In this section, we present the main contributions of this paper, namely the formulation of Some Iterated MetaStructure.
2.1. Iterated-MetaOntology (Ontology of ... of Ontology)
An
ontology is a formal system specifying entities, their kinds, and relations, thereby providing a structured representation of existence within a logical framework [
37,
38]. A
MetaOntology is a higher–level structure that treats ontologies themselves as objects, studying their commitments, fundamentality orders, and interrelations across different domains [
39,
40,
41]. An
Iterated MetaOntology is a recursive generalization in which the meta-level construction is reapplied, forming hierarchical structures of ontologies of ontologies, rigorously captured by the theory of Iterated MetaStructures.
Definition 4 (MetaOntology (Ontology of Ontologies)).
Fix a first–order two–sorted language with sorts (ontologies) and (entity kinds). The nonlogical symbols are:
Intended readings: (“ is at least as strong as O”), (“ontology O is committed to kind e” in the Quinean sense), and (“in O, e is no more fundamental than ”).
A MetaOntology
(literally, an ontology of ontologies
) is an –structure
where is a set of ontologies (elements of sort ), is a set of entity kinds (elements of sort ), and the following axioms (the theory ) hold:
-
1.
is a preorder: and .
-
2.
For each fixed , is a preorder on E: and .
-
3.
Monotonicity of ontological commitment: ,
When concrete ontologies and a defining family are given, one may define
by
so that K records Quinean ontological commitments, while F captures a neo-Aristotelian fundamentality preorder per O.
Example 1 (Real-world MetaOntology: Retail product ontologies).
Fix the kind universe
Consider three concrete retail ontologies (base-level objects)
with Quinean commitments encoded as 0–1 row vectors in the order :
Define the strength preorder by componentwise inclusion (i.e., for all i). Then
For each , specify a fundamentality preorder on E via its (Boolean) adjacency matrix , where abbreviates (“ no more fundamental than ”). Take (always) reflexivity , and add the following domain-motivated relations:
Transitivity holds because with Boolean matrix product we have
and similarly for all coordinates (diagonal reflexivity is preserved, off-diagonal arrows only compose to existing ones), hence each is a preorder.
Finally, MetaOntology axiom (commitment monotonicity) is verified numerically: if and , then forces . For instance, along , since (commitment toDevice), we get . Thus with is a valid MetaOntology in the sense of Definition 4.
Definition 5 (Iterated-MetaOntology (Ontology of … of Ontology)). Let be a nonempty class of (base) ontologies , and let be a fixed set of entity kinds. Let , , and be relations satisfying the axioms in Definition 4 (preorder, commitment monotonicity, and per-kind fundamentality).
Inductively for , a depth-
t Iterated-MetaOntology
is a structure
defined from a nonempty set of depth- Iterated-MetaOntologies
and with the level-t relations lifted
from level as follows:
Example 2 (Real-world Iterated-MetaOntology: Cross-domain data governance (Retail ⇒ Healthcare)). Keep the same kind universe . Form two level-1 MetaOntologies (each as in Example 1):
Retail layer with
Healthcare layer with base ontologies specified by
and fundamentality preorders (besides reflexivity) given by
Within each layer we use the same strength preorder (componentwise inclusion), so and .
Depth-2 objects and their lifted relations. Define the depth-2 Iterated-MetaOntologies
By Definition 5, the level-2 commitment and fundamentality are:
and analogously for .
Concretely, using Boolean OR/AND across the layer:
Commitment (OR over bases).
Fundamentality (AND over bases).
For , both and have , hence
For , while , hence
In both cases, is a preorder (reflexivity by construction; transitivity holds since Boolean composition of reflexive relations with only these off-diagonal arrows does not create new arrows absent in all bases).
Order lift (witness map). Define by
Then for each we have :
so . By (1), this proves
Level-2 commitment monotonicity (numerical check). Take . Since (because ), and via f, we have , hence
as required by the lifted monotonicity in Lemma 1.
Therefore, the pair , with the above computations of and and the witness f, constitutes a concrete Iterated MetaOntology of depth 2 that models cross-domain data governance: retail ontologies feeding into healthcare governance while preserving commitment monotonicity and maintaining well-formed fundamentality preorders at the meta-level.
Proposition 1 (Generalization of MetaOntology). Depth recovers Definition 4. In particular, with is precisely a (first-level) MetaOntology; for one is left with base ontologies only.
Proof. By construction, the case uses exactly the relations postulated for MetaOntology, with underlying domain (the sort ). No lifting occurs, so the axioms coincide. For there is no meta-level structure: only the objects of remain. □
Lemma 1 (Axioms are preserved by lifting).
Fix . If is a preorder on , if each is a preorder on E, and if
then is a preorder on , each is a preorder on E, and the level-t monotonicity
holds for all and .
Proof.(Preorder for ). Reflexivity: take
and choose
in (
1); since
for all
O , we get
.
Transitivity: suppose
via
and
via
. Then for all
,
so by transitivity of
,
, and (
1) yields
.
(Preorder for ). Reflexivity: for all and all , , hence (3) gives .
Transitivity: if and , then for all we have and ; by transitivity at level , , hence (3) yields .
(Monotonicity of ). Assume
via
f and
. Then there exists
with
by (2). From (
1) we have
, so by (∗),
. Since
, (2) gives
. □
Theorem 1 (Iterated-MetaOntology as an Iterated MetaStructure). There exists a single–sorted signature and a family of lifts such that the tower from Definition 5 forms an Iterated MetaStructure in the sense of Definition 3. Moreover, depth coincides with MetaOntology and the lifts are isomorphism–invariant.
Proof. Step 1 (Many–sorted to single–sorted coding). Let
have unary predicates
,
distinguishing “ontology–points’’ and “kind–points’’, and relation symbols
A two–sorted structure is represented by a single–sorted –structure whose carrier is (tagged disjoint union), interpreting as the tags and the relations by restriction to the intended sorts. This standard reduction is definitional and reversible.
Step 2 (Choose the MetaStructure data). Let be the class of all –structures encoding MetaOntologies over the fixed E and base , and let the meta–operations be empty. Take as meta–relations exactly . This yields a MetaStructure .
