Submitted:
25 October 2024
Posted:
25 October 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
- Representing a comprehensive review of security requirements of IoT device approaches in the manufacturing environment.
- We are providing a comparison of the domain, architecture, requirements, and solution of chosen papers.
- Illustrating the architecture of IoT frameworks in the context of IoT security and IoT retrofitting.
- Proposing secure IoT Retrofitting System Architecture for Manufacturing Environment.
2. Background
2.1. IoT Security
2.1.1. IoT Retrofitting
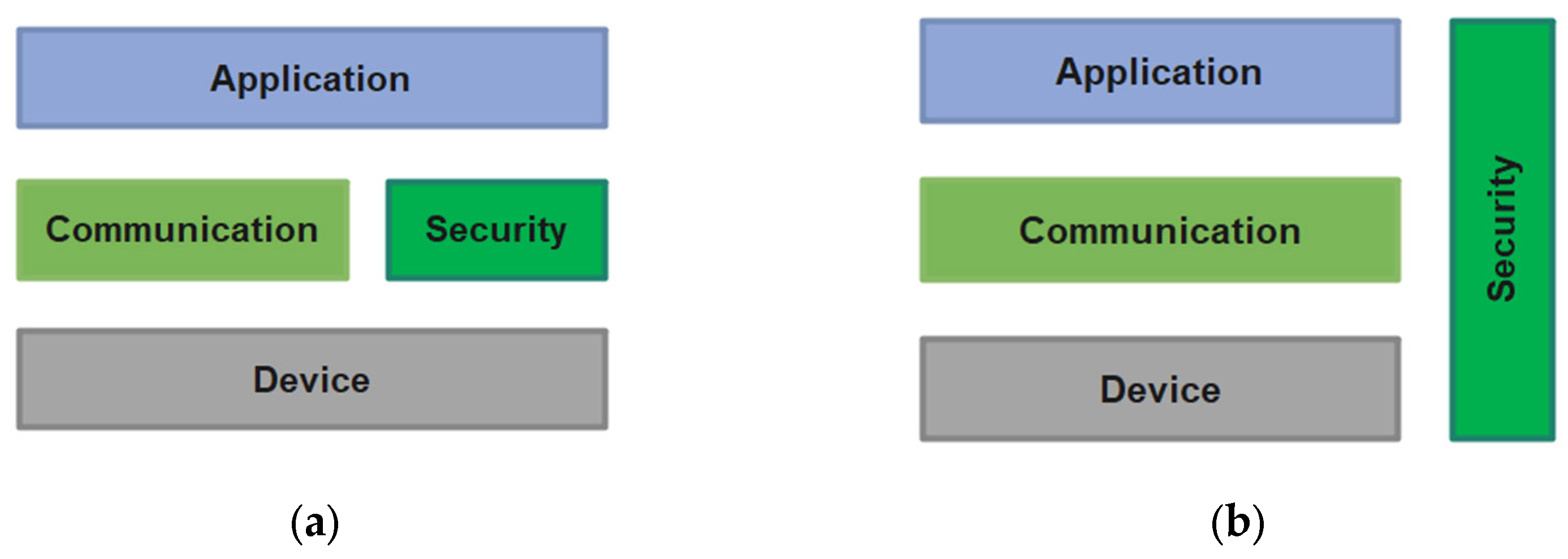
2.1.2. Security in IoT Architecture
2.1.3. Integration of Emerging Technologies for IoT Security in Industry 4.0
2.2. Related Works
2.4. Popular Open-Source IoT Frameworks
Security Aspects of Top 5 Opensource IoT Framework
- KAA IoT security: KAA provides user authentication, access authorization and server authentication using OAuth 2.0 and keylock.
