Submitted:
18 July 2024
Posted:
18 July 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Literature Review
2.1. IoT Security Challenges
2.1.1. Overview of IoT Security Landscape
2.1.2. Common Vulnerabilities in IoT Devices
2.1.3. Attacks on IoT Devices
2.2. Hardware Trojans (HT)
Definition and Classification of HTs
- Alteration of functionality: This causes the circuit to perform unauthorized operations such as encryption algorithm bypassing, privilege escalation, and denial of service.
- Degraded performance: This can potentially jeopardize the critical system through the induced electromigration of wires caused by continuous DC stress, increased or decreased path delay, and fault injection.
- Information leakage: This undermines the security provided by cryptographic algorithms or directly leaks sensitive data handled by an integrated circuit (IC). This could include the disclosure of cryptographic keys or other sensitive information via debugging or I/O ports and side channels (e.g., delay, power).
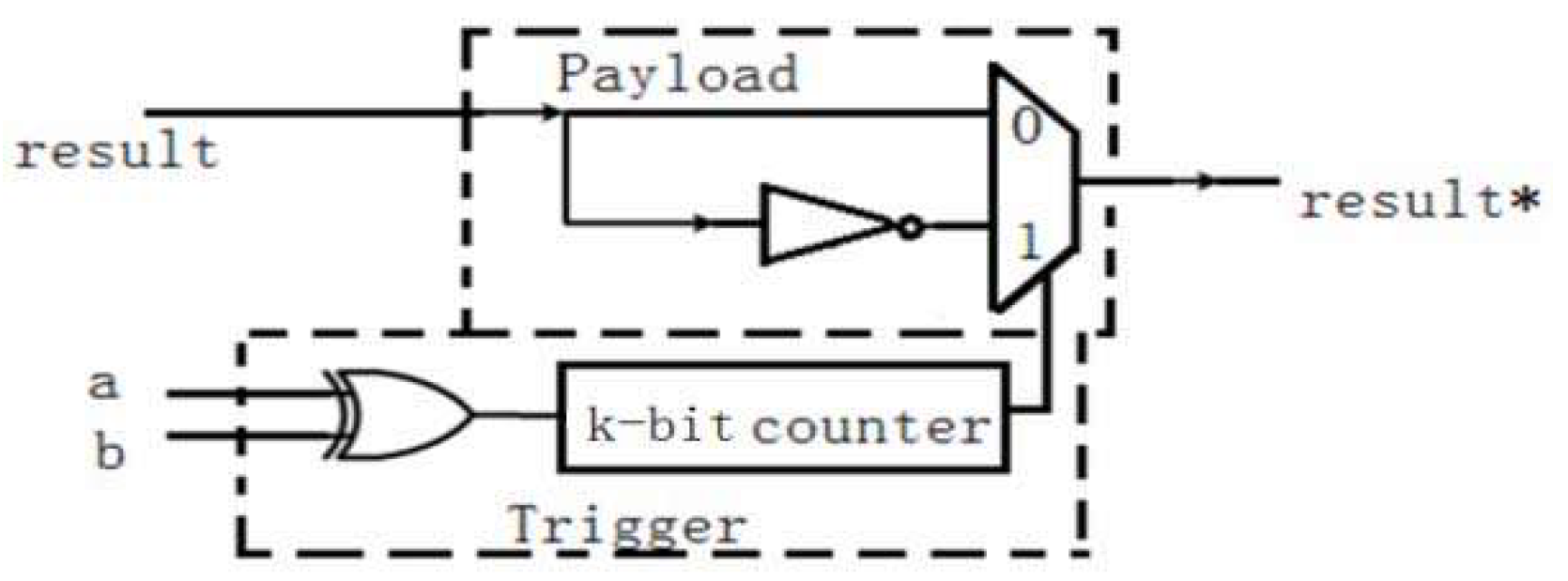
- Combinational: A trigger is taken from a circuit’s primary inputs and/or internal nodes, and a payload can be activated once the trigger is asserted. Any Trojan design can be classified as a Type-p Trojan based on p-trigger inputs. An AND gate with p-inputs can be used to create the most basic trigger form. Any other combinational logic can also be used as a trigger to result in a different logic when activated.
- Sequential: The payload is delivered when a sequence of input patterns occurs or a period is triggered. To accomplish this goal, the trigger design of a sequential Trojan incorporates state elements and combinational logic. The payload is delivered only when the counter reaches its maximum count or when the Finite State Machine (FSM) for the counter reaches its final state in the first approach. Because specific test patterns or inputs are unlikely to occur consecutively multiple times during testing or normal operations on IC, this property of sequential Trojan makes detection even more difficult.
- Analog (RF Trojan): The trigger circuit is designed with capacitors that are activated by accumulating the charge from the toggling of a nearby victim wire that exceeds a specified threshold.
2.3. Detection Mechanisms for Hardware Trojans
2.4. Honeypots
-
Purpose-Based:
- Research Honeypot: A research honeypot is designed to gather information about the specific methods and techniques used by adversaries as well as to identify potential vulnerabilities within the system related to these tactics. Typically, research honeypots are more complex than production honeypots are.
- Production Honeypot: The common type of honeypot is the production honeypot. Businesses use this decoy to gather information and intelligence regarding cyberattacks on their production networks. The collected data can include IP addresses, intrusion attempt times and dates, traffic volume, and other attributes. Production honeypots are relatively simple to design and deploy, but they produce less sophisticated intelligence than research honeypots.
-
Levels of Interactivity-Based:
- Low-Interaction Honeypot: Low-interaction Honeypots use a small number of resources to simulate parts of a system’s software or network services while gathering basic information about the attacker. Because of their limited capabilities, attackers cannot escape emulation; thus, no host system can be compromised. The vast majority of production honeypots have low-interaction. HoneyD is one of the most popular low-interaction honeypots.
- High-Interaction Honeypot: A high-interaction honeypot represents the other end of the spectrum in deception technology. Without a simulation, high-interaction honeypots use a comprehensive operating system. They are difficult to maintain and sophisticated, and are designed to keep hackers occupied for long periods by utilizing a network of exploratory targets, such as several databases. This provides the cybersecurity team with a better understanding of how these attackers operate, their tactics, and even hints as to who they are [34,35].
-
Implementation Based:
- Physical Honeypot: The term “physical honeypot” or “hardware honeypot” refers to a honeypot powered by a physical mechanism. It is running on a real machine connected to the network using its assigned IP address. Physical Honeypot generally suggests a high level of engagement, which allows the system to be entirely compromised.
- Virtual Honeypot: Virtual Honeypots can combine different levels of interactivity as they can host more than one honeypot and control the number and characteristics of the ones deployed. This can be more cost-efficient and less time consuming [36].
2.5. Analysis and Gaps
3. Proposed Approach
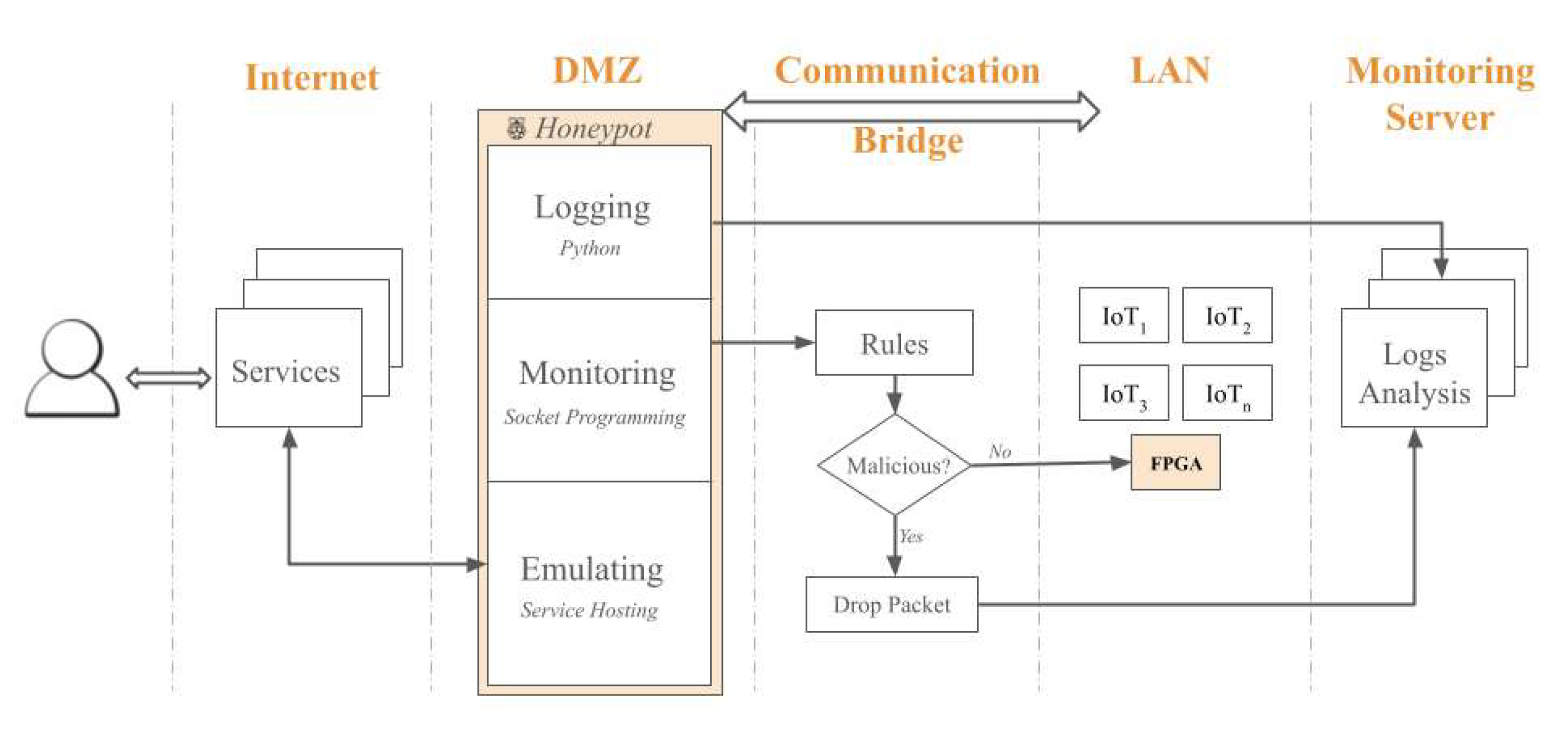
3.1. Honeypot Design Architecture
- Emulation Layer: Simulates various IoT device vulnerabilities.
- Monitoring Layer: Tracks interactions with the honeypot.
- Logging Layer: Records data about the attacks for further analysis.
