1. Introduction
1.1. The Problem
Verification problem: When AI agents perform work (data labeling, model inference, web scraping), requesters have no cryptographic guarantee the work was actually done. This creates a trust bottleneck that prevents large-scale coordination.
Capital inefficiency: Agents with proven computational capability cannot monetize this capability until they find work. Their demonstrated capacity sits idle, generating no return. Requesters who need compute in the future have no mechanism to secure capacity in advance.
Composition problem: Complex AI tasks require multiple specialized agents working in sequence (scrape → analyze → report → visualize). Current systems cannot cryptographically prove that each step correctly used outputs from previous steps, making multi-agent workflows unverifiable.
1.2. The Opportunity
Three technological shifts create a new opening:
AI proliferation – exponential agent growth drives demand for verifiable work coordination.
Layer-2 scalability – sub-$0.01 transactions make on-chain verification economical.
DeFi maturity – existing lending protocols can accept new collateral types with proper risk management.
ExecMesh transforms verified compute into programmable collateral and enables the formation of verifiable computational supply chains.
2. Design Goals and Assumptions
2.1. Design Goals
G1: Verifiable Execution Without Trust. Each task’s correctness must be provable via succinct cryptographic evidence without reliance on intermediaries.
G2: Capital Efficiency for Agents. Agents with verified capacity can use compute credits as collateral to obtain capital with graduated risk management.
G3: Composable Workflows. Complex pipelines involving multiple agents are verifiable end-to-end through proof composition.
G4: Economic Sustainability. Fees and incentives ensure self-sustaining operations with realistic bootstrap strategy.
G5: Security First. Multi-source oracles, graduated liquidation, and post-quantum migration roadmap.
2.2. Assumptions
Assumption A1 (Honest Majority). Most agents act rationally to preserve reputation; slashing and challenge periods deter malicious behavior.
Assumption A2 (Oracle Reliability). Price feeds from multiple independent sources with maximum 15% deviation per update; fallback to last known good price with circuit breaker.
Assumption A3 (L2 Viability). Transaction costs on rollups remain below $0.10 per proof verification.
Assumption A4 (zkSNARK Security). Groth16 on BN254 remains secure under the discrete log assumption; at least one trusted setup participant is honest.
3. System Architecture
3.1. Overview
The ExecMesh protocol consists of five interconnected layers that together realize the Proof-of-Execution (PoX) system:
Core Protocol Layer – intent registry, escrow, reputation staking.
Verification Layer – zkSNARK validation and recursive composition.
Financial Primitive Layer – collateral vault, compute futures, AMM liquidity with secure oracles.
Oracle Layer – decentralized multi-source pricing aggregation.
Application Layer – web wallet, CLI, SDK interfaces.
| Listing 1: ExecMesh Layered Architecture |
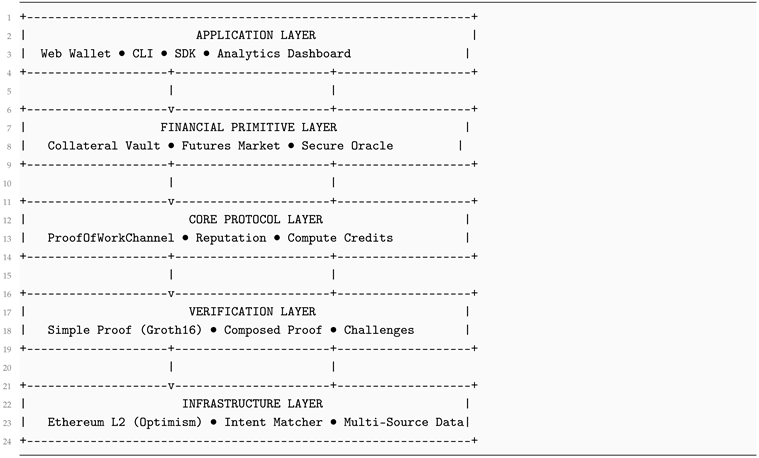 |
3.2. Core Protocol Layer
The core contract, ProofOfWorkChannel.sol, manages job postings and escrow. Participants interact through an intent lifecycle:
Post Intent: Requester specifies reward, deadline, and capability.
Accept: Agent stakes reputation and agrees to perform work.
Complete: Agent executes the job off-chain and generates a zk proof.
Submit Proof: Proof and output hash are recorded on-chain.
Challenge Period: A 1-hour window permits disputes.
