Submitted:
14 May 2024
Posted:
14 May 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
- Determining and analyzing the research papers that have already been written about access control and secure authentication in IoT communications.
- Delving into the several authentications and access control techniques that have been suggested for IoT communications.
- Listing all challenges and open research issues about authentication and access control to secure IoT.
- Offering analysis and recommendations for research future directions.
1.1. Motivations
1.2. Scope
- The study looks at a number of authentication techniques suggested for IoT environments, such as MFA, certificate-based authentication, biometric authentication, and the conventional username/password method.
- Various access control mechanisms that apply to IoT environments are examined in this study. Context-aware access control, Attribute-Based Access Control (ABAC) and Role-Based Access Control (RBAC) are examples. In the analysis, we will examine their suitability , scalability and effectiveness for various IoT applications.
- The paper examines the special qualities and limitations of IoT devices, including their constrained amounts of memory, processing power, and energy. It looks at how these restrictions affect the way secure authentication and access control systems are designed and implemented for the IoT and looks into effective, low-cost solutions that can work around these restrictions.
- The paper explores the security concerns that raise from authentication and access control in the IoT. These challenges include those relating to scalability, privacy, interoperability, and standardization. It examines the developments and fixes to deal with these issues and tries to minimize security threats in IoT environments.
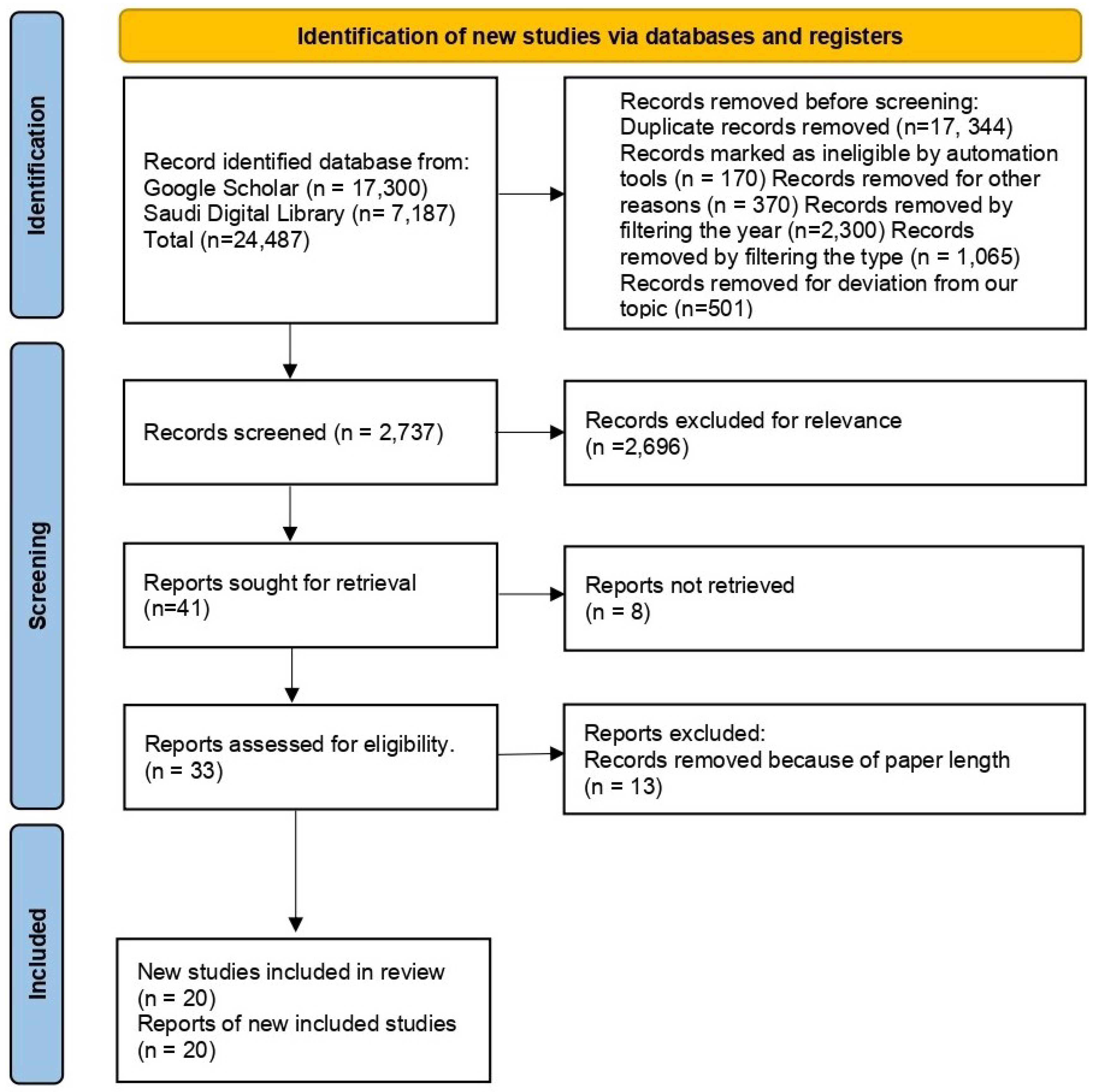
2. Papers Selection for Literature Review
2.1. Methodology
2.2. Search String
2.3. Data Sources
2.4. Screening Process
2.5. Data charting process
2.6. Systematic Review registration statement
3. Overview of IoT Authentication Mechanisms
-
Password-based authentication: Passwords are the most common authentication method. Devices in IoT environments use a combination of username and password to authenticate other devices. Using only passwords is not enough to provide optimum security, especially when weak passwords are used. Also, brute-force attacks can be used to guess the passwords.Both Hammi [4] and Alshahrani [5] offer creative password-based authentication methods for the IoT. Alphanumeric and graphical passwords are combined in Alshahrani’s graphical-based password scheme, IoT-GP, a two-factor technique that greatly enhances security and usability. With excellent security and performance, Hammi’s lightweight ECC-based authentication technique uses isogeny and Elliptic Curve Cryptography (ECC) to expand on the One-Time Password (OTP) concept. In order to defend against dictionary and brute force attacks, Tarish [6] recommends using the Secure Remote Password Protocol (SRPP) in Wi-Fi-based IoT networks.
