Submitted:
18 December 2023
Posted:
22 December 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Related Works
1.2. Contributions
1.3. Outline of the Article
2. Security of Legacy Mobile Networks in Vertical Applications
2.1. Security of Vertical Applications in 2G
2.2. Security of Vertical Applications in 3G
2.3. Security of Vertical Applications in 4G
3. Security of 5G Networks in Vertical Applications
3.1. 5G General Threats
3.1.1. Confidentiality
3.1.2. Integrity
3.1.3. Availability
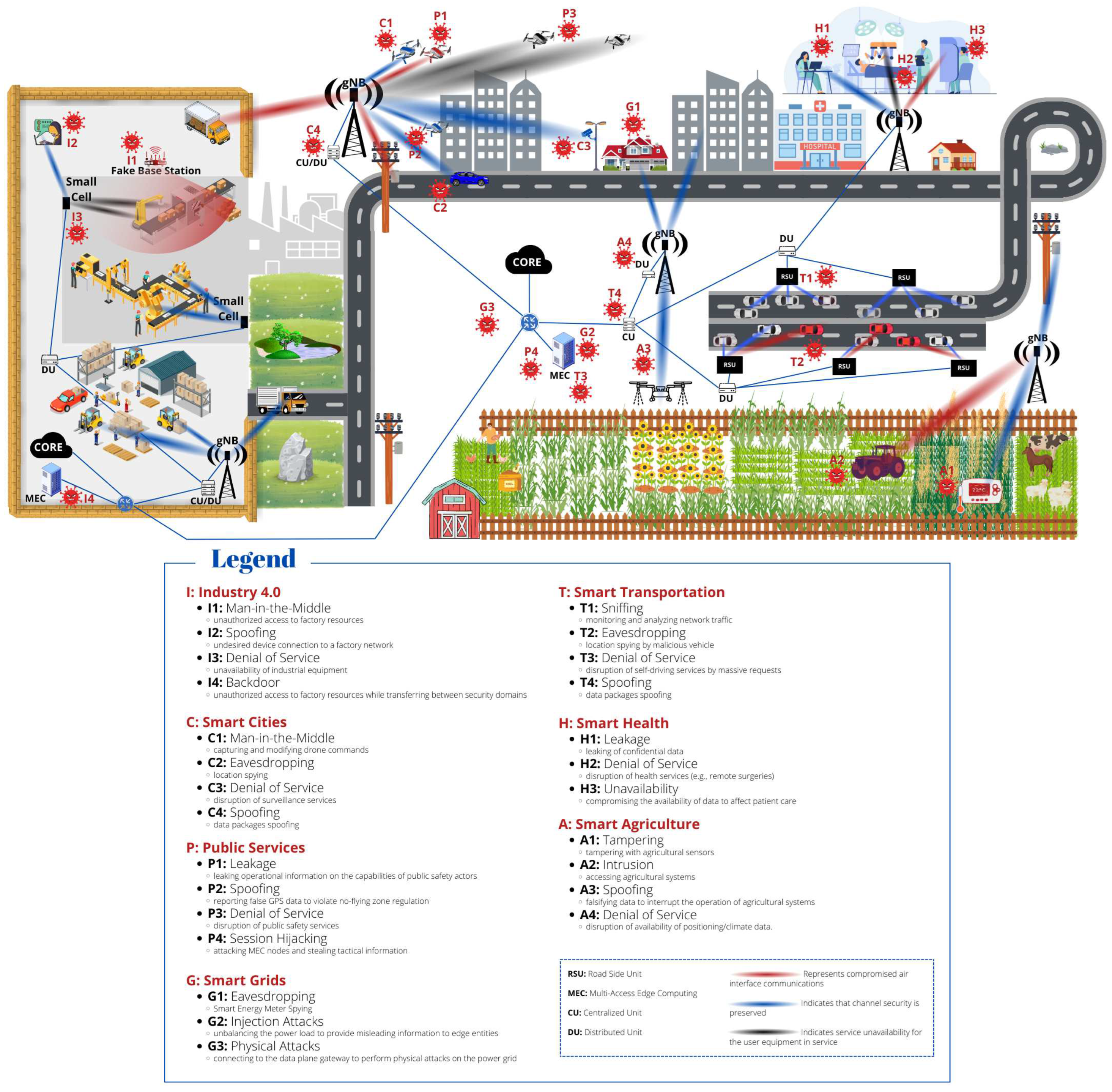
3.2. 5G Vertical Applications Threats
3.3. Security in Smart Cities
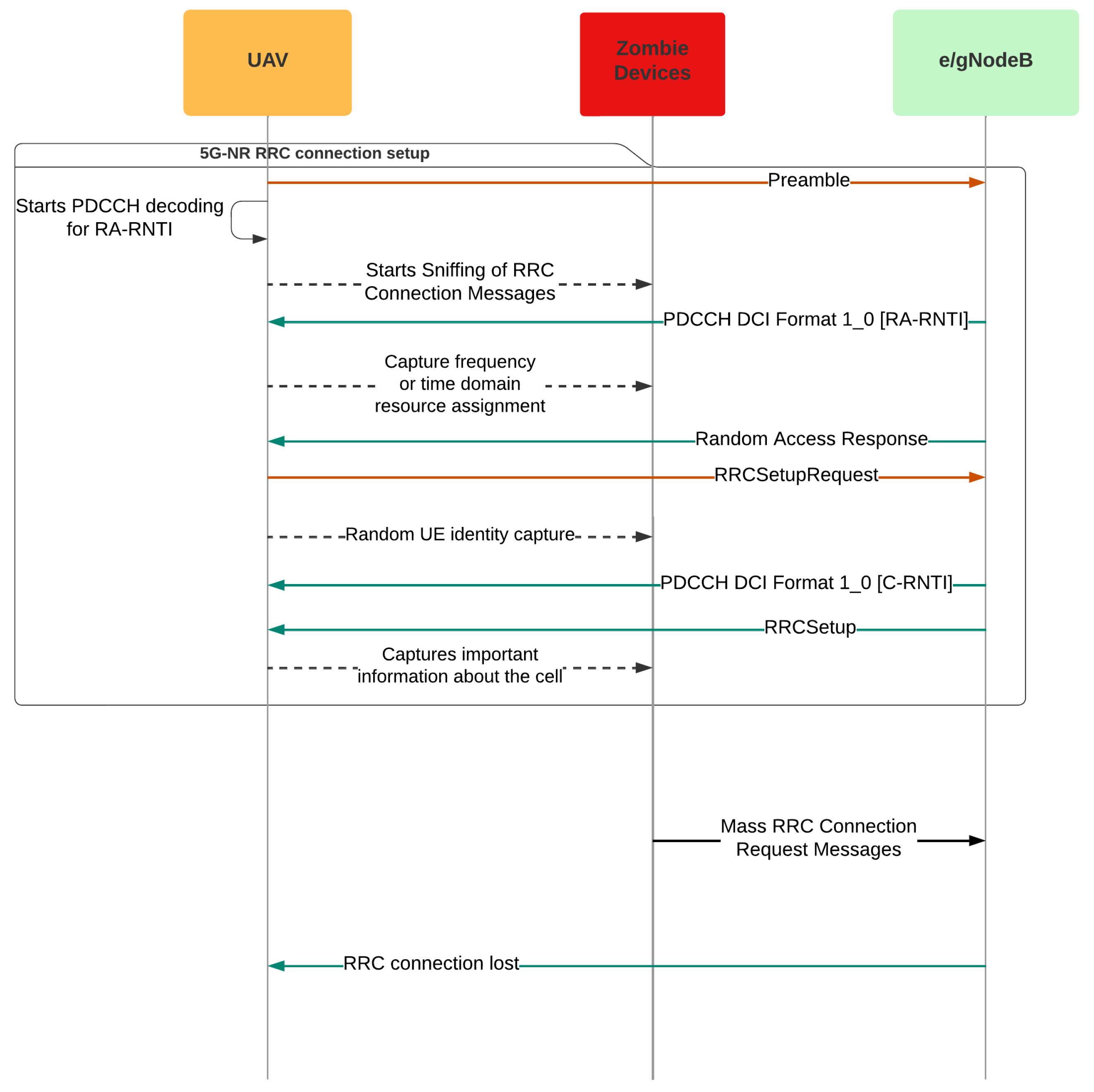
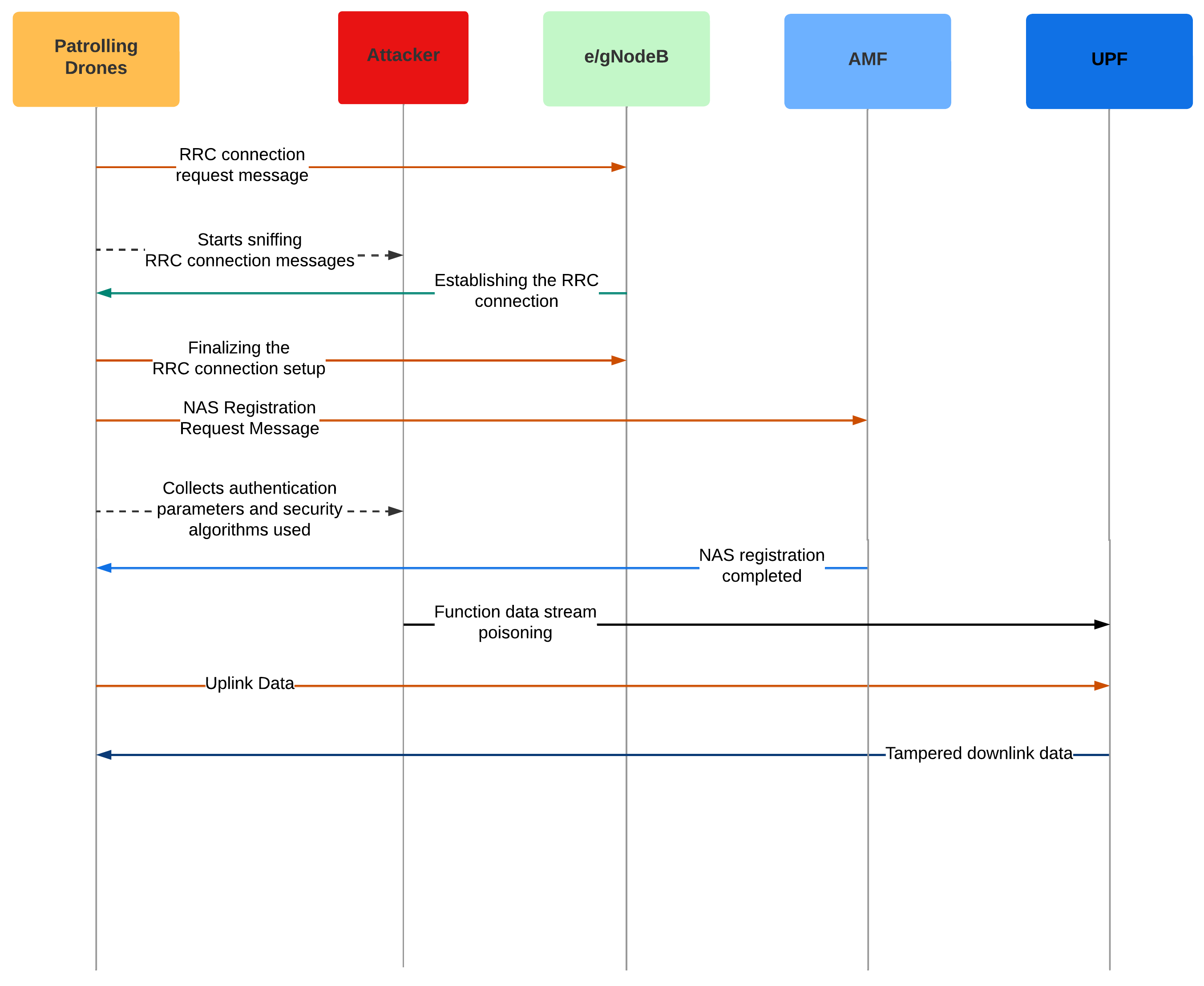
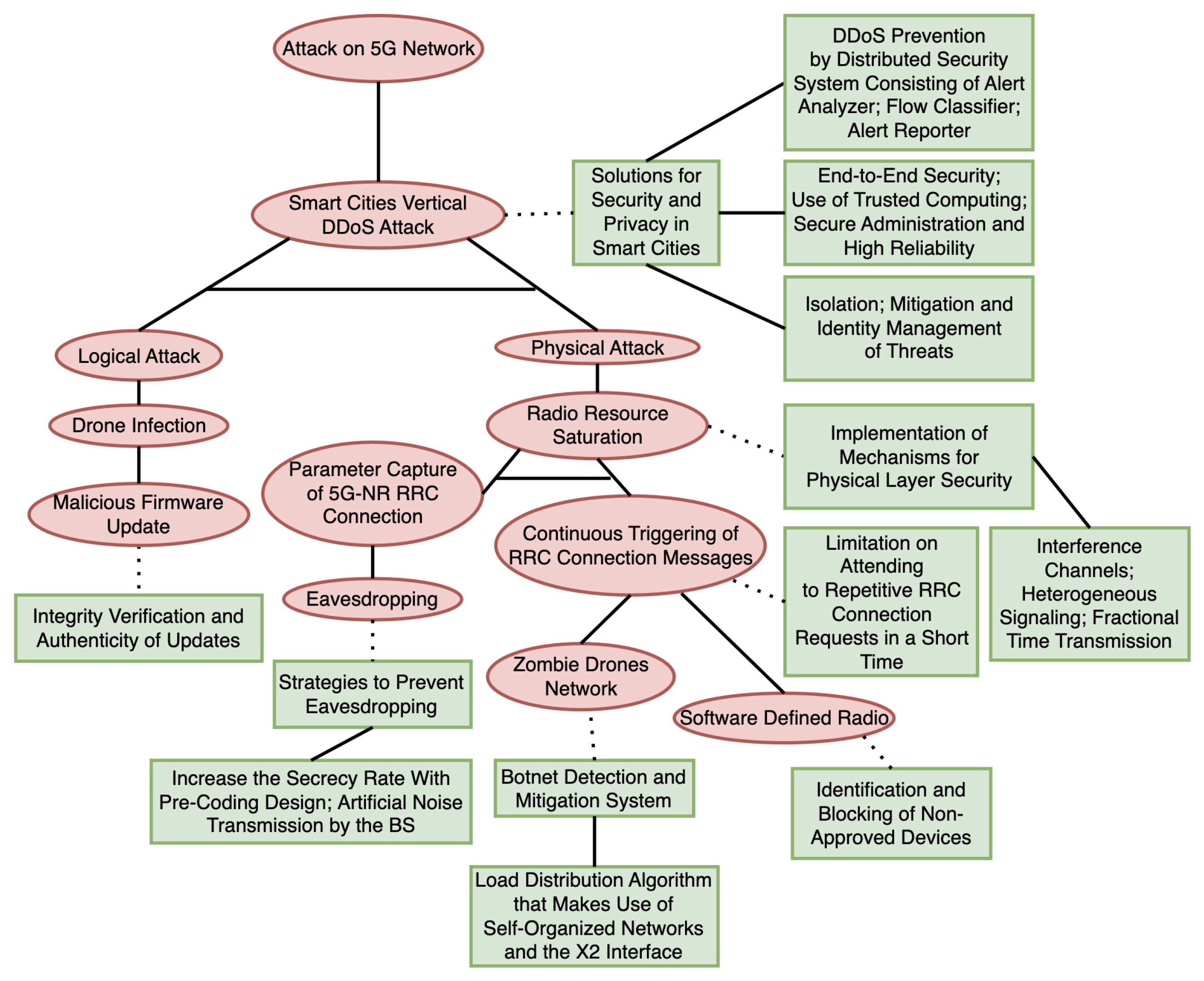
3.3.1. Example of a Smart City Attack Scenario
