Submitted:
02 December 2024
Posted:
04 December 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Human Centric Risk Management (HRM) Objectives and Main Principles
1.2. HRM Tools for Estimating Technical Risks
- Specific knowledge of the company's cybersecurity;
- The methodologies employed within the company;
- The distribution of administrative fees on systems;
- The information segmentation policy;
- Authentication policies for accessing corporate systems;
- Previous assessments conducted.
1.3. HRM Socio-Psychological Instruments for Estimating Social Risks
- Diversity of Participants: These workshops prioritise the inclusion of a diverse range of ICT users, such as organisational insiders (e.g., CISOs, risk managers, incident handlers, defenders, administrators, and general employees), suppliers or supply chain partners, and third parties (e.g., suppliers, auditors, external penetration testers). This diversity is crucial for capturing a wide array of perspectives and experiences, which enriches the security discourse [18];
- Collaboration: Participants are encouraged to collaborate in a structured setting, facilitated by experienced leaders. This approach mirrors effective teamwork strategies that are essential for problem-solving and innovation in cybersecurity [19];
- Interactive Activities: Employing methods such as brainstorming sessions, design thinking exercises, and prototyping fosters a creative and engaging environment. These activities are foundational to generating practical and innovative solutions [20];
- Risk Treatment Generation and Refinement: The workshops focus on co-developing a comprehensive set of social and technical measures that ICT users embrace and comprehend, which are refined through collaboration into viable security controls. This process aligns with best practices in risk management [21].
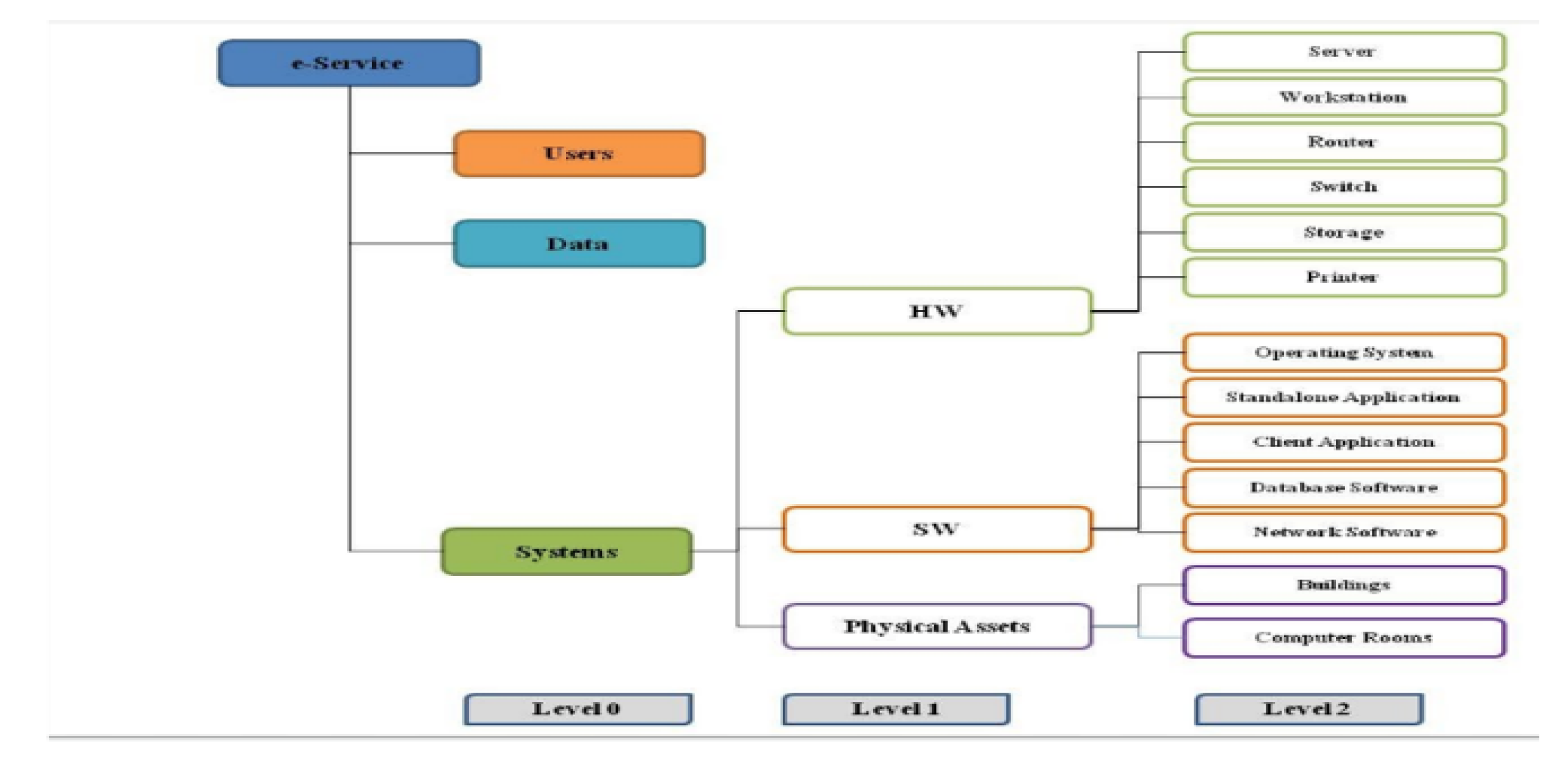
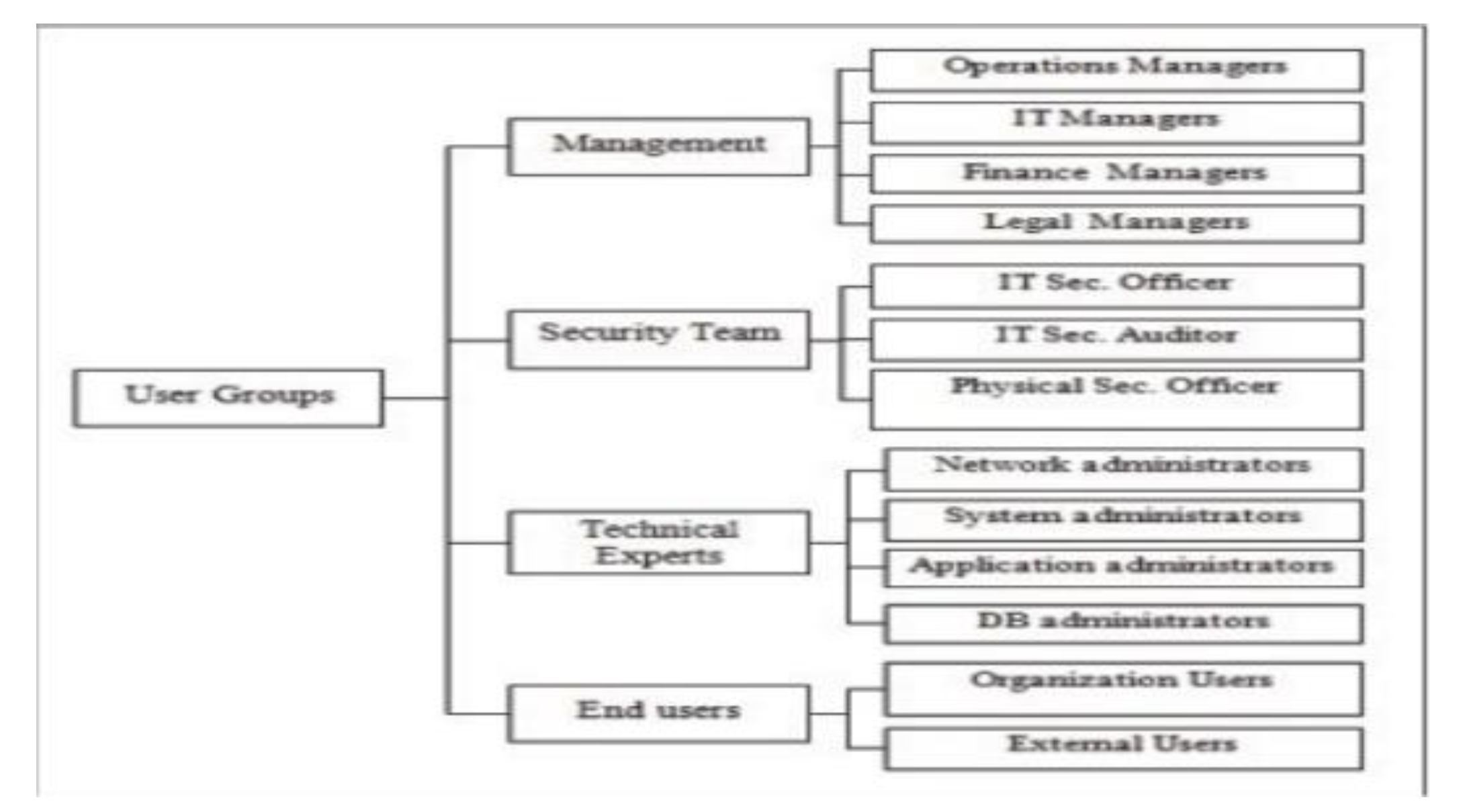
2. User Profiles
2.1. ICT User Profile (UP)
2.2. Adversary Profile (AP)
2.3. Measuring Profiles
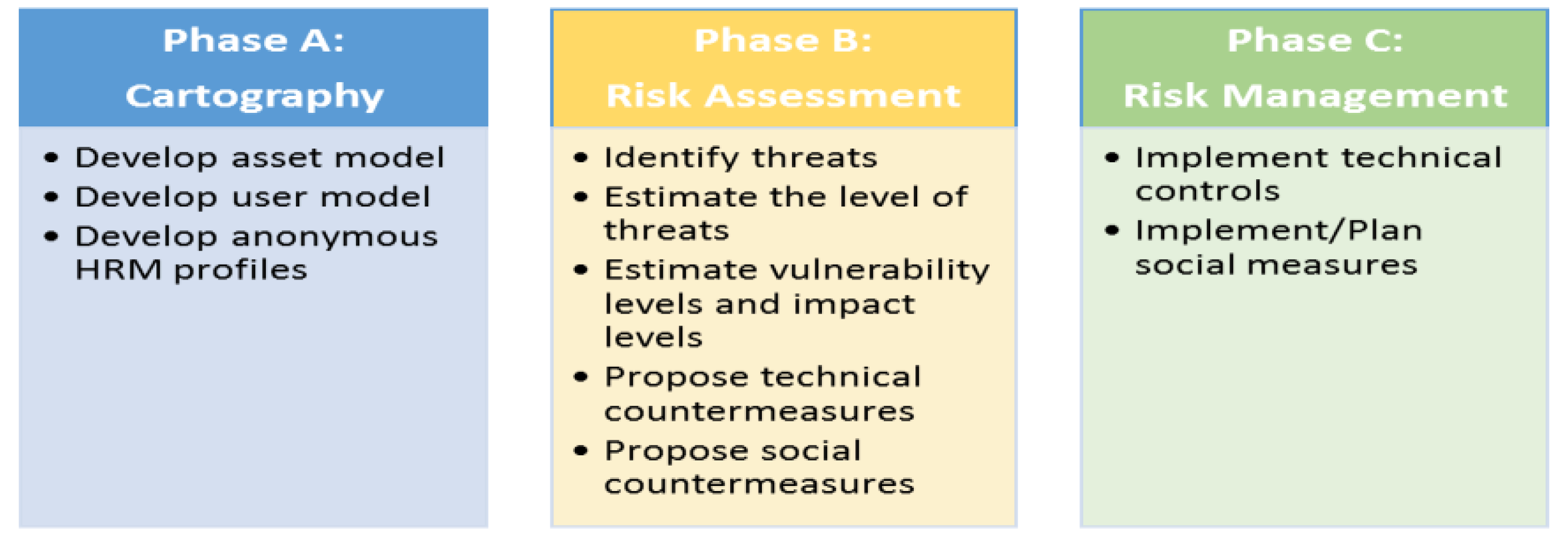
