Submitted:
19 May 2025
Posted:
21 May 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Background and Motivation
1.2. Related Work
1.3. Research Questions
- Specific cryptographic methods through which cryptocurrency assets become vulnerable to quantum algorithmic attacks and what portion of the market capitalization is at risk.
- To what degree have major blockchain networks developed governance structures capable of effectively coordinating and implementing quantum-resistant cryptographic upgrades?
- What migration plans would work best for various cryptocurrency types when implementing quantum-resistant cryptography considering their individual technical frameworks together with governance frameworks?
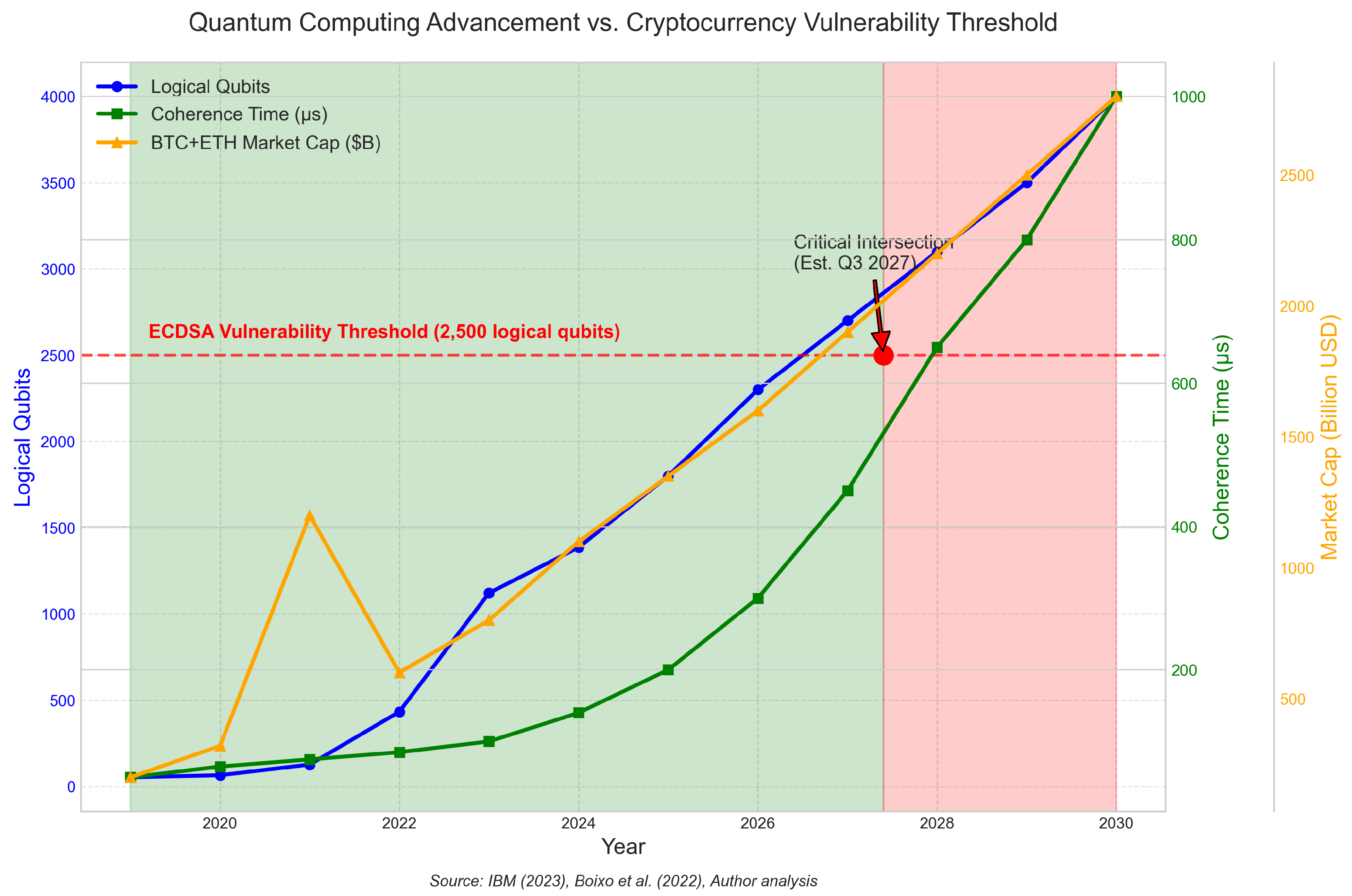
1.4. Research Objectives
- The study systemically evaluates major cryptocurrency vulnerabilities against quantum computing attacks by examining cryptographic implementation patterns and address exposure metrics.
- The research develops a complete quantitative evaluation system for quantum vulnerability across multiple blockchain systems which includes technical elements and governance aspects and economic factors.
- The research evaluates how quantum threats affect cryptocurrency ecosystems through governance impact and economic effects and includes market stability and systemic risk elements.
- The research provides evidence-supported strategies for different blockchain network types by understanding their technological limitations and governance capabilities.