-
Public Key Infrastructure (PKI): This type of authentication depends on the cryptography keys, involving both public and private keys. Every device in IoT environments has a unique private key, while the public key remains for the public to be used by other servers or other devices.A lightweight certificate enrollment mechanism and a profile for X.509 digital certificates are introduced by Höglund [7] in order to meet the resource limitations of IoT devices. In order to improve storage, communication, reaction time, and resistance against malicious nodes, Belattaf [8] offers a distributed public-key management infrastructure that is both dependable and adaptable. Using a different strategy, Antony [9] proposes a blockchain-based PKI that provides safe data sharing for IoT-based healthcare systems. Balakrichenan [10] investigates the creation of a PKI for the IoT by utilizing the Domain Name System (DNS) infrastructure, especially the DNS-based Authentication of Named Entities protocol (DANE) and DNS’s Security Extensions (DNSSEC).
-
X.509 certificates: Digital papers called X.509 certificates link an identity to a public key. When establishing their identity with other devices or servers, IoT devices can employ X.509 certificates. The device’s validity and integrity can be confirmed by relying parties through the verification of certificates that are provided by a reliable Certificate Authority (CA).Using X.509 certification and LZW compression, Karthikeyan [11] suggests a way for data security in IoT networks. Höglund [7] concentrates on addressing the resource limitations of IoT devices through the creation of a lightweight certificate enrollment protocol and an X.509 digital certificate profile known as XIOT. A blockchain-based lightweight certificate authentication solution that does not rely on Certification Authorities is introduced by Garba [12] as LightCert4IoT. L-ECQV is a lightweight ECQV implicit certificate that minimizes message overhead and energy usage for IoT authentication, as presented by Malik [13].
-
OAuth and OAuth 2.0: Widely employed in IoT applications, OAuth is an authorization protocol that permits safe resource access on behalf of a user or device. By using OAuth, a third-party service or application (referred to as the OAuth provider) can grant access to resources without disclosing the user’s credentials. This is known as delegated permission. Widely used for IoT installations, OAuth 2.0 is an enhanced version of the protocol.This is further improved by the ACE-OAuth framework, which extends OAuth 2.0 to accommodate IoT device restrictions and incorporates CoAP [14]. OAuth 2.0 is suggested as a useful option for authorization and authentication in certain applications, such as Forestry 4.0 [15]. Oh et al. [16] highlight the necessity of security interoperability in diverse IoT platforms and suggest the interoperable OAuth 2.0 framework as a potential solution.
-
Token-based authentication: Every authorized entity in the IoT network has a unique token that will be used for other authentication requests rather than the need to send credentials information with every request. In addition, the tokens can be live shortly, revocable, and tied to specific permissions to improve the scalability and security of IoT environments.In order to provide safe and decentralized identity management, several studies have suggested token-based authentication methods for the IoT [17]. These protocols make use of blockchain technology and fog computing. The use of Ethereum smart contracts for secure connectivity between miner nodes and IoT devices [18] and random forest learning for authorization and key management [19] are two further elements that have improved these protocols. The security and functionality of token-based authentication in the IoT have greatly enhanced as a result of these developments.