3. Phases of the HRM Methodology and Implementation
3.2. Phase B: Risk Assessment
3.3. Phase C: Risk Management (Treatment)
4. User Profiles
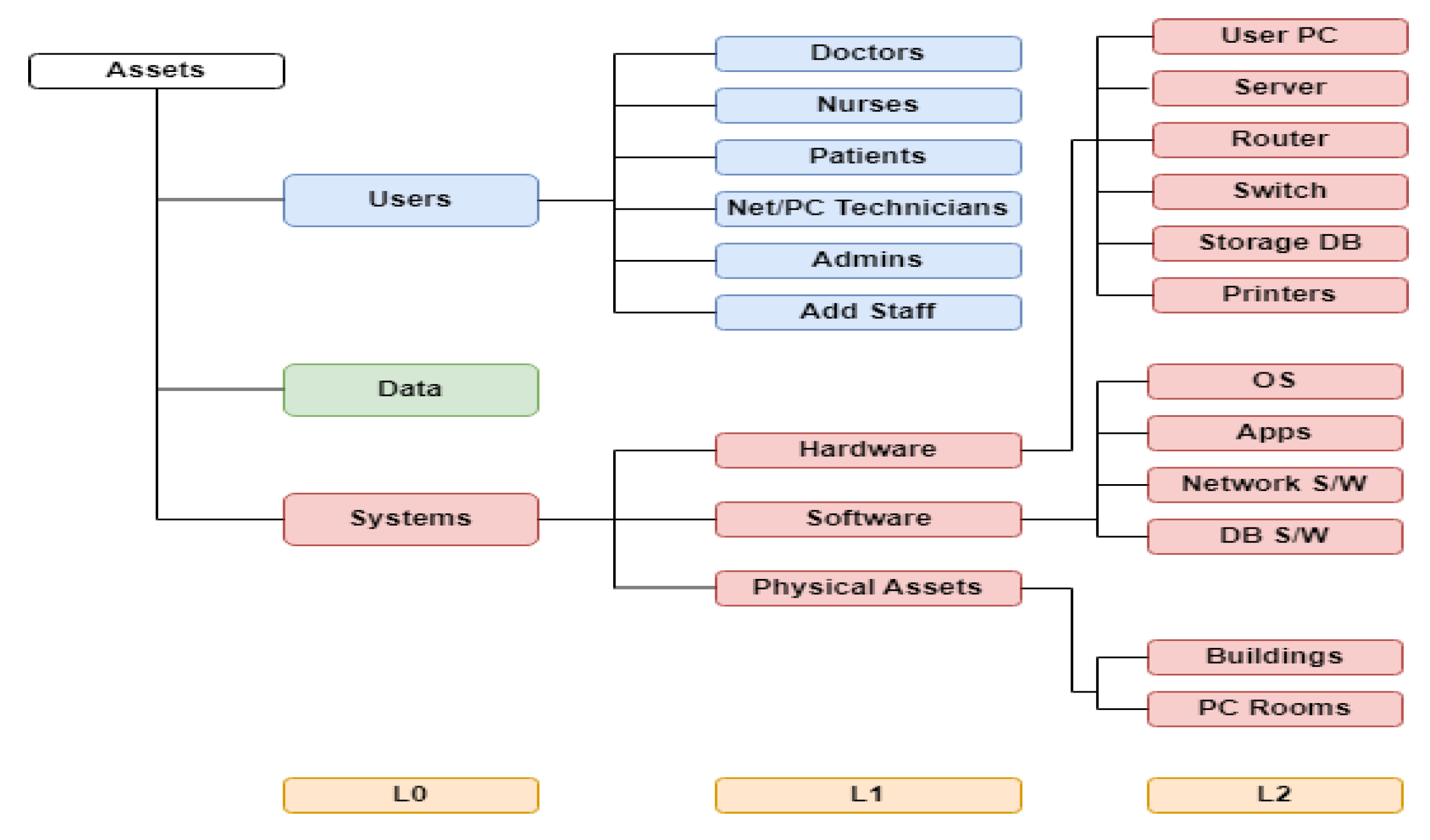
4.1. Phase A (Cartography)
4.2. Phase B: Risk Assessment
- Technical Controls: Advanced access control, data encryption, network and endpoint security;
- Administrative Controls: Policy development, access management, employee training, and security audits;
- Physical Controls: Access control systems, surveillance, alarms, and restricted-access storage;
- Social Controls: Enhance software and IT skills based on personality traits, social factors, and technical skills identified earlier.
