Submitted:
12 April 2025
Posted:
14 April 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
- The authors used only one database (Web of Science, WoS) for their research, significantly limiting the number of sources;
- The inclusion and exclusion criteria were not described in their paper [2].
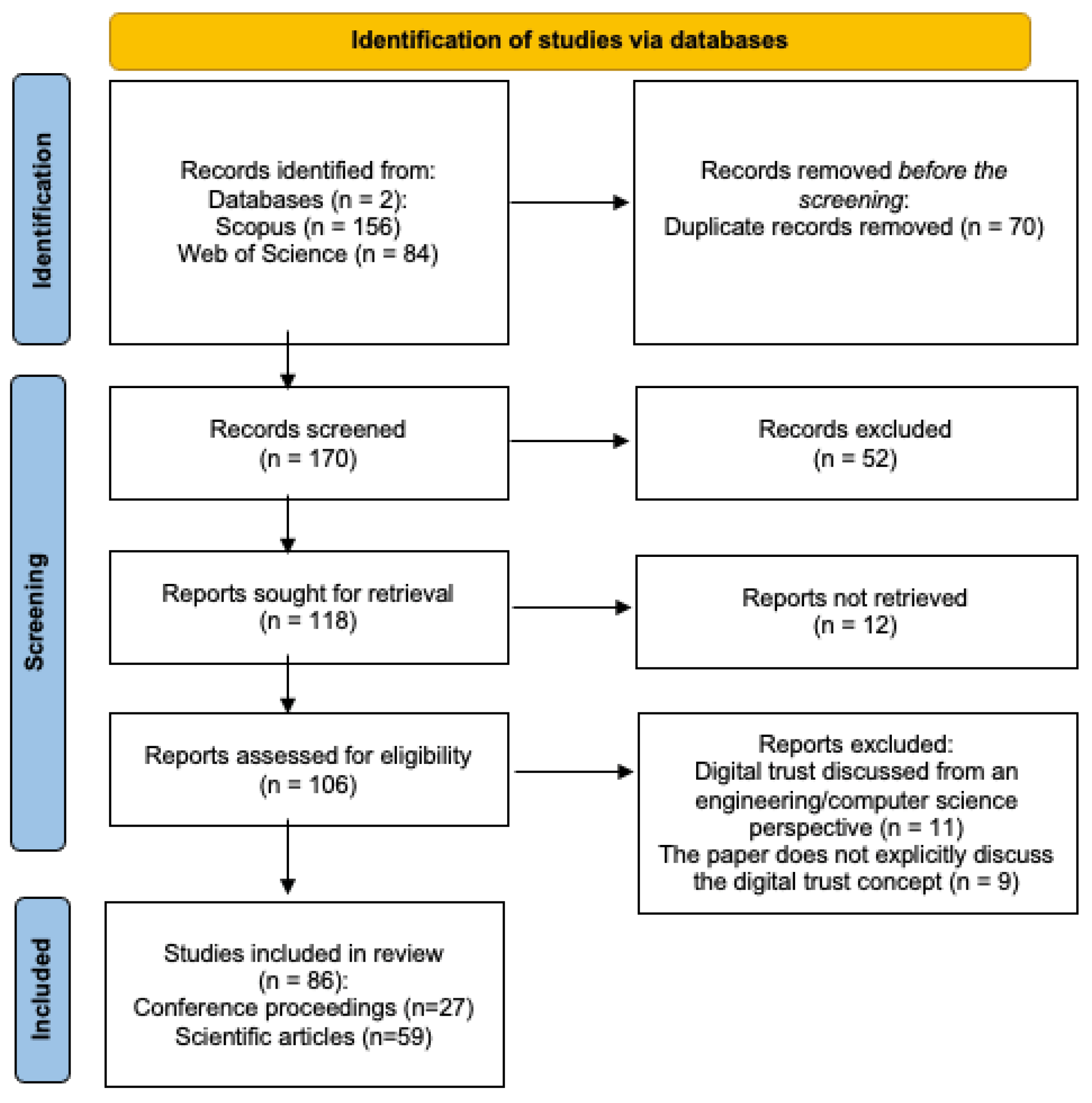
2. Materials and Methods
3. Systematic Literature Review Results
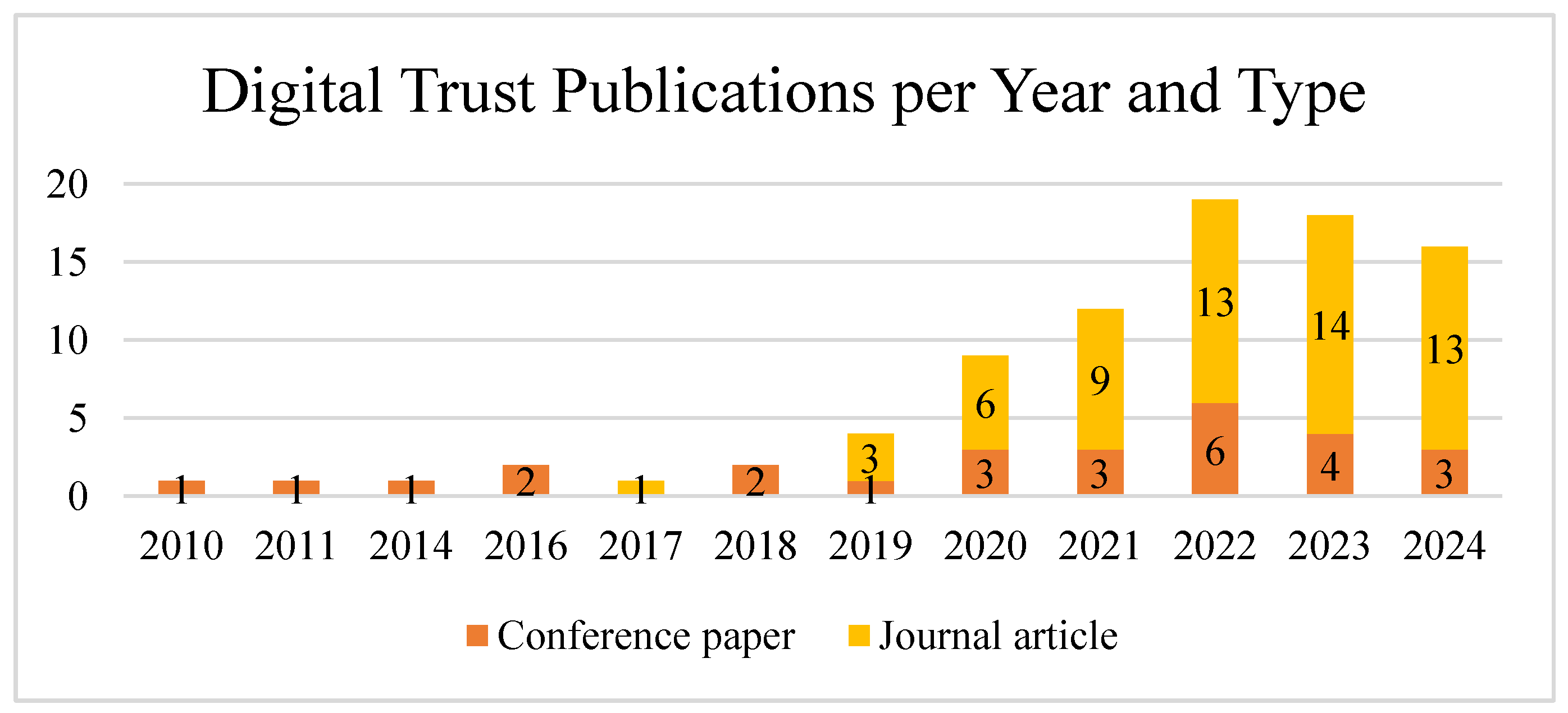
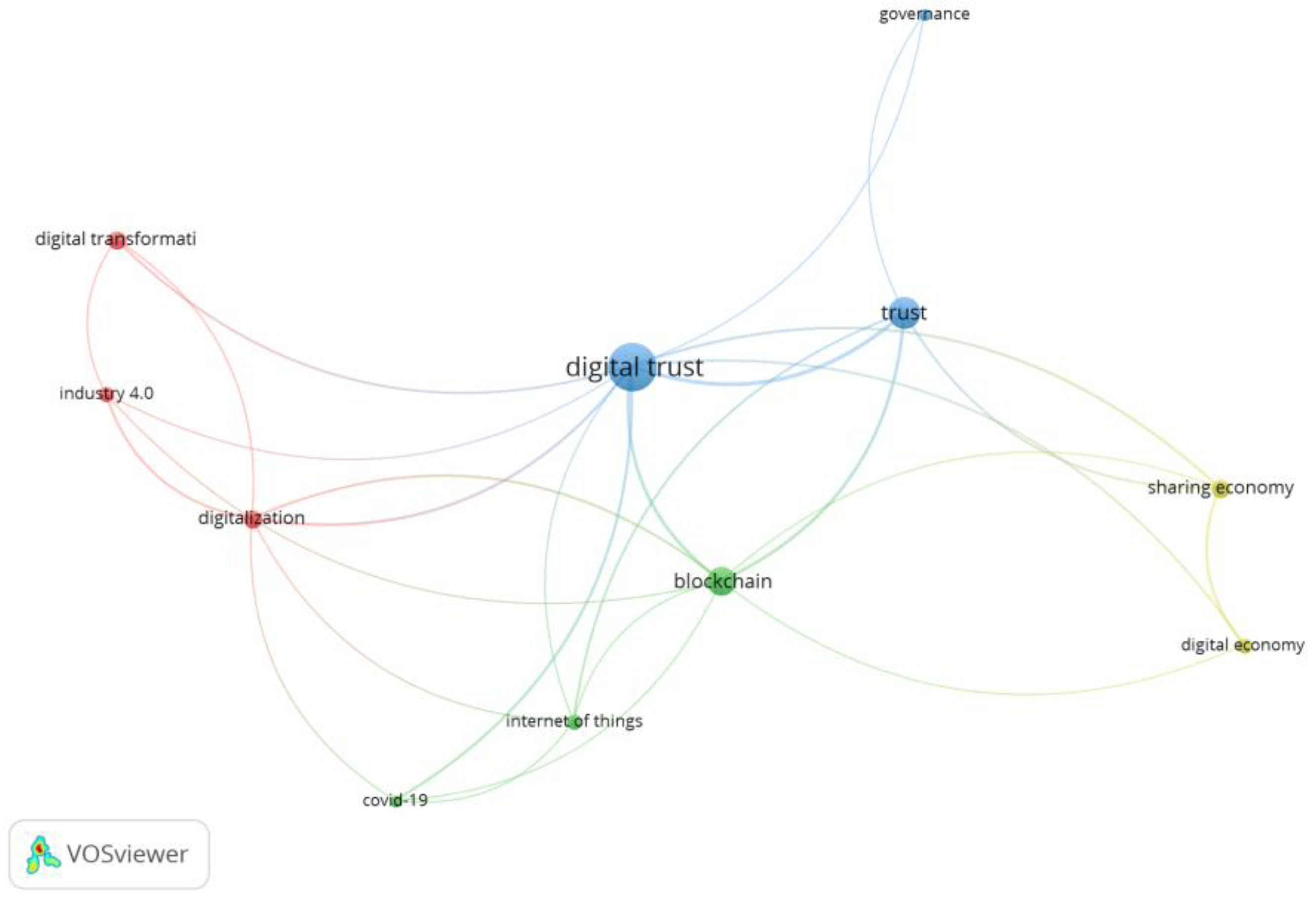
3.1. Bibliographical Analysis
- Blue: Devoted to governance
- Red: Focused on digital transformation and digitalisation, strongly linking them with industrial or organisational changes.
- Green: Related to the technological application of DT
- Yellow: concerned with socio-economic aspects
3.2. Existing Definitions of Digital Trust
- Focus on the collective confidence in people, processes and technology, i.e. “holistic trust”.
- Emphasis on having a secure and reliable digital environment.
- Includes trust from various stakeholders such as users, customers, individuals, partners, and society.
- Assurance that personal and sensitive data is protected from unauthorised access and breaches.
- Expectation in the organisations to handle data responsibly and ethically, respecting user privacy.
- Meeting stakeholders’ expectations regarding data handling practices.
- Confidence in technology's ability to execute tasks and transactions accurately and securely.
- Trust in the consistent performance and punctuality of digital systems, platforms, and services.
- Use specific technologies (e.g., blockchain, AI) to establish or enhance trust.
- Trust involves rational evaluations (competence, integrity) and emotional responses (feelings, beliefs).
- Trust is built upon past experiences and evidence of behaviour, influencing future expectations.
- Trust affects the willingness to take risks and make decisions, even with limited verification.
- Trust enables interactions in environments involving human actors and technological elements.
- Trust is crucial for customer acquisition, retention, and the formation of reliable business networks and partnerships.
- Technology can be an enabler that can enhance or hinder trust in digital relationships.
- Trust is based on digital partners’ integrity, benevolence, and predictability.
- Trust encompasses adherence to both written and unspoken commitments to avert harm.
- It emphasises privacy, security, protection, and data management as part of an organisation's culture.
