Submitted:
18 April 2025
Posted:
21 April 2025
You are already at the latest version
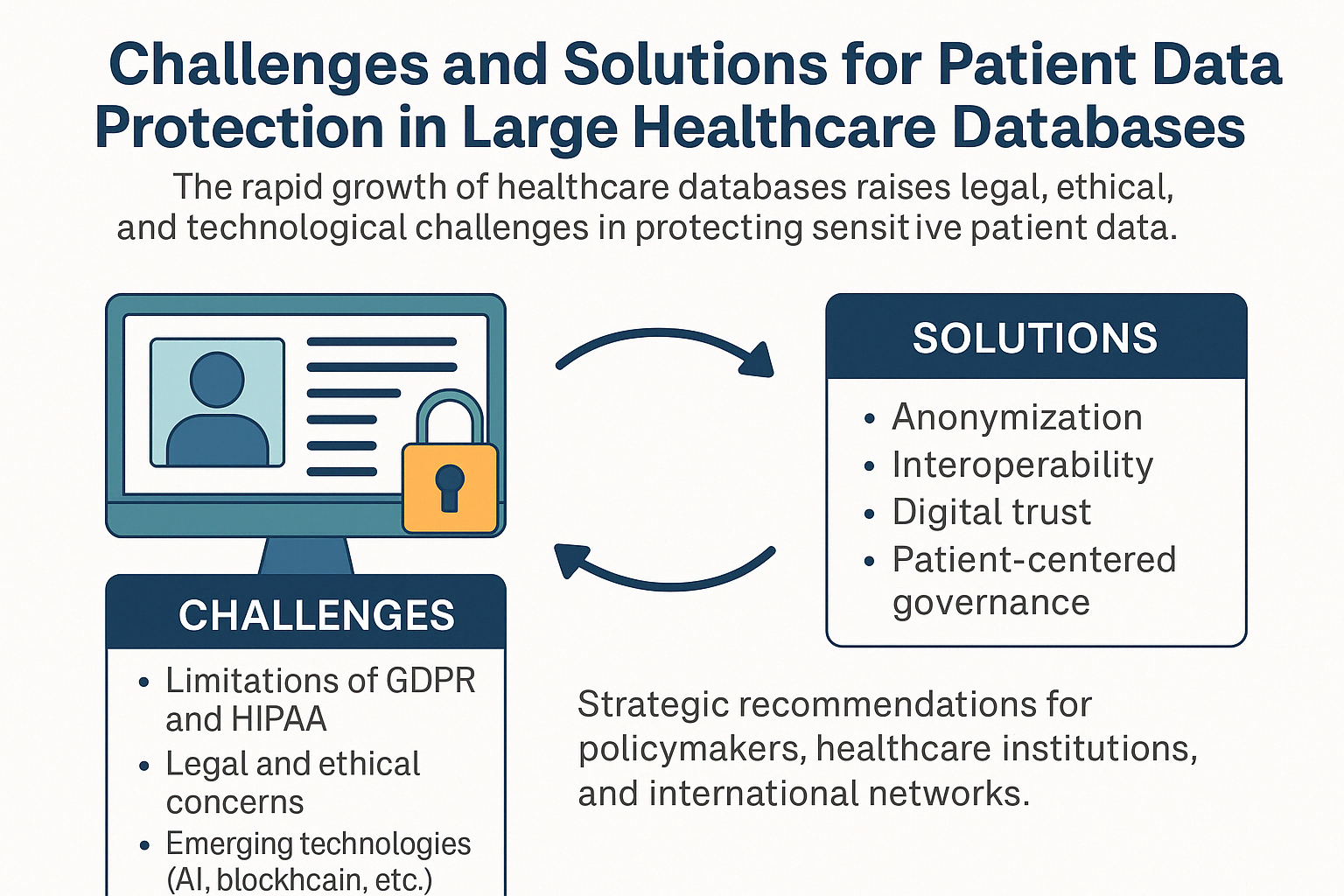
Abstract
Keywords:
1. Introduction
1.1. Bioethics and Digital Patient Rights
1.2. Information Security Theory
1.3. Legal Frameworks (GDPR, HIPAA)
1.4. Digital Trust and Patient Autonomy
- What are the main challenges in ensuring data privacy in large healthcare databases?