-
Mutual authentication: The server and gateway have to authenticate each other before starting the connection, which prevents unauthorized access or special types of attacks like Man-In-The-Middle (MITM) from accessing the IoT network.Simplicity, optimality, and efficiency have been prioritized in the exploration of various techniques and algorithms for mutual authentication in IoT devices [20]. To solve security weaknesses, especially in RFID-based IoT systems, an effective authentication strategy based on mutual key update and self-adaptation has been presented [21]. With an emphasis on efficiency and simplicity, attribute-based encryption has been used to construct private and mutual authentication protocols that safeguard the privacy of IoT devices [22].
-
Biometric authentication: Biometric authentication uses biometric individual information to authenticate users who are using IoT devices. Every individual has unique biometric information, such as facial recognition, fingerprints, and voices.Secure biometric authentication solutions for IoT devices are proposed by Golec [23] and Bedari [24], with Golec concentrating on edge devices and Bedari on industrial IoT devices over 5G networks. Both studies stress the significance of safe data transmission and storage; Golec emphasizes the use of AES-128-bit key encryption, while Bedari presents a fingerprint template that can be cancelled. While Rao [25] introduces a user authentication protocol for IoT networks, highlighting the necessity of dual-factor authentication and strong encryption, Alsellami [26] gives an overview of the possibilities of biometric authentication in IoT. The combined findings of these studies highlight how biometric authentication can improve the security and privacy of IoT devices.
-
Multi-Factor Authentication (MFA): MFA is the combination of two authentication methods like passwords, biometrics, tokens or smart cards. MFA enhances security by adding an extra layer of protection against unauthorized access to IoT devices.Mishra [27] proposes an MFA-integrated cloud-based security system for Industry 4.0 communication. With an emphasis on identity, password, and digital signatures, Saqib [28] presents a framework for lightweight three-factor authentication for essential IoT applications. An improved IoT security architecture for authorization and authentication, which includes MFA, is presented by Al-Refai [29] to fend against various sorts of threats. With the goal of enhancing efficiency and resource management, Sudha [30] suggests a low-area design of two-factor authentication utilizing the substitution-box-based inverter and Data Inverting Encoding Scheme (DIES) for IoT security.
4. Overview of IoT Access Control Mechanisms
-
Authorization: Authorization guarantees that only authorized entities can access specific resources or functionalities. Authorization defines the actions that authenticated users or devices are allowed to perform and is based on roles, permissions, or attributes. For instance, some users may have limited access to IoT data, while others have full access to devices.The constraints of conventional access control methods are addressed by Putra [31] and Hameed [32] with their proposals for blockchain-based authorization mechanisms for IoT. Using Attribute-Based Access Control (ABAC) and environmental factors to establish policies, Hameed’s method is decentralized, dynamic, and adaptable. The dynamic and flexible nature of access control is enhanced by Putra’s approach, which integrates a Trust and Reputation approach to quantify node trust and reputation ratings. In restricted IoT environments, Siris [33] provides approaches that leverage smart contracts and interledger techniques for decentralized authorization, with an emphasis on tradeoffs between cost, latency, complexity, and privacy. The combined findings of these research demonstrate how blockchain technology may improve the effectiveness and security of IoT authorization systems.
-
Encryption: Data is encrypted so that only authorized parties can decode it, protecting it both while it’s in transit and at rest. IoT devices frequently use secure communication protocols like Transport Layer Security (TLS) or Secure Sockets Layer (SSL) to encrypt data exchanged with servers or other devices. Data manipulation, eavesdropping, and illegal access to private information are all made more difficult by encryption.Ciphertext-Policy Attribute-Based Encryption (CP-ABE) is suggested as an access control method for the IoT by Nakanishi [34] and Alsolami [35]. Specifically, Nakanishi [34] creates a distributed, fee-free, and scalable access control system by combining CP-ABE with IOTA technology. The throughput of access request processing can be greatly increased with this system’s fine-grained attribute-based access control. Using CP-ABE to protect data from unwanted access, Alsolami [35] focuses on safeguarding smart homes. By putting out a modified CP-ABE technique with a constant size ciphertext that is appropriate for IoT devices with constrained memory and processing power, Yang [36] also contributes to this field. All of these research show that encryption, and especially CP-ABE, has great potential as an efficient access control method in the IoT.
-
Role-based Access Control (RBAC): An organization or system’s roles determine which devices or users are granted rights, and the RBAC access control paradigm is commonly used for this purpose. Permissions are linked to each role, and decisions about access are dependent on the roles that devices or users hold. Because RBAC centralizes rights and eliminates the need for unique user/device setups, it makes access management simpler.Both Kumar [37] and Amoon [38] provide RBAC frameworks for IoT networks; Kumar concentrates on resource management and load balancing, while Amoon concentrates on thwarting malicious assaults. Abushmmala [39] builds on this work by using blockchain technology with RBAC to improve security and privacy in IoT applications for smart health.