3.4. Security in Smart Transportation
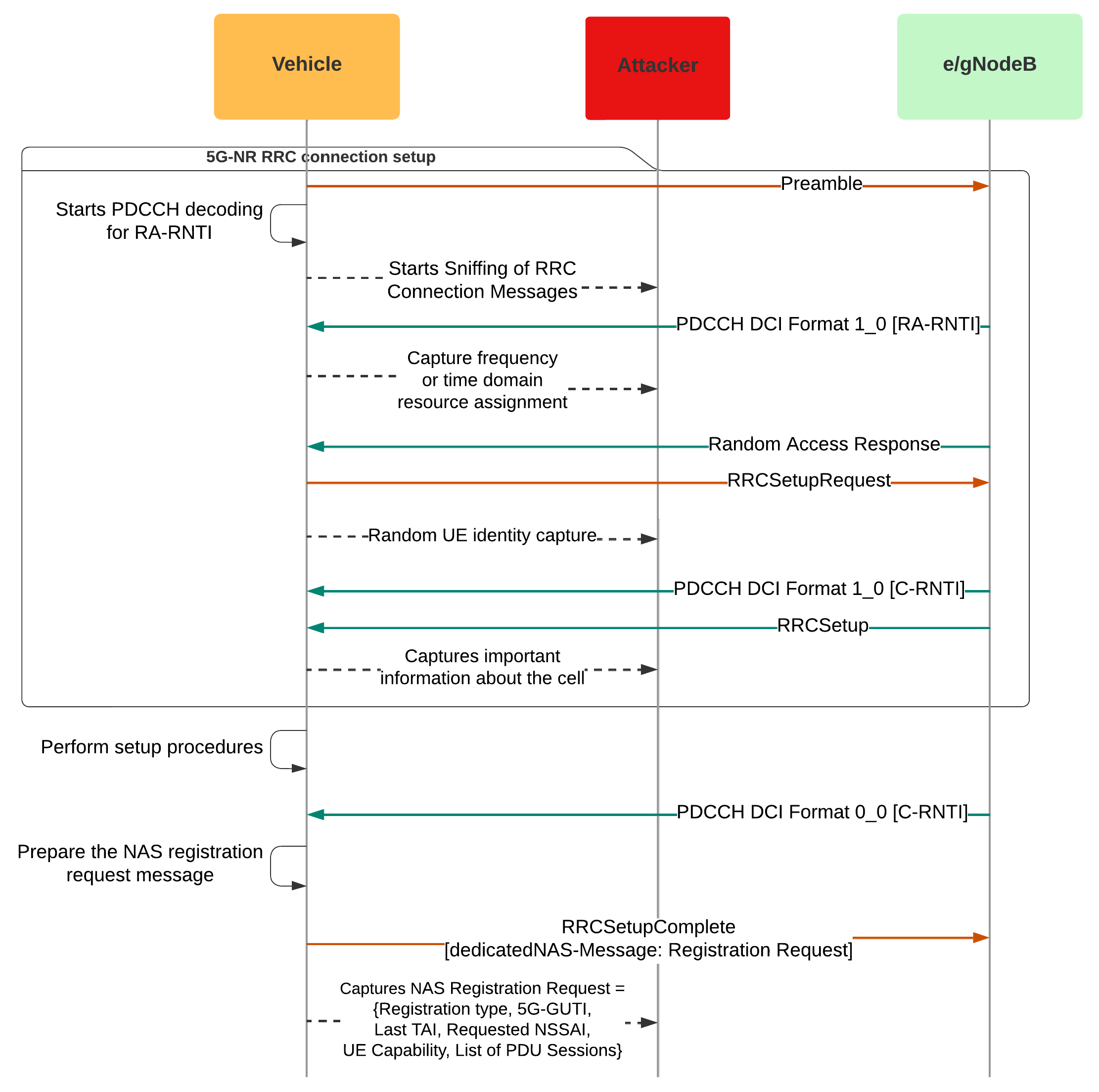
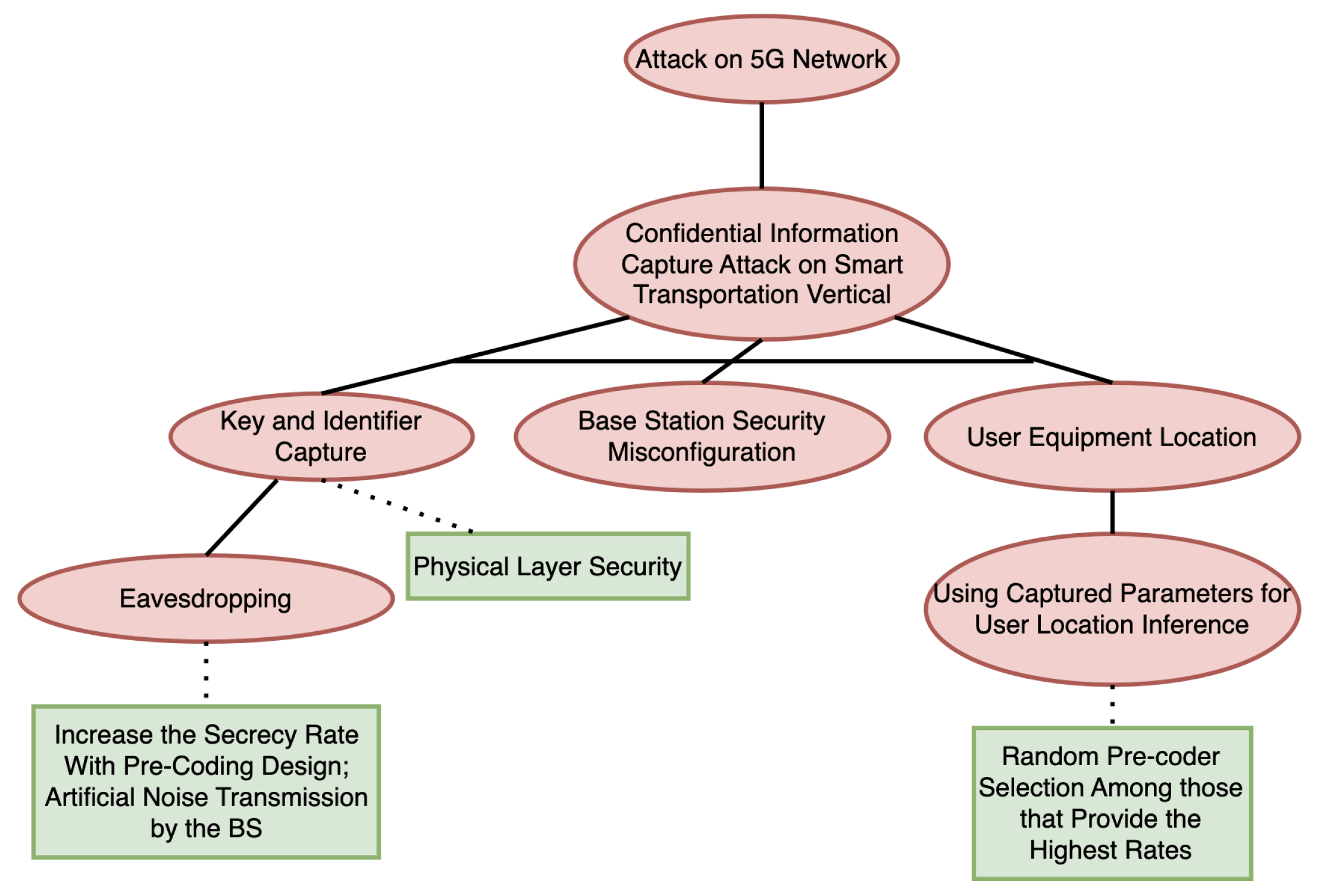
3.4.1. Example of a Smart Transportation Attack Scenario
3.5. Security in Public Services
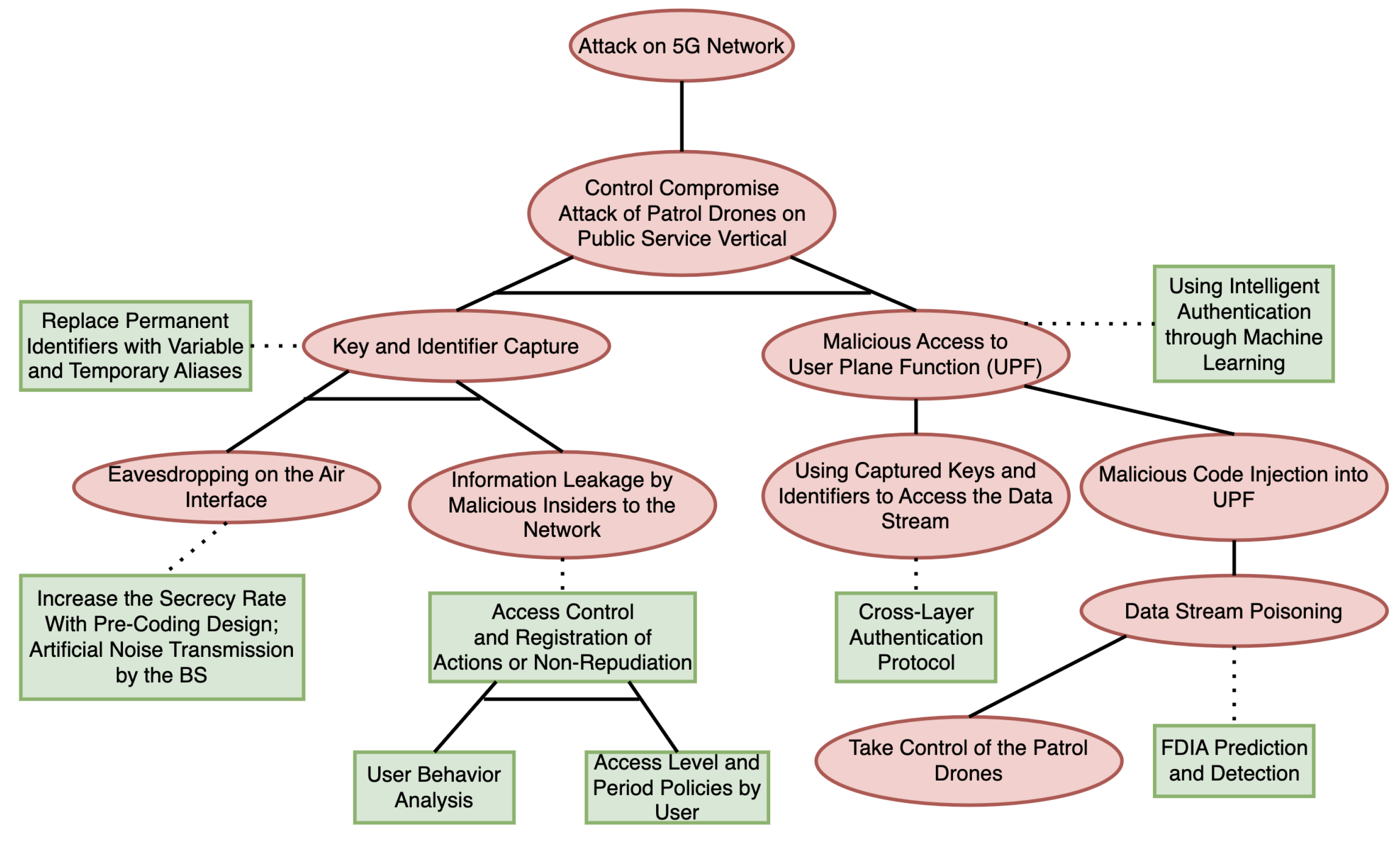
3.5.1. Example of a Public Service Attack Scenario
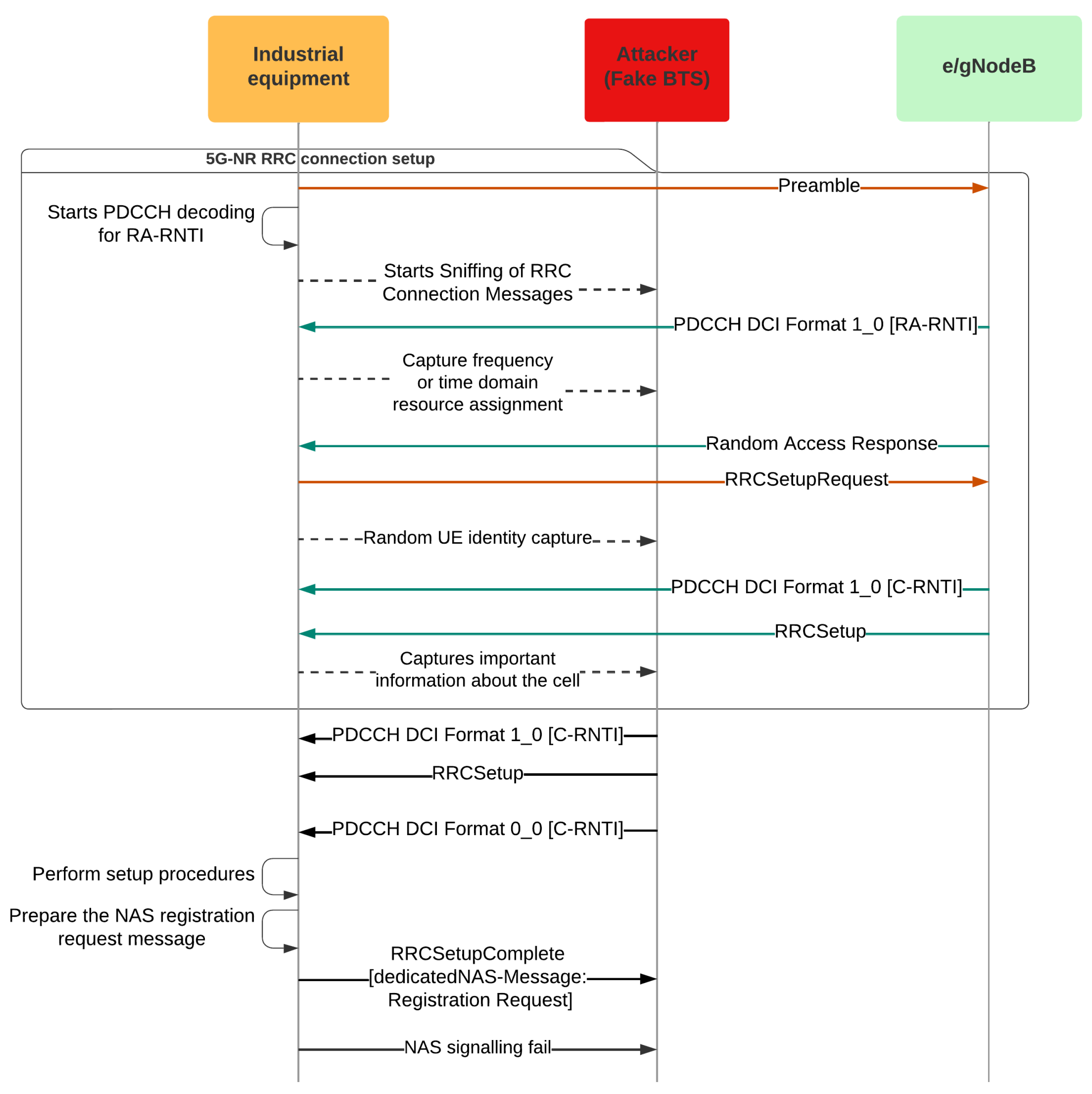
3.6. Security in Industry 4.0
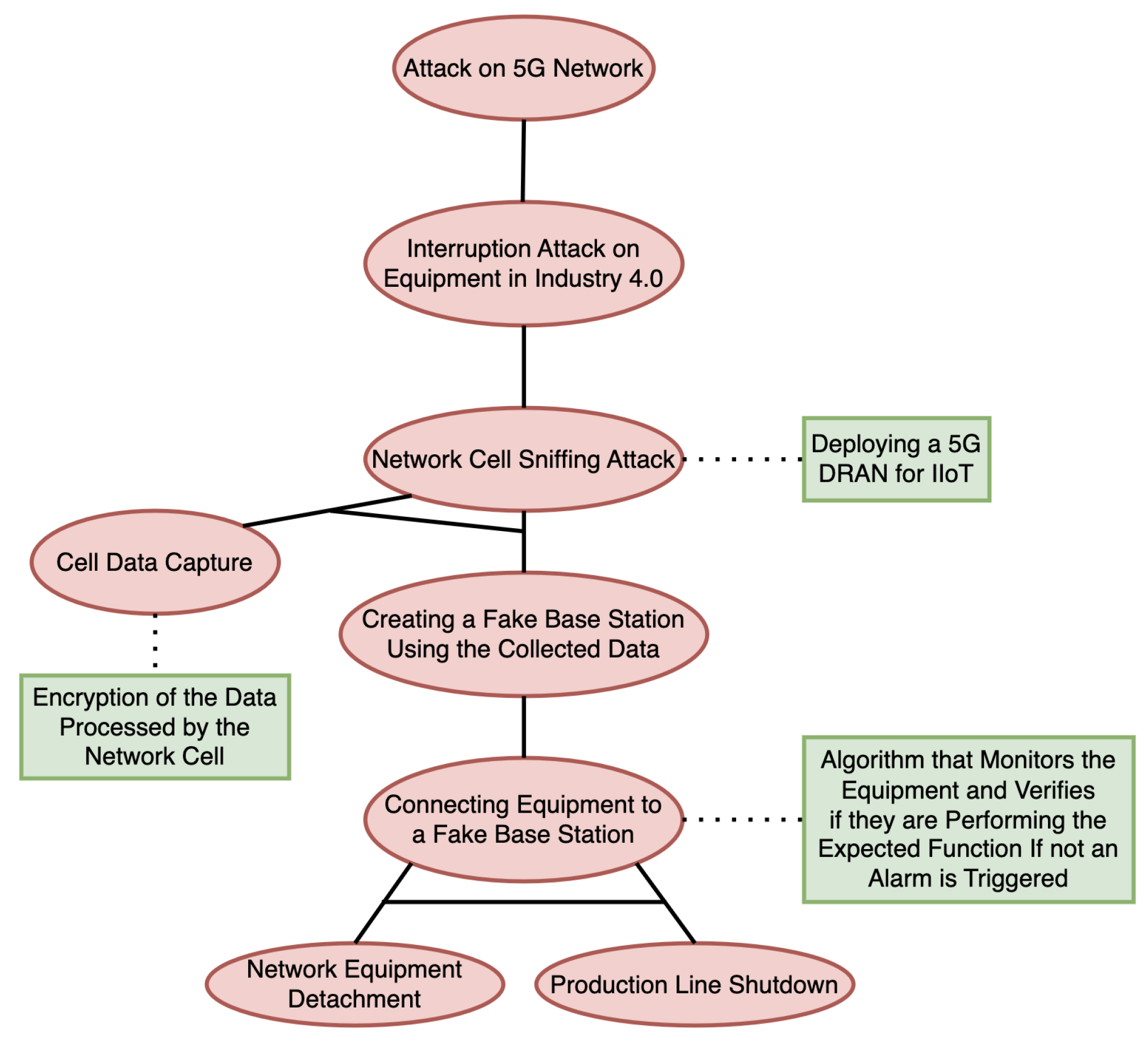
3.6.1. Example of an Industry 4.0 Attack Scenario
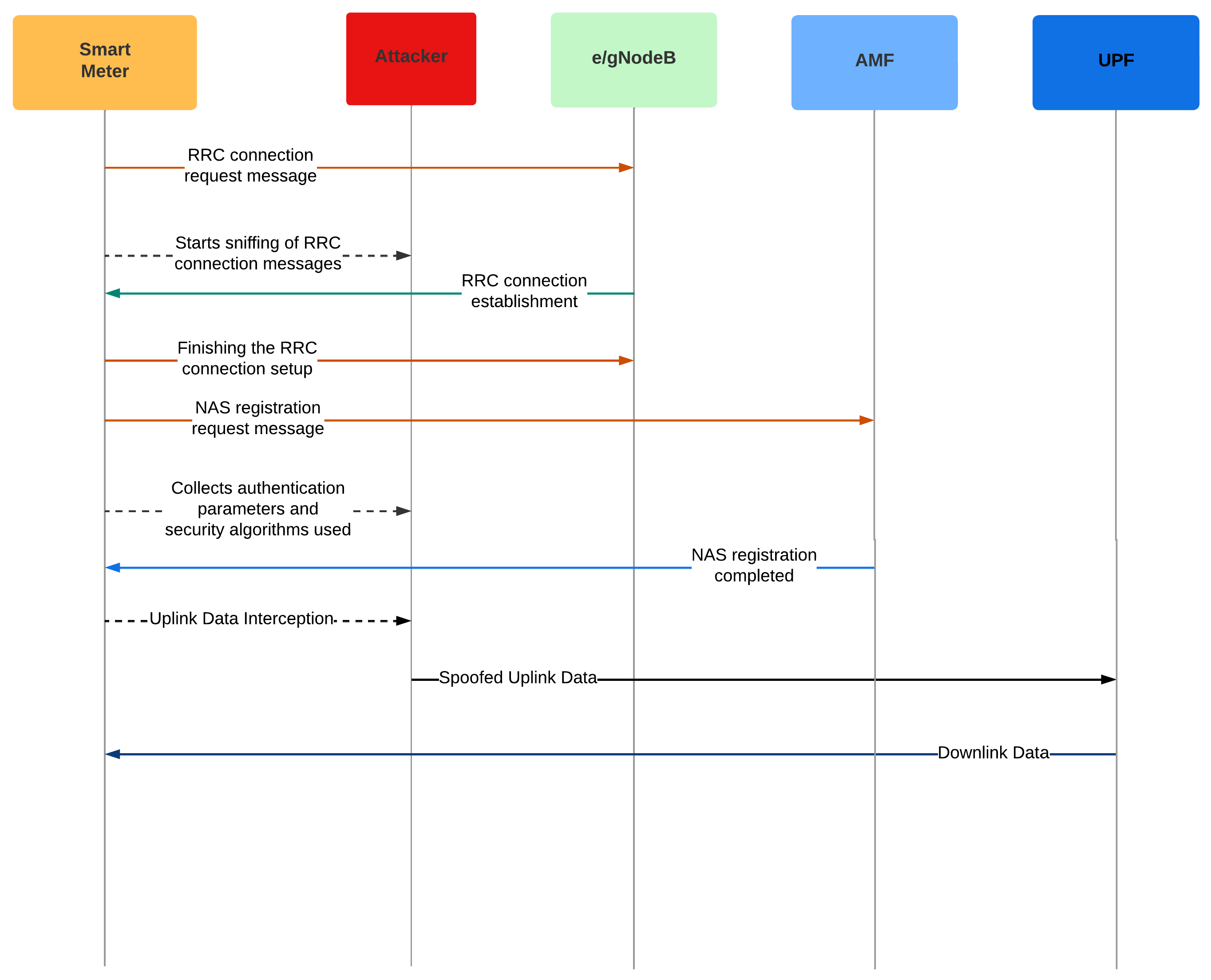
3.7. Security in Smart Grid
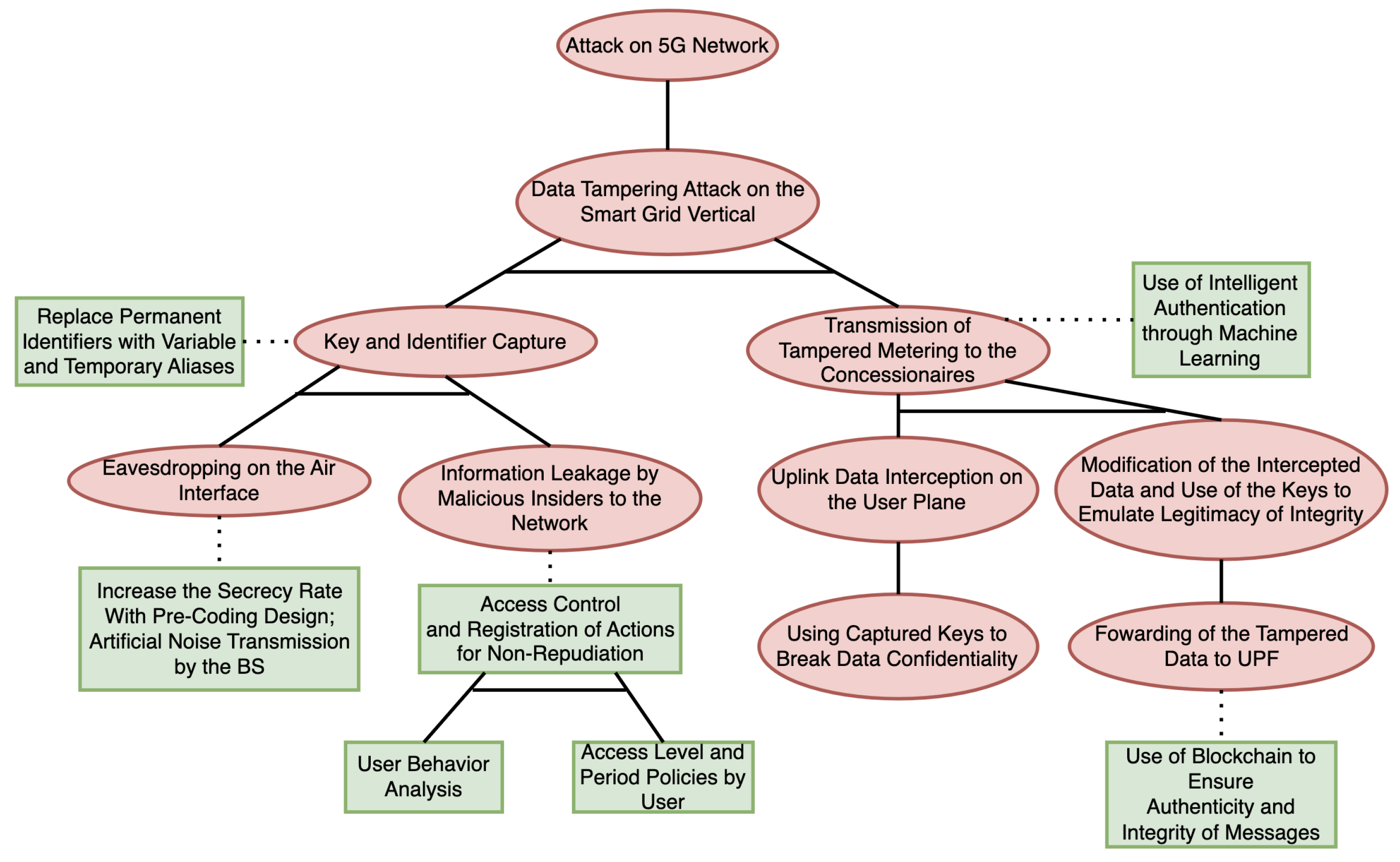
3.7.1. Example of a Smart Grid Attack Scenario
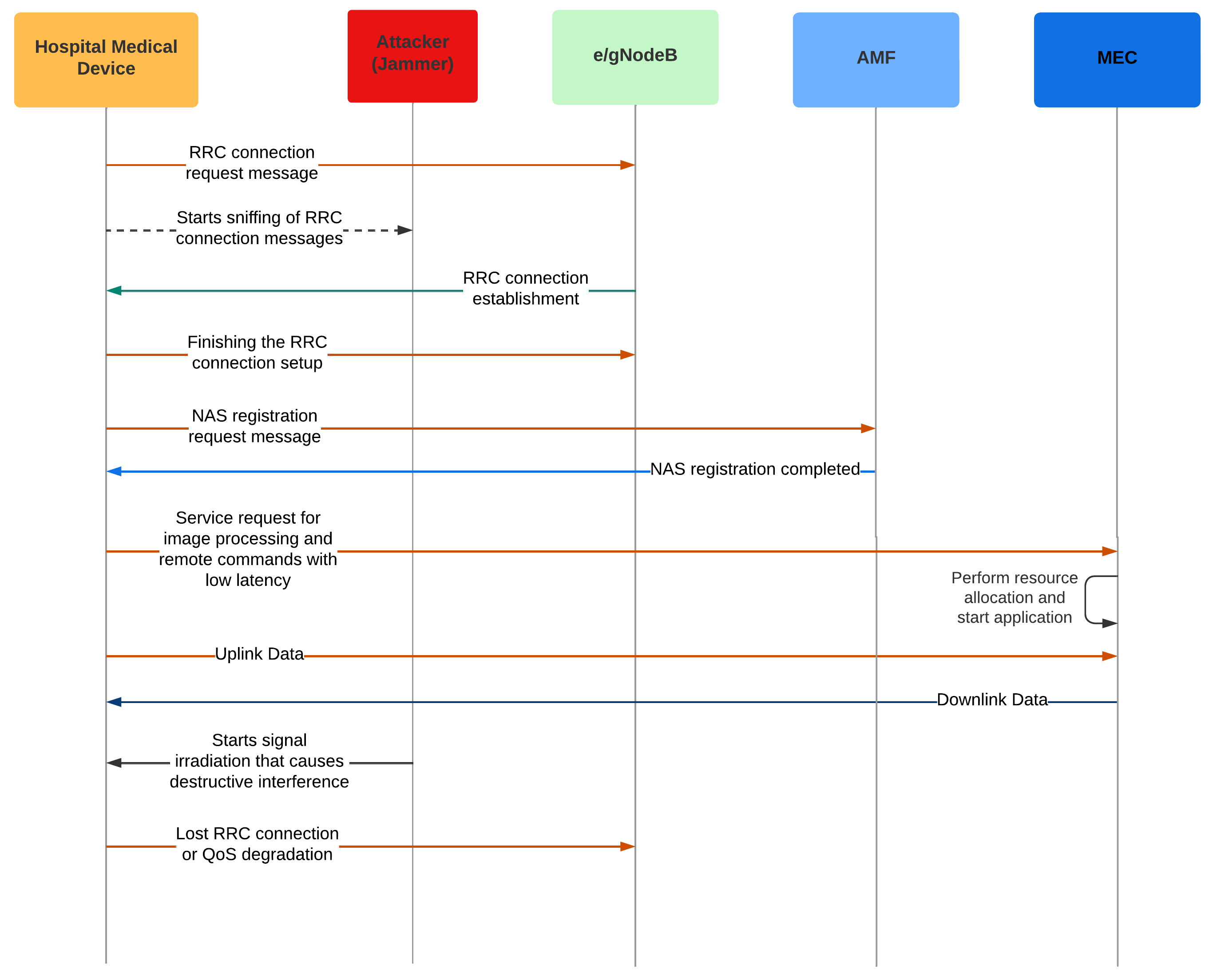
3.8. Security in Smart Health
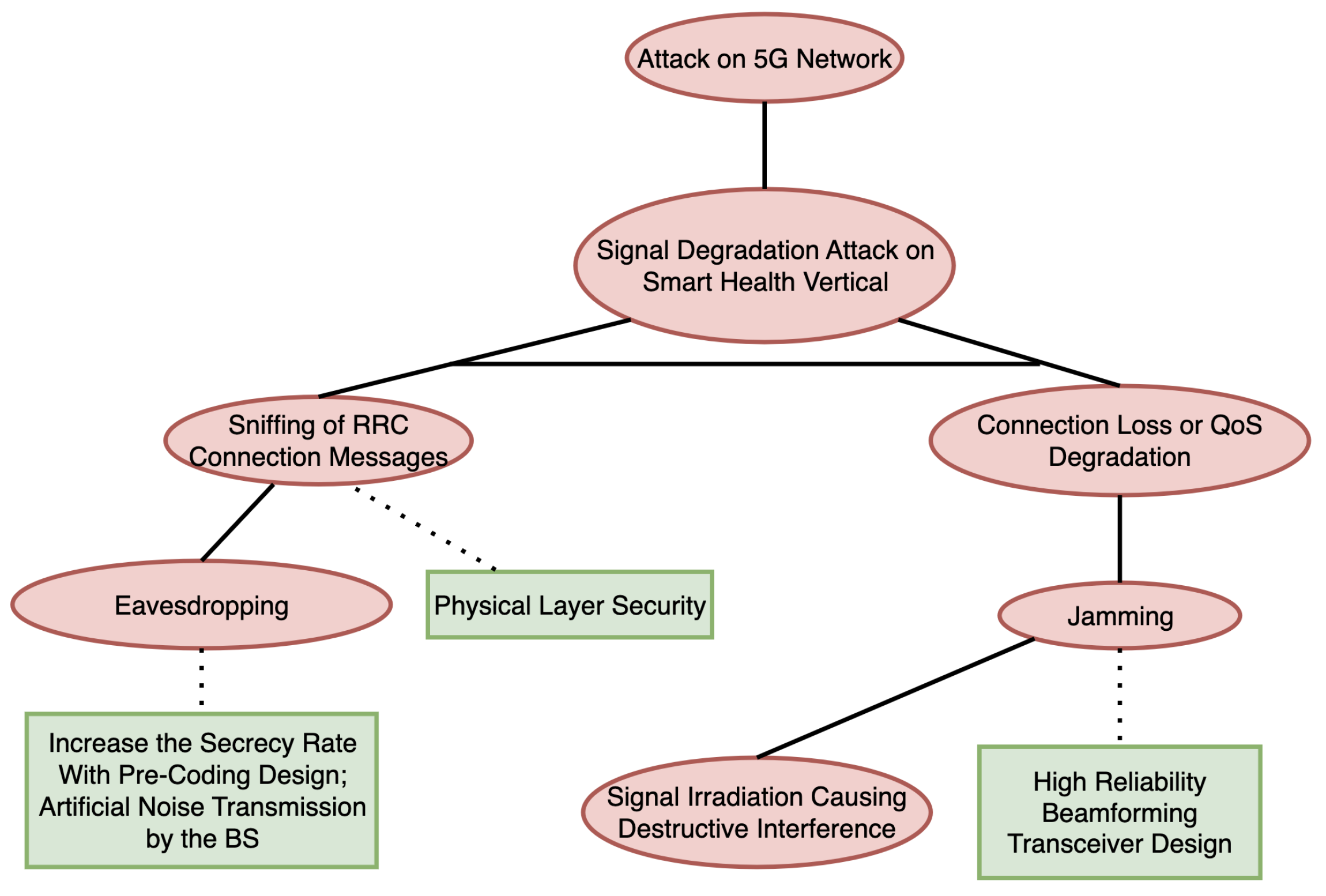
3.8.1. Example of a Smart Health Attack Scenario