Step 3 (Define the lift ). Given any depth-
object
, define
to be the
–structure whose “ontology–points’’ are the elements of
(i.e., all depth-
Iterated-MetaOntologies), whose “kind–points’’ are still
E , and with relations given by the lifted clauses (
1)–(3). This is exactly the lifting recipe of Definition 3 specialized to relations (no function symbols).
Step 4 (Verification of the Iterated MetaStructure axioms). By Lemma 1, the three axioms of Definition 4 are preserved by the lift from level to t ; hence the class equipped with the lifted relations again forms a valid MetaOntology object. The isomorphism–invariance required in Definition 2 holds because each lifted relation depends only on the images of elements under set–maps f and on universal/existential quantification over the isomorphism classes of lower–level elements; if at level , then iff etc., so the truth values are preserved.
Step 5 (Depth ). When there is no lifting; thus the construction reproduces Definition 4 verbatim, proving the claimed coincidence and hence the generalization property of Proposition 1. □
Corollary 1 (Sound tower). For every , is well defined, and forms an Iterated MetaStructure with relations obtained by repeated application of the lift .
Proof. Immediate by induction on t using Lemma 1 and Theorem 1. □
2.2. Iterated-Metacomputing (Computing of ... of Computing)
Metacomputing studies computings as objects, applying computable transformations to their descriptions, optimizing performance and costs—thus “computing of computings (cf.[
42,
43,
44,
45]).
Iterated Metacomputing repeatedly re-applies metacomputation, producing hierarchical layers where transformations optimize not only computings but entire metacomputing structures.
Definition 6 (Computing, extensional equality).
Let be a nonempty class of computings
, each a tuple
with input space I, output space O, a (partial) computable map (the extensional semantics), and a resource profile R (e.g., time, space, energy budgets). Two computings are extensionally equal , written , if as partial functions (after identifying domains/codomains in the obvious way).
Definition 7 (Descriptions and metacomputations).
Fix an effective encoder into a set of descriptions
(programs, circuits, schedules, architectures, ...). A metacomputation
is any computable functional . Its extensional lifting
is required to satisfy with (semantics preservation). Fix global evaluation functionals
and let be a tradeoff parameter.
Definition 8 (Metacomputing structure (level 1)).
A Metacomputing structure
is a pair
where is nonempty and is a nonempty set of metacomputations on . Define the improvement relation
(w.r.t. β) on U by
Write the capability predicate
for a partial function f to mean with . We induce a preorder on level 1 objects by
Remark 1.
Definition 8 generalizes the “single-operator” presentation ( Metacomputing (Computing of Computings) in the prompt): choosing recovers that setting and the same objective .
(level 1): Top-
k service in an e-commerce backend).
Example 3 (Real-world Metacomputing Task. A REST endpoint returns the top-k products by score from an input list. Let the computing be
maps to the subsequence of the k largest entries of a in nonincreasing order. (We assume stable ordering for ties; outputs are exact, not approximate.) The resource profile tracks average latency (ms) at a fixed input mix.
Description and objective. Fix an encoder . For C, write for the (lower-is-better) average latency (ms), and for an engineering cost proxy (nonnegative units). Choose (ms per cost unit). The scalar objective is
Baseline. Suppose for we measured
Metacomputations. Consider two computable, semantics-preserving description-level transforms:
-
(M1)
Selection-then-partial-sort: rewrite the implementation to usenth_element followed by a partial sort on the top-k window. As a functional on descriptions, .
-
(M2)
SIMD kernel fusion : fuse adjacent passes and employ vectorized comparisons for the partition step; functional .
Each preserves extensional semantics (same top-k with the same stable tie-breaking), so for every C in scope.
After (M1). Let , with empirical
Numeric verification of improvement:
so by Definition 8, holds for any whose contains .
After (M2) on top of (M1). Let . Suppose
Again , so . By transitivity of ≤, also .
A level-1 Metacomputing structure. Let and . Then is a valid level-1 object and the above inequalities prove concrete instances of .
Definition 9 (Iterated-Metacomputing (depth
t)).
For , a depth-
t Iterated-Metacomputing structure
is a pair
where is a nonempty set of depth- structures and is a nonempty set of metacomputations (acting on the common description space ). Define the lifted improvement
between level- objects inside two level-t structures by
where abbreviates . Set the level-t preorder by
Lift the capability predicate to level t by
with the base clause from Definition 8.
Example 4 (Iterated-Metacomputing (depth 2): Company-wide CI/CD + runtime unification).
Setting. Two product teams own separate services:
Each service already has its own level-1 Metacomputing structure:
where includes kernel fusion and tiling passes, and includes index-layout rewrites and query-plan normalizations. All transforms are semantics-preserving for their services.
Numbers at level 1. With the same objective and :
Here, does not improve the scalar objective (145 → 150), so fails . By contrast, holds (320 → 300).
A level-2 initiative (cross-cutting metacomputations). Define a depth-2 structure
Let contain computable functionals acting on descriptions across services :
-
(T1)
LTO-unified toolchain : enforce link-time optimization and PGO across all C/C++ components;
-
(T2)
Allocator standardization : replace per-service allocators with a shared slab allocator tuned for the joint workload;
-
(T3)
CI cache coherence : unify build cache keys and artifact promotion across repos to reduce engineering overhead.
Each induces a semantics-preserving map on every underlying computing and has a well-defined design-cost impact via .
Lifted improvements. We must witness (Definition 9) that for each level-1 object in there is an improved counterpart inside . Pick a single cross-cutting transformation that applies (T1)+(T2)+(T3) jointly.
Define by
Assume measured post- figures:
Numeric verification (per-object):
Therefore, for every we have , so by Definition 9
hold (taking the codomain objects to be themselves but post-). Hence, with on both sides,
is certified by the witness ϕ.
Capability monotonicity at depth 2 (worked check). Let be the exact “thumbnail → JPEG” map realized by some . Since holds (witness C), and , Lemma 2(2) ensures . Indeed, computes the same partial function, so extensionally.