- Zetta IoT security: While interacting, Zetta keeps track of security credentials and relevant information. Zetta supports MQTT, and CoAP protocol to ensure the security of the IoT environment.
- DeviceHive security: DeviceHive security is safe by design. The platform is built using modern security techniques. JSON Web Tokens are used to secure DeviceHive authentication (JWT). It supports MQTT protocol and custom firmware as well.
- Aurdino IoT platform security: Arduino is very aware of the dangers of hacking and is continuously working to improve security in both its hardware and software. Customization users may utilize the Arduino libraries, which include HTTP, MQTT, X.509, and JSON support, to connect to any web service they choose.
- OpenRemote Security: HTTP and MQTT are examples of standard protocols supported by the OpenRemote platform. OpenRemote protects all assets and keeps stored data fully secured in both cloud and on-premise platforms.
3. Methodology
3.1. Planning
3.2. Research Questions
3.3. Search Process
3.4. Inclusion and Exclusion Criteria
3.5. Data Collection
3.6. Final Selection
4. Security Requirements and Solutions in IoT
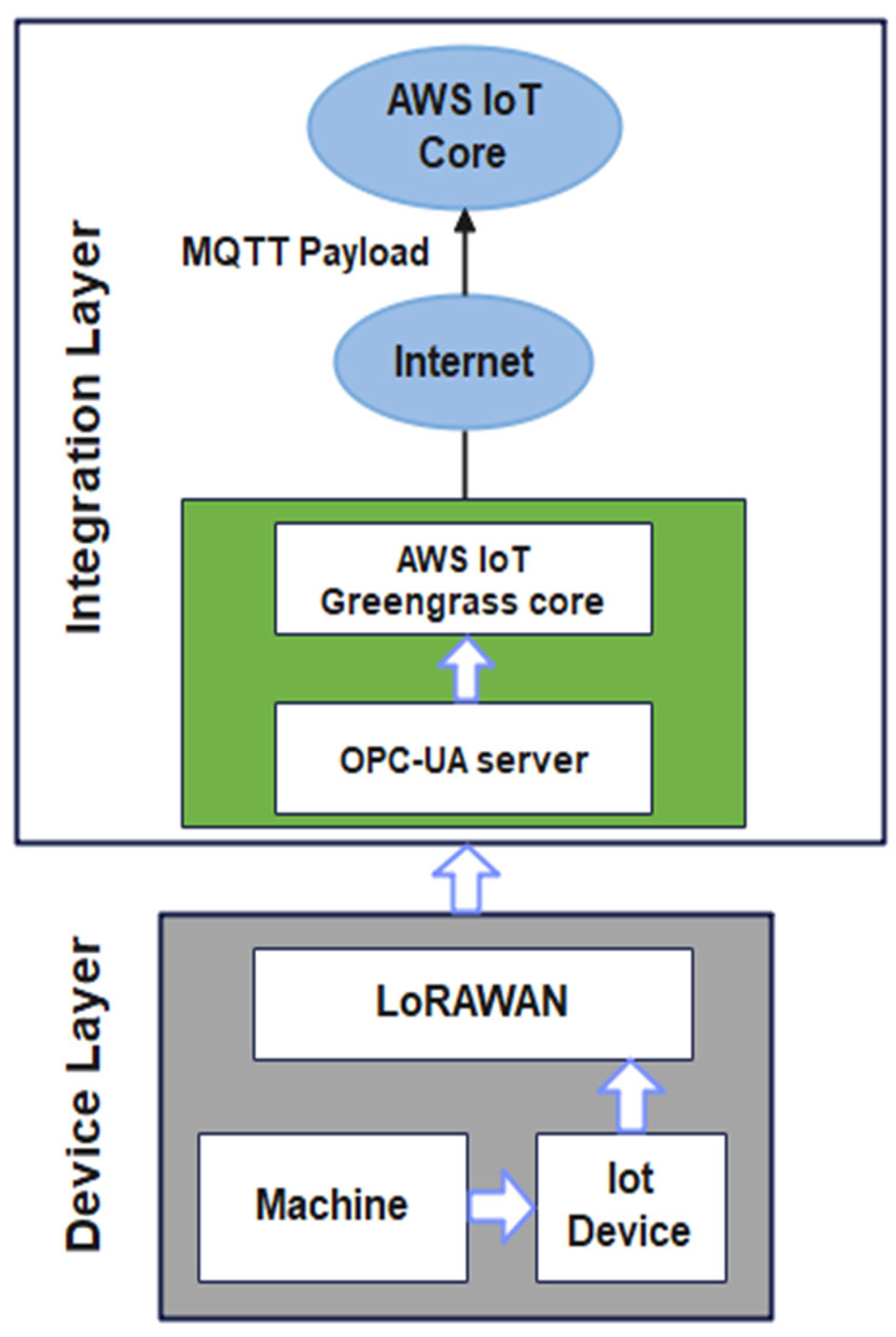
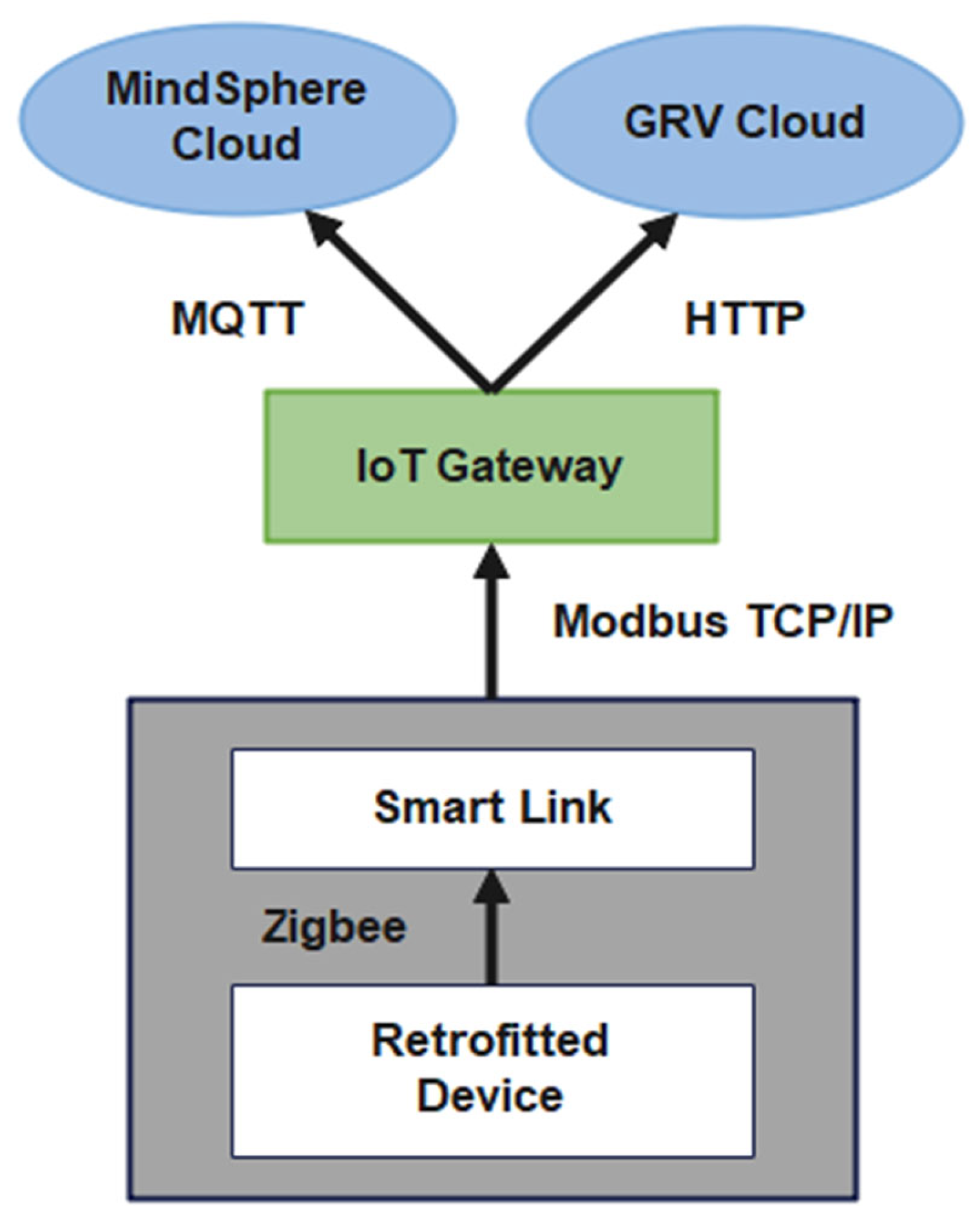
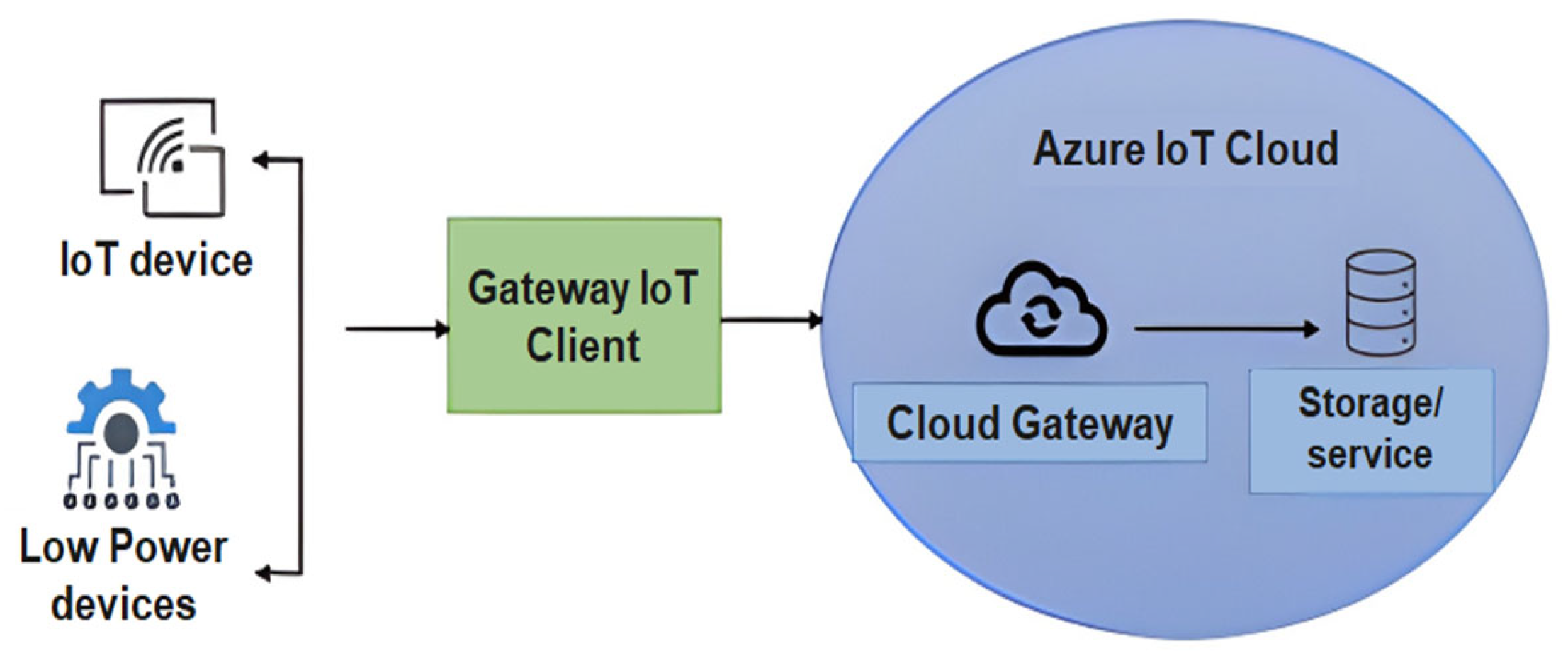
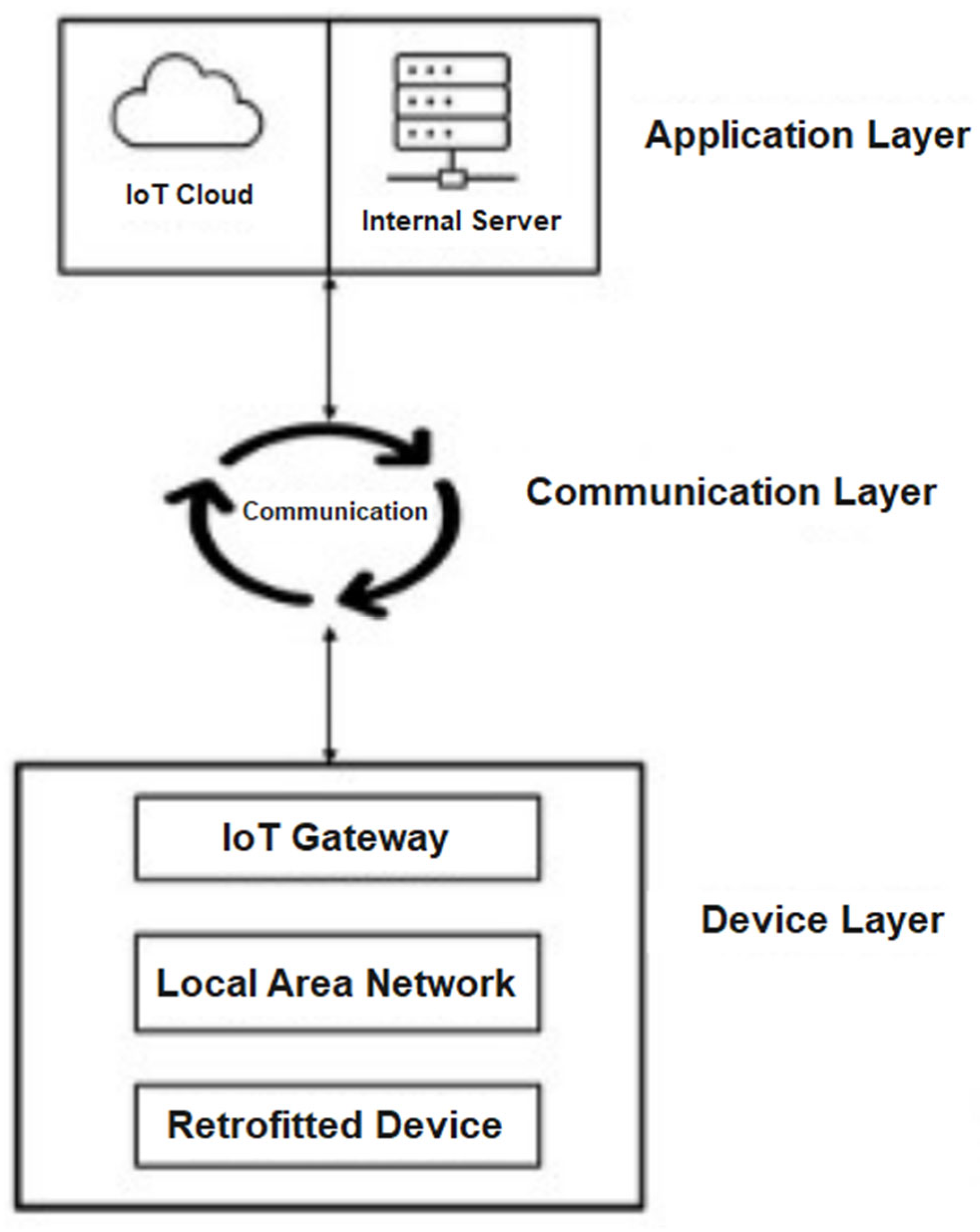
5. Retrofitted IoT System Architecture in Manufacturing Environment
5.1. Device Layer
5.2. Communication Layer
5.3. Application Layer
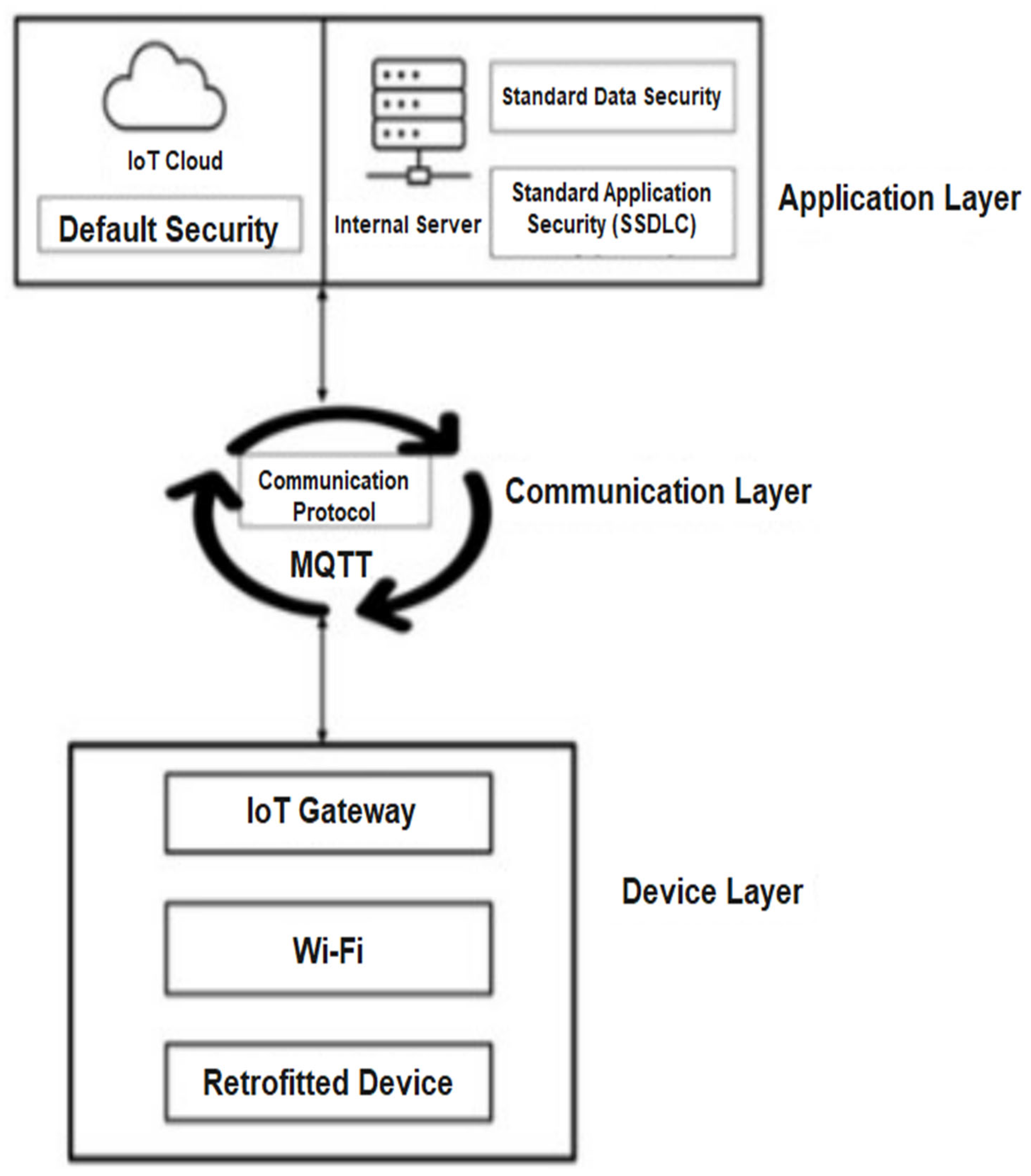
6. Proposed Secure Retrofitted IoT System Architecture in Manufacturing Environment
7. Sustainability in IoT-Enabled Manufacturing
7.1. Sustainable IoT Architecture
8. Discussion
9. Conclusion and Future Work
Acknowledgements
Conflicts of Interest
References
- Ye, C.; Indra, P.P.; Aspinall, D. Retrofitting Security and Privacy Measures to Smart Home Devices, 2019 6th Int. Conf. Internet Things Syst. Manag. Secur. IOTSMS 2019. (2019) 283–290. [CrossRef]
- Gupta, P. Gupta, J. Chhabra, 07414782, (2015) 285–289.
