Submitted:
16 July 2025
Posted:
16 July 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
- External and also internal threats to a database.
- Users abuse their privileges which could have been gained legally or obtained illegally.
- Audit logs can not always be depended on.
- Discovering breaches are extremely difficult.
- Insiders who misused their account privileges.
- Lost or stolen devices that hold the data of employees.
- Data leakage and cyber threats.
- The Internet.
- Data breaches and database security.
- Data privacy.
- Cyber security measures which are insufficient.
2. What Is the Motivation Behind This Research
3. The Centralised Database and Security
4. Cloud Computing and Database Security
4.1. Abuse of Authority With Security Misconfiguration of The Database and Unpatched Security Vulnerabilities
4.2. The Consequences of Unpatched Software
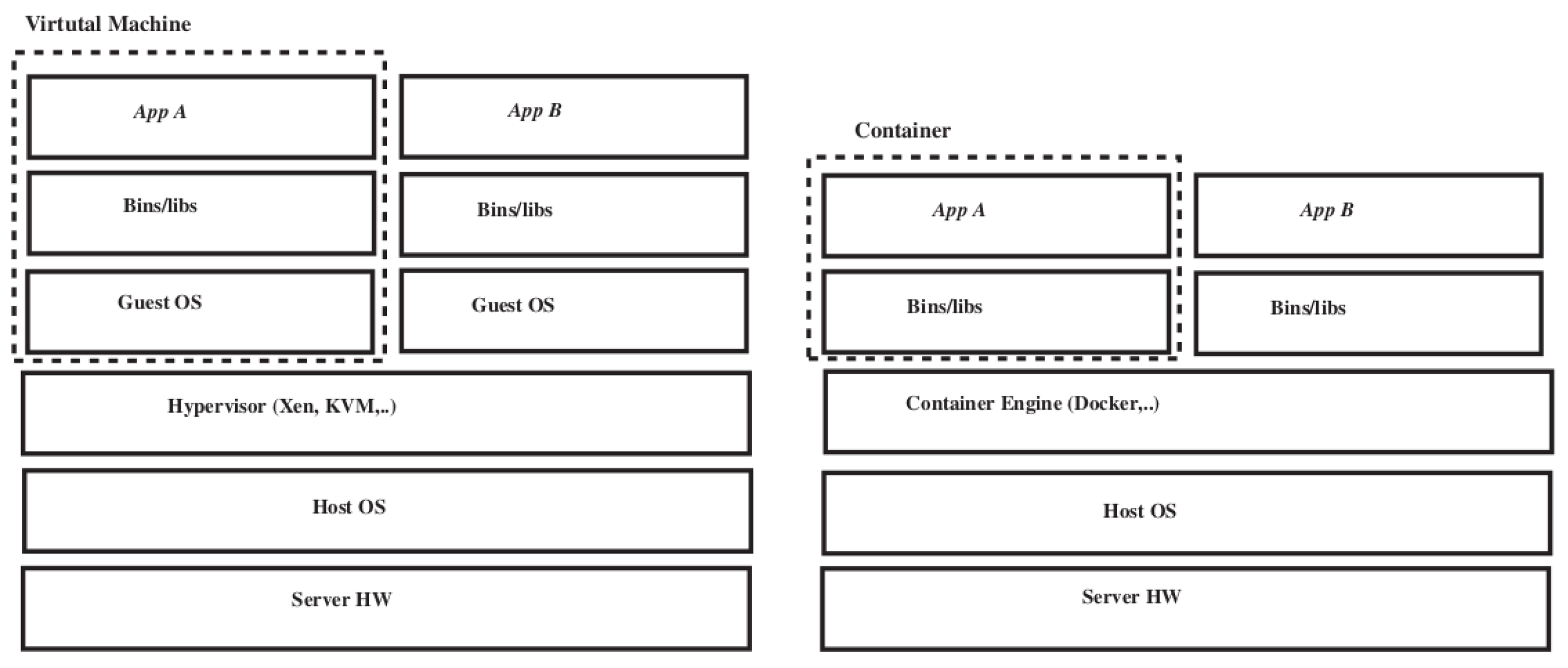
5. The Introduction of Docker
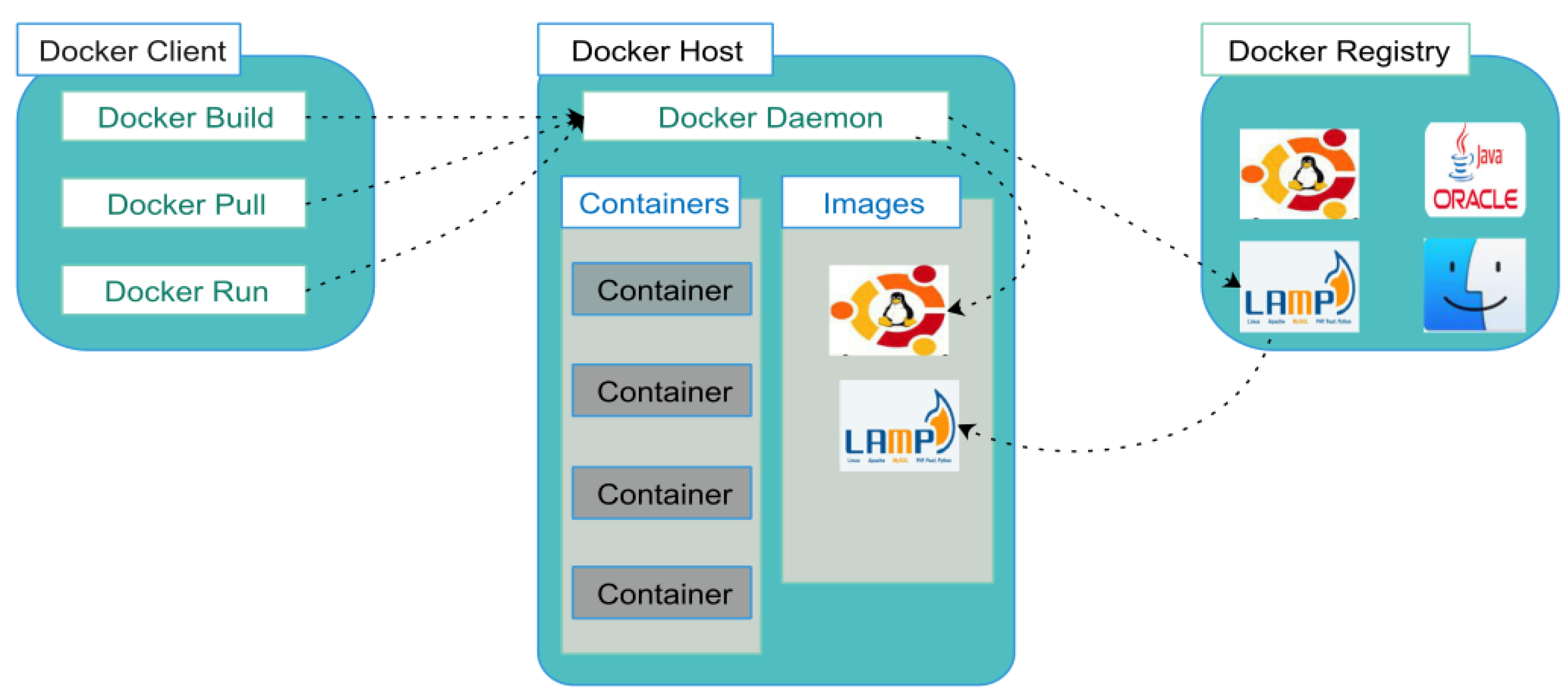
5.1. Docker Architecture
- Docker Images - Firstly, an image can be built in two methods. Using a read-only template is the first method this, is always a base template of the operating system it is built on. To give