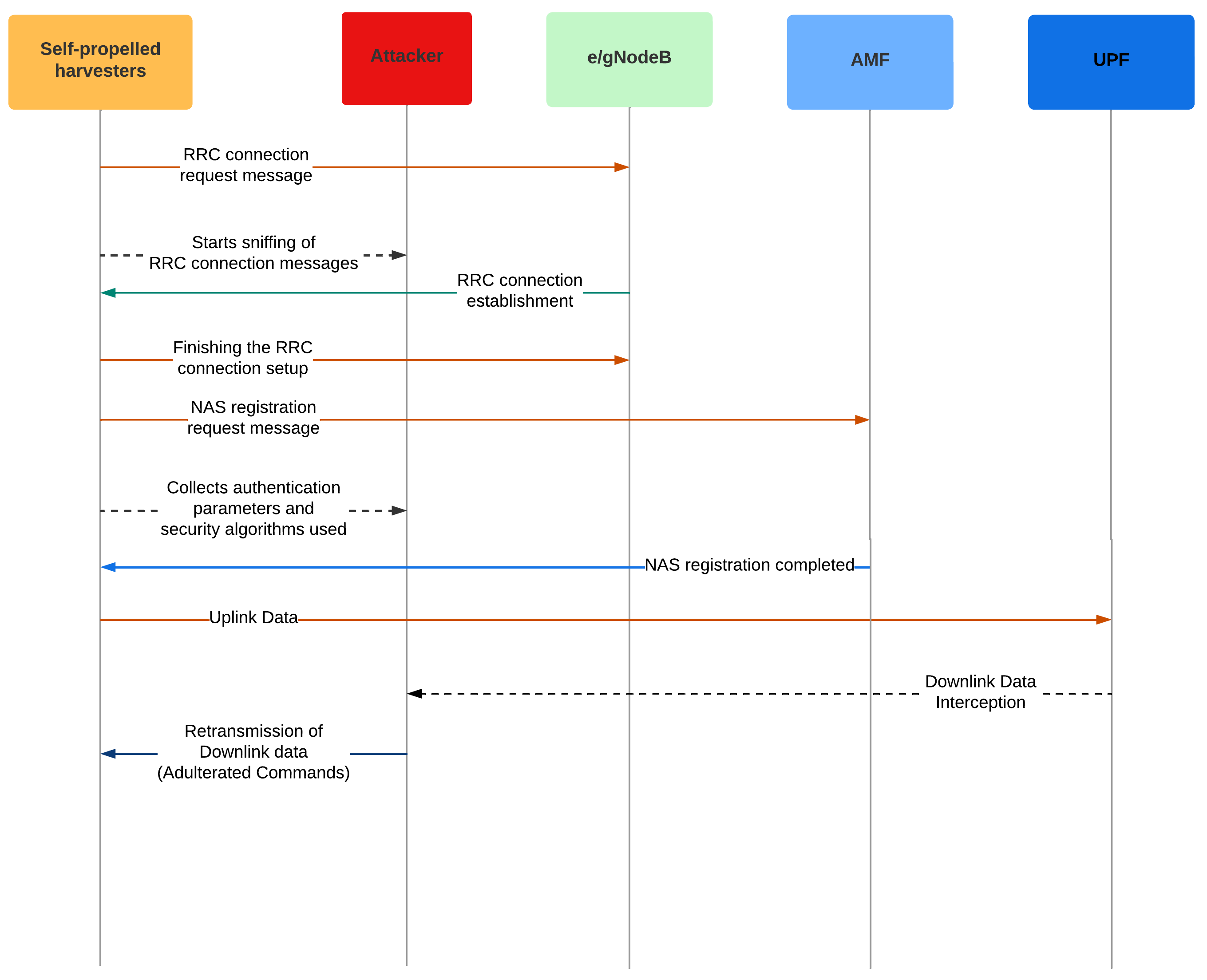
3.9. Security in Smart Agriculture
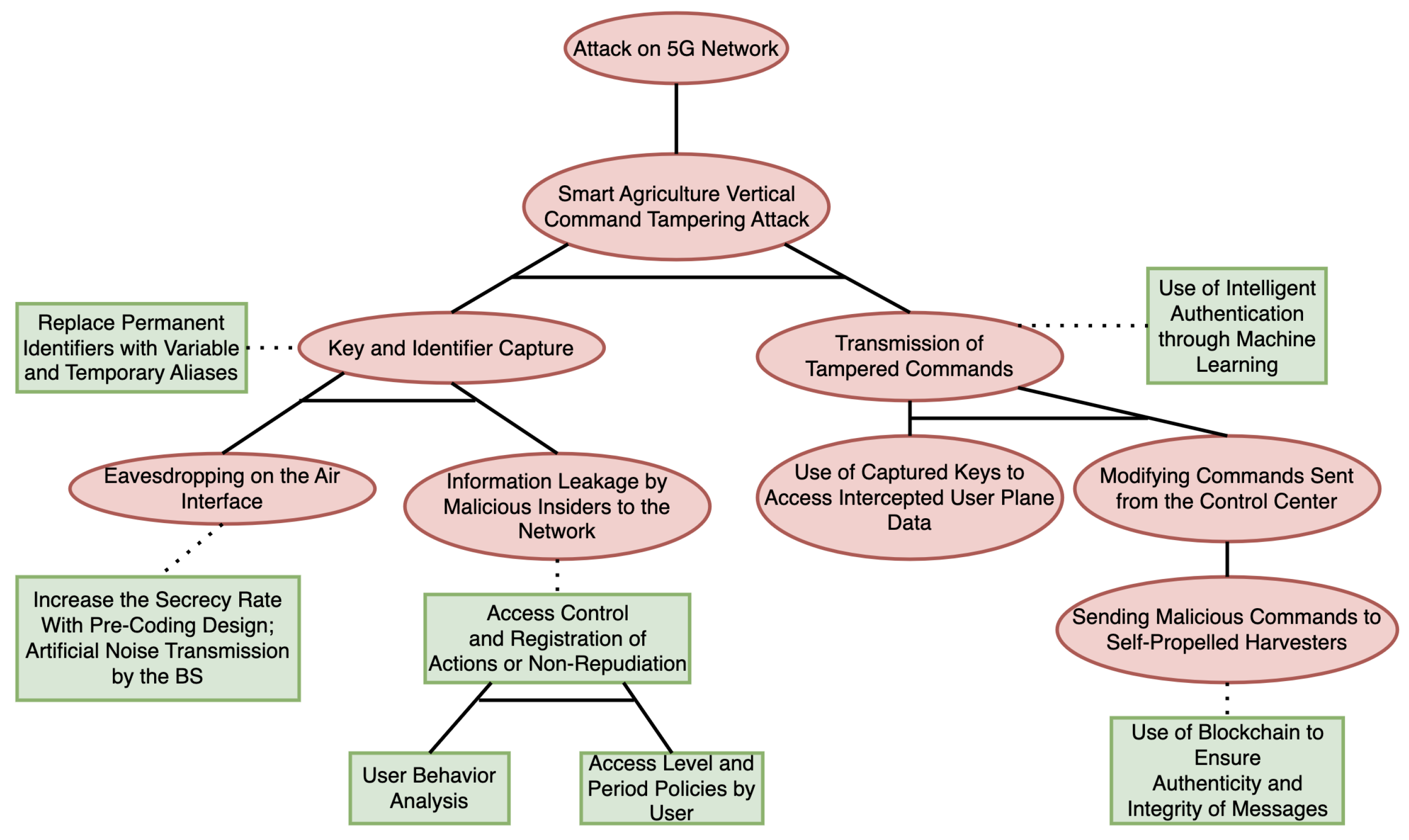
3.9.1. Example of a Smart Agriculture Attack Scenario
3.10. Security in Other Verticals
3.11. Attack-Defense Trees
3.11.1. Attack-Defense Tree for the Smart City Scenario
3.11.2. Attack-Defense Tree for the Smart Transportation Scenario
3.11.3. Attack-Defense Tree for the Public Service Scenario
3.11.4. Attack-Defense Tree for the Industry 4.0 Scenario
3.11.5. Attack-Defense Tree for the Smart Grid Scenario
3.11.6. Attack-Defense Tree for the Smart Health Scenario
3.11.7. Attack-Defense Tree for the Smart Agriculture Scenario
4. Other Concerns on the Privacy in Vertical Applications
4.1. Privacy in Vertical Applications Communications