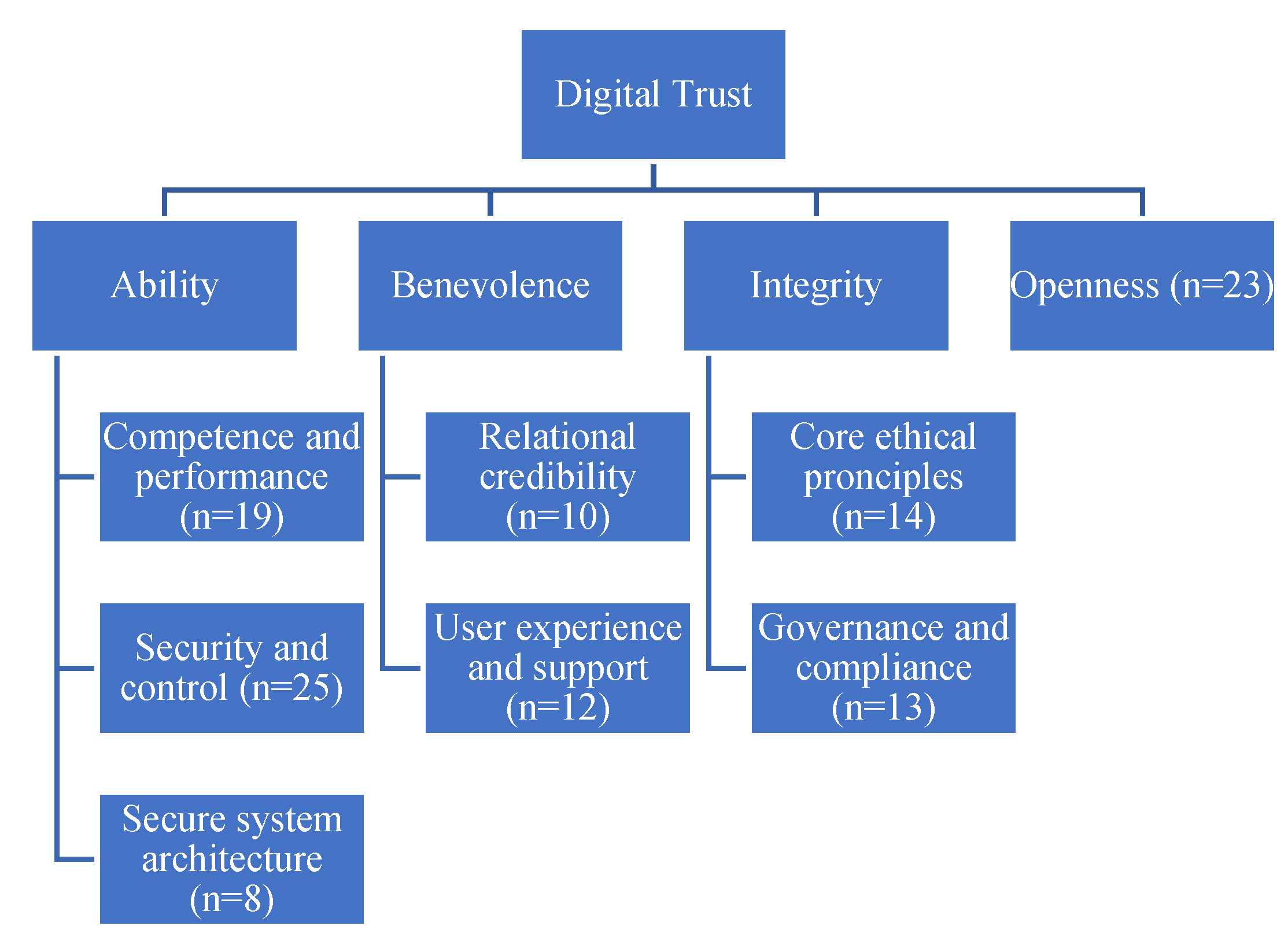
3.3. Key Characteristics of Digital Trust
- System’s, services, and service provider’s competence and performance;
- Security and control factors, i.e. internal technical capabilities required to operate reliably;
- Secure system architecture factors represent internal design choices to enhance systems or services’ capabilities and perform reliably.
- Relational credibility includes elements like goodwill, the reliability of the supplier or service provider, and their reputation.
- User experience and the level of support received – how satisfied the trustor is with the service, their prior experiences, and the convenience of using the product or service.
- The organisation's core ethical principles include integrity, which guides its adherence to data ethics.
- Governance and compliance encompass accountability for the organisation’s actions, adherence to regulations, and the implementation of standards, including industry best practices and other frameworks.
- Transparency signifies open and clear information about how the service functions.
- Auditability pertains to an external party's capacity to examine the service or its provider and provide independent verification or certification. In this context, the experiences of other users may also be emphasised, whether through feedback, reviews, or word of mouth.
- Traceability refers to the ability to track processes and data flows within the service.
4. Digital Trust Definition Validation
4.1. Definition Validation Methodology
- 1 means that the characteristic is not presented in the definition at all.
- 2 means that the characteristic is more absent than presented.
- 3 means that the characteristic is partially presented.
- 4 means that the characteristic is more presented than absent.
- 5 means that the characteristic is fully presented in the definition.
4.2. Definition Validation Study Results
5. Discussion
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| DT | Digital trust |
| WoS | Web of Science |
Appendix A
Appendix A.1
- Suppose the definition was found in a source included in 86 analysed papers and copied directly from this source. In that case, the reference is included in the column source, and the field in the column “quoted in” is marked N/A (even if other authors from the scope of SLR also referenced this paper).
- If the authors of the paper quoted another source when providing the definition, the source of the quotation is referenced in the “source” column, while the paper itself is referenced in the “quoted in” column.
| Nr | Definition | Source | Quoted in |
|---|---|---|---|
| Thematical Group 1 | |||
| 1 | “In the digital context, trust refers to users' confidence and reliability in the systems, services, and organizations they interact with. Users must trust that their personal information will be handled responsibly, that their privacy will be respected, and that the systems they rely on are secure from malicious actors.” | [27], (p.360) | N/A14/04/2025 13:15:00 |
| 2 | “The perceived confidence individuals have in the ability of people, technology, and processes to build a secure digital environment.” | [73] | [42], (p.4329) |
| 3 | “A concept that defines confidence in the reliability of all components of digital interaction: users, processes, devices, technologies and vendors” | [74] | [12], (p.433) |
| 4 | “Digital Trust can be defined as the confidence that users have in processes, technology and people to create a secure digital world.” | [51], (p.1) | N/A |
| 5 | “Digital trust underpins every digital interaction by measuring and quantifying the expectation that an entity is who or what it claims to be and that it will behave in an expected manner.” | [75] | [76], (p.179) |
| 6 | “The general belief that technology, people, and processes act or are aligned in ways that will fulfill people's digital expectations, such as sense of confidence, security, or control to support the creation of a secure digital environment.” | [75] | [77], (p.30) |
| 7 | “Digital trust implies a sufficient level of confidence in people, processes, and technology to build a secure digital world” | [47], (p.245) | N/A |
| 8 | “Confidence in the creation of a secure digital world” | [78] | [38], (p.539) |
| 9 | “DTrust is associated with trust in digital institutions, digital technologies and platforms, which, in other words, means the user's trust in the capability of digital institutions, companies, technologies and processes to create a safe digital world.” | [57], (p.490) | N/A |
| 10 | “Digital trust can be referred to as the confidence of stakeholders on the competence of actors, technologies, and processes for establishing reliable and secure business networks.” | [23], (p.3) | N/A |
| 11 | “Digital trust has been defined in practitioner circles as the confidence users have in the ability of people, technology, and processes to create a secure digital world. Yet the basis of trust placed in people, technology (e.g., devices, platforms), and processes (e.g., systems, institutions) will likely differ across digital contexts.” | [79] | [80], (p.668) |
| 12 | “DT represents stakeholders' confidence in the competence of actors, technologies, platforms and processes of establishing a reliable network.” | [81] | [48], (p.74) |
| Thematical Group 2 | |||
| 13 | “Digital trust represents the acquisition and retention of customers and shareholder value via providing confidence in the digital services with digital channels” | [35] | [36], (p.6) |
| 14 | “Reliability of information provided by trade partners, or the safety and security of the data managed by a central authority” | [82] | [40], (p.19) |
| 15 | “The confidence that a digital society attains in terms of data protection and privacy protection” | [83] | [33], (p.168) |
| 16 | “Confidence in the counterparty that stores and use consumers’ digital information in such a way that this meets the expectations of consumers” | [84] | [12], (p.433) |
| 17 | “Digital trust is assumed to be the measure of confidence which workers, consumers/buyers, partners and other stakeholders have in the ability of an organisation to protect data and the privacy of individuals” | [2], (p.65) | N/A |
| 18 | “The confidence placed in an organisation to collect, store, and use the digital information” | [85] | [2], (p.65) |
| 19 | “Digital trust stems from a combination of different factors (...): security, identifiability, and traceability. Quite often, however, the presence of these features can be too difficult for an individual to evaluate – and especially so in a digital environment.” | [86] | [2], (p.65) |
| 20 | “Digital trust can be seen as insurance placed by data owners in an actor empowered to manage their digital data. This means that data owners feel secure with their data, by securely controlling their distribution. Their consent is required to access this data.” | [87], (p.262) | N/A |
| 21 | “Digital trust refers to the belief that technology and information systems can be relied upon, secure, and well-integrated into business processes”. | [88] | [89], (p.4) |
| 22 | “Digital trust, which is the users' confidence in the safety, privacy, security, reliability, and ethical handling of data by companies in the digital environment, correlates with the perceived value of the information conveyed” | [89], (p.6) | N/A |
| Thematical Group 3 | |||