Settle: Escrow releases payment; compute credits are minted.
Reputation and compute credits both use ERC-1155 token standards. Reputation tokens are non-transferable and subject to slashing; compute credits are transferable receipts representing verified capacity.
3.3. Verification Layer
3.3.1. Simple Proof Verification
For atomic tasks, the protocol validates Groth16 proofs [
1]. Given circuit
C, inputs
, and verification key
:
On success, the transaction finalizes and credits are minted.
3.3.2. Composed Proof Verification
Complex workflows are chains of dependent tasks. Let denote the proof for step i with public hash , where is the step’s output. A composition proof demonstrates that the prover knew the actual outputs and correctly computed a new result .
Definition 1 (Composed Proof)
. Given dependency hashes , a composed proof is valid if:
and proves knowledge of and transformation f satisfying the above.
Verification Logic (Solidity).
| Listing 2: Verification Logic (Solidity) |
 |
3.3.3. ZK Circuit for Composition
Implemented in Circom:
| Listing 3: composition.circom (simplified) |
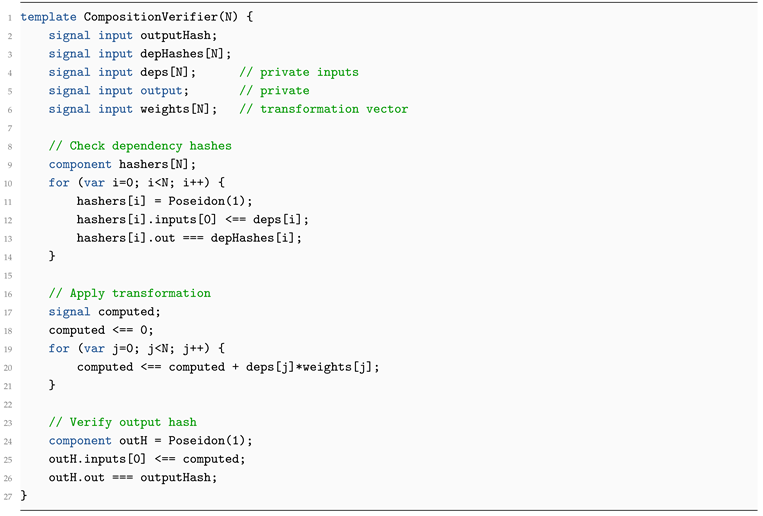 |
What it Proves.
The prover knows dependency data that hash to the declared values and that the final output was derived by an agreed computation f. Actual data remain private; only hashes and succinct proof are public.
3.4. Gas Optimization Strategies
Batch verification: aggregate multiple proofs per tx.
Proof recursion: nested Groth16 (phase 2).
Calldata compression: packed bytes for proof elements.
L2 deployment: Optimism/Arbitrum yields cost reduction.
| Scenario |
Gas |
Cost (L2 est.) |
| Simple proof |
150k |
$0.005 |
| 3-dependency composition |
280k |
$0.009 |
| Batch of 10 |
800k |
$0.027 |
4. Financial Primitives
ExecMesh transforms verified computation into programmable capital through a set of smart-contract primitives deployed on Layer 2 networks. These extend traditional DeFi mechanisms by introducing compute-backed assets.
4.1. Compute Credit Vault
The ComputeCreditVault contract locks ERC-1155 compute credits as collateral and interfaces with external lending protocols such as Aave or Compound.
Data Structure.
| Listing 4: Locked position structure (production implementation) |
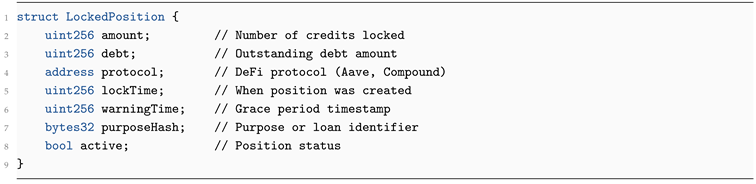 |
Lifecycle.
Agent mints compute credits after verified completion.
Credits are deposited into the Vault via lockAsCollateral.
Lending protocol queries value through secure adapter contract.
Borrower obtains liquidity up to an LTV ratio r (typically 66%).
Health factor monitored continuously with graduated liquidation.
Upon repayment, credits are unlocked and returned.