-
Attribute-based Access Control: ABAC expands access control beyond roles to take into account a variety of factors, including device properties, environmental factors, and user attributes. More precise control over access permissions is made possible by rules that assess these attributes as the basis for access decisions. In dynamic IoT systems, where access requirements may change depending on contextual factors, ABAC is especially helpful.ABAC integration is a promising method for improving security and controlling access, especially in the context of 5G networks [40]. This is further reinforced by the ABAC-CC framework proposal [41], which secures access and communication control to solve security and privacy concerns in Cloud-Enabled IoT (CE-IoT). Additionally, the application of ABAC in a cloud-enabled IoT environment is examined, emphasizing the use of the XACML language to build policy rules that block unwanted access to remote resources [42].
-
Network Segmentation: Network segmentation is a technique used to isolate IoT devices and reduce the possible scope of security breaches. It entails splitting a network into distinct segments or subnetworks. Organizations may limit security risks and stop unwanted access to vital systems or data by isolating IoT devices into distinct network segments with controlled access.Novel approaches to network segmentation for IoT access control have been put forth in a number of research. In order to stop risks from spreading over the IoT networks, Lim [43] proposes a smart segmentation system that makes use of device features, network information, and service kinds. In order to minimize the attack surface, Vaere [44] presents Hopper, a security system that isolates each network host into a separate, access-controlled micro segment. A permission token segmentation approach based on blockchain is presented by Shi [45], which enables IoT access control systems to have fine-grained control over permissions. Wei [46] focuses on an SDN-based approach to fine-grained access control for IoT devices that efficiently
-
Firewalls and Intrusion Detection/Prevention Systems (IDS/IPS): To monitor and regulate network traffic, detect and prevent malicious activity or unauthorized access attempts, firewalls and IDS/IPS systems are used. These security precautions aid in preventing external threats or unauthorized users from compromising IoT devices to obtain private information or take control of the devices.In order to maintain the security of IoT networks and devices, IDS and IPS are essential. However, creating an efficient IDS for these networks is difficult because to the lightweight nature of IoT nodes [47]. In order to mitigate this issue, a resilient intrusion detection system architecture has been suggested, which reduces communication overhead and energy consumption while preserving elevated detection rates [48]. Furthermore, emphasis has been placed on the role Identity and Access Management (IAM) controls play in safeguarding IoT systems, with an emphasis on classifying and visualizing IAM technologies at the state of the art [49].
5. Related Study
| Reference | Key Findings | Methodology | Limitations/Research Gaps |
|---|---|---|---|
| [50] |
|
|
|
| [51] |
|
|
|
| [52] |
|
|
|
| [53] |
|
|
|
| [54] |
|
|
|
| [55] |
|
|
|
| [56] |
|
|
|
| [57] |
|
|
|
| [58] |
|
|
|
| [59] |
|
|
|
| [60] |
|
|
|
| [61] |
|
|
|
| [62] |
|
|
|
| [63] |
|
|
|
| [65] |
|
|
|
| [66] |
|
|
|
| [67] |
|
|
|
| [68] |
|
|
|
| [69] |
|
|
|
| [70] |
|
|
|
6. Challenges and Future Directions
6.1. Challenges in IoT security
- Variations in device design and challenges in putting standard mechanisms into practice [71].
- To improve authentication and authorization, a decentralized IoT access control architecture that makes use of OAuth and decentralized identity technology is required [72].
- Strong access control systems are required, especially given the explosive expansion of the IoT and the production of sensitive data [73].
- To address security and privacy problems in the IoT, lightweight and interoperable authentication protocols are required [74].
- The requirement for more reliable authorization and authentication mechanisms makes the application of machine learning techniques essential. According to [68].
- It is necessary to investigate how hybrid deep learning techniques, namely the fusion of physiological and behavioral characteristics, might improve Internet of Things security [75].
6.2. Future Directions
- Investigating the possibilities for improving IoT security offered by revolutionary technologies like blockchain, artificial intelligence, and 5G networks, as well as solving the open issues in creating comprehensive, lightweight, and scalable security frameworks for the IoT.
- Offering effective and safe IoT authentication techniques with the goal of improving the security of IoT environments. In addition to potentially looking into new methods or technologies to address the security issues in IoT systems, this could entail further research and development of authentication protocols based on encryption cryptography.
- concentrating on approaches for authorization and authentication that have a high level of security, good throughput, low computational cost, and good tolerance.
- Investigating the creation of ML-driven authorization systems to improve the security of IoT environments, taking into account a hybrid strategy that combines centralized and distributed techniques to successfully solve security concerns.
- Developing lightweight platforms for blockchain implementation, investigating novel consensus algorithms appropriate for IoT devices, optimizing blockchain technology for resource-constrained IoT environments, and improving blockchain’s security and privacy features for IoT applications. Scalability and effectiveness of blockchain technology in IoT can be the subject of future research.
- In order to apply blockchain-based access control approaches, it is necessary to analyze the interaction between authentication and authorization techniques and research paradigms like fog computing, multi-access edge computing, and dew computing.