| 23 | Digital trust is maintained through technologies like blockchain and smart contracts, replacing traditional 'implicit trust' with 'technically expressed trust'. | [90] | [91], (p.6) |
| 24 | The consumer’s belief that the service is technically capable of ensuring the successful execution of the transaction | [28] | [12], (p.433) |
| 25 | “The concepts of digital trust are represented as a layered model by dividing the system into trust, credentials, control data, and trust storage abstraction levels.” | [52], (p.582) | N/A |
| 26 | “Trust in the technology environment, digital trust (DT) in other words, as the belief of an individual towards a digital system regarding its reliability and punctuality in performing commercial and operational transactions.” | [44], (p.7) | N/A |
| 27 | “The extent to which users believe that a platform provides reliable services and maintains a trustworthy status within relevant verification organizations.” | [92] | [93], (p.5) |
| 28 | “The reliability of the system involves a shift from physical to digital and human to machine, which we refer to as digital trust, reflecting users' positive beliefs about accepting and using voice-assisted AI systems.” | [94] | [49], (p.203) |
| 29 | “DT reflects the user's confidence in the digital platform's consistency and punctuality when executing operational and commercial transactions.” | [44,95] | [96], (p.235) |
| Thematical Group 4 | |||
| 30 | “Trust is a mental state comprising (1) expectancy: the trustor expects a specific behaviour of the trustee such as providing valid information or effectively performing cooperative actions; (2) belief: the trustor believes that the expected behavior will occur, based on the evidence of the trustee’s competence, good intention, and integrity; (3) willingness to take a risk: the trustor is willing to take the risk for (or be vulnerable) that belief in a specific context, where there is an expectation for the specific behaviour of the trustee.” | [97] | [64], (p.107) |
| 31 | “Digital trust in blockchain can be defined as enabling user heuristics made between security and privacy that reflect their level of confidence. Digital trust is a kind of user heuristics in blockchain. (…)Digital trust as cognitive heuristics constitute information processing methods to make decisions more quickly and with less effort than more complex methods, and thus they reduce cognitive load during security assessment.” | [29], (p.2) | N/A |
| 32 | “A trust based either on past experience or evidence that an entity has behaved and/or will behave in accordance with the self-stated behaviour.” | [61], (p.885) | N/A |
| 33 | “The combination of cognitive trust and emotional trust. Cognitive trust includes practicality, commitment to execution, honesty, benevolence, and so on. Emotional trust includes likes, beliefs, and so on.” | [59], (p.4) | N/A |
| 34 | “Digital trust is defined as a ''measurable belief and/or confidence'' that is ''accumulated from past experiences'' and is an ''expecting value for the future''.” | [98] | [99], (p.106745) |
| 35 | “The willingness to rely on digitally presented information when there is limited means of verification” | [34], (p.1) | N/A |
| Thematical Group 5 | |||
| 36 | “The confidence that causes users to exercise a choice to interact, transact, and consume online. Fundamentally, it determines the quality of the interaction between those who give trust and those who guarantee to uphold said trust.” | [100], (p.25) | [101], (p.3) |
| 37 | “Trust in interactions that take place in an environment where human actors and/or technological elements are involved.” | [60], (p.2) | N/A |
| 38 | “Specific beliefs about the way that technology operates through a work environment” | [102] | [44], (p.7) |
| 39 | “Digital trust is a third dimension that affects digital B2B relationships. It specifically refers to trust between digital partners and it can also be influenced by the perception of the tools used. For instance, the opportunity to use technology that simulates real in-person contact reinforces trust, while only chatting has the opposite effect. According to this vision, technology represents an enabler of the relationship that can influence the formation of trust in a techno-mediated environment.” | [103], (p.2107) | N/A |
| Thematical Group 6 | |||
| 40 | “Digital trust, or "e-trust," is characterized as one's set of specific beliefs in the e-vendor, including integrity, benevolence, ability, and predictability, that results in behavioral intentions.” | [104] | [41], (p.1361) |
| 41 | “The digital trust category is also used as a general term to describe behavioral and cultural principles, including privacy, security, protection and data management” | [37] | [38], (p.544) |
| 42 | Is consumer’s confidence in a digital partner’s, business’ or institution’s commitment (written/unwritten) to prevent all sources of harm that may arise in transacting business between the two parties (consumer and partner/business/ institution). | [105] | N/A |
References
- Chauhan, D. Digital Trust Is Core to Our Relationship with Technology. Network Security 2023, 2023, S1353-4858(23)70047-0. [CrossRef]
- Pietrzak, P.; Takala, J. Digital Trust– Asystematic Literature Review. Forum Scientiae Oeconomia 2021, 9, 59–71. [CrossRef]
- Alpcan, T.; Levi, A.; Savas, E. Digital Trust Games: An Experimental Study. In Proceedings of the Lect. Notes Comput. Sci.; Baras, J., Katz, J., Altman, E., Eds.; 2011; Vol. 7037 LNCS, pp. 182–200.
- World Economic Forum Digital Trust Available online: https://initiatives.weforum.org/digital-trust/about (accessed on 17 March 2024).
- PwC Digital Trust and Cybersecurity Available online: https://www.pwc.com/my/en/services/digital/digital-trust-and-cybersecurity.html (accessed on 17 March 2024).
- ISACA Digital Trust Available online: https://www.isaca.org/digital-trust (accessed on 17 March 2024).
- Deloitte Future of Digital Trust Available online: https://www2.deloitte.com/de/de/pages/risk/articles/future-of-digital-trust.html (accessed on 17 March 2024).
- Marsh, S. Formalising Trust as a Computational Concept. PhD, University of Stirling, 1994.
- Mayer, R.C.; Davis, J.H.; Schoorman, F.D. An Integrative Model of Organizational Trust. The Academy of Management Review 1995, 20, 709. [CrossRef]
- Dimitrakos, T. System Models, e-Risks and e-Trust.; Zürich, Switzerland, 2001.
- Kożuch, B. The Dimensions of Trust in the Digital Era. In Trust, Organizations and the Digital Economy; Routledge: New York, 2021; pp. 15–26 ISBN 978-1-00-316596-5.
- Tunkevichus, E.; Rebiazina, V. CONSUMER DIGITAL TRUST: THE MAIN TRENDS AND RESEARCH DIRECTIONS. ROSSIISKII ZHURNAL MENEDZHMENTA-RUSSIAN MANAGEMENT JOURNAL 2021, 19, 429–450. [CrossRef]
- Chen, X.; Li, B.; Song, D.; Wang, M. Influences of Risk-Aversion Behavior and Purchasing Option in a Cross-Border Dual-Channel Supply Chain. Int. Trans. Oper. Res. 2023. [CrossRef]
- Chaudhuri, A. TRANSFORMATION WITH TRUSTWORTHY DIGITAL: POLICY DESIDERATA FOR BUSINESSES IN POST COVID-19 WORLD. EDPACS 2021, 63, 1–8. [CrossRef]
- Zhghenti, T.; Chkareuli, V. ENHANCING ONLINE BUSINESS SECTOR: DIGITAL TRUST FORMATION PROCESS. MARKETING AND MANAGEMENT OF INNOVATIONS 2021, 87–93. [CrossRef]
- Papic, A.; Radoja, K.; Szombathelyi, D. CYBER SECURITY AWARENESS OF CROATIAN STUDENTS AND THE PERSONAL DATA PROTECTION. In Proceedings of the University of JJ Strossmayer Osijek; Simic, M., Ed.; 2022; pp. 563–574.