- How effective are current legal and technical frameworks (e.g., GDPR, HIPAA) in addressing these challenges?
- How do different countries approach data protection in the healthcare sector?
- Which ethical and technological solutions can enhance patient trust and data security?
2. Methodology
2.1. Data Collection Approach:
- Selection Criteria: Case studies were selected based on their relevance to the use of health data in medical research, AI applications, or public health emergencies.
- Focus Areas: Specific focus was placed on instances where data protection laws and patient consent procedures were challenged, especially during health crises or innovative research efforts.
- Institutional Policies: This included reviewing internal protocols for patient consent, data access, data sharing, and oversight mechanisms within the organizations involved in patient advocacy and health data protection.
- International Guidelines: The study compared institutional policies to international frameworks and guidelines, such as GDPR, and their practical implementation in the context of patient privacy and public health research. Legal and ethical analysis (GDPR, HIPAA, national laws).
- Theoretical frameworks and ethical principles guiding data governance in healthcare.
- Global and regional privacy laws, including GDPR, HIPAA and their impact on data sharing in medical research and public health surveillance.
- Published case studies on the use of health data in AI applications and personalized medicine, with an emphasis on privacy concerns and ethical implications.
2.2. Data Analysis:
- Identify recurring ethical dilemmas related to data use in healthcare settings.
- Understand the effectiveness of current data protection measures and patient consent protocols.
- Assess the impact of data sharing and privacy regulations on medical innovation, AI development, and public health outcomes.
2.3. Ethical Considerations:
- Privacy Protection: Ensuring that all data collected and analyzed were anonymized, preventing the identification of individuals.
- Transparency: Clear communication about how the anonymized data would be used in the study, ensuring transparency in data governance.
- Patient Autonomy: Although informed consent was not necessary due to anonymization, the autonomy of patients was respected through transparent processes and ethical handling of data.
2.4. Conclusion and Recommendations:
- Strike a balance between data protection and data use, especially in the context of public health emergencies or AI research.