an illustration, Ubuntu 20.04 when built would only contain the base elements to operate as an operating system. Additionally, creating a Docker file is the second method. This method requires instructions or commands written in a file and when, this file is run in a Linux terminal, this will then build an image Rad et al. [37].
- Docker Containers - Secondly, Docker containers are created from a Docker image. These containers are run in isolation in other words, the Docker containers are mirror images of the Docker image Rad et al. [37].
- Docker Registries - Thirdly, Docker images are placed in docker registries. These images can be either pushed or pulled from a single source. On top of that, there are private and public registries. Docker hub is known as a public registry where, images can be freely uploaded or downloaded Rad et al. [37].
- Docker Client And Server - Lastly, Docker is a client and server based application Rad et al [37].
5.2. Linux Mobile Phones That Ship with Docker Installed
5.3. Docker Updates and Unpatched Software
6. Putting Profit Ahead of Security
7. Data Collection from Two Different Databases Hosted on the Internet
7.1. Measuring Instruments - Psychometrics - Glances
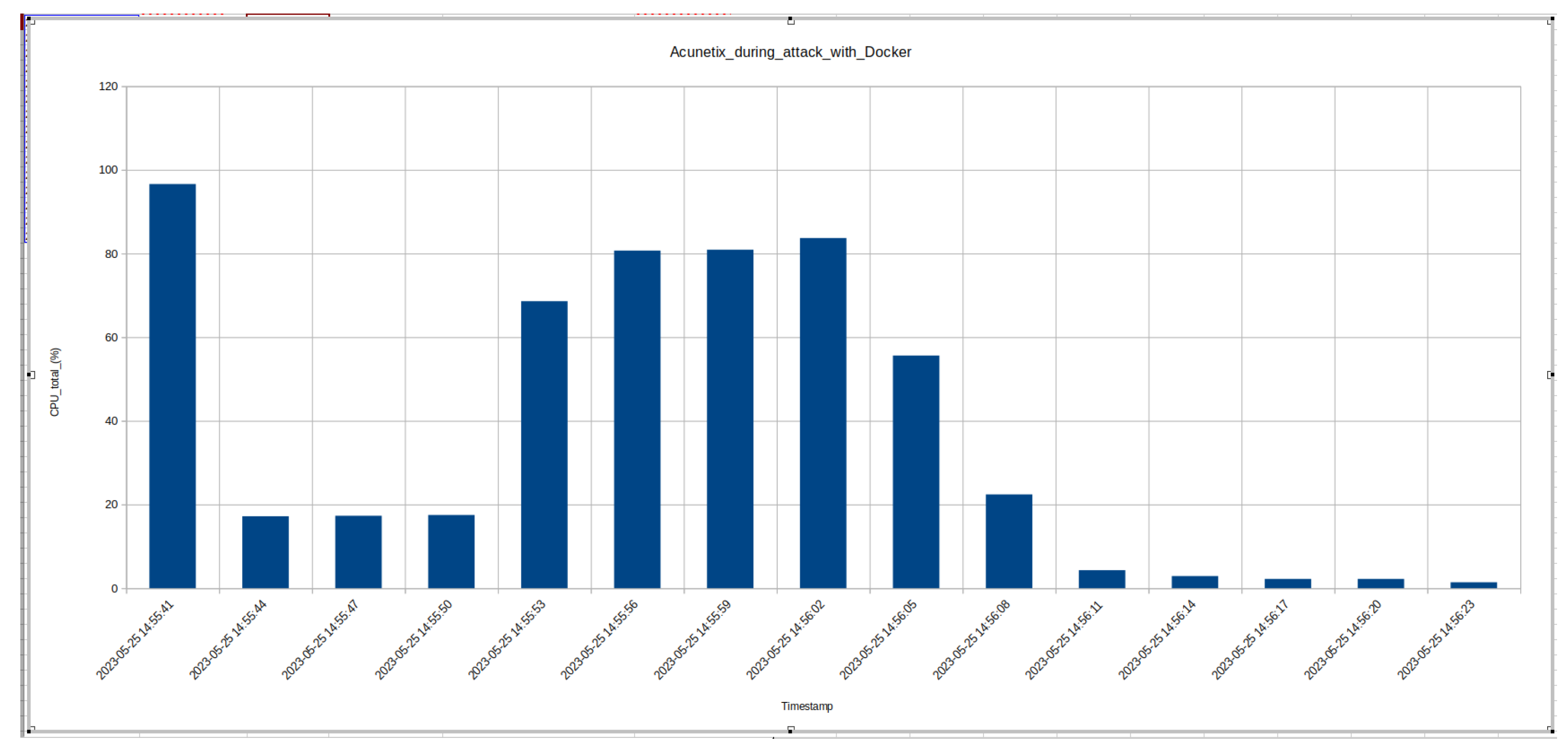
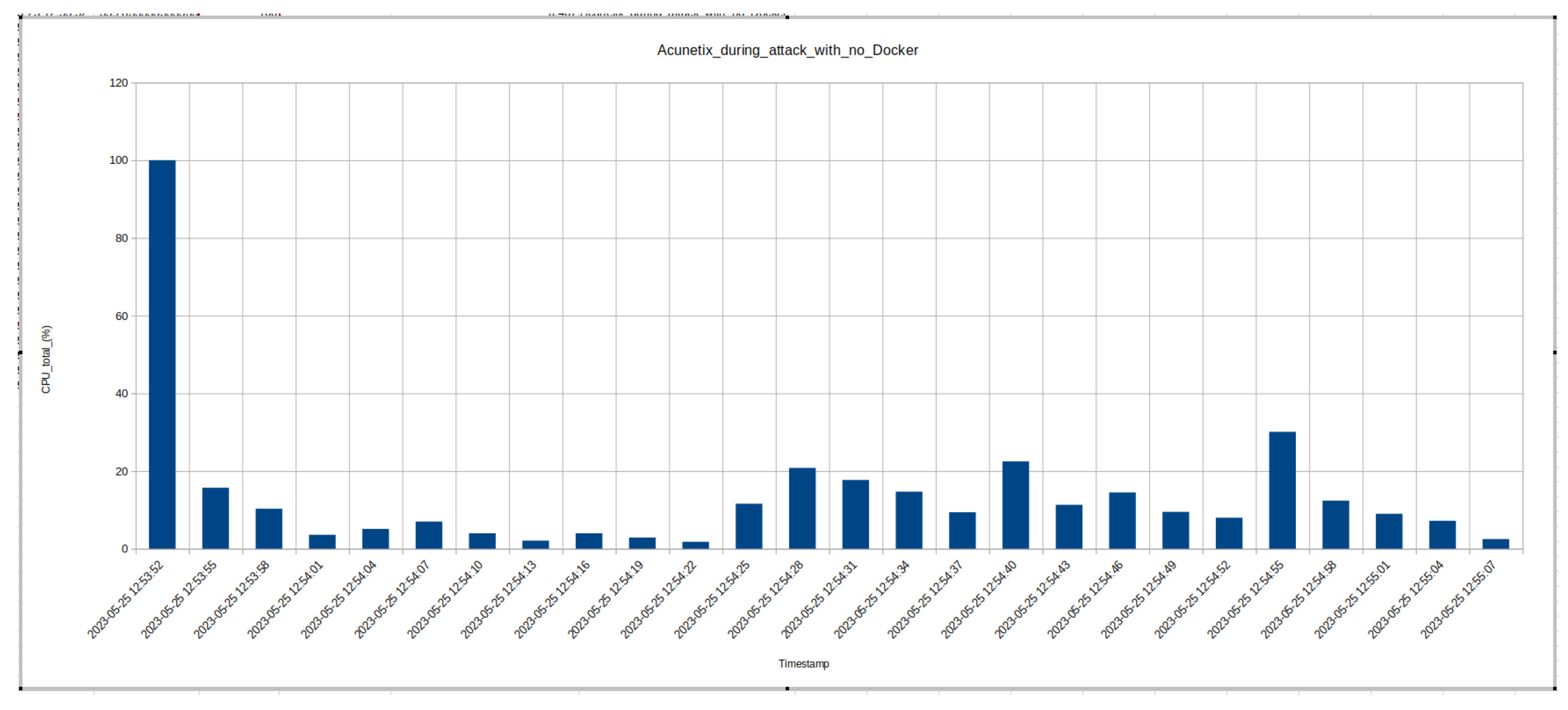
8. Performance Data and Trade Off Results
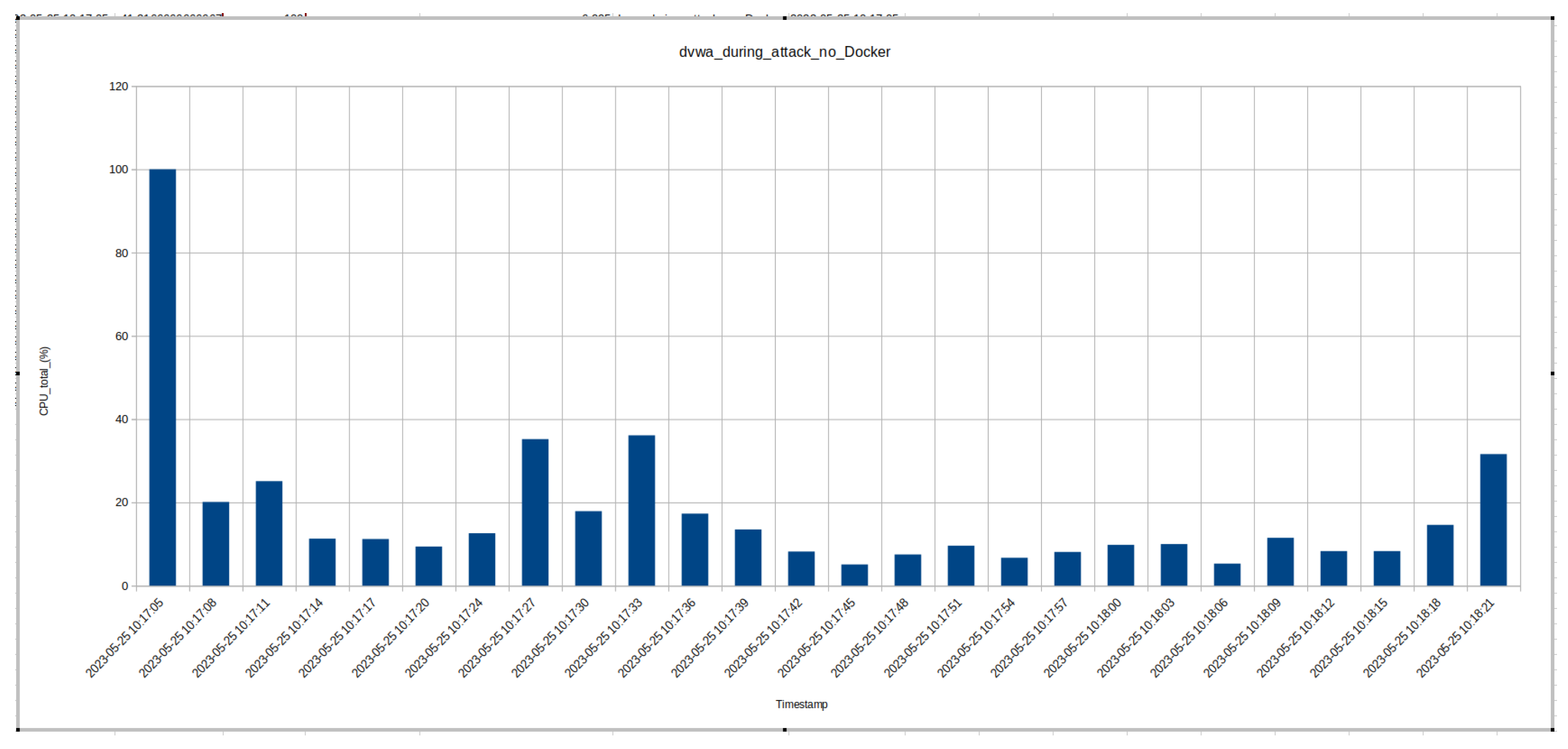
8.1. Performance Data - CPU
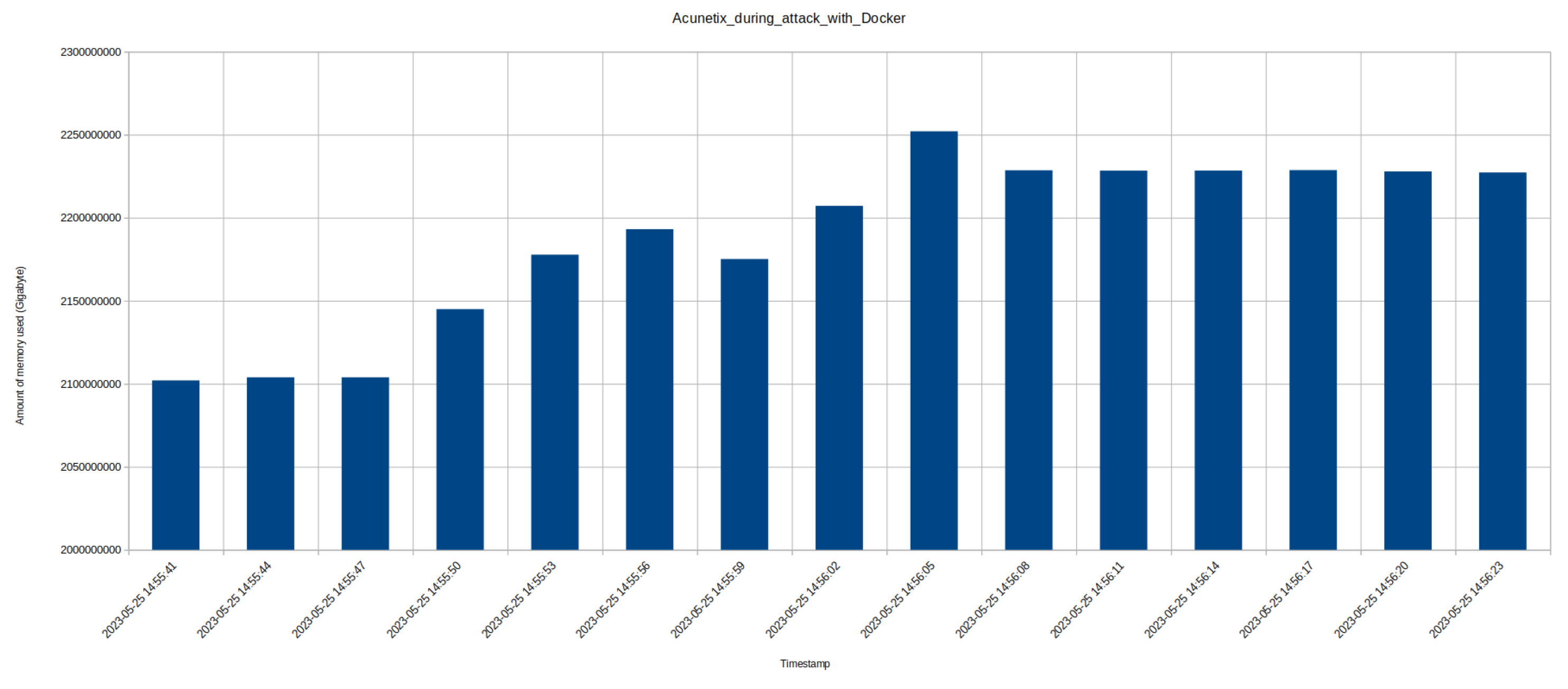
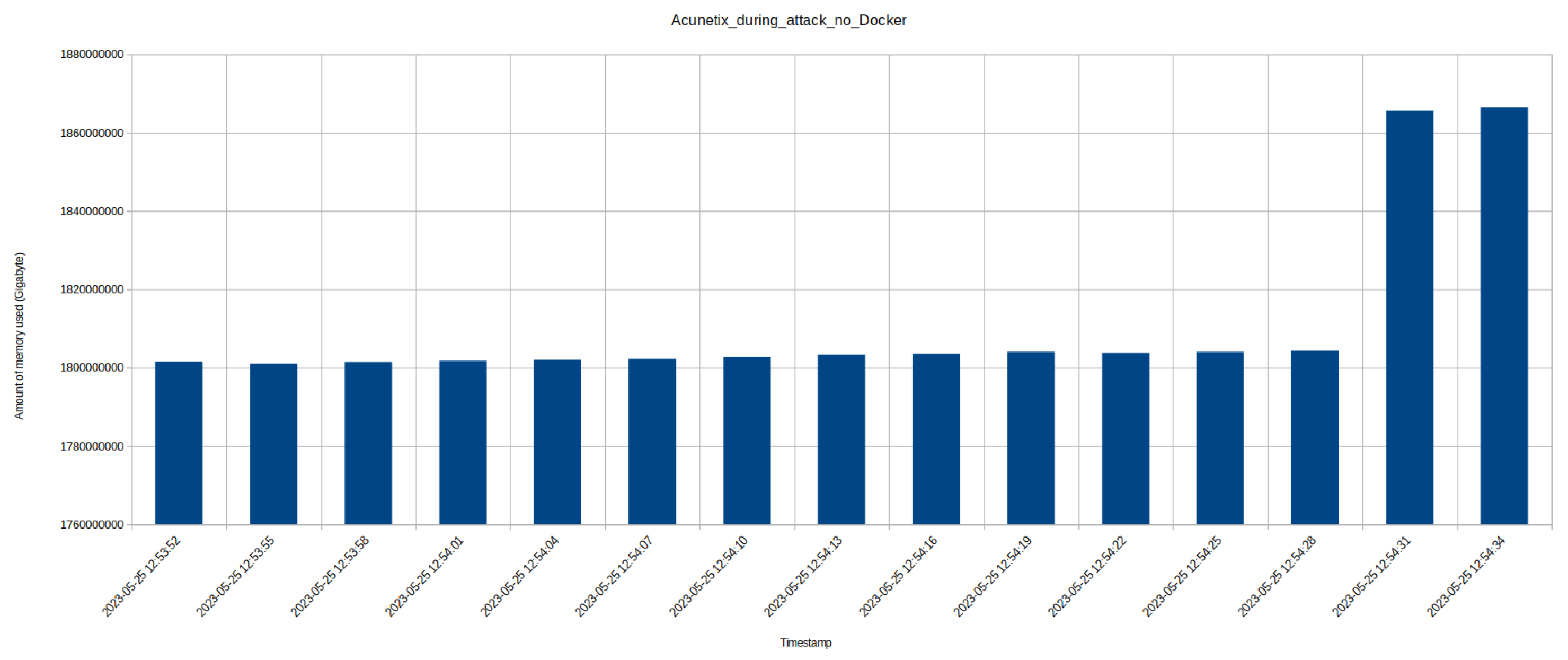
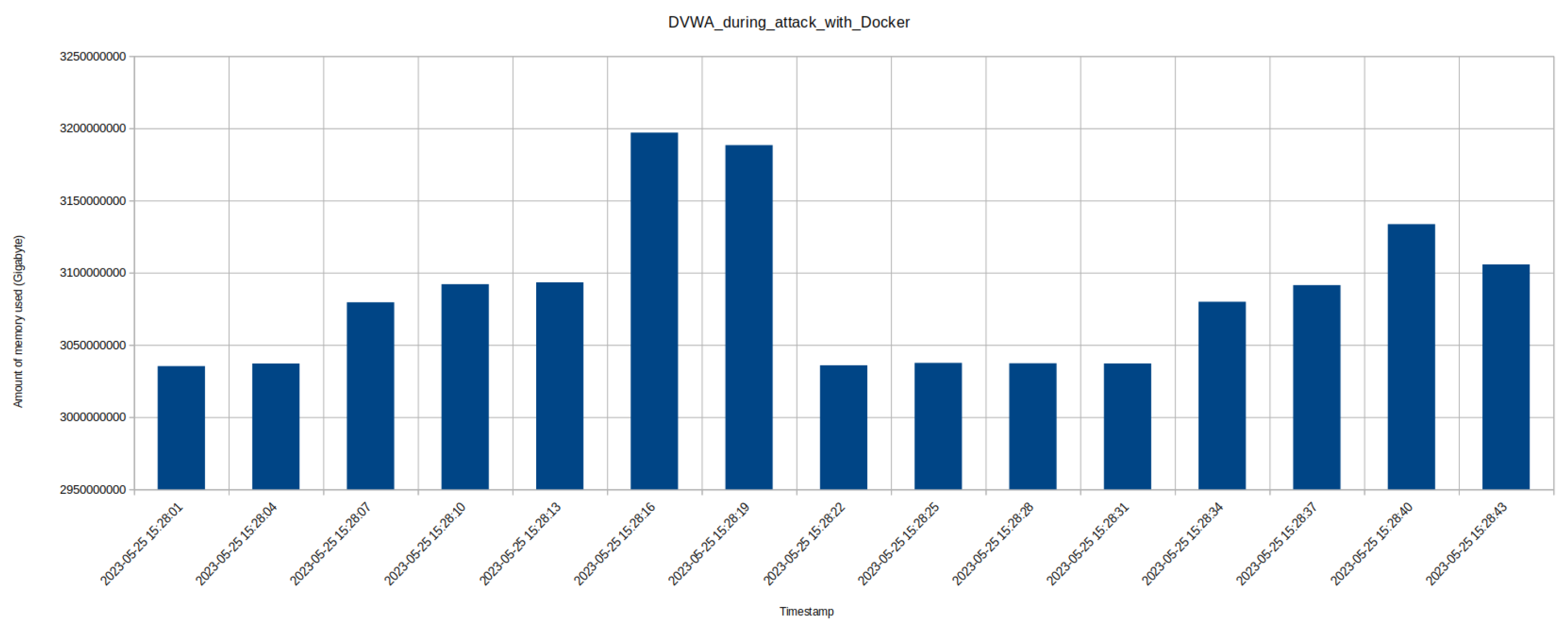
8.2. Performance Data - Memory
9. Summary of Findings
10. Conclusions
References
- Zhao, X.; Lin, Q.; Chen, J.; Wang, X.; Yu, J.; Ming, Z. Optimizing security and quality of service in a Real-time database system using Multi-objective genetic algorithm 2016. 64, 11–23.