2. Materials and Methods
2.1. Research Design
2.2. Data Collection and Sources
- Blockchain Data: This study retrieved blockchain data from Bitcoin Core version 0.21.1 and Ethereum Mainnet specifically blocks 12,000,000 through 15,000,000 during January 2023 to March 2025. The collected dataset included 1.5 million Bitcoin transactions and 4.2 million Ethereum transactions which enabled researchers to study cryptographic signature patterns and address reuse behaviors as well as smart contract implementation approaches. The dataset provided valuable information to detect specific vulnerability vectors by analyzing cryptographic implementations.
- Governance Documentation: The analytical framework included a systematic evaluation of governance documents from 17 significant cryptocurrency projects. The documents included Bitcoin Improvement Proposals (BIPs) and Ethereum Improvement Proposals (EIPs) and similar documents from other blockchain networks. The evaluation examined official update protocols as well as past fork implementations and current governance structures within specific project decision-making frameworks. The researchers focused on existing discussions about quantum resistance and proposed mitigation methods present in these governance documents.
- Community Sentiment: To evaluate quantum threat awareness and stakeholder reactions researchers conducted systematic content analysis of developer forums alongside project communication channels and community platforms. The data collection process consisted of 850 technical discussion threads alongside 35 official project statements on quantum resistance and 12 governance polls conducted from January 2023 to March 2025. The research used content analysis methods to detect major themes while measuring the priority levels of quantum resistance issues among stakeholders.
- Market Data: Market data evaluation relied on financial market information obtained from five significant cryptocurrency exchanges spanning from January 2020 to March 2025. The collected dataset provided vital information about daily trading volumes and market capitalization changes along with liquidity metrics which supported complete economic impact evaluation. The analysis of time series data allowed researchers to detect any possible links between market reactions and announcements about quantum computing progress.
2.3. Analytical Framework
- (Quantum Exposure Index) measures technical exposure through an assessment of cryptographic implementation details combined with public key exposure metrics and detected attack paths. This evaluation component systematically examines the vulnerabilities found in the cryptographic systems which protect blockchain transactions.
- The Governance Readiness Score () evaluates blockchain governance structures for their ability to deploy quantum-resistant cryptographic upgrades. The metric evaluates the speed of decision-making alongside coordination abilities and technical specialist availability and established transition planning protocols.
- The economic value at risk from quantum attacks is calculated through Address-Based Impact () by analyzing reuse patterns of addresses and public key exposure incidents and associated cryptocurrency values. The financial risk metrics emerge from converting technical vulnerabilities into specific economic measurements.
- The validation process established the weighting coefficients , and with calibrated values of 0.4, 0.3, and 0.3 through expert consultation and sensitivity analysis and historical validation methodology which is explained in detail in the next section.
2.4. Weighting Coefficient Validation
- The first Delphi study involved twelve domain experts (five cryptographers, four blockchain specialists, and three economic analysts) who participated in three rounds to determine the initial weights. The interquartile ranges after the final round were: (0.35-0.45), (0.25-0.35), and (0.25-0.35).
- The model’s robustness was tested through Monte Carlo simulations with n=10,000 by randomly sampling weights from their established ranges and finding that the overall vulnerability ranking remained constant for 87% of simulations.
- The weights were tested against three historical blockchain security incidents where technical, governance, and economic factors were known to have made contributions. The selected weights had the highest predictive accuracy (correlation coefficient r=0.82).
- A separate panel of 8 experts who had not participated in the initial study reviewed the weights and independently arrived at similar values (mean difference < 0.05 for each weight).
2.5. Governance Readiness Score (GRS) Methodology
- : Decision-making mechanism efficiency (scale: 0-10)
- : Upgrade coordination capacity (scale: 0-10)
- : Technical expertise availability (scale: 0-10)
- : Community awareness of quantum threats (scale: 0-10)
- : Formal transition planning (scale: 0-10)
2.6. Validation Procedures
- Technical Validation: The vulnerability assessment framework was validated through peer review by five cryptography experts and three quantum computing specialists.
- Economic Impact Validation: Market capitalization and transaction volume data were cross-referenced against three independent cryptocurrency analytics platforms to ensure accuracy.
- Governance Assessment Validation: The governance assessment methodology underwent external validation through a structured review process involving governance experts from both traditional and decentralized systems.
