Submitted:
14 February 2025
Posted:
18 February 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Blood Circulation-Based Fingerprinting: Technology Overview
2.1. Detection Method
2.2. Unique Features
2.3. Advantages
- Enhanced Security: Blood flow patterns are harder to spoof compared to traditional fingerprint systems. According to Ratha et al. (2001), the complexity of vascular patterns makes them nearly impossible to replicate using conventional spoofing techniques.
- Live Verification: The system can validate that the sample comes from a living person, adding an additional layer of security. This feature is particularly important in high-security environments where liveness detection is crucial.
- Reduced Error Rates: The technology reduces false acceptance and rejection rates, improving overall system reliability. Studies have shown that blood flow- based systems achieve a false acceptance rate (FAR) of less than 0.001%, significantly lower than traditional fingerprint systems.
3. Comparative Analysis: Traditional vs. Blood Flow-Based Biometric Systems
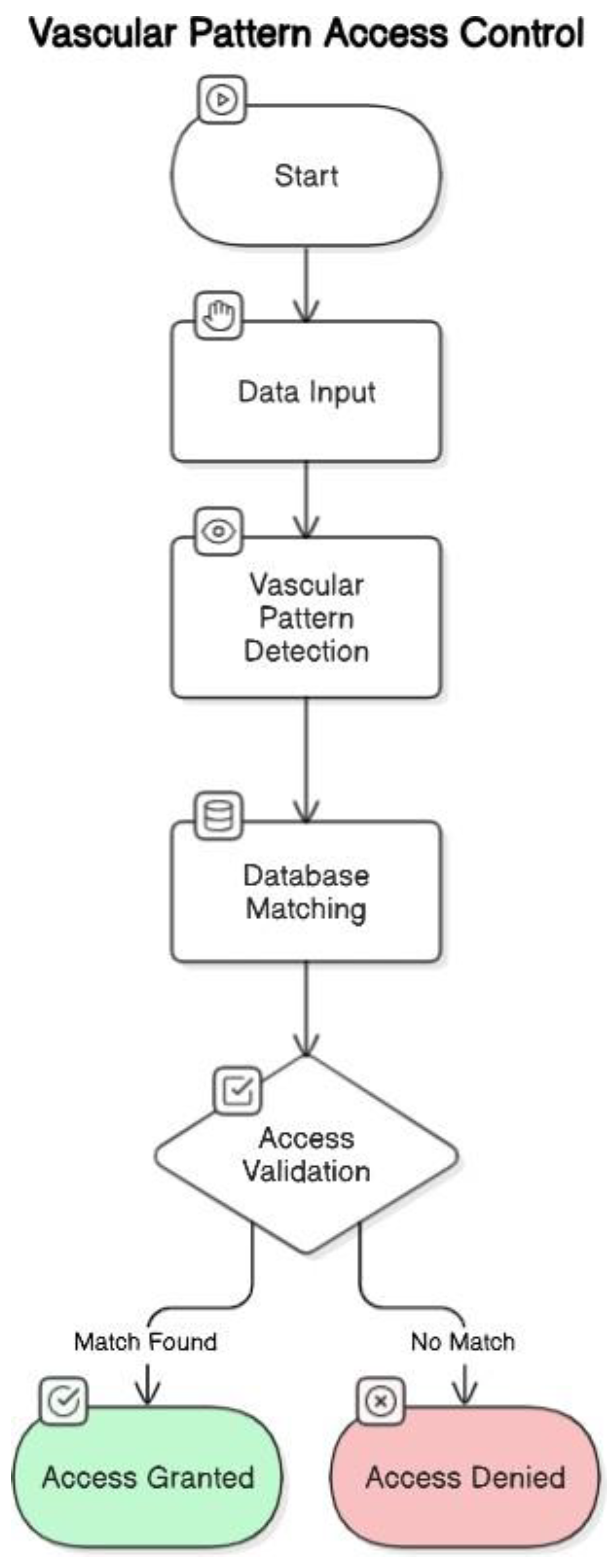
3.1. Technical Process of Biometric Authentication
- Data Input: The system captures a hand scan to detect vascular patterns.
- Vascular Pattern Detection: Specialized sensors detect the unique blood flow patterns.
- Database Matching: The detected patterns are compared against a database of stored vascular patterns.
- Access Validation: If a match is found, access is granted; otherwise, it is denied.
4. Potential Sales Models for Blood Flow-Based Bio-Metric Technology
4.1. B2B (Business-to-Business) Sales Model
- Target Audience: Enterprises, government agencies, security firms, hospitals, banks, and data centers.
-
Revenue Streams:
- -
- Direct sales of biometric hardware (scanners, sensors).
- -
- Subscription-based access to cloud-based biometric authentication services.
- -
- Licensing the technology to security companies or device manufacturers.
-
Sales Approach:
- -
- Direct Sales Team: A specialized sales force focusing on large contracts and customizing solutions for businesses.