4.1.1. Privacy of 5G Vehicular Networks
4.1.2. Privacy of 5G Drone Communications
4.2. Privacy in Network Slicing
4.3. Privacy of Application Data in MEC
5. Discussion and Future Research Directions
6. Conclusion
Acknowledgments
References
- Salahdine, F.; Han, T.; Zhang, N. Security in 5G and beyond recent advances and future challenges. Security and Privacy 2023, 6, e271. [Google Scholar] [CrossRef]
- Lin, C.C.; Tsai, C.T.; Liu, Y.L.; Chang, T.T.; Chang, Y.S. Security and Privacy in 5G-IIoT Smart Factories: Novel Approaches, Trends, and Challenges. Mobile Networks and Applications, 2023; 1–16. [Google Scholar]
- Fragkos, D.; Makropoulos, G.; Sarantos, P.; Koumaras, H.; Charismiadis, A.S.; Tsolkas, D. 5G Vertical Application Enablers Implementation Challenges and Perspectives. 2021 IEEE International Mediterranean Conference on Communications and Networking (MeditCom), 2021, pp. 117–122. [CrossRef]
- Khan, R.; Kumar, P.; Jayakody, D.N.K.; Liyanage, M. A Survey on Security and Privacy of 5G Technologies: Potential Solutions, Recent Advancements, and Future Directions. IEEE Communications Surveys & Tutorials 2020, 22, 196–248. [Google Scholar] [CrossRef]
- Wan, L.; Guo, Z.; Chen, X. Enabling efficient 5G NR and 4G LTE coexistence. IEEE Wireless Communications 2019, 26, 6–8. [Google Scholar] [CrossRef]
- NSA. Potential Threat Vectors to 5g Infrastructure. Technical report, Cybersecurity & Infrastructure Security Agency, National Security Agency, and Office of the Director of Nacional Intelligence, 2021.