Interpretation. Level 1 optimizes each service locally via its own . Level 2 introduces organization-wide metacomputations that act across description spaces, yielding uniform runtime/toolchain improvements that strictly reduce the scalar objective for every underlying computing—thereby establishing the level-2 preorder and preserving capabilities.
Example 5 (Iterated-Metacomputing (depth 2): AutoML training pipelines over tasks).
Base tasks (computings). For datasets , let
be training pipelines that map hyperparameters to trained models and metrics ( returns the same validation metric as the rewritten pipeline; we freeze the metric definition to ensure extensional equality). Take as epoch-time × epochs-to-target, and as GPU-engineering overhead units; choose (hours per cost unit).
Level 1 AutoML metacomputations. Each task has including: ( a ) static-graph rewrites, ( b ) kernel autotuning, ( c ) input pipeline fusion. Suppose
Thus and hold.
Depth 2 (portfolio-level metacomputations). Define
where contains:
Unified mixed-precision policy: standardize AMP levels, loss-scaling, and BF16/FP16 toggles across tasks;
Checkpoint/IO harmonization: align shard sizes and prefetch depths across all tasks.
Let apply both. For define with measured
Thus for each underlying computing there is an improved with , certifying in the sense of Definition 9.
Proposition 2 (Reduction to Metacomputing). Depth in Definition 9 is exactly Definition 8. Hence Iterated-Metacomputing generalizes Metacomputing.
Proof. At there is no nesting: and . All lifted clauses in Definition 9 collapse to those of Definition 8. □
Lemma 2 (Preorder and capability monotonicity are preserved). For every :
-
1.
is a preorder on the class of depth-t structures.
-
2.
If and , then .
Proof. (1) Reflexivity: take in the definition of and note that holds by choosing and using itself.
Transitivity: suppose via witnesses and via . Compose the witnessing maps and use the transitivity of (non-strict) ≤ on the scalar objective to obtain .
(2) If , choose with . By there exists with , which in particular provides, for some realizing f , a with ; hence and therefore . □
Theorem 2 (Iterated-Metacomputing as an Iterated MetaStructure). There exists a single–sorted signature and a lift such that the tower of Definition 9 forms an Iterated MetaStructure in the sense of Definition 3. Moreover, depth coincides with Metacomputing (Definition 8), and the lift is isomorphism–invariant.
Proof. Step 1 (Coding many–sorted data in one sort). Let
contain unary predicates
and
, intended to tag
structures vs.
computings , and binary/ternary relations:
where the third argument
z ranges over a fixed universe of partial computable functions (we can represent such
z by Gödel codes). Any pair
at some level
t is encoded by a
–structure
whose carrier is
(finite nesting as needed), with
indicating the tags and with
interpreted exactly by
,
, and
.
Step 2 (Define the lift ). Given , let be the –structure whose S –elements are all depth- objects, whose C –elements are the computings they contain, and whose relations are the lifted ones from Definition 9. This is the purely relational instance of Definition 3 (no function symbols are needed).
Step 3 (Iterated MetaStructure axioms). By Lemma 2(1), each –slice is a preorder; by Lemma 2(2) the monotonicity of along holds. These properties are preserved under the lift by construction (the clauses only use existential witnesses and composition of witnessing maps), hence the tower is an Iterated MetaStructure.
Step 4 (Isomorphism–invariance). If is a bijection that preserves and the three relations, then the truth of the lifted clauses is preserved under because they are defined by bounded first–order formulas using only ∃/∀ over the underlying sets and composition of witnessing maps; hence is an isomorphism at level t .
Step 5 (Depth ). When , encodes exactly the data of Definition 8, so level 1 coincides with Metacomputing. □
Corollary 2 (Soundness of the tower). For every , the object is well defined and the family forms an Iterated MetaStructure under , with preorder and capability predicate at each level.
Proof. Immediate by induction on t using Lemma 2 and Theorem 2. □
2.3. Iterated-Metapuzzle (Puzzle of ... of Puzzle)
A
puzzle is a constraint satisfaction problem: variables have finite domains, constraints restrict assignments, and solutions minimize objectives(cf.[
46,
47]). A
Metapuzzle treats multiple puzzles as components, enforcing meta-constraints across their solutions, optionally optimizing a higher-level objective [
48]. An
Iterated Metapuzzle recursively re-applies this construction, forming hierarchical layers where meta-constraints and objectives operate over metasolutions themselves.
Definition 10 (Puzzle and solution).
Let be a finite set of variables with finite domains and write . Let be predicates and let be an (optional) objective (when no objective is intended, take ). The feasible set
and solution set
are
A puzzle is the tuple .
Definition 11 (Metapuzzle level 1): puzzle of puzzles).
Let be a finite family of puzzles, and abbreviate . A metapuzzle
is a pair
where each meta-constraint
couples base solutions, and is a meta-objective (set if not given). Define
Example 6 (Real-world Metapuzzle (level 1): E-commerce packing & courier choice). Setting. A single customer order must be (i) packed into shipping boxes and (ii) dispatched by a courier. Packing and routing are modeled as two base puzzles; meta-constraints couple their solutions.
Base puzzle (bin-packing with costs). Items have volumes and weights , so and . Available boxes:
Variables: choose a multiset of boxes and an assignment of items so that box capacities are not exceeded. Objective : total box cost. Two feasible optimal
packings (both attain cost ):
Hence with
Base puzzle (courier choice). Couriers:
Variable: choose such that (both satisfy). Objective : delivery time (we will combine cost at the meta-level).
Level-1 metapuzzle . For any pair define the meta-constraints:
These encode handling and size restrictions (multiple boxes or any requires a van). Define the meta-objective with tradeoff parameter :
Feasibility and enumeration. The two candidate packings force by :
Pairs with are infeasible: for by , for by .
Numerical minimization. Compute
Either meta-solution attains the optimal meta-objective value 42 and satisfies both and .
Definition 12 (Iterated-Metapuzzle (depth
t )).
Inductively define depth-t objects for by taking a finite family of depth- metapuzzles and setting
A depth-
t metapuzzle
is a pair
with meta-constraints and objective . Define
Example 7 (Iterated-Metapuzzle (depth 2): Two orders with pooled routing at the meta-level).