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| IoT | Internet of Things |
| ECC | Elliptic Curve Cryptography |
| OTP | One-Time Password |
| SRPP | Secure Remote Password Protocol |
| PKI | Public Key Infrastructure |
| DNS | Domain Name System |
| DANE | DNS-based Authentication of Named Entities protocol |
| DNSSEC | DNS’s Security Extensions |
| CA | Certificate Authority |
| MITM | Man-In-The-Middle attack |
| MFA | Multi-Factor Authentication |
| DIES | Data Inverting Encoding Scheme |
| ABAC | Attribute-Based Access Control |
| TLS | Transport Layer Security |
| SSL | Secure Sockets Layer |
| RBAC | Role-based Access Control |
| IDS | Intrusion Detection Systems |
| IPS | Intrusion Prevention Systems |
| IAM | Identity and Access Management |
| MAC | Message Authentication Code |
| PUF | Physically Unclonable Function |
| CRP | Challenge-Response Pair |
| XOR | bitwise-Exclusive-OR |
| ROR | Real-Or-Random |
| OAI | Open Air Interface |
| AES | Advanced Encryption Standard |
| AD | Angular Distance |
References
- Michailidis, E.T.; Vouyioukas, D. A review on software-based and hardware-based authentication mechanisms for the Internet of Drones. Drones 2022, 6, 41. [CrossRef]
- Mehta, M.; Baldaniya, H.; Goriya, N. A Systematic Review of Authentication Methods for Internet of Things. In Proceedings of the 2020 IEEE International Conference for Innovation in Technology (INOCON). IEEE, 2020, pp. 1–6.
- Putra, G.D.; Dedeoglu, V.; Kanhere, S.S.; Jurdak, R. Trust management in decentralized iot access control system. In Proceedings of the 2020 IEEE international conference on blockchain and cryptocurrency (ICBC). IEEE, 2020, pp. 1–9.
- Hammi, B.; Fayad, A.; Khatoun, R.; Zeadally, S.; Begriche, Y. A lightweight ECC-based authentication scheme for Internet of Things (IoT). IEEE Systems Journal 2020, 14, 3440–3450. [CrossRef]
- Alshahrani, F.S.; Abdullah, M. Graphical-based password for user authentication in internet of things. Indonesian Journal of Electrical Engineering and Computer Science 2022, 28, 1139–1146. [CrossRef]
- Tarish, H.A. Enhanced IoT Wi-Fi protocol standard’s security using secure remote password. Periodicals of Engineering and Natural Sciences 2022, 10, 632–644. [CrossRef]
- Höglund, J.; Lindemer, S.; Furuhed, M.; Raza, S. PKI4IoT: Towards public key infrastructure for the Internet of Things. Computers & Security 2020, 89, 101658. [CrossRef]
- Belattaf, S.; Mohammedi, M.; Omar, M.; Aoudjit, R. Reliable and adaptive distributed public-key management infrastructure for the Internet of things. Wireless Personal Communications 2021, 120, 113–137. [CrossRef]
- Joseph Antony, A.; Singh, K. A Blockchain-Based Public Key Infrastructure For IoT-Based Healthcare Systems. The Computer Journal 2024, 67, 1531–1537. [CrossRef]
- Balakrichenan, S.; Ayoub, I.; Ampeau, B. PKI for IoT using the DNS infrastructure. In Proceedings of the 2022 IEEE International Conference on Public Key Infrastructure and its Applications (PKIA). IEEE, 2022, pp. 1–8.
- Karthikeyan, S.; Poongodi, T. Secured Data Compression and Data Authentication in Internet of Thing Networks Using LZW Compression Based X. 509 Certification. In Proceedings of the 2022 IEEE International Conference on Data Science and Information System (ICDSIS). IEEE, 2022, pp. 1–5.
- Garba, A.; Khoury, D.; Balian, P.; Haddad, S.; Sayah, J.; Chen, Z.; Guan, Z.; Hamdan, H.; Charafeddine, J.; Al-Mutib, K. LightCERT4IoTs: Blockchain-based lightweight certificates authentication for IoT applications. IEEE Access 2023, 11, 28370–28383. [CrossRef]
- Malik, M.; Dutta, M.; Granjal, J.; et al. L-ecqv: Lightweight ecqv implicit certificates for authentication in the internet of things. IEEE Access 2023, 11, 35517–35540. [CrossRef]
- Seitz, L.; Selander, G.; Wahlstroem, E.; Erdtman, S.; Tschofenig, H. Authentication and Authorization for Constrained Environments Using the OAuth 2.0 Framework (ACE-OAuth). RFC 2022, 9200, 1–72.
- Chen, J.; Hoppen, M.; Böken, D.; Reitz, J.; Schluse, M.; Roßmann, J. Identity, authentication and authorization in forestry 4.0 using oauth 2.0. In Proceedings of the 2022 3rd International Informatics and Software Engineering Conference (IISEC). IEEE, 2022, pp. 1–6.
