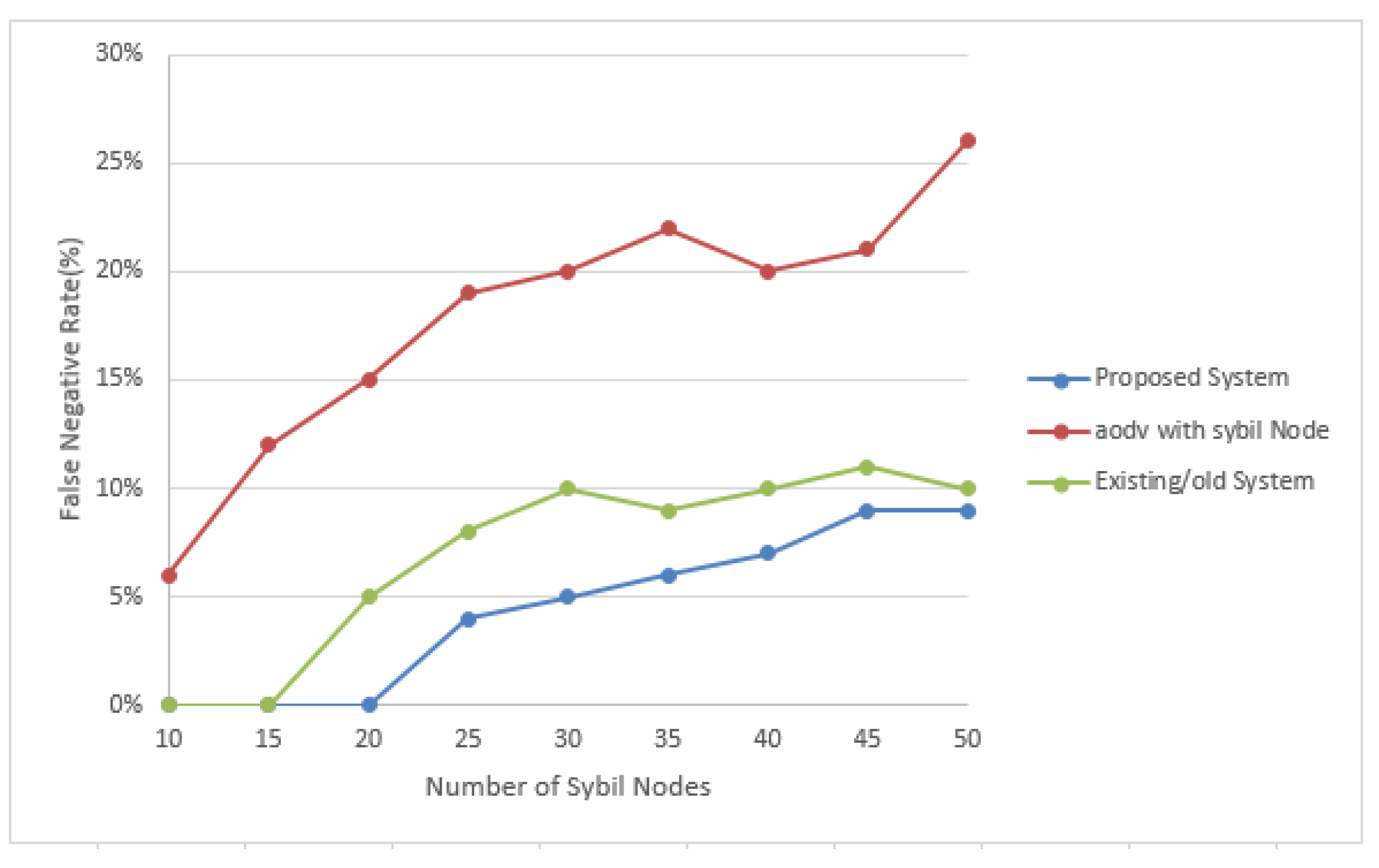
4.2.2. False Negative Rate (FNR)
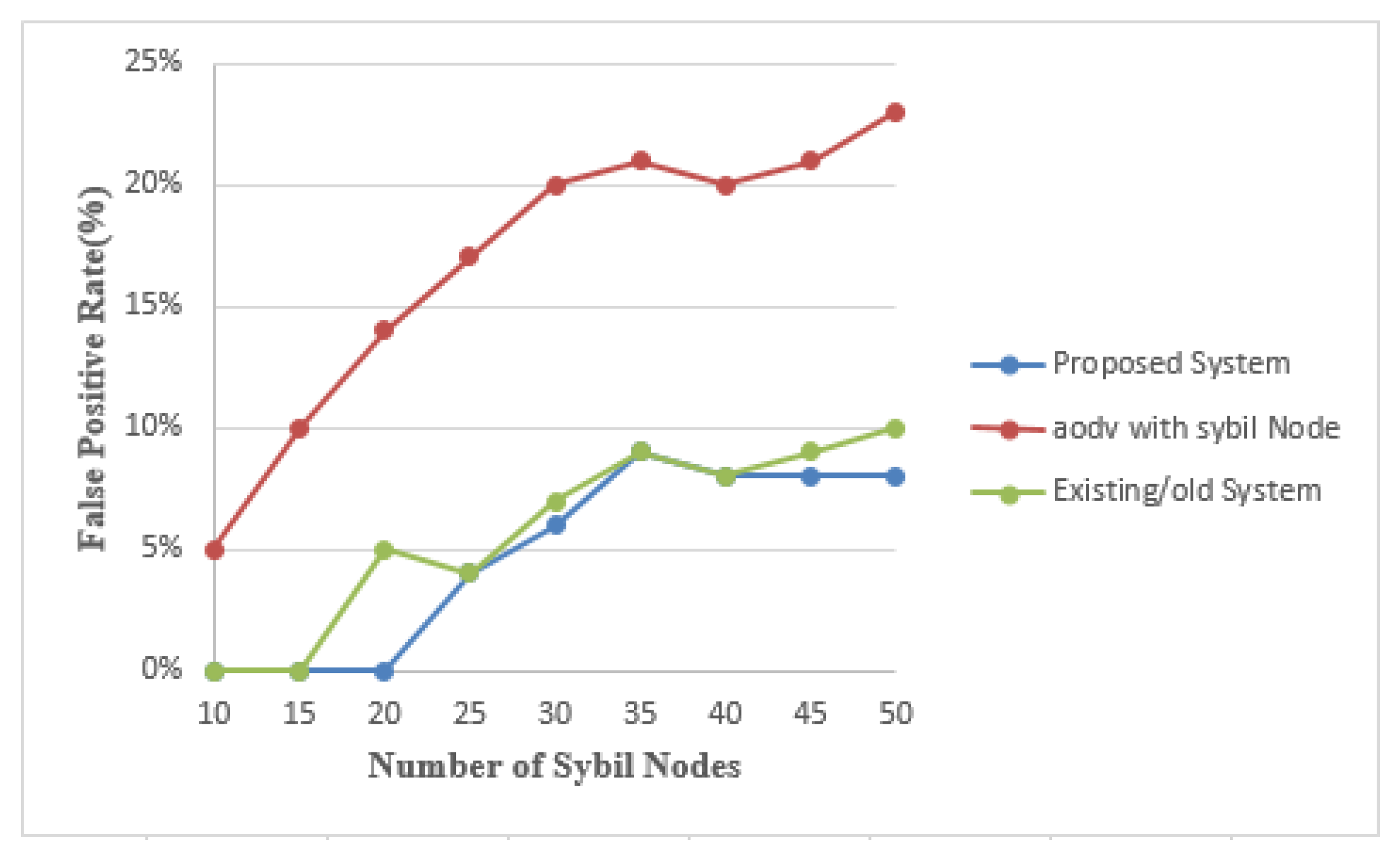
4.2.3. False Positive Rate (FPR)
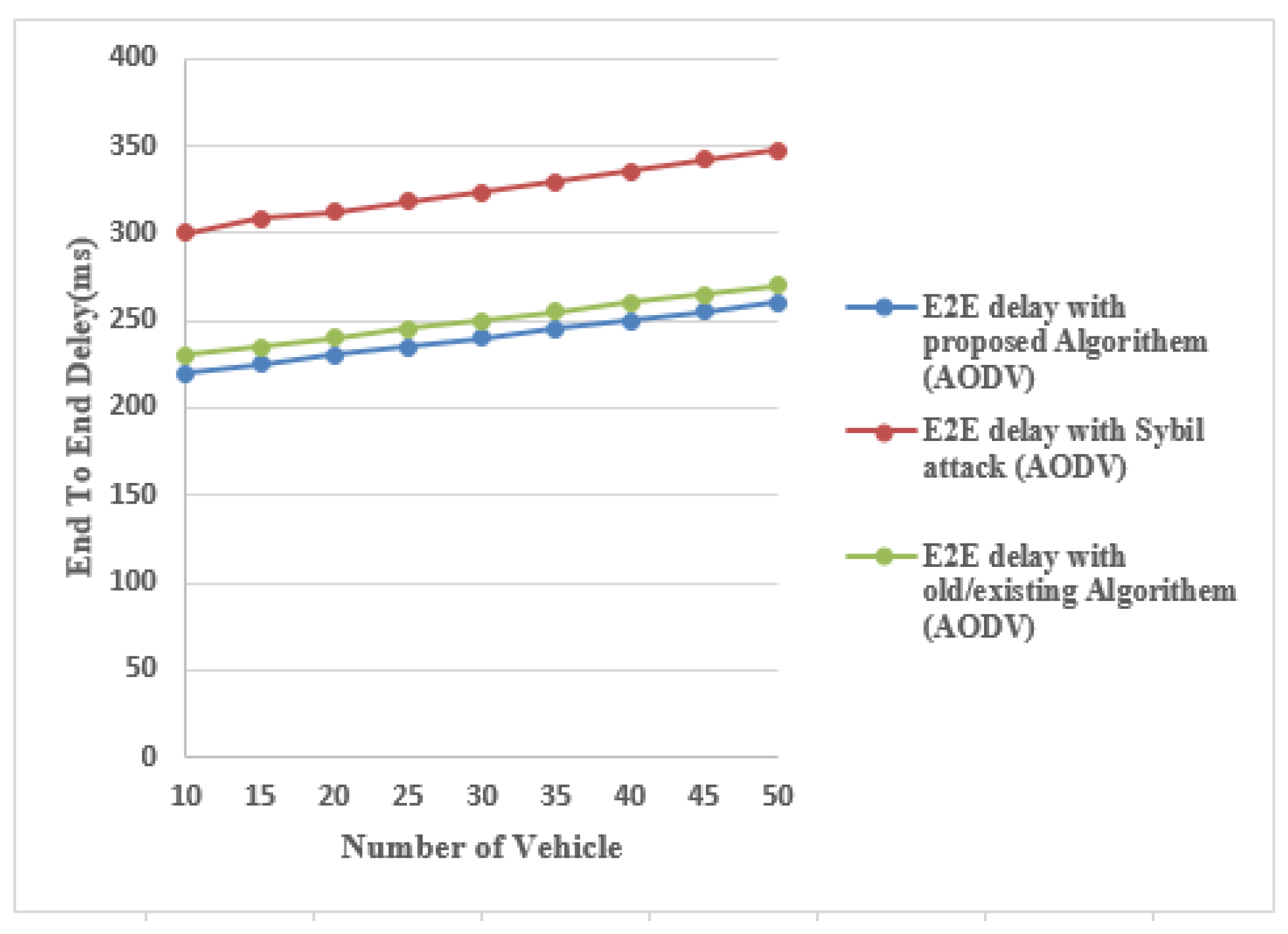
4.2.4. End-to-End Delay (E2E):
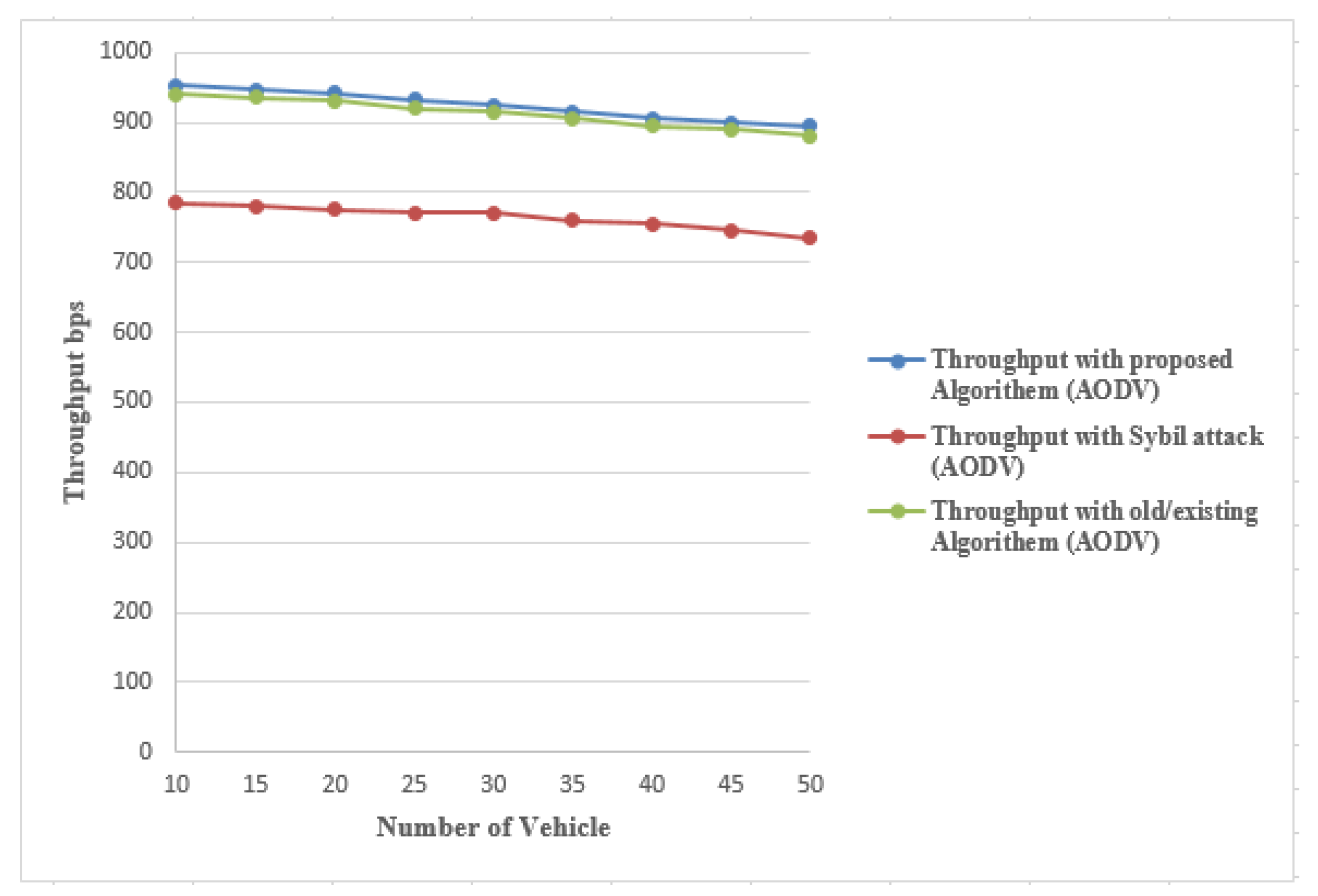
4.2.5. Throughput
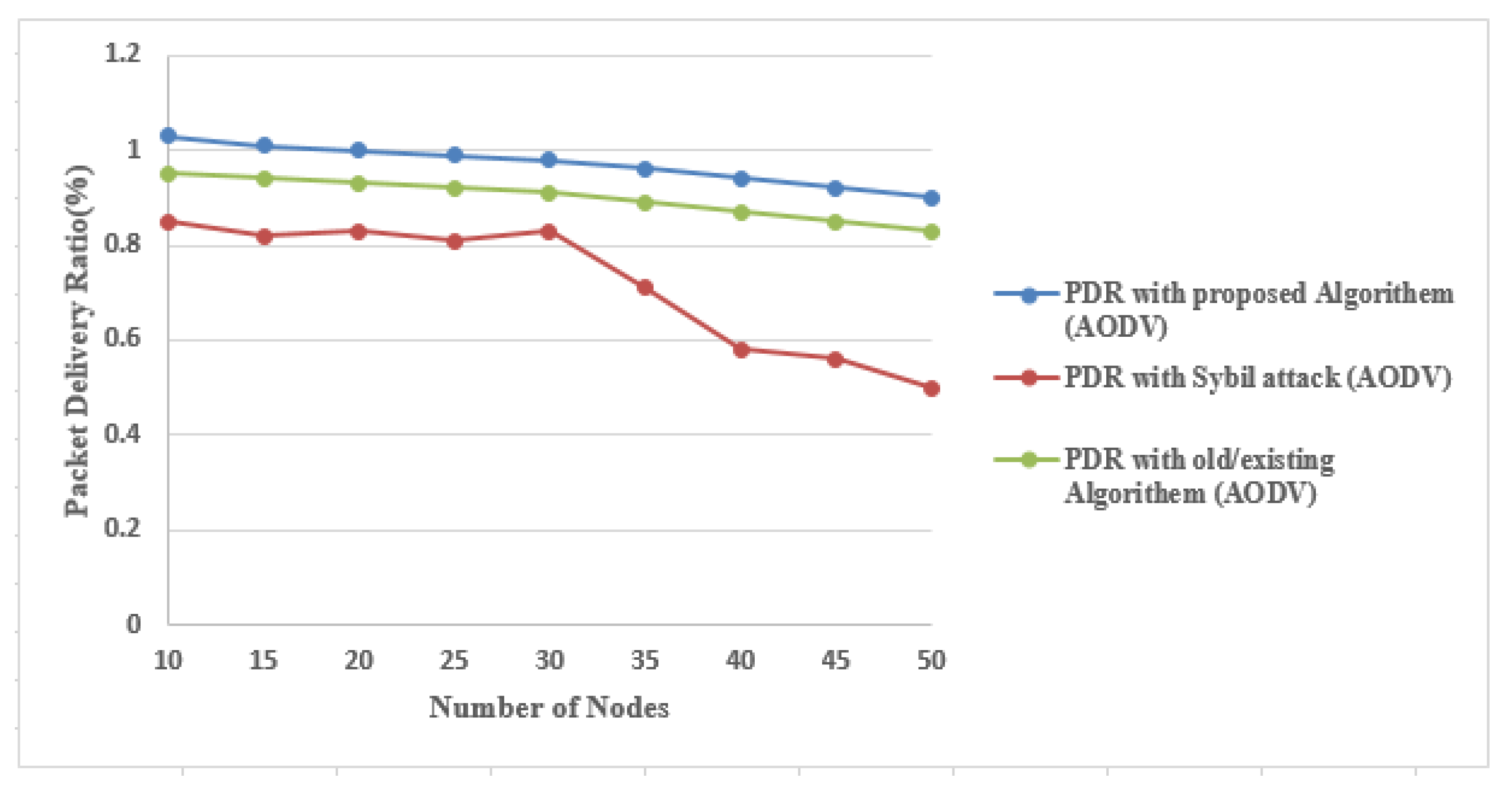
4.2.6. Packet Deliver Ratio (PDR)
5. Conclusions
References
- K. Tanuja, “A Survey on VANET Technologies,” vol. 121, no. 18, pp. 1–9, 2015.
- P. Gu, R. Khatoun, Y. Begriche, A. Serhrouchni, and T. Paristech, “Vehicle Driving Pattern Based Sybil Attack Detection,” pp. 1282–1288, 2016. [CrossRef]