Adapter Interface.
| Listing 5: Aave Compute Adapter (corrected) |
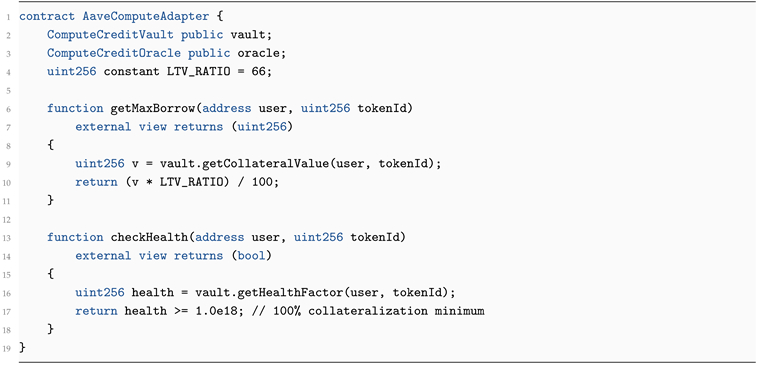 |
4.2. Compute Futures Market
A secondary contract, ComputeFutures, allows trading of future compute commitments.
| Listing 6: Compute future struct |
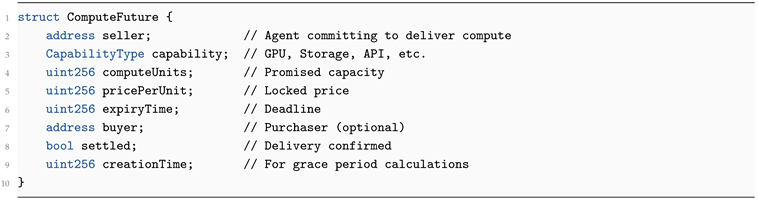 |
Use Cases.
Hedging. Requesters fix future compute prices.
Speculation. Traders arbitrage between spot and future prices.
Yield. Agents monetize idle capacity ahead of delivery.
Settlement occurs when a verified intent corresponding to the future is submitted; failure to deliver results in forfeiture and reputation slashing.
4.3. Secure Oracle System
Pricing of compute credits relies on a secure multi-source oracle service that aggregates data with robust safeguards:
| Listing 7: Secure Multi-Source Oracle (production implementation) |

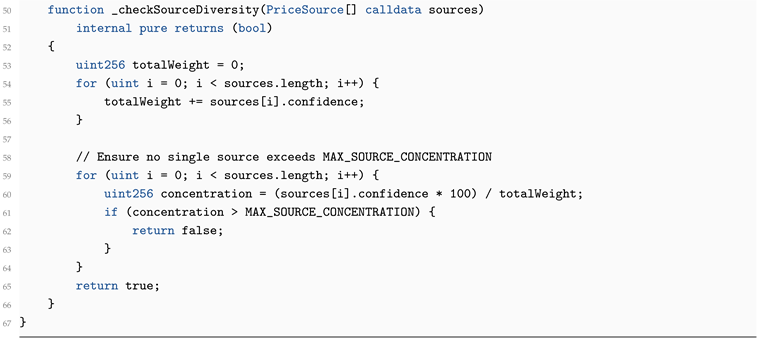
|
4.3.0.6. Oracle Data Sources & Weights
The protocol does not enforce fixed weights on-chain. Instead, it ensures no single source exceeds 40% of total confidence weight. This provides flexibility while preventing manipulation.
Recommended weights for oracle operators:
Historical ExecMesh marketplace data (30% suggested weight)
External cloud markets (AWS, GCP, Azure - 25% suggested)
Decentralized compute (Akash, Render - 20% suggested)
Uniswap V3 on-chain liquidity pools (15% suggested)
Futures market time-weighted average (10% suggested)
These are guidelines; the on-chain enforcement is the 40% concentration limit per source, providing both flexibility and security.