Setting. Two independent customer orders, A and B, are each solved by the level-1 metapuzzle of Example 6. Order A uses the data and Order B uses . Boxes and couriers are the same as before. Thus each order has the level-1 metasolution set
where for each order the subscript 1 denotes “1×M” (one box) and 2 denotes “2×S” (two boxes). All level-1 pairs already use by .
Depth-2 metapuzzle . For any tuple with
define summary statistics
Meta-constraint (pooled-trip admissibility):
By construction and both use Van , so the decisive condition is .
Meta-objective applies a synergy when pooling is admissible:
with the same as in Example 6. Recall for all four packings under consideration.
Feasibility and numeric evaluation. Enumerate the four combinations :
and every feasible x with attains the optimal value
for instance the explicit choice
has and yields .
Discussion. Level 1 solves two coupled puzzles per order (packing + courier) under handling constraints, with a latency–cost objective. Level 2 couples the two orders via a pooled-routing admissibility constraint and realizes a quantifiable synergy when admissible. This instantiates Definitions 11–12 with explicit domains, constraints, and numeric optimality checks.
Proposition 3 (Generalization). Depth in Definition 12 reproduces Metapuzzle (Definition 11). In particular, and the constructions of and coincide.
Proof. For we have , , and the admissible meta-constraints/objective act on , exactly as in Definition 11; the two minimizations are identical by definition. □
Lemma 3 (Product/isomorphism invariance).
Let be bijections and define . For any family and objective F, set
Then α restricts to a bijection and carries onto .
Proof. By construction, for all , . Hence ; this is the first claim. For minimizers, , so minimizes over iff minimizes F over . □
Theorem 3 (Iterated-Metapuzzle as an Iterated MetaStructure). There exists a single–sorted signature and a lift such that the tower of Definitions 11–12 forms an Iterated MetaStructure (Definition 3). Moreover, depth coincides with Metapuzzle and the lift is isomorphism–invariant.
Proof.
Step 1 (Choose and the universe U ). Let have: (i) a unary relation symbol and (ii) a unary function symbol . A –structure consists of a carrier set S (intended as a product of solution sets), an interpretation , and a function . Let U be the class of all such structures.
Step 2 (Encode metapuzzles as –structures). Given
with factors
, set
and interpret
Then .
Step 3 (Define the meta–operation and the lift). For each finite index set size
k and each choice of
, define a meta–operation
by
where
is the carrier of
. This constructor
only depends on the carriers (and the chosen
label), not on representatives; it is therefore isomorphism–invariant.
Define by replacing each with the carrier of the encoded lower–level solution set, i.e., for depth t take inputs from depth and apply to their carriers. This is exactly the “lift” of Definition 3: carriers are functorially built by product, the feasible predicate is the conjunction of meta–constraints, and the objective is copied as prescribed.
Step 4 (Verification). By construction, U is nonempty and closed under . Naturality (isomorphism–invariance) follows from the Lemma. Since Definition 3 requires that meta–operations be given by uniform recipes on carriers and on symbol interpretations, and our does precisely that (product on carriers; conjunction for ; copy of ), the tower obtained by iterating is an Iterated MetaStructure. When , this recovers Definition 11. □
2.4. Iterated-Metabibliography (Bibliography of Bibliography)
A
bibliography is a finite collection of bibliographic records, each describing works by authors, year, title, venue, and identifiers[
49,
50,
51]. A
Metabibliography merges multiple bibliographies: canonicalizes records, deduplicates overlaps, and orders results, producing a single coherent reference list [
52]. An
Iterated Metabibliography applies this process recursively, merging metabibliographies into higher-level structures, ensuring consistent canonicalization, deduplication, ordering, and stability across layers.
Definition 13 (Canonical records, equality).
Let be the universe of raw bibliographic records and a canonicalization (e.g., case-folding, punctuation stripping, normalized author lists). Assume an identifier map ( collects DOI/ISBN/arXiv ids). Define iff
A canonical record is an element that represents a ∼-class. We henceforth regard equality on canonical records as: iff they represent the same ∼-class.
Definition 14 (Bibliography and its canonical set).
A (finite) bibliography
is a finite multiset . Its canonical, deduplicated set
is
Definition 15 (Key and order).
Fix a total key
map
(e.g., ) and let be the usual lexicographic order on K. For , define a total order by
Definition 16 (MB-structure (a metabibliographic structure, level 1)).
A metabibliographic structure
is a pair
where is finite and is as in Definition 15. Given a bibliography B, its associated level-1 structure is
Given with , define the merge
operator
The output list of is the sequence obtained by sorting H under .
Definition 17 (Metabibliography (Bibliography of Bibliographies, level 1)).
Given bibliographies , the metabibliography
is the MB-structure
Its output list coincides with the canonize–deduplicate–order pipeline of the Definitions.
Example 8 (Metabibliography (level 1): Lab & course lists merged into one canon).
Inputs (three everyday bibliographies).
Base extraction (normalize fields).
Canonical keys (examples).
Metabibliography merge (Def. 17).
Deduplicated output (5 unique items from 8 inputs).
Everyday reading: a lab, a collaborator, and a course syllabus collapse into one clean, de-duplicated, consistently ordered bibliography ready for a paper or website.
Definition 18 (Iterated-Metabibliography (depth
)).
Let be a finite family of depth- MB-structures, each . Define the depth-
t metabibliography
by
Equivalently, its carrier is with the order induced by Key.
Example 9 (Iterated-Metabibliography (level 2): Department → School consolidation).
Two level–1 metabibliographies (already merged inside each unit).
School-wide consolidation (Def. 18).
so its carrier and order are
(sorted by Key; the duplicate[Goodfellow2016] appears once).Counts. Input size , unique output size .
Everyday outcome: a school library or website shows one unified canon drawn from departmental metabibliographies, automatically deduplicated and consistently ordered.
Proposition 4 (Generalization of Metabibliography).
Depth of Definition 18 reproduces the (one-shot) Metabibliography:
where ≤ is the total order induced by Key. In particular, the ordered output equals sorting the aggregate deduplicated set under Key.
Proof.