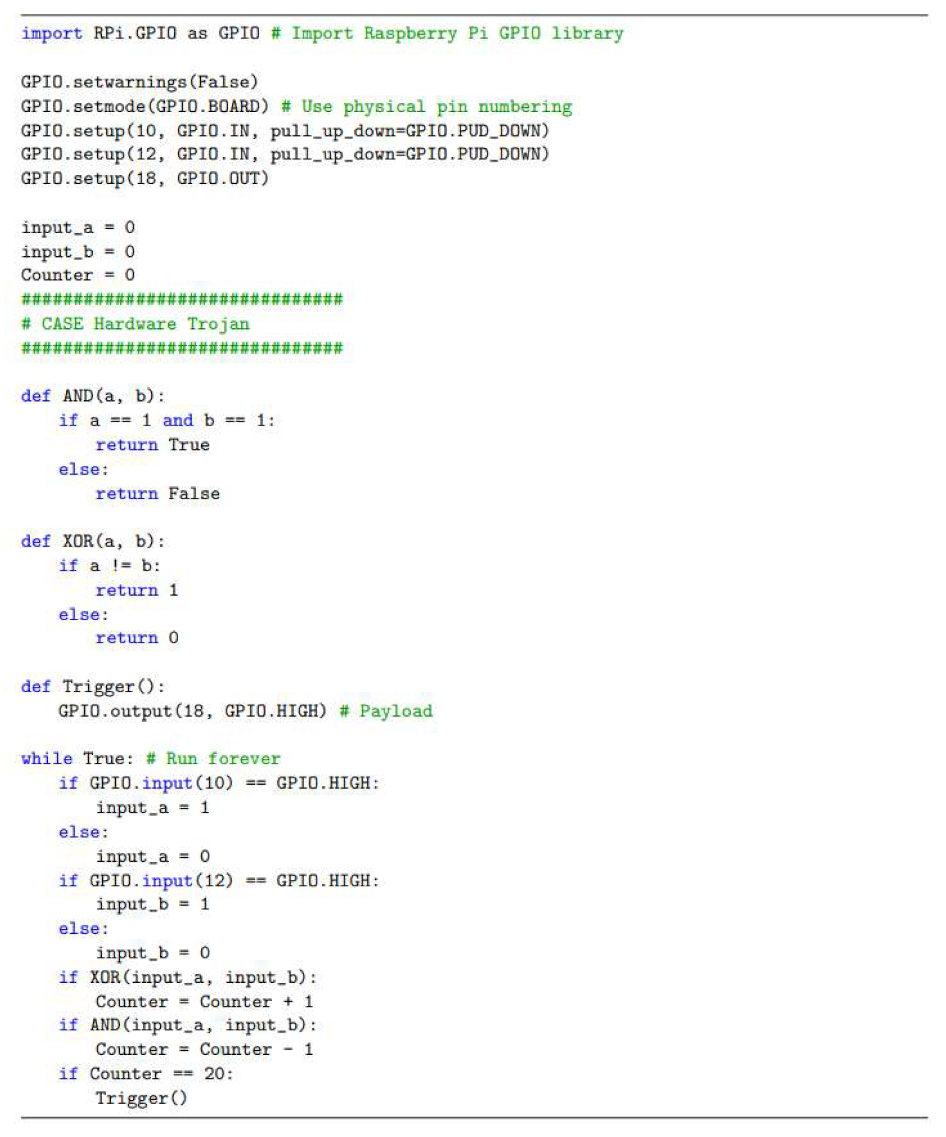
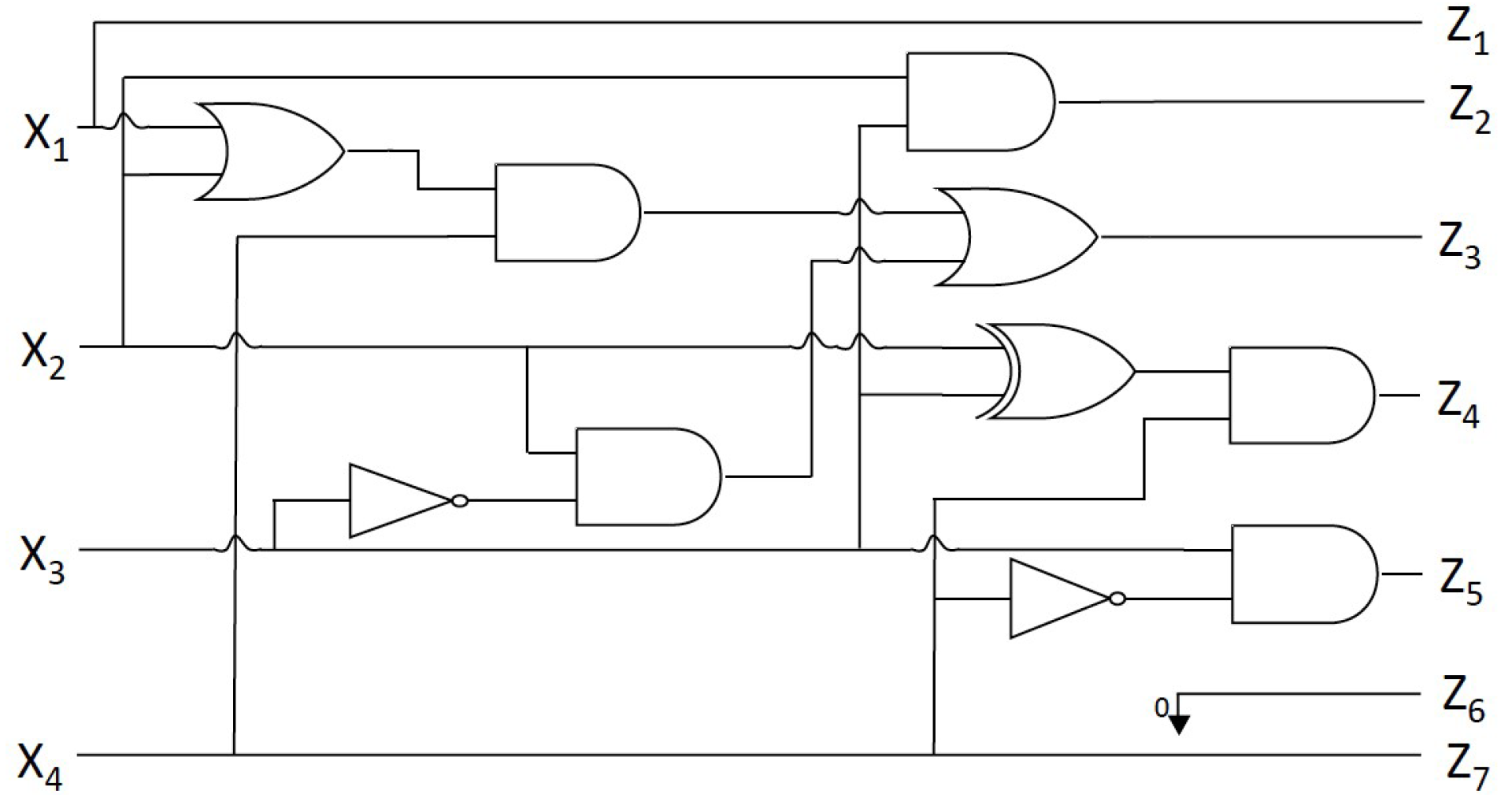
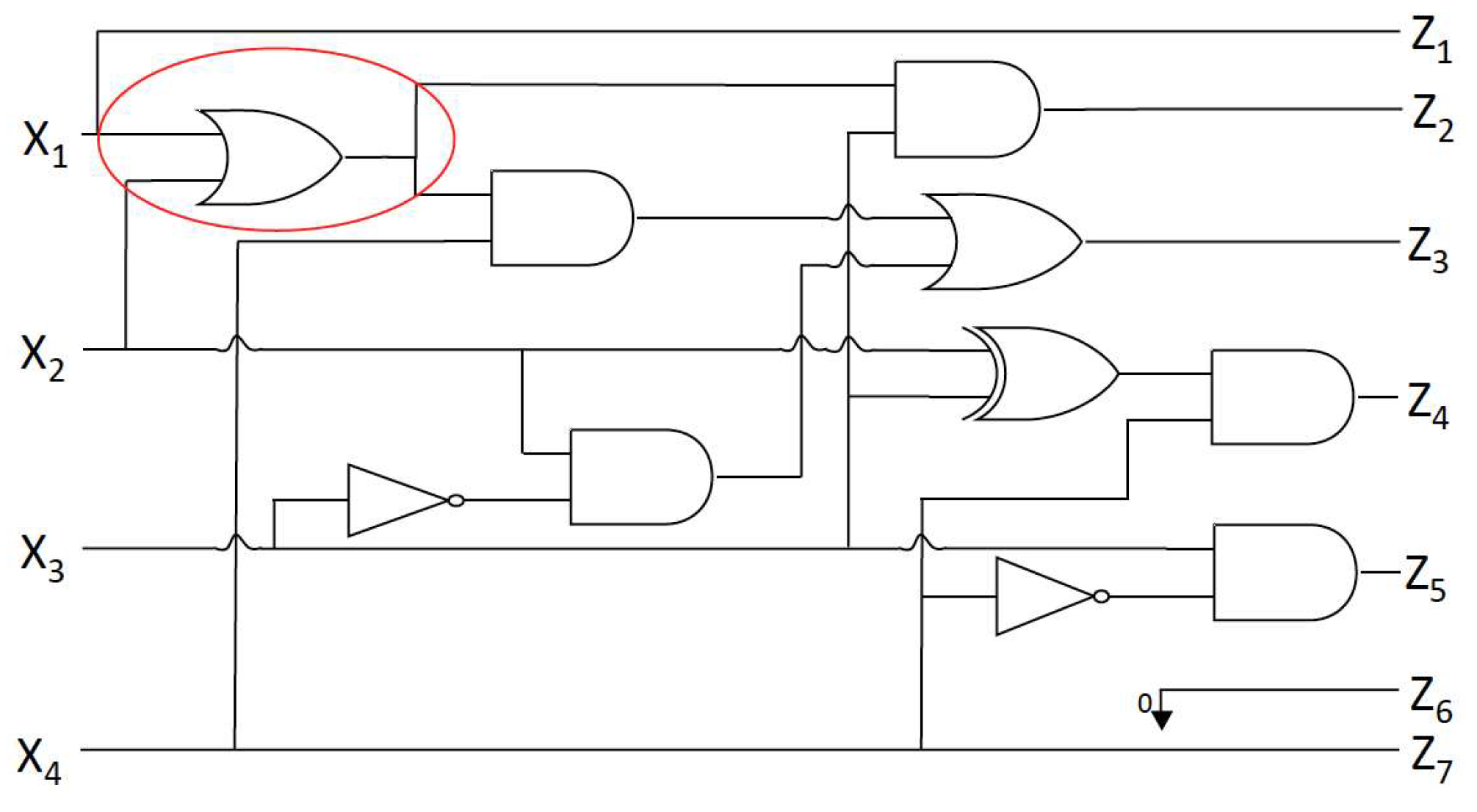
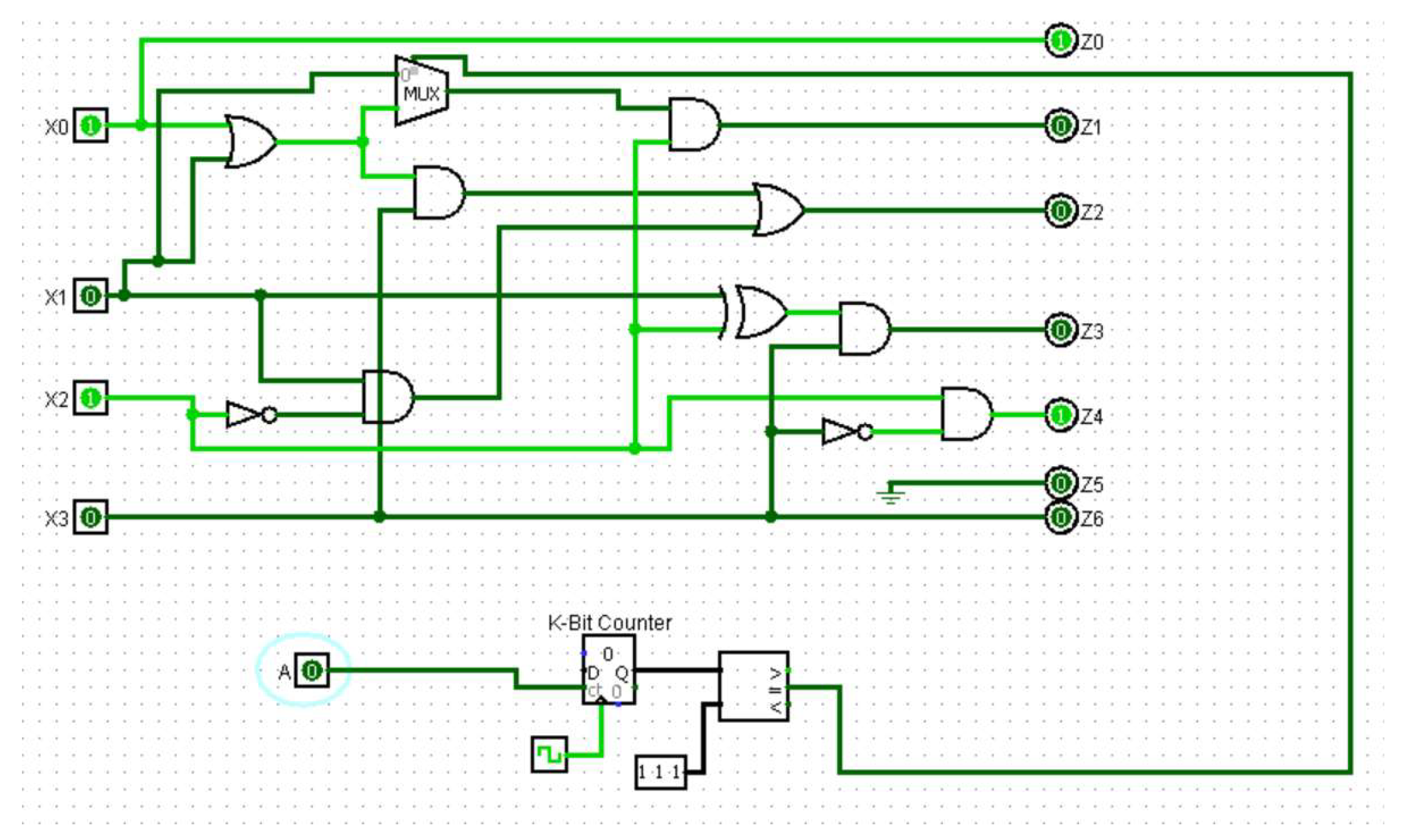
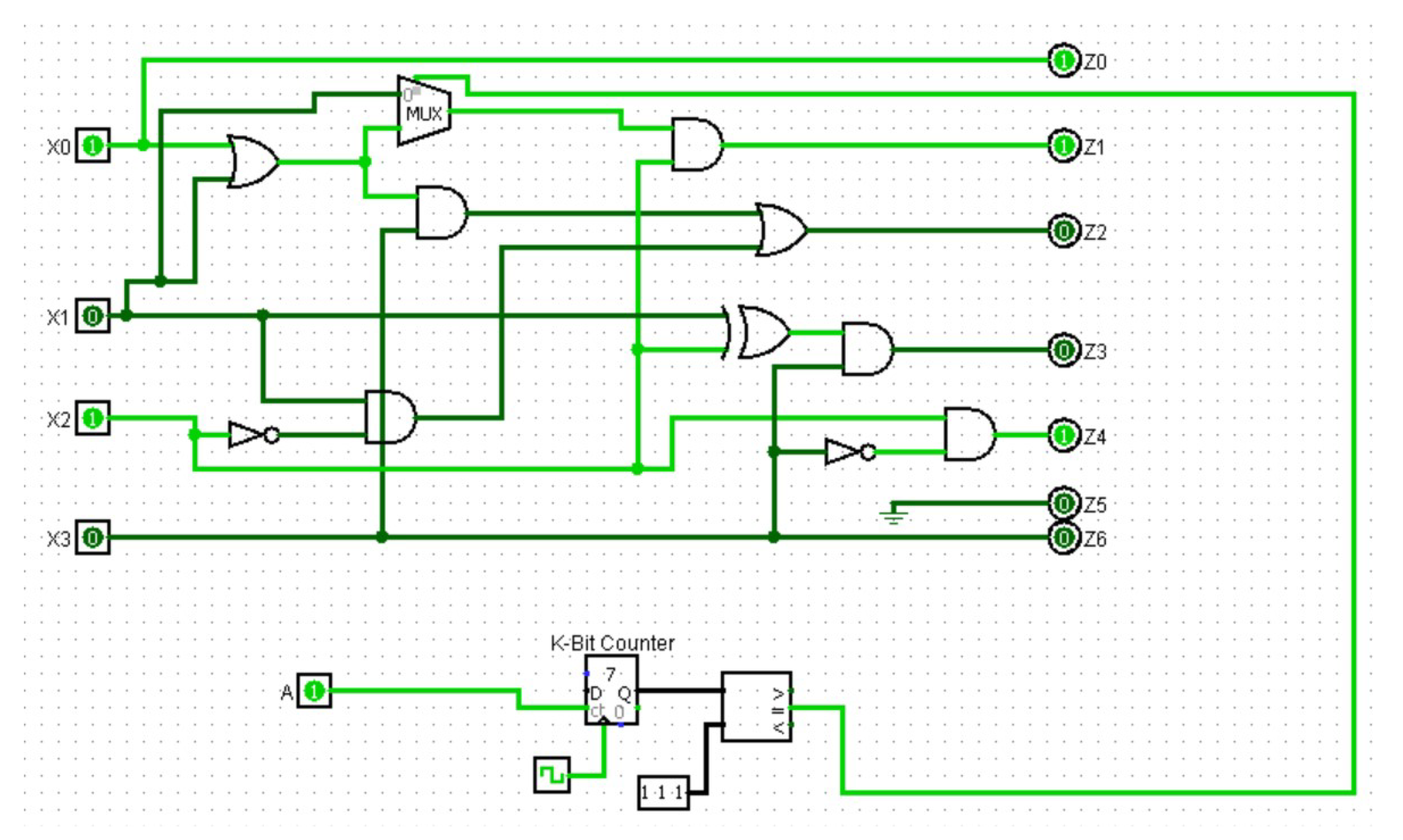
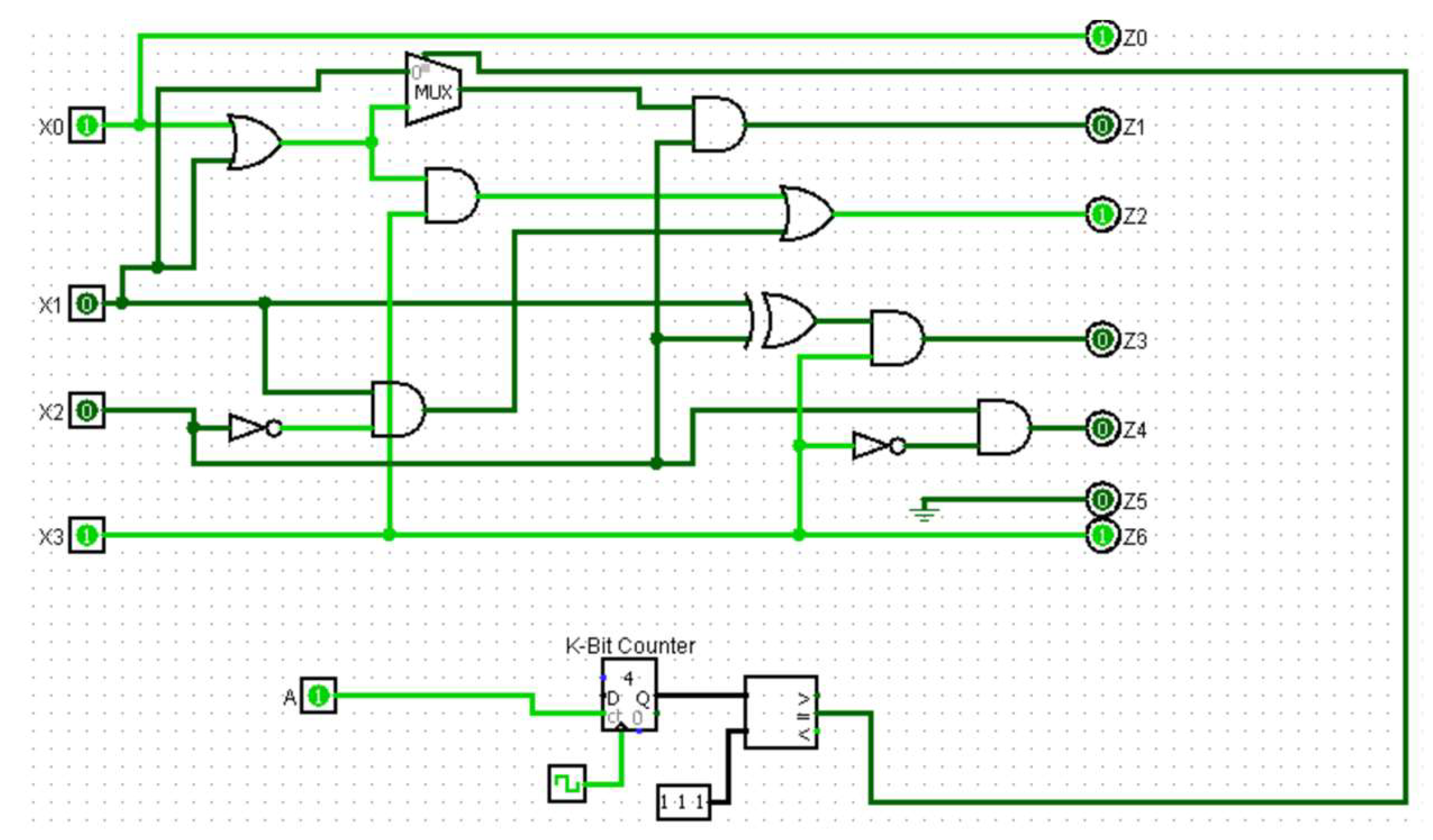
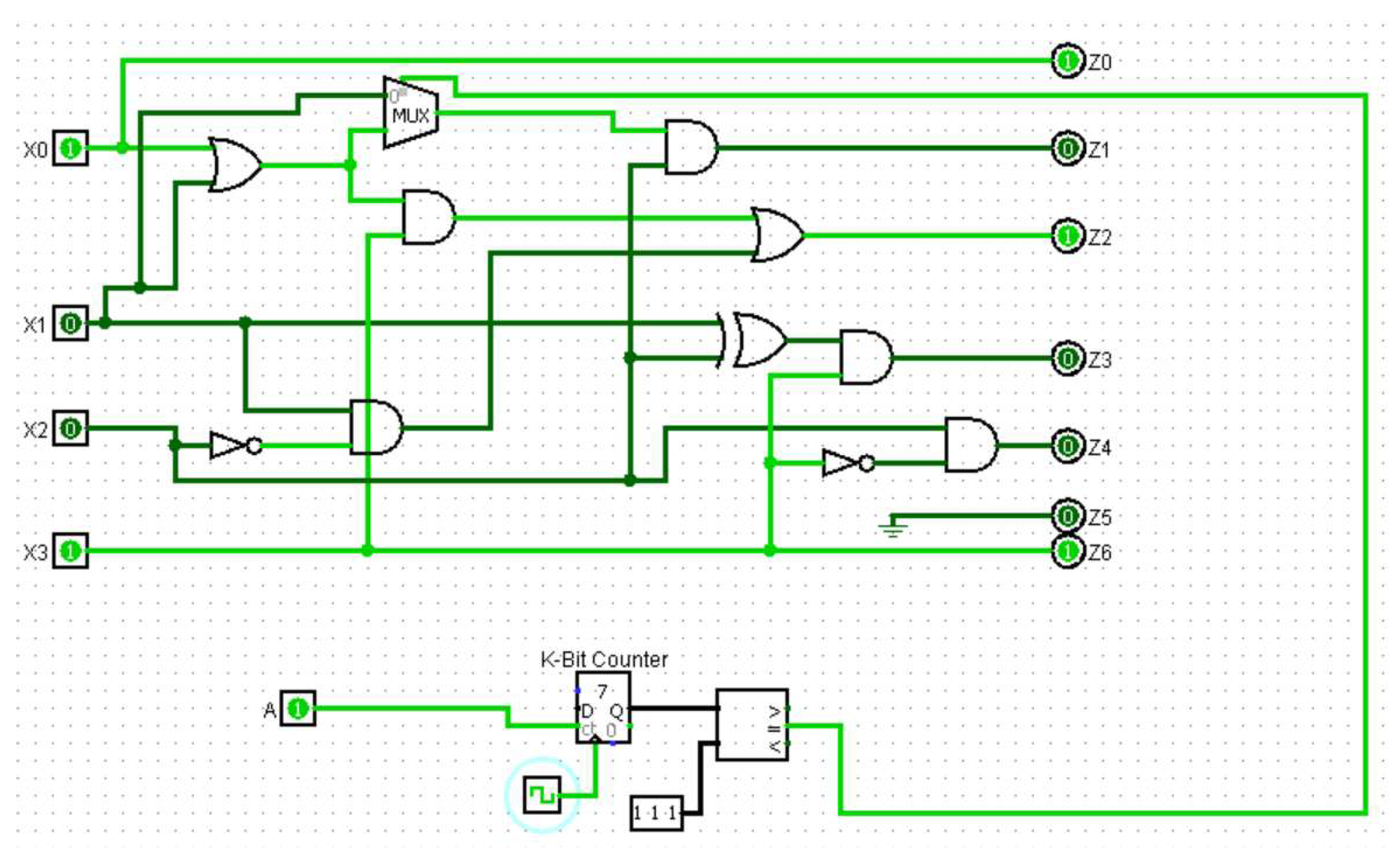
3.2. HT Design
- Internal triggers: These Trojans are conditional, such as a ticking time bomb, using counters