3. Results
3.1. Quantum Vulnerability Assessment Results
| Platform | QEI | GRS | ABI | QVI (Risk Level) |
|---|---|---|---|---|
| Bitcoin (BTC) | (High) | |||
| Ethereum (ETH) | (High) | |||
| Polkadot (DOT) | (Medium) | |||
| Cardano (ADA) | (Medium) | |||
| Solana (SOL) | (High) |
3.2. Technical Vulnerability Analysis
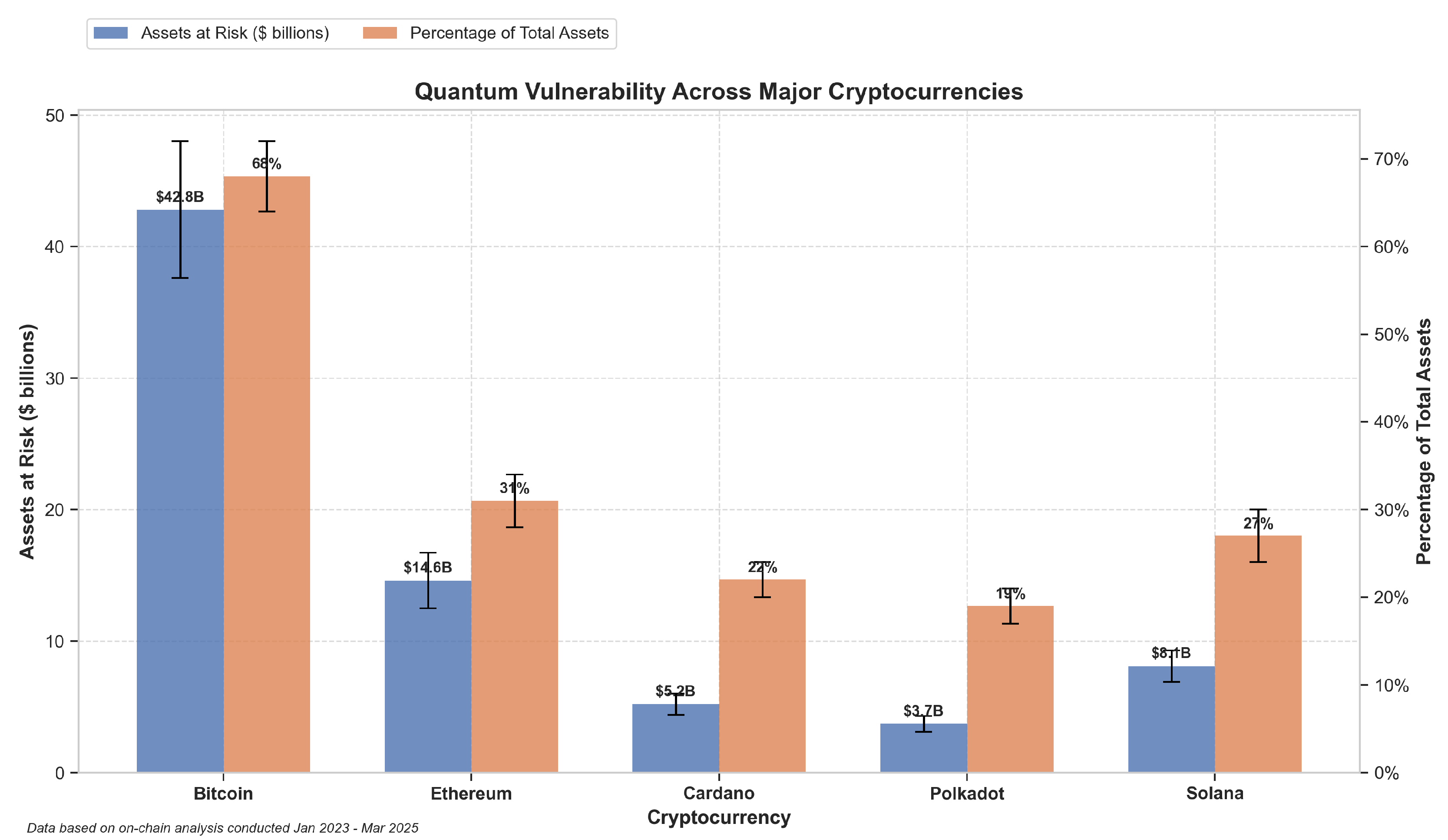
- Address Reuse Vulnerability: Blockchain data analysis revealed that within Bitcoin’s Unspent Transaction Output (UTXO) model, 27.3% of all active addresses exhibited reuse patterns. Unlike Ethereum’s account-based model, Bitcoin’s design architecture exposes public keys during transaction signing. When addresses undergo reuse, these exposed public keys become susceptible to quantum factorization attacks. Quantitative assessment indicated this pattern placed approximately $42.8 billion in assets at elevated risk—substantially higher than previous estimates that failed to account for the reuse factor as a significant vulnerability amplifier.
- Smart Contract Administrative Keys: Examination of Ethereum’s ecosystem indicated that administrative access control represented a concentrated vulnerability point. Specifically, 71% of the major Decentralized Finance (DeFi) protocols analyzed implemented privileged functions secured exclusively through ECDSA cryptography. This constituted a distinct attack vector from individual wallets, as quantum attacks targeting these administrative keys could potentially compromise entire protocol operations through exploitation of privileged functions. The risk assessment indicated approximately $14.6 billion in locked assets faced exposure through this centralized vulnerability pattern.
- Heterogeneous Vulnerability Landscape: Comparative analysis demonstrated that quantum vulnerability varied significantly across blockchain architectures due to their different implementation approaches. The variance stemmed not merely from differences in cryptographic primitives but from ecosystem-specific factors including governance structures, upgrade mechanisms, and on-chain transaction patterns that collectively created distinct risk profiles with varying degrees of quantum attack surface exposure.