5. Economic Model
5.1. Conservative Market Analysis
Global compute market: $500B+ (Gartner 2024)
AI/ML compute segment: $50B growing 40% YoY
Decentralized compute: $500M (1% penetration)
Addressable market for ExecMesh: AI agent workflows = $5B by 2028
5.2. Bootstrap Strategy: From Zero to Critical Mass
Phase 1: Seeded Liquidity (Months 0-3)
Protocol treasury provides $100k in initial liquidity incentives
10x rewards for first 100 agents and 50 requesters
Zero fees for first 1,000 jobs
Target: 100 jobs/month @ $50 average (realistic micro-tasks)
Focus: Data labeling partnerships with AI training companies
Phase 2: Organic Growth (Months 3-12)
Reduced incentives: 3x rewards for strategic capabilities
-
Tiered fee structure:
- –
Micro jobs (<$10): 0.1% (loss leader)
- –
Standard ($10-$100): 1.0%
- –
Enterprise (>$100): 0.5% (volume discount)
Target: 1,000 jobs/month by month 12
Expand to research automation and content generation
Phase 3: Self-Sustaining (Year 2+)
Standard fees: 1% average across all job sizes
Target: 5,000-10,000 jobs/month
Total addressable market: $50B compute market × 2% capture = $1B potential
5.3. Conservative Revenue Projections
Break-even Analysis
Table 1.
Realistic Three-Year Revenue Projection.
Table 1.
Realistic Three-Year Revenue Projection.
| Phase |
Jobs/Month |
Avg. Value |
Fee Rate |
Monthly Revenue |
Annual |
| Bootstrap (Y1) |
100 → 1,000 |
$50 |
0.5% |
$1,500 |
$18,000 |
| Growth (Y2) |
1,000 → 5,000 |
$75 |
1.0% |
$22,500 |
$270,000 |
| Scale (Y3) |
5,000 → 10,000 |
$100 |
1.0% |
$75,000 |
$900,000 |
5.4. Value Accrual
Agents earn ETH for jobs, reputation tokens for trust, and compute credits for collateralization or sale. Requesters gain verifiable output and predictable pricing. The protocol captures fees from transactions and liquidity pools.
5.5. Tokenomics
If governance token
$EXEC is introduced, supply and allocation are:
| Category |
Share |
Vesting |
| Community Rewards |
30% |
10 yr emission |
| Team & Contributors |
20% |
4 yr vesting |
| Treasury |
20% |
– |
| Investors |
15% |
2 yr vesting |
| Liquidity Mining |
10% |
– |
| Grants & Partnerships |
5% |
– |
Utility includes governance, staking, and boosted rewards.
5.6. Fee Structure
| Action |
Fee |
Notes |
| Job Settlement |
0.1-1.0% |
Tiered by size |
| Future Creation |
0.1% |
of notional value |
| Future Settlement |
0.5% |
of notional value |
| Collateral Unlock |
0.1% |
on release |
| Liquidation |
2-5% |
graduated penalties |
5.7. Market Dynamics
Supply Side: Low entry barriers for agents; reputation and specialization drive premiums.
Demand Side: Pay-per-use model with transparent, verifiable outcomes.
Equilibrium: Price discovery via futures, quality via reputation, capacity planning via collateral.
6. Security Model & Risk Mitigation
6.1. Enhanced Threat Model
We categorize threats by adversary class with graduated mitigations:
Malicious Agent: attempts to submit forged proofs or double-spend reputation.
Malicious Requester: disputes valid work to avoid payment.
Oracle Manipulator: feeds distorted price data to profit from liquidation.
Market Manipulator: abuses futures to influence spot pricing.
Quantum Adversary: future threat to cryptographic foundations.
6.2. Smart-Contract Security
Reentrancy protection and checked arithmetic (Solidity ).
Access control via OpenZeppelin roles with multi-sig for critical functions.
Pausable emergency circuit breakers with time-lock governance.
Proxy upgradeability with 7-day timelock for major changes.
Comprehensive test coverage () and formal verification for critical circuits.
6.3. Enhanced Liquidation Mechanisms
Multi-tier Liquidation Thresholds
Rather than a single 150% collateralization ratio, we implement graduated margins:
Table 2.
Graduated Liquidation Safeguards.
Table 2.
Graduated Liquidation Safeguards.
