Submitted:
17 November 2024
Posted:
19 November 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Related Work
3. Methdology
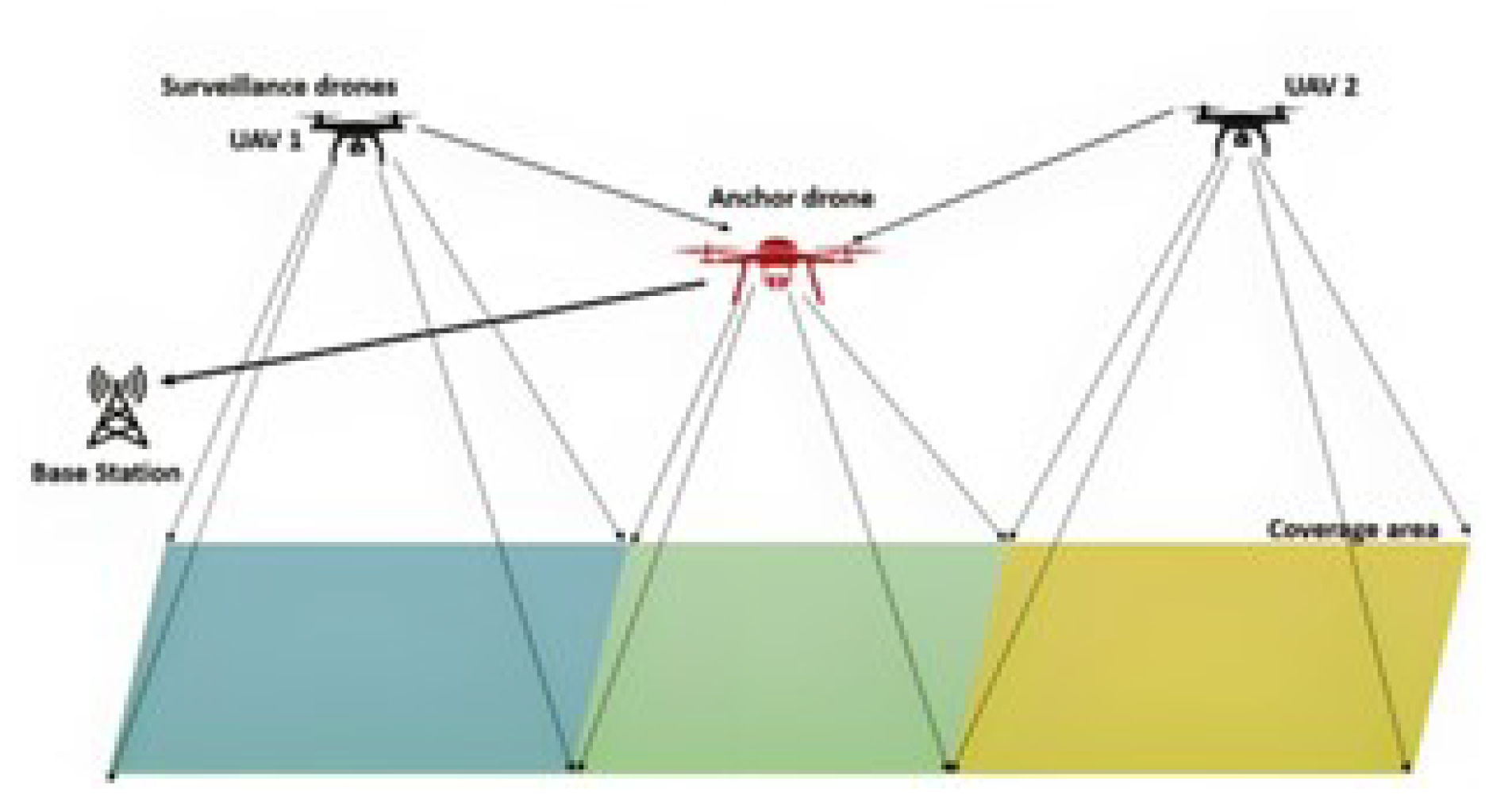
3.1. Algorithm for Effective UAV-based Network Surveillance
3.1.1. Log Distance Path-Loss
- = Transmitted power = ,
- = Transmitted gain = 10,
- = Receiver gain = 10,
- = Wavelength, where (with c being the speed of light and f the frequency),
- n = Path loss exponent for free space.
3.1.2. Uplink Path Loss
- = Path loss exponent,
- = Channel coefficient of the wireless channel between the transmitter (TX) and receiver (RX).
- = Large-scale path loss, which is defined as:
- g = Rayleigh fading,
- = Path loss gain,
- N = Power of Additive White Gaussian Noise (AWGN) at the receiver = .