- Alladi, T.; Chamola, V.; Sikdar, B.; Choo, K.-K.R. Consumer IoT: Security Vulnerability Case Studies and Solutions. IEEE Consum. Electron. Mag. 2020, 9, 17–25. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Ahmad, I.; Niazy, M.S.; Ziar, R.A.; Khan, S. Survey on IoT: Security Threats and Applications. J. Robot. Control. (JRC) 2021, 2, 42–46. [Google Scholar] [CrossRef]
- Santhosh, N.; Srinivsan, M.; Ragupathy, K. Internet of Things (IoT) in smart manufacturing. IOP Conf. Series: Mater. Sci. Eng. 2020, 764. [Google Scholar] [CrossRef]
- Ammar, M.; Russello, G.; Crispo, B. Internet of Things: A survey on the security of IoT frameworks. J. Inf. Secur. Appl. 2018, 38, 8–27. [Google Scholar] [CrossRef]
- A.D. Jurcut, P. A.D. Jurcut, P. Ranaweera, L. Xu, Introduction to IoT Security, 2019. [CrossRef]
- Lins, T.; Oliveira, R.A.R.; Correia, L.H.A.; Silva, J.S. Industry 4.0 retrofitting, Brazilian Symp. Comput. Syst. Eng. SBESC. 2018-Novem (2018) 8–15. [CrossRef]
- Tuptuk, N.; Hailes, S. Security of smart manufacturing systems. J. Manuf. Syst. 2018, 47, 93–106. [Google Scholar] [CrossRef]
- A.M. Mzahm, M.S. A.M. Mzahm, M.S. Ahmad, A.Y.C. Tang, Enhancing the Internet of Things ( IoT ) via the Concept of Agent of Things ( AoT ), J. Netw. Innov. Comput. 2 (2014) 101–110.
- Thilakarathne, N.N. Security and Privacy Issues in IoT Environment. Int. J. Eng. Manag. Res. 2020, 10, 26–29. [Google Scholar] [CrossRef]
- Panda, S.K.; Blome, A.; Wisniewski, L.; Meyer, A. IoT Retrofitting Approach for the Food Industry, IEEE Int. Conf. Emerg. Technol. Fact. Autom. ETFA. 2019-Septe (2019) 1639–1642. [CrossRef]
- Macedo, E.L.C.; de Oliveira, E.A.R.; Silva, F.H.; Mello, R.R.; Franca, F.M.G.; Delicato, F.C.; de Rezende, J.F.; de Moraes, L.F.M. On the security aspects of Internet of Things: A systematic literature review. J. Commun. Networks 2019, 21, 444–457. [Google Scholar] [CrossRef]
- Lima, F.; Massote, A.A.; Maia, R.F. IoT Energy Retrofit and the Connection of Legacy Machines Inside the Industry 4.0 Concept, IECON Proc. (Industrial Electron. Conf. 2019-Octob (2019) 5499–5504. [CrossRef]
- Asghari, P.; Rahmani, A.M.; Javadi, H.H.S. Service composition approaches in IoT: A systematic review. J. Netw. Comput. Appl. 2018, 120, 61–77. [Google Scholar] [CrossRef]
- Maswadi, K.; Ghani, N.B.A.; Hamid, S.B. Systematic Literature Review of Smart Home Monitoring Technologies Based on IoT for the Elderly. IEEE Access 2020, 8, 92244–92261. [Google Scholar] [CrossRef]
- Kitchenham, B.; Brereton, O.P.; Budgen, D.; Turner, M.; Bailey, J.; Linkman, S. Systematic literature reviews in software engineering – A systematic literature review. Inf. Softw. Technol. 2008, 51, 7–15. [Google Scholar] [CrossRef]
- Al-Turjman, F.; Zahmatkesh, H.; Shahroze, R. An overview of security and privacy in smart cities' IoT communications. Trans. Emerg. Telecommun. Technol. 2019, 33. [Google Scholar] [CrossRef]
- Deep, S.; Zheng, X.; Jolfaei, A.; Yu, D.; Ostovari, P.; Bashir, A.K. A survey of security and privacy issues in the Internet of Things from the layered context. Trans. Emerg. Telecommun. Technol. 2020, 33. [Google Scholar] [CrossRef]
- Samaila, M.G.; Neto, M.; Fernandes, D.A.B.; Freire, M.M.; Inácio, P.R.M. Challenges of securing Internet of Things devices: A survey. Secur. Priv. 2018, 1. [Google Scholar] [CrossRef]
- Gupta, B.; Quamara, M. An overview of Internet of Things (IoT): Architectural aspects, challenges, and protocols. Concurr. Comput. Pr. Exp. 2018, 32. [Google Scholar] [CrossRef]
- Mai, T.D. Research on Internet of Things security architecture based on fog computing. Int. J. Distrib. Sens. Networks 2019, 15. [Google Scholar] [CrossRef]
- Liu, J.; Chen, M.; Wang, L. A new model of industrial internet of things with security mechanism—An application in complex workshop of diesel engine. Proc. Inst. Mech. Eng. Part C: J. Mech. Eng. Sci. 2019, 234, 564–574. [Google Scholar] [CrossRef]
- Aydos, M.; Vural, Y.; Tekerek, A. Assessing risks and threats with layered approach to Internet of Things security. Meas. Control. 2019, 52, 338–353. [Google Scholar] [CrossRef]
- Selimis, G.; Wang, R.; Maes, R.; Schrijen, G.-J.; Münzer, M.; Ilić, S.; Willems, F.M.J.; Kusters, L. RESCURE: A security solution for IoT life cycle, ACM Int. Conf. Proceeding Ser. ( 2020. [CrossRef]
- Tange, K.; De Donno, M.; Fafoutis, X.; Dragoni, N. A Systematic Survey of Industrial Internet of Things Security: Requirements and Fog Computing Opportunities. IEEE Commun. Surv. Tutorials 2020, 22, 2489–2520. [Google Scholar] [CrossRef]
- Mena, D.M.; Papapanagiotou, I.; Yang, B. Internet of things: Survey on security. Inf. Secur. Journal: A Glob. Perspect. 2018, 27, 162–182. [Google Scholar] [CrossRef]
- Iqbal, W.; Abbas, H.; Daneshmand, M.; Rauf, B.; Bangash, Y.A. An In-Depth Analysis of IoT Security Requirements, Challenges, and Their Countermeasures via Software-Defined Security. IEEE Internet Things J. 2020, 7, 10250–10276. [Google Scholar] [CrossRef]
- Sharma, V.; You, I.; Andersson, K.; Palmieri, F.; Rehmani, M.H.; Lim, J. Security, Privacy and Trust for Smart Mobile- Internet of Things (M-IoT): A Survey. IEEE Access 2020, 8, 167123–167163. [Google Scholar] [CrossRef]
- Ebo, I.O.; Falana, O.J.; Taiwo, O.; Olumuyiwa, B.A. An Enhanced Secured IOT Model for Enterprise Architecture, 2020 Int. Conf. Math. Comput. Eng. Comput. Sci. ICMCECS 2020. ( 2020. [CrossRef]
- Serror, M.; Hack, S.; Henze, M.; Schuba, M.; Wehrle, K. Challenges and Opportunities in Securing the Industrial Internet of Things. IEEE Trans. Ind. Informatics 2020, 17, 2985–2996. [Google Scholar] [CrossRef]
- Bhawiyuga, A.; Data, M.; Warda, A. Architectural design of token based authentication of MQTT protocol in constrained IoT device, Proceeding 2017 11th Int. Conf. Telecommun. Syst. Serv. Appl. TSSA 2017. 2018-Janua (2018) 1–4. [CrossRef]
- Shen, W.; Yin, B.; Cao, X.; Cai, L.X.; Cheng, Y. Secure device-to-device communications over WiFi direct. IEEE Netw. 2016, 30, 4–9. [Google Scholar] [CrossRef]
- Gebremichael, T.; Ledwaba, L.P.I.; Eldefrawy, M.H.; Hancke, G.P.; Pereira, N.; Gidlund, M.; Akerberg, J. Security and Privacy in the Industrial Internet of Things: Current Standards and Future Challenges. IEEE Access 2020, 8, 152351–152366. [Google Scholar] [CrossRef]
- Celik, Z.B.; Fernandes, E.; Pauley, E.; Tan, G.; McDaniel, P. Program Analysis of Commodity IoT Applications for Security and Privacy. ACM Comput. Surv. 2019, 52, 1–30. [Google Scholar] [CrossRef]
- Aazam, M.; Zeadally, S.; Harras, K.A. Deploying Fog Computing in Industrial Internet of Things and Industry 4.0. IEEE Trans. Ind. Informatics 2018, 14, 4674–4682. [Google Scholar] [CrossRef]
- Hassan, R.; Qamar, F.; Hasan, M.K.; Aman, A.H.M.; Ahmed, A.S. Internet of Things and Its Applications: A Comprehensive Survey. Symmetry 2020, 12, 1674. [Google Scholar] [CrossRef]
- Somaya, H.; Tomadar, M. Secure communication in E-health care system monitoring, ACM Int. Conf. Proceeding Ser. (2019) 1–9. [CrossRef]
- X. Yang, LoRaWAN: Vulnerability Analysis and Practical Exploitation, (2017). http://repository.tudelft.nl/.