to compute the execution of an instruction or physical conditions, such as tampering with the internal temperature of the components.
- External triggers: These Trojans can be activated remotely by an attacker based on external factors, such as the user entering a specified input (cheat code) or a component returning a specific output.
4. Experimental Setup
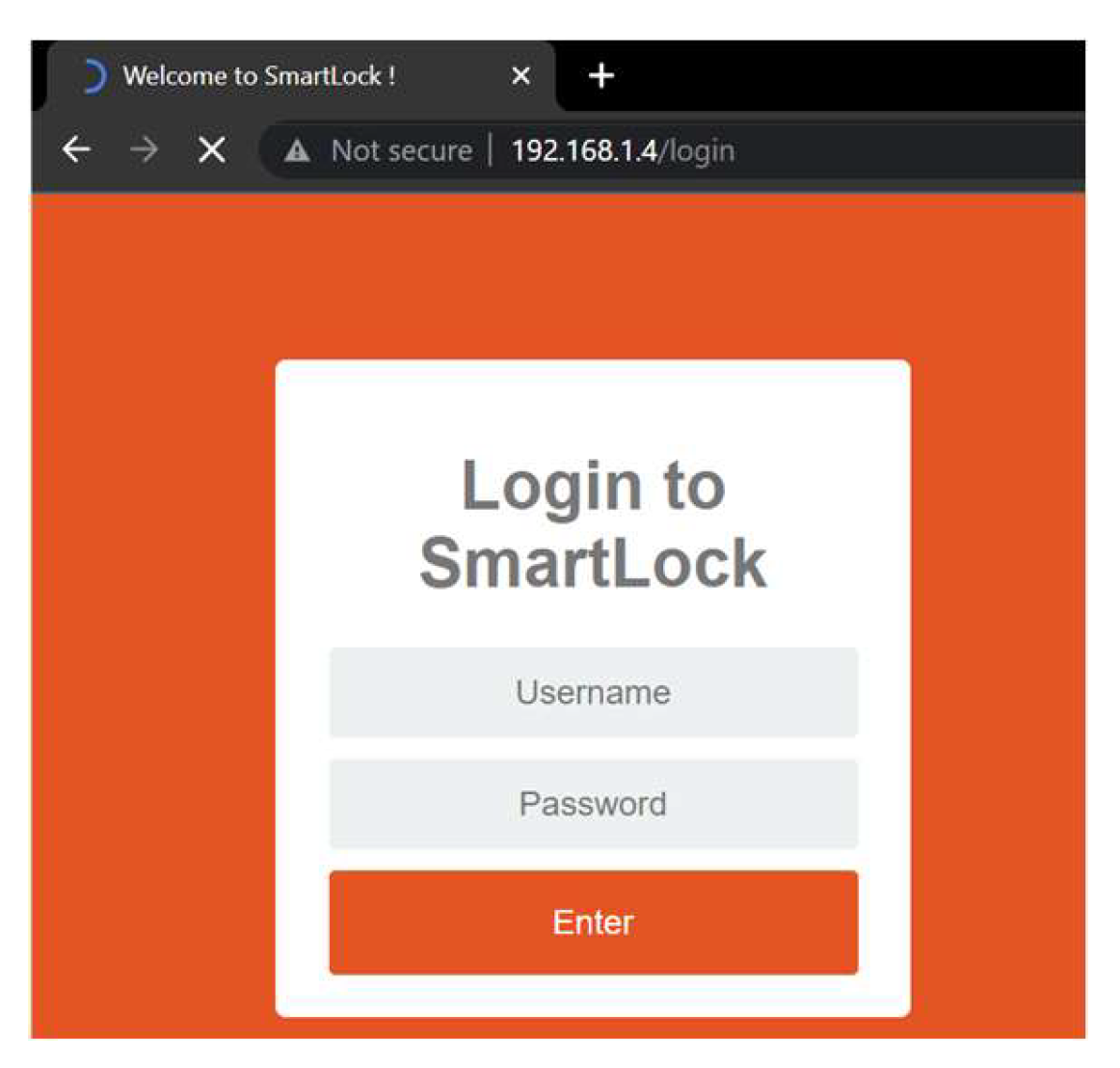