5. Conclusions
Acknowledgments
References
- ISO/IEC 27001:2005. Information Technology - Security Techniques – Information Security Management Systems – Requirements. Known as ISO 27001.
- ISO/IEC – Global standards, https://www.iso.org/home.html, last assessed 2024/9/5.
- ISO/IEC 27002:2005. Information Technology - Security Techniques - Code of Practice for Information Security Management. Known as ISO 27002.
- NIST cyber hygiene guidelines, https://www.nist.gov/blogs/taking-measure/stay-safe-and-secure-online-during-cybersecurity-awareness-month-and-all-year, last accessed 2024/9/5.
- Kioskli K.; Polemi N. Estimating attackers’ profiles results in more realistic vulnerability severity scores. In proceedings of the 13th International Conference on Applied Human factors and Ergonomics (AHFE2022), July 24-July 28, 2022, New York, New York, USA, 2022, 53 (1), 138-150. Springer, Elsevier, CRC.
- Kioskli, K.; Fotis, T.; Nifakos, S.; Mouratidis, H. The Importance of conceptualising the human-centric approach in maintaining and promoting cybersecurity-hygiene in healthcare 4.0. Applied Sciences, Special Issue eHealth Innovative Approaches and Applications 2023, 13, 1–16. [Google Scholar] [CrossRef]
- Alwaheidi, M.; Islam, S.; Papastergiou, S.; Kioskli, K. Integrating Human Factors into Data-driven Threat Management for Overall Security Enhancement. In: Abbas Moallem (eds) Human Factors in Cybersecurity. AHFE (2024) International Conference. AHFE Open Access, 2024, vol 127. AHFE International,, USA. [CrossRef]
- ENISA risk management toolbox. Available online: https://www.enisa.europa.eu/publications/interoperable-eu-risk-management-toolbox, last accessed 2024/9/5.
- OWASP risk assessment calculator. Available online: https://owasp-risk-rating.com/, last accessed 2024/9/5.
- OWASP Threat Modeling Process. Available online: https://owasp.org/www-community/Threat_Modeling_Process, last accessed 2024/9/5.
- MISP Project. Available online: https://www.misp-project.org/, last assessed 2024/9/5.
- Cyberwatching. Available online: The European watch on Cybersecurity & Privacy, https://cyberrisk.cyberwatching.eu/Pages/Home.aspx, last accessed 2024/9/5.
- Egelman, S.; Peer, E. The Security Behaviour Intentions scale. Frontiers, 2015.
- Nobles, C. : Understanding the Human Factor of Cyber Security. IEEE IT Professional 2018, 20, 7–15. [Google Scholar] [CrossRef]
- Fogg B. J. A behavior model for persuasive design. In Proceedings of the 4th international Conference on Persuasive Technology, 2009, pp. 1–7.
- Kioskli, K.; Polemi, N. A psychosocial approach to cyber threat intelligence. International Journal of Chaotic Computing 2020, 7, 159–165. [Google Scholar] [CrossRef]
- Williams, H. The impact of collective intelligence on cybersecurity. Cyber Psychology 2020, 7, 111–126. [Google Scholar]
- Schneier, B. Liars and Outliers: Enabling the Trust That Society Needs to Thrive. Wiley, 2012.