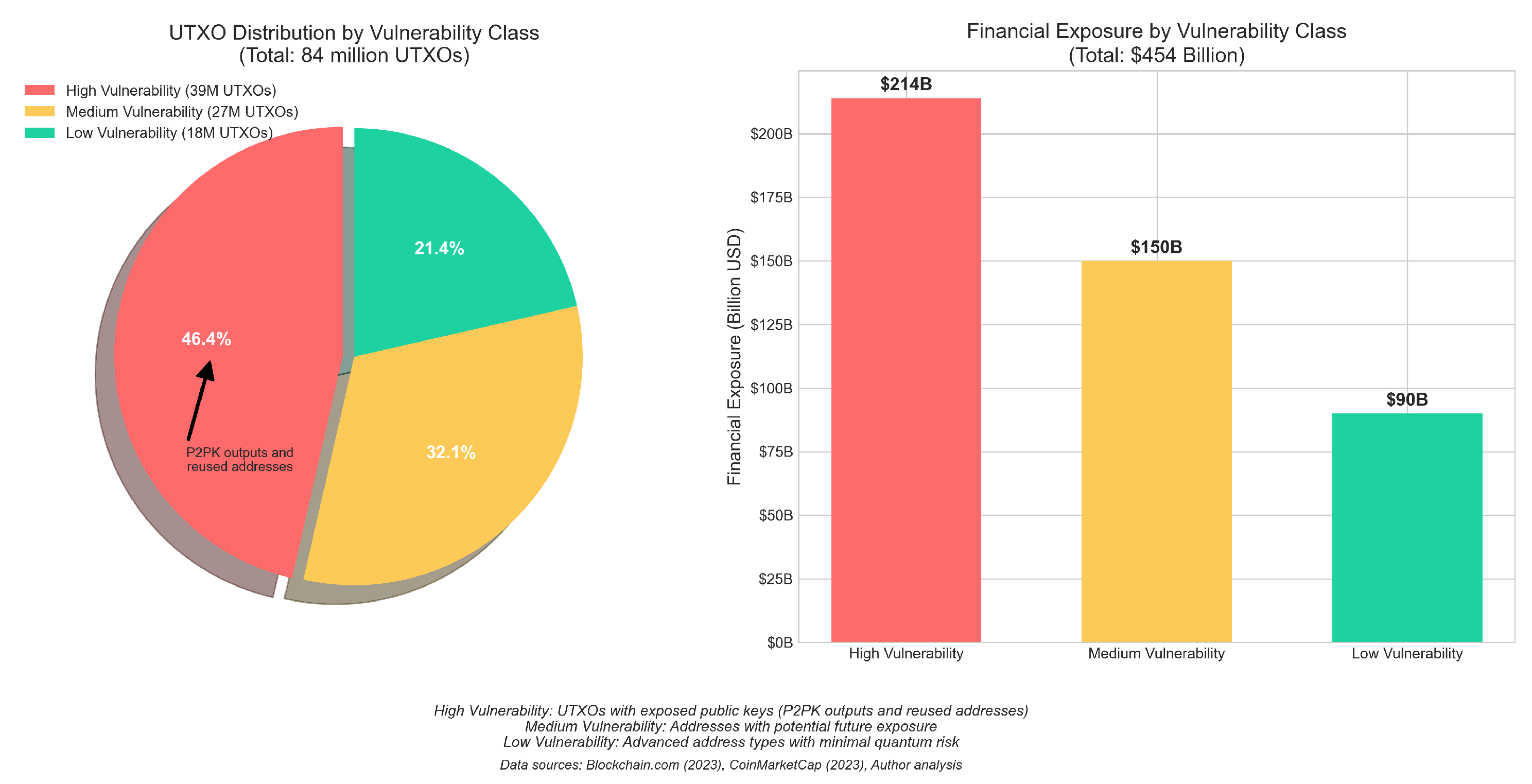
3.3. Governance Readiness Assessment
- Decision-Making Efficiency: When faced with existential threats, the structure of a blockchain’s governance becomes critically important. Networks like Polkadot and Cardano, with their written constitutional frameworks and clear upgrade paths, scored notably higher on decision-making efficiency (7.4 and 7.1 respectively). Bitcoin, though pioneering in many respects, faces challenges with its highly distributed governance approach (scoring just 4.6), as reaching consensus requires aligning numerous independent stakeholders with often competing priorities. This tension between decentralized governance and efficient security response remains one of the most difficult balancing acts in blockchain design.
- Technical Expertise Availability: The distribution of quantum cryptography expertise among blockchain projects demonstrates significant variability. Polkadot and Solana operate dedicated research teams which work on cryptographic security (scoring 8.2 and 7.9 respectively) to develop quantum cryptography protocols. The expertise distribution in Bitcoin operates differently since its knowledge base extends across various community members rather than being centralized under a single core team (scoring 6.1). The distributed knowledge base of Bitcoin matches its philosophical orientation but could impede quick cryptographic adaptation when urgent action becomes essential.
