Submitted:
23 December 2024
Posted:
24 December 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
- How to incorporate the use of DTCWT and PSO to improve the imperceptibility of watermarked images while retaining high robustness?
- How well does the proposed method compare with traditional techniques like DWT and DCT in terms of PSNR (Peak Signal-to-Noise Ratio) and NCC (Normalized Cross-Correlation) under standard image processing manipulations: compression, cropping, scaling?
- What are the practical challenges in this watermarking scheme when applying it to real-world digital media applications, and how can these limitation be addressed?
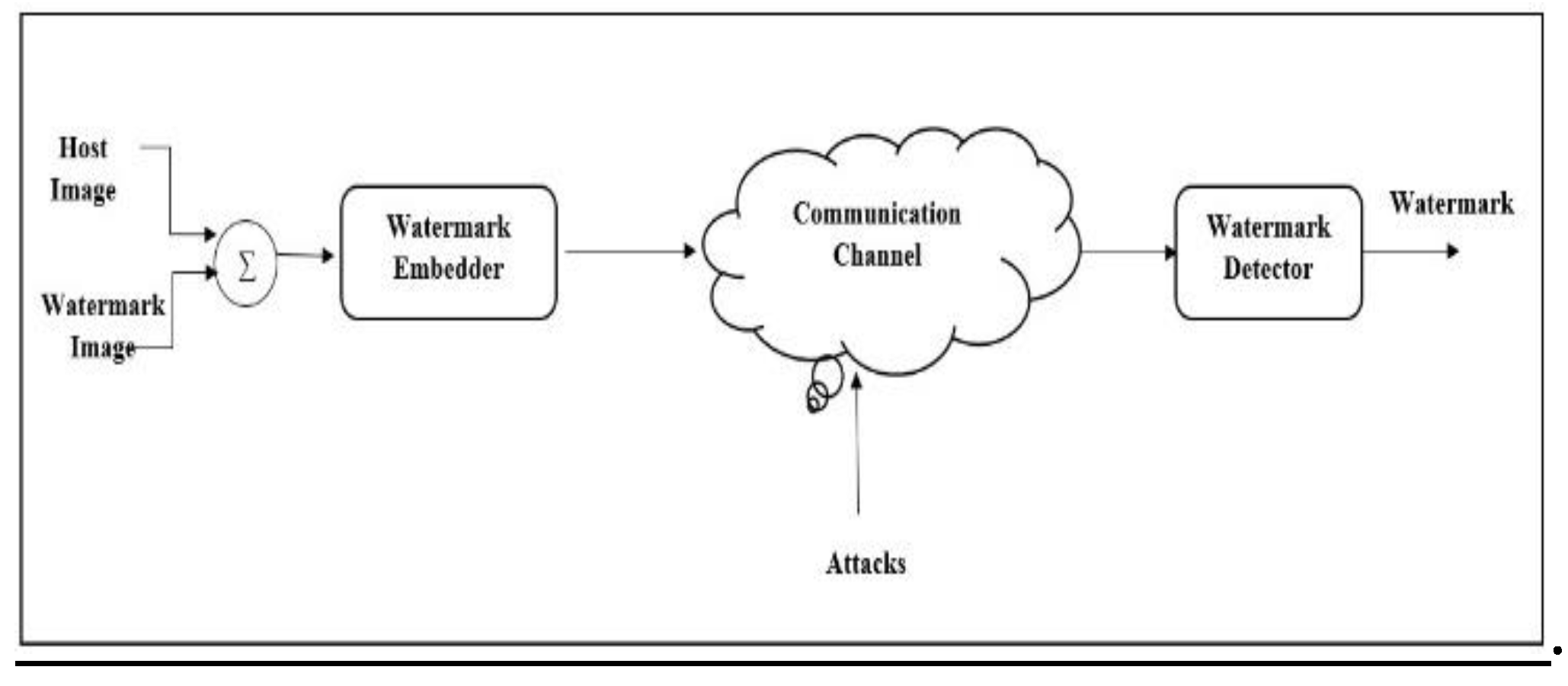
2. Methodology
2.1. Overall Research Design
2.2. Dataset
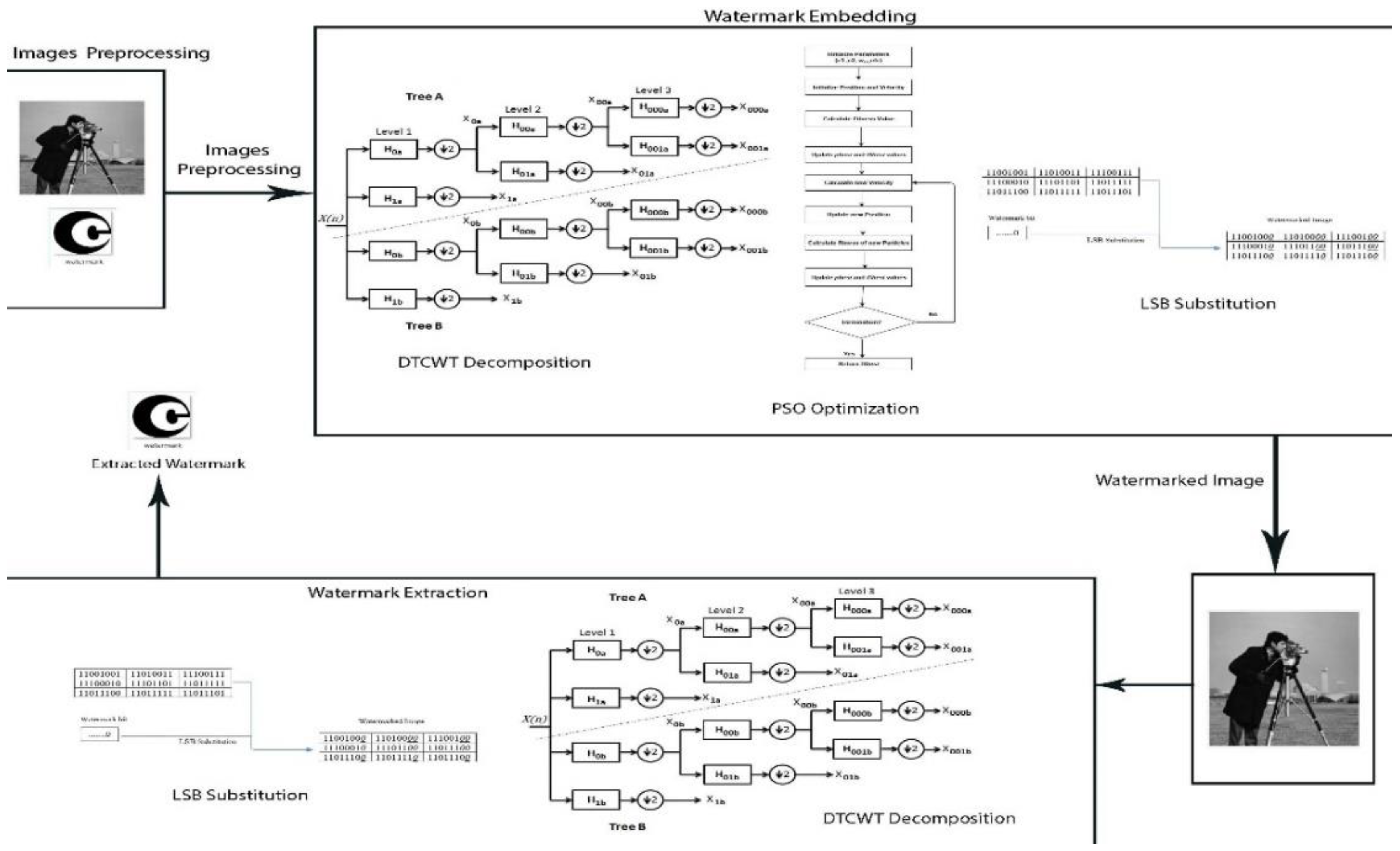