3.1.3. Channel Capacity
- B = Bandwidth of the channel = 360 kHz.
3.1.4. Actual Channel Capacity and Transmission Time
- = Maximum channel capacity,
- = Remaining battery capacity,
- = Maximum battery capacity.
- = Amount of data to be transmitted,
- = Remaining channel capacity.
- 11.1 = Voltage of the battery (in Volts),
- 2200 = Battery capacity (in mAh),
- 3.6 = Conversion factor to Joules.
- = Previous battery level.
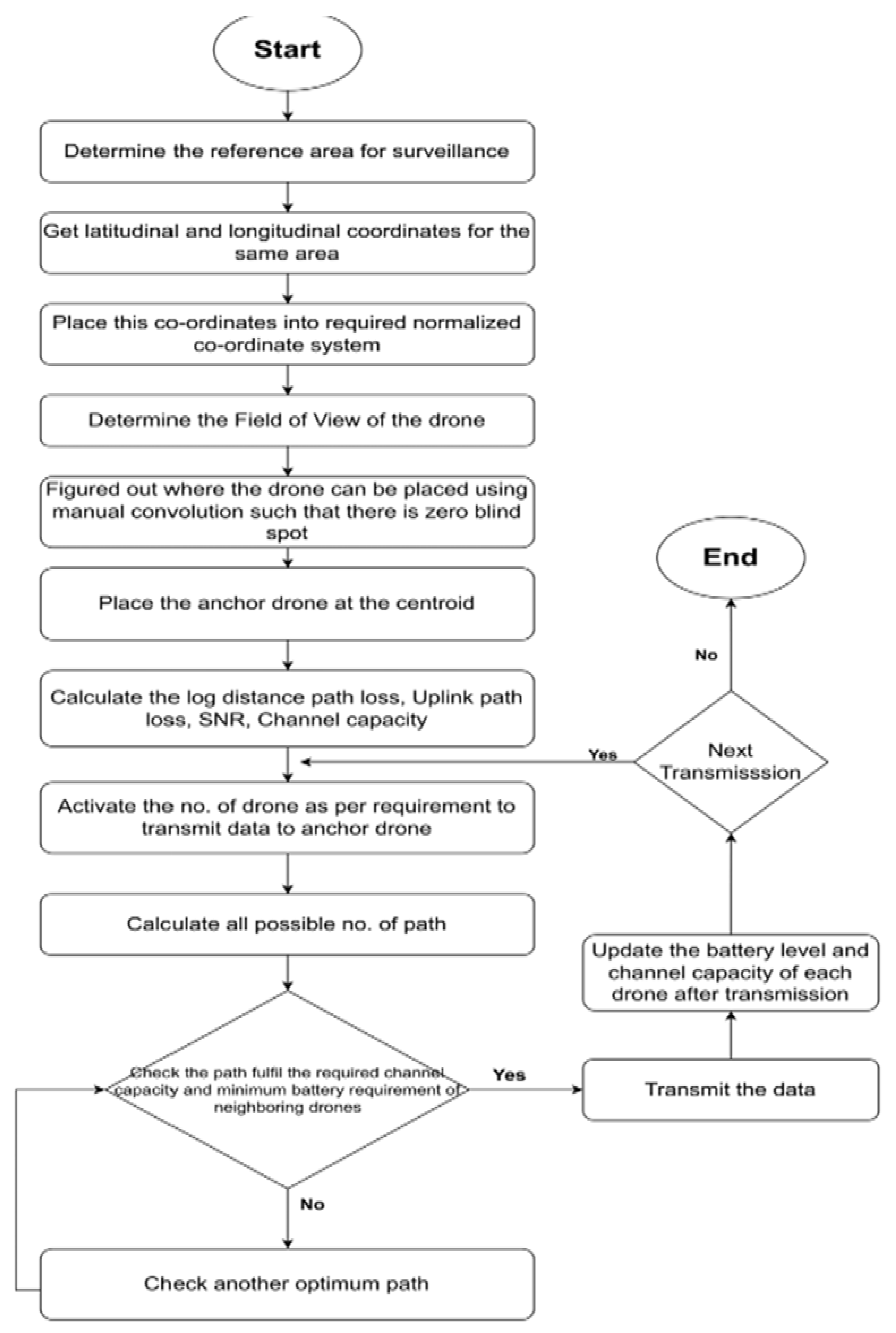
3.1.5. Algorithms
| Algorithm 1 Function for All Paths |
|
| Algorithm 2 Main Algorithm |
|
4. Implementation and Simulation of UAV Network
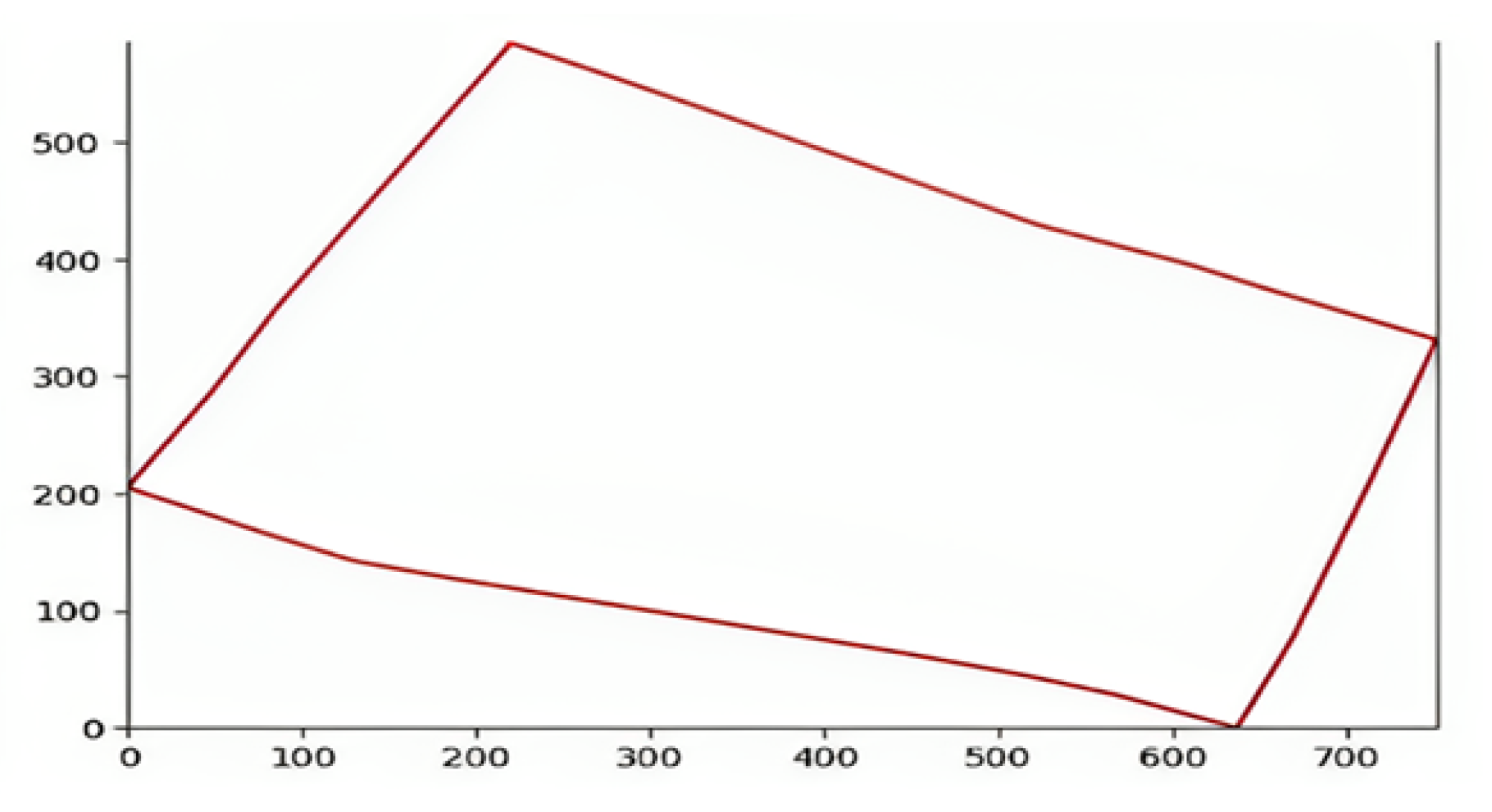
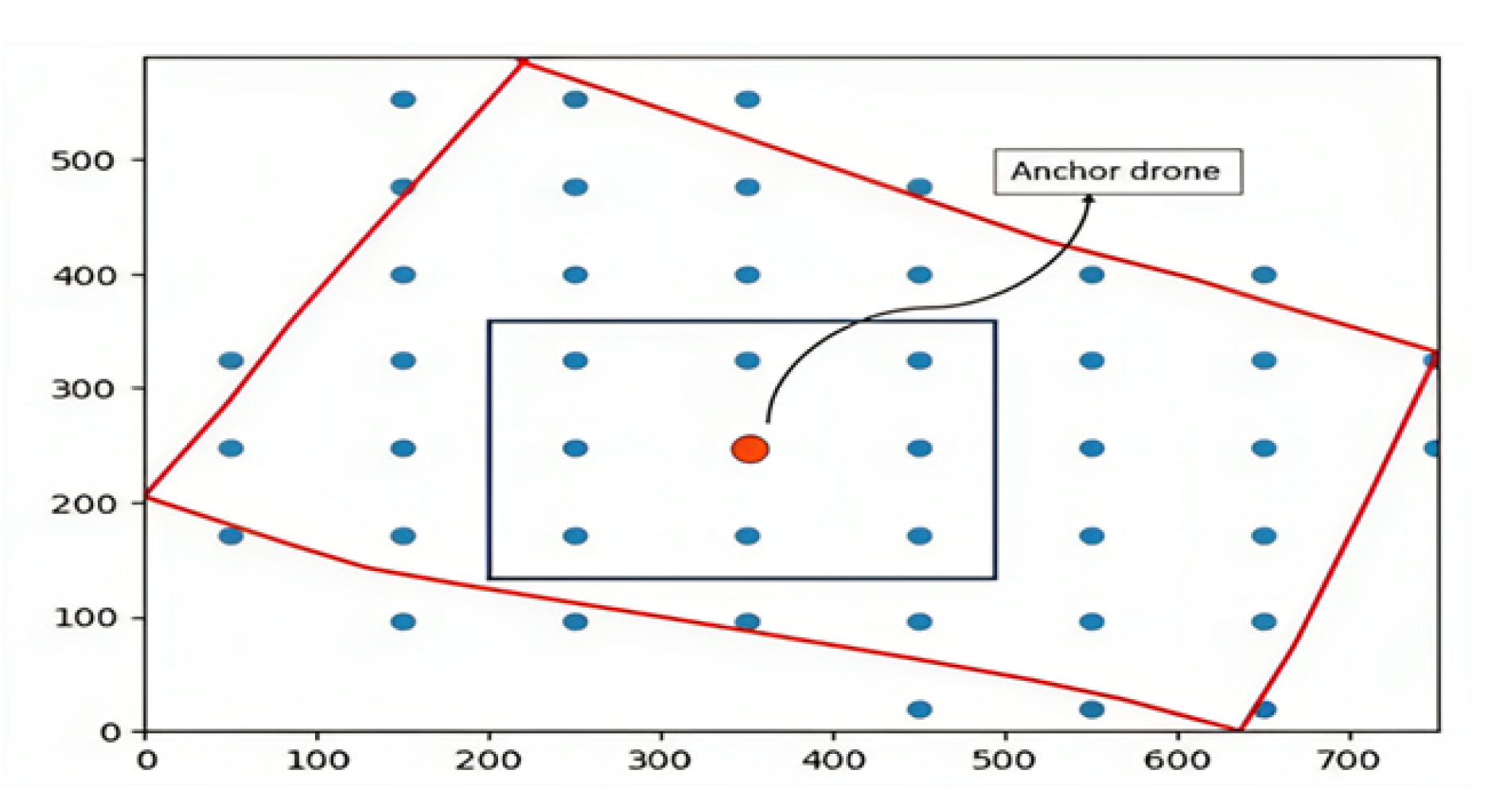
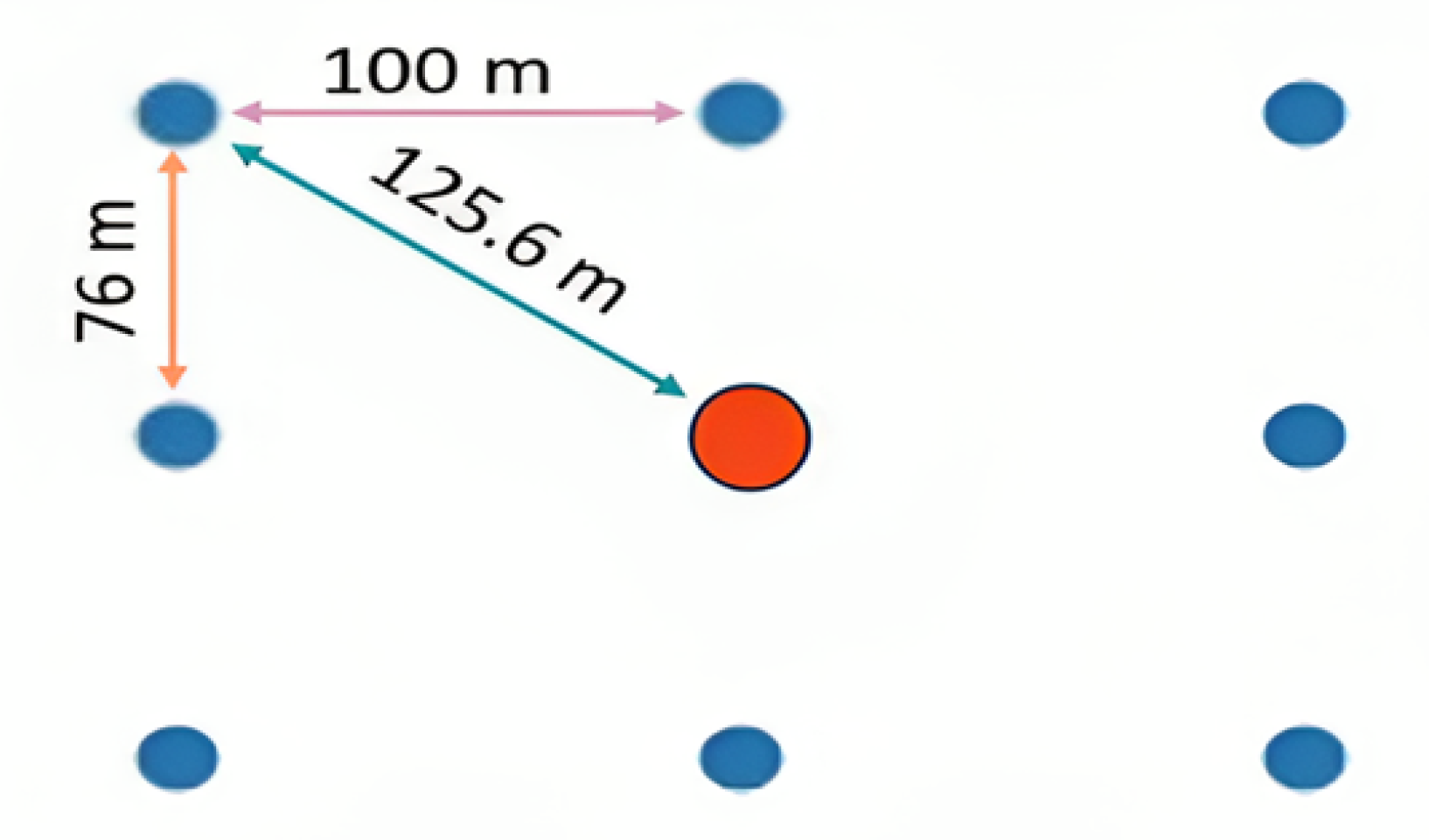
4.0.1. Determining the Shape of the Surveillance Area from Google Maps and Plot it
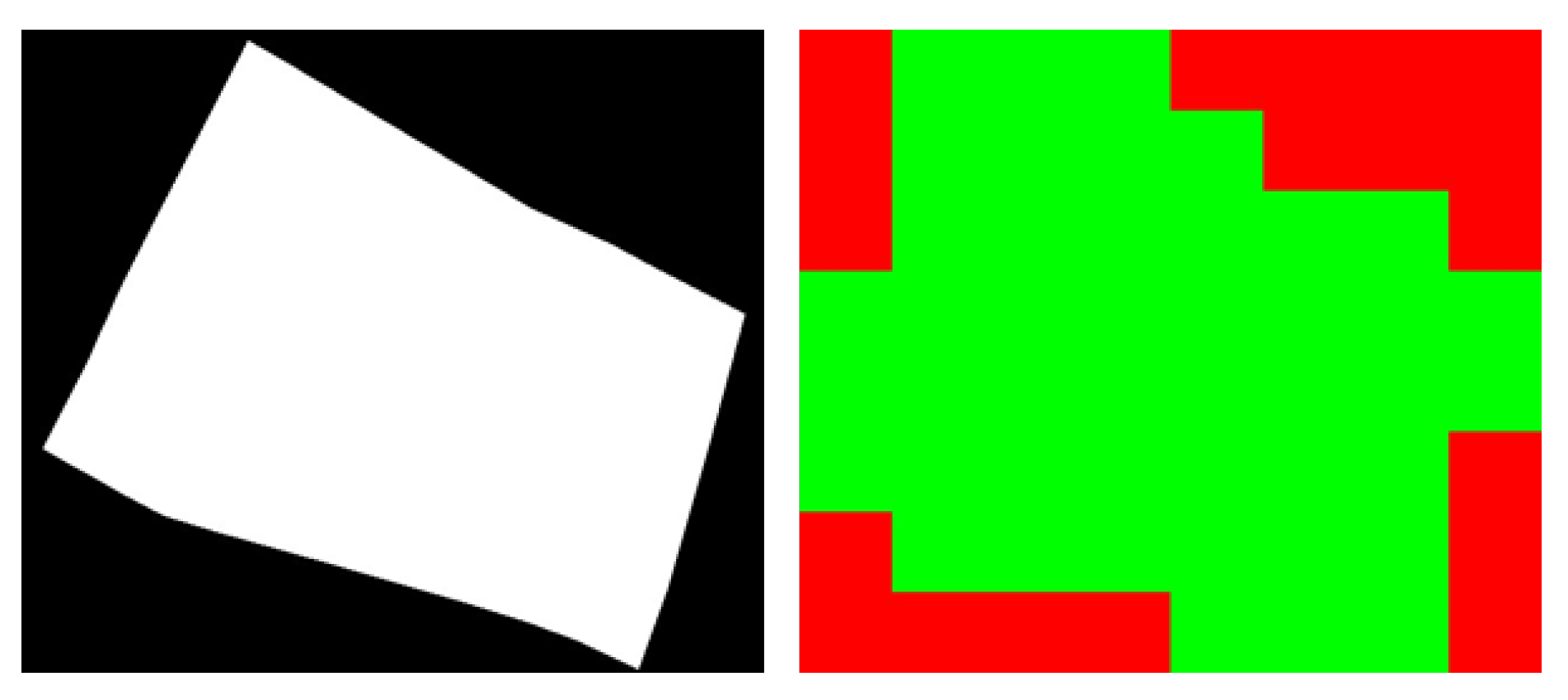
4.0.2. Image Processing
4.0.3. Drone Deployment
4.0.4. Path Planning
5. Result
6. Conclusions
7. Future Work