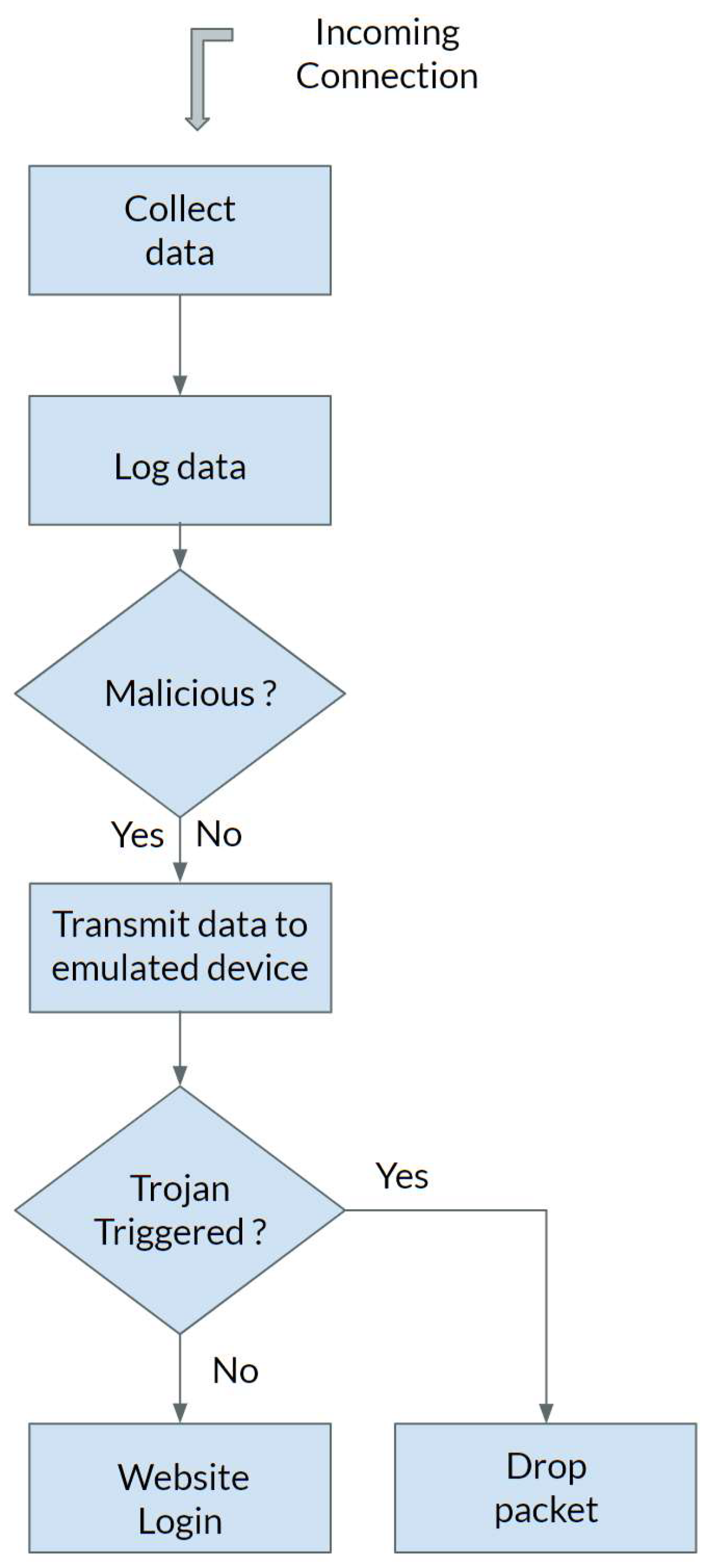
4.1. Honeypot
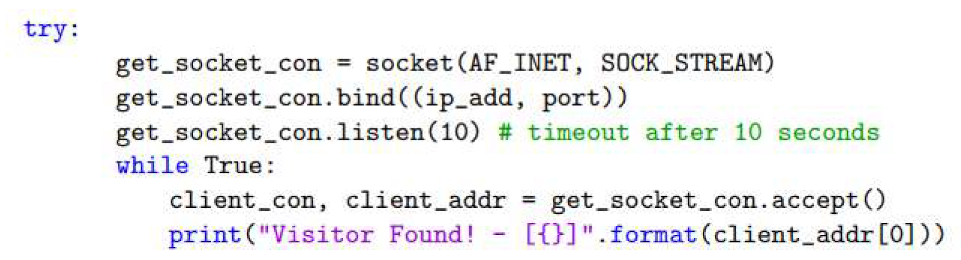
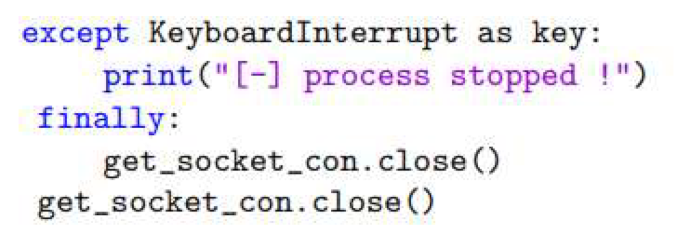
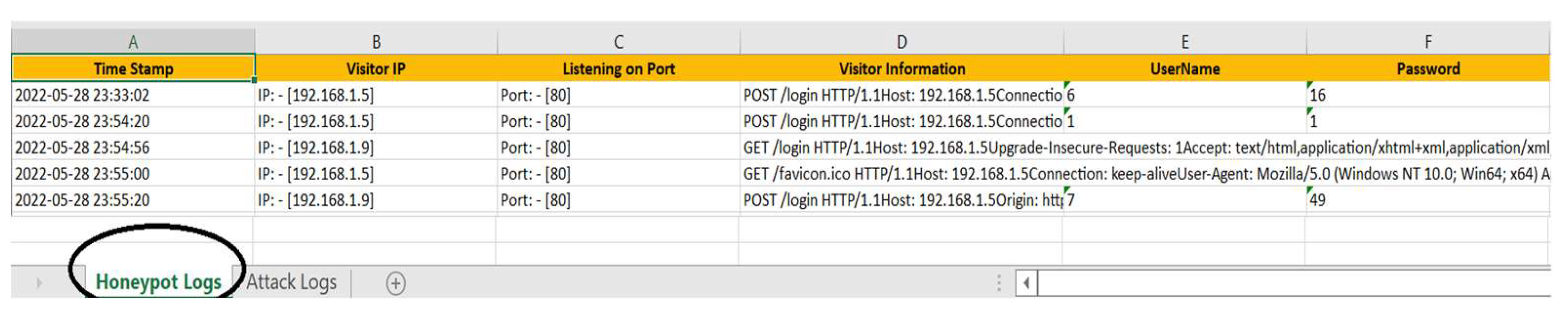
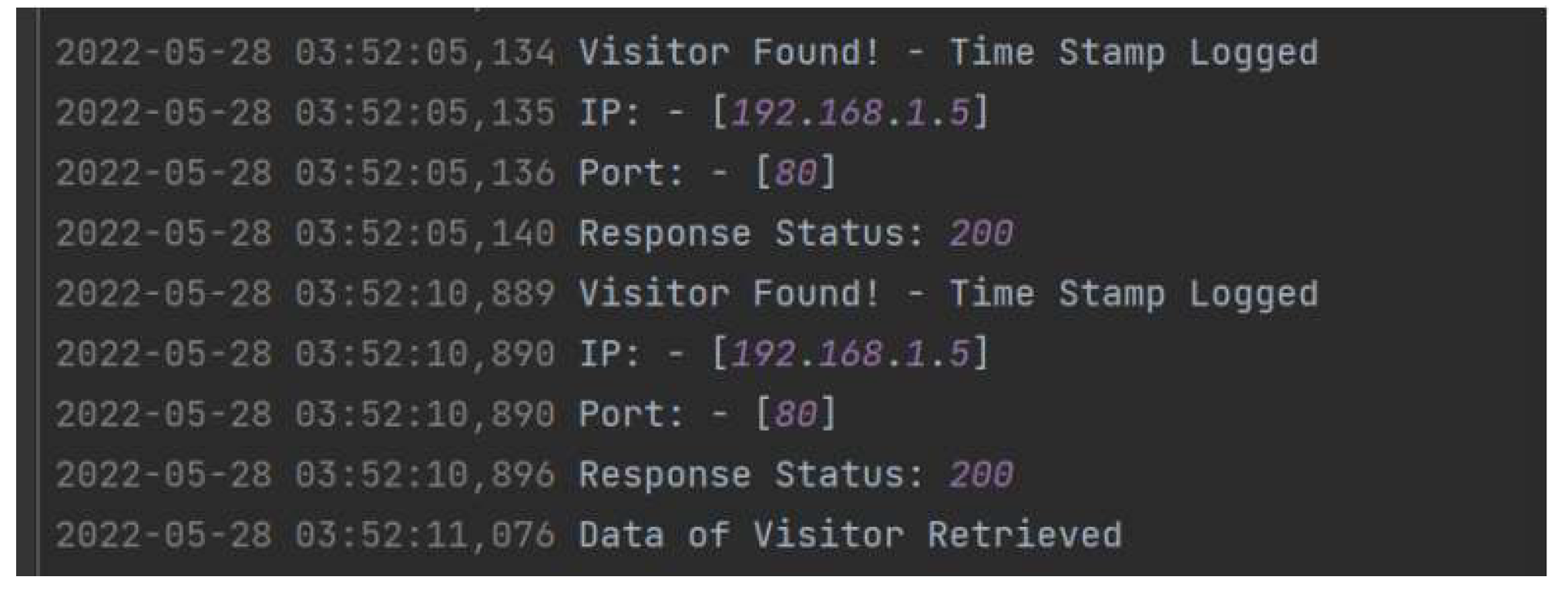
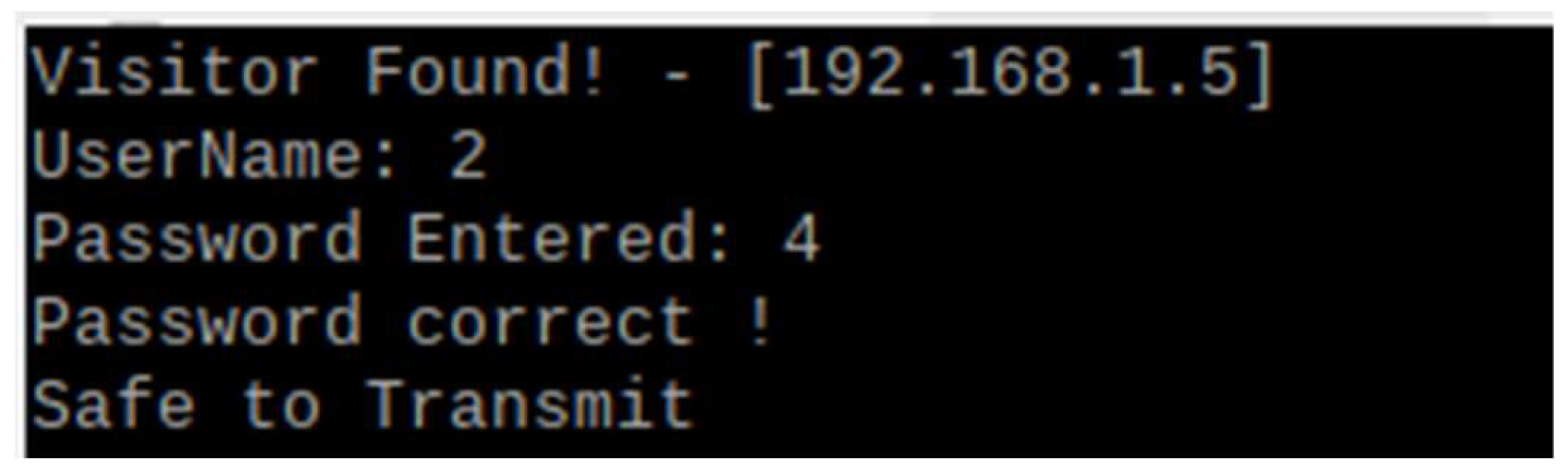
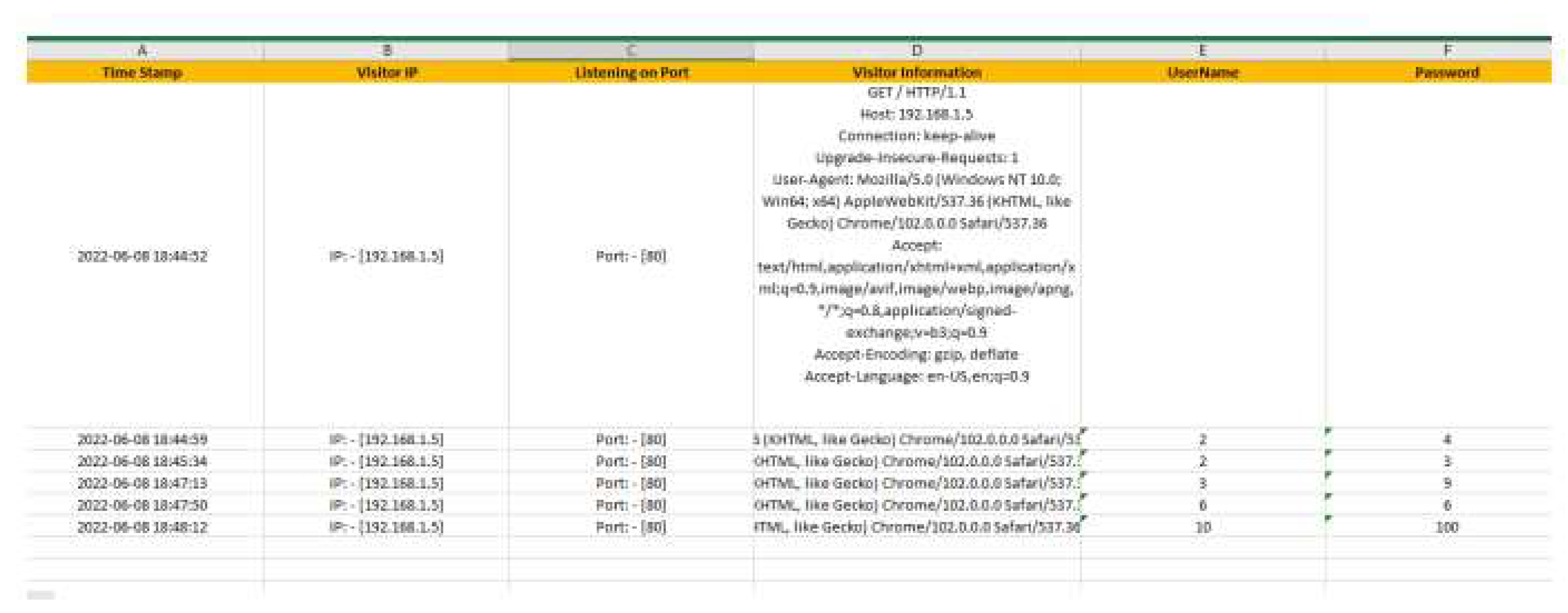
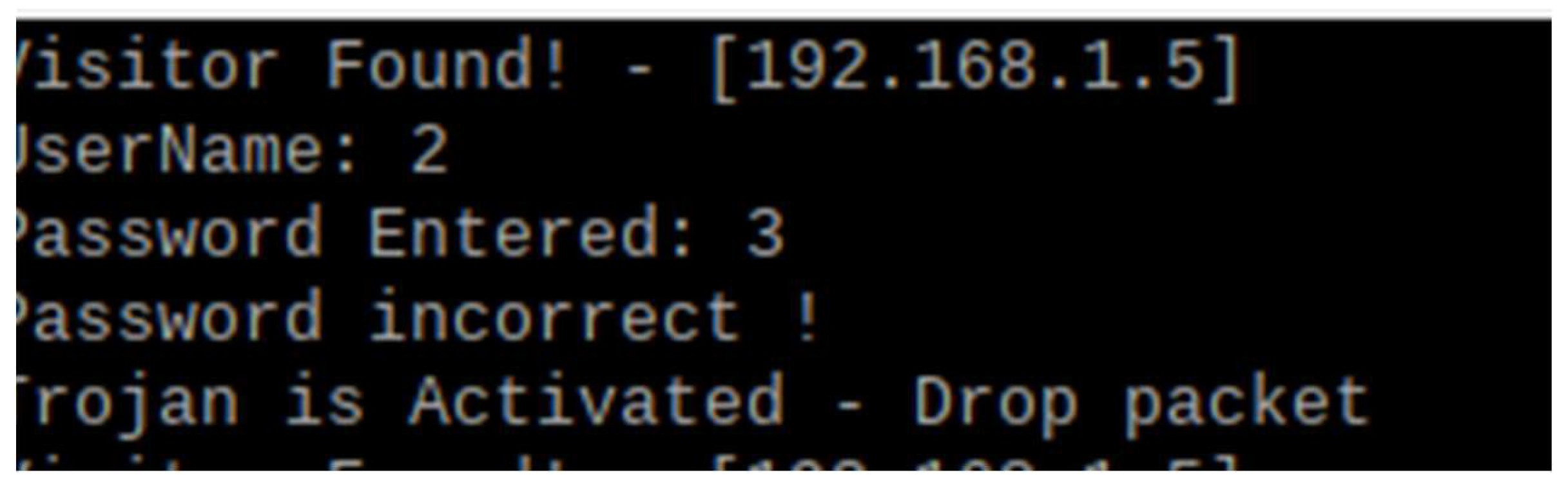
- Time Stamp: The exact time a connection was made.