- Sullivan, S.; Brighente, A.; Kumar, S.A.P.; Conti, M. 5G Security Challenges and Solutions: A Review by OSI Layers. IEEE Access 2021, 9, 116294–116314. [Google Scholar] [CrossRef]
- Tanveer, J.; Haider, A.; Ali, R.; Kim, A. Machine Learning for Physical Layer in 5G and beyond Wireless Networks: A Survey. Electronics 2022, 11. [Google Scholar] [CrossRef]
- Tang, Q.; Ermis, O.; Nguyen, C.D.; Oliveira, A.D.; Hirtzig, A. A Systematic Analysis of 5G Networks With a Focus on 5G Core Security. IEEE Access 2022, 10, 18298–18319. [Google Scholar] [CrossRef]
- Suomalainen, J.; Juhola, A.; Shahabuddin, S.; Mämmelä, A.; Ahmad, I. Machine Learning Threatens 5G Security. IEEE Access 2020, 8, 190822–190842. [Google Scholar] [CrossRef]
- Varga, P.; Peto, J.; Franko, A.; Balla, D.; Haja, D.; Janky, F.; Soos, G.; Ficzere, D.; Maliosz, M.; Toka, L. 5G support for Industrial IoT Applications— Challenges, Solutions, and Research gaps. Sensors 2020, 20. [Google Scholar] [CrossRef]
- Wijethilaka, S.; Liyanage, M. Survey on Network Slicing for Internet of Things Realization in 5G Networks. IEEE Communications Surveys & Tutorials 2021, 23, 957–994. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Shetty, S.; Gope, P.; Rodrigues, J.J.P.C. Security in 5G-Enabled Internet of Things Communication: Issues, Challenges, and Future Research Roadmap. IEEE Access 2021, 9, 4466–4489. [Google Scholar] [CrossRef]
- Sanchez-Gomez, J.; Carrillo, D.G.; Sanchez-Iborra, R.; Hernández-Ramos, J.L.; Granjal, J.; Marin-Perez, R.; Zamora-Izquierdo, M.A. Integrating LPWAN Technologies in the 5G Ecosystem: A Survey on Security Challenges and Solutions. IEEE Access 2020, 8, 216437–216460. [Google Scholar] [CrossRef]
- Sharma, P.; Jain, S.; Gupta, S.; Chamola, V. Role of machine learning and deep learning in securing 5G-driven industrial IoT applications. Ad Hoc Networks 2021, 123, 102685. [Google Scholar] [CrossRef]
- Zhang, J.; Yan, Z.; Fei, S.; Wang, M.; Li, T.; Wang, H. Is Today’s End-to-End Communication Security Enough for 5G and Its Beyond? IEEE Network 2022, 36, 105–112. [Google Scholar] [CrossRef]
- Liu, J.; Shu, L.; Lu, X.; Liu, Y. Survey of Intelligent Agricultural IoT Based on 5G. Electronics 2023, 12, 2336. [Google Scholar] [CrossRef]
- Ahad, A.; Tahir, M.; Aman Sheikh, M.; Ahmed, K.I.; Mughees, A.; Numani, A. Technologies trend towards 5G network for smart health-care using IoT: A review. Sensors 2020, 20, 4047. [Google Scholar] [CrossRef] [PubMed]
- Hui, H.; Ding, Y.; Shi, Q.; Li, F.; Song, Y.; Yan, J. 5G network-based Internet of Things for demand response in smart grid: A survey on application potential. Applied Energy 2020, 257, 113972. [Google Scholar] [CrossRef]
- Ogbodo, E.U.; Abu-Mahfouz, A.M.; Kurien, A.M. A survey on 5G and LPWAN-IoT for improved smart cities and remote area applications: From the aspect of architecture and security. Sensors 2022, 22, 6313. [Google Scholar] [CrossRef] [PubMed]
- Hakak, S.; Gadekallu, T.R.; Maddikunta, P.K.R.; Ramu, S.P.; Parimala, M.; De Alwis, C.; Liyanage, M. Autonomous Vehicles in 5G and beyond: A Survey. Vehicular Communications, 2022; 100551. [Google Scholar]
- Qiu, Q.; Liu, S.; Xu, S.; Yu, S. Study on security and privacy in 5g-enabled applications. Wireless Communications and Mobile Computing 2020, 2020, 1–15. [Google Scholar] [CrossRef]
- Valinevicius, A.; Zilys, M.; Kilius, S. Mobile Technologies Applications in Security Systems. 2007 29th International Conference on Information Technology Interfaces, 2007, pp. 657–662. [CrossRef]
- Pal, S.; Bandyopadhyay, M.; Chowdhury Kolay, S.; Chattopadhyay, S. Remote Air Quality Sensing and Temperature Monitoring System using GSM for Smart City Application. 2023 International Conference on Artificial Intelligence and Smart Communication (AISC), 2023, pp. 338–342. [CrossRef]
- Benbatouche, A.; Kadri, B. Design and realization of low-cost solenoid valve remotely controlled, application in irrigation network. Bulletin of Electrical Engineering and Informatics 2022. [Google Scholar] [CrossRef]
- Khan, M.A.; Jawed, S.F.; Khan, M.O.; Mazhar, O. An innovative approach towards E-health in development of tele auscultation system for heart using GSM mobile communication technology. 2013 IEEE 19th International Symposium for Design and Technology in Electronic Packaging (SIITME), 2013, pp. 201–204. [CrossRef]
- Baswa, M.; Karthik, R.; Natarajan, P.B.; Jyothi, K.; Annapurna, B. Patient health management system using e-health monitoring architecture. 2017 International Conference on Intelligent Sustainable Systems (ICISS), 2017, pp. 1120–1124. [CrossRef]
- Elgali, A.; Saad, A. An Industrial SC AD A System Remote Control Using Mobile Phones. 2022 IEEE 7th International Energy Conference (ENERGYCON), 2022, pp. 1–6. [CrossRef]
- Jarwal, M.K.; Barun, A.; Singh, A.; Srivastava, A. Mobile Application based Tracking using GPS and GSM. 2022 8th International Conference on Signal Processing and Communication (ICSC), 2022, pp. 153–156. [CrossRef]
- Phuoc Dai, N.H.; Ruiz, L.; Zoltán, R. Mobile Technology Security Concerns and NESAS as a Solution. 2022 IEEE 26th International Conference on Intelligent Engineering Systems (INES), 2022, pp. 000127–000130. [CrossRef]
- Clavier, C. An improved SCARE cryptanalysis against a secret A3/A8 GSM algorithm. Information Systems Security: Third International Conference, ICISS 2007, Delhi, India, December 16-20, 2007. Proceedings 3. Springer, 2007, pp. 143–155.
- Wamyil, M.; Mu’Azu, M. Gsm Networks: A Review Of Security Threats And Mitigation Measures. Information Manager (The) 2008, 6. [Google Scholar] [CrossRef]
- Toorani, M.; Beheshti, A. Solutions to the GSM Security Weaknesses. 2008 The Second International Conference on Next Generation Mobile Applications, Services, and Technologies. IEEE, 2008. [CrossRef]
- Qiu, R.; Zhu, W.; Zhang, Y.Q. Third-generation and beyond (3.5G) wireless networks and its applications. 2002 IEEE International Symposium on Circuits and Systems (ISCAS), 2002, Vol. 1, pp. I–I. [CrossRef]
- Zhang, Y.; Zhao, G.; Zhang, Y. A Smart Home Security System Based on 3G. 2009 International Forum on Computer Science-Technology and Applications, 2009, Vol. 2, pp. 291–294. [CrossRef]
- Sun, J.; Lin, D.; Zhao, P.; Zhang, Y. Based on Internet/2G/3G Converged Network Intelligent Image Monitoring System. 2010 International Forum on Information Technology and Applications, 2010, Vol. 2, pp. 277–279. [CrossRef]
- Xu, F.; Zhou, Q. The application of 3G technology in water resources monitoring system. 5th International Conference on Computer Sciences and Convergence Information Technology, 2010, pp. 977–980. [CrossRef]
- Kang, J.; Shin, I.H.; Koo, Y.; Jung, M.Y.; Suh, G.J.; Kim, H.C. HSDPA (3.5G)-Based Ubiquitous Integrated Biotelemetry System for Emergency Care. 2007 29th Annual International Conference of the IEEE Engineering in Medicine and Biology Society, 2007, pp. 3665–3668. [CrossRef]
- Yamamoto, H.; Fujii, T.; Ha, P.T.T.; Yamazaki, K. New development of remote control system for air vehicle using 3G cellular network. 16th International Conference on Advanced Communication Technology, 2014, pp. 456–461. [CrossRef]
- Ye, H.; Ding, G. A digital vehicle monitoring system based on 3G for public security. 2010 International Conference on Computer and Information Application, 2010, pp. 146–148. [CrossRef]
- Yundong, L.; Weigang, Z. Intelligent bridge monitoring system based on 3G. 2011 International Conference on Consumer Electronics, Communications and Networks (CECNet), 2011, pp. 426–429. [CrossRef]
- Jianqiang, K. ; Zhaochenxu.; Kanghaiping. Research and application of 3G electrical safety job site intelligent monitoring device. 2014 China International Conference on Electricity Distribution (CICED), 2014, pp. 745–747. [CrossRef]
- Yun, H.; hua, P.A.; zhi, Z.S. Intelligent video monitoring system based on 3G. 2010 International Conference on Educational and Network Technology, 2010, pp. 135–138. [CrossRef]
- Lundevall, M.; Olin, B.; Olsson, J.; Wiberg, N.; Wanstedt, S.; Eriksson, J.; Eng, F. Streaming applications over HSDPA in mixed service scenarios. IEEE 60th Vehicular Technology Conference, 2004. VTC2004-Fall. 2004, 2004, Vol. 2, pp. 841–845 Vol. 2. [Google Scholar] [CrossRef]
- Li, H.; Guo, S.; Zheng, K.; Chen, Z.; Zhang, Z.; Du, X. Security analysis and defense strategy on access domain in 3G. 2009 First International Conference on Information Science and Engineering, 2009, pp. 1851–1854. [CrossRef]
- Lian, Y.; Zhang, W.; Jiang, J. The architecture of the remote control system oriented to 4G networks. 2012 2nd International Conference on Consumer Electronics, Communications and Networks (CECNet), 2012, pp. 1386–1390. [CrossRef]
- Ting, C.; Yun, X.; Xiangmo, Z.; Tao, G.; Zhigang, X. 4G UAV communication system and hovering height optimization for public safety. 2017 IEEE 19th International Conference on e-Health Networking, Applications and Services (Healthcom), 2017, pp. 1–6. [CrossRef]