2.3. Watermark Embedding
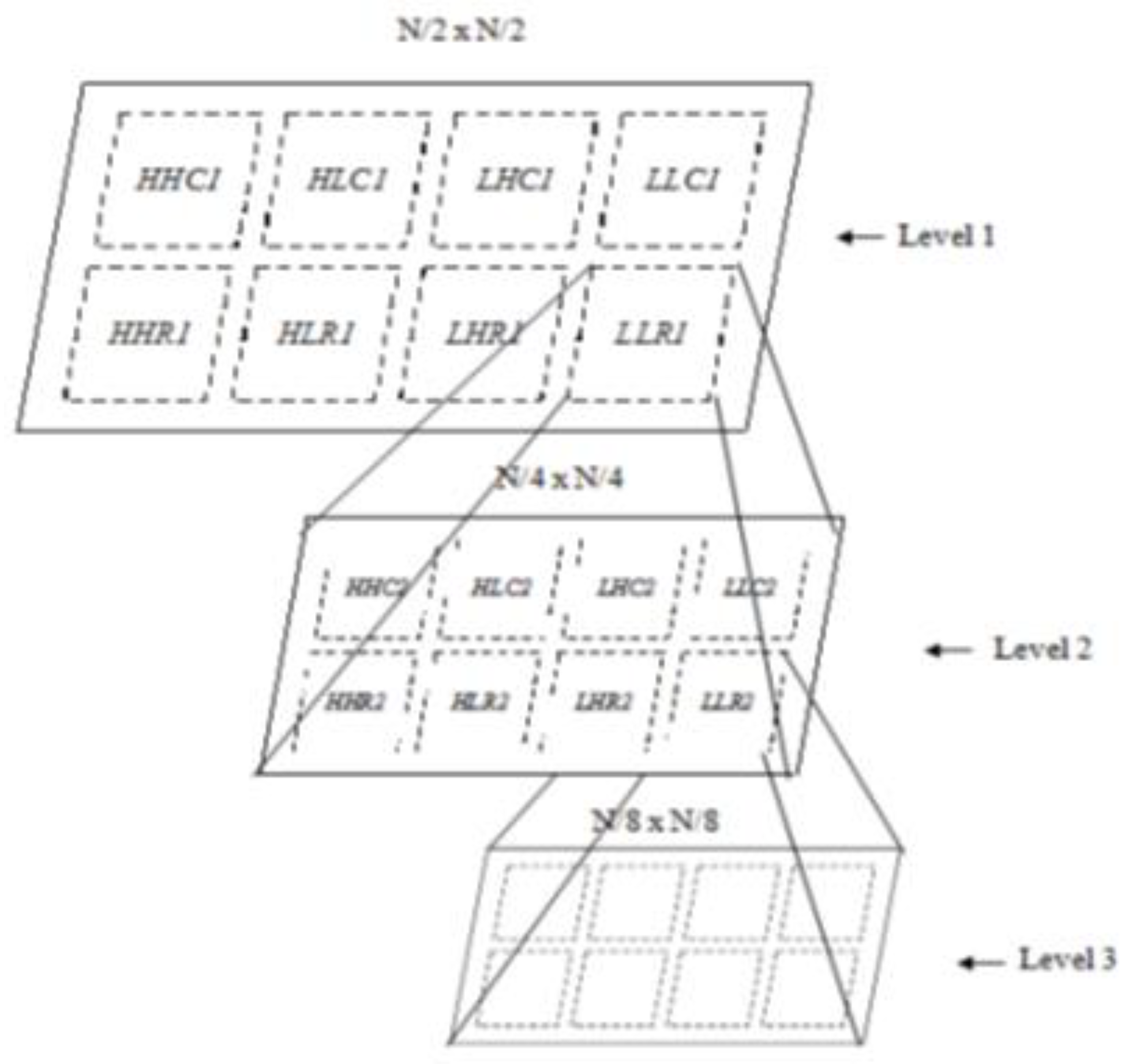
2.3.1. Frequency Domain Transformation
2.3.2. Optimizing the Embedding Process
2.3.3. Insertion in the Least Significant Bit (LSB)
2.3.4. Watermarking Evaluation
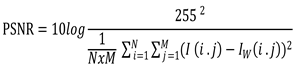 (5)