- Propose frameworks for enhancing patient trust and transparency in data governance.
- Suggest ways to refine patient consent processes and strengthen data security measures while fostering innovation in healthcare.
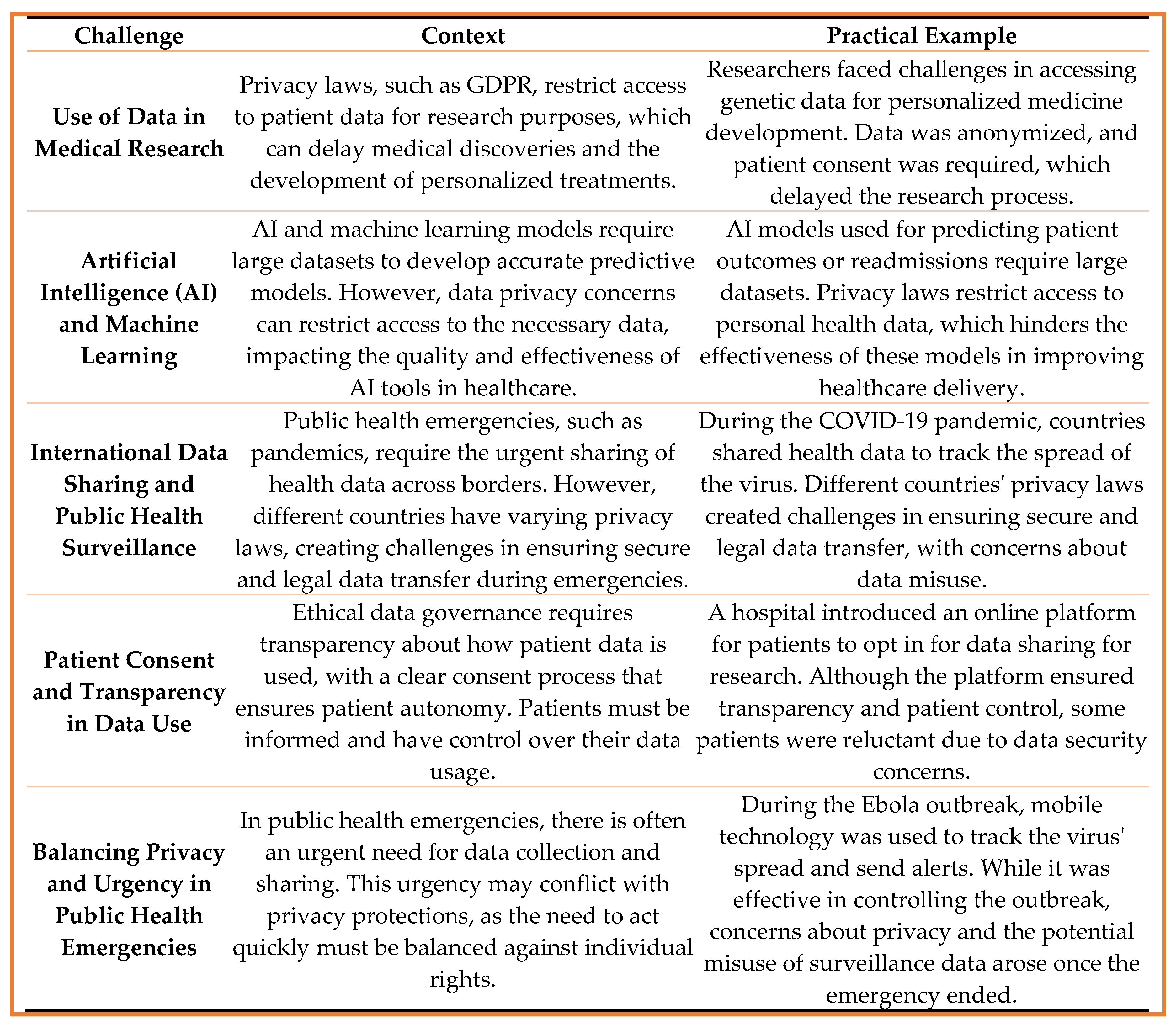
3. Results
3.1. Technical Challenges:
- Cyberattacks, Hacking, Ransomware
- The increasing reliance on digital health systems exposes patient data to a range of cyber threats, including cyberattacks, hacking, and ransomware. Healthcare institutions are prime targets for cybercriminals due to the valuable nature of the sensitive data they handle. These threats pose significant risks to data confidentiality and integrity, leading to potential breaches that can undermine public trust and safety.
- b.
- Interoperability Issues
- A major technical challenge is the lack of interoperability between different health IT systems. Healthcare organizations often use varied systems that may not communicate with each other effectively, making it difficult to share patient data across institutions or borders. This can hinder patient care, delay treatments, and prevent the seamless integration of new digital health tools, such as AI and predictive models.
- c.
- Weak Encryption or Outdated Software
- Insufficient encryption protocols and outdated software can compromise the security of health data. These vulnerabilities make systems more susceptible to breaches, data leaks, and unauthorized access, undermining patient privacy. Continuous updates and robust encryption standards are crucial to protecting patient information from emerging threats.
3.2. Legal and Regulatory Challenges:
- Different Interpretations of GDPR
- While the General Data Protection Regulation (GDPR) provides a comprehensive framework for data protection within the European Union, there are ongoing challenges regarding its interpretation. Different organizations and countries may interpret GDPR provisions in varying ways, which can create confusion and inconsistency in the application of data protection laws, especially when dealing with international data transfers.
- b.
- Cross-Border Data Sharing Limitations
- The movement of health data across borders presents significant challenges due to varying legal frameworks and privacy regulations. For instance, the GDPR imposes stringent requirements on data transfers outside the EU, creating obstacles for global health research collaborations or multinational health organizations. This limitation can delay medical breakthroughs and limit access to vital health data.
- c.