- Oh, S.R.; Koo, J.; Kim, Y.G. Security interoperability in heterogeneous IoT platforms: threat model of the interoperable OAuth 2.0 framework. In Proceedings of the Proceedings of the 37th ACM/SIGAPP Symposium on Applied Computing, 2022, pp. 22–31.
- Ahmed, N.A.; Ammar, M.; Hefny, H.A. Proposed authentication protocol for IoT using blockchain and fog nodes. International Journal of Advanced Computer Science and Applications 2020, 11.
- Hameed, K.; Garg, S.; Amin, M.B.; Kang, B. A formally verified blockchain-based decentralised authentication scheme for the internet of things. The Journal of Supercomputing 2021, 77, 14461–14501. [CrossRef]
- Manogaran, G.; Rawal, B.S.; Saravanan, V.; MK, P.; Xin, Q.; Shakeel, P. Token-based authorization and authentication for secure internet of vehicles communication. ACM Transactions on Internet Technology 2023, 22, 1–20. [CrossRef]
- Sonth, R.R.; Pranamya, Y.; Harish Kumar, N.; Deepak, G. A Survey on Methodologies and Algorithms for Mutual Authentication in IoT Devices. In Proceedings of the Evolutionary Computing and Mobile Sustainable Networks: Proceedings of ICECMSN 2020. Springer, 2021, pp. 309–315.
- Mbarek, B.; Ge, M.; Pitner, T. An efficient mutual authentication scheme for internet of things. Internet of things 2020, 9, 100160. [CrossRef]
- Jiang, L.; Cui, H. Private and Mutual Authentication Protocols for Internet of Things. Mathematics 2023, 11, 1929. [CrossRef]
- Golec, M.; Gill, S.S.; Bahsoon, R.; Rana, O. BioSec: A biometric authentication framework for secure and private communication among edge devices in IoT and industry 4.0. IEEE Consumer Electronics Magazine 2020, 11, 51–56. [CrossRef]
- Bedari, A.; Wang, S.; Yang, W. A secure online fingerprint authentication system for industrial IoT devices over 5G networks. Sensors 2022, 22, 7609. [CrossRef] [PubMed]
- Kameswara Rao, M.; Santhi, S. A novel user authentication protocol using biometric data for iot networks. In Proceedings of the Rising Threats in Expert Applications and Solutions: Proceedings of FICR-TEAS 2020. Springer, 2021, pp. 85–91.
- Alsellami, B.M.; Deshmukh, P.D. The recent trends in biometric traits authentication based on internet of things (IoT). In Proceedings of the 2021 international conference on artificial intelligence and smart systems (ICAIS). IEEE, 2021, pp. 1359–1365.
- Mishra, A.K.; Wazid, M. Design of a cloud-based security mechanism for Industry 4.0 communication. In Proceedings of the 2023 Third International Conference on Secure Cyber Computing and Communication (ICSCCC). IEEE, 2023, pp. 337–343.
- Saqib, M.; Jasra, B.; Moon, A.H. A lightweight three factor authentication framework for IoT based critical applications. Journal of King Saud University-Computer and Information Sciences 2022, 34, 6925–6937. [CrossRef]
- Mohammad, A.; Al-Refai, H.; Alawneh, A.A. User authentication and authorization framework in IoT protocols. Computers 2022, 11, 147. [CrossRef]
- Sudha, M.; Rajendiran, M.; Specht, M.; Reddy, K.S.; Sugumaran, S. A low-area design of two-factor authentication using DIES and SBI for IoT security. The Journal of Supercomputing 2022, 78, 4503–4525. [CrossRef]
- Putra, G.D.; Dedeoglu, V.; Kanhere, S.S.; Jurdak, R.; Ignjatovic, A. Trust-based blockchain authorization for iot. IEEE Transactions on Network and Service Management 2021, 18, 1646–1658. [CrossRef]
- Hameed, K.; Raza, A.; Garg, S.; Amin, M.B. A Blockchain-based Decentralised and Dynamic Authorisation Scheme for the Internet of Things. arXiv preprint 2022. arXiv:2208.07060.
- Siris, V.A.; Dimopoulos, D.; Fotiou, N.; Voulgaris, S.; Polyzos, G.C. Decentralized authorization in constrained IoT environments exploiting interledger mechanisms. Computer Communications 2020, 152, 243–251. [CrossRef]
- Zhang, Y.; Nakanishi, R.; Sasabe, M.; Kasahara, S. Combining IOTA and attribute-based encryption for access control in the Internet of Things. Sensors 2021, 21, 5053. [CrossRef] [PubMed]
- Alsolami, H.; Bamasag, O.; Aljahdali, A. A Novel Access Control Security Model Based on Ciphertext Policy Attribute-Based Encryption for Smart Homes. In Proceedings of the Proceedings of the 4th International Conference on Future Networks and Distributed Systems, 2020, pp. 1–5.