- Hinkin, T.R.; Tracey, J.B. An Analysis of Variance Approach to Content Validation. Organizational Research Methods 1999, 2, 175–186. [CrossRef]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 Statement: An Updated Guideline for Reporting Systematic Reviews. Syst Rev 2021, 10, 89. [CrossRef]
- Pranckutė, R. Web of Science (WoS) and Scopus: The Titans of Bibliographic Information in Today’s Academic World. Publications 2021, 9, 12. [CrossRef]
- Elsevier Scopus Available online: https://www.scopus.com (accessed on 18 November 2024).
- Clarivate Web of Science Available online: https://www.webofscience.com (accessed on 18 November 2024).
- VOSviewer Available online: https://www.vosviewer.com// (accessed on 26 April 2024).
- Mubarak, M.F.; Petraite, M. Industry 4.0 Technologies, Digital Trust and Technological Orientation: What Matters in Open Innovation? Technological Forecasting and Social Change 2020, 161, 120332. [CrossRef]
- Mo, Z.; Liu, Y.; Lu, C.; Yu, J. Influences of Industrial Internet Platform Firms’ ESG Performance and Digital Leadership on User Firms’ Innovation Performance: The Mediating Role of Inter-Firm Trust. J. Digit. Econ. 2023, 2, 204–220. [CrossRef]
- Han, S.; Ulhoi, J.; Song, H. Digital Trust in Supply Chain Finance: The Role of Innovative Fintech Service Provision. J. Enterp. Inf. Manage. 2024. [CrossRef]
- Mubarak, M.; Ghobakhloo, M.; Evans, R.; Jucevicius, G.; Prestianawati, S.; Mubarik, M. Metaverse Adoption in the Manufacturing Industry: Impact on Social and Environmental Sustainability Performance. Asia-Pac. J. Bus. Adm. 2024. [CrossRef]
- Das, D.; Banerjee, S.; Chatterjee, P.; Ghosh, U.; IEEE A Comprehensive Analysis of Trust, Privacy, and Security Measures in the Digital Age. In Proceedings of the Proc. - IEEE Int. Conf. Trust, Priv. Secur. Intell. Syst. Appl., TPS-ISA; Institute of Electrical and Electronics Engineers Inc., 2023; pp. 360–369.
- Harrison McKnight, D.; Choudhury, V.; Kacmar, C. The Impact of Initial Consumer Trust on Intentions to Transact with a Web Site: A Trust Building Model. The Journal of Strategic Information Systems 2002, 11, 297–323. [CrossRef]
- Shin, D. Blockchain: The Emerging Technology of Digital Trust. TELEMATICS AND INFORMATICS 2019, 45. [CrossRef]
- Taghiyeva-Zeynalova, M.; Wang, Y.; Ta’eed, O.; ASSOC COMP MACHINERY Blockchain as a Value Enabler: Bridging Financial Assets and Intangibles. In Proceedings of the BSCI - Proc. ACM Int. Symp. Blockchain Secur. Crit. Infrastruct., co-located AsiaCCS; Association for Computing Machinery, Inc, 2019; pp. 113–119.
- Osuagwu, O.N.; Lekan Gbadamosi, S.; Ojo, E.E. Blockchain-Based Platforms for Agricultural Supply Chains. In Proceedings of the Int. Conf. Sci., Eng. Bus. Driv. Sustain. Dev. Goals, SEB4SDG; Institute of Electrical and Electronics Engineers Inc., 2024.
- Lee, N.; Varshney, L.; Michelson, H.; Goldsmith, P.; Davis, A. Digital Trust Substitution Technologies to Support Smallholder Livelihoods in Sub-Saharan Africa. Global Food Secur. 2022, 32. [CrossRef]
- Katete, G. Digital Elections and the Problem of Liquid Trust in the Kenyan Electoral Management Institution. Int. J. Afr. Renaiss. Stud. 2021, 16, 165–176. [CrossRef]
- Hochstein, R.; Harmeling, C.; Perko, T. Toward a Theory of Consumer Digital Trust: Meta-Analytic Evidence of Its Role in the Effectiveness of User-Generated Content. J. Acad. Mark. Sci. 2023. [CrossRef]
- Neill, G. Digital Trust and Emerging Technologies; KPMG, 2015;
- Büyüközkan, G.; Havle, C.; Feyzioglu, O. A New Digital Service Quality Model and Its Strategic Analysis in Aviation Industry Using Interval-Valued Intuitionistic Fuzzy AHP. J. Air Transp. Manage. 2020, 86. [CrossRef]
- Abraham, C.; Sims, R.; Daultrey, S.; Buff, A.; Fealey, A. March 18 2019,.
- Aiusheeva, I.; Soyfer, T. FORMATION OF THE ENVIRONMENT OF CONFIDENCE IN SHARING ECONOMY: PROBLEMS OF CIVIL REGULATION IN RUSSIA. INDEPENDENT JOURNAL OF MANAGEMENT & PRODUCTION 2022, 13, S536–S559. [CrossRef]
- Rychkova, I.; Ghriba, M. Trustworthiness Requirements in Information Systems Design: Lessons Learned from the Blockchain Community. Complex. Syst. Inform. Model. Q. 2023, 2023, 67–91. [CrossRef]
- Sharma, V.; Agrawal, R.; Manupati, V. Blockchain Technology as an Enabler for Digital Trust in Supply Chain: Evolution, Issues and Opportunities. INTERNATIONAL JOURNAL OF SYSTEM ASSURANCE ENGINEERING AND MANAGEMENT 2024. [CrossRef]
- Zolfaghari, A.; Thomas-Francois, K.; Somogyi, S. Consumer Adoption of Digital Grocery Shopping: What Is the Impact of Consumer’s Prior-to-Use Knowledge? Br. Food J. 2023, 125, 1355–1373. [CrossRef]
- Asprion, P.M.; Grieder, H.; Grimberg, F. Building Digital Trust to Protect Whistleblowers - A Blockchain-Based Reporting Channel. In Proceedings of the Proc. Annu. Hawaii Int. Conf. Syst. Sci.; Bui T.X., Ed.; IEEE Computer Society, 2023; Vol. 2023-January, pp. 4328–4337.
- Kfoury, E.; Khoury, D.; AlSabeh, A.; Gomez, J.; Crichigno, J.; Bou-Harb, E. A Blockchain-Based Method for Decentralizing the ACME Protocol to Enhance Trust in PKI. In Proceedings of the Int. Conf. Telecommun. Signal Process., TSP; Herencsar, N., Ed.; Institute of Electrical and Electronics Engineers Inc., 2020; pp. 461–465.
- Balci, G. Digitalization in Container Shipping: Do Perception and Satisfaction Regarding Digital Products in a Non-Technology Industry Affect Overall Customer Loyalty? Technol. Forecast. Soc. Change 2021, 172. [CrossRef]
- Svenson, F.; Peuser, M.; Çetin, F.; Aidoo, D.C.; Launer, M.A. Decision-Making Styles and Trust across Farmers and Bankers: Global Survey Results. Decis. Anal. J. 2024, 10. [CrossRef]
- Mohlmann, M. Unjustified Trust Beliefs: Trust Conflation on Sharing Economy Platforms. Res Policy 2021, 50. [CrossRef]
- Shipunova, O.; Berezovskaya, I.; Pozdeeva, E.; Evseeva, L.; Barlybayeva, S. Digital Trust Indicators in Human-Computer Interaction. In Proceedings of the Peter the Great St. Petersburg Polytechnic University; Rocha, A., Adeli, H., Dzemyda, G., Moreira, F., Eds.; Springer Science and Business Media Deutschland GmbH, 2022; Vol. 468 LNNS, pp. 245–254.