- Wagner, J.; Rasin, A.; Glavic, B.; Heart, K.; Furst, J.; Bressan, L.; Grier, J. Carving database storage to detect and trace security breaches 2017. 22, S127–S136. [CrossRef]
- Said, W.; Mostafa, A.M. Towards a Hybrid Immune Algorithm Based on Danger Theory for Database Security 2020. 8, 145332–145362. Conference Name: IEEE Access. [CrossRef]
- Tahir, M.; Abdullah, A.; Udzir, N.I.; Kasmiran, K.A. A novel approach for handling missing data to enhance network intrusion detection system 2024. 3, 100063. [CrossRef]
- Neto, N.N.; Madnick, S.; Paula, A.M.G.D.; Borges, N.M. Developing a Global Data Breach Database and the Challenges Encountered. Journal of Data and Information Quality 2021, 13, 1–33. [CrossRef]
- Algarni, A.M.; Thayananthan, V.; Malaiya, Y.K. Quantitative Assessment of Cybersecurity Risks for Mitigating Data Breaches in Business Systems. Applied Sciences 2021, 11, 3678. Number: 8 Publisher: Multidisciplinary Digital Publishing Institute. [CrossRef]
- Wang, K.C.; Reiter, M.K. Using Amnesia to Detect Credential Database Breaches 2021. p. 18.
- Hassanzadeh, Z.; Biddle, R.; Marsen, S. User Perception of Data Breaches. IEEE Transactions on Professional Communication 2021, 64, 374–389. Conference Name: IEEE Transactions on Professional Communication. [CrossRef]
- Goel, K.; Hofstede, A.H.M.T. Privacy-Breaching Patterns in NoSQL Databases. IEEE Access 2021, 9, 35229–35239. Conference Name: IEEE Access. [CrossRef]
- Miyamoto, E. The Decades-Long Struggle of ‘Comfort Women’ for Justice 2023. 6, 272–278. Number: 1. [CrossRef]
- Seidelman, W.E. Nuremberg lamentation: for the forgotten victims of medical science. BMJ : British Medical Journal 1996, 313, 1463–1467.
- Zaw, T.M.; Thant, M.; Bezzateev, S. Database Security with AES Encryption, Elliptic Curve Encryption and Signature. In Proceedings of the 2019 Wave Electronics and Its Application in Information and Telecommunication Systems (weconf), New York, 2019. WOS:000635354100017.
- Santos, N.; Younis, W.; Ghita, B.; Masala, G. Enhancing Medical Data Security on Public Cloud. In Proceedings of the 2021 IEEE International Conference on Cyber Security and Resilience (CSR), 2021, pp. 103–108. [CrossRef]
- Crooks, N. A Client-centric Approach to Transactional Datastores. In Proceedings of the Proceedings of the 2021 International Conference on Management of Data. ACM, 2021, pp. 3–5. [CrossRef]
- Toapanta, S.M.T.; Gallegos, L.E.M.; Trejo, J.A.O. Security analysis of civil registry database of Ecuador. In Proceedings of the 2016 International Conference on Electrical, Electronics, and Optimization Techniques (ICEEOT). IEEE, 2016, pp. 1024–1029. [CrossRef]
- Perri, D.; Simonetti, M.; Gervasi, O. Deploying Efficiently Modern Applications on Cloud. Electronics 2022, 11, 450. Number: 3 Publisher: Multidisciplinary Digital Publishing Institute. [CrossRef]
- Nelson Novaes Neto.; Stuart Madnick.; Anchises Moraes G. de Paula.; Natasha Malara Borges. Cyber Security Data Breaches, 2022.
- Ding, Y.; Sato, H. Dagbase: A Decentralized Database Platform Using DAG-Based Consensus. In Proceedings of the 2020 Ieee 44th Annual Computers, Software, and Applications Conference (compsac 2020); Chan, W.K.; Claycomb, B.; Takakura, H.; Yang, J.J.; Teranishi, Y.; Towey, D.; Segura, S.; Shahriar, H.; Reisman, S.; Ahamed, S.I., Eds., New York, 2020; pp. 798–807. ISSN: 0730-3157 WOS:000629086600105. [CrossRef]
- Samaraweera, G.D.; Chang, J.M. Security and Privacy Implications on Database Systems in Big Data Era: A Survey 2021. 33, 239–258. Conference Name: IEEE Transactions on Knowledge and Data Engineering. [CrossRef]
- Nash, T.; Olmsted, A. Performance vs. security: Implementing an immutable database in MySQL. In Proceedings of the 2017 12th International Conference for Internet Technology and Secured Transactions (ICITST). IEEE, 2017, pp. 290–291. [CrossRef]
- Lee, B.H.; Dewi, E.K.; Wajdi, M.F. Data Security in Cloud Computing Using AES Under HEROKU Cloud. In Proceedings of the 2018 27th Wireless and Optical Communication Conference (wocc), New York, 2018; pp. 242–246. ISSN: 2379-1268 WOS:000443454700060.
- Odirichukwu, J.C.; Asagba, P.O. Security concept in web database development and administration — A review perspective. In Proceedings of the 2017 IEEE 3rd International Conference on Electro-Technology for National Development (NIGERCON), 2017, pp. 383–391. ISSN: 2377-2697. [CrossRef]
- Deepa, G.; Thilagam, P.S. Securing web applications from injection and logic vulnerabilities 2016. 74, 160–180. [CrossRef]
- Park, J.H.; Yoo, S.M.; Kim, I.S.; Lee, D.H. Security Architecture for a Secure Database on Android. Ieee Access 2018, 6, 11482–11501. Place: Piscataway Publisher: Ieee-Inst Electrical Electronics Engineers Inc WOS:000622030100002. [CrossRef]
- Gao, B. Path Analysis of Using Big Data to Build Engineering Cost Database under the Background of Information Management. In Proceedings of the 2020 5th International Conference on Mechanical, Control and Computer Engineering (ICMCCE). IEEE, 2020, pp. 1963–1966. [CrossRef]
- Khan, W.; Ahmad, W.; Luo, B.; Ahmed, E. SQL Database with physical database tuning technique and NoSQL graph database comparisons. In Proceedings of the Proceedings of 2019 Ieee 3rd Information Technology, Networking, Electronic and Automation Control Conference (itnec 2019); Xu, B., Ed., New York, 2019; pp. 110–116. WOS:000491352900022.