(5)
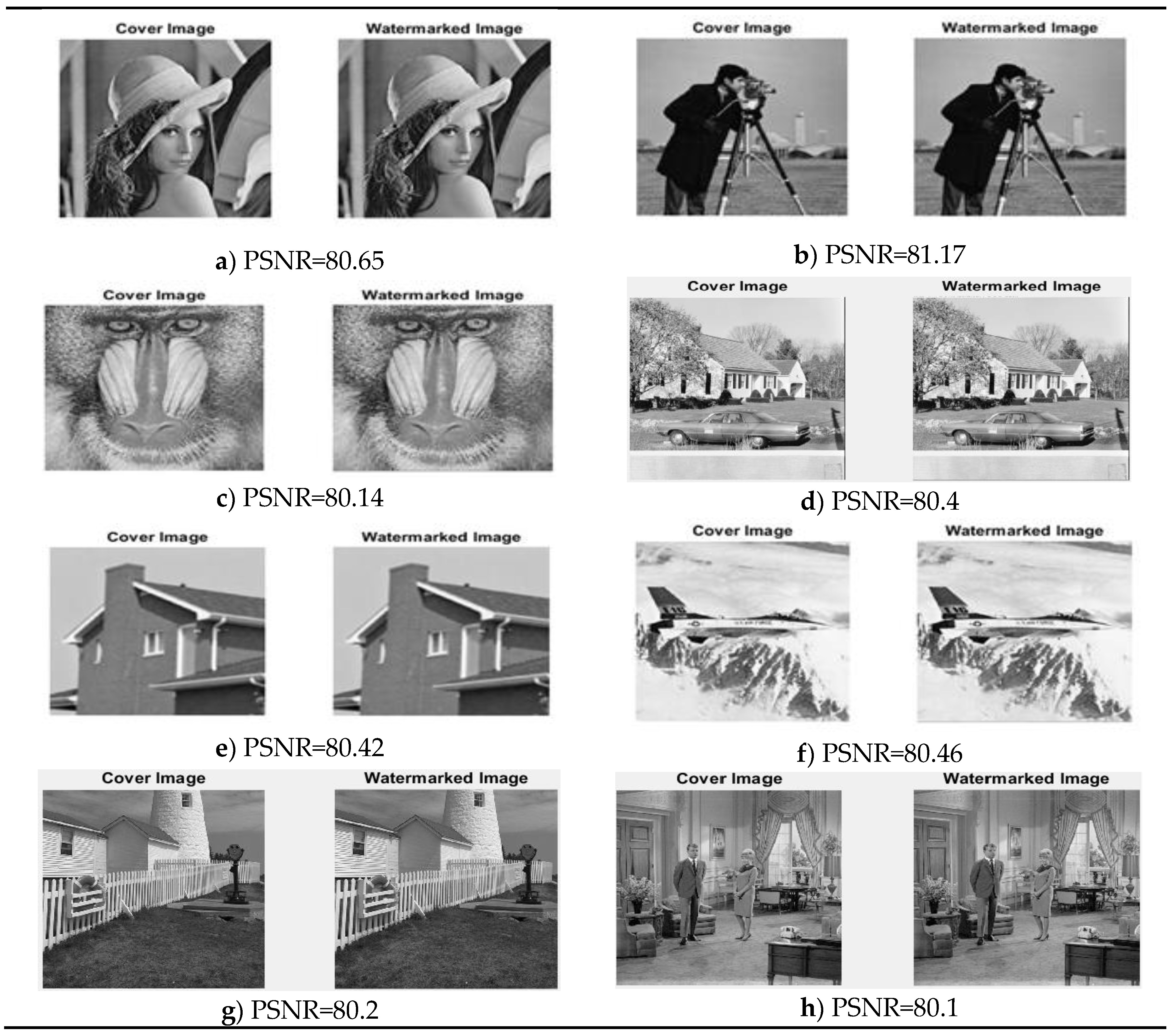
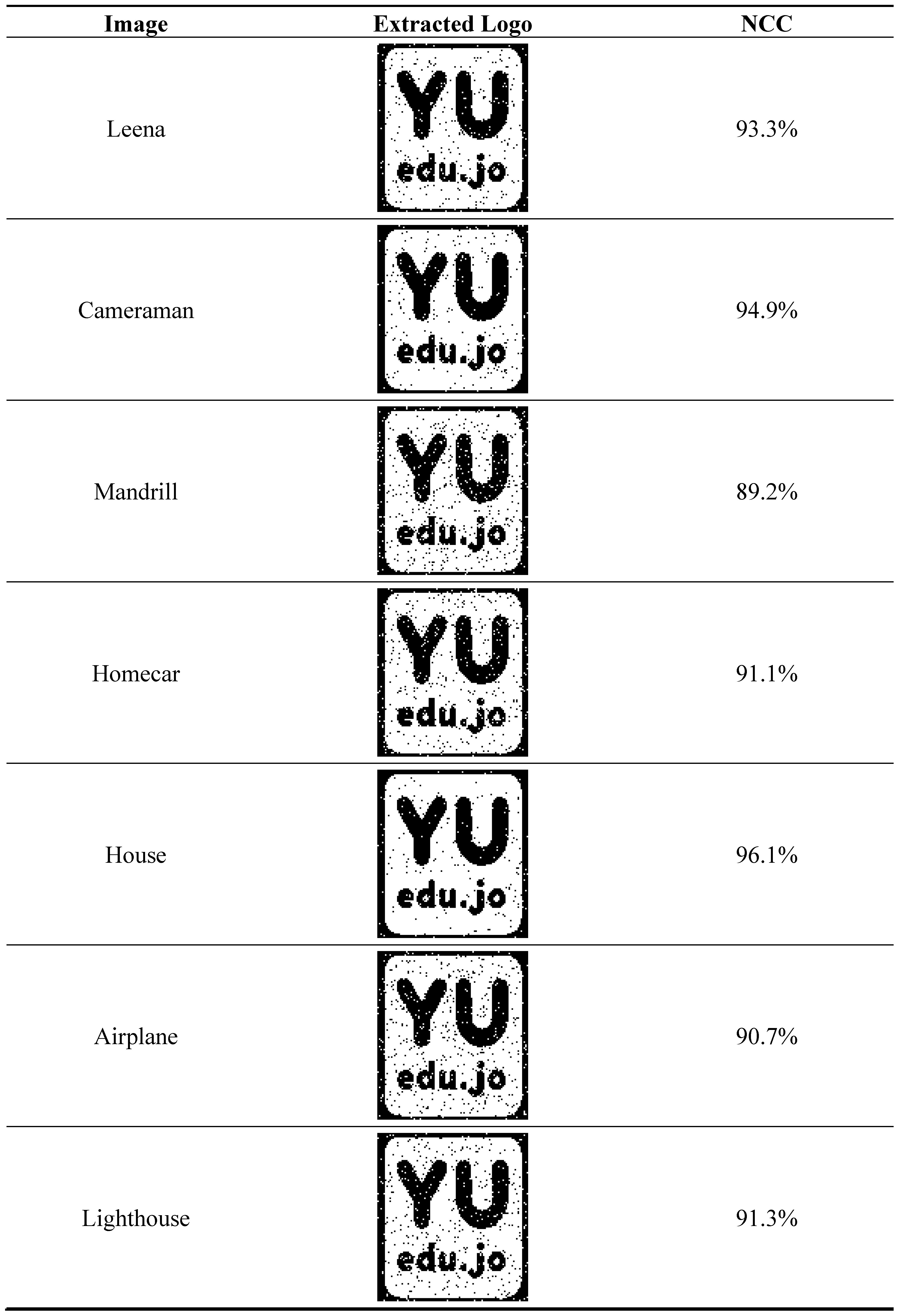
3. Results
4. Discussion and Conclusion
References
- S. E. Siwek, “The true cost of sound recording piracy to the US economy,” 2007, Institute for Policy Innovation Lewisville, TX.