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Jain, A.P.; Joshi, S. UAV-Enabled D2D Vehicular Communication Network: Link Selection and Outage Analysis. In Proceedings of the 2024 IEEE 99th Vehicular Technology Conference (VTC2024-Spring), Singapore, 24-27 June 2024; pp. 1–5. [Google Scholar] [CrossRef]
- Li, Y.; Bi, Y.; Wang, J.; Li, Z.; Zhang, H.; Zhang, P. Unmanned Aerial Vehicle Assisted Communication: Applications, Challenges, and Future Outlook. Cluster Computing 2024. [CrossRef]
- Moghadam, M.N.; Taheri, H.; Karrari, M. Multi-Class Multipath Routing Protocol for Low Power Wireless Networks with Heuristic Optimal Load Distribution. Wireless Personal Communications 2014, 82, 861–881. [Google Scholar] [CrossRef]
- Singhal, C.; De, S.; Gupta, H.M. User Heterogeneity and Priority Adaptive Multimedia Broadcast over Wireless. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10-14 June 2014; pp. 1699–1704. [Google Scholar] [CrossRef]
- Nadeem, A.; Ullah, A.; Choi, W. Social-Aware Peer Selection for Energy Efficient D2D Communications in UAV-Assisted Networks: A Q-Learning Approach. IEEE Wireless Communications Letters 2024, 13, 1468–1472. [Google Scholar] [CrossRef]