- Lack of Harmonization Between National Laws
- The absence of harmonized data protection laws across different jurisdictions creates legal complexities when health data is shared internationally. Inconsistent national regulations can lead to uncertainty, inefficiencies, and legal risks, particularly for multinational organizations or cross-border healthcare services. This challenge highlights the need for international standards to ensure a unified approach to data governance in healthcare.
3.3. Organizational Challenges:
- Lack of Staff Training in Data Protection
- Many healthcare organizations face challenges in ensuring that their staff is adequately trained in data protection laws and best practices. Inadequate training can lead to accidental breaches, non-compliance with regulations, or mishandling of sensitive patient information. Organizations must prioritize training and capacity-building to safeguard patient data and maintain legal compliance.
- Insufficient Internal Policies or Enforcement
- Even when data protection policies exist within healthcare organizations, the enforcement and application of these policies can be weak. The lack of clear internal protocols, or insufficient monitoring and enforcement mechanisms, leaves room for errors in data management. Without strong governance, organizations may struggle to ensure that privacy protections are consistently maintained.
3.4. Ethical Challenges:
- Informed Consent in Digital Health Systems.
- Obtaining informed consent in digital health systems is a major ethical challenge. Patients may not fully understand how their data will be used, shared, or stored in digital platforms. Clear, transparent, and accessible consent processes are necessary to ensure that patients are informed about the implications of their data being used in research, AI development, or other applications.
- Patient Awareness and Digital Literacy.
- A significant barrier to effective data governance is the varying levels of digital literacy among patients. Many patients may not have the technical knowledge to understand the risks and benefits of digital health systems or the implications of sharing their data. Improving digital literacy and patient education is crucial to ensuring that patients can make informed decisions about their health data.
- Concerns About Surveillance and Secondary Data Use.
- Ethical concerns surrounding the secondary use of health data and surveillance practices can undermine patient trust in healthcare systems. Patients may worry that their health data is being used for purposes they did not consent to, such as marketing or surveillance. Addressing these concerns requires strong safeguards, transparency, and ethical guidelines to protect patient privacy and autonomy.
Ethical Reflections on the Balance Between Data Protection and Data Use