- M. Rizzi, M. D’Aloia, and A. Longo, “Digital watermarking for healthcare: a survey of ECG watermarking methods in telemedicine,” International Journal of Computational Science and Engineering, vol. 23, no. 3, pp. 235–249, 2020.
- R. Kumar, P. K. Singh, and J. Yadav, “Digital image watermarking technique based on adaptive median filter and HL sub-band of two-stage DWT,” International Journal of Computer Aided Engineering and Technology, vol. 18, no. 4, pp. 290–310, 2023.
- M. Begum and M. S. Uddin, “Digital image watermarking techniques: a review,” Information, vol. 11, no. 2, p. 110, 2020.
- P. Garg and R. R. Kishore, “Performance comparison of various watermarking techniques,” Multimed Tools Appl, vol. 79, no. 35, pp. 25921–25967, 2020.
- D. R. I. M. Setiadi, “PSNR vs SSIM: imperceptibility quality assessment for image steganography,” Multimed Tools Appl, vol. 80, no. 6, pp. 8423–8444, 2021.
- S. Rustad, P. N. Andono, G. F. Shidik, and others, “Digital image steganography survey and investigation (goal, assessment, method, development, and dataset),” Signal Processing, vol. 206, p. 108908, 2023.
- O. Evsutin and K. Dzhanashia, “Watermarking schemes for digital images: Robustness overview,” Signal Process Image Commun, vol. 100, p. 116523, 2022.
- Z. Yuan, Q. Su, D. Liu, and X. Zhang, “A blind image watermarking scheme combining spatial domain and frequency domain,” Vis Comput, vol. 37, pp. 1867–1881, 2021.
- P. Garg and R. R. Kishore, “Optimized color image watermarking through watermark strength optimization using particle swarm optimization technique,” Journal of Information and Optimization Sciences, vol. 41, no. 6, pp. 1499–1512, 2020.
- A. Husain, A. D. Mishra, and S. K. Jena, “A robust approach for digital watermarking of satellite imagery dataset,” International Journal of Swarm Intelligence, vol. 7, no. 1, pp. 82–93, 2022.
- S. A. Barlaskar, S. V. Singh, K. Anish Monsley, and R. H. Laskar, “Genetic algorithm based optimized watermarking technique using hybrid DCNN-SVR and statistical approach for watermark extraction,” Multimed Tools Appl, vol. 81, no. 5, pp. 7461–7500, 2022.
- T. Zhu, W. Qu, and W. Cao, “An optimized image watermarking algorithm based on SVD and IWT,” J Supercomput, vol. 78, no. 1, pp. 222–237, 2022.
- T. Huang, J. Xu, Y. Yang, and B. Han, “Robust zero-watermarking algorithm for medical images using double-tree complex wavelet transform and Hessenberg decomposition,” Mathematics, vol. 10, no. 7, p. 1154, 2022.
- N. Nouioua, A. Seddiki, and A. Ghaz, “Blind Digital Watermarking Framework Based on DTCWT and NSCT for Telemedicine Application.,” Traitement du Signal, vol. 37, no. 6, pp. 955–964, 2020.
- K. Balasamy and S. Suganyadevi, “A fuzzy based ROI selection for encryption and watermarking in medical image using DWT and SVD,” Multimed Tools Appl, vol. 80, no. 5, pp. 7167–7186, 2021.
- J.-X. Liu, X. Wen, L.-M. Yuan, and H.-X. Xu, “A robust approach of watermarking in contourlet domain based on probabilistic neural network,” Multimed Tools Appl, vol. 76, pp. 24009–24026, 2017.
- I. Hamamoto and M. Kawamura, “Digital watermarking method by encoder using neural network,” IEICE Technical Report; IEICE Tech. Rep., vol. 117, no. 282, pp. 17–22, 2017.
- W. Ding, Y. Ming, Z. Cao, and C.-T. Lin, “A generalized deep neural network approach for digital watermarking analysis,” IEEE Trans Emerg Top Comput Intell, vol. 6, no. 3, pp. 613–627, 2021.
- P. Kumsawat, K. Attakitmongcol, and A. Srikaew, “A new approach for optimization in image watermarking by using genetic algorithms,” IEEE Transactions on Signal Processing, vol. 53, no. 12, pp. 4707–4719, 2005.