- Yang, W.; Wang, R.; Guan, Z.; Wu, L.; Du, X.; Guizani, M. A lightweight attribute based encryption scheme with constant size ciphertext for internet of things. In Proceedings of the ICC 2020-2020 IEEE International Conference on Communications (ICC). IEEE, 2020, pp. 1–6.
- Kumar, R.; Agrawal, N. RBAC-LBRM: An RBAC-based load balancing assisted efficient resource management framework for IoT-edge-fog network. IEEE Sensors Letters 2022, 6, 1–4. [CrossRef]
- Amoon, M.; Altameem, T.; Altameem, A. RRAC: Role based reputed access control method for mitigating malicious impact in intelligent IoT platforms. Computer Communications 2020, 151, 238–246. [CrossRef]
- Abushmmala, F.F.; AbuSamra, A.A. Blockchain-Based Secure Smart Health IoT solution Using RBAC Architecture. Journal of Engineering Research and Technology 2023, 10.
- Kaven, S.; Skwarek, V. Poster: Attribute based access control for IoT devices in 5G networks. In Proceedings of the Proceedings of the 28th ACM Symposium on Access Control Models and Technologies, 2023, pp. 51–53.
- Bhatt, S.; Sandhu, R. Abac-cc: Attribute-based access control and communication control for internet of things. In Proceedings of the Proceedings of the 25th ACM Symposium on Access Control Models and Technologies, 2020, pp. 203–212.
- Sifou, F.; AlShahwan, F.; Hammoud, A.; Marwan, M.; Hammouch, A. Implementing Policy Rules in Attributes Based Access Control with XACML within Cloud-Enabled IoT Environment. J. Commun. 2020, 15, 107–112. [CrossRef]
- Lim, J.; Sohn, S.; Kim, J. Proposal of Smart Segmentation Framework for preventing threats from spreading in IoT. In Proceedings of the 2020 International Conference on Information and Communication Technology Convergence (ICTC). IEEE, 2020, pp. 1745–1747.
- De Vaere, P.; Tulimiero, A.; Perrig, A. Hopper: Per-Device Nano Segmentation for the Industrial IoT. In Proceedings of the Proceedings of the 2022 ACM on Asia Conference on Computer and Communications Security, 2022, pp. 279–293.
- Shi, J.; Li, R. Permission Token Segmentation Scheme Based on Blockchain Access Control. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom). IEEE, 2020, pp. 1956–1964.
- Wei, M.; Liang, E.; Nie, Z. A SDN-based IoT fine-grained access control method. In Proceedings of the 2020 International Conference on Information Networking (ICOIN). IEEE, 2020, pp. 637–642.
- Anitha, A.A.; Arockiam, L. A review on intrusion detection systems to secure IoT networks. International Journal of Computer Networks and Applications 2022, 9, 38–50. [CrossRef]
- Al Qurashi, M.; Angelopoulos, C.M.; Katos, V. An architecture for resilient intrusion detection in IoT networks. In Proceedings of the ICC 2020-2020 IEEE International Conference on Communications (ICC). IEEE, 2020, pp. 1–7.
- Ward, G.; Janczewski, L. Analysis of Identity Access Management Controls in IoT Systems. In Proceedings of the 2022 IEEE 7th International conference for Convergence in Technology (I2CT). IEEE, 2022, pp. 1–7.
- Sheron, P.F.; Sridhar, K.; Baskar, S.; Shakeel, P.M. A decentralized scalable security framework for end-to-end authentication of future IoT communication. Transactions on Emerging Telecommunications Technologies 2020, 31, e3815. [CrossRef]
- Fang, D.; Qian, Y.; Hu, R.Q. A flexible and efficient authentication and secure data transmission scheme for IoT applications. IEEE Internet of Things Journal 2020, 7, 3474–3484. [CrossRef]
- Al Hwaitat, A.K.; Almaiah, M.A.; Ali, A.; Al-Otaibi, S.; Shishakly, R.; Lutfi, A.; Alrawad, M. A new blockchain-based authentication framework for secure IoT networks. Electronics 2023, 12, 3618. [CrossRef]
- Liu, Z.; Guo, C.; Wang, B. A physically secure, lightweight three-factor and anonymous user authentication protocol for IoT. IEEE Access 2020, 8, 195914–195928. [CrossRef]
- Alnefaie, S.; Alshehri, S.; Cherif, A. A survey on access control in IoT: Models, architectures and research opportunities. International Journal of Security and Networks 2021, 16, 60–76. [CrossRef]
- Abushmmala, F.F.; AbuSamra, A.A. Blockchain-Based Secure Smart Health IoT solution Using RBAC Architecture. Journal of Engineering Research and Technology 2023, 10.