| Health Factor |
State |
Action |
Penalty |
|
Healthy |
None |
0% |
|
Warning |
Email/on-chain alert |
0% |
|
At Risk |
Collateral top-up required |
0% |
|
Critical |
Partial liquidation (50%) |
2% |
|
Underwater |
Full liquidation |
5% |
Liquidation Safeguards Implementation
| Listing 8: Safe Graduated Liquidation (production implementation) |
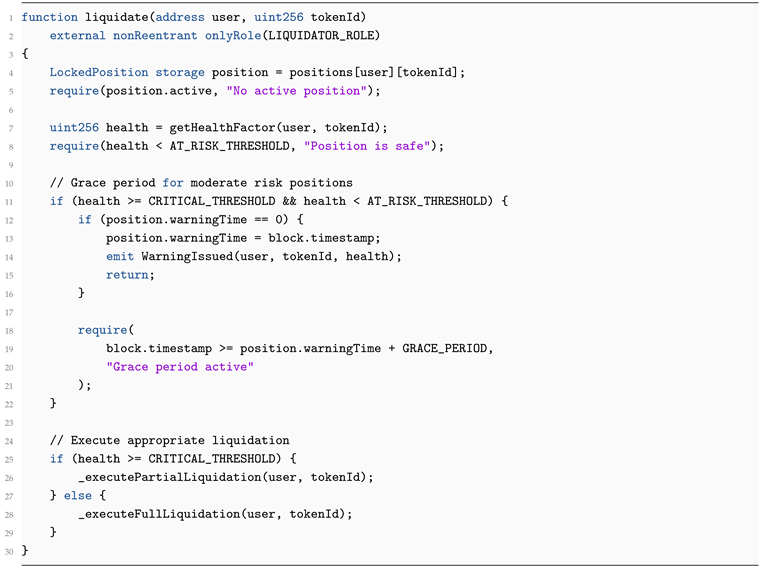 |
6.4. Oracle and Market Security
Multi-source aggregation with weighted median calculation
Maximum 15% deviation per update with circuit breaker
1-hour staleness threshold for price data
Maximum 40% concentration per source to prevent manipulation
Emergency freeze function for extreme market conditions
7. Competitive Positioning & Market Differentiation
7.1. Unique Value Proposition Matrix
Table 3.
ExecMesh vs. Alternative Solutions.
Table 3.
ExecMesh vs. Alternative Solutions.
| Capability |
ExecMesh |
Akash |
Render |
Giza |
Chainlink |
| Verifiable Compute |
✓✓ |
✗ |
✗ |
✓ |
✗ |
| Financial Primitives |
✓✓ |
✗ |
✗ |
✗ |
Partial |
| Multi-Agent Workflows |
✓✓ |
Partial |
✗ |
✗ |
✗ |
| Compute Futures |
✓✓ |
✗ |
✗ |
✗ |
✗ |
| EVM Native |
✓✓ |
✗ |
✗ |
✗ |
✓✓ |
| Proving Cost |
$0.005 |
N/A |
N/A |
$0.10+ |
N/A |
| Time to Proof |
<2s |
N/A |
N/A |
10s+ |
N/A |
| Collateralization |
✓✓ |
✗ |
✗ |
✗ |
✗ |
7.2. Strategic Focus: AI Agent Economy
While competitors focus on infrastructure replacement, ExecMesh targets the emerging AI agent coordination market:
Initial Wedge: Data Labeling Pipelines ($2B Market)
Scrape: Web data collection with proof of source integrity
Label: Human/AI labeling with quality verification proofs
Verify: Cross-validation with consensus proofs
Train: Model training with reproducible dataset proofs
Expansion Verticals
Research Automation: Literature review → Analysis → Drafting → Peer review
Content Generation: Research → Outline → Draft → Edit → Publish
Financial Analysis: Data gathering → Modeling → Risk assessment → Reporting
7.3. Competitive Advantages
First-mover in compute financialization - No other protocol offers compute credits as DeFi collateral
Recursive proof composition - Unique capability for multi-agent workflows
EVM-native deployment - Immediate compatibility with existing DeFi ecosystem
Graduated risk management - Superior collateral protection vs. traditional DeFi
8. Technical Implementation
8.1. Smart-Contract Suite
Target coverage , gas k per composed proof, formal verification for critical financial functions.
| Listing 9: Enhanced Smart Contract Suite |
 |
8.2. Off-Chain Infrastructure
Intent Matcher: REST API + WebSocket for job discovery and ML-based agent scoring.
Proof Generator: Circom circuit compilation, witness and Groth16 proof creation with optimization.
Oracle Service: Multi-source price aggregation, anomaly detection, and secure on-chain updates.
Analytics Service: Market statistics, gas monitoring, health factor alerts.
Security Monitoring: 24/7 threat detection and emergency response system.
8.3. Frontend Applications
Web Wallet (React + TypeScript) for human interaction; CLI tool for agent automation; analytics dashboard built on Grafana + PostgreSQL with real-time health monitoring.
9. Roadmap & Future Work
Phase 1 (Completed): PoX v1, Merkle proofs, reputation system.