- Kim, N.M.; Jeong, N.E.; Bang, N.Y.-C.; Hwang, N.S.; Kim, N.B. Multipath Energy-Aware Routing Protocol in Wireless Sensor Networks. In Proceedings of the 2008 5th International Conference on Networked Sensing Systems, Kanazawa, 17-19 June 2008; pp. 127–130. [Google Scholar] [CrossRef]
- Kumar, N.; Ghosh, M.; Singhal, C. UAV Network for Surveillance of Inaccessible Regions with Zero Blind Spots. In Proceedings of the IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, Canada, 6–9 July 2020; pp. 1213–1218. [Google Scholar] [CrossRef]
- Olsson, P.-M.; Kvarnstrom, J.; Doherty, P.; Burdakov, O.; Holmberg, K. Generating UAV Communication Networks for Monitoring and Surveillance. In Proceedings of the 2010 11th International Conference on Control Automation Robotics & Vision, Singapore, 07-10 December 2010. [Google Scholar] [CrossRef]
- Kwan, R.; Leung, C.; Zhang, J. Resource Allocation in an LTE Cellular Communication System. In Proceedings of the 2009 IEEE International Conference on Communications, Dresden, Germany, 14-18 June 2009; pp. 1–5. [Google Scholar] [CrossRef]
- Pan, H.; Liu, Y.; Sun, G.; Wang, P.; Yuen, C. Resource Scheduling for UAVs-Aided D2D Networks: A Multi-Objective Optimization Approach. IEEE Transactions on Wireless Communications 2023. [CrossRef]
- Feng, D.; Lu, L.; Yuan-Wu, Y.; Li, G.Y.; Feng, G.; Li, S. Device-to-Device Communications Underlaying Cellular Networks. IEEE Transactions on Communications 2013, 61, 3541–3551. [Google Scholar] [CrossRef]
- Barik, P.K.; Chaurasiya, A.D.; Datta, R. DOCA: A UAV-Assisted Multi-Hop D2D Resource Allocation Scheme for 5G and beyond Using Machine Learning. Telecommunication Systems 2024. [CrossRef]
- Barik, P.K.; Singhal, C.; Datta, R. An Efficient Data Transmission Scheme through 5G D2D-Enabled Relays in Wireless Sensor Networks. Computer Communications 2021, 168, 102–113. [Google Scholar] [CrossRef]
- Min, H.; Lee, J.; Park, S.; Hong, D. Capacity Enhancement Using an Interference Limited Area for Device-to-Device Uplink Underlaying Cellular Networks. IEEE Transactions on Wireless Communications 2011, 10, 3995–4000. [Google Scholar] [CrossRef]