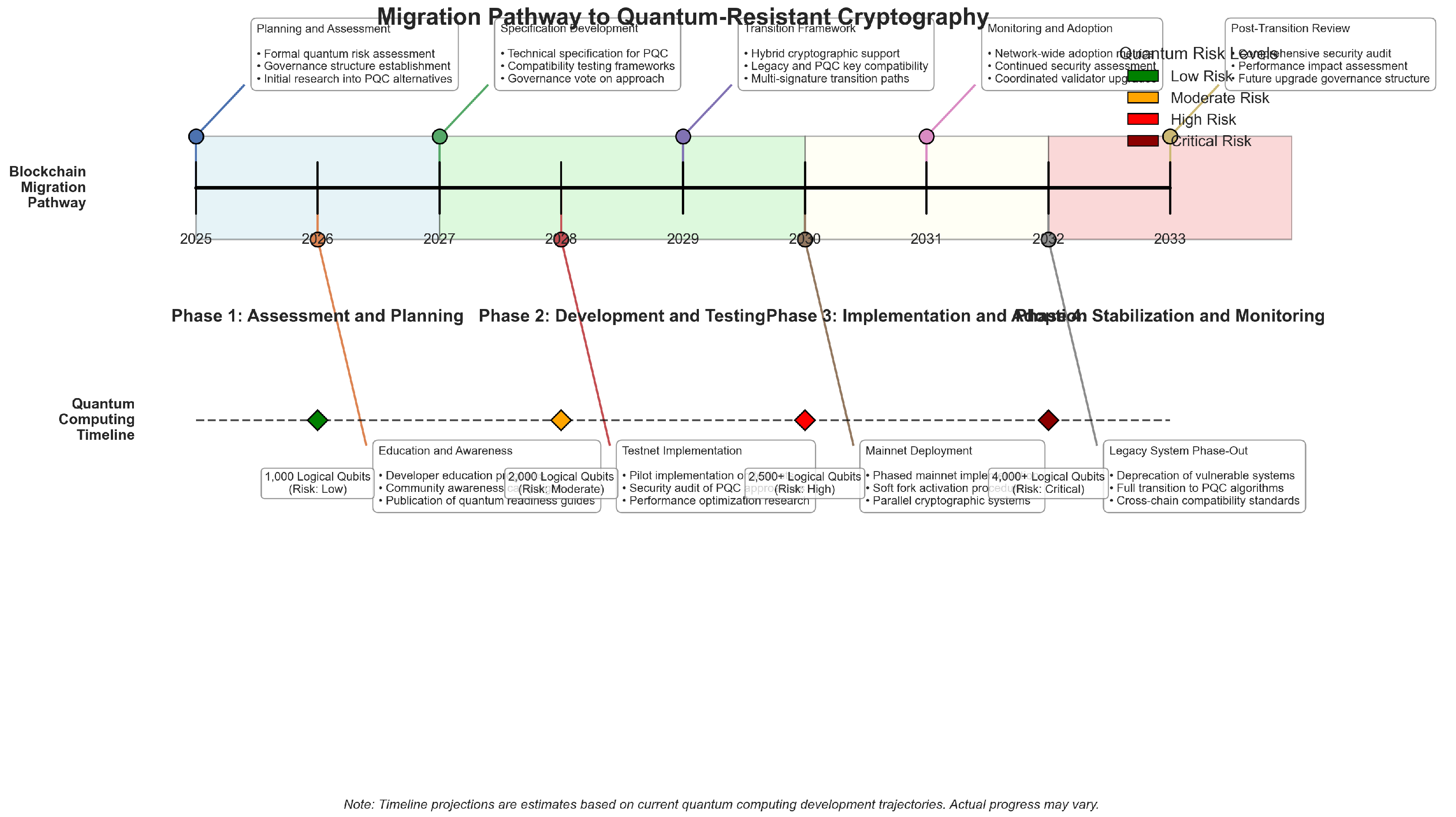
- Formal Transition Planning: The absence of formal transition plans for quantum resistance stands as the most critical issue among blockchain networks. The research demonstrates that 3 out of 17 blockchain projects have developed concrete transition frameworks that include specific technical requirements and implementation schedules. The transition process for Ethereum advanced from conceptual studies to actual implementation through the deployment of quantum-resistant signature schemes on testnets. The current preparedness deficit among cryptocurrency systems shows that they lack necessary governance mechanisms to execute sophisticated security updates despite rising quantum threat awareness.
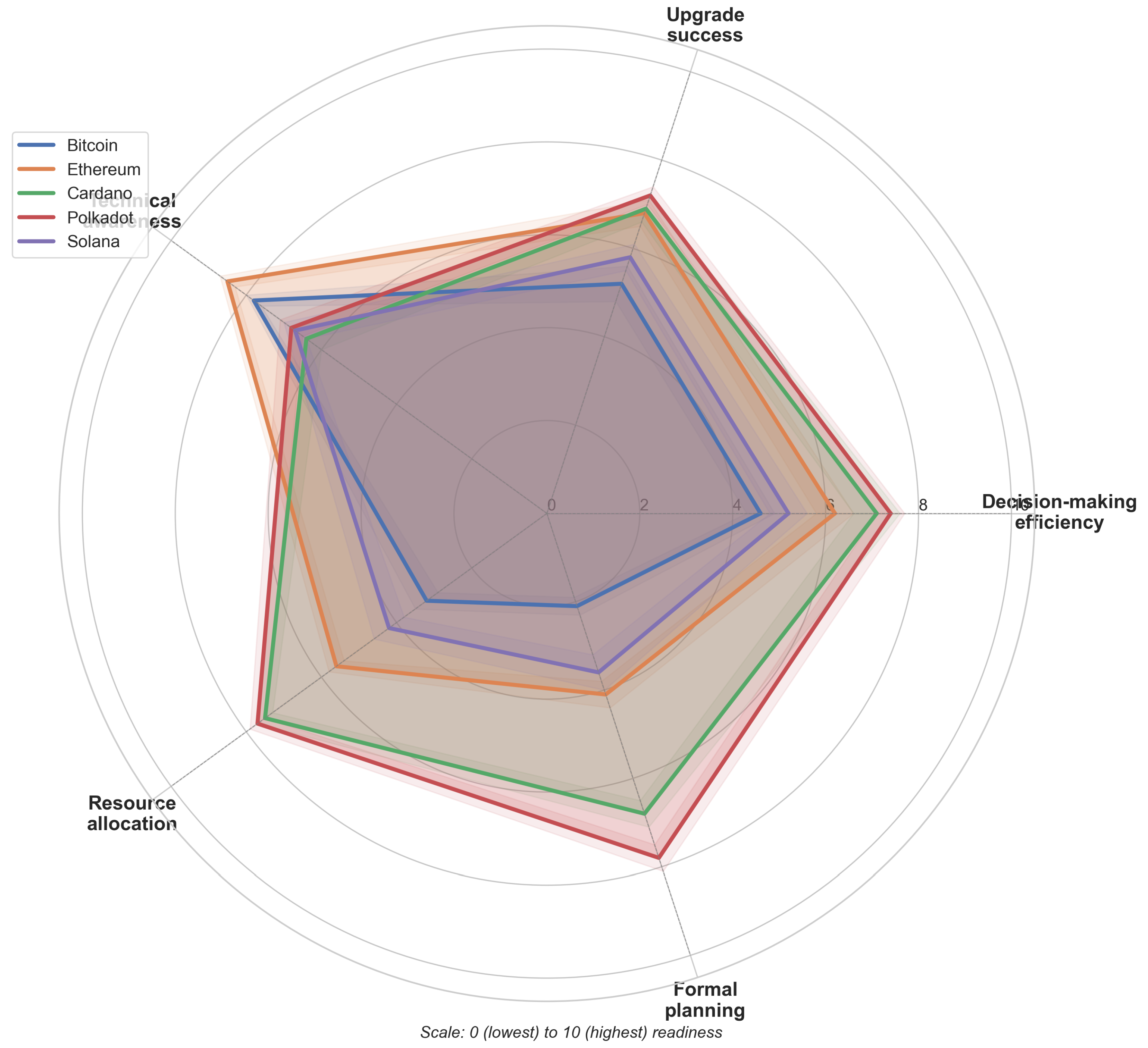
3.4. Economic Impact Assessment
- Asset Class Vulnerability Stratification: The vulnerability levels of cryptocurrency assets were categorized based on their exposure to quantum attacks. The risk level was higher for Bitcoin and other store-of-value currencies because their addresses remained active for extended periods while users reused them repeatedly. Utility tokens together with governance-focused cryptocurrencies demonstrated lower exposure because users kept them for brief durations and used their addresses infrequently. The analysis revealed distinct vulnerability levels across different cryptocurrencies which indicates protection plans should be adapted to each asset’s particular threat profile.
- Market Concentration Risk Factors: The blockchain data shows that the 50 largest holders among major cryptocurrency networks collectively manage assets worth $82 billion. Of particular concern, about 38% of these addresses—representing $31.2 billion—used signature schemes vulnerable to quantum attacks and had exposed their public keys. This concentration posed a heightened risk; should quantum attacks target these high-value addresses, the economic impact could be substantially magnified beyond what aggregate statistics might suggest.
- Governance Token Implications: Governance tokens presented a unique concern in the quantum security landscape. The tokens possess dual value because they provide financial worth and enable voting authority to influence protocol decisions. The research established that governance tokens comprise 42% of voting power in major DAOs could be compromised if quantum attacks successfully targeted key addresses. This vulnerability highlighted an often-overlooked dimension of the quantum threat—it endangered not just financial assets but also governance systems themselves, potentially undermining the democratic mechanisms that blockchain projects depend on for protocol evolution.