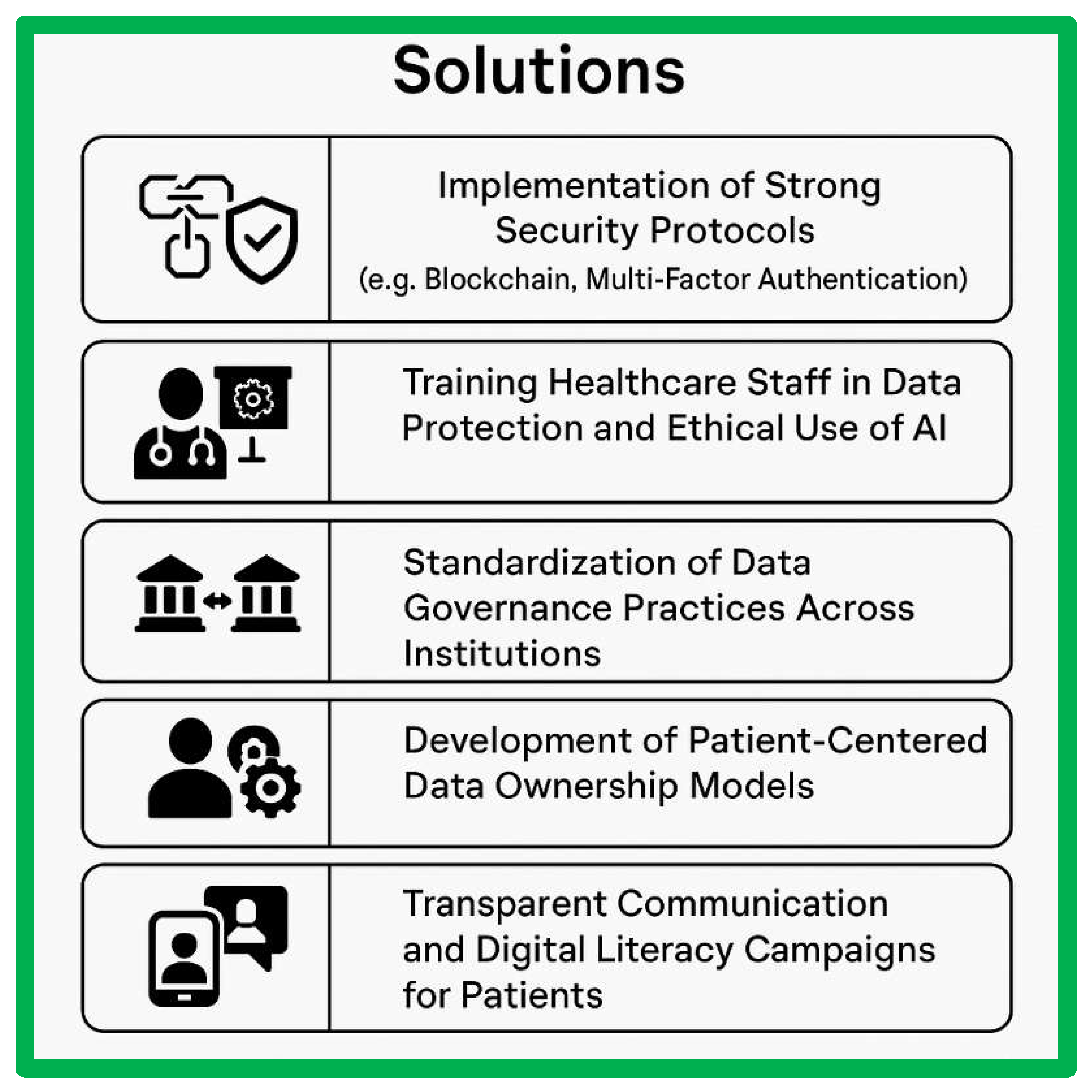
- Implementation of Strong Security Protocols (e.g., Blockchain, Multi-Factor Authentication)
- To address technical challenges, it is essential to implement strong security protocols to safeguard patient data from cyberattacks and unauthorized access. Technologies such as blockchain can offer decentralized and immutable data storage, ensuring the integrity of health data. Additionally, multi-factor authentication (MFA) can be employed to enhance access controls and prevent unauthorized access to sensitive healthcare systems.
- b.
- Training Healthcare Staff in Data Protection and Ethical Use of AI
- One of the key organizational solutions is to train healthcare staff in both data protection principles and the ethical use of artificial intelligence (AI) in healthcare. Comprehensive training programs should be implemented to ensure that staff understand the legal, ethical, and technical requirements for handling patient data. This can help minimize risks related to data breaches and ensure that AI is used responsibly to support patient care and innovation.
- c.
- Standardization of Data Governance Practices Across Institutions
- To overcome legal and regulatory challenges, there is a need for the standardization of data governance practices across institutions. Harmonizing data protection policies and practices within and between healthcare organizations can improve data interoperability, facilitate cross-border data sharing, and ensure consistent compliance with data protection laws, such as GDPR. This standardization can also enhance efficiency and reduce the risk of non-compliance.
- d.
- Development of Patient-Centered Data Ownership Models
- Ethical solutions to ensure patient autonomy include the development of patient-centered data ownership models. These models empower patients to have greater control over their health data, including the ability to decide how and with whom their data is shared. By involving patients in the decision-making process and offering clearer consent protocols, healthcare systems can build trust and respect patient rights while still enabling valuable data use for research and innovation.
- e.
- Transparent Communication and Digital Literacy Campaigns for Patients
- To address concerns about informed consent and improve digital literacy, healthcare institutions should initiate transparent communication and digital literacy campaigns for patients. These campaigns should educate patients about the digital health tools being used, the ways in which their data will be protected, and the benefits of sharing their data for research and public health purposes. Improving patient awareness will help them make informed decisions about their data and foster a sense of trust in digital healthcare systems.