- Zhao, J.; Chai, K.K.; Chen, Y.; Schormans, J.; Alonso-Zarate, J. Two-Level Game for Relay-Based Throughput Enhancement via D2D Communications in LTE Networks. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, 22-27 May 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Gupta, L.; Jain, R.; Vaszkun, G. Survey of Important Issues in UAV Communication Networks. IEEE Communications Surveys & Tutorials 2015, 18, 1123–1152. [Google Scholar] [CrossRef]
- Fu, X.; Ding, T.; Peng, R.; Liu, C.; Cheriet, M. Joint UAV Channel Modeling and Power Control for 5G IoT Networks. EURASIP Journal on Wireless Communications and Networking 2021. [CrossRef]
- Dixit, A.; Singh, S.K. DCM-D2X: An Effective Communication Mobility Model for Decentralized Cooperative Multi-Layer Drone to Everything. IEEE Access 2024, 12, 37326–37348. [Google Scholar] [CrossRef]
- Begen, A.; Akgul, T.; Baugher, M. Watching Video over the Web: Part 1: Streaming Protocols. IEEE Internet Computing 2011, 15, 54–63. [Google Scholar] [CrossRef]
- Xiao, S.; Zhou, X.; Feng, D.; Yuan-Wu, Y.; Li, G.Y.; Guo, W. Energy-Efficient Mobile Association in Heterogeneous Networks With Device-to-Device Communications. IEEE Transactions on Wireless Communications 2016, 15, 5260–5271. [Google Scholar] [CrossRef]
- Dan, F.; Ma, Y.; Yin, W.; Yang, X.; Zhou, F.; Lu, S.; Ning, B. An Accuracy-Aware Energy-Efficient Multipath Routing Algorithm for WSNs. Sensors 2024, 24, 285. [Google Scholar] [CrossRef] [PubMed]
- Zhang, J.; Wang, T.; Wang, J.; Du, W.; Zheng, D.; Wang, S.; Li, Y. Multi-UAV Collaborative Surveillance Network Recovery Via Deep Reinforcement Learning. IEEE Internet of Things Journal 2024, 1. [Google Scholar] [CrossRef]
- Abubakar, A.; Ahmad, I.; Omeke, K.; Ozturk, M.; Ozturk, C.; Abdel-Salam, A.; Mollel, M.; Abbasi, Q.; Hussain, S.; Imran, M. A Survey on Energy Optimization Techniques in UAV-Based Cellular Networks: From Conventional to Machine Learning Approaches. Drones 2023, 7, 214. [Google Scholar] [CrossRef]