- West D., M. Digital Government: Technology and Public Sector Performance. Princeton University Press, 2012.
- Brown, T. Change by Design: How Design Thinking Transforms Organizations and Inspires Innovation. HarperBusiness, 2009.
- Stoneburner, G.; Goguen, A.; Feringa, A. Risk Management Guide for Information Technology Systems (NIST Special Publication 800-30). National Institute of Standards and Technology, 2022.
- Ramaswamy, V.; Ozcan, K. What is co-creation? An interactional creation framework and its implications for value creation. Journal of Business Research 2018, 84, 196–205. [Google Scholar] [CrossRef]
- Kioskli, K.; Polemi, N. Psychosocial approach to cyber threat intelligence. International Journal of Chaotic Computing 2020, 7, 159–165. [Google Scholar] [CrossRef]
- ENISA ECSF. Available online: https://www.enisa.europa.eu/topics/education/european-cybersecurity-skills-framework, last accessed 2024/9/4.
- StaySafeOnline guidelines. Available online: https://staysafeonline.org/resources/online-safety-basics/, last accessed 2024/9/5.
- Smith, J.; Doe, A.; James, S. The efficacy of questionnaires in the assessment of secure behaviors in IT users. Journal of Cybersecurity Research 2019, 12, 45–59. [Google Scholar]
- Kioskli K.; Polemi N. Measuring psychosocial and behavioural factors improves ttack potential estimates. In Proceedings of the 15th International Conference for Internet Technology and Secured Transactions, 2020, 216–219.
- Kioskli, K.; Polemi, N. A socio-technical approach to cyber risk assessment. International Journal of Electrical and Computer Engineering 2020, 14, 305–309. [Google Scholar]
- Mattelmäki, T.; Vaajakallio, K.; Koskinen, I. What happened to empathic design? Design Issues 2014, 30, 67–77. [Google Scholar] [CrossRef]
| HRM ICT users’ profiles (HRM-UP) | |
|---|---|
| Personality Traits | |
| Vigilance | Consistently remains alert and attentive to potential security threats, and is proactive in identifying and addressing suspicious activities. |
| Responsibility, Curiosity | Takes full ownership of their role, with an innate curiosity that drives them to deepen their understanding of cybersecurity threats and vulnerabilities. |
| Adaptable-Openness to experiences | Displays flexibility and openness to new security technologies, strategies, and approaches that enhance their security posture. Possesses a blend of intellect and creativity, demonstrates originality, and shows a keen scientific interest alongside a spirit of adventurousness. |
| Resilient | Has the capacity to cope with stress, setbacks, and failures, demonstrating resilience by quickly bouncing back and steadfastly maintaining a strong focus on achieving security objectives. |
| Social Traits | |
| Social exposure | Adapts to conventional social norms with ease, excelling in forging strong bonds with each co-worker. Collaborates effectively with colleagues, security teams, and external partners to tackle security challenges, sharing information and insights for collective benefit. |
| Conventional relationships | Effortlessly establishes professional virtual relationships, fostering collaborations and creating synergies. |
| Ethical | Individuals with integrity prioritise honesty, transparency, and respect, steadfastly adhering to ethical principles and professional codes of conduct. |
| Personality Traits | Description & Examples |
|---|---|
| Extraversion | Gregariousness (e.g., Social engagement in attackers’ groups); Assertiveness/Outspokenness (e.g., Leadership skills); Activity/Energy level (e.g., Enjoys a busy life); Positive Emotions/Mood (e.g., Happiness) |
| Conscientiousness | Orderliness/Neatness (e.g., Well-organized) Striving/Perseverance (e.g., Aims to achieve excellence) Self-Discipline (e.g., Persistent engagement to goals) Dutifulness/Carefulness (e.g., Strong sense of duty) Self-Efficacy (e.g., Confidence to achieve goals) |
| Openness to experiences | Intellect/Creativity Imaginative (e.g., Intellectual style) Scientifically Interested/Originality (e.g., Evidence-based) Adventurousness (e.g., Experiences of different things) |