Phase 2 (Q4 2025): Deploy Secure Vault, Futures Market, Multi-source Oracle, Aave adapter.
Phase 3 (Q1 2026): Deploy composition circuits, launch workflow marketplace, data labeling partnerships.
Phase 4 (Q2–Q3 2026): Mainnet deployment (Optimism/Base), compute provider partnerships, formal verification.
Phase 5 (Q4 2026+): Launch governance token, transition to DAO, expand to research automation.
9.1. Post-Quantum Cryptography Migration
Current Vulnerability
BN254 curve used in Groth16 is vulnerable to Shor’s algorithm. Estimated break time: 1 hour on a 10M-qubit quantum computer (expected 2035+).
Migration Timeline
Table 4.
Post-Quantum Migration Strategy.
Table 4.
Post-Quantum Migration Strategy.
| Timeline |
Technology |
Action |
| 2025-2026 |
Groth16 (BN254) |
Current implementation |
| 2027-2028 |
PLONK + BN254 |
Add alternative verifier |
| 2029-2030 |
Lattice-based SNARKs |
Pilot with new curves |
| 2031+ |
STARKs/other PQ |
Full migration |
Contingency Plan
Monitor NIST post-quantum standardization process
Maintain contract upgradeability via proxy pattern
Community governance vote on migration timing
Emergency freeze: Protocol can be paused if quantum threat becomes imminent
Research collaboration with academic institutions
10. Conclusions
ExecMesh v2.1 represents a fundamental shift in how we value computational work. By transforming verified compute into a financial primitive with robust security safeguards and enabling recursive proof composition, we create the infrastructure for a truly trustless AI economy. Our enhanced security model with multi-source oracles, graduated liquidation, and post-quantum migration roadmap addresses critical vulnerabilities while maintaining capital efficiency.
The protocol’s initial focus on data labeling pipelines provides a concrete wedge into the $2B AI training market, with clear expansion paths to research automation and content generation. Our conservative economic projections and realistic bootstrap strategy ensure sustainable growth.
This is the foundational protocol for the AI economy, where work is verifiable, composable, and financially productive—creating a world where computational output becomes as programmable and valuable as capital itself.
Acknowledgments
This work builds upon research and implementations from Satoshi Nakamoto [
2], Vitalik Buterin et al. [
3], Gavin Wood [
4], Jens Groth [
1], Ben-Sasson et al. [
5], Bünz et al. [
6], and the Aave [
7] and Uniswap [
8] teams. Special thanks to the critical reviewers whose feedback significantly strengthened this whitepaper.
Appendix A. Mathematical Proofs & Formal Verification
Appendix A.1. Collateral Safety Theorem
Theorem A1 (Enhanced Collateral Safety). For any locked compute credit with collateralization ratio and graduated liquidation thresholds, the vault remains solvent under price drops up to with partial liquidation restoring health before full insolvency.
Proof. Let
be the initial credit value and
D the debt issued. By definition
with
. The graduated liquidation system triggers at
(
collateralization):
For , safe decline to partial liquidation = .
Partial liquidation then restores health to , providing additional buffer. The system remains solvent through this graduated approach. □
Appendix A.2. Proof Composition Soundness
Theorem A2 (Soundness of Composed Proofs). If individual proofs are valid and the composition proof references their output hashes using collision-resistant hash function H, then acceptance of implies the prover used the genuine dependency outputs with negligible probability of forgery.
Proof. Let be dependency outputs and their hashes. Each proves knowledge of such that with soundness error .
The composed proof proves knowledge of inputs whose hashes equal and transformation producing output O.
By the collision-resistance of H, the probability of finding such that is negligible .
Thus the probability that
verifies but uses incorrect dependencies is bounded by:
Which is negligible in security parameter
. □
Appendix A.3. Oracle Manipulation Resistance
Theorem A3 (Oracle Manipulation Resistance). Given independent price sources with at least honest sources, the weighted median calculation resists manipulation requiring control of more than sources.
Proof. Let S be the set of price sources with , and be the honest sources with .
The weighted median calculation sorts sources by price and selects the price where cumulative weight reaches .
To manipulate the median downward, an attacker must control enough sources to push the cumulative weight of lower prices past . This requires controlling sources with total weight .
But honest sources have total weight , so the median must include at least one honest source price.