- Kluiters, L.; Srivastava, M.; Tyll, L. The Impact of Digital Trust on Firm Value and Governance: An Empirical Investigation of US Firms. Soc. Bus. Rev. 2023, 18, 71–103. [CrossRef]
- Ranieri, A.; Di Bernardo, I.; Mele, C. Serving Customers through Chatbots: Positive and Negative Effects on Customer Experience. Journal of Service Theory and Practice 2024, 34, 191–215. [CrossRef]
- Deprez, J.; Ponsard, C.; Matskanis, N.; IEEE A Goal-Oriented Requirements Analysis for the Collection, Use and Exchange of Electronic Evidence across EU Countries. In Proceedings of the Proc. - IEEE Int. Requir. Eng. Conf. Workshops, REW; Institute of Electrical and Electronics Engineers Inc., 2016; pp. 106–113.
- Chatterjee, J.; Damle, M.; Aslekar, A. Digital Trust in Industry 4.0 & 5.0: Impact of Frauds. In Proceedings of the Proc. Int. Conf. Intell. Comput. Control Syst., ICICCS; Institute of Electrical and Electronics Engineers Inc., 2023; pp. 922–928.
- Latvakoski, J.; Kylloenen, V.; Ronkainen, J. Decentralised IOTA-Based Concepts of Digital Trust for Securing Remote Driving in an Urban Environment. IoT. 2023, 4, 582–609. [CrossRef]
- Alsamara, T.; Khalidi, F. Review Of Covid-19 And E-Commerce In The Moroccan Legal System: Challenges And Opportunities. J. Leg. Ethical Regul. Iss. 2020, 23, 1–9.
- Soldatova, A.V.; Budrin, A.G.; Budrina, E.V.; Presnova, A.A.; Girsh, L.V. Customer Loyalty Management in the Context of Digital Transformation of Business. In Proceedings of the Proc. IEEE Int. Conf. “Qual. Manag., Transp. Inf. Secur., Inf. Technol.”, T QM IS; Shaposhnikov S.O., Saint Petersburg Electrotechnical University “LETI,” Prof.P.Str. 5, Saint Petersburg, Eds.; Institute of Electrical and Electronics Engineers Inc., 2021; pp. 907–910.
- Kayhan, H. Ensuring Trust In Pharmaceutical Supply Chains By Data Protection Through A Design Approach To Blockchains. Blockchain. Healthc. Today. 2022, 5. [CrossRef]
- Piccininni, M.; Rohmann, J.; Logroscino, G.; Kurth, T. Blockchain-Based Innovations for Population-Based Registries for Rare Neurodegenerative Diseases. Front. Blockchain. 2020, 3. [CrossRef]
- Jelovac, D.; Ljubojevic, C.; Ljubojevic, L. HPC in Business: The Impact of Corporate Digital Responsibility on Building Digital Trust and Responsible Corporate Digital Governance. Digit. Poli. Regul. Govern. 2022, 24, 485–497. [CrossRef]
- Kafeza, I. An Intelligent Mediation Platform for Smart Contracts in Blockchain. In Proceedings of the CEUR Workshop Proc.; Cong G., Ramanath M., Eds.; CEUR-WS, 2021; Vol. 3052.
- Guo, Y. Digital Trust and the Reconstruction of Trust in the Digital Society: An Integrated Model Based on Trust Theory and Expectation Confirmation Theory. Digit. Gov. Res. Pract. 2022, 3. [CrossRef]
- Gronier, G.; Lambert, M. A Model to Measure the Perceived Quality of Service in eGovernment. In Proceedings of the Proc. European Conf. on e-Gov., ECEG; ODonnell, D., Ed.; 2010; pp. 527–531.
- Akram, R.; Ko, R. Digital Trust - Trusted Computing and beyond: A Position Paper. In Proceedings of the Proc. - IEEE Int. Conf. Trust, Secur. Priv. Comput. Commun., TrustCom; Institute of Electrical and Electronics Engineers Inc., 2014; pp. 884–892.
- Khan, W.; Aalsalem, M.; Khan, M.; Arshad, Q. Enabling Consumer Trust Upon Acceptance of IoT Technologies Through Security and Privacy Model. In Proceedings of the Lect. Notes Electr. Eng.; Park, J., Jin, H., Jeong, Y., Khan, M., Eds.; Springer Verlag, 2016; Vol. 393, pp. 111–117.
- Flew, T. The Crisis of Digital Trust in the Asia-Pacific Commentary. INTERNATIONAL JOURNAL OF COMMUNICATION 2019, 13, 4738–4750.
- Rane, T.; Huang, J. Blockchain-Based Digital Trust Mechanism: A Use Case of Cloud Manufacturing of LDS Syringes for COVID-19 Vaccination. J. Integr. Des. Process Sci. 2022, 26, 103–129. [CrossRef]
- Podsakoff, P.M.; MacKenzie, S.B.; Podsakoff, N.P. Recommendations for Creating Better Concept Definitions in the Organizational, Behavioral, and Social Sciences. Organizational Research Methods 2016, 19, 159–203. [CrossRef]
- Sell, J. Definitions and the Development of Theory in Social Psychology. Soc Psychol Q 2018, 81, 8–22. [CrossRef]
- Colquitt, J.A.; Sabey, T.B.; Rodell, J.B.; Hill, E.T. Content Validation Guidelines: Evaluation Criteria for Definitional Correspondence and Definitional Distinctiveness. Journal of Applied Psychology 2019, 104, 1243–1265. [CrossRef]
- Vidiasova, L.; Tensina, I.; Bershadskaya, E. Cyber-Social Trust in Different Spheres: An Empirical Study in Saint-Petersburg. In Digital Transformation and Global Society; Alexandrov, D.A., Boukhanovsky, A.V., Chugunov, A.V., Kabanov, Y., Koltsova, O., Musabirov, I., Eds.; Communications in Computer and Information Science; Springer International Publishing: Cham, 2020; Vol. 1242, pp. 3–13 ISBN 978-3-030-65217-3.
- Wu, G.; Hu, X.; Wu, Y. Effects of Perceived Interactivity, Perceived Web Assurance and Disposition to Trust on Initial Online Trust. Journal of Computer-Mediated Communication 2010, 16, 1–26. [CrossRef]
- Facebook Available online: https://www.facebook.com/ (accessed on 21 February 2025).
- Linkedin Available online: https://www.linkedin.com/ (accessed on 21 February 2025).
- jamovi The Jamovi Project 2022.
- Ritter, J. Digital Trust Available online: https://www.techtarget.com/whatis/definition/digital-trust (accessed on 11 March 2024).
- Orekhova, E. Digital Trust as a Contributor to Development under Uncertainty and Turbulence. Bulletin of the Saratov State Socio-Economic University 2020, 3, 24–27.
- Marcial, D.E.; Launer, M.A. Towards the Measurement of Digital Trust in the Workplace: A Proposed Framework. 2019. [CrossRef]
- Marcial, D.E.; Arcelo, A.; Montemayor, J.; Launer, M. DIGITAL TRUST IN THE ACADEME: PEOPLE, SOFTWARE, AND HARDWARE. INFORMATION TECHNOLOGIES AND LEARNING TOOLS 2022, 89, 178–189. [CrossRef]
- Launer, M.; Çetin, F.; Paliszkiewicz, J. Digital Trust in the Workplace: Testing a New Instrument on a Multicultural Sample. Forum Scientiae Oeconomia 2022, 10, 29–47. [CrossRef]
- Frenehard, T. GRC Tuesdays: Building Digital Trust, What Does It Really Mean? Available online: https://community.sap.com/t5/technology-blogs-by-sap/grc-tuesdays-building-digital-trust-what-does-it-really-mean/ba-p/13412611 (accessed on 11 April 2024).