- Elem, M.; Elem, N.; Obinna, C. Online Database Security Threats and Solutions: The NetFlix Incident 2020. 5, 6.
- Huijie, W. A Security Framework for Database Auditing System. In Proceedings of the 2017 10th International Symposium on Computational Intelligence and Design (iscid), Vol. 1, New York, 2017; pp. 350–353. ISSN: 2165-1701 WOS:000427991100080. [CrossRef]
- Jusak, J.; Mahmoud, S.S.; Laurens, R.; Alsulami, M.; Fang, Q. A New Approach for Secure Cloud-Based Electronic Health Record and its Experimental Testbed. IEEE Access 2022, 10, 1082–1095. Conference Name: IEEE Access. [CrossRef]
- Kalkman, S.; van Delden, J.; Banerjee, A.; Tyl, B.; Mostert, M.; van Thiel, G. Patients’ and public views and attitudes towards the sharing of health data for research: a narrative review of the empirical evidence. Journal of Medical Ethics 2022, 48, 3–13. [CrossRef]
- He, Y.; Maglaras, L.; Aliyu, A.; Luo, C. Healthcare Security Incident Response Strategy - A Proactive Incident Response (IR) Procedure 2022. 2022, 1–10. [CrossRef]
- Khan, S.; Kabanov, I.; Hua, Y.; Madnick, S. A Systematic Analysis of the Capital One Data Breach: Critical Lessons Learned 2023. 26, 1–29. [CrossRef]
- Liu, J.; Ni, X. Ordeal by innocence in the big-data era: Intended data breach disclosure, unintended real activities manipulation 2023. n/a. _eprint: https://onlinelibrary.wiley.com/doi/pdf/10.1111/eufm.12410. [CrossRef]
- Li, Y.; Mamon, R. Modelling health-data breaches with application to cyber insurance 2023. 124, 102963. [CrossRef]
- Vinicius, L.; Rodrigues, L.; Torquato, M.; Silva, F.A. Docker platform aging: a systematic performance evaluation and prediction of resource consumption 2022. 78, 1–31. [CrossRef]
- Ahmed, A.; Pierre, G. Docker Image Sharing in Distributed Fog Infrastructures. In Proceedings of the 2019 IEEE International Conference on Cloud Computing Technology and Science (CloudCom), 2019, pp. 135–142. ISSN: 2330-2186. [CrossRef]
- Rad, B.B.; Bhatti, H.J.; Ahmadi, M. An Introduction to Docker and Analysis of its Performance. International Journal of Computer Science and Network Security 2017, 17, 228–235. Place: Seoul Publisher: Int Journal Computer Science & Network Security-Ijcsns WOS:000402797500027.
- Pratap Yadav, M.; Pal, N.; Kumar Yadav, D. A formal approach for Docker container deployment. Concurrency and Computation: Practice and Experience 2021, 33. [CrossRef]
- Musleh, S.; Islam, M.T.; Qureshi, R.; Alajez, N.M.; Alam, T. MSLP: mRNA subcellular localization predictor based on machine learning techniques 2023. 24, 109. [CrossRef]
- Want, R. When Cell Phones Become Computers 2009. 8, 2–5. Conference Name: IEEE Pervasive Computing. [CrossRef]
- Qian, K.; Lo, D.; Shahriar, H.; Li, L.; Wu, F.; Bhattacharya, P. Learning Database Security with Hands-on Mobile Labs. In Proceedings of the 2017 Ieee Frontiers in Education Conference (fie), New York, 2017. ISSN: 0190-5848 WOS:000426974900282.
- Keim, Y.; Yoon, Y.H.; Karabiyik, U. Digital Forensics Analysis of Ubuntu Touch on PinePhone 2021. 10, 343. [CrossRef]
- Jain, V.; Singh, B.; Choudhary, N.; Yadav, P.K. A Hybrid Model for Real-Time Docker Container Threat Detection and Vulnerability Analysis 2023. 11, 782–793. Number: 6s.
- Doan, P.; Jung, S. DAVS: Dockerfile Analysis for Container Image Vulnerability Scanning 2022. 72, 1699–1711. [CrossRef]
- Wu, Y.; Zhang, Y.; Wang, T.; Wang, H. Dockerfile Changes in Practice: A Large-Scale Empirical Study of 4,110 Projects on GitHub. In Proceedings of the 2020 27th Asia-Pacific Software Engineering Conference (APSEC), 2020, pp. 247–256. ISSN: 2640-0715. [CrossRef]
- Leahy, D.; Thorpe, C. Zero Trust Container Architecture (ZTCA): A Framework for Applying Zero Trust Principals to Docker Containers. International Conference on Cyber Warfare and Security 2022, 17, 111–120. Number: 1. [CrossRef]
- Bettini, A.; Com, F. VULNERABILITY EXPLOITATION IN DOCKER CONTAINER ENVIRONMENTS 2015.
- Sultan, S.; Ahmad, I.; Dimitriou, T. Container Security: Issues, Challenges, and the Road Ahead 2019. 7, 52976–52996. Conference Name: IEEE Access. [CrossRef]
- Wist, K.; Helsem, M.; Gligoroski, D. Vulnerability Analysis of 2500 Docker Hub Images, 2020, [2006.02932 [cs]].
- Lu, T.; Chen, J. Research of Penetration Testing Technology in Docker Environment. Atlantis Press, 2017, pp. 1354–1359. ISSN: 2352-5401. [CrossRef]
- Alwabel, A. A Novel Container Placement Mechanism Based on Whale Optimization Algorithm for CaaS Clouds 2023. 12, 3369. Number: 15 Publisher: Multidisciplinary Digital Publishing Institute. [CrossRef]
- Patra, M.K.; Sahoo, B.; Turuk, A.K.; Misra, S. Task grouping and optimized deep learning based VM sizing for hosting containers as a service 2023. 12, 65. [CrossRef]
- Turuk, Bibhudatta Sahoo, A.K.M.K.P. Container as a Service in the Cloud: An Approach to Secure Hybrid Virtualization. In Recent Trends and Best Practices in Industry 4.0; River Publishers, 2023. Num Pages: 18.