- What is an IoT Gateway? | Lanner, (n.d.). https://www.lanner-america.com/blog/what-is-an-iot-gateway/ (accessed December 21, 2020).
- Bicaku, A.; Tauber, M.; Delsing, J. Security standard compliance and continuous verification for Industrial Internet of Things. Int. J. Distrib. Sens. Networks 2020, 16. [Google Scholar] [CrossRef]
- U. Hunkeler, H.L. U. Hunkeler, H.L. Truong, A. Stanford-clark, MQTT-S – A Publish / Subscribe Protocol For Wireless Sensor Networks, (n.d.).
- Cendón, M2M interworking technologies and underlying market considerations, Mach. Commun. (2015) 79–92. [CrossRef]
- Luzuriaga, J.E.; Perez, M.; Boronat, P.; Cano, J.C.; Calafate, C.; Manzoni, P. A comparative evaluation of AMQP and MQTT protocols over unstable and mobile networks. In Proceedings of the 12th Annual IEEE Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2015. [Google Scholar] [CrossRef]
- Nebbione, G.; Calzarossa, M.C. Security of IoT Application Layer Protocols: Challenges and Findings. Futur. Internet 2020, 12, 55. [Google Scholar] [CrossRef]
- Michaud, M.J.; Dean, T.; Leblanc, S.P. Attacking OMG Data Distribution Service (DDS) Based Real-Time Mission Critical Distributed Systems, MALWARE 2018 - Proc. 2018 13th Int. Conf. Malicious Unwanted Softw. (2019) 68–77. [CrossRef]
- Kim, J.; Park, J.; Lee, J.-H. Analysis of recent IIoT security technology trends in a smart factory environment. In2023 International Conference on Artificial Intelligence in Information and Communication (ICAIIC) 2023 Feb 20 (pp. 840-845). IEEE. [CrossRef]
- Juma, M.; Alattar, F.; Touqan, B. Securing Big Data Integrity for Industrial IoT in Smart Manufacturing Based on the Trusted Consortium Blockchain (TCB). IoT 2023, 4, 27–55. [Google Scholar] [CrossRef]
- Safavi, S.; Shukur, Z. Conceptual Privacy Framework for Health Information on Wearable Device. PLOS ONE 2014, 9, e114306. [Google Scholar] [CrossRef]
- Safavi, S.; Meer, A.M.; Melanie, E.K.J.; Shukur, Z. Cyber vulnerabilities on smart healthcare, review and solutions. In2018 Cyber Resilience Conference (CRC) 2018 Nov 13 (pp. 1-5). IEEE. [CrossRef]
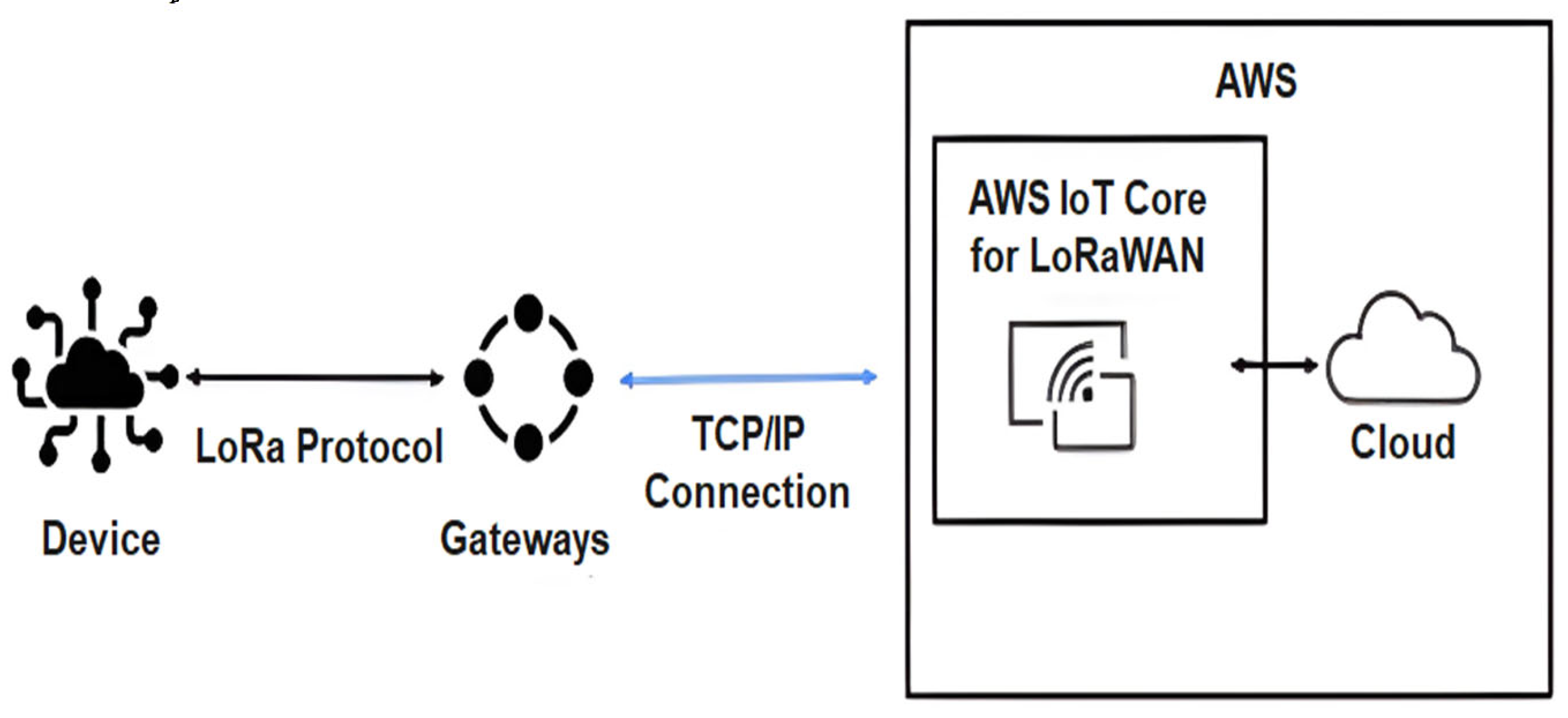
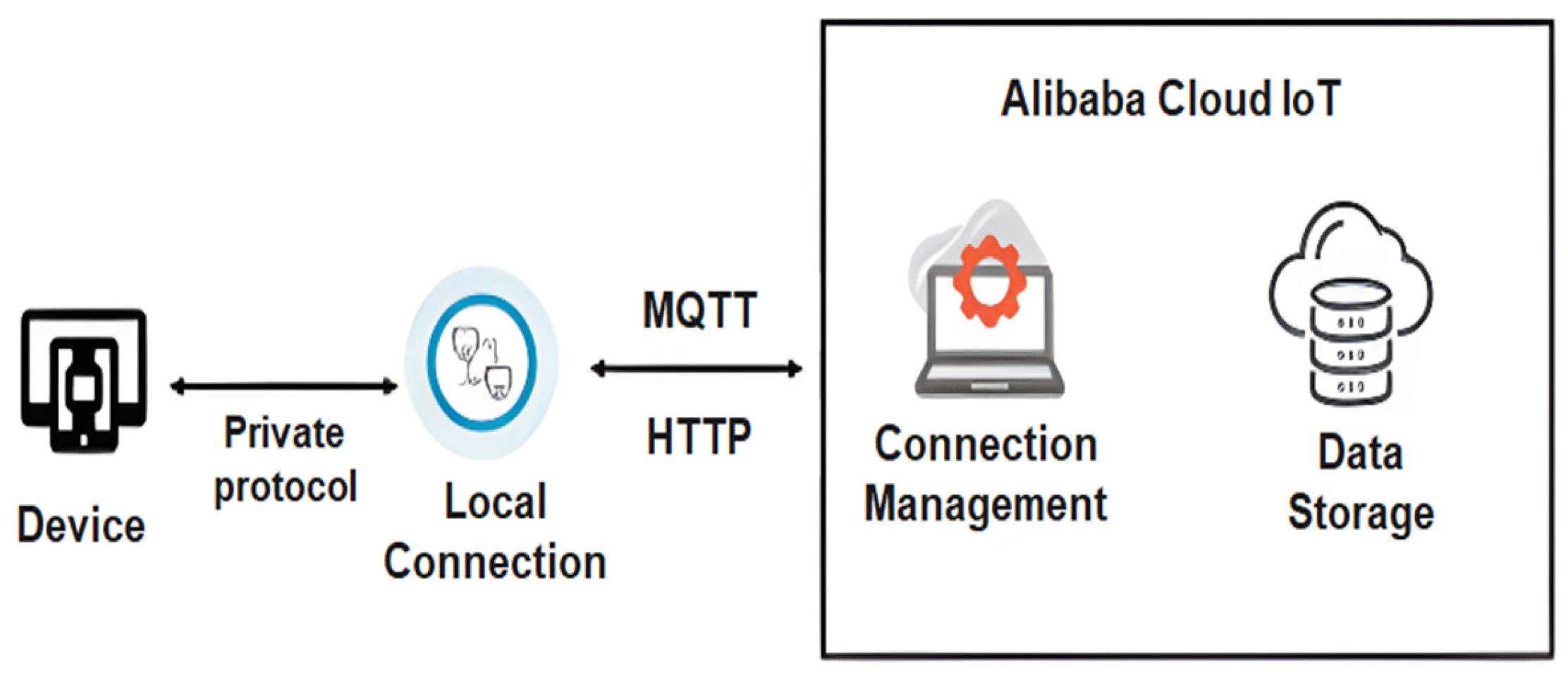
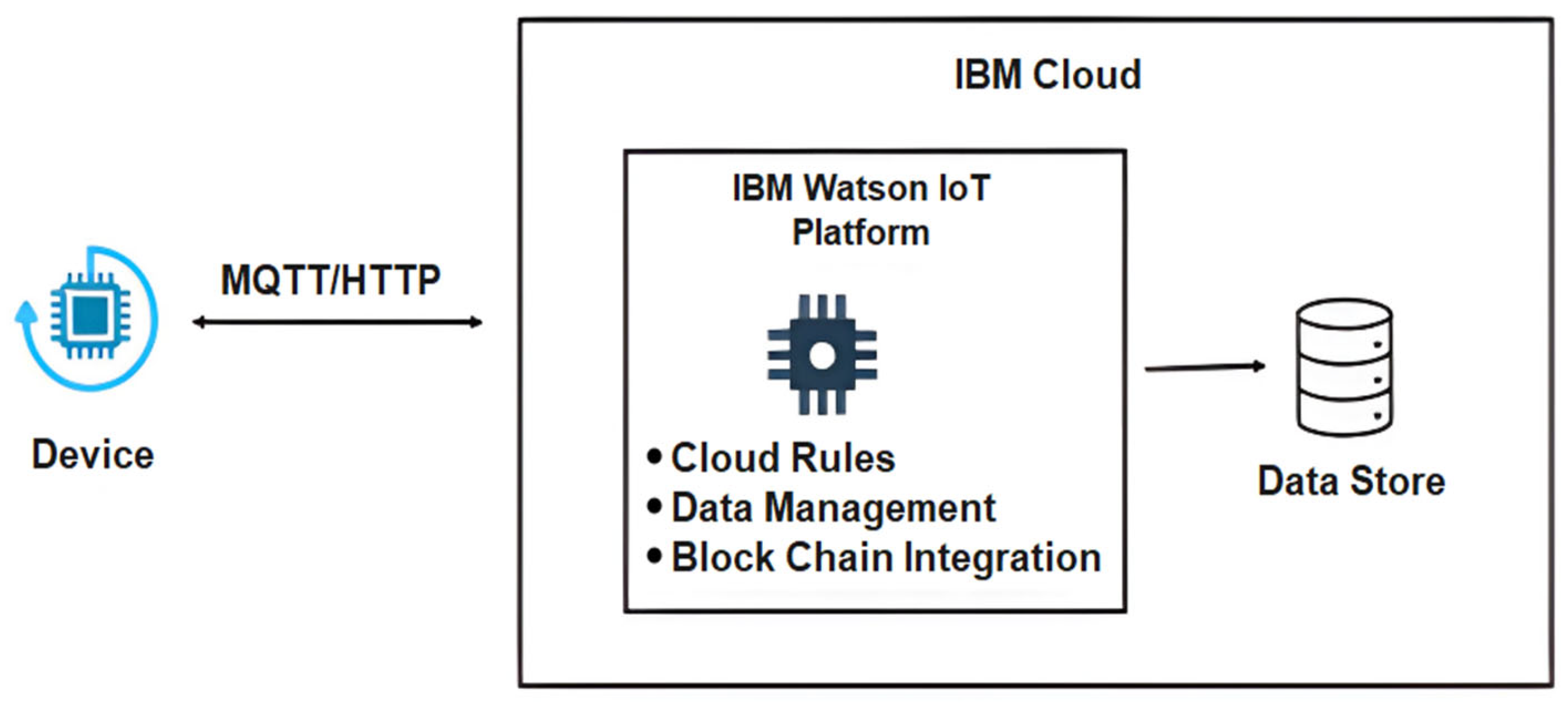
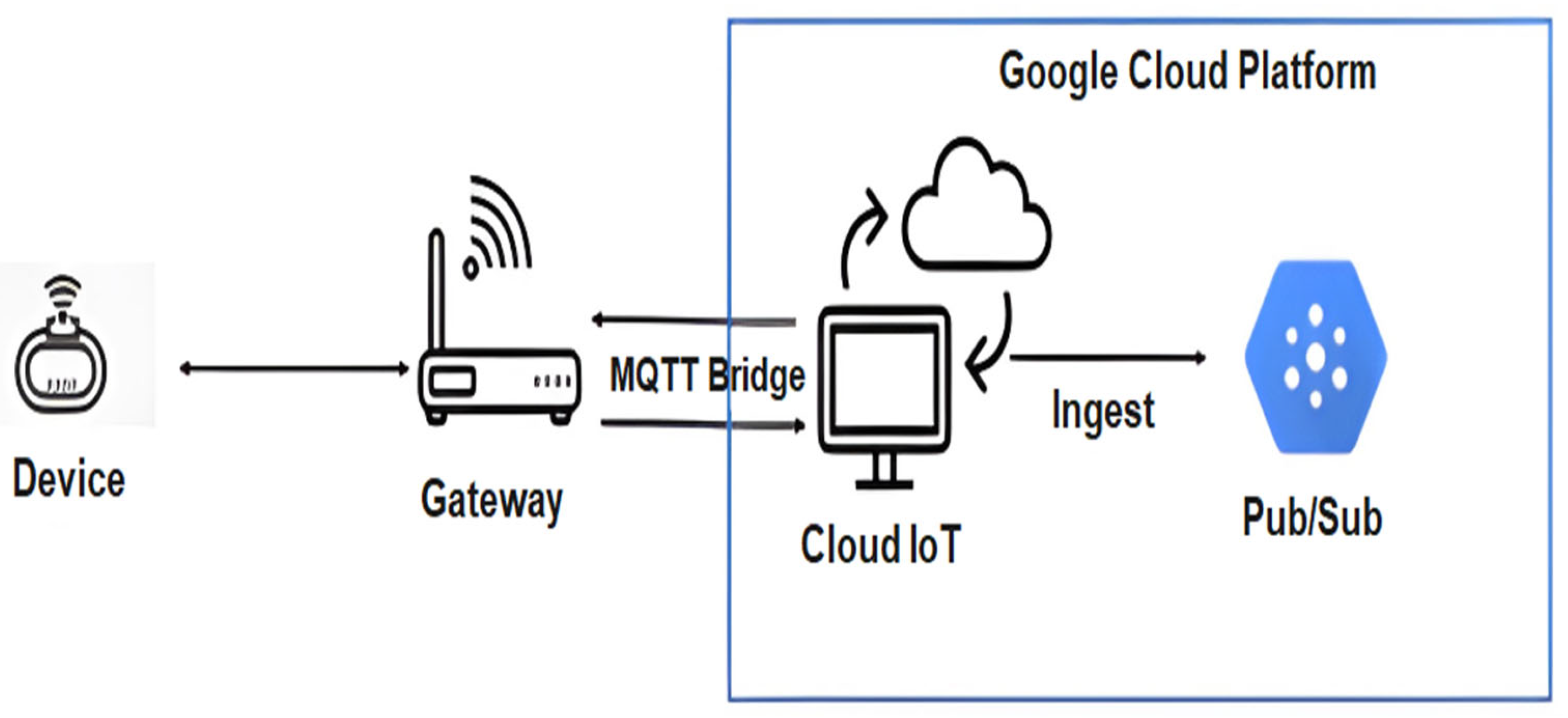
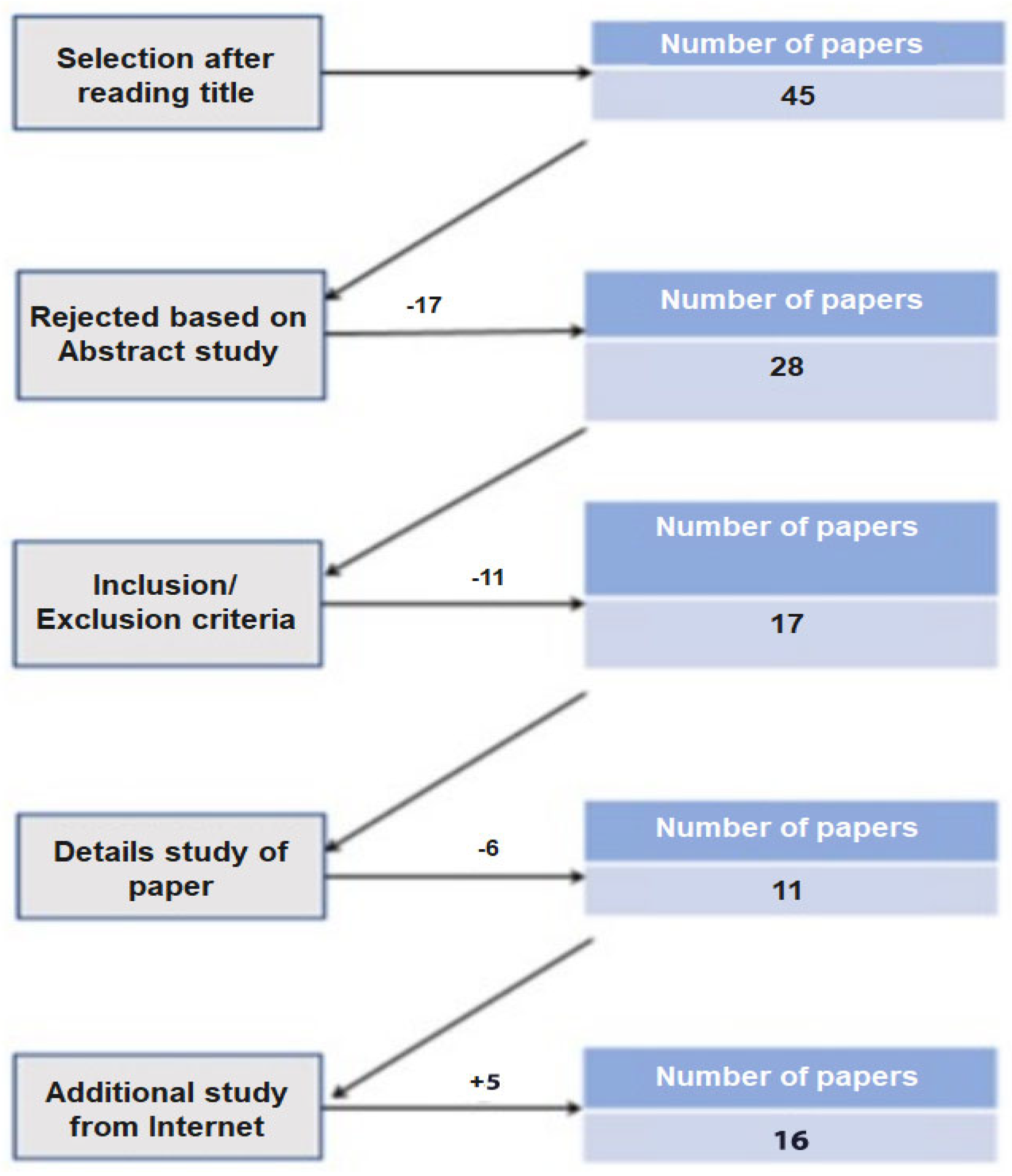
| Study / Protocol | Security Protocol | Implementation Cost | Integration Level | Scalability | Security Level |
| Study A [48] (5G) | 5G | High | High | High | Strong |
| Study B [4] (AI) | AI-driven Monitoring | Medium | Medium | High | Strong |
| Study C [49] (Blockchain) | Blockchain | High | Low | Medium | Strong |
| Study D [33] (MQTT) | MQTT | Low | High | Medium | Moderate |
| Study E [46] (CoAP) | CoAP | Low | Medium | Low | Moderate |
| WebPages | Open-source IoT framework | Higher frequency framework based on mentioned webpages |
|---|---|---|
| www.techtic.com | Kaa IoT, Macchina.io, Zetta ,GE PREDIX,ThingSpeak ,DeviceHive ,Distributed Services Architecture,Eclipse , Open Connectivity Foundation , OpenHAB |
Kaa IoT |
| https://geekflare.com | Zetta ,Arduino OpenRemote ,Node-RED ,Flutter, M2MLabs Mainspring ,ThingsBoard, Kinoma, Kaa IoT Platform ,SiteWhere ,DSA ,Thinger | Zetta |
| https://bitnine.net | Arduino,Devicehub.net,IoTToolkit,OpenWSN,Particle,SiteWhere,ThingSpeak,Webinos, Zetta | Arduino |
| www.esparkinfo.com | Kaa IoT, Macchina.io, Zetta ,GE PREDIX,ThingSpeak,DeviceHive,Distributed Services Architecture, Eclipse,OpenConnectivity Foundation,OpenHAB, CiscoIoT Cloud Connect,Salesforce, Oracle,SAP,Microsoft Azure, Google Cloud Platform, Hewlett Packard Enterprise, DataV by Bsquare, Mindsphere by Siemens, MBED IoT Device platform, Amazon Web Services [AWS], Mocana,RTI |
Kaa IoT |