| Social - Behavioural Traits | Description & Examples |
| Selected social exposure | Difficult to adapt to conventional social norms (e.g., Events) Easy to build virtual anonymous, professional relationships (e.g., Using anonymous identity has contacts with other attackers in the Deep Web) Easy to build strong e-bonds in hacking communities (e.g., These communities are closed to the public) |
| Not conventional relationships | Difficult to build physical relationships or contacts Easy to build professional (with other attackers) virtual, anonymous relationships under their moral code (us versus them approach) |
| Not talkative | Difficult to initiate small casual talks or social talks Difficult to express him/herself |
| Manipulative | Easy manipulating people via electronic means (e.g., phishing) |
| Levels | Description | Semi-Quantitative Values | UP/AP score of profile | Indicative Social Measures needed | |
|---|---|---|---|---|---|
| Very High (VH)-5 | Sophisticated | 96-100 | 10 | > 96% of each of the traits in each category | social and technical threat intelligence updates, ethical training, advance cybersecurity exercises |
| High (H)-4 | Experienced | 80-95 | 8 | > 80% | ethical training , cybersecurity exercises, social and technical threat intelligence updates, ethical training |
| Medium (M)-3 | Moderate | 21-79 | 5 | > 21% | secure behaviour intervention, training in operational cybersecurity, cybersecurity exercises |
| Basic (B)-2 | Basic | 5-20 | 2 | > 5% | awareness , secure behaviour interventions , training in operational cybersecurity exercises |
| Low (I) -1 | Insufficient | 1-4 | 0 | < 5% | awareness , secure behaviour interventions , training in basic concepts, basic cyber exercises |
| General Information | Technical Specifications | Location and Owner | Network Configuration (for Servers) | Implementation of Controls -History of Updates | |
|---|---|---|---|---|---|
| 1 | Asset ID: Unique identifier for each piece of equipment. | Processor: Type and speed of the processor. | Location: Physical location of the asset. | IP Address: Network IP address. | Controls Implemented |
| 2 | Asset Type: Differentiates between PCs and servers. | RAM: Amount of memory in GB. | Owner of Asset (Assigned to): Name of the employee responsible of the asset. | Role: Function or role of the server (e.g., file server, web server). | Update History of controls |
| 3 | Brand/Model: Specific model of the hardware. | Storage: Size and type of storage (e.g., SSD, HDD). | Owner/ User(s) of asset : interacting entity | - | Testing date of controls |
| 4 | Serial Number: Manufacturer's serial number. Date of purchase ….. |
Operating System: Installed operating system and version. | - | - | - |
| User ID: 001 | User ID: 002 | …. | |
|---|---|---|---|
| General Information | Name: Full name of the employee/ Role/ Location/Contact | … | - |
| System & Credential System Access | Privileges, List of systems the user has access to (e.g., CRM, ERP, Email), | … | - |
| Supervisor & Interrelations | Direct supervisor or manager Interactions with other users (model interaction) |
… | - |
| User ID: 001 | User ID: 002 | … | |
|---|---|---|---|
| General Information | Name: Full name of the employee/ Role/ Location/Contact | … | - |
| System & Credential System Access | Privileges, List of systems the user has access to (e.g., CRM, ERP, Email), | … | - |
| Supervisor & Interrelations | Direct supervisor or manager Interactions with other users (model interaction) |
… | - |
| UP score | See Table 3 above | ... | - |
| Social Measures Implemented/Required | See Table 3 above | …. | …. |
| General Information | Technical Specifications | Location and Owner | Network Configuration (for Servers) | Implementation of Controls -History of Updates |
|---|---|---|---|---|
| Asset ID: Unique identifier for each asset. | Software Suite for Patient Records, Network infrastructure etc. | Location: Physical location of the asset. | Wired and Wireless setup | Controls Implemented |