- Naveed, M.; Qazi, S.; Khawaja, B.A. UAV-based Life-Saving Solution For Police To Maintain Social-Distancing During Covid-19 Pandemic Using 4G-LTE Technology. 2021 International Conference on Communication Technologies (ComTech), 2021, pp. 28–32. [CrossRef]
- Lin, B.S.P.; Tsai, W.H.; Wu, C.; Hsu, P.; Huang, J.; Liu, T.H. The Design of Cloud-Based 4G/LTE for Mobile Augmented Reality with Smart Mobile Devices. 2013 IEEE Seventh International Symposium on Service-Oriented System Engineering, 2013, pp. 561–566. [CrossRef]
- Hiramatsu, K.; Nakao, S.; Hoshino, M.; Imamura, D. Technology evolutions in LTE/LTE-advanced and its applications. 2010 IEEE International Conference on Communication Systems, 2010, pp. 161–165. [CrossRef]
- Widjaja, D.; Damar Wisya Wicaksana, D. Performance Evaluation of Body Temperature Data Transmission Using Turbo Codes in 4G-LTE. 2020 2nd International Conference on Industrial Electrical and Electronics (ICIEE), 2020, pp. 179–182. [CrossRef]
- Gözde, H.; Taplamacıoğlu, M.C.; Arı, M.; Shalaf, H. 4G/LTE technology for smart grid communication infrastructure. 2015 3rd International Istanbul Smart Grid Congress and Fair (ICSG), 2015, pp. 1–4. [CrossRef]
- Cao, J.; Ma, M.; Li, H.; Zhang, Y.; Luo, Z. A Survey on Security Aspects for LTE and LTE-A Networks. IEEE Communications Surveys & Tutorials 2014, 16, 283–302. [Google Scholar] [CrossRef]
- Tahir, M.; Habaebi, M.H.; Dabbagh, M.; Mughees, A.; Ahad, A.; Ahmed, K.I. A Review on Application of Blockchain in 5G and Beyond Networks: Taxonomy, Field-Trials, Challenges and Opportunities. IEEE Access 2020, 8, 115876–115904. [Google Scholar] [CrossRef]
- Liyanage, M.; Salo, J.; Braeken, A.; Kumar, T.; Seneviratne, S.; Ylianttila, M. 5G Privacy: Scenarios and Solutions. 2018 IEEE 5G World Forum (5GWF), 2018, pp. 197–203. [CrossRef]
- Sharma, A.; Balasubramanian, V.; Jolfaei, A. Security Challenges and Solutions for 5G HetNet. 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), 2020, pp. 1318–1323. [CrossRef]
- Nieto, A.; Acien, A.; Lopez, J. Capture the RAT: Proximity-Based Attacks in 5G Using the Routine Activity Theory. 2018 IEEE 16th Intl Conf on Dependable, Autonomic and Secure Computing, 16th Intl Conf on Pervasive Intelligence and Computing, 4th Intl Conf on Big Data Intelligence and Computing and Cyber Science and Technology Congress(DASC/PiCom/DataCom/CyberSciTech), 2018, pp. 520–527. [CrossRef]
- Dutta, A.; Hammad, E. 5G Security Challenges and Opportunities: A System Approach. 2020 IEEE 3rd 5G World Forum (5GWF), 2020, pp. 109–114. [CrossRef]
- Dey, A.; Nandi, S.; Sarkar, M. Security Measures in IOT based 5G Networks. 2018 3rd International Conference on Inventive Computation Technologies (ICICT), 2018, pp. 561–566. [CrossRef]
- Lichtman, M.; Rao, R.; Marojevic, V.; Reed, J.; Jover, R.P. 5G NR Jamming, Spoofing, and Sniffing: Threat Assessment and Mitigation. 2018 IEEE International Conference on Communications Workshops (ICC Workshops), 2018, pp. 1–6. [CrossRef]
- Liyanage, M.; Abro, A.B.; Ylianttila, M.; Gurtov, A. Opportunities and Challenges of Software-Defined Mobile Networks in Network Security. IEEE Security & Privacy 2016, 14, 34–44. [Google Scholar] [CrossRef]
- Ksentini, A.; Frangoudis, P.A. Toward Slicing-Enabled Multi-Access Edge Computing in 5G. IEEE Network 2020, 34, 99–105. [Google Scholar] [CrossRef]
- Ghafoor, A.; Shah, M.A.; Mushtaq, M.; Iftikhar, M. 5G SECURITY THREATS AFFECTING DIGITAL ECONOMY AND THEIR COUNTERMEASURES. Competitive Advantage in the Digital Economy (CADE 2021), 2021, Vol. 2021, pp. 70–77. [CrossRef]
- Zhang, A.; Lin, X. Security-Aware and Privacy-Preserving D2D Communications in 5G. IEEE Network 2017, 31, 70–77. [Google Scholar] [CrossRef]
- Liyanage, M.; Ahmed, I.; Ylianttila, M.; Santos, J.L.; Kantola, R.; Perez, O.L.; Itzazelaia, M.U.; Montes De Oca, E.; Valtierra, A.; Jimenez, C. Security for Future Software Defined Mobile Networks. 2015 9th International Conference on Next Generation Mobile Applications, Services and Technologies, 2015, pp. 256–264. [CrossRef]
- Mazin, A.; Davaslioglu, K.; Gitlin, R.D. Secure key management for 5G physical layer security. 2017 IEEE 18th Wireless and Microwave Technology Conference (WAMICON), 2017, pp. 1–5. [CrossRef]
- Settembre, M. A 5G Core Network Challenge: Combining Flexibility and Security. 2021 AEIT International Annual Conference (AEIT), 2021, pp. 1–6. [CrossRef]
- Thantharate, A.; Paropkari, R.; Walunj, V.; Beard, C.; Kankariya, P. Secure5G: A Deep Learning Framework Towards a Secure Network Slicing in 5G and Beyond. 2020 10th Annual Computing and Communication Workshop and Conference (CCWC), 2020, pp. 0852–0857. [CrossRef]
- Barrachina, J.; Garrido, P.; Fogue, M.; Martinez, F.J.; Cano, J.C.; Calafate, C.T.; Manzoni, P. Road side unit deployment: A density-based approach. IEEE Intelligent Transportation Systems Magazine 2013, 5, 30–39. [Google Scholar] [CrossRef]
- Bajpai, A.; Balodi, A. Applications of 5G and Beyond in Smart Cities; CRC Press, 2023. [Google Scholar]
- Abdel-Malek, M.A.; Akkaya, K.; Bhuyan, A.; Ibrahim, A.S. A Proxy Signature-Based Drone Authentication in 5G D2D Networks. 2021 IEEE 93rd Vehicular Technology Conference (VTC2021-Spring), 2021, pp. 1–7. [CrossRef]
- Shin, D.; Yun, K.; Kim, J.; Astillo, P.V.; Kim, J.N.; You, I. A Security Protocol for Route Optimization in DMM-Based Smart Home IoT Networks. IEEE Access 2019, 7, 142531–142550. [Google Scholar] [CrossRef]
- Nowak, T.W.; Sepczuk, M.; Kotulski, Z.; Niewolski, W.; Artych, R.; Bocianiak, K.; Osko, T.; Wary, J.P. Verticals in 5G MEC-use cases and security challenges. IEEE Network 2021, 9, 87251–87298. [Google Scholar] [CrossRef]
- Swami, M.; Swami, S. The Role of 5G in Smart Transportation. In Applications of 5G and Beyond in Smart Cities; CRC Press, 2023; pp. 27–42. [Google Scholar]
- Eltahlawy, A.M.; Azer, M.A. Using Blockchain Technology for the Internet Of Vehicles. 2021 International Mobile, Intelligent, and Ubiquitous Computing Conference (MIUCC), 2021, pp. 54–61. [CrossRef]
- Falchetti, A.; Azurdia-Meza, C.; Cespedes, S. Vehicular cloud computing in the dawn of 5G. 2015 CHILEAN Conference on Electrical, Electronics Engineering, Information and Communication Technologies (CHILECON), 2015, pp. 301–305. [CrossRef]
- Moulahi, T.; Zidi, S.; Alabdulatif, A.; Atiquzzaman, M. Comparative Performance Evaluation of Intrusion Detection Based on Machine Learning in In-Vehicle Controller Area Network Bus. IEEE Access 2021, 9, 99595–99605. [Google Scholar] [CrossRef]
- Ayoub, T.; Mazri, T. Security Challenges in V2I Architectures and Proposed Solutions. 2018 IEEE 5th International Congress on Information Science and Technology (CiSt), 2018, pp. 594–599. [CrossRef]
- Lu, R.; Zhang, L.; Ni, J.; Fang, Y. 5G Vehicle-to-Everything Services: Gearing Up for Security and Privacy. Proceedings of the IEEE 2020, 108, 373–389. [Google Scholar] [CrossRef]
- Aljeri, N.; Boukerche, A. Mobility Management in 5G-Enabled Vehicular Networks: Models, Protocols, and Classification. ACM Comput. Surv. 2020, 53. [Google Scholar] [CrossRef]
- Huang, J.; Qian, Y.; Hu, R.Q. Secure and Efficient Privacy-Preserving Authentication Scheme for 5G Software Defined Vehicular Networks. IEEE Transactions on Vehicular Technology 2020, 69, 8542–8554. [Google Scholar] [CrossRef]
- Hasan, R.; Hasan, R. Towards a Threat Model and Privacy Analysis for V2P in 5G Networks. 2021 IEEE 4th 5G World Forum (5GWF), 2021, pp. 383–387. [CrossRef]
- Asensio, R.; Benzaid, C.; Alemany, P.; Ayed, D.; Christopoulou, M.; Dangerville, C.; Gür, G.; La, V.H.; Lefebvre, V. ; E. Montes de Oca, R.M.; Nguyen, H.; Nguyen, M.; Ortiz, J.; Pastor, A.; Porambage, P.; Santinelli, G.; W. Soussi, T.T.; Vilalta, R.; Zarca, A. Evolution of 5G Cyber Threats and Security Solutions. Technical report, INSPIRE-5Gplus, 2022.
- Suomalainen, J.; Julku, J.; Vehkaperä, M.; Posti, H. Securing public safety communications on commercial and tactical 5G networks: A survey and future research directions. IEEE Open Journal of the Communications Society 2021, 2, 1590–1615. [Google Scholar] [CrossRef]
- Suomalainen, J.; Julku, J.; Vehkaperä, M.; Posti, H. Securing Public Safety Communications on Commercial and Tactical 5G Networks: A Survey and Future Research Directions. IEEE Open Journal of the Communications Society 2021, 2, 1590–1615. [Google Scholar] [CrossRef]
- Elmasry, G.; Corwin, P. Hiding the RF Signal Signature in Tactical 5G. MILCOM 2021 - 2021 IEEE Military Communications Conference (MILCOM), 2021, pp. 733–738. [CrossRef]
- Makropoulos, G.; Fragkos, D.; Koumaras, H.; Alonistioti, N.; Kaloxylos, A.; Koumaras, V.; Dounia, T.; Sakkas, C.; Tsolkas, D. 5G Network Programmability Enabling Industry 4.0 Transformation. In Opportunities and Challenges of Industrial IoT in 5G and 6G Networks; IGI Global, 2023; pp. 119–137.