- Do, T.H.; Truong, L.H.; Nguyen, M.T.; Chien, C.-F.; Tran, H.T.; Hua, H.T.; Nguyen, C.V.; Nguyen, H.T.T.; Nguyen, N.T.T. Energy-Efficient Unmanned Aerial Vehicle (UAV) Surveillance Utilizing Artificial Intelligence (AI). Wireless Communications and Mobile Computing 2021, 2021, 1–11. [Google Scholar] [CrossRef]
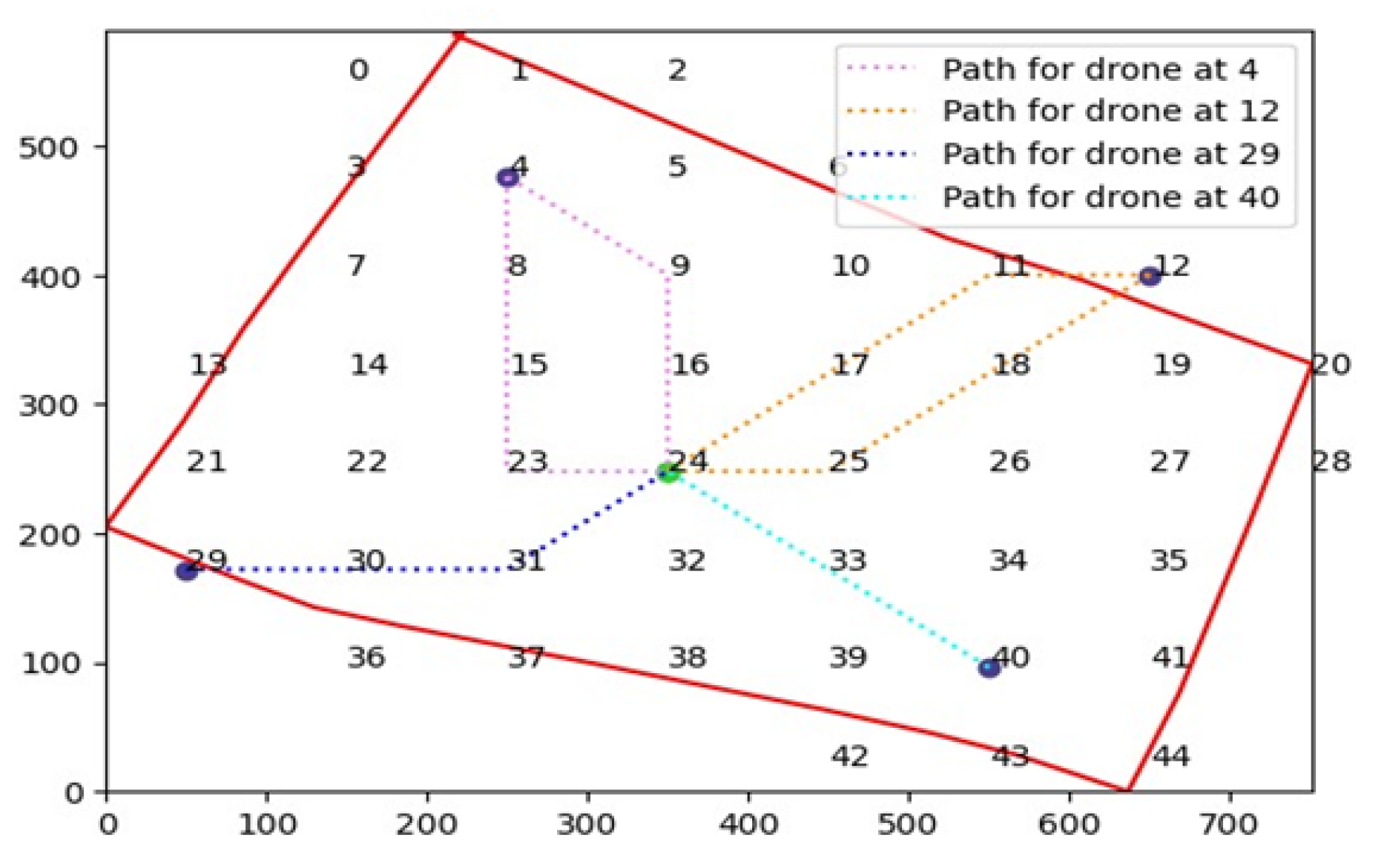
| Data To be Transmitted (MB) | Path | Previous Capacity (Mbps) | Transmission Time (s) | Initial Battery Level (%) | Remaining Battery Level (%) | Current Capacity |
|---|---|---|---|---|---|---|
| 600 | 4 → 8 → 15 → 23 → 24 | 3.5 → 3.5 → 3.5 → 3.5 | 172 → 172 → 176 → 172 | 100 → 100 → 100 → 100 | 31 → 31 → 32 → 31 | 1.085 → 1.085 → 1.088 → 1.085 |
| 600 | 12 → 18 → 25 → 24 | 3.4 → 3.4 → 3.3 → 3.3 | 176 → 176 → 180 | 100 → 100 → 100 | 32 → 32 → 34 | 1.088 → 1.088 → 1.122 |
| 330 | 29 → 30 → 31 → 24 | 3.5 → 3.5 → 3.3 → 3.3 | 172 → 172 → 180 | 100 → 100 → 100 | 31 → 31 → 34 | 1.085 → 1.085 → 1.122 |
| 300 | 40 → 33 → 24 | 3.4 → 3.4 | 176 → 176 | 100 → 100 | 32 → 32 | 1.088 → 1.088 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