Because
already quotients by ∼, multiset union across raw
followed by canonicalization/dedup equals set union across the
:
The order is by Key in both constructions, hence the outputs coincide. □
Lemma 4 (Idempotence, commutativity, associativity of merge).
For finite MB-structures we have
Proof. All three equalities are immediate from set-theoretic identities on carriers (, , ), while the order is always the one induced by the fixed Key on the resulting carrier. □
Lemma 5 (Isomorphism invariance).
Let be bijections with (i.e., they only rename canonical representatives within equal keys). Then
via (well-defined on disjoint copies), and the sorted output lists coincide.
Proof. The carrier is preserved up to the bijection , and since , the induced total order is preserved; therefore is an order isomorphism and sorting commutes with . □
Theorem 4 (Iterated-Metabibliography as an Iterated MetaStructure). There exists a single–sorted signature and a lift such that the tower forms an Iterated MetaStructure (Definition 3). Moreover, depth coincides with Metabibliography and the lift is isomorphism–invariant.
Proof. Signature and objects. Let have a carrier sort with: (i) a unary function symbol with codomain K (fixed), (ii) a binary relation symbol . A –structure is a pair where H is a finite subset of and is the total order induced by Key (Definition 15); the function Key is interpreted as the fixed map restricted to H .
Meta-operation (merge). For each arity
, define
on the class
U of all finite
–structures by
This recipe depends only on the carriers and the fixed Key; by Lemma 5 it is isomorphism–invariant (naturality).
Iterated lift. Define the “base constructor’’ Base (Definition 16) that sends a raw bibliography
B to
–structure
. For
set
as in Definition 17. For
, take inputs that are already
–structures and apply
, which is exactly the lift
in the sense of Definition 3:
Verification. Closure: U is closed under since finite unions of finite subsets of are finite, and ≤ is induced by the fixed Key. Associativity/commutativity/idempotence of follow from Lemma 4, ensuring that iterated applications are well formed and independent of bracketing. Isomorphism–invariance holds by Lemma 5. Therefore the tower obtained by repeated application of is an Iterated MetaStructure. The case agrees with Proposition 4, i.e., the standard Metabibliography. □
Corollary 3 (Sound tower and stable outputs). For all , is well defined; moreover, isomorphic changes of inputs do not affect the (ordered) output list at level t.
Proof. Induction on t using Theorem 4 and Lemma 5. □
2.5. Metapopulation (Population of Populations)
A
population is a group of individuals in a habitat, modeled with dynamics of growth, mortality, migration, and reproduction (cf.[
53]). A
Metapopulation is a structured population system of populations across habitat patches, with colonization, extinction, and interpatch interactions[
54,
55,
56,
57]. An
Iterated Metapopulation recursively aggregates metapopulations into higher-level superpopulations, using coarse-graining schemes preserving Levins-type dynamic structure.
Definition 19 (Metapopulation).
Let be a finite set of habitat patches. Let , , be extinction rates and , , be colonization influences (from j to i). The state
is , , evolving by the Levins–type system
A metapopulation
is the triple equipped with the flow governed by (4). (Existence/uniqueness holds by local Lipschitz continuity of the right-hand side on .)
Example 10 (Metapopulation (level 1): Urban pollinators in three patches).
Real setting.Three city habitats for wild bees: . Extinction rates (per unit time). Colonization influences (from j to i):
Initial occupancies .
Levins dynamics (Def. 19). For , . At (numbers rounded to ):
Interpretation: all three patches are expected to increase occupancy initially, with the park () increasing fastest under the given flows.
Definition 20 (Coarse-graining schema).
Let be a finite disjoint union of patch sets. A coarse-graining schema
is a pair
where is a surjection onto a finite superpatch set
and are nonnegative weights
such that
We write as shorthand for .
Definition 21 (Aggregation of parameters).
Given metapopulations () and a schema on , define aggregated rates on Q by
where is the index with . Define the coarse state
by weighted averages
Lemma 6 (Closure under aggregation).
If each is a metapopulation, then the aggregated triple satisfies , , and has Levins–type dynamics
provided the micro-to-macro closure
holds (mean-field factorization). In particular, solves a Levins system with parameters (6)–(7).
Proof. Nonnegativity is immediate from (
6)–(
7). Differentiating (
8) and using the base equations (
4) for each
yields
Insert
in the first term and apply the moment closure (
10) to identify the first sum with
; the second sum equals
by (
6)–(
8). This is (
9). □
Definition 22 (Iterated-Metapopulation (depth t )). Depth 1 objects are metapopulations as in Definition 19. For , a depth- t Iterated-Metapopulation is obtained by:
take a finite family of depth- objects , choose a coarse-graining schema on , and output the aggregated metapopulation
Its state evolves by (9).
Example 11 (Iterated-Metapopulation (level 2): Two campuses aggregated to districts).
Micro level (two campuses). North campus with and
South campus with and
Assume no cross-campus dispersal (off-block entries ). Initial occupancies: .
Coarse-graining (Def. 20). Aggregate to districts with , and weights .
Aggregated parameters (Def. 21).
Coarse state and its initial change.
Levins form (Lemma 6): gives
Interpretation: at district scale, both aggregated occupancies initially decline slightly because extinction averages outweigh within-district colonization; the construction realizes an Iterated-Metapopulation (Def. 22) with explicit .
Proposition 5 (Generalization of Metapopulation).
Depth of Definition 22 coincides with the (one-level) metapopulation of Definition 19. Equivalently, taking , , gives , , , and (9) reduces to (4).
Proof. Immediate from the formulas: with
and
, the sums (
6), (
7) collapse to
. □
Lemma 7 (Isomorphism invariance). If is a bijection (relabeling patches) and we transport by , , and replace π by and w by , then the aggregated parameters are unchanged.
Proof. Both (
6) and (
7) are sums over fibers
with weights
; the relabeling permutes the summation indices without changing the summands, hence the sums are identical. □
Theorem 5 (Iterated-Metapopulation as an Iterated MetaStructure). There exists a single–sorted signature and a lift such that the tower from Definition 22 forms an Iterated MetaStructure (Definition 3). Moreover, depth coincides with Metapopulation (Definition 19), and the lift is isomorphism–invariant.