| Asset Type: Software or Hardware | Software suite for patients records / Server hardware for data storage | Owner of Asset (Assigned to): Name of the employee responsible of the asset. | Role: Function or role of the software or hardware | Update History of controls |
| Brand/Model: Specific model of the software or hardware. | Electronic Medical Records (EMR) System, Database Management Platform etc. | Owner/ User(s) of asset : Doctor, Nurse, admin etc | - | Testing date of controls |
| Serial Number: Manufacturer's serial number. Date of purchase ….. |
Software versions, Hardware specifications | - | - | - |
| User ID: 001-doctor1 | User ID: 002-nurse | …. | |
|---|---|---|---|
| General Information | Name: Full name of the employee/ Role/ Location/Contact | … | |
| System & Credential System Access | Privileges, List of systems the user has access to (e.g., CRM, ERP, Email), | ||
| Supervisor & Interrelations | Direct supervisor or manager Interactions with other users (model interaction) |
- | |
| UP score | Basic (B)-2 | ||
| Social Measures Implemented/Required | According to Table 3 the measures needed are: awareness , secure behaviour interventions , training in operational cybersecurity exercises |
| Threat | Category | Security Dimension | Action | Assets | Explanation |
|---|---|---|---|---|---|
| Hardware or Software failure | Industrial | Availability | Deliberate or Accidental | H/W devices and equipment – S/W and applications | Failures in the equipment (eg. user PC, server, router etc) and/or programs (eg. apps, OS etc.) |
| User errors | Errors and unintentional failures | Confidentiality, Integrity, Availability | Accidental | H/W devices and equipment – S/W and applications – Organisational infrastructure | Mistakes by persons when using the services, data, etc. For example making a mistake in saving data, or in a PC’s usage. |
| Threat of system / security administrator errors | Errors and unintentional failures | Confidentiality, Integrity, Availability | Accidental | H/W devices and equipment - S/W and applications- Organisational infrastructure | Mistakes by persons with responsibilities for installation and operation of the systems / system’s security. For example the PC technician can unintentionally cause the system failure of a user PC or server. |
| Destruction of information | Errors and unintentional failures | Availability | Accidental | All the categories of supporting assets | The accidental loss of the information due to a user’s (doctor or nurse) mistake. |
| S/W vulnerabilities | Errors and unintentional failures | Confidentiality, Integrity, Availability | Accidental | S/W and applications | Defects in the code that cause a defective operation without intention on the part of the user but with consequences to the data confidentiality, integrity, availability or to its capacity to operate. This can be detected in apps or OS for example. |
| Abuse of access privileges | Willful attacks | Confidentiality, Integrity, Availability | Deliberate | S/W and applications - Locations and Utilities - Organisational infrastructure | When users abuse their privilege level to carry out tasks that are not their responsibility, there are problems. For example a user might use a doctor’s account and delete patients’ data. |
| Misuse | Willful attacks | Confidentiality, Integrity, Availability | Deliberate | S/W and applications - Locations and Utilities - Organisational infrastructure | The use of system resources for unplanned purposes, typically of personal interest. For example a user connects an app or to a PC inside the HSMEs facility. |
| Threat | Skill level | Motive | Opportunity | Size |
|---|---|---|---|---|
| Unauthorised access | 6 | 9 | 4 | 9 |
| Threat | Ease of Discovery | Ease of Exploit | Awareness | Intrusion Detection |
|---|---|---|---|---|
| Unauthorised access | 7 | 9 | 6 | 3 |
| Threat | Loss of Confidentiality | Loss of Integrity | Loss of Availability | Loss of Accountability |
|---|---|---|---|---|
| Unauthorised access | 7 | 7 | 7 | 9 |
| Threat | Financial damage | Reputation damage | Non-complience | Privacy violation |
|---|---|---|---|---|
| Unauthorised access | 3 | 5 | 7 | 7 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