| www.iotforall.com | DeviceHive,ThingSpeak,Mainflux,Thinger.io,Zetta | DeviceHive |
| iot4beginners.com | Kaa, Zetta, thinger.io, ThingsBoard, DeviceHive, Mainflux, ThingSpeak, myDevices, openremote, WSO2 | Kaa |
| iotdunia.com | Kaa IoT, Macchina.io, Zetta ,GE PREDIX,ThingSpeak,DeviceHive ,Distributed Services Architecture · ,Arduino, Node-RED, Flutter | Kaa |
| www.yumpu.com | Kaa IoT, Macchina.io, Zetta ,GE PREDIX,ThingSpeak ,DeviceHive ,Distributed Services Architecture, Eclipse, Open Connectivity Foundation,OpenHAB |
Kaa |
| www.record-evolution.de | Open Remote, Things Board, Thinger.io,MainFlux, Arduino |
OpenRemote |
| https://internetofthingsagenda.techtarget.com | Open Remote, Device Hive, The Thing System, Distributed Services Architecture, Node-RED, DeviceHub,Kaa | OpenRemote |
| https://medium.com | Kaa IoT, Macchina.io, Zetta ,GE PREDIX, ThingSpeak, DeviceHive ,Distributed Services Architecture, Eclipse, Open Connectivity Foundation, OpenHAB |
Kaa IoT |
| www.allerin.com | Kaa,Zetta,DeviceHive, SiteWhere Distributed Services Architecture | DeviceHive |
| Database | URL |
|---|---|
| IEEE Xplore | http://ieeexplore.ieee.org |
| ACM digital library | http://dl.acm.org |
| Wiley | https://onlinelibrary.wiley.com |
| Taylor & Francis | https://www.tandfonline.com |
| Sage | https://journals.sagepub.com |
| Inclusion Criteria | Articles are related to IoT security in manufacturing Article content applicable to research questions. The article must report either architecture or security of IoT devices nor both. Articles should be review, survey or original article which contains in-depth literature review. |
| Exclusion Criteria | Articles not focusing on security of IoT device or manufacturing. Articles are out of the scope of this study. Articles were published before 2018. |
| Keywords | Delimitation Criteria | Database/ Journal/ Conference |
Hits | Selection after reading title |
|---|---|---|---|---|
| “IoT AND security AND requirements AND manufacturing” OR “IoT AND security AND requirements AND industry” OR “Internet of Things AND security AND requirements AND manufacturing” OR “Internet of Things AND security AND requirements AND industry” |
Language: English Document Type: Conference & journals (Related to Computer science, IT & cyber security) Advanced search based on keywords, abstract & Publication year :2018 to 2024 |
Sage | 14 | 7 |
| Wiley | 42 | 7 | ||
| Taylor & Francis | 9 | 5 | ||
| ACM | 69 | 17 | ||
| IEEE | 44 | 10 |
| Publisher Year Author |
Title | Domain | Type | Architecture | Requirement | Solutions |
|---|---|---|---|---|---|---|
| Willey 2019 Fadi Al-Turjman et al [19]. |
An overview of security and privacy in smart cities' IoT communications | Non-manufacture | Review | Physical layer, Network layer, Database layer, virtualization layer, Data analytics and mining layer, Application layer | data privacy, integrity, confidentiality and availability | black networks (BNs), trusted software-defined networking (SDN) controller named as TTP, unified registry (UR), and key management system (KMS) |
| Willey 2020 Samundra Deep et al [20]. |
A survey of security and privacy issues in the Internet of Things from the layered context | General | Survey | Perception layer, Network layer, Middleware layer, Application layer | data privacy, integrity, confidentiality, availability |
data encryption, key management scheme and lightweight cryptographic algorithms |
| Willey 2020 Gupta et al [22]. |
An overview of Internet of Things (IoT): Architectural aspects, challenges, and protocols | General | Review | Perception Layer, Transmission Layer, and Application Layer. | confidentiality, integrity, and user privacy. Trust Management | Trust management |
| Sagepub 2019 Trung Dong Mai [23] |