Proof. Step 1 (Signature and objects). Let
be relational with carrier
P and nonlogical symbols
A
–structure is precisely a metapopulation
. The dynamics (
4) depend functorially on
and need not be part of the signature.
Step 2 (Meta-operations). For each arity
k and each coarse-graining schema
on
, define the meta-operation
by the uniform recipes on carriers and symbols:
These depend only on and the input interpretations .
Step 3 (Isomorphism–invariance). If
are isomorphisms (relabelings), Lemma 7 shows that with
and
we get
so
is natural in the sense of Definition 2.
Step 4 (Iterated lift). Define
by: on a level-
family, choose
and output
as in Step 2. By construction this matches the lift scheme of Definition 3: carriers are built by
, and the symbol interpretations are given by fixed recipes (
/
) (
6)–(
7).
Step 5 (). Taking and , yields the identity meta-operation, so level 1 objects are exactly Definition 19. □
Corollary 4 (Sound tower).
For every , the Iterated-Metapopulation is well defined; the family forms an Iterated MetaStructure under , and the dynamics at each level are of Levins type with aggregated parameters (6)–(7).
Proof. Induction on t , using Lemma 6 for well-posed Levins dynamics and Theorem 5 for the MetaStructure properties. □
2.6. Metalogic (Logic of Logics)
A
logic is a formal system of formulas and consequence relations, capturing valid inference rules and reasoning principles. A
Metalogic studies logics as mathematical objects, comparing strengths, defining translations, and organizing them into structured categories (cf.[
58,
59,
60]). An
Iterated Metalogic recursively treats metalogics as objects, lifting strength and translation relations into higher meta-levels systematically.
Definition 23 (Logics, translations, and Metalogic (level 1)).
Let a logic
be a pair , where is a set of formulas and is a Tarskian consequence operator (extensive, monotone, idempotent). For logics with the same
formula set, define the strength preorder
A translation code
is an element λ of a fixed set Λ equipped with a partial decoding
map
We write iff is consequence-preserving:
Assume Λ carries typed identity codes
and a typed, associative composition
operation
compatible with function composition of decodings. A (level–1) Metalogic
is the structure
where is a nonempty set of logics, is the above preorder (on those pairs with equal formula sets), and is the typed family of translation codes closed under identities and composition.
Example 12 (Metalogic (level 1): Marketing vs. GDPR consent rules). Setup. Let be propositional formulas over atoms A (“adult”), C (“has consent”), S (“may send promo email”). For a finite axiom set , write for classical propositional consequence from premises .
Two real-life logics on thesame
formula set .
Strength check. Since , by monotonicity of ,
Hence (Def. 23).
A translation code (renaming to a notification platform). Let over atoms A, C, N with . Define with decoding by the homomorphic renaming , , . Then
i.e., . This models a real deployment: the same policy is transferred from “marketing logic” to a “notification system logic” by a safe symbol renaming.
Definition 24 (Iterated-Metalogic (depth
)).
Assume level objects have been defined. A depth-
t Metalogic
is a triple
where is a nonempty set of level- metalogics. The level-t relations are lifted as follows:
(Lifted strength). For with carriers ,
(Lifted translations). A level-
t translation code
from to is a pair
where and each . The set contains exactly these families. Define identities and composition by
Example 13 (Iterated-Metalogic (level 2): Company standardization across subsidiaries).
Level 1 metalogics. Subsidiary A uses atoms and maintains two logics
forming with . Subsidiary B adopts a company standard
vocabulary and corresponding logics
so has carrier .
Level 2 translation family (lifted). Define by and . For each , choose a level-1 translation code with decoding given by the homomorphic renaming
Then and because axioms map to axioms (e.g., becomes ). Hence
(Def. 24), and since each , we also have by (11). Interpretation:
a company-wide standardization lifts per-logic renamings to a uniform, family-wise translation between two subsidiaries’ policy logics.
Proposition 6 (Generalization). Depth of Definition 24 coincides with Definition 23. Hence Iterated-Metalogic generalizes Metalogic.
Proof. At we have consisting of logics, the strength preorder, and the base translation family. No lifting occurs. □
Lemma 8 (Preorder and categorical laws lift). For every :
-
1.
of (11) is a preorder on . -
2.
contains identities and is closed under composition; composition is associative and identities are two-sided units.
Proof. (1) Reflexivity holds by choosing and using reflexivity at level . Transitivity: if via f and via g , then for all , , so via .
(2) Identities are by definition. If and , then for each A the typed composition , hence the family belongs to . Associativity and unit laws follow pointwise from those of level . □
Theorem 6 (Iterated-Metalogic as an Iterated MetaStructure). There exists a single–sorted signature and a lift such that the tower in Definition 24 forms an Iterated MetaStructure in the sense of Definition 3. Moreover, depth coincides with Metalogic and the lift is isomorphism–invariant.
Proof. Signature and coding. Let
be relational with carrier
X and the following symbols:
where
is the fixed set of translation codes equipped with typed identities and composition. A
–structure
encodes a metalogic by taking
X as its carrier, interpreting
as ⪯, and
as the binary–indexed family
.
Meta-operations and lift. There are no function symbols; meta–operations act only on relations. Given a level
structure
encoding
, define
to be the structure whose carrier
is the set
of all level
objects, with relations
By Lemma 8, is a preorder and is closed under the typed identities and composition provided by ; thus the –axioms (namely: “ is a preorder” and “ is a category over X ’’) hold at each level.
Naturality (isomorphism–invariance). An isomorphism of level structures is a bijection preserving and . The lifted carrier map sends a level object to the pointwise transport ; the defining clauses for and are first–order formulas using only ∃/∀ over and composition/identities in , hence preserved by . Therefore is natural.
Base level. For , encodes exactly the data of Definition 23. Hence the tower is an Iterated MetaStructure and depth 1 coincides with Metalogic. □
Corollary 5 (Sound tower). For every , is well defined; the family forms an Iterated MetaStructure under , with a preorder of strength and a category of translations at each level.