- Algarni, S.; Eassa, F.; Almarhabi, K.; Almalaise, A.; Albassam, E.; Alsubhi, K.; Yamin, M. Blockchain-based secured access control in an IoT system. Applied Sciences 2021, 11, 1772. [CrossRef]
- Janes, B.; Crawford, H.; OConnor, T. Never ending story: Authentication and access control design flaws in shared iot devices. In 2020 IEEE Security and Privacy Workshops (SPW), 2020.
- Aftab, M.U.; Oluwasanmi, A.; Alharbi, A.; Sohaib, O.; Nie, X.; Qin, Z.; Ngo, S.T. Secure and dynamic access control for the Internet of Things (IoT) based traffic system. PeerJ Computer Science 2021, 7, e471. [CrossRef] [PubMed]
- Putra, G.D.; Dedeoglu, V.; Kanhere, S.S.; Jurdak, R.; Ignjatovic, A. Trust-based blockchain authorization for iot. IEEE Transactions on Network and Service Management 2021, 18, 1646–1658. [CrossRef]
- Fotouhi, M.; Bayat, M.; Das, A.K.; Far, H.A.N.; Pournaghi, S.M.; Doostari, M.A. A lightweight and secure two-factor authentication scheme for wireless body area networks in health-care IoT. Computer Networks 2020, 177, 107333. [CrossRef]
- Behrad, S.; Bertin, E.; Tuffin, S.; Crespi, N. A new scalable authentication and access control mechanism for 5G-based IoT. Future Generation Computer Systems 2020, 108, 46–61. [CrossRef]
- Kumar, P.; Chouhan, L. A privacy and session key based authentication scheme for medical IoT networks. Computer Communications 2021, 166, 154–164. [CrossRef]
- Chaudhry, S.A.; Yahya, K.; Al-Turjman, F.; Yang, M.H. A secure and reliable device access control scheme for IoT based sensor cloud systems. Ieee Access 2020, 8, 139244–139254. [CrossRef]
- Das, A.K.; Wazid, M.; Yannam, A.R.; Rodrigues, J.J.; Park, Y. Provably secure ECC-based device access control and key agreement protocol for IoT environment. IEEE Access 2019, 7, 55382–55397. [CrossRef]
- Panda, P.K.; Chattopadhyay, S. A secure mutual authentication protocol for IoT environment. Journal of Reliable Intelligent Environments 2020, 6, 79–94. [CrossRef]
- Alladi, T.; Chamola, V.; et al. HARCI: A two-way authentication protocol for three entity healthcare IoT networks. IEEE Journal on Selected Areas in Communications 2020, 39, 361–369. [CrossRef]
- Trivedi, H.S.; Patel, S.J. Design of secure authentication protocol for dynamic user addition in distributed Internet-of-Things. Computer Networks 2020, 178, 107335. [CrossRef]
- Istiaque Ahmed, K.; Tahir, M.; Hadi Habaebi, M.; Lun Lau, S.; Ahad, A. Machine learning for authentication and authorization in iot: Taxonomy, challenges and future research direction. Sensors 2021, 21, 5122. [CrossRef]
- Vishwakarma, L.; Das, D. SCAB - IoTA: Secure communication and authentication for IoT applications using blockchain. Journal of Parallel and Distributed Computing 2021, 154, 94–105. [CrossRef]
- Sivaselvan, N.; Bhat, K.V.; Rajarajan, M.; Das, A.K.; Rodrigues, J.J. SUACC-IoT: Secure unified authentication and access control system based on capability for IoT. Cluster Computing 2023, 26, 2409–2428. [CrossRef]
- Tinnaluri, V.N.; Babu, A.J.; Shanmugaraja, P.; Kumar, S.S.; AdityPai, H. A Productive Model for Secured Data Sharing in Blockchain Technology based IoT. In Proceedings of the 2023 International Conference on Inventive Computation Technologies (ICICT). IEEE, 2023, pp. 1426–1431.
- Kang, J.H.; Seo, M. Enhanced Authentication for Decentralized IoT Access Control Architecture. Cryptography 2023, 7, 42. [CrossRef]
- Mishra, R.; Yadav, R. Access control in IoT networks: analysis and open challenges. In Proceedings of the Proceedings of the International Conference on Innovative Computing & Communications (ICICC), 2020.
- Sahoo, A.; Sahoo, S.S.; Sahoo, S.; Sahoo, B.; Turuk, A.K. An interoperable ECC based authentication and key agreement scheme for IoT environment. In Proceedings of the 2020 International Conference on COMmunication Systems & NETworkS (COMSNETS). IEEE, 2020, pp. 419–426.
- Chen, J.I.Z.; Lai, K.L. Internet of Things (IoT) authentication and access control by hybrid deep learning method-a study. Journal of Soft Computing Paradigm (JSCP) 2020, 2, 236–245. [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