- Visitor IP: The IP address of the suspicious device.
- Listening on Port: The vulnerable port accessed on the honeypot.
- Visitor Information: Details about the type of connection made.
- Username: The username entered on the website.
- Password: The password entered on the website.
4.2. Hardware Trojan
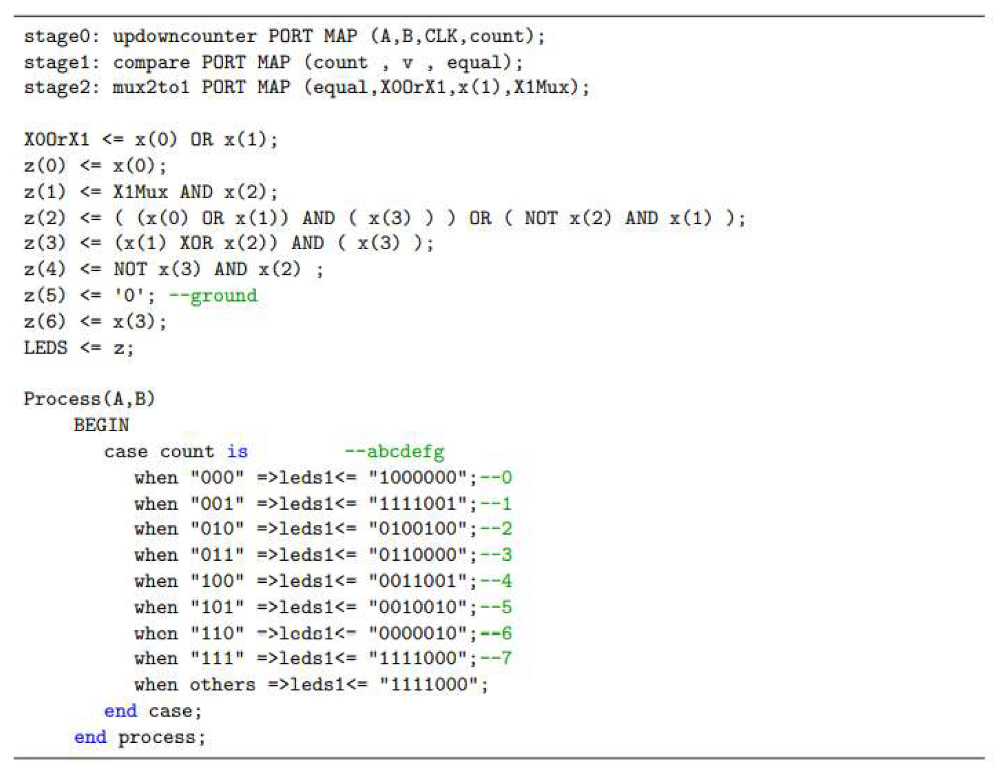
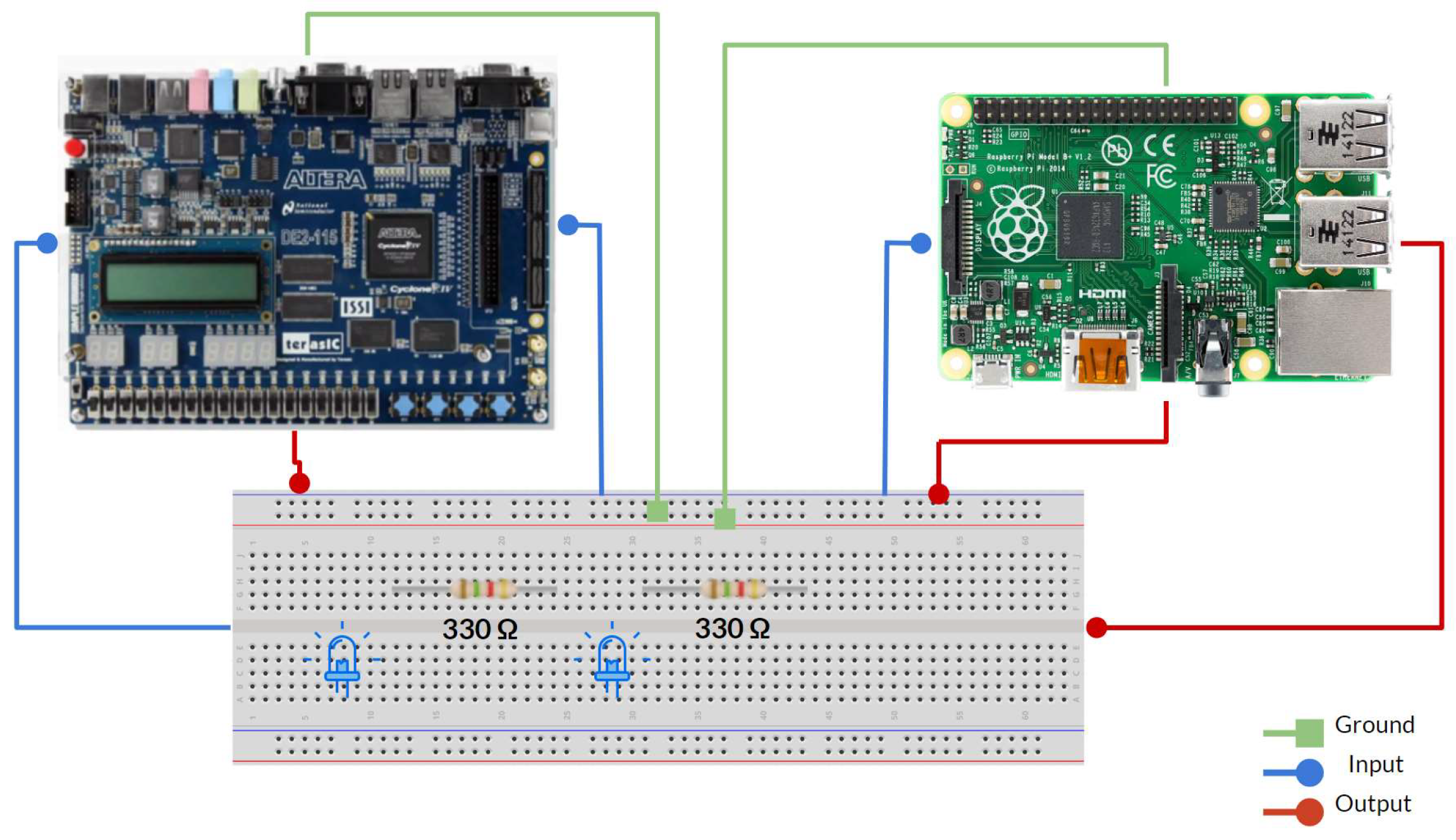
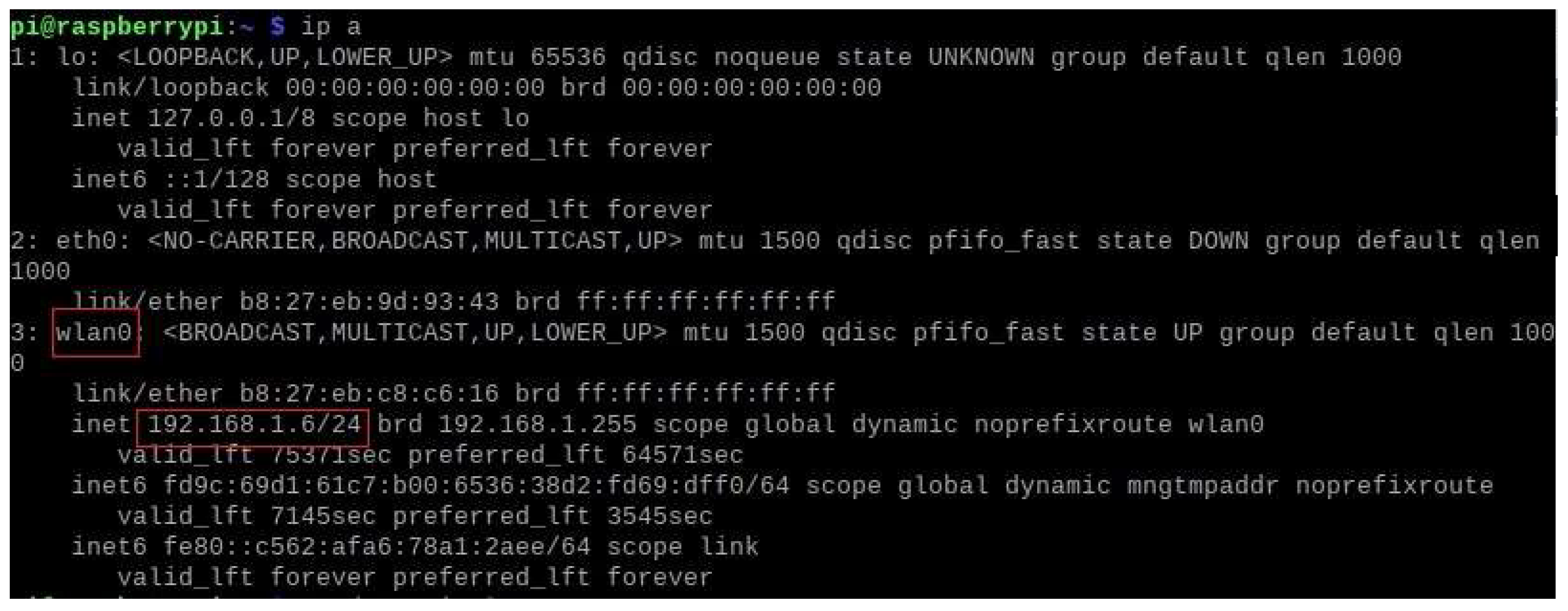
4.3. System Integration.
-
Inputs:
- ∘
-
FPGA:
- ▪
- Pin ‘AB 22’ is used for transmitting the result of XORing values A and B.
- ▪
- Pin ‘Y 17’ determines whether access is authorized. Authorized access occurs when the password entered on the website matches the correct password generated for the username and the Trojan has not been triggered. Failure to meet any of these conditions results in unauthorized access.
- ∘
-
Raspberry Pi:
- ▪
- Pin 37 is used by the FPGA to alert the honeypot of a malicious packet if a Trojan has been triggered.
-
Outputs:
- ∘
-
FPGA:
- ▪
- Pin ‘AC 215’ is used to report back to the honeypot that the Trojan is activated.
- ∘
-
Raspberry Pi:
- ▪
- Pin 40 is used to send the result of the XOR function to the FPGA.
- ▪
- Pin 35 is used to compare the password entered on the website with the correct password generated for the username.
- Resistors: As a result of the DE2-115 board I/O standard mismatch, 330 Ω pull-down resistors were used to compensate for the mismatched GPIO pin differences.
- LEDs: Used for testing and debugging purposes.