Proof. By induction on t using Lemma 8 and Theorem 6. □
2.7. Meta-ethics (Ethics of Ethics)
An
ethics is a normative system mapping situations to actions with statuses obligatory, permissible, or forbidden, constraining human behavior [
61,
62]. A
Metaethics compares ethical systems themselves, ordering them by permissiveness and analyzing coherence, consistency, and higher-level normative principles [
63]. An
Iterated-Metaethics recursively treats metaethics structures as objects, lifting permissiveness preorders across multiple levels into hierarchical normative meta-systems.
Definition 25 (Ethical system and permissiveness).
Let S be a set of situations
and A a set of actions
. An ethical system
is a triple with a deontic map
such that for all , : (i) (obligatory implies permissible), (ii) (no action is both obligatory and forbidden), (iii) (some action is permissible). Write
For two systems on the same , define the permissiveness preorder
Definition 26 (Meta-ethics (level 1)).
Fix once and for all. A (level–1) Meta-ethics structure
is the pair
where is a nonempty set of ethical systems on and is the permissiveness preorder from Definition 25. (Optionally, one may equip with consensus/union meta-operations and defined by , , and , ; these preserve the coherence axioms.)
Example 14 (Meta-ethics (level 1): Home vs. Workplace data-sharing rules). Situations and actions. Let and .
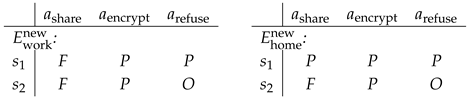
Two ethical systems on . Define and by the following deontic labels (O=obligatory, P=permissible, F=forbidden):
Permissiveness check. From Definition 25,
Hence for each , , i.e., . All coherence axioms hold (no , and some action is always permissible).
Definition 27 (Iterated-Meta-ethics (depth
)).
Assume level objects have been defined. A depth-
t Meta-ethics structure
is
where is a nonempty set of level- Meta-ethics structures. The level-t preorder is lifted
by
where denotes the carrier (set of objects) of .
Example 15 (Iterated Meta-ethics (level 2): Policy update mapping old → new). Same as above. Consider old and new versions of the two systems:
Old policies. as in the previous example. as in the previous example.
New policies (strictly more permissive or equal).
(Practically: after adding vetted vendor channels, encrypted transfer becomes permitted.)
Level–1 inclusions. For each ,
so and .
Level–2 structures and witness. Let
Define by and . Then for all we have , hence by (12)
This models a real-life policy modernization : the level–2 object collects updated (more permissive but controlled) codes that uniformly extend the old ones.
Proposition 7 (Generalization of Meta-ethics). Depth in Definition 27 reproduces Meta-ethics (Definition 26). Hence Iterated-Meta-ethics generalizes Meta-ethics.
Proof. For there is no lifting and is exactly Definition 26. □
Lemma 9 (The lifted relation is a preorder).
For every , defined in (12) is a preorder on .
Proof. Reflexivity: take ; since is reflexive, . Transitivity: if via f and via g , then for all ; thus via . □
Theorem 7 (Iterated-Meta-ethics as an Iterated MetaStructure). There exists a single–sorted signature and a lift such that the tower forms an Iterated MetaStructure in the sense of Definition 3. Moreover, depth coincides with Meta-ethics and the lift is isomorphism–invariant.
Proof. Signature and coding. Let be relational with a single binary symbol . A –structure encodes a Meta-ethics structure by taking X as its carrier (set of objects at that level) and interpreting as the corresponding preorder ⊑.
Lift. Given a level
structure
, define
to be the structure
whose carrier
is the set of all level-
objects and whose relation is the lifted preorder (
12). By Lemma 9,
is a preorder.
Isomorphism–invariance. Let
be an isomorphism (a bijection preserving the preorder). Transporting witnesses
f in (
12) by
shows that
induces an isomorphism between the lifted structures
and
; hence the lift is natural.
Base level. For the encoding is exactly , which is Meta-ethics (Definition 26). Therefore the tower is an Iterated MetaStructure with signature . □
Corollary 6 (Sound tower). For every , is well defined and forms an Iterated MetaStructure under , with a (lifted) permissiveness preorder at each level.
Proof. Immediate by induction using Lemma 9 and Theorem 7. □
2.8. Metadata (Data of Data)
A
Metadata is structured descriptive information about data objects, defined by schema, attributes, identifiers, and canonical assignments (cf.[
64,
65,
66]). An
Iterated-Metadata recursively applies metadata construction, lifting data–about–data into multiple hierarchical levels, preserving identifiers, schemas, and isomorphism invariance.
Definition 28 (Metadata (level 1)). Let D be a (nonempty) set of data objects . A schema is a pair where K is a finite set of attribute keys and assigns to each a value domain . A –record is a function with for all k; write for the set of all such records.
Fix a distinguished reference key
and an identifier map . A metadata assignment
on is a map
The triple is called metadata on D.
Definition 29 (Isomorphisms of metadata). Two metadata triples and are isomorphic , written , if there exist bijections and such that
-
(a)
for all and ,
-
(b)
for all ,
-
(c)
for every and , .
(I.e. α renames data, ψ renames keys while preserving value domains and the aboutness key, and the records commute with these renamings.)
Definition 30 (Lift to metadata-of-metadata).
Given with , define its lift
by:
Then is again metadata by Definition 28 (with reference key and identifier ).
Definition 31 (Iterated-Metadata (depth
t )).
Let be metadata. Define inductively for :
using (13)–() at level . We call Iterated-Metadata of depth
t.
Example 16 (From file metadata to metadata-of-metadata).
Level 1 (ordinary metadata). Let the data objects be two photos . Use schema with
The identifier is . Define the metadata assignment by
Thus is metadata in the sense of Definition 28.
Lift (metadata-of-metadata, Level 2). Apply Definition 30:
The lifted identifier is . The lifted assignment satisfies, for each ,
Concrete instance (for
).
The case for is analogous. Intuitively, each Level 2 record keeps all Level 1 fields, plus (i) a copied identifier for stable linkage and (ii) a pointer to the previous metadata record (provenance). Hence is a simple, real-life “metadata-of-metadata” for a phone photo library.
Proposition 8 (Generalization of Metadata). Depth of Definition 31 reproduces ordinary metadata (Definition 28). Hence Iterated-Metadata generalizes Metadata.