- PwC The Journey to Digital Trust.; PricewaterhouseCoopers.: London, UK, 2019;
- Ferraro, C.; Wheeler, M.; Pallant, J.; Wilson, S.; Oldmeadow, J. Not so Trustless after All: Trust in Web3 Technology and Opportunities for Brands. Bus. Horiz. 2023, 66, 667–678. [CrossRef]
- Bhattacharjee, S.; Gopal, R.D.; Lertwachara, K.; Marsden, J.R. Impact of Legal Threats on Online Music Sharing Activity: An Analysis of Music Industry Legal Actions. SSRN Journal 2005. [CrossRef]
- Wang, Y.; Han, J.H.; Beynon-Davies, P. Understanding Blockchain Technology for Future Supply Chains: A Systematic Literature Review and Research Agenda. SCM 2019, 24, 62–84. [CrossRef]
- Gangneux, J. Digital Citizenship in a Datafied Society: By Arne Hintz, Lina Dencik and Karin Wahl-Jorgensen, Cambridge, UK, Polity Press, 2019,180 Pp., £15.99 (Hardback), ISBN 9781509527168. Information, Communication & Society 2019, 22, 2211–2213. [CrossRef]
- Li, F.; Betts, S.C. Trust: What It Is And What It Is Not. IBER 2003, 2. [CrossRef]
- Accenture Digital Trust in the IoT Era; Accenture Consulting, 2015;
- Mattila, J.; Seppälä, T. Digital Trust, Platforms, and Policy 2016.
- Goint, M.; Bertelle, C.; Duvallet, C. Establish Trust for Sharing Data for Smart Territories Thanks to Consents Notarized by Blockchain. In Proceedings of the Universite de Rouen Normandie; Prieto, J., Partida, A., Leitao, P., Pinto, A., Eds.; Springer Science and Business Media Deutschland GmbH, 2022; Vol. 320 LNNS, pp. 261–271.
- Launer, M.; Çetin, F.; Paliszkiewicz, J. Digital Trust in the Workplace: Testing a New Instrument on a Multicultural Sample. Forum Scientiae Oeconomia 2022, 10, 29–47. [CrossRef]
- Sartono, Y.; Siti Astuti, E.; Wilopo, W.; Noerman, T. Sustainable Digital Transformation: Its Impact on Perceived Value and Adoption Intention of Industry 4.0 in Moderating Effects of Uncertainty Avoidance. F1000 Res. 2024, 13. [CrossRef]
- Gromek, M. Clarifying the Blurry Lines of FinTech: Opening the Pandora’s Box of FinTech Categorization. In The Rise and Development of FinTech Accounts of Disruption from Sweden and Beyond; Routledge, 2018.
- Pashkov, P.; Pelykh, V. A Conceptual Framework of Developing Ecosystem Strategies for Digital Financial Services. In Proceedings of the CEUR Workshop Proc.; Telnov Y., Plekhanov Russian University of Economics, A.D. of A.I. and I.S., Stremyanny lane 36, Moscow, Fiodorov I., Plekhanov Russian University of Economics, A.D. of A.I.T. and I.S., Stremyanny lane 36, Moscow, Eds.; CEUR-WS, 2021; Vol. 2919, pp. 48–58.
- Sundararajan, A. Commentary: The Twilight of Brand and Consumerism? Digital Trust, Cultural Meaning, and the Quest for Connection in the Sharing Economy. Journal of Marketing 2019, 83, 32–35. [CrossRef]
- Ko, G.; Amankwah-Amoah, J.; Appiah, G.; Larimo, J. Non-Market Strategies and Building Digital Trust in Sharing Economy Platforms. AIMS Research Publication 2023, 2, 1–10. [CrossRef]
- Fernandes, T.; Oliveira, E. Understanding Consumers’ Acceptance of Automated Technologies in Service Encounters: Drivers of Digital Voice Assistants Adoption. Journal of Business Research 2021, 122, 180–191. [CrossRef]
- Davis, F.D. Perceived Usefulness, Perceived Ease of Use, and User Acceptance of Information Technology. MIS Quarterly 1989, 13, 319. [CrossRef]
- Loh, H.; Lee, J.; Gu, Y.; Chen, H.; Tay, H. The Effects of Digital Platforms on Customers’ Satisfaction in International Shipping Business. Rev. Int. Bus. Strategy 2024, 34, 231–244. [CrossRef]
- Huang, J.; Nicol, D.M. Trust Mechanisms for Cloud Computing. J Cloud Comput Adv Syst Appl 2013, 2, 9. [CrossRef]
- International Telecommunication Union Telecommunication Standardization (ITU-T) Series Y: Global Information Infrastructure, Internet Protocol Aspects, Next-Generation Networks, Internet of Things and Smart Cities; Geneva, Switzerland, 2017;
- Ting, H.; Kang, X.; Li, T.; Wang, H.; Chu, C. On the Trust and Trust Modeling for the Future Fully-Connected Digital World: A Comprehensive Study. IEEE Access 2021, 9, 106743–106783. [CrossRef]
- Bhaskar, C.; Chaturvedi, R.S.; Filipovic, c.; Brewer, G. Digital Intelligence Index; The Fletcher School: Medford, 2021;
- Venter, I.M.; Cranfield, D.J.; Tick, A.; Blignaut, R.J.; Renaud, K.V. ‘Lockdown’: Digital and Emergency eLearning Technologies—A Student Perspective. Electronics (Switzerland) 2022, 11. [CrossRef]
- Akbari, M.; Rezvani, A.; Shahriari, E.; Zúñiga, M.Á.; Pouladian, H. Acceptance of 5 G Technology: Mediation Role of Trust and Concentration. Journal of Engineering and Technology Management 2020, 57, 101585. [CrossRef]
- Corsaro, D.; D’Amico, V. How the Digital Transformation from COVID-19 Affected the Relational Approaches in B2B. J. Bus. Ind. Mark. 2022, 37, 2095–2115. [CrossRef]
- Gefen; Karahanna; Straub Trust and TAM in Online Shopping: An Integrated Model. MIS Quarterly 2003, 27, 51. [CrossRef]
- Thomas-Francois, K.; Somogyi, S.; Zolfaghari, A. The Cultural Acceptance of Digital Food Shopping: Conceptualisation, Scale Development and Validation. Int. J. Retail Disrtib. Manage. 2023, 51, 306–326. [CrossRef]

| Group nr. | Main group’s theme |
|---|---|
| Group 1 (n=12) | Confidence in people, processes and technology to create a secure digital environment |
| Group 2 (n=8) | Trust in data protection, privacy, security, and ethical information handling |
| Group 3 (n=8) | Trust in the technical capability and reliability of technology |
| Group 4 (n=7) | Trust as a mental state involving cognitive, emotional, and experiential factors |
| Group 5 (n=4) | Trust as an enabler in digital relationships, interactions, and business networks |
| Group 6 (n=3) | Trust based on ethical behaviour and cultural principles |
| Category 1: Ability | Source |
|---|---|
| 1.Competence and reliable performance (cumulative n=19) | |
| 1.1. Competence (n=2) | [39,44] |
| 1.2. Performance (n=2) | [39,45] |
| 1.3. System’s reliability (incl. safety and quality) (n=8) | [14,33,42,43,46,47,48,49] |
| 1.4. Operational stability (incl. availability, resilience and business continuity) (n=7) | [14,36,39,42,45,47,49] |
| 2. Security and control (cumulative n=25) | |