5. Results and Discussion
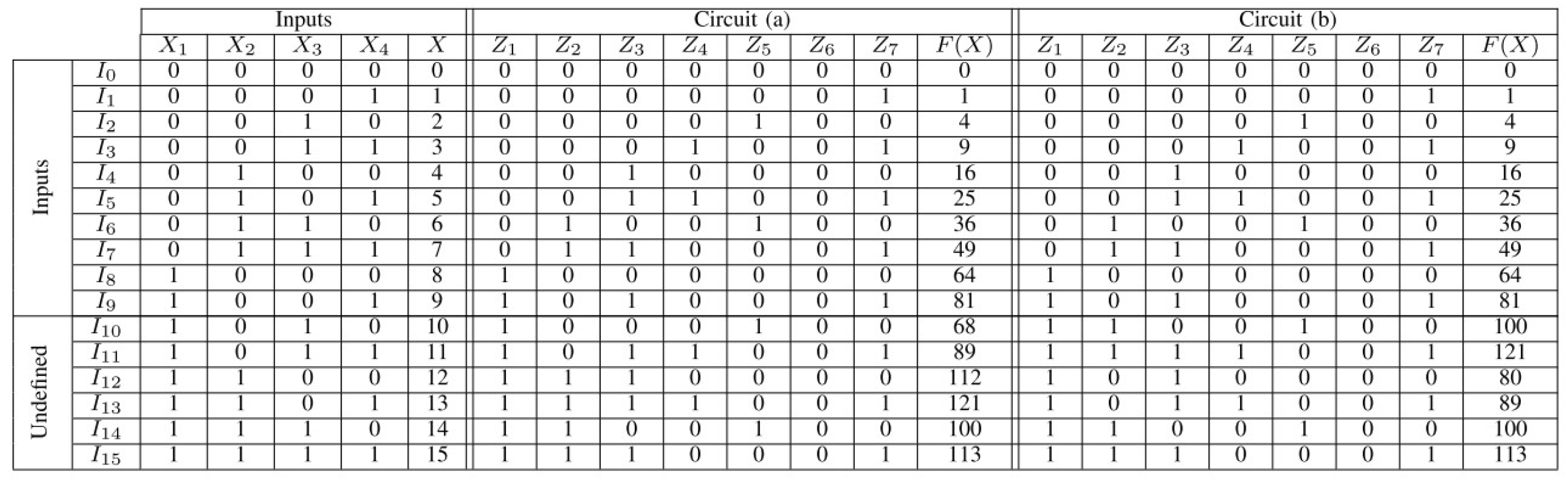
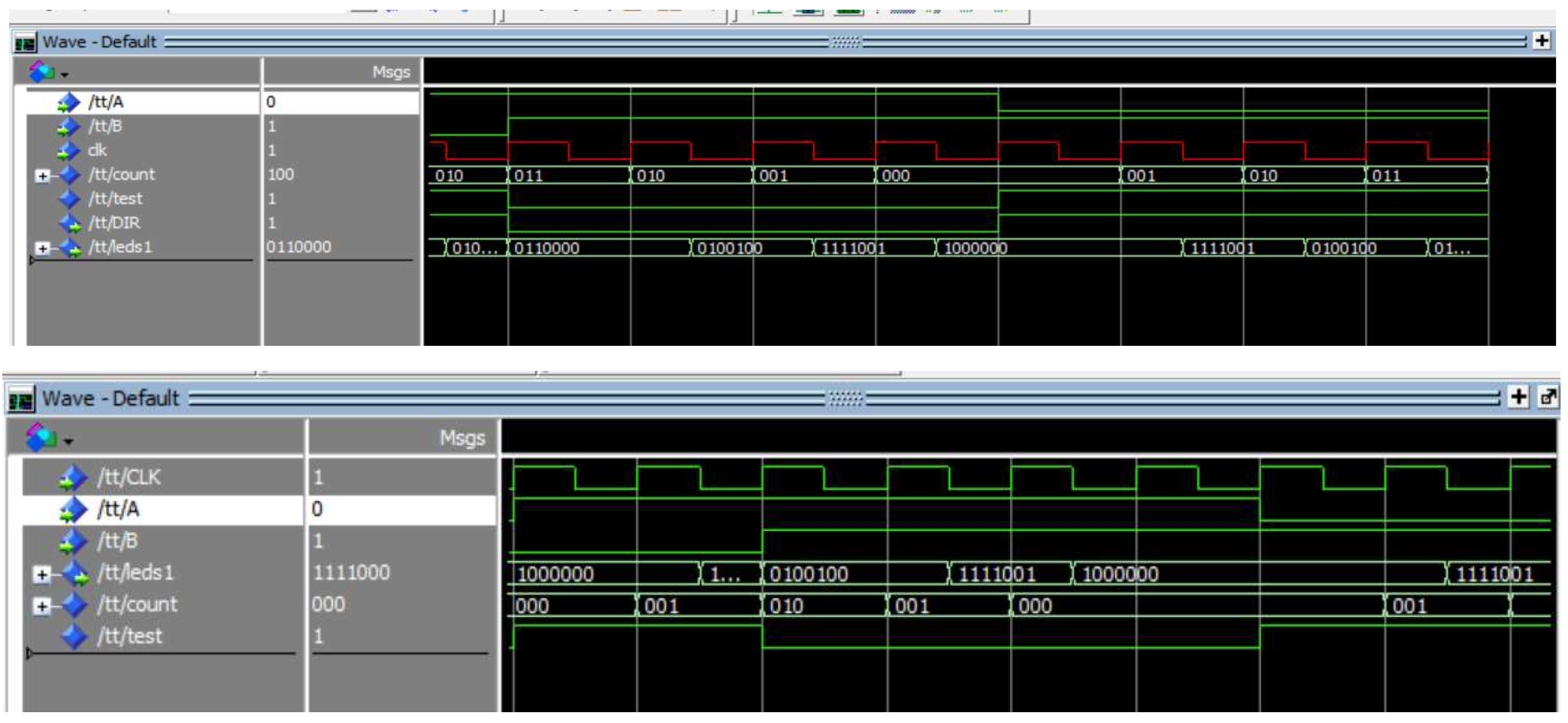
5.1. Emulating the Hardware Trojan
5.2. Evasion Testing
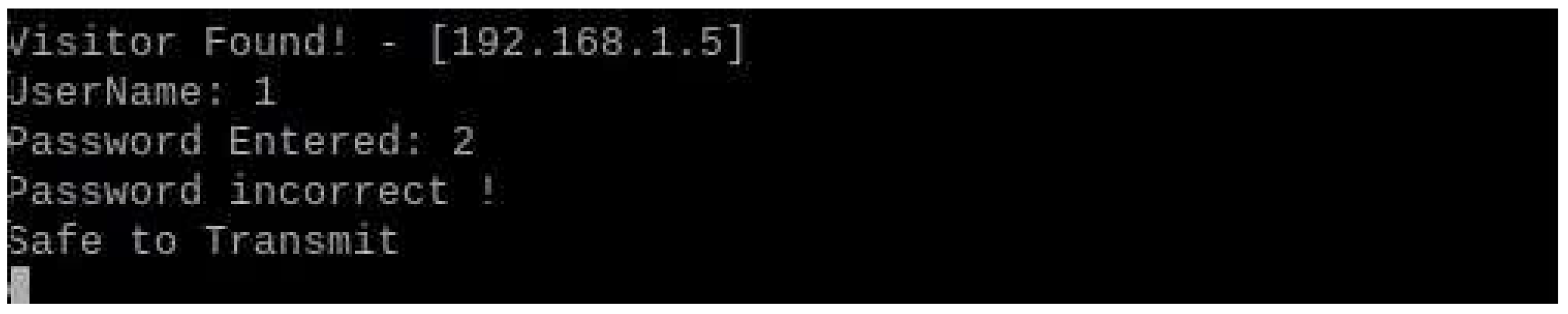
5.2.1. Authorized Attacks
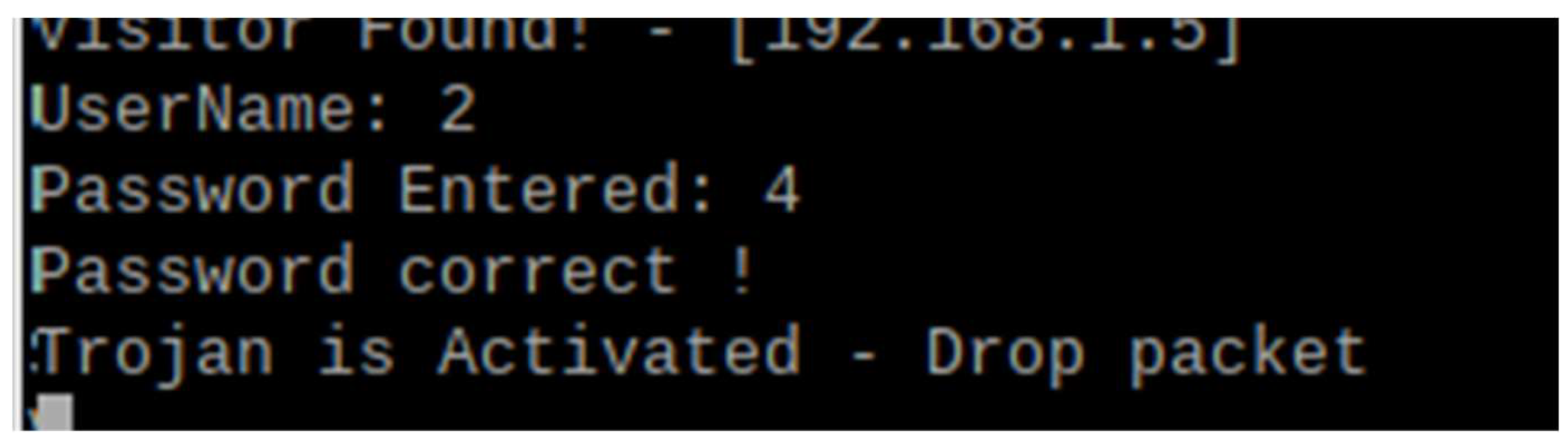
5.2.2. Unauthorized Attacks
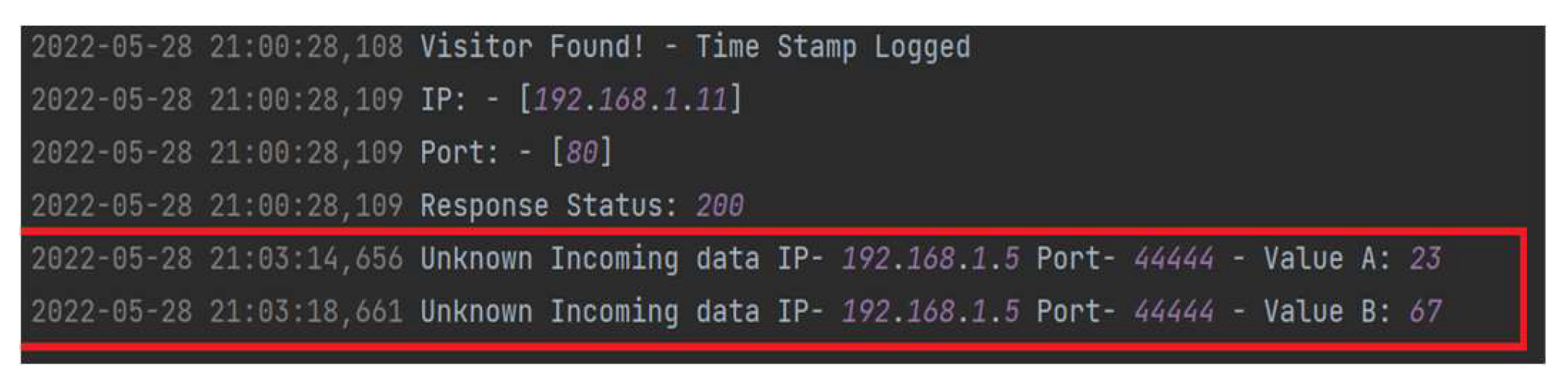
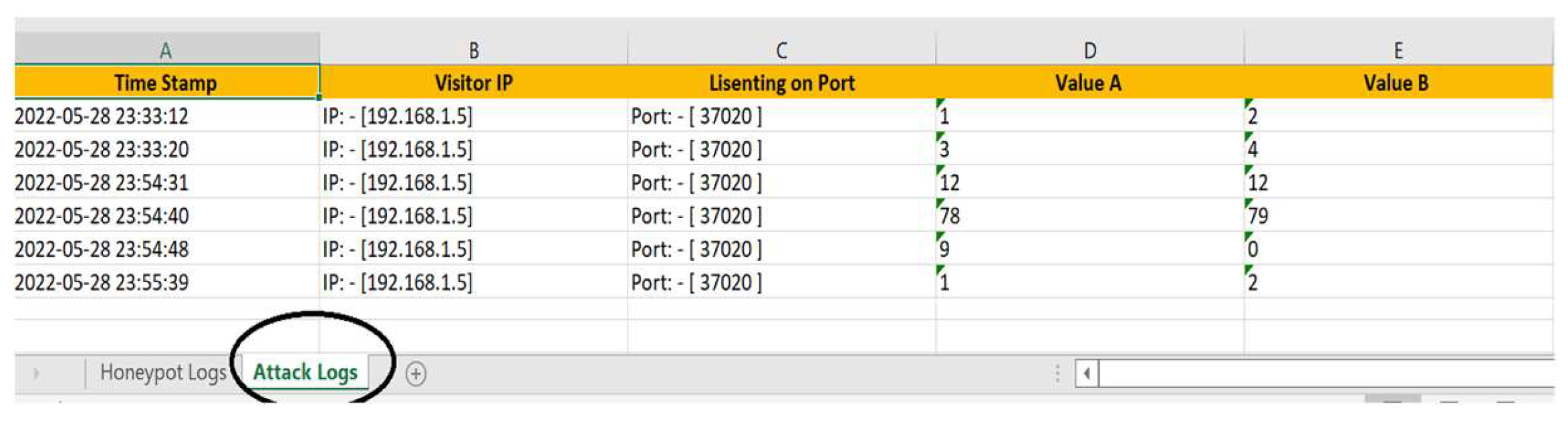
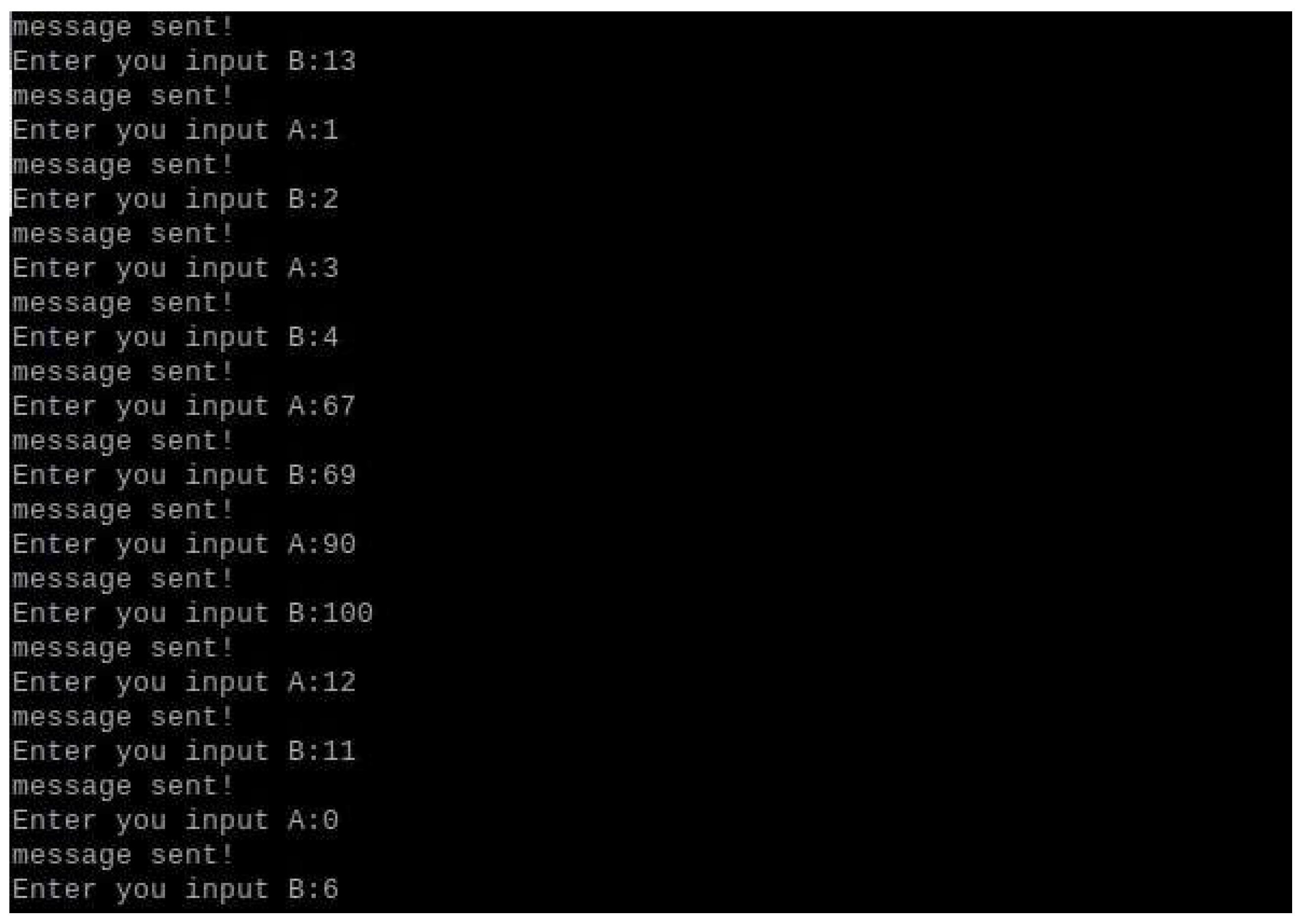
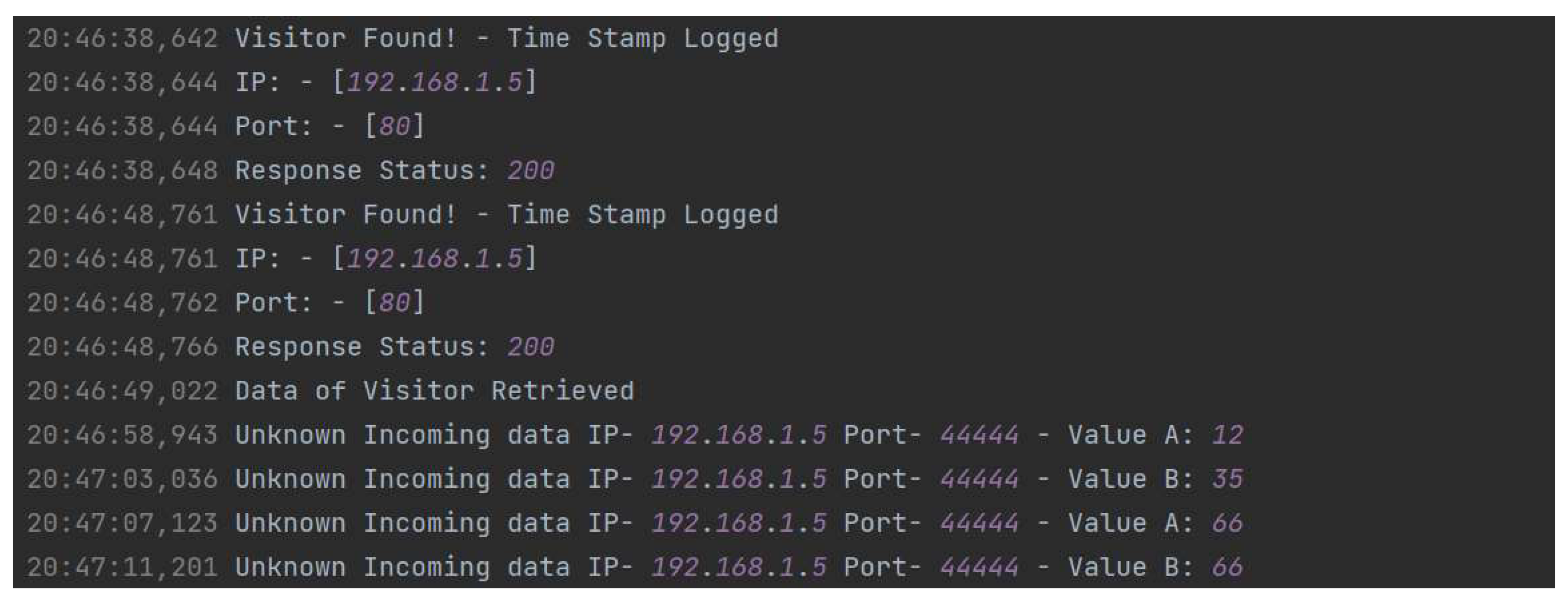
5.2.3. Triggering Attacks
5.2.4. Non-Triggering Attacks
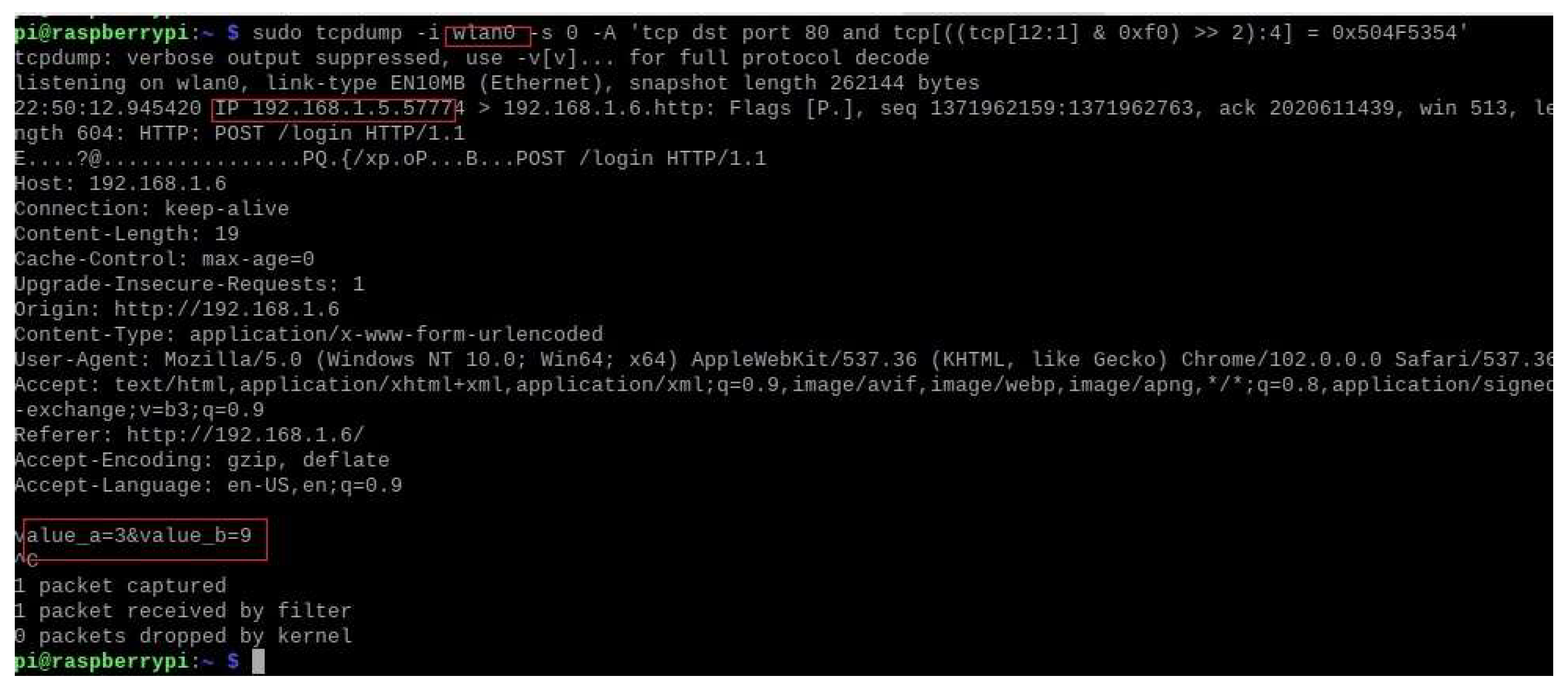
5.3. TCPdump
5.4. Analysis
6. Conclusion and Future Work
6.1. Main Contribution
6.1.1. Effectiveness of Hardware Honeypots
6.1.2. Hardware Trojan Detection and Prevention
6.1.3. Analysis of Attack Scenarios
- Authorized Attacks: The system’s response to authorized attacks is both effective and efficient. Logging every attempt and verifying credentials ensured that only valid access was granted. This verification process also included a fallback mechanism that prevented unauthorized access, even with valid credentials, highlighting the robustness of the security measures in place.
- Unauthorized Attacks: In scenarios involving unauthorized access attempts, the honeypot’s logging and redirecting capabilities are critical. Immediate feedback and logging of unauthorized entries allowed real-time monitoring and a potential rapid response. This capability is crucial for identifying and mitigating potential threats before vulnerabilities can be exploited.
- Triggering Attacks: The results of triggering attacks are particularly noteworthy. The system’s ability to activate the HT only when a specific condition was met (e.g., a counter reaching seven) ensured that false positives were minimized. This selective activation mechanism is crucial for maintaining the reliability and availability of IoT devices that are often subjected to numerous benign inputs that do not trigger security measures.