4. Discussion
5. Conclusions and Recommendations
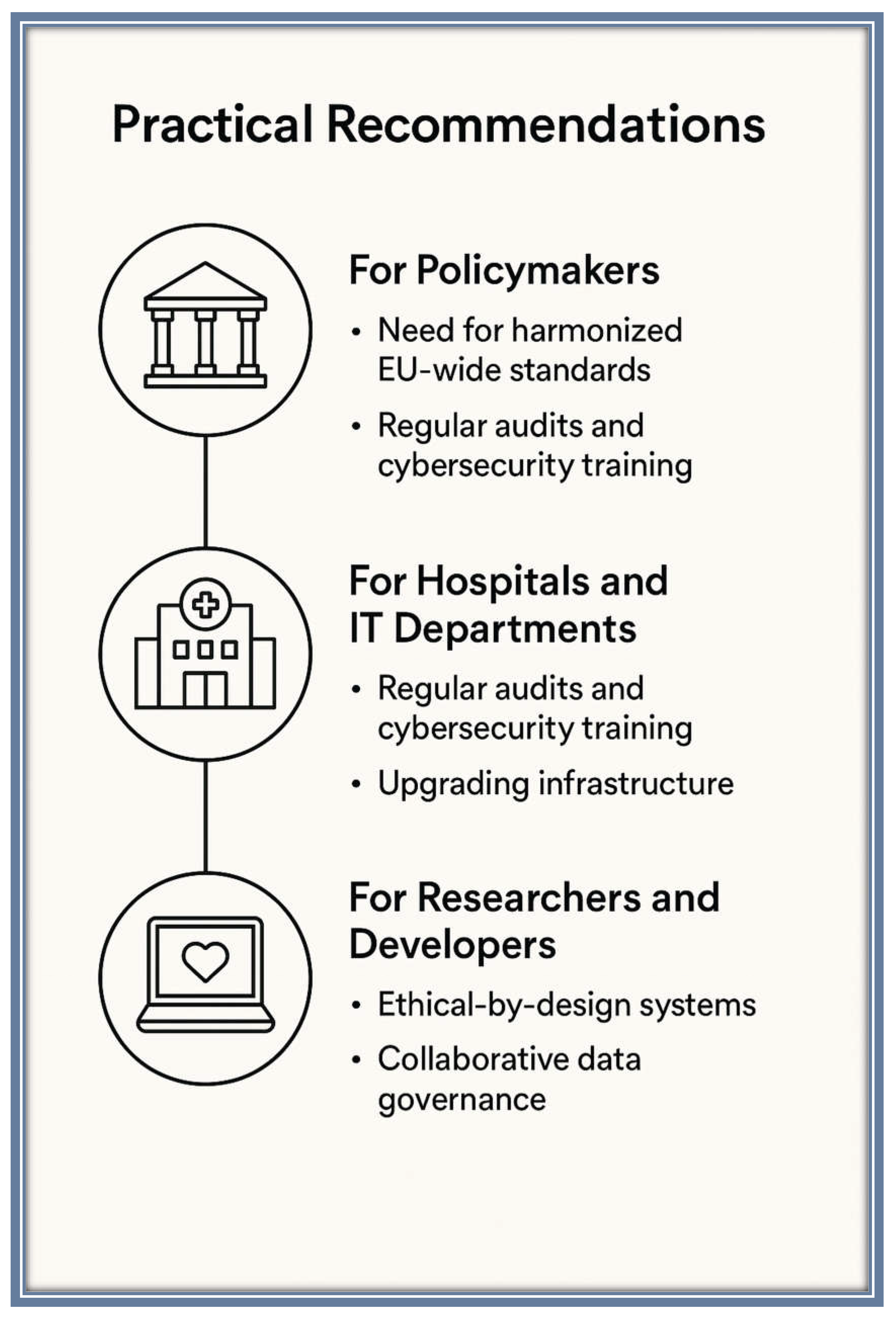
5.1. Practical Recommendations:
- Need for Harmonized EU-Wide Standards: Policymakers should work towards the harmonization of data protection standards across the EU, addressing the challenges posed by varying interpretations of GDPR and creating uniform regulations that facilitate cross-border data sharing while ensuring robust privacy protection. International cooperation is also necessary to standardize privacy laws and create global frameworks for health data use.