Thus manipulation requires controlling of total weight, which is impossible with honest assumption. □
Appendix B. Circuit Specifications & Benchmarks
Appendix B.1. Cryptographic Parameters
Table A1.
Enhanced Cryptographic Parameters for ExecMesh v2.1
Table A1.
Enhanced Cryptographic Parameters for ExecMesh v2.1
| Parameter |
Value |
Security Level |
Rationale |
| zkSNARK System |
Groth16 |
128-bit |
Industry standard, battle-tested |
| Elliptic Curve |
BN254 (alt_bn128) |
128-bit |
Native to EVM, gas-efficient |
| Hash Function |
Poseidon |
128-bit |
ZK-friendly, optimized for circuits |
| Proof Size |
256 bytes |
Constant |
Independent of circuit size |
| Verification Gas |
∼150k gas |
∼$0.005 on L2 |
Acceptable for settlements |
| Trusted Setup |
Powers of Tau |
Phase 1: Perpetual |
Community ceremony |
| Security Margin |
operations |
128-bit |
Sufficient until quantum era |
| Quantum Timeline |
2035+ |
Migration roadmap |
Section 9.1 |
Appendix B.2. Circuit Complexity Benchmarks
Table A2.
Enhanced Circuit Complexity Benchmarks
Table A2.
Enhanced Circuit Complexity Benchmarks
| Circuit |
Constraints |
Proving Time |
Verification Time |
Memory |
| Simple (compute.circom) |
1 |
∼200ms |
∼5ms |
<100MB |
| Composition (5 deps) |
17 |
∼500ms |
∼8ms |
∼500MB |
| Composition (20 deps) |
62 |
∼2s |
∼12ms |
∼2GB |
| Oracle Verification |
25 |
∼300ms |
∼6ms |
∼200MB |
| Liquidation Check |
8 |
∼150ms |
∼4ms |
∼100MB |
Appendix B.3. Gas Cost Analysis
Table A3.
Detailed Gas Cost Analysis (L2 Optimism Estimates)
Table A3.
Detailed Gas Cost Analysis (L2 Optimism Estimates)
| Operation |
Description |
Gas Used |
Cost @ 0.001gwei |
| Simple Proof Verify |
Groth16 verification |
150,000 |
$0.005 |
| Composition Verify |
3 dependencies |
280,000 |
$0.009 |
| Batch Verify (10) |
Aggregated proofs |
800,000 |
$0.027 |
| Oracle Update |
Multi-source median |
120,000 |
$0.004 |
| Liquidation Check |
Health calculation |
80,000 |
$0.003 |
| Future Settlement |
With reputation check |
200,000 |
$0.007 |
| Collateral Lock |
ERC-1155 approval |
100,000 |
$0.003 |
Appendix C. Formal Security Specifications
Appendix C.1. Oracle Security Parameters
Deviation Limits
Maximum price change per update: 15%
-
Minimum time between updates: 10 minutes
Staleness threshold: 1 hour
Minimum sources: 3 independent providers
Maximum concentration: 40% per source
Recommended Source Weights (Guidelines for Operators)
Note: These are suggested weights. The protocol enforces only the 40% concentration limit on-chain.
Appendix C.2. Liquidation Safety Proofs
Health Factor Calculation
The health factor
H for a position with collateral value
V and debt
D is:
where the result is in 18 decimal precision (e.g.,
represents 150% collateralization).