- Non-Triggering Attacks: For non-triggering attacks, the system effectively logged all attempts and maintained normal operation without activating the Trojan. This capability underscores the system’s reliability in distinguishing between benign and malicious inputs, further enhancing its overall security.
- TCPdump and Packet Analysis: The deployment of TCPdump for capturing incoming HTTP POST requests provides an additional layer of network security monitoring. The successful installation and testing of the TCPdump demonstrated its capability to log and analyze network traffic in real-time. This tool proved invaluable in identifying and documenting malicious attempts to access IoT devices, thereby providing a comprehensive view of the network’s security landscape. The logs captured from ports 80 and 44444 offered detailed insights into the nature and frequency of access attempts, informing further security enhancements.
6.2. System Limitations and Future Work
- Scalability: Although the current system is effective for the tested scenarios, it may face challenges when scaled to larger networks with multiple IoT devices. Future studies should explore the integration of distributed honeypots and scalable logging mechanisms to manage larger data volumes and more complex attack patterns.
- Machine Learning Integration: Incorporating machine learning algorithms can enhance a system’s ability to adaptively respond to evolving attack patterns. By analyzing historical attack data, machine learning models can predict and preemptively mitigate new types of attacks, thereby improving the system’s proactive defense capabilities.
- High-Interaction Honeypots: Transitioning to high-interaction honeypots can provide deeper insights into attacker behavior. These honeypots, which simulate full operating systems and applications, can capture more detailed data on sophisticated attacks, thereby informing more comprehensive security strategies.
- User Experience and Usability: Enhancing the user interface to monitor and manage the honeypot system can improve its usability. Providing intuitive dashboards and real-time alerts can help security teams respond quickly and effectively to detected threats.