- S. A. Syed, “Merged technique to prevent SYBIL Attacks in VANETs,” 2019 Int. Conf. Comput. Inf. Sci., pp. 1–6, 2019.
- I. Transportation, S. Committee, I. Vehicular, and T. Society, IEEE Guide for Wireless Access in Vehicular Environments ( WAVE ) Architecture IEEE Vehicular Technology Society. 2013.
- M. Khalil and M. A. Azer, “Scheme in Vehicular Ad-Hoc Networks,” pp. 184–186, 2018.
- M. K. Saggi, “Isolation of Sybil Attack in VANET using Neighboring Information,” pp. 46–51, 2015.
- J. Grover, “A Sybil Attack Detection Approach using Neighboring Vehicles in VANET,” pp. 151–158, 2011.
- A. Pareek, “Detection and Prevention of Sybil Attack in MANET using MAC Address,” vol. 122, no. 21, pp. 20–23, 2015.
- P. Gu, R. Khatoun, Y. Begriche, A. Serhrouchni, and T. Paristech, “k-Nearest Neighbours Classification Based Sybil Attack Detection in Vehicular Networks”.
- H. Hamed, “Sybil Attack Detection in Urban VANETs Based on RSU Support,” Electr. Eng. (ICEE), Iran. Conf., pp. 602–606, 2018. [CrossRef]
- D. S. Reddy and V. Bapuji, “Sybil Attack Detection Technique Using Session Key Certificate in Vehicular Ad Hoc Networks,” pp. 2–6.