- Corici, A.A.; Corici, M.; Troudt, E.; Riemer, B.; Magedanz, T. Framework for Trustful Handover of M2M devices between Security Domains. 2020 23rd Conference on Innovation in Clouds, Internet and Networks and Workshops (ICIN), 2020, pp. 102–109. [CrossRef]
- Abdel-Basset, M.; Hawash, H.; Sallam, K. Federated threat-hunting approach for microservice-based industrial cyber-physical system. IEEE Transactions on Industrial Informatics 2021, 18, 1905–1917. [Google Scholar] [CrossRef]
- Abdel-Basset, M.; Hawash, H.; Sallam, K. Federated Threat-Hunting Approach for Microservice-Based Industrial Cyber-Physical System. IEEE Transactions on Industrial Informatics 2022, 18, 1905–1917. [Google Scholar] [CrossRef]
- Selvam, P.; Sridhar, J.; Ganesan, V.; Ravindraiah, R. The future of Industry 4.0: private 5G networks. In Advanced Signal Processing for Industry 4.0, Volume 1: Evolution, communication protocols, and applications in manufacturing systems; IOP Publishing: Bristol, UK, 2023; pp. 3–1. [Google Scholar]
- FORTINET. Securing 5G Private Mobile Networks. Technical report, FORTINET, 2021.
- Jamshidi, M.; Yahya, S.I.; Nouri, L.; Hashemi-Dezaki, H.; Rezaei, A.; Chaudhary, M.A. A High-Efficiency Diplexer for Sustainable 5G-Enabled IoT in Metaverse Transportation System and Smart Grids. Symmetry 2023, 15, 821. [Google Scholar] [CrossRef]
- Ranaweera, P.; Jurcut, A.; Liyanage, M. MEC-Enabled 5G Use Cases: A Survey on Security Vulnerabilities and Countermeasures. ACM Comput. Surv. 2021, 54. [Google Scholar] [CrossRef]
- Xuesong, H.; Wei, L.; Tao, Z.; Haidong, H.; Kangle, Y.; Pei, P. An Endogenous Security Protection Framework adapted to 5G MEC in Power Industry. 2021 China Automation Congress (CAC), 2021, pp. 5155–5159. [CrossRef]
- Devi, D.H.; Duraisamy, K.; Armghan, A.; Alsharari, M.; Aliqab, K.; Sorathiya, V.; Das, S.; Rashid, N. 5g technology in healthcare and wearable devices: A review. Sensors 2023, 23, 2519. [Google Scholar] [CrossRef]
- Menon, S.P.; Shukla, P.K.; Sethi, P.; Alasiry, A.; Marzougui, M.; Alouane, M.T.H.; Khan, A.A. An intelligent diabetic patient tracking system based on machine learning for E-health applications. Sensors 2023, 23, 3004. [Google Scholar] [CrossRef] [PubMed]
- Le, T.V.; Hsu, C.L. An Anonymous Key Distribution Scheme for Group Healthcare Services in 5G-Enabled Multi-Server Environments. IEEE Access 2021, 9, 53408–53422. [Google Scholar] [CrossRef]
- Fatima, R.; Manal, R.; Tomader, M. Cryptography in E-Health Using 5G Based IOT: A Comparison Study. Proceedings of the 4th International Conference on Big Data and Internet of Things; Association for Computing Machinery: New York, NY, USA, 2020. [Google Scholar] [CrossRef]
- Le, T.V.; Hsu, C.L. An anonymous key distribution scheme for group healthcare services in 5G-enabled multi-server environments. IEEE Access 2021, 9, 53408–53422. [Google Scholar] [CrossRef]
- Mangra, N.; Behmann, F.; Thakur, A.; Popescu, A.; Suciu Jr, G.; Giannattasio, G.; Uppal, R.; Montlouis, W. White Paper-5G Enabled Agriculture Ecosystem: Food Supply Chain, Rural Development, and Climate Resiliency. 5G Enabled Agriculture Ecosystem: Food Supply Chain, Rural Development, and Climate Resiliency 2023, 1–40. [Google Scholar]
- Nowak, T.W.; Sepczuk, M.; Kotulski, Z.; Niewolski, W.; Artych, R.; Bocianiak, K.; Osko, T.; Wary, J.P. Verticals in 5G MEC-Use Cases and Security Challenges. IEEE Access 2021, 9, 87251–87298. [Google Scholar] [CrossRef]
- Yu, L.; Enzheng, W. 5G network education and smart campus based on heterogeneous distributed platform and multi-scheduling optimization. Soft Computing 2023, 1–12. [Google Scholar]
- Akhunzada, A.; Islam, S.u.; Zeadally, S. Securing Cyberspace of Future Smart Cities with 5G Technologies. IEEE Network 2020, 34, 336–342. [Google Scholar] [CrossRef]
- Mamolar, A.S.; Pervez, Z.; Wang, Q.; Alcaraz-Calero, J.M. Towards the Detection of Mobile DDoS Attacks in 5G Multi-Tenant Networks. 2019 European Conference on Networks and Communications (EuCNC), 2019, pp. 273–277. [CrossRef]
- Nasir, A.A.; Tuan, H.D.; Nguyen, H.H.; Nguyen, N.M. Physical Layer Security by Exploiting Interference and Heterogeneous Signaling. IEEE Wireless Communications 2019, 26, 26–31. [Google Scholar] [CrossRef]
- Bhuyan, A.; Guvenç, I.; Dai, H.; Sichitiu, M.L.; Singh, S.; Rahmati, A.; Maeng, S.J. Secure 5G Network for a Nationwide Drone Corridor. 2021 IEEE Aerospace Conference (50100), 2021, pp. 1–10. [CrossRef]
- Gokul, N.; Sankaran, S. Modeling and Defending against Resource Depletion Attacks in 5G Networks. 2021 IEEE 18th India Council International Conference (INDICON), 2021, pp. 1–7. [CrossRef]
- Lin, M.; Huang, Q.; de Cola, T.; Wang, J.B.; Wang, J.; Guizani, M.; Wang, J.Y. Integrated 5G-Satellite Networks: A Perspective on Physical Layer Reliability and Security. IEEE Wireless Communications 2020, 27, 152–159. [Google Scholar] [CrossRef]
- Yerrapragada, A.K.; Ormond, P.; Kelley, B. On the Application of Key-Based Physical Layer Security in 5G Heterogeneous Networks. MILCOM 2019 - 2019 IEEE Military Communications Conference (MILCOM), 2019, pp. 1–6. [CrossRef]
- Li, A. Enhancing the Physical Layer Security of Cooperative NOMA System. 2019 IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), 2019, pp. 2194–2198. [CrossRef]
- Roth, S.; Tomasin, S.; Maso, M.; Sezgin, A. Localization Attack by Precoder Feedback Overhearing in 5G Networks and Countermeasures. IEEE Transactions on Wireless Communications 2021, 20, 4100–4112. [Google Scholar] [CrossRef]
- van den Broek, F.; Verdult, R.; de Ruiter, J. Defeating IMSI Catchers. Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security; Association for Computing Machinery: New York, NY, USA, 2015; CCS ’15, p. 340–351. [CrossRef]
- Schinianakis, D.; Trapero, R.; Michalopoulos, D.S.; Crespo, B.G.N. Security Considerations in 5G Networks: A Slice-Aware Trust Zone Approach. 2019 IEEE Wireless Communications and Networking Conference (WCNC), 2019, pp. 1–8. [CrossRef]
- Fang, H.; Wang, X.; Tomasin, S. Machine Learning for Intelligent Authentication in 5G and Beyond Wireless Networks. IEEE Wireless Communications 2019, 26, 55–61. [Google Scholar] [CrossRef]
- Moreira, C.M.; Kaddoum, G.; Bou-Harb, E. Cross-Layer Authentication Protocol Design for Ultra-Dense 5G HetNets. 2018 IEEE International Conference on Communications (ICC), 2018, pp. 1–7. [CrossRef]
- Moudoud, H.; Khoukhi, L.; Cherkaoui, S. Prediction and Detection of FDIA and DDoS Attacks in 5G Enabled IoT. IEEE Network 2021, 35, 194–201. [Google Scholar] [CrossRef]
- Ali, A.; Ware, A. Anomaly Based IDS Via Customised CUSUM Algorithm for Industrial Communication Systems. 2021 3rd IEEE Middle East and North Africa COMMunications Conference (MENACOMM), 2021, pp. 31–36. [CrossRef]
- Feng, C.; Yu, K.; Bashir, A.K.; Al-Otaibi, Y.D.; Lu, Y.; Chen, S.; Zhang, D. Efficient and Secure Data Sharing for 5G Flying Drones: A Blockchain-Enabled Approach. IEEE Network 2021, 35, 130–137. [Google Scholar] [CrossRef]
- Li, M.; Zhu, L.; Zhang, Z.; Lal, C.; Conti, M.; Martinelli, F. Privacy for 5G-Supported Vehicular Networks. IEEE Open Journal of the Communications Society 2021, 2, 1935–1956. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, J.; Zheng, D.; Li, P.; Tian, Y. Privacy-preserving communication and power injection over vehicle networks and 5G smart grid slice. Journal of Network and Computer Applications 2018, 122, 50–60. [Google Scholar] [CrossRef]
- CISA.; NSA.; of the Director of National Intelligence, O. Potential Threat Vectors to 5G Infrastructure. Technical report, Department of Computer Science, Michigan State University, 2021.
- Abdalla, A.S.; Shang, B.; Marojevic, V.; Liu, L. Performance Evaluation of Aerial Relaying Systems for Improving Secrecy in Cellular Networks. 2020 IEEE 92nd Vehicular Technology Conference (VTC2020-Fall), 2020, pp. 1–5. [CrossRef]
- Chen, B.; Zhu, C.; Li, W.; Wei, J.; Leung, V.C.M.; Yang, L.T. Original Symbol Phase Rotated Secure Transmission Against Powerful Massive MIMO Eavesdropper. IEEE Access 2016, 4, 3016–3025. [Google Scholar] [CrossRef]
- Benzid, D.; Kadoch, M.; Cheriet, M. Raptor Code based on punctured LDPC for Secrecy in Massive MiMo. 2019 15th International Wireless Communications & Mobile Computing Conference (IWCMC), 2019, pp. 1884–1889. [CrossRef]
- Lin, C.H.; Wu, C.C.; Chen, K.F.; Lee, T.S. A Variational Autoencoder-Based Secure Transceiver Design Using Deep Learning. GLOBECOM 2020 - 2020 IEEE Global Communications Conference, 2020, pp. 1–7. [CrossRef]
- Barik, D.; Sanyal, J.; Samanta, T. Prevention of Denial-of-Service Attacks in 5GD2D Wireless Communication Networks Employing Double Auction Game Based Resource Trading. 2020 IEEE 3rd 5G World Forum (5GWF), 2020, pp. 239–244. [CrossRef]
- Fang, L.; Zhao, B.; Li, Y.; Liu, Z.; Ge, C.; Meng, W. Countermeasure Based on Smart Contracts and AI against DoS/DDoS Attack in 5G Circumstances. IEEE Network 2020, 34, 54–61. [Google Scholar] [CrossRef]
- Tan, Z.; Ding, B.; Zhang, Z.; Li, Q.; Guo, Y.; Lu, S. Device-Centric Detection and Mitigation of Diameter Signaling Attacks against Mobile Core. 2021 IEEE Conference on Communications and Network Security (CNS), 2021, pp. 29–37. [CrossRef]
- Vidal, J.M.; Monge, M.A.S.; Villalba, L.J.G. Detecting Workload-Based and Instantiation-Based Economic Denial of Sustainability on 5G Environments. Proceedings of the 13th International Conference on Availability, Reliability and Security; Association for Computing Machinery: New York, NY, USA, 2018; ARES 2018. [Google Scholar] [CrossRef]
- Cabaj, K.; Gregorczyk, M.; Mazurczyk, W.; Nowakowski, P.; Żórawski, P. SDN-Based Mitigation of Scanning Attacks for the 5G Internet of Radio Light System. Proceedings of the 13th International Conference on Availability, Reliability and Security; Association for Computing Machinery: New York, NY, USA, 2018; ARES 2018. [Google Scholar] [CrossRef]
- Norrman, K.; Näslund, M.; Dubrova, E. Protecting IMSI and User Privacy in 5G Networks. Proceedings of the 9th EAI International Conference on Mobile Multimedia Communications; ