Submitted:
04 June 2024
Posted:
05 June 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
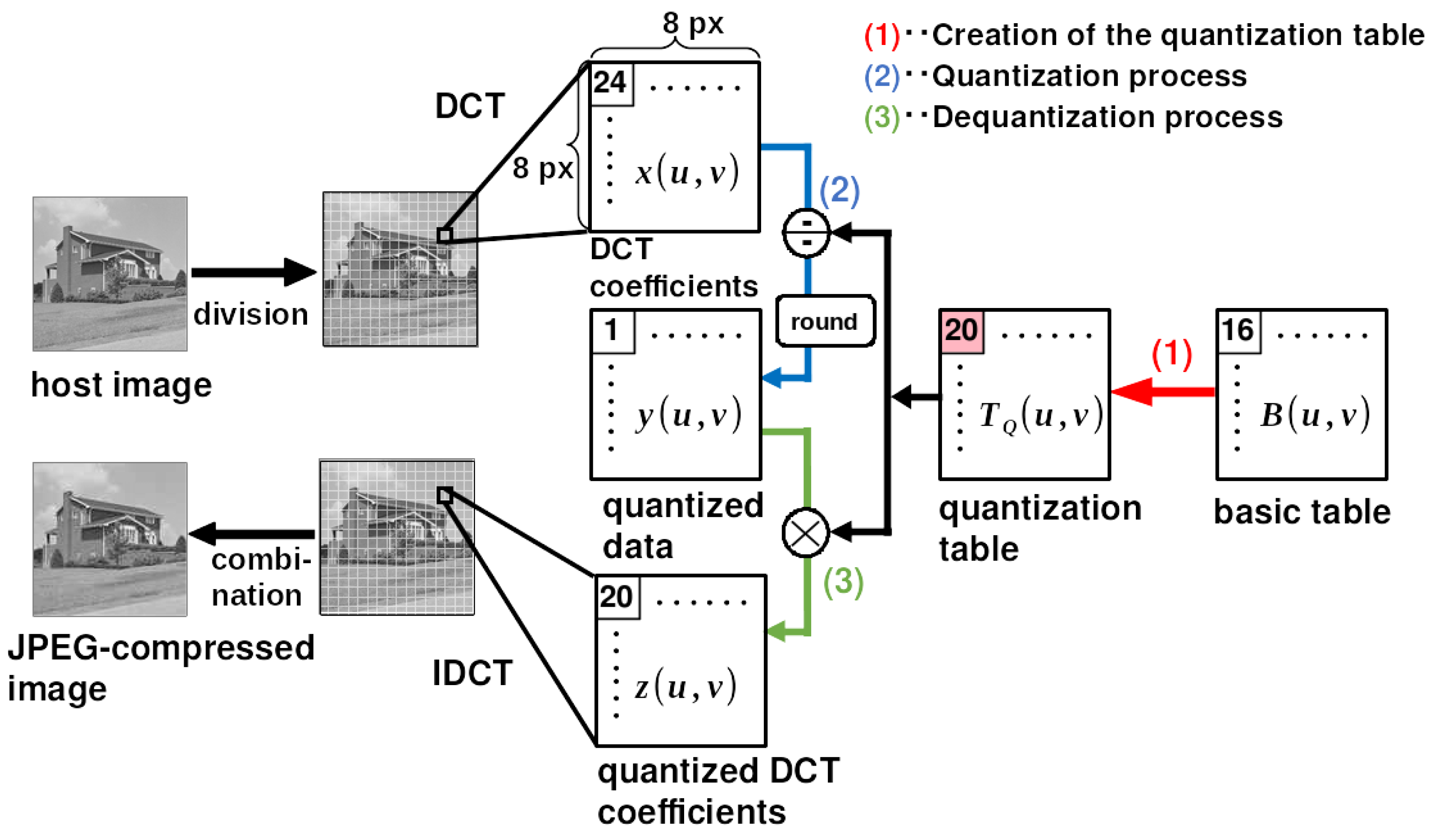
2. Preliminary: JPEG Quantization
3. Related Works
3.1. ReDMark
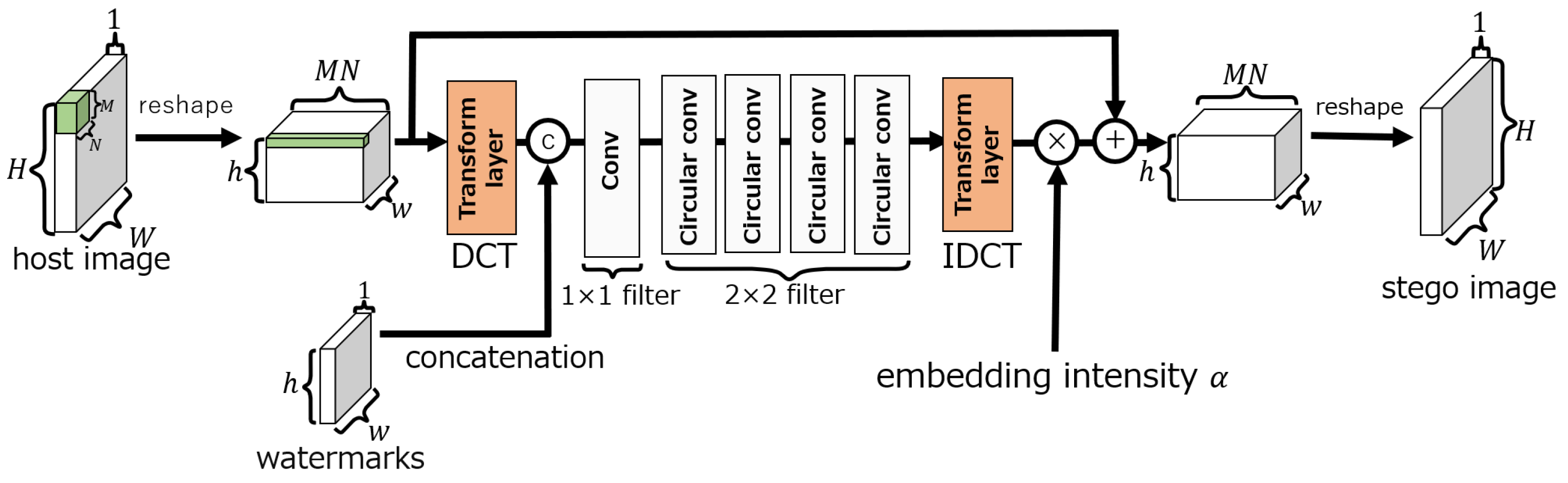
3.1.1. Embedding Network
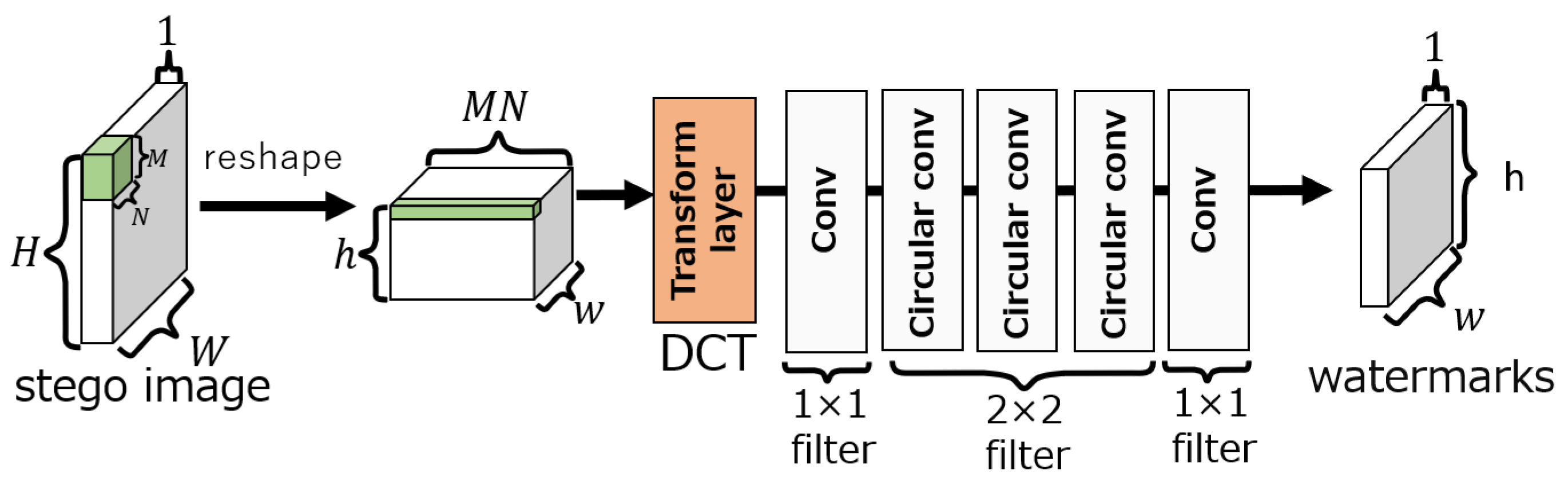
3.1.2. Extraction network
3.1.3. Attack Layer
3.2. JPEGdiff
3.3. Previous work
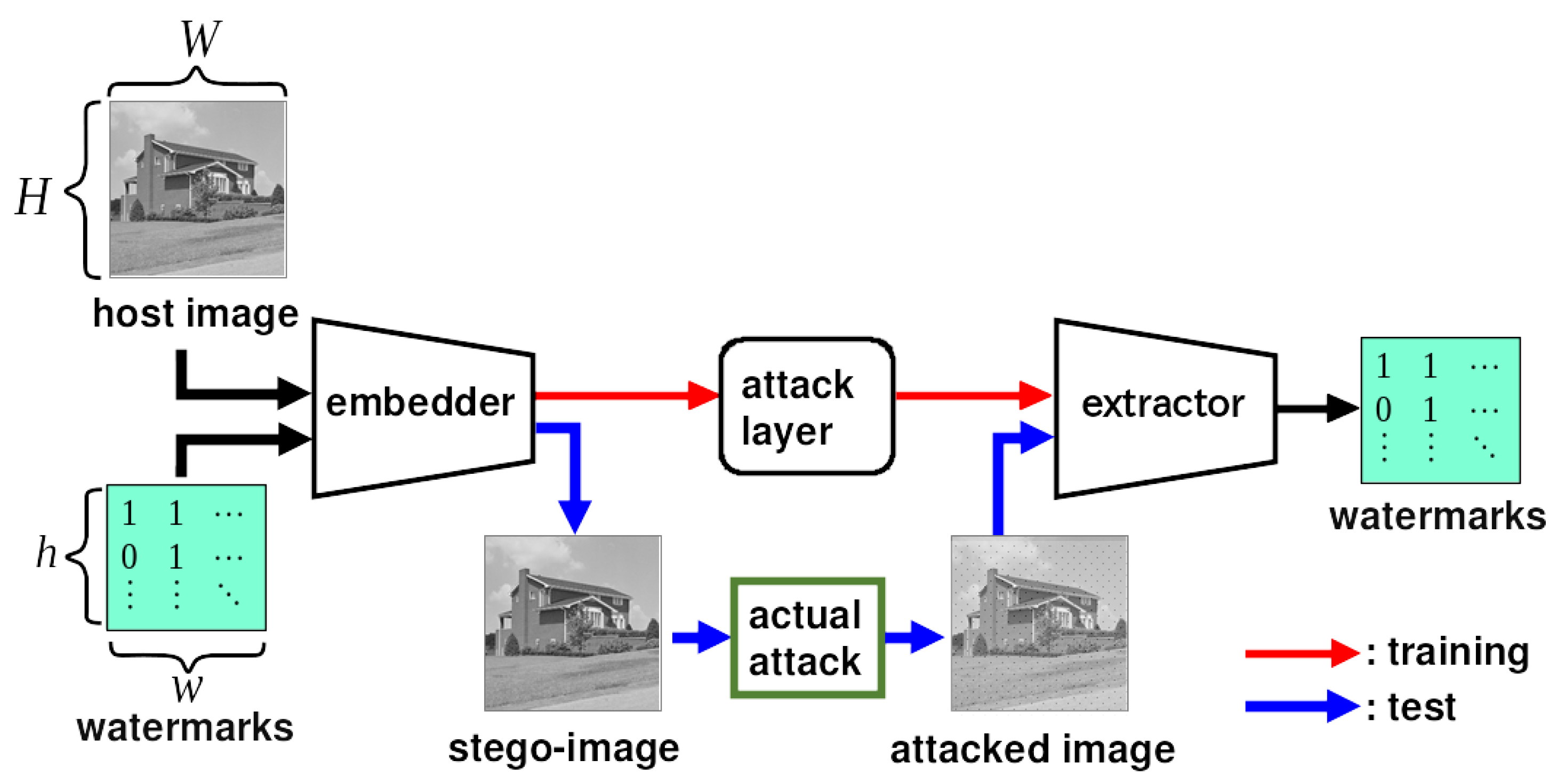
4. Proposed Method
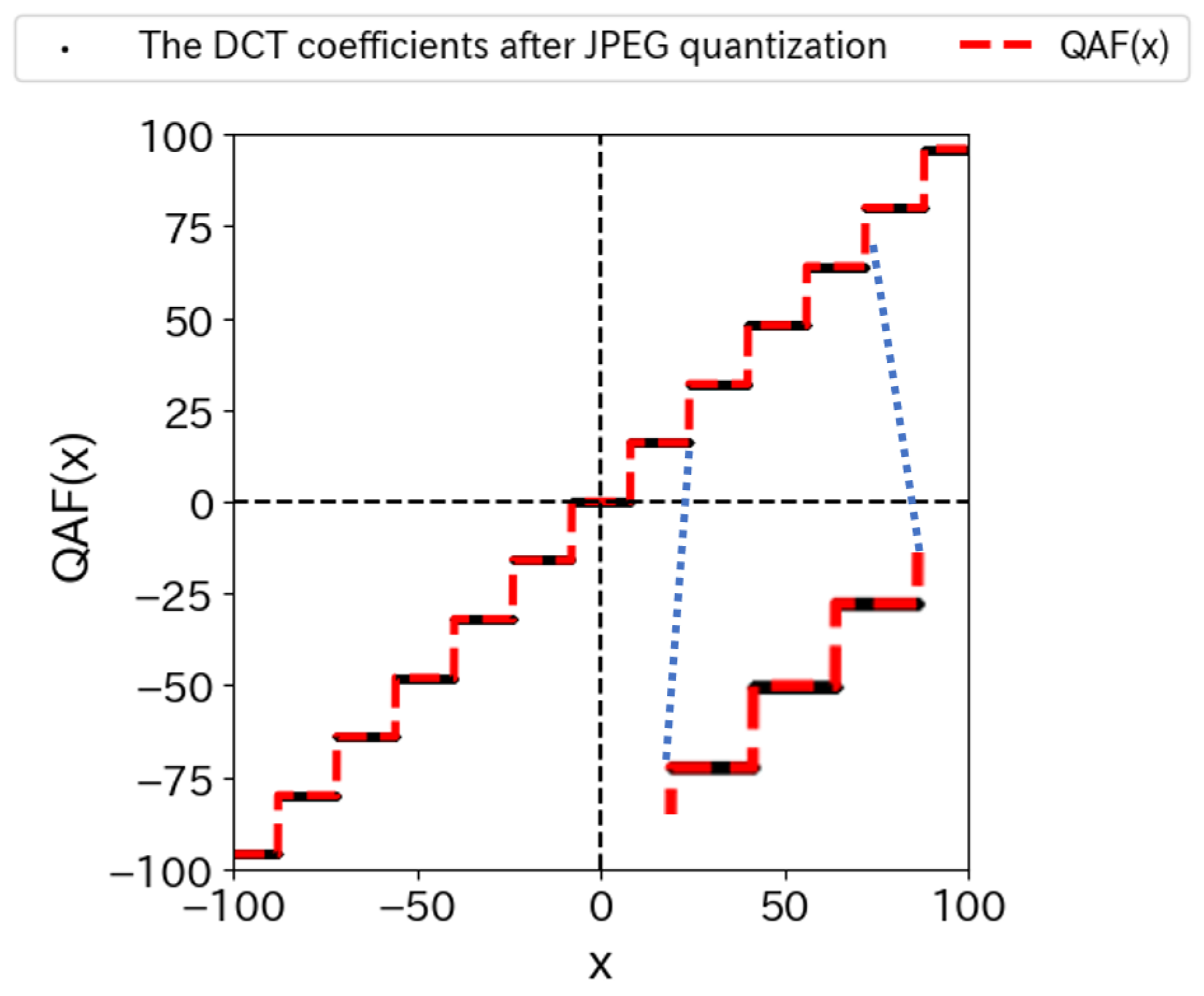
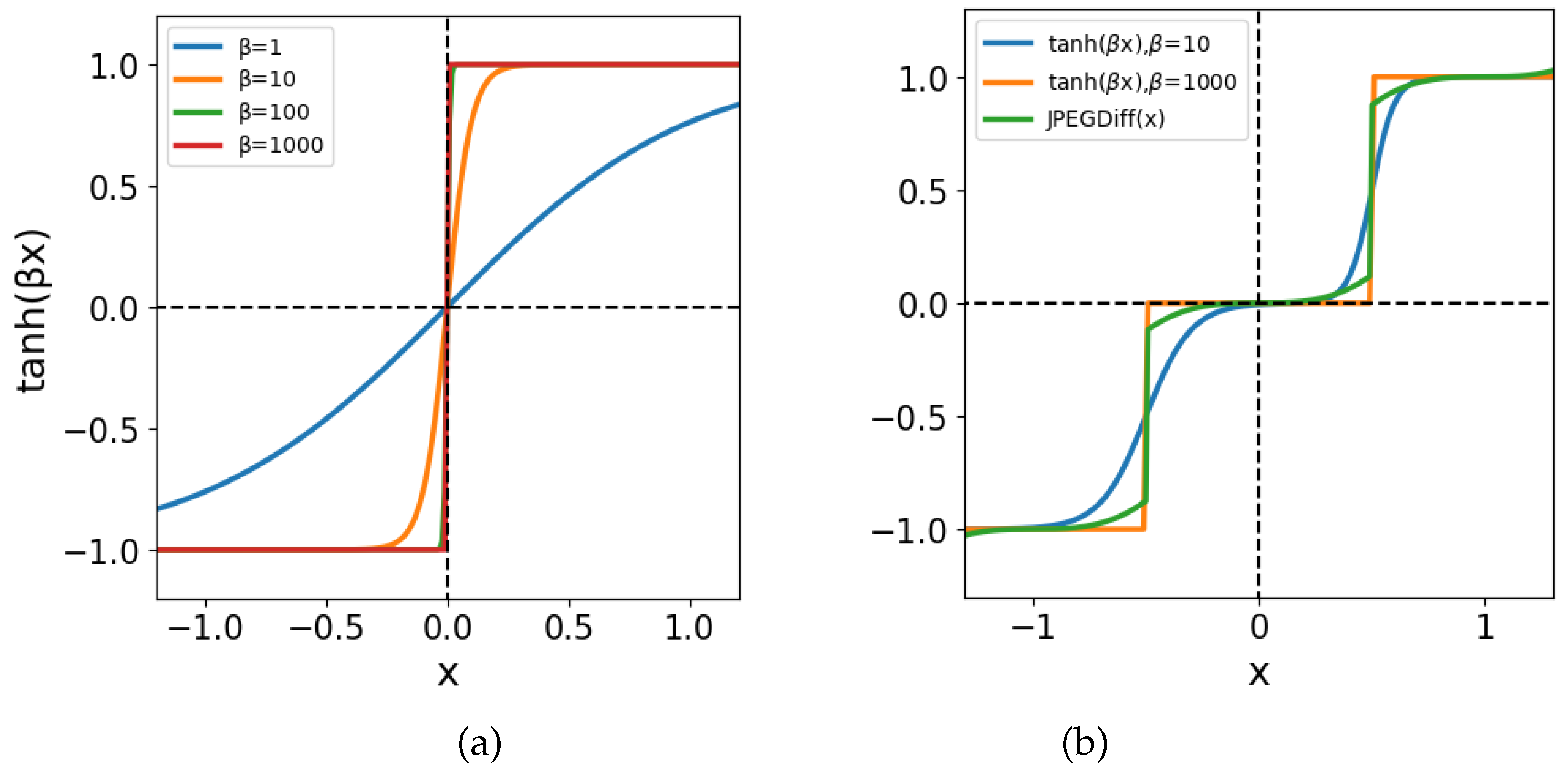
4.1. Quantized Activation Function
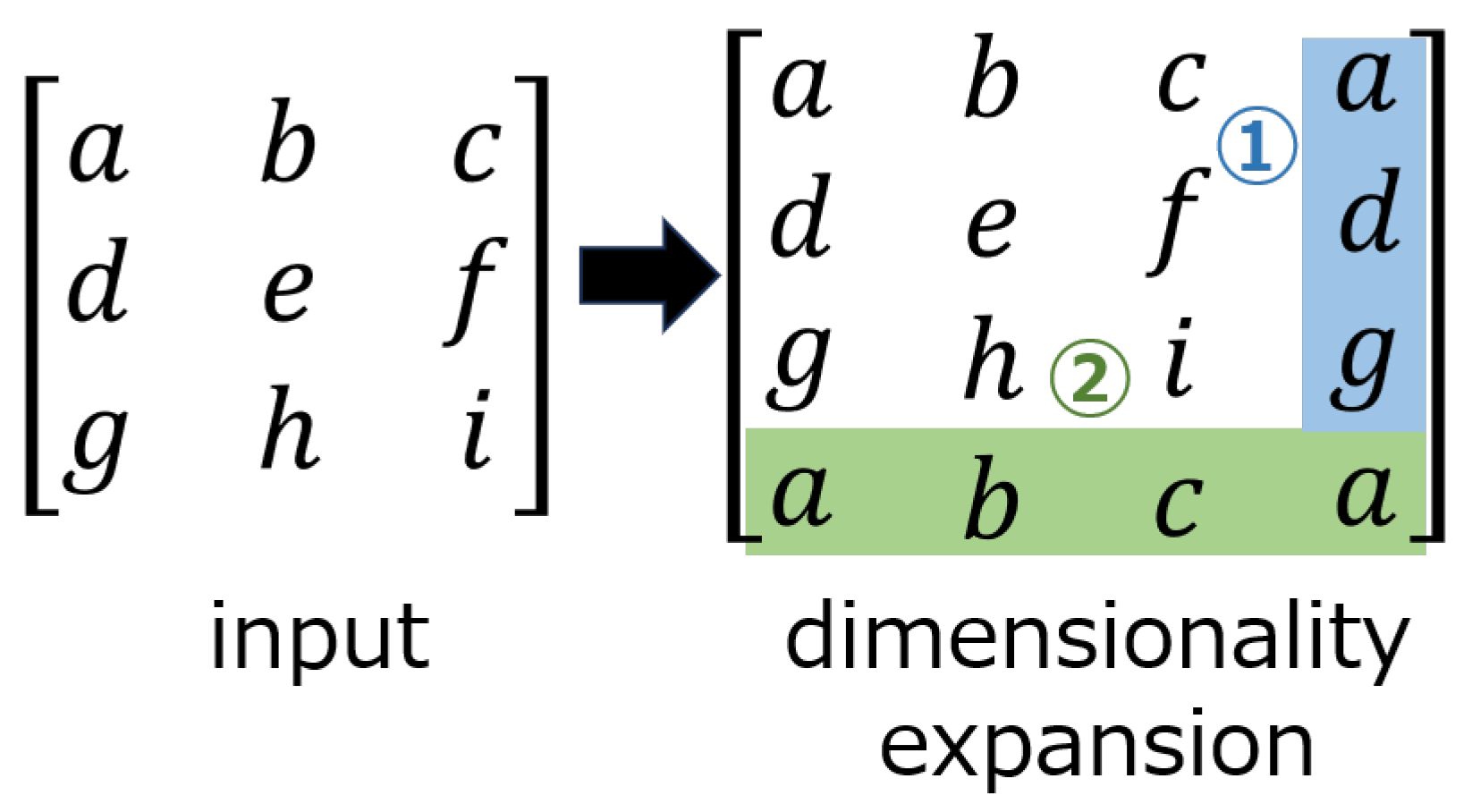
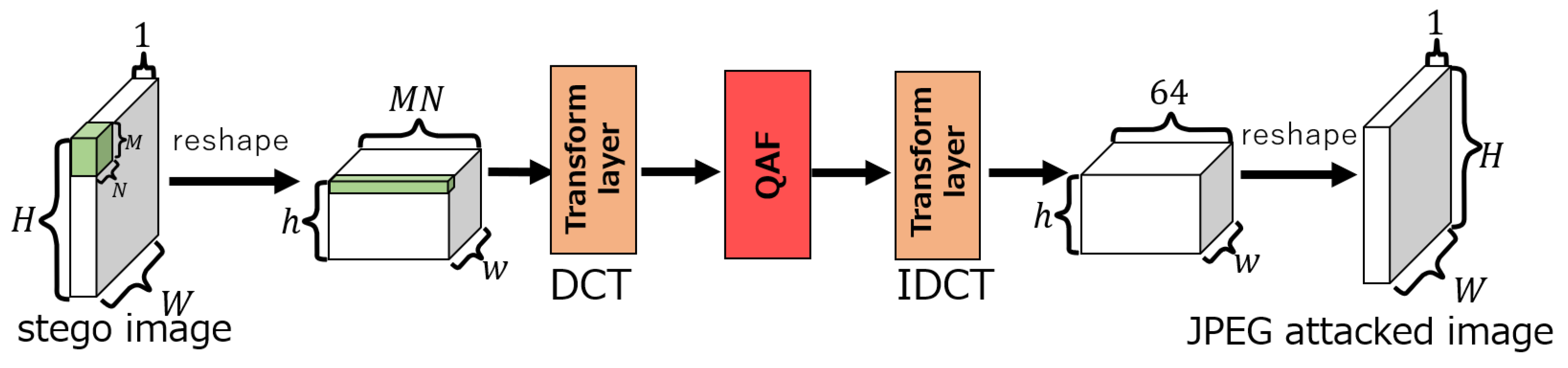
4.2. Proposed Attack Layer
4.3. Training Method
5. Computer Simulations
5.1. Evaluation of the QAF
5.2. Evaluation of the Proposed Attack Layer
5.2.1. Experimental Conditions
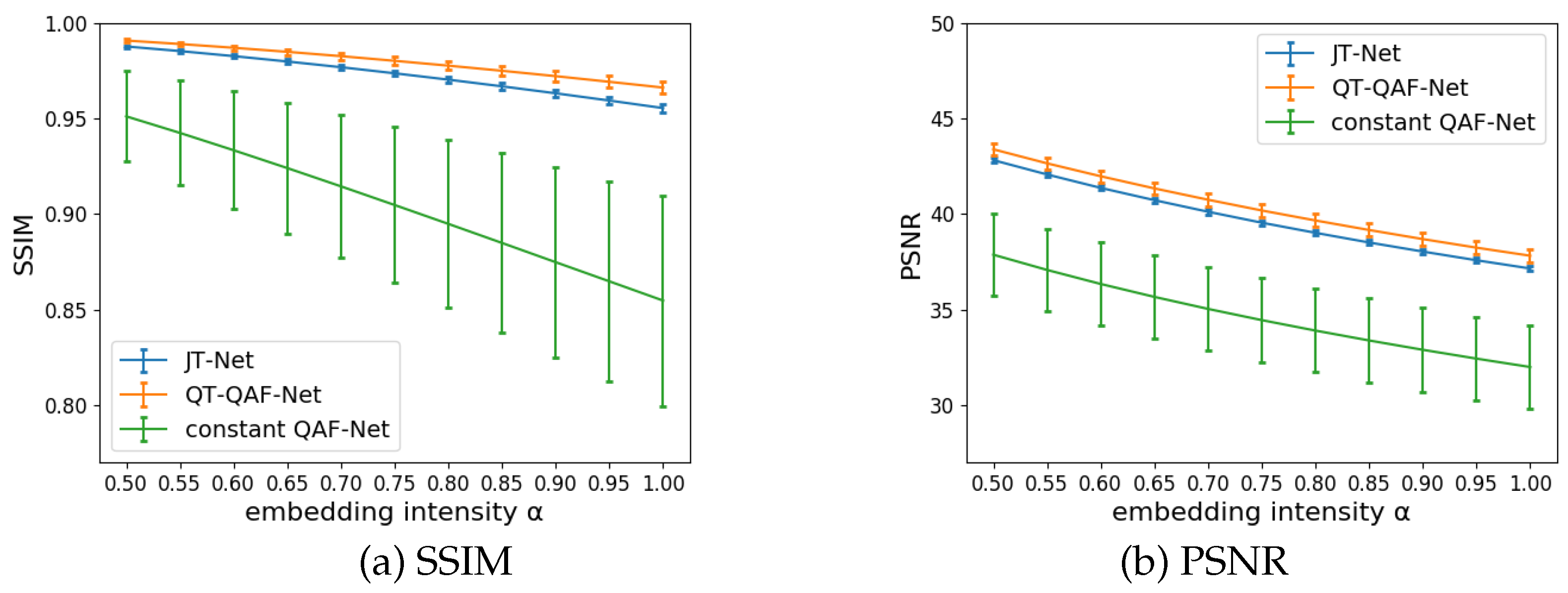
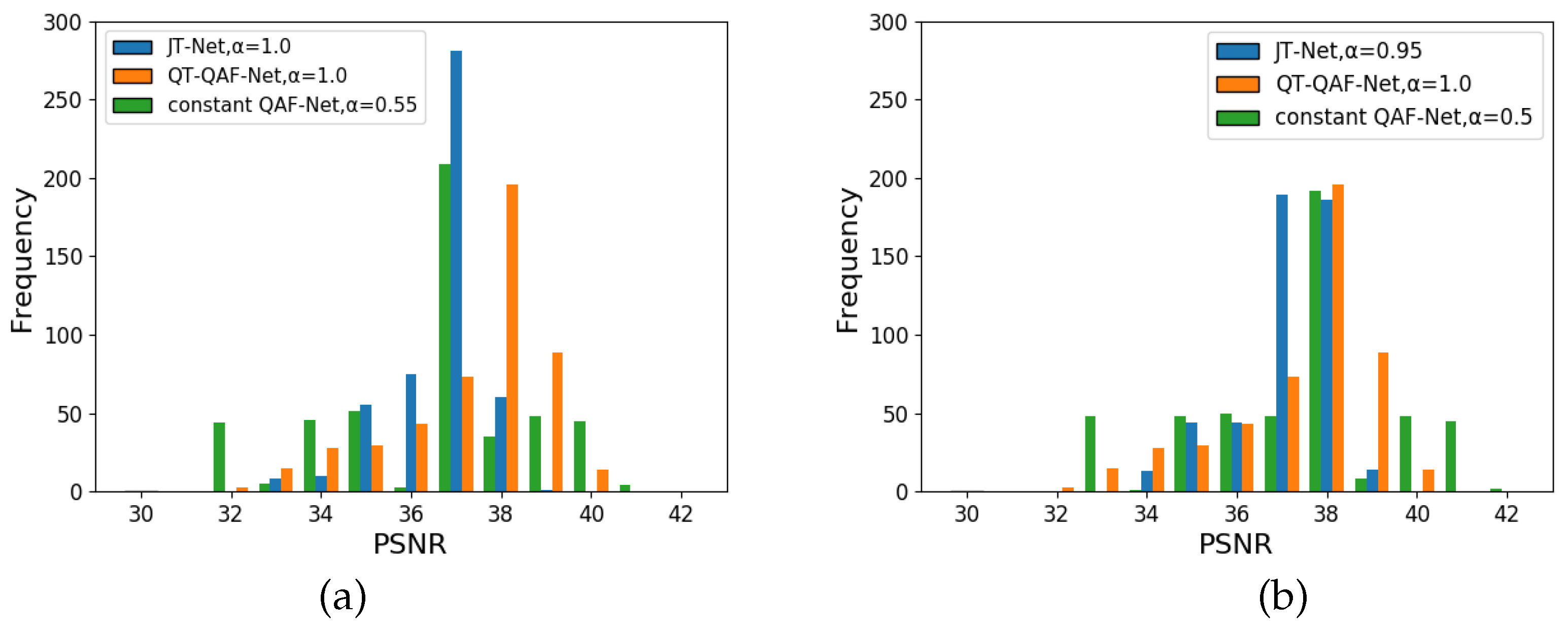
5.2.2. Evaluation of the Image Quality

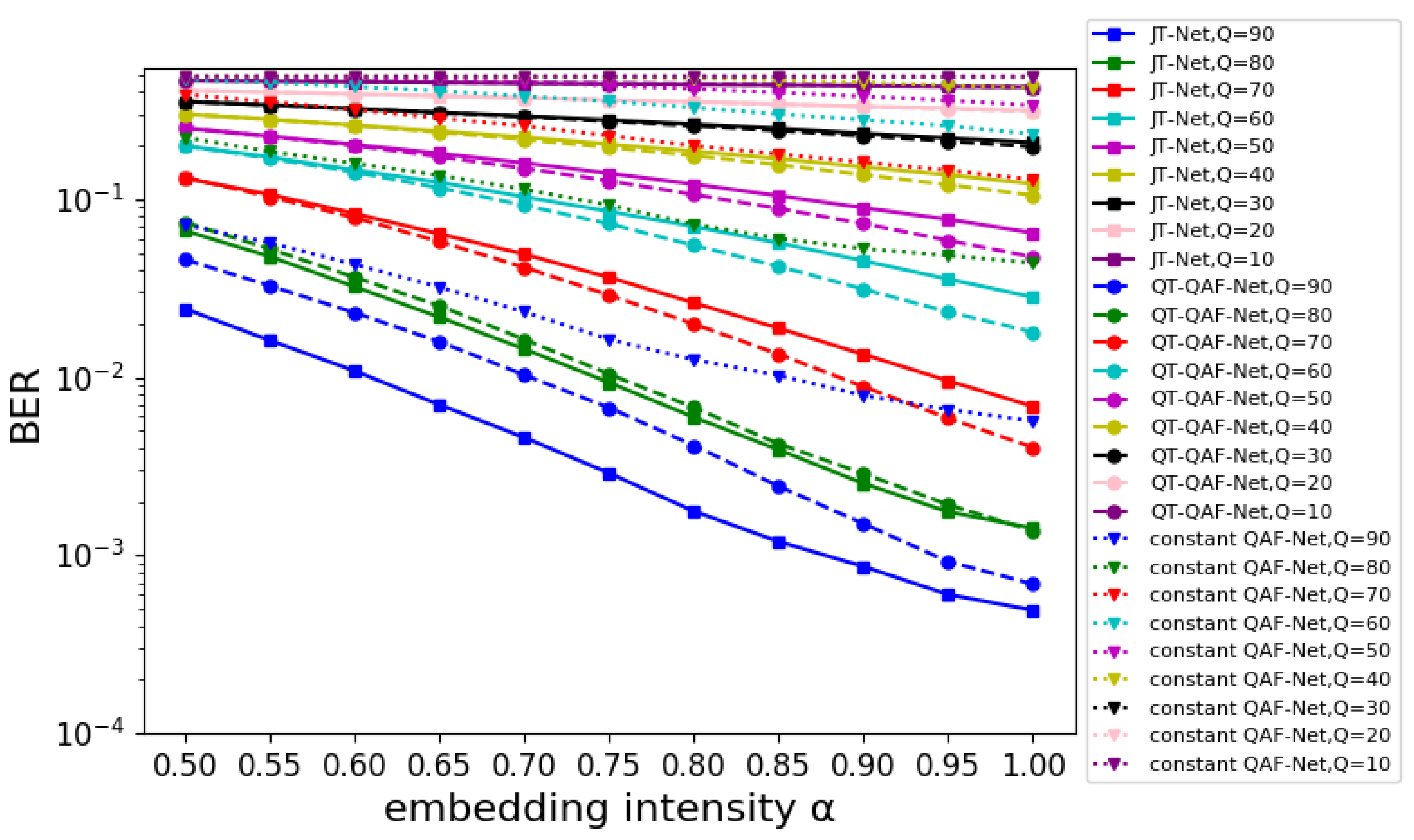
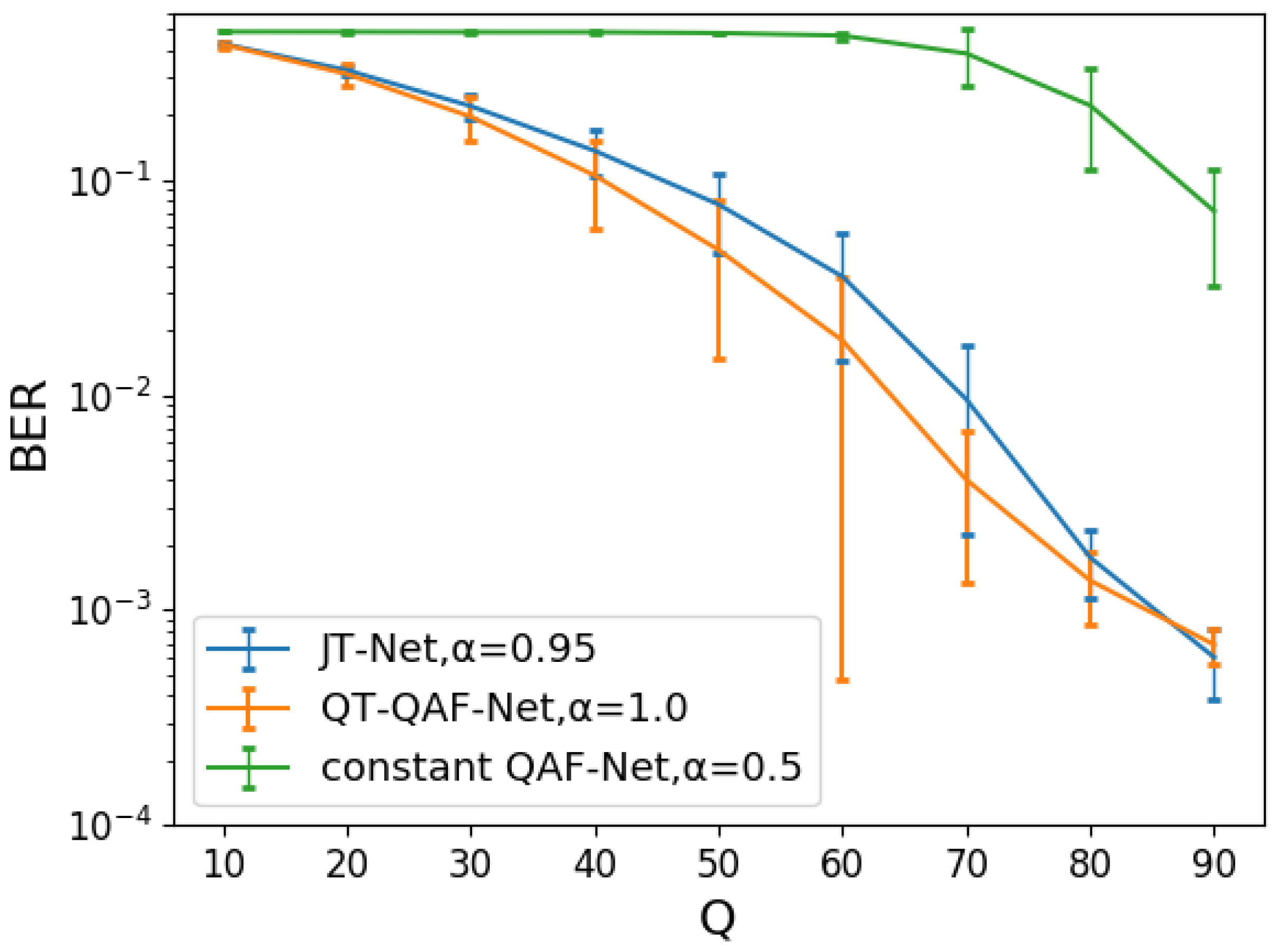
5.2.3. Evaluation of the BER
6. Conclusion
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Wan, W.; Wang, J.; Zhang, Y.; Li, J.; Yu, H.; Sun, J. A comprehensive survey on robust image watermarking. Neurocomputing 2022, 488, 226–247, . [CrossRef]
- M. Vafaei, H. M.-Nasab and H. Pourghassem, “A new robust blind watermarking method based on neural networks in wavelet transform domain,”World Applied Sciences Journal, vol. 22, no. 11, pp. 1572–1580, 2013.
- Sy, N.C.; Kha, H.H.; Hoang, N.M. An Efficient Robust Blind Watermarking Method Based on Convolution Neural Networks in Wavelet Transform Domain. Int. J. Mach. Learn. Comput. 2020, 10, 675–684, . [CrossRef]
- He, D.; Xu, K.; Wang, D. Design of multi-scale receptive field convolutional neural network for surface inspection of hot rolled steels. Image Vis. Comput. 2019, 89, 12–20, . [CrossRef]
- Singh, H.K.; Singh, A.K. Digital image watermarking using deep learning. Multimedia Tools Appl. 2023, 83, 2979–2994, . [CrossRef]
- Hamamoto, I.; Kawamura, M. Image Watermarking Technique Using Embedder and Extractor Neural Networks. IEICE Trans. Inf. Syst. 2019, E102.D, 19–30, . [CrossRef]
- M. Jamali , N. Karimi, P. Khadivi, S. Shirani, S. Samavi “Robust watermarking using diffusion of logo into auto-encoder feature maps,” Multimedia Tools and Applications, vol. 82, pp.45175–45201, 2023.
- J. Zhu, R. Kaplan, J. Johnson, L. Fei-Fei, “HiDDeN: hiding data with deep networks,” European Conference on Computer Vision, 2018.
- Zhao, Y.; Wang, C.; Zhou, X.; Qin, Z. DARI-Mark: Deep Learning and Attention Network for Robust Image Watermarking. Mathematics 2022, 11, 209, . [CrossRef]
- Hamamoto, I.; Kawamura, M. Neural Watermarking Method Including an Attack Simulator against Rotation and Compression Attacks. IEICE Trans. Inf. Syst. 2020, E103.D, 33–41, . [CrossRef]
- Ahmadi, M.; Norouzi, A.; Karimi, N.; Samavi, S.; Emami, A. ReDMark: Framework for residual diffusion watermarking based on deep networks. Expert Syst. Appl. 2019, 146, 113157, . [CrossRef]
- R. Shin, D. Song, “Jpeg-resistant adversarial images,” NIPS 2017 workshop on machine learning and computer security, vol. 1, pp. 8–13, 2017.
- Mareen, H.; Antchougov, L.; Van Wallendael, G.; Lambert, P. Blind deep-learning-based image watermarking robust against geometric transformations, 2024 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 2024, pp. 1-2, 2024.
- S. Yamauchi, M. Kawamura, “Neural network based watermarking trained with quantized activation function,” Asia Pacific Signal and Information Processing Association Annual Summit and Conference 2022, pp. 1608–1613, 2022.
- C. Guo, M. Rana, M. Cisse, L. van der Maaten, “Countering adversarial images using input transformations,” International Conference on Learning Representations, 2018.
- Independent JPEG group, http://www.ijg.org/, (Accessed 2023-05-21).
- D. Clevert, T. Unterthiner, S. Hochreiter, “Fast and accurate deep network learning by exponential linear units (ELUs),” arXiv preprint arXiv:1511.07289, 2015.
- Wang, Z.; Bovik, A.C.; Sheikh, H.R.; Simoncelli, E.P. Image Quality Assessment: From Error Visibility to Structural Similarity. IEEE Trans. Image Process. 2004, 13, 600–612, . [CrossRef]
- D. E. Rumelhart, G. E. Hinton, R. J.Williams, “Learning representations by back-propagating errors,” Nature, vol. 323, no. 6, pp. 533–536, 1986.
- Computer vision group at the University of Granada, dataset of standard 512 × 512 grayscale test images, http://decsai.ugr.es/cvg/CG/base.htm, (Accessed 2023-06-09).
- A. Krizhevsky, V. Nair, G. Hinton, The CIFAR-10 dataset, https://www.cs.toronto.edu/ kriz/cifar.html, (Accessed 2023-06-09).
- Lin, R.; Liu, S.; Jiang, J.; Li, S.; Li, C.; Kuo, C.-C.J. Recovering sign bits of DCT coefficients in digital images as an optimization problem. J. Vis. Commun. Image Represent. 2024, 98, . [CrossRef]


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).