- Regular Audits and Cybersecurity Training: Healthcare institutions must implement regular audits to assess the security of their data systems and ensure compliance with privacy regulations. IT departments should prioritize cybersecurity training for all staff members to minimize the risk of data breaches and improve internal data management practices.
- Upgrading Infrastructure: Hospitals and IT departments should focus on upgrading outdated systems and ensuring the use of state-of-the-art encryption technologies and secure access controls to safeguard patient data.
- Ethical-by-Design Systems: Researchers and developers should embrace ethical-by-design principles when creating new digital health tools and AI applications. This includes embedding privacy protection mechanisms and transparent consent processes directly into the design of systems to ensure that patient data is handled ethically throughout the research and development phases.
- Collaborative Data Governance: Developers should also collaborate with healthcare institutions to create data governance models that prioritize patient autonomy, transparency, and control over health data, ensuring that individuals have a meaningful say in how their data is used.
5.2. Suggestions for Further Research:
- Emerging Technologies: Future research should focus on the ethical implications and potential of emerging technologies in digital health, such as blockchain for secure data storage, AI for predictive healthcare models, and wearable devices that collect continuous health data. Research should explore how these technologies can be integrated into existing systems without compromising patient privacy.
- Patient Engagement Strategies: There is a need for further studies on patient engagement strategies in digital health systems, particularly how patients can be empowered to make informed decisions about their data and the ways in which digital literacy can be improved across diverse populations. Research into participatory models for patient consent and data ownership would also be valuable in aligning technology with patient rights and public trust.
References
- Shabani M, Marelli L. Re-identifiability of genomic data and the GDPR. EMBO Rep. 2019;20(6):e48316.
- Organisation for Economic Co-operation and Development (OECD). Health Data Governance: Privacy, Monitoring and Research. Paris: OECD Publishing; 2021.
- Wang Y, Kung L, Byrd TA. Big data analytics: Understanding its capabilities and potential benefits for healthcare organizations. Technol Forecast Soc Change. 2018;126:3–13.
- Rieke N, Hancox J, Li W, Milletari F, Roth HR, Albarqouni S, et al. The future of digital health with federated learning. NPJ Digit Med. 2020;3:119.
- Glicksberg BS, Johnson KW, Shameer K, Dudley JT. Data science approaches to precision medicine. Curr Cardiol Rep. 2018;20(12):139.
- Engelhardt, MA. Hitching healthcare to the chain: An introduction to blockchain technology in the healthcare sector. Technol Innov Manag Rev. 2017;7(10):22–34.
- Karacic Zanetti J, Nunes R. To Wallet or Not to Wallet: The Debate over Digital Health Information Storage. Computers. 2023;12(6):114. [CrossRef]
- Appari A, Johnson ME. Information security and privacy in healthcare: current state of research. Int J Internet Enterp Manag. 2010;6(4):279–314.
- Voigt P, Von dem Bussche A. The EU General Data Protection Regulation (GDPR): A Practical Guide. 1st ed. Cham: Springer International Publishing; 2017.
- U.S. Department of Health and Human Services (HHS). Summary of the HIPAA Privacy Rule [Internet]. Washington, DC: HHS; 2003 [cited 2025 Apr 10]. Available from: https://www.hhs.gov/hipaa/for-professionals/privacy/laws-regulations/index.html.
- Nebeker C, Torous J, Bartlett Ellis RJ. Building the case for actionable ethics in digital health research supported by artificial intelligence. BMC Med. 2019;17(1):137.
- Kluge EHW, Ruotsalainen P. A comparative study of health information privacy in Europe: An illustration of the influence of European Union and national policies. Int J Med Inform. 2012;81(12):834–41.
- Mittelstadt BD, Floridi L. The ethics of big data: Current and foreseeable issues in biomedical contexts. Sci Eng Ethics. 2016;22(2):303–41.
- Morley J, Floridi L. The limits of empowerment: How to reframe the role of mHealth tools in the healthcare ecosystem. Sci Eng Ethics. 2020;26(3):1159–83.
- Price WN, Cohen IG. Privacy in the age of medical big data. Nat Med. 2019;25(1):37–43.
 |
|---|
 |
|---|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