Research on Internet of Things security architecture based on fog computing | General | Research Article | Perceptual layer, Transport layer, Processing layer, Application layer |
data traceability, integrity, identity authentication, credibility management, confidentiality, and privacy protection |
Light weight encryption method |
| Sagepub 2020 Liu et al [24]. |
A new model of industrial internet of things with security mechanism—An application in complex workshop of diesel engine | Industry | Research Article | data acquisition layer, data access layer, data processing layer, data transfer layer, network layer, and data application layer | user access system and the reliability and integrity of data transmission | security transmission mechanism at all levels |
| Sagepub 2019 Aydos et al [25]. |
Assessing risks and threats with layered approach to Internet of Things security | General | Research Article | Perception layer, Network layer, Data processing layer ,Application layer | integrity, accessibility and privacy | risk-based IoT security model |
| ACM 2020 Selimis et al [26]. |
RESCURE: A security solution for IoT life cycle | General | Research Article | Device layer, Cloud layer | Authentication, Privacy, Integrity | SRAM-PUF |
| ACM 2020 Tange et al [27]. |
Towards a systematic survey of industrial IoT security requirements: research method and quantitative analysis | Manufacturing | Survey | N/A | CIA Triad, Authentication, Access control,Network Security, Data security |
MQTT, Key distribution,.Fingerprint |
| Taylor & Francis 2018 Mendez Mena et al [28]. |
Internet of things: Survey on security | General | Survey | Perception layer, Network layer, Application layer | attack resiliency, authentication, access control, client Privacy |
Encryption scheme, key distribution mechanism, privacy policy |
| IEEE 2020 Iqbal et al [29]. |
An In-Depth Analysis of IoT Security Requirements, Challenges and their Countermeasures via Software Defined Security |
General | Review | Perception layer, Network layer, Application layer | availability, confidentiality, integrity, non-repudiation, privacy and authentication | Multi firewalls and hypervisors integration solution, VArmour DSS ,Deception Virtual Security Framework, OneControl, DefenseFlow |
| IEEE 2020 Sharma et al[30]. |
Security, Privacy and Trust for Smart Mobile-Internet of Things (M-IoT): A Survey | General | survey | Physical layer, Data Link layer, Network layer, Transport layer, Application layer |
Security,privacy,trust | Access control, Quick identification and release of patches, Credential management, Firmware security, Device policy compliance, Script disabling, Continuous application security |
| IEEE 2020 Ebo et al [31]. |
An Enhanced Secured IOT Model for Enterprise Architecture | SME | Research Article | Perception Layer, Network Layer, Processing Layer, Application Layer, Service Management Layer | authentication, authorization, access control, and non- repudiation |
Enterprise’s IoT framework |
| IEEE 2021 Serror et al[32]. |
Challenges and Opportunities in Securing the Industrial Internet of Things | Industry | Survey | Perception layer, Network layer, Application layer | key management, user/device authentication, access control, and privacy preservation | Public-key mechanism,fingerprinting,rules& policiees for access control & encrypted data |
| IEEE 2024 Kim et al[48]. |
Analysis of Recent IIoT Security Technology Trends in a Smart Factory Environment | Smart Manufacturing | Research Article | Integration of 5G, AI, and cloud technologies with operational technology. | Enhanced security for interconnected systems in smart factories, focusing on operational reliability and data integrity. |