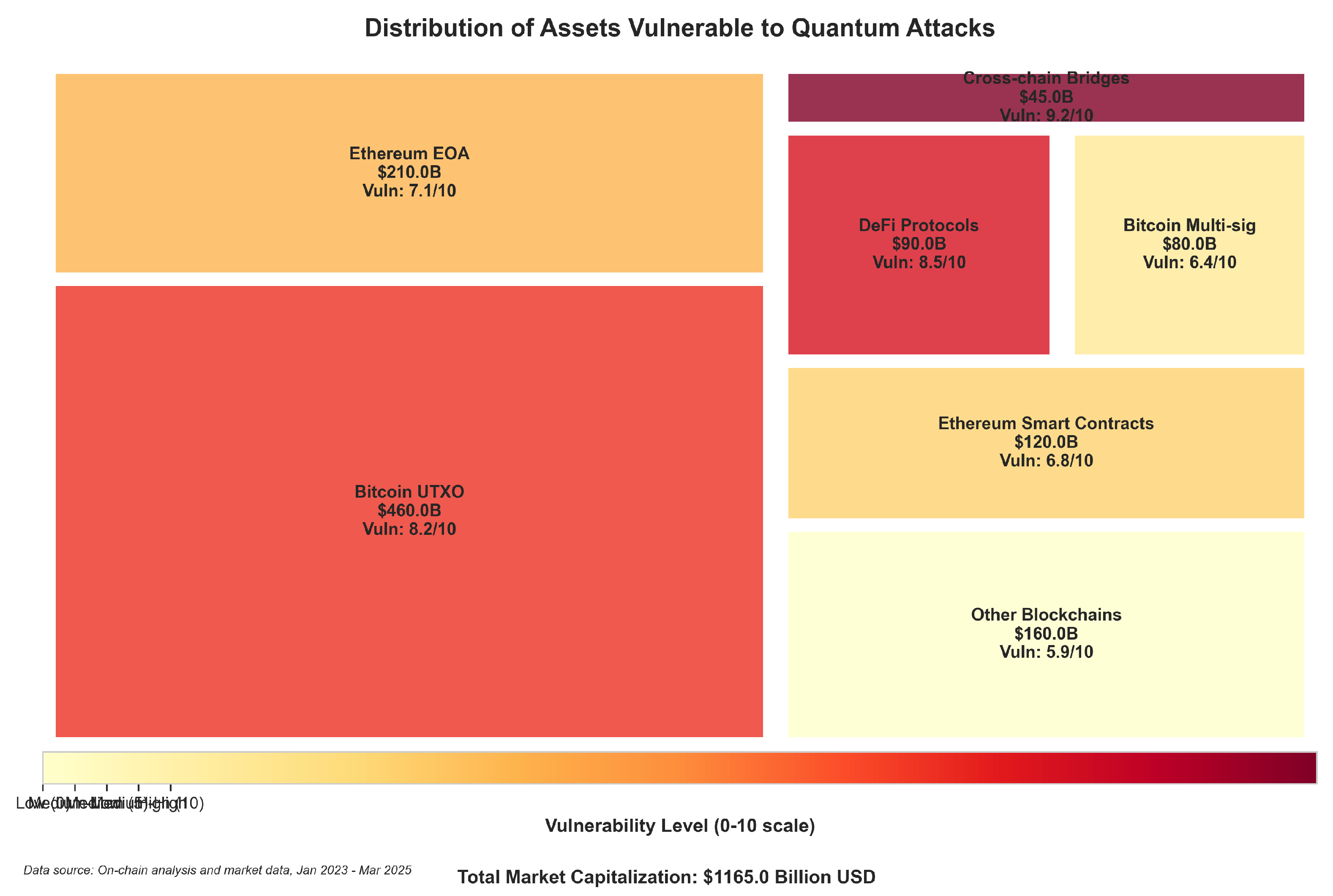
4. Discussion
4.1. Implications of Quantum Vulnerability Variation
4.2. Governance as a Critical Factor
4.3. Timeline Considerations
5. Practical Implications
5.1. For Cryptocurrency Developers
- Priority Areas: The framework should guide developers to conduct cryptographic upgrades starting with components having high QEI values.
- Governance Enhancement: The development of clear governance protocols with emergency plans for cryptographic attacks must become a priority.
- Technical Preparation: The implementation of post-quantum cryptography standards should start now for technical integration because final NIST standardization will reduce the time needed to implement standards.
5.2. For Exchange Operators and Custodians
- Risk Assessment: Perform QVI framework-based quantum vulnerability assessments on custodial systems according to the methods described in this study.
- Cold Storage Practices: The implementation of quantum-resistant signature schemes for cold storage systems should be paired with one-time address usage for high-value storage protection.
- User Education: The development of educational materials about quantum security threats and protection techniques should be made available to exchange users.
5.3. For Regulatory Bodies
- Risk Disclosure Requirements: The assessment of quantum vulnerability along with mitigation plans should be mandatory disclosure requirements for cryptocurrency projects.
- Coordination Support: Industry-wide collaboration must receive support from the regulatory framework to establish quantum resistance standards and schedule implementation dates.
5.4. For Individual Cryptocurrency Holders
- Address Usage: The practice of using the same addresses multiple times on ECDSA blockchains should be avoided to prevent exposing public keys.
- Portfolio Considerations: When making decisions about portfolio diversification consider quantum vulnerability as one of the factors to consider.
- Governance Participation: Participate in blockchain governance processes to support timely implementation of quantum resistance upgrades.
6. Conclusions
7. Data Availability Statement
Supplementary Materials
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| ABI | Address-Based Impact |
| BIP | Bitcoin Improvement Proposal |
| CRQC | Cryptographically Relevant Quantum Computer |
| DAO | Decentralized Autonomous Organization |
| DeFi | Decentralized Finance |
| ECDSA | Elliptic Curve Digital Signature Algorithm |
| EIP | Ethereum Improvement Proposal |
| FAIR | Findable, Accessible, Interoperable, and Reusable |
| GRS | Governance Readiness Score |
| NIST | National Institute of Standards and Technology |
| PQC | Post-Quantum Cryptography |
| QEI | Quantum Exposure Index |
| QVI | Quantum Vulnerability Index |
| UTXO | Unspent Transaction Output |
References
- Aggarwal, D.; Brennen, G.K.; Lee, T.; Santha, M.; Tomamichel, M. Quantum Attacks on Bitcoin and ECDSA. Ledger Journal 2023, 8, 15–32. [Google Scholar] [CrossRef]
- Alagic, G.; Alperin-Sheriff, J.; Apon, D.; Cooper, D.; Dang, Q.; Kelsey, J.; Liu, Y.K.; Miller, C.; Moody, D.; Peralta, R.; Perlner, R.; Robinson, A.; Smith-Tone, D. Status Report on the Third Round of the NIST Post-Quantum Cryptography Standardization Process; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2022. [Google Scholar] [CrossRef]
- Boixo, S.; Isakov, S.V.; Smelyanskiy, V.N.; Neven, H. Scaling Quantum Hardware Beyond Classical Limits. Nature Physics 2022, 18, 1166–1173. [Google Scholar] [CrossRef]
- Bernstein, D.J.; Lange, T. Post-Quantum Cryptography: Current Status and Quantum Mitigation Strategies. Cryptology ePrint Archive 2023, 2023/456, 1–35. [Google Scholar] [CrossRef]
- Bindel, N.; Buchmann, J.; Krämer, J.; Mantel, H.; Schickel, J.; Weber, A. Transitional Post-Quantum Cryptography Protocols. ACM Transactions on Privacy and Security 2017, 21, 1–31. [Google Scholar] [CrossRef]
- Blockchain.com Research Team. Bitcoin UTXO Statistics Report: Analysis of Address Reuse and Quantum Vulnerability. 2023. Available online: https://www.blockchain.com/explorer/utxo-report (accessed on 15 January 2025).