- Q. Wu, A. Qu, D. Huang, and L. Ma, “Robust and blind audio watermarking scheme based on genetic algorithm in dual transform domain,” Math Probl Eng, vol. 2021, no. 1, p. 3378683, 2021.
- R. Thanki, “Genetic algorithm-based intelligent watermarking for security of medical images in telemedicine applications,” in Intelligent Data Security Solutions for e-Health Applications, Elsevier, 2020, pp. 185–204.
- Laxmanika and P., K. Singh, “Robust and imperceptible image watermarking technique based on SVD, DCT, BEMD and PSO in wavelet domain,” Multimed Tools Appl, vol. 81, no. 16, pp. 22001–22026, 2022.
- D. Awasthi and V. K. Srivastava, “Performance enhancement of SVD based dual image watermarking in wavelet domain using PSO and JAYA optimization and their comparison under hybrid attacks,” Multimed Tools Appl, vol. 82, no. 23, pp. 35685–35717, 2023.
- S. Sharma, H. Sharma, and J. B. Sharma, “Artificial intelligence based watermarking in hybrid DDS domain for security of colour images,” International Journal of Intelligent Engineering Informatics, vol. 8, no. 4, pp. 331–345, 2020.
- P. Garg and R. R. Kishore, “An efficient and secured blind image watermarking using ABC optimization in DWT and DCT domain,” Multimed Tools Appl, vol. 81, no. 26, pp. 36947–36964, 2022.
- A. Pourhadi and H. Mahdavi-Nasab, “A robust digital image watermarking scheme based on bat algorithm optimization and SURF detector in SWT domain,” Multimed Tools Appl, vol. 79, no. 29, pp. 21653–21677, 2020.
- M. Gupta and M. Saraswat, “Grey wolf optimisation-based colour image watermarking,” World Review of Entrepreneurship, Management and Sustainable Development, vol. 16, no. 6, pp. 648–664, 2020.
- I. W. Selesnick, R. G. Baraniuk, and N. C. Kingsbury, “The dual-tree complex wavelet transform,” IEEE Signal Process Mag, vol. 22, no. 6, pp. 123–151, 2005.
- D. Wang, D. Tan, and L. Liu, “Particle swarm optimization algorithm: an overview,” Soft comput, vol. 22, no. 2, pp. 387–408, 2018.
- M.Anitha and M. Senbagavalli, “Dynamic Mobile Cloud Eco System Security - A Review,” International Journal of Data Informatics and Intelligent Computing, vol. 2, no. 1, pp. 62–69, Mar. 2023. [CrossRef]
- Ö. Y.-C. O. R. Review and undefined 2020, “Robust optimization for U-shaped assembly line worker assignment and balancing problem with uncertain task times,” hrcak.srce.hrÖF YılmazCroatian Operational Research Review, 2020•hrcak.srce.hr, vol. 11, pp. 229–239. 2020. [CrossRef]
- T. C. Phan, H. C. T. C. Phan, H. C. Tran, T. Chi, P. Quang, T. Teacher, and T. College, “Consideration of Data Security and Privacy Using Machine Learning Techniques,” International Journal of Data Informatics and Intelligent Computing, vol. 2, no. 4, pp. 20–32, Dec. 2023. [Google Scholar] [CrossRef]
- U. D. Maiwada, K. U. Danyaro, A. B. Sarlan, and A. A. Aliyu, “Dynamic Handover Optimization Protocol to enhance energy efficiency within the A-LTE 5G network’s two-tier architecture,” International Journal of Data Informatics and Intelligent Computing, vol. 3, no. 3, pp. 8–15, Aug. 2024. [CrossRef]
- S. Chaturvedi, “IoT-Based Secure Healthcare Framework Using Blockchain Technology with A Novel Simplified Swarm-Optimized Bayesian Normalized Neural Networks,” International Journal of Data Informatics and Intelligent Computing, vol. 2, no. 2, pp. 63–71, Jun. 2023. [CrossRef]

 |
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