| 2.1. Identity and access management (inc. authentication, authorization, safe credentials and identifiability) (n=6) | [2,36,39,50,51,52] |
| 2.2. Confidentiality (incl. data protection and control over own data) (n=9) | [38,39,40,42,50,52,53,54,55] |
| 2.3. Integrity of data (incl. immutability) (n=10) | [27,32,39,42,43,45,49,50,56,57] |
| 3. Secure system architecture (cumulative n=8) | [39,56] |
| 3.1. Automation (n=2) | |
| 3.2. Decentralisation (incl. consensus algorithms, permissionless access, censorship resistance and cryptographic functions / protocols) (n=5) | [32,39,42,43,56] |
| 3.3. Interoperability (n=1) | [39] |
| Category 2: Benevolence | Source |
|---|---|
| 1. Relational credibility (cumulative n=10) | |
| 1.1. Goodwill (incl. benevolence, fairness and honesty) (n=3) | [41,58,59] |
| 1.2. Reliability (predictability of or confidence in service provider) (n=3) | [2,41,49] |
| 1.3. Reputation (incl. credibility) (n=4) | [2,57,60,61] |
| 2. User experience and support (cumulative n=12) | |
| 2.1. Satisfaction of customer service and support (incl. prompt resolution of the issues) (n=6) | [27,44,45,46,48,49] |
| 2.2. Positive past experience (n=3) | [47,60,61] |
| 2.3. Usability (n=3) | [39,59,60] |
| Category 3: Integrity | Source |
|---|---|
| 1. Core ethical principles (cumulative n=14) | |
| 1.1. Integrity (the principle of the organization) (n=1) | [39] |
| 1.2. Data ethics (incl. responsible use and privacy) (n=12) | [26,29,33,36,39,42,47,50,53,54,61,62] |
| 1.3. Sustainability (n=1) | [24] |
| 2. Governance and compliance (cumulative n=13) | |
| 2.1. Accountability (n=6) | [27,32,36,39,40,63] |
| 2.2. Compliance with regulations (n=6) | [15,39,40,55,62,63] |
| 2.3. Application of standards (n=1) | [60] |
| Category 4: Openness (cumulative n=23) | Source |
|---|---|
| 1. Transparency (n=11) | [27,32,36,39,40,43,47,50,58,63,64] |
| 2. Auditability (incl. certification and independent verification) (n=6) | [24,32,39,47,50,61] |
| 3. Traceability (incl. data provenance) (n=6) | [2,39,40,50,51,64] |
| Code | Category | Operationalised description |
|---|---|---|
| Category 1: Ability | ||
| F1 | 1.Competence and performance | The entity demonstrates competence and reliably delivers services or products. |
| F2 | 2. Security and control | The entity ensures secure access, protects data, and maintains its integrity. |
| F3 | 3. Secure system architecture | The entity employs a secure architecture and processes to ensure efficiency, control, and integration. |
| Category 2: Benevolence | ||
| F4 | 1. Relational credibility | The entity demonstrates fairness, honesty, and reliability, building a strong reputation. |
| F5 | 2. User experience and support | The entity ensures a positive user experience and provides responsive support. |
| Category 3: Integrity | ||
| F6 | 1. Core ethical principles | The entity demonstrates integrity, protects data privacy, and adopts sustainable practices. |
| F7 | 2. Governance and compliance | The entity ensures governance and compliance in accordance with regulations and standards. |
| Category 4: Openness | ||
| F8 | 1. Auditability | The entity ensures compliance through certifications, audits, and supervision. |
| F9 | 2. Traceability | The entity ensures traceability by providing information about data origins. |
| Language | N | % | Age | N | % | Education | N | % |
|---|---|---|---|---|---|---|---|---|
| English | 47 | 47,5% | 18-24 | 21 | 21,2% | High school diploma or equivalent | 20 | 20,2% |
| Latvian | 52 | 52,5% | 25-34 | 28 | 28,3% | College | 10 | 10,1% |
| 35-44 | 34 | 34,3% | Bachelor's degree | 26 | 26,3% | |||
| 45-54 | 13 | 13,3% | Master's degree | 43 | 43,4% | |||
| 55-64 | 3 | 3,0% |
| Code | Category | SD | p | Rating | htc |
|---|---|---|---|---|---|
| F1 | Competence and performance | 1.173 | <.001 | 4.18 | 0.84 |
| F2 | Security and control | 0.969 | <.001 | 4.41 | 0.88 |
| F3 | Secure system architecture | 0.959 | <.001 | 4.28 | 0.86 |
| F4 | Relational credibility | 0.956 | <.001 | 4.32 | 0.86 |
| F5 | User experience and support | 1.082 | <.001 | 4.18 | 0.84 |
| F6 | Core ethical principles | 1.036 | <.001 | 4.26 | 0.85 |
| F7 | Governance and compliance | 0.873 | <.001 | 4.48 | 0.90 |
| F8 | Auditability | 1.152 | <.001 | 4.17 | 0.83 |
| F9 | Traceability | 0.894 | <.001 | 4.34 | 0.87 |
| Overall | 4.29 | 0.86 |
| Code | Category | D2 SD | D2 p | D3 SD | D3 p | D4 SD | D4 p |
|---|---|---|---|---|---|---|---|
| F1 | Competence and performance | 1.003 | <.001 | 1.035 | <.001 | 1.082 | <.001 |
| F2 | Security and control | 0.955 | <.001 | 1.218 | <.001 | 1.204 | <.001 |
| F3 | Secure system architecture | 1.082 | <.001 | 1.051 | <.001 | 1.109 | <.001 |
| F4 | Relational credibility | 1.069 | <.001 | 1.190 | <.001 | 1.063 | <.001 |
| F5 | User experience and support | 1.094 | <.001 | 1.123 | <.001 | 1.071 | <.001 |
| F6 | Core ethical principles | 1.041 | <.001 | 1.211 | <.001 | 1.023 | <.001 |
| F7 | Governance and compliance | 1.114 | <.001 | 1.228 | <.001 | 1.161 | <.001 |
| F8 | Auditability | 1.264 | <.001 | 1.229 | <.001 | 1.159 | <.001 |
| F9 | Traceability | 1.161 | <.001 | 1.123 | <.001 | 1.218 | <.001 |
| Code | Category | D1 Rating | D2 Rating | D2 htd | D3 Rating | D3 htd | D4 Rating | D4 htd |
|---|---|---|---|---|---|---|---|---|
| F1 | Competence and performance | 4.18 | 3,65 | 0,13 | 3,36 | 0,21 | 3,53 | 0,16 |
| F2 | Security and control | 4.41 | 3,62 | 0,20 | 3,31 | 0,28 | 3,59 | 0,21 |
| F3 | Secure system architecture | 4.28 | 3,47 | 0,20 | 3,43 | 0,21 | 3,35 | 0,23 |
| F4 | Relational credibility | 4.32 | 3,41 | 0,23 | 3,15 | 0,29 | 3,48 | 0,21 |
| F5 | User experience and support | 4.18 | 3,13 | 0,26 | 3,27 | 0,23 | 3,71 | 0,12 |
| F6 | Core ethical principles | 4.26 | 3,42 | 0,21 | 3,06 | 0,30 | 3,35 | 0,23 |
| F7 | Governance and compliance | 4.48 | 3,23 | 0,31 | 3,11 | 0,34 | 3,17 | 0,33 |
| F8 | Auditability | 4.17 | 3,21 | 0,24 | 3,00 | 0,29 | 3,06 | 0,28 |
| F9 | Traceability | 4.34 | 3,17 | 0,29 | 3,06 | 0,32 | 2,92 | 0,36 |
| Overall | 4.29 | 3,37 | 0,23 | 3,20 | 0,27 | 3,35 | 0,24 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).