Grace Period Justification
The 6-hour grace period for positions with provides:
Time for price oracle updates to reflect market conditions
Opportunity for position owners to add collateral
Prevention of premature liquidations during temporary volatility
Balance between protection and capital efficiency
Appendix C.3. Emergency Scenarios & Response
Oracle Failure
Detect insufficient sources (<3 available)
Freeze new loans and liquidations
Use last known good price for up to 24 hours
Emergency governance vote for resolution
Market Manipulation Detection
Monitor for coordinated price source deviations
Check futures market arbitrage opportunities
Analyze trading patterns for wash trading
Implement circuit breaker if manipulation detected
Quantum Emergency
Monitor quantum computing milestones
Freeze protocol if Shor’s algorithm becomes practical
Execute post-quantum migration via governance
Use insurance fund for any losses during transition
Appendix D. API Reference & Integration Guide
Appendix D.1. ComputeCreditVault API
lockAsCollateral(uint256 tokenId, uint256 amount, address protocol, bytes32 purposeHash)
unlockCollateral(uint256 tokenId)
getHealthFactor(address user, uint256 tokenId) returns (uint256)
recordDebt(address user, uint256 tokenId, uint256 debtAmount)
recordRepayment(address user, uint256 tokenId, uint256 repayAmount)
liquidate(address user, uint256 tokenId) // liquidator role only
getMaxBorrow(address user, uint256 tokenId) returns (uint256)
Appendix D.2. Secure Oracle API
updatePrice(CapabilityType cap, PriceSource[] calldata sources)
getPrice(CapabilityType cap) returns (uint256)
getPriceWithAge(CapabilityType cap) returns (uint256 price, uint256 age)
isStale(CapabilityType cap) returns (bool)
addTrustedSource(address source, string calldata name) // admin only
pause() // admin only
Appendix D.3. Intent Matcher REST API
GET /api/v1/intents/open?capability={type}&maxReward={amount}
GET /api/v1/futures/market?capability={type}&timeframe={days}
GET /api/v1/agents/{address}/reputation
POST /api/v1/agents/register
POST /api/v1/intents/create
GET /api/v1/oracle/health // system status
Appendix D.4. Web3 Integration Examples
Checking Collateral Health
| Listing 10: Monitoring Position Health (corrected) |
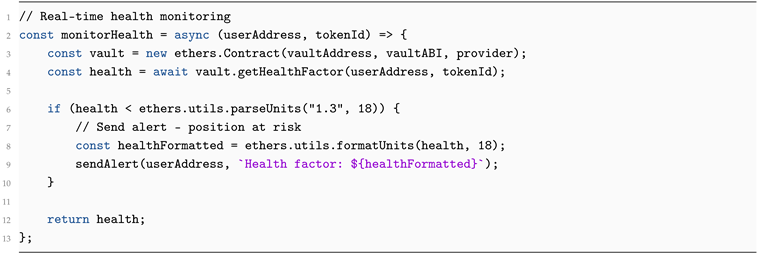 |
Secure Price Updates
| Listing 11: Oracle Price Update Script |
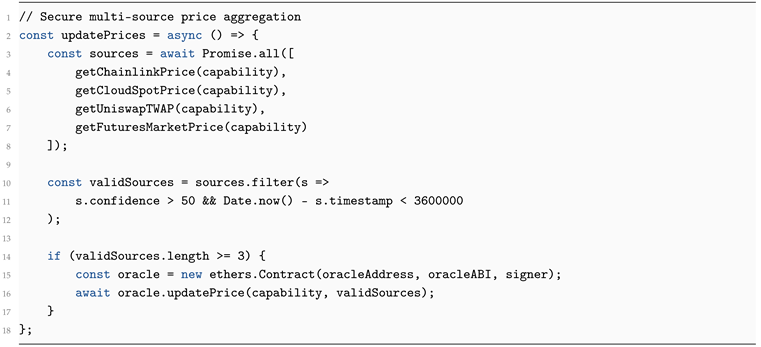 |
References
- Groth, J. On the Size of Pairing-Based Non-Interactive Arguments. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques. Springer, 2016, EUROCRYPT 2016, pp. 305–326. pp. 305–326. [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. https://bitcoin.org/bitcoin.pdf, 2008. Accessed: 2025-11-01.
- Buterin, V.; Griffith, V. Casper the Friendly Finality Gadget. In Proceedings of the arXiv preprint arXiv:1710.09437, 2019. [CrossRef]
- Wood, G. Ethereum: A Secure Decentralised Generalised Transaction Ledger. Ethereum Project Yellow Paper 2014, 151, 1–32. [Google Scholar]
- Ben-Sasson, E.; Chiesa, A.; Tromer, E.; Virza, M. Succinct Non-Interactive Zero Knowledge for a von Neumann Architecture. In Proceedings of the 23rd USENIX Security Symposium; 2014; pp. 781–796. [Google Scholar]
- Bünz, B.; Fisch, B.; Szepieniec, A. Transparent SNARKs from DARK Compilers. IACR Cryptology ePrint Archive 2020, 2019, 1229. [Google Scholar]
- Aave Companies. Aave Protocol V3: Technical Paper. Aave Documentation 2023. Available at: https://github.com/aave/aave-v3-core.
- Adams, H.; Zinsmeister, N.; Salem, M.; Keefer, R.; Robinson, D. Uniswap V3 Core. Uniswap Whitepaper 2021. [Google Scholar]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).

