- A. K. Sharma, “Sybil Attack Prevention and Detection in Vehicular Ad hoc Network,” pp. 594–599, 2016.
- E. Eziama, K. Tepe, A. Balador, K. S. Nwizege, and L. M. S. Jaimes, “Malicious Node Detection in Vehicular Ad-Hoc Network Using Machine Learning and Deep Learning,” 2018 IEEE Globecom Work. (GC Wkshps), pp. 1–6, 2018.
- S. Agrawal and R. Lingawar, “Application of Ns2 To Overcome Computer Networks Attacks,” World Res. J. Comput. Archit., vol. 1, no. 1, pp. 6–10, 2012.
| Parameters | Value |
| Simulator NS2 | Version Ns-allinone-2.35 |
| Simulation Area (Grid Size) | 3m x 3000m |
| Total number of nodes | 50 |
| Number Simulated node | 10,15,20,25,30,35,40,45,50 |
| Number of malicious nodes | 36,38,40,49 |
| Number of static nodes | 21,22,24,27,28,29,30,33 |
| Maximum Vehicle speed | 50m/s |
| Minimum vehicle speed | 20m/s |
| Routing protocol | AODV |
| Packet size | 512kb |
| Packet type | TCP |
| Node Communication range | 3000m |
| Simulation Time | 150sec |
| Antenna model | Omnidirectional Antenna |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