Implementation of advanced monitoring systems and real-time data analytics to detect and mitigate threats. |
| MDPI 2024 Juma et al[49]. |
Securing Big Data Integrity for Industrial IoT in Smart Manufacturing Based on the Trusted Consortium Blockchain (TCB) | Smart Manufacturing | Research Article | Trusted Consortium Blockchain (TCB) architecture with hyperledger fabric modular. | Integrity of big data across IoT devices and platforms in smart manufacturing, with a focus on real-time transaction monitoring and peer validation. | Blockchain-driven data validation and encryption methods to ensure data security and integrity, supporting high transaction throughput and low latency. |
| Local Area Networks | Pros | Cons |
|---|---|---|
| Wi-Fi | S.Habibah [33] et al mentioned in their paper that Wi-Fi is a secure choice for communication. Wi-Fi protocol includes two security features which are Wireless Equivalent Privacy (WEP) and Wi-Fi Protected Access(WPA). |
Wi-Fi needs more energy than other communication technology which makes it undesirable[34]. |
| ZigBee | Zigbee is a wireless network for consumer electronics devices that is meant to be simple and low-cost[35]. | Mendez Mena et al [28] mentioned that there are threats in Zigbee-enabled systems include traffic sniffing (eavesdropping), packet decoding, and data manipulation/injection. |
| Bluetooth | Bluetooth Low Energy protocol is a short-range communication technology that saves a lot of energy [36]. There are four different access security modes available with Bluetooth which ensures privacy, authenticity and integrity of endpoint data [35]. | Bluetooth may face issue to communicate to a long distance IoT node[37]. |
| LorRAWAN | The LoRaWAN protocol offers a number of benefits in IoT applications, including low cost, low power, security, and ease of implementation [38]. Additionally, LoRaWAN provides two -layer security which provides confidentiality, integrity and authenticity [39] |
There are weaknesses of LoRaWAN v1.0 such as the bit-flipping attack, in which an attacker can alter the content of a message over the connection between the network server and the application server [40] |
| Communication Protocol | Advantages | Disadvantages |
|---|---|---|
| MQTT | MQTT is a low-power, low-bandwidth protocol commonly utilized by IoT devices[42]. It provides data confidentiality, authentication for the security mechanism [28]. | MQTT protocol does not provide encrypted connection[28]. In MQTT Authentication is accomplished with a basic username and password combination, which is sent in plaintext [27]. So, according to [43] MQTT offers basic and unsecure communication methods. |
| CoAP | For communication, CoAP provides data confidentiality and integrity, authentication, non-repudiation, and replay protection [33]. | CoAP protocol is running over UDP, and data transmission is not reliable [44]. CoAP only allows four types of messages and the packet size shorter than MQTT. |
| AMQP | AMQP protocol for the establishment of secure, scalable, and advanced clustering messaging infrastructures over an ideal network [45] | AMQP uses the Simple Authentication and Security Layer (SASL) framework for authentication. Nebbione et al. [46] mentioned on their paper that according to the NVD database, a wide range of vulnerabilities in AMQP-based products and services have been found in the last few years. |
| DDS | Concerning security DDS supports DDS and TLS for ensuring confidentiality, integrity and authenticity in communication [46] | Michaud et al [47] shared in their paper that sometimes in DDS system, node misconfiguration can be utilized to carry out malicious operations. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).