- Interoperability with Existing Security Systems: Ensuring that the honeypot system can seamlessly integrate with existing security infrastructure (e.g., firewalls and intrusion detection/prevention systems) will enhance its effectiveness and facilitate broader adoption in enterprise environments.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Alyasiri, H.; Clark, J.A.; Malik, A.; Fréin, R.d. Grammatical evolution for detecting cyberattacks in internet of things environments. In Proceedings of the International Conference on Computer Communications and Networks (ICCCN), Athens, Greece; 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Suber, J.G.; Zantua, M. Intelligent Interaction Honeypots for Threat Hunting within the Internet of Things. Journal of The Colloquium for Information Systems Security Education. 2022, 9, 1–5. [Google Scholar] [CrossRef]
- Khraisat, A., Alazab, A. A critical review of intrusion detection systems in the internet of things: techniques, deployment strategy, validation strategy, attacks, public datasets and challenges. Cybersecur. 2021, 4, 18, 1-27. [CrossRef]
- Kumar, A.; Abhishek, K.; Ghalib, M.R.; Shankar, A.; Cheng, X. Intrusion detection and prevention system for an IoT environment. Digital Communications and Networks. 2022, 8, 540–551. [Google Scholar] [CrossRef]
- Pa, Y.M.P.; Suzuki, S.; Yoshioka, K.; Matsumoto, T.; Kasama, T.; Rossow, C. IoTPOT: A novel honeypot for revealing current IoT threats. Journal of Information Processing. 2016, 24, 522–533. [Google Scholar] [CrossRef]
- Almohannadi, H.; Awan, I.; Al Hamar, J.; Cullen, A.; Disso, J.P.; Armitage, L. Cyber Threat Intelligence from Honeypot Data Using Elasticsearch. In Proceedings of the 2018 IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA), Krakow, Poland; 2018; pp. 900–906. [Google Scholar] [CrossRef]
- Hakim, M.A.; Aksu, H.; Uluagac, A.S.; Akkaya, K. U-PoT: A Honeypot Framework for UPnP-Based IoT Devices. In Proceedings of the 2018 IEEE 37th International Performance Computing and Communications Conference (IPCCC), Orlando, FL, USA; 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Shahin, S.; Soubra, H. An IoT Adversary Emulation prototype tool. In Proceedings of the 2022 5th International Conference on Information and Computer Technologies (ICICT), New York, NY, USA; 2022; pp. 7–12. [Google Scholar] [CrossRef]
- Sabry, N.; Abobkr, M.; ElHayani, M.; Soubra, H. A Cyber-Security Prototype Module for Smart Bikes. In Proceedings of the 2021 16th International Conference on Computer Engineering and Systems (ICCES), Cairo, Egypt, Egypt; 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Elhusseiny, N.; Sabry, M.; Soubra, H. B2X Multiprotocol Secure Communication System for Smart Autonomous Bikes. In Proceedings of the 2023 IEEE Conference on Power Electronics and Renewable Energy (CPERE), Luxor, Egypt; 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Joel, M.R.; Manikandan, G.; Bhuvaneswari, G. An Analysis of Security Challenges in Internet of Things (IoT) based Smart Homes. In Proceedings of the 2023 Second International Conference on Electronics and Renewable Systems (ICEARS), Tuticorin, India; 2023; pp. 490–497. [Google Scholar] [CrossRef]
- Bryant, B.; Saiedian, H. Key challenges in security of IoT devices and securing them with the blockchain technology. Security and privacy. 2022, 5, 5. [Google Scholar] [CrossRef]
- Alawadhi, J.; AlJanabi, A.M.; Khder, M.A.; Ali, B.J.A.; Al–Shalabi, R.F. Internet of Things (IoT) Security Risks: Challenges for Business. In Proceedings of the 2022 ASU International Conference in Emerging Technologies for Sustainability and Intelligent Systems (ICETSIS), Manama, Bahrain; 2022; pp. 450–456. [Google Scholar] [CrossRef]
- Khanam, R. Review of Threats in IoT Systems: Challenges and Solutions. International Journal For Science Technology And Engineering. 2023, 11, 325–341. [Google Scholar] [CrossRef]
- Haris, M.A.H.B.; Yahya, M.I.H.B.; Ibrahim, M.N.B. Security and Privacy Issues in Internet of Things (IoT). TechRxiv. 2023. [CrossRef]
- Gupta, S.; Lingareddy, N. Security Threats and Their Mitigations in IoT Devices. In: Pawar, P.M., Balasubramaniam, R., Ronge, B.P., Salunkhe, S.B., Vibhute, A.S., Melinamath, B. (eds) Techno-Societal 2020. Springer, Cham, 2021. [CrossRef]
- Bakshi, G. IoT Architecture Vulnerabilities and Security Measures. In: Bhardwaj, A., Sapra, V. (eds) Security Incidents & Response Against Cyber Attacks. EAI/Springer Innovations in Communication and Computing. Springer, Cham, 2021. [CrossRef]
- Hromada, D.; Costa, R.L.; Santos, L.; Rabadão, C. Security Aspects of the Internet of Things. In C. González García & V. García-Díaz (Eds.), IoT Protocols and Applications for Improving Industry, Environment, and Society (pp. 207-233). IGI Global, 2021. [CrossRef]
- Mallik, P.; Jena, O.P. Analysis of Security Vulnerabilities of Internet of Things and It’s Solutions. In: Udgata, S.K., Sethi, S., Srirama, S.N. (eds) Intelligent Systems. Lecture Notes in Networks and Systems, vol 185. Springer, Singapore, 2021. [CrossRef]
- Amit, Dhingra, A.; Sangwan, A.; Sindhu, V. DDOS Attack on IOT devices. Int J Circuit Comput Networking 2022; 3(1), 33-42. [CrossRef]
- Lightbody, D.; Ngo, D.-M.; Temko, A.; Murphy, C.C.; Popovici, E. Attacks on IoT: Side-Channel Power Acquisition Framework for Intrusion Detection. Future Internet, 2023, 15, 187. [CrossRef]
- Mohd Bakry, B.B.; Bt Adenan, A.R.; Mohd Yussoff, Y.B. Security Attack on IoT Related Devices Using Raspberry Pi and Kali Linux. In Proceedings of the 2022 International Conference on Computer and Drone Applications (IConDA), Kuching, Malaysia; 2022; pp. 40–45. [Google Scholar] [CrossRef]
- Neto, E.C.P.; Dadkhah, S.; Ferreira, R.; Zohourian, A.; Lu, R.; Ghorbani, A.A. CICIoT2023: A Real-Time Dataset and Benchmark for Large-Scale Attacks in IoT Environment. Sensors 2023, 23, 5941. [Google Scholar] [CrossRef] [PubMed]
- Kampel, L.; Kitsos, P.; Simos, D.E. Locating Hardware Trojans Using Combinatorial Testing for Cryptographic Circuits. IEEE Access 2022, 10, 18787–18806. [Google Scholar] [CrossRef]
- Jain, A.; Zhou, Z.; Guin, U. Survey of Recent Developments for Hardware Trojan Detection. In Proceedings of the 2021 IEEE International Symposium on Circuits and Systems (ISCAS), Daegu, Korea; 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Liu, H.; Luo, H.; Wang, L. Design of hardware trojan horse based on counter. In Proceedings of the 2011 International Conference on Quality, Reliability, Risk, Maintenance, and Safety Engineering, Xi’an, China; 2011; pp. 1007–1009. [Google Scholar] [CrossRef]
- Shakya, B.; He, T.; Salmani, H. et al. Benchmarking of Hardware Trojans and Maliciously Affected Circuits. J Hardw Syst Secur 2017, 1, 85–102. [CrossRef]
- Tang, W.; Su, J.; Gao, Y. Hardware Trojan Detection Method Based on Dual Discriminator Assisted Conditional Generation Adversarial Network. J Electron Test 2023, 39, 129–140. [Google Scholar] [CrossRef]
- Dakhale, B.; Vipinkumar, K.; Narotham, K.; Kadam, S.; Bhurane, A.A.; Kothari, A.G. Automated Detection of Hardware Trojans using Power Side-Channel Analysis and VGG-Net. In Proceedings of the 2023 2nd International Conference on Paradigm Shifts in Communications Embedded Systems, Machine Learning and Signal Processing (PCEMS), Nagpur, India; 2023; pp. 1–5. [Google Scholar] [CrossRef]
- Mao, J.; Jiang, X.; Liu, D.; Chen, J.; Huang, K. A Hardware Trojan-Detection Technique Based on Suspicious Circuit Block Partition. Electronics 2022, 11, 4138. [Google Scholar] [CrossRef]
- Hassan, R.; Meng, X.; Basu, K.; Dinakarrao, S.M.P. Circuit Topology-Aware Vaccination-Based Hardware Trojan Detection. Trans. Comp.-Aided Des. Integ. Cir. Sys. 42, 9 (Sept. 2023), 2852–2862. [CrossRef]
- Yasaei, R.; Chen, L.; Yu, S.-Y.; Faruque, M.A.A. Hardware trojan detection using graph neural networks. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems 2022, 1-14. [CrossRef]
- Brunner, M.; Lee, H.H.; Hepp, A.; Baehr, J.; Sigl, G. Hardware Honeypot: Setting Sequential Reverse Engineering on a Wrong Track. In Proceedings of the 2024 27th International Symposium on Design & Diagnostics of Electronic Circuits & Systems (DDECS), Kielce, Poland; 2024; pp. 47–52. [Google Scholar] [CrossRef]
- Wegerer, M.; Tjoa, S. Defeating the Database Adversary Using Deception - A MySQL Database Honeypot. In Proceedings of the 2016 International Conference on Software Security and Assurance (ICSSA), Saint Pölten, Austria; 2016; pp. 6–10. [Google Scholar] [CrossRef]
- Piggin, R.; Buffey, I. Active defence using an operational technology honeypot. In Proceedings of the 11th International Conference on System Safety and Cyber-Security (SSCS 2016), London, UK; 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Kibret, Y.; Yong, W. Design and Implementation of Dynamic Hybrid Virtual Honeypot Architecture for Attack Analysis. Int J Netw Distrib Comput 2013, 1, 108–123. [Google Scholar] [CrossRef]
- Guan, C.; Liu, H.; Cao, G.; Zhu, S.; La Porta, T. HoneyIoT: Adaptive High-Interaction Honeypot for IoT Devices Through Reinforcement Learning. In Proceedings of the 16th ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec ‘23). Association for Computing Machinery, New York, NY, USA; 2023; pp. 49–59. [Google Scholar] [CrossRef]
- Ellouh, M.; Ghaleb, M.; Felemban, M. IoTZeroJar: Towards a Honeypot Architecture for Detection of Zero-Day Attacks in IoT. In Proceedings of the 2022 14th International Conference on Computational Intelligence and Communication Networks (CICN), Al-Khobar, Saudi Arabia; 2022; pp. 765–771. [Google Scholar] [CrossRef]
- Srinivasa, S.; Pedersen; J.M.; Vasilomanolakis, E. RIoTPot: A Modular Hybrid-Interaction IoT/OT Honeypot. In Proceedings of the the 26th European Symposium on Research in Computer Security (ESORICS), Darmstadt, Germany, 2021, 1-7. [CrossRef]
- Srinivasa, S.; Pedersen; J.M.; Vasilomanolakis, E. 2022. Interaction matters: a comprehensive analysis and a dataset of hybrid IoT/OT honeypots. In Proceedings of the 38th Annual Computer Security Applications Conference (ACSAC ‘22). Association for Computing Machinery, New York, NY, USA, 742–755. [CrossRef]
- Lu, X. -X.; Yu, X. -N.; Liu, Y. -Z.; Zhang, M. Dynamic Deployment Model of Lightweight Honeynet for Internet of Things. In Proceedings of the 2022 International Conference on 6G Communications and IoT Technologies (6GIoTT), Fuzhou, China, 2022, pp. 30-34. [CrossRef]
- Moein, S.; Gulliver, T.A.; Gebali, F.; Alkandari, A. A New Characterization of Hardware Trojans. IEEE Access 2016, 4, 2721–2731. [Google Scholar] [CrossRef]

| Reference | Method/Technique | Strengths of the Study | Weaknesses of the Study |
|---|---|---|---|
| [11] Joel et al., 2023 | Analysis of security challenges in IoT smart homes | Comprehensive analysis of various IoT security challenges | Limited focus on mitigation strategies |
| [12] Blake et al., 2022 | Security with blockchain technology | Innovative use of blockchain for IoT security | Does not address integration with other security measures |
| [13] Alawadhi et al., 2022 | Analysis of IoT security risks for businesses | Focuses on business-related IoT risks | Lack of technical details on mitigation |
| [14] Khanam, 2023 | Review of IoT threats and solutions | Provides a broad overview of IoT threats | Lacks in-depth analysis of specific threats |
| [15] Haris et al., 2023 | Discussion on IoT security and privacy issues | Highlights various security and privacy issues | Limited empirical data to support claims |
| [16] Gupta and Lingareddy, 2021 | Security threats and mitigations in IoT | Discusses a range of security threats and solutions | Focuses mainly on theoretical aspects |
| [17] Bakshi, 2021 | IoT architecture vulnerabilities | Detailed analysis of IoT architecture vulnerabilities | Limited focus on practical solutions |
| [18] Hromada et al., 2021 | Security aspects of IoT | Comprehensive discussion on IoT security protocols | Limited real-world application examples |
| [19] Mallik and Jena, 2021 | Analysis of IoT security vulnerabilities | Provides solutions for common IoT vulnerabilities | Focuses on general rather than specific vulnerabilities |
| [20] Amit et al., 2022 | Study on DDoS attacks on IoT devices | Detailed analysis of DDoS attack methods | Limited focus on preventive measures |
| [21] Lightbody et al., 2023 | Framework for intrusion detection in IoT | Innovative use of side-channel analysis | Limited scalability for large IoT networks |
| [22] Mohd Bakry et al., 2022 | Security attack study using Raspberry Pi | Practical demonstration of IoT attacks | Limited scope with a single device model |
| [23] Neto et al., 2023 | Real-time IoT attack dataset | Provides a comprehensive IoT attack dataset | Limited focus on mitigation strategies |
| [24] Kampel et al., 2022 | Detection of HTs using combinatorial testing | Effective method for detecting HTs in cryptographic circuits | May not be applicable to all circuit types |
| [25] Jain et al., 2021 | Survey of HT detection methods | Comprehensive survey of HT detection techniques | Limited practical application examples |
| [26] Liu et al., 2011 | Design of counter-based HT | Innovative HT design method | Dated methodology, lacks modern context |
| [27] Shakya et al., 2017 | Benchmarking of HTs | Provides a benchmarking framework for HTs | Limited focus on detection methods |
| [28] Tang et al., 2023 | HT detection using adversarial networks | High accuracy in HT detection | Complex implementation |
| [29] Dakhale et al., 2023 | Detection of HTs using VGG-Net | Effective use of neural networks for HT detection | Computationally intensive |
| [30] Mao et al., 2022 | HT detection using suspicious circuit partition | Novel approach to HT detection | May produce false positives |
| [31] Hassan et al., 2023 | GNN-based HT detection | High accuracy without a golden IC reference | Requires complex graph learning algorithms |
| [33] Brunner et al., 2024 | FSM-based hardware honeypot | Realistic imitation of original FSM | May not cover all HT types |
| [34] Wegerer and Tjoa, 2016 | MySQL database honeypot | Effective in deceiving database adversaries | Limited to MySQL databases |
| [35] Piggin and Buffey, 2016 | Operational technology honeypot | Provides insights into attacker methods | Limited scope, focused on specific technologies |
| [36] Kibret and Yong, 2013 | Dynamic hybrid virtual honeypot | Combines multiple honeypot types | Complex implementation |
| [37] Guan et al., 2023 | Adaptive honeypot for IoT using RL | Adapts to evolving threats using RL | High resource requirements |
| [38] Ellouh et al., 2022 | IoT honeypot for zero-day attacks | Effective against zero-day attacks | Limited real-world deployment |
| [39] Srinivasa et al., 2021 | Modular hybrid-interaction honeypot | Flexible and modular design | Limited long-term studies |
| [40] Srinivasa et al., 2022 | Comprehensive honeypot analysis and dataset | Provides extensive data on attack patterns | High complexity in analysis |
| [41] Xiaoming et al., 2022 | Lightweight honeynet for IoT | Cost-effective and scalable | Limited to lightweight applications |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