- -
- Channel Partnerships: Partnering with security equipment suppliers and technology resellers.
4.2. B2C (Business-to-Consumer) Sales Model
- Target Audience: Individual consumers, home users, tech enthusiasts, and privacy- conscious individuals.
-
Revenue Streams:
- -
- Direct sales of consumer devices (fingerprint scanners, personal security sys- tems).
- -
- Software-as-a-Service (SaaS) model for personalized biometric access on per- sonal devices.
-
Sales Approach:
- -
- Online Direct Sales: E-commerce platforms to sell personal biometric secu- rity devices.
- -
- Marketing and PR Campaigns: Emphasizing the privacy and security aspects of the technology.
- -
- Retail Partnerships: Collaborating with consumer electronics stores.
4.3. Subscription-Based SaaS Model
- Target Audience: Small and medium-sized businesses (SMBs), security-conscious individuals, or businesses needing scalable authentication solutions.
-
Revenue Streams:
- -
- Monthly or annual subscription fees for access to biometric authentication services.
- -
- Tiered pricing based on the number of users or authentication requests.
-
Sales Approach:
- -
- Freemium Model: Offering a free trial with limited features.
- -
- Partner Integrations: Collaborating with software developers or hardware manufacturers.
4.4. Licensing or White-Label Model
- Target Audience: Security companies, device manufacturers, and software devel- opers.
- Revenue Streams:
- Licensing the proprietary technology to other businesses.
- White-labeling the technology for companies to brand as their own biometric solution.
- Sales Approach:
- License Agreement: Negotiating licensing agreements for the rights to use the technology.
- Long-term Partnerships: Customizing and integrating the technology into existing offerings.
4.5. Enterprise Sales & Consulting Model
- Target Audience: Large organizations, government entities, military institutions, and high-security industries.
- Revenue Streams:
- High-value, bespoke solutions developed for specific clients.
- Ongoing service agreements for maintenance, updates, and technical support.
- Sales Approach:
- Consultative Selling: Offering personalized consultations to understand client needs.
- Long Sales Cycles: Managing the complexity and costs of enterprise solu- tions.
4.6. Partnerships and Collaborations
- Target Audience: Technology companies, hardware manufacturers, and large enterprise systems.
-
Revenue Streams:
- -
- Co-branded partnerships with larger companies.
- -
- Joint ventures for shared product development and distribution.
-
Sales Approach:
- -
- Strategic Alliances: Collaborating with leading players in the security and tech industries.
- -
- Cross-Promotion: Creating bundled products with existing systems.
4.7. Freemium and Consumer Education Model
- Target Audience: Tech-savvy individuals, privacy advocates, and general con- sumers.
-
Revenue Streams:
- -
- Offering a free version of the biometric security software with an option to upgrade to premium features.
-
Sales Approach:
- -
- Free Trials: Encouraging user adoption through free trials.
- -
- User Education: Educating the target audience about the benefits of blood flow-based biometric security.
5. Discussion
6. Conclusions
References
- Jain, A. K., Ross, A., & Nandakumar, K. (2011). Introduction to Biometrics. Springer.
- Maltoni, D., Maio, D., Jain, A. K., & Prabhakar, S. (2009). Handbook of Fingerprint Recognition. Springer.
- Ratha, N. K., Connell, J. H., & Bolle, R. M. (2001). Enhancing security and privacy in biometrics-based authentication systems. IBM Systems Journal, 40(3), 614-634. [CrossRef]
- Zhang, D., & Lu, G. (2003). Advanced Biometric Technologies. CRC Press.
- Wayman, J. L., Jain, A. K., Maltoni, D., & Maio, D. (2005). Biometric Systems: Technology, Design, and Performance Evaluation. Springer.
- Phillips, P. J., Scruggs, T., O’Toole, A. J., Flynn, P. J., Bowyer, K. W., Schott,.
- C. L., & Sharpe, M. (2010). FRVT 2006 and ICE 2006 large-scale results. IEEE Transactions on Pattern Analysis and Machine Intelligence, 32(5), 831-846.
- Ross, A., & Jain, A. K. (2004). Multimodal biometrics: An overview. Proceedings of the 12th European Signal Processing Conference (EUSIPCO), 1221-1224.Bowyer, K. W., Hollingsworth, K., & Flynn, P. J. (2008). Image understanding for iris biometrics: A survey. Computer Vision and Image Understanding, 110(2), 281-307.
| Category | Traditional Fingerprint | Blood Flow-Based |
|---|---|---|
| Input Data | Fingerprint ridges | Blood flow patterns |
| Detection Method | Capacitive or optical scanners | Optical/infrared sensors |
| Key Features | Easy to collect but prone to spoofing | Difficult to replicate, live verification |
| Applications | Smartphones, access control | High-security areas, sensitive data |
| Security Level | Moderate | High |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