- Chainlink Labs. Quantum Resistance in Blockchain Oracles: Technical Implementation Report. 2023. Available online: https://chain.link/whitepaper (accessed on 20 January 2025).
- Fedorov, A.K.; Kiktenko, E.O.; Lvovsky, A.I. Quantum Computers Put Blockchain Security at Risk. Nature 2022, 563, 465–467. [Google Scholar] [CrossRef] [PubMed]
- Forbes Business Development Council. Post-Quantum Blockchain Security: Timeline and Implications. 2025. Available online: https://www.forbes.com/sites/forbesbusinessdevelopmentcouncil/2025/03/quantum-blockchain/ (accessed on 16 March 2025).
- Mosca, M. Cybersecurity in an Era with Quantum Computers: Will We Be Ready? IEEE Security & Privacy 2018, 16, 38–41. [Google Scholar] [CrossRef]
- Google Quantum AI Team. Quantum Supremacy and Beyond: Performance Benchmarks for Cryptographically Relevant Quantum Computers. 2023. Available online: https://ai.google/research/quantum-supremacy (accessed on 10 February 2025).
- Shor, P.W. Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer. SIAM Review 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Stewart, I.; Ilie, D.; Zamyatin, A.; Werner, S.; Torshizi, M.F.; Knottenbelt, W.J. Committing to Quantum Resistance: A Slow Defence for Bitcoin Against a Fast Quantum Computing Attack. Royal Society Open Science 2018, 5, 180410. [Google Scholar] [CrossRef] [PubMed]
- Blockchain Reporter. Cryptocurrency Community Concerns Amid Quantum Computing Advances. 2023. Available online: https://blockchainreporter.net/quantum-concerns-2023/ (accessed on 3 January 2025).
- Fernández-Caramés, T.M.; Fraga-Lamas, P. Blockchain Security in the Quantum Era: A Systematic Review. IEEE Access 2023, 11, 14876–14899. [Google Scholar] [CrossRef]
- Buterin, V.; Wood, G.; Zamfir, V. Post-Quantum Cryptography Implementation in Blockchain Networks. Proceedings of DevCon 2023; Ethereum Foundation, 2023; pp. 112–128. [Google Scholar]
- Ethereum Foundation. Ethereum Quantum Resistance Working Group Report. 2024. Available online: https://ethereum.org/en/roadmap/future-proofing/ (accessed on 20 March 2025).
- Hülsing, A.; Ning, P.; Perlner, R.; Schwabe, P.; Bernstein, D.J. SPHINCS+: Practical Stateless Hash-Based Signatures. Journal of Cryptology 2022, 35, 36. [Google Scholar] [CrossRef]
- Kannengießer, N.; Lins, S.; Sunyaev, A.; Treib, K. Approaching Post-Quantum Blockchains: Challenges and Opportunities for Quantum-Resistant Distributed Ledger Technologies. IEEE Access 2022, 10, 27518–27535. [Google Scholar] [CrossRef]
- Maxwell, G.; Wuille, P. Post-Quantum Bitcoin Security: Practical Approaches to Address Migration. Bitcoin Dev 2024, January, 1–10. [Google Scholar] [CrossRef]
- National Institute of Standards and Technology. Post-Quantum Cryptography Standardization. 2022. Available online: https://csrc.nist.gov/projects/post-quantum-cryptography/post-quantum-cryptography-standardization (accessed on 15 January 2025).
- Faqiry, M.N.; Zarabie, A.K.; Nassif, S.R.; Das, S. Risk Metrics for Cryptocurrency Ecological Vulnerabilities. Nature Communications 2023, 14, 4536. [Google Scholar] [CrossRef]
- García-Díaz, Víctor; Espada, Jordán Pascual; Pelayo, B. Cristina; G-Bustelo, Carlos P. Sentiment Analysis in Cryptocurrency Communities: Methodological Approaches and Limitations. Information Processing & Management 2023, 59, 102776. [Google Scholar] [CrossRef]
- Qiskit Development Team. Qiskit: An Open-Source Framework for Quantum Computing. 2023. Available online: https://qiskit.org/ (accessed on 10 February 2025).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