Proof. Trivial: by definition is exactly Definition 28. No lifting is applied at . □
Lemma 10 (Naturality (isomorphism invariance) of the lift).
If via as in Definition 29, then via
Proof. By (b)–(c) of Definition 29, for , and . Therefore (16) commutes under for all keys, including the two new ones, and (15) is preserved as well. □
Theorem 8 (Iterated-Metadata as an Iterated MetaStructure). There exists a single–sorted signature and a lift such that the tower forms an Iterated MetaStructure (Definition 3). Moreover, depth coincides with Metadata and the lift is isomorphism–invariant.
Proof. Signature and objects. Let
be relational over a single carrier
X (tagged union of data, keys, and records) with symbols:
A –structure encodes a metadata triple by taking , marking sorts with /, interpreting from , and / from and id.
Meta–operation (the lift). Define a unary meta–operation
on the class
U of
–structures by performing the recipes (
13)–(16) at the level of carriers and of the relations
. Concretely: carriers are rebuilt by adding the graph pairs and the two fresh keys;
is extended so that each lifted record inherits all original key–value pairs and additionally has entries for
(the old identifier) and
(the previous record).
Isomorphism–invariance. If is an isomorphism (in particular inducing a pair as in Definition 29), then by Lemma 10 the assignments of all relation symbols in and agree through the transported ; hence is natural.
Iterated MetaStructure. Let be the functor that sends to and acts on isomorphisms by transport as above. Iterating produces the tower of Definition 31. Depth clearly coincides with ordinary metadata (no lifting applied). □
Corollary 7 (Sound tower). For every , is well defined, and the family forms an Iterated MetaStructure under the isomorphism–invariant lift .
Proof. Immediate by induction on t using Lemma 10 and Theorem 8. □
2.9. Meta-Governance (Governance of Governance)
A
Governance system specifies how actors, decision rules, instruments, and processes interact to steer collective actions within institutions. A
Meta-Governance structure organizes governance systems, redesigning their modes, instruments, and processes to coordinate failures and reweight steering mechanisms (cf.[
67,
68,
69,
70]). An
Iterated-Meta-Governance recursively applies meta-governance, layering higher-level coordination over sets of governance structures, ensuring adaptive, hierarchical, multi-level institutional steering.
Definition 32 (Governance System).
A governance system
is a finite tuple
where
A is a nonempty finite set of actors;
D is a set of decision rules and procedures (e.g., voting rules, mandates);
lists the governance modes present;
I is a set of steering instruments partitioned as (authority, economic, informational instruments);
P is a set of institutionalized processes (forums, committees, contracts, etc.).
Let denote a nonempty set of such governance systems. A (nonnegative) failure functional quantifies coordination deficits, legitimacy problems, or outcome shortfalls.
Definition 33 (Meta-Governance (level 1)).
Let be the class of governance systems over the fixed . A Meta-Governance structure
is a pair
where is nonempty and
is a preorder on defined componentwise by
and ;
is the compliance predicate of G from Definition .
This satisfies meta-monotonicity
:
Example 17 (Concrete level-1 Meta-Governance with numbers).
Let
. Write rows in the order and columns . Consider with
Then and , hence . Compliance:
The risk profile respects (G1) and (G2): adding coverage (from to ) weakly decreases risk componentwise: and .
Definition 34 (Iterated-Meta-Governance (depth
t )).
For , a depth-
t Iterated-Meta-Governance structure
is a tuple
where is a nonempty set of depth- objects and the lift
is:
Set by the same formula as at base level:
Proposition 9 (Generalization of Meta-Governance). Depth in Definition 34 reduces to Meta-Governance (Definition 33). For one has only base governance systems.
Proof. At the lifted clauses are identities: no f is required beyond and (18)–(19) collapse to the base relations. For , the meta-level disappears. □
Lemma 11 (Axioms preserved by the lift). Fix . If is a preorder and the meta-monotonicities of Definition 33 hold at depth , then:
-
(a)
is a preorder;
-
(b)
is monotone along ;
-
(c)
is monotone along ;
-
(d)
is monotone along .
Proof. (a) Reflexivity is witnessed by . Transitivity: if via f and via g , then witnesses because is transitive.
(b) Suppose via f and . Choose with . Then and level- monotonicity give , hence by (18) we get .
(c) Suppose via f and . Then for all , . By monotonicity at and we have for all G , so by (19), .
(d) Combine (b) and (c) with the definition of . □
Example 18 (Worked depth-2 check using Example 17). Let be the level-1 object containing only and the one containing only . Then witnesses .
Lifted requirement (OR): because ; likewise for .
Lifted coverage (AND): since ; while .
Lifted compliance:, , . Thus compliance is monotone along , in line with Lemma 11(d).
Theorem 9 (Iterated Meta-Governance is an Iterated MetaStructure). There exists a single-sorted signature and a lift such that the family of Definitions 33–34 forms an Iterated MetaStructure in the sense of Definition 3. Moreover, depth coincides with Meta-Governance and the lift is isomorphism-invariant.
Proof. Coding. Let
have unary predicates
,
,
tagging
governance objects ,
assets , and
obligations , and relation symbols
A Meta-Governance structure is represented by a –structure whose carrier is the disjoint union of (tags of) , A , O , with interpreted as (compliance is definable from and ).
Lift. Given a level-
structure, define
by replacing governance-points with depth-
objects and interpreting
by the lifted clauses (
17)–(19). This is a purely relational instance of Definition 2.
Verification. By Lemma 11, is a preorder and , (hence ) are monotone along at every height; these properties are preserved by because the lift only composes witnessing maps f and quantifies over elements of (no choice of representatives is involved). Isomorphism-invariance follows since the definitions use only first-order formulas built from the relations and bounded quantifiers over the carriers, hence are stable under any isomorphism of the lower-level structures.
Depth 1. When there is no lifting and the encoded structure is exactly Definition 33. □
Corollary 8 (Soundness of the governance tower). For every , the object is well defined and forms an Iterated MetaStructure under .
Proof. Immediate from Lemma 11 and Theorem 9 by induction on t . □