- Patra, M.K.; Misra, S.; Sahoo, B.; Turuk, A.K. GWO-Based Simulated Annealing Approach for Load Balancing in Cloud for Hosting Container as a Service 2022. 12, 11115. Number: 21 Publisher: Multidisciplinary Digital Publishing Institute. [CrossRef]
- O’Dowd, A. Labour calls for inquiry into NHS cyber-attack 2017. 357, j2395. Publisher: British Medical Journal Publishing Group Section: News. [CrossRef]
- Aljaidi, M.; Alsarhan, A.; Samara, G.; Alazaidah, R.; Almatarneh, S.; Khalid, M.; Al-Gumaei, Y.A. NHS WannaCry Ransomware Attack: Technical Explanation of The Vulnerability, Exploitation, and Countermeasures. In Proceedings of the 2022 International Engineering Conference on Electrical, Energy, and Artificial Intelligence (EICEEAI), 2022, pp. 1–6. [CrossRef]
- Tyagi, S.; Kumar, K. Evaluation of Static Web Vulnerability Analysis Tools. In Proceedings of the 2018 Fifth International Conference on Parallel, Distributed and Grid Computing (PDGC). IEEE, 2018, pp. 1–6. [CrossRef]
- Costa, G.; Russo, E.; Valenza, A. Damn Vulnerable Application Scanner 2021. p. 15.
- Makino, Y.; Klyuev, V. Evaluation of web vulnerability scanners. In Proceedings of the 2015 IEEE 8th International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS). IEEE, 2015, pp. 399–402. [CrossRef]
- Nagpure, S.; Kurkure, S. Vulnerability Assessment and Penetration Testing of Web Application. In Proceedings of the 2017 International Conference on Computing, Communication, Control and Automation (ICCUBEA). IEEE, 2017, pp. 1–6. [CrossRef]
- Vyamajala, S.; Mohd, T.K.; Javaid, A. A Real-World Implementation of SQL Injection Attack Using Open Source Tools for Enhanced Cybersecurity Learning. In Proceedings of the 2018 IEEE International Conference on Electro/Information Technology (EIT). IEEE, 2018, pp. 0198–0202. [CrossRef]
- Manore, C.; Manjunath, P.; Larkin, D. Performance of Single Board Computers for Vision Processing. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC). IEEE, 2021, pp. 0883–0889. [CrossRef]
- Kok, G.X.; Choong, K.N.; Vethanayagam, C.; Owada, Y.; Sato, G. An Analysis of a Large Scale Wireless Image Distribution System Deployment. In Proceedings of the 2019 IEEE 9th Symposium on Computer Applications & Industrial Electronics (ISCAIE). IEEE, 2019, pp. 150–155. [CrossRef]
- Ajasa, A.D.; Chizari, H.; Alam, A. Database Security and Performance: A Case of SQL Injection Attacks Using Docker-Based Virtualisation and Its Effect on Performance. Future Internet 2025, 17, 156. Number: 4 Publisher: Multidisciplinary Digital Publishing Institute. [CrossRef]
- Choquette, J.; Gandhi, W.; Giroux, O.; Stam, N.; Krashinsky, R. NVIDIA A100 Tensor Core GPU: Performance and Innovation. IEEE Micro 2021, 41, 29–35. Conference Name: IEEE Micro. [CrossRef]
- Singh, N.; Hamid, Y.; Juneja, S.; Srivastava, G.; Dhiman, G.; Gadekallu, T.R.; Shah, M.A. Load balancing and service discovery using Docker Swarm for microservice based big data applications 2023. 12, 4. [CrossRef]
- Gore, R.; Banerjea, S.; Tyagi, N.; Saurav, S.; Acharya, D.; Verma, V. An Efficient Edge Analytical Model on Docker Containers for Automated Monitoring of Public Restrooms in India. In Proceedings of the 2020 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS). IEEE, 2020, pp. 1–6. [CrossRef]
- Velasquez, W.; Munoz-Arcentales, A.; Salvachua Rodriguez, J. A Case Study: Ingestion Analysis of WSN Data in Databases using Docker. In Proceedings of the 2018 1st International Conference on Computer Applications & Information Security (iccais’ 2018), New York, 2018. WOS:000493071300040.
- Reis, D.; Piedade, B.; Correia, F.F.; Dias, J.P.; Aguiar, A. Developing Docker and Docker-Compose Specifications: A Developers’ Survey. IEEE Access 2022, 10, 2318–2329. Conference Name: IEEE Access. [CrossRef]
- Alkhimenkov, Y. Digital rock physics: Calculation of effective elastic properties of heterogeneous materials using graphical processing units (GPUs). Computers & Geosciences 2025, 194, 105749. [CrossRef]
- Castaño-Díez, D.; Moser, D.; Schoenegger, A.; Pruggnaller, S.; Frangakis, A.S. Performance evaluation of image processing algorithms on the GPU. Journal of Structural Biology 2008, 164, 153–160. [CrossRef]
- Saha, P.; Govindaraju, M.; Marru, S.; Pierce, M. Integrating Apache Airavata with Docker, Marathon, and Mesos 2016. 28, 1952–1959. _eprint: https://onlinelibrary.wiley.com/doi/pdf/10.1002/cpe.3708. [CrossRef]
- Aleksandrovs-Moisejs, D.; Ipatovs, A.; Grabs, E.; Rjazanovs, D. Evaluation of a Long-Distance IEEE 802.11ah Wireless Technology in Linux Using Docker Containers 2022. 28, 71–77. Number: 3. [CrossRef]
- Seifi, N.; Al-Mamun, A. Optimizing Memory Access Efficiency in CUDA Kernel via Data Layout Technique. Journal of Computer and Communications 2024, 12, 124–139. [CrossRef]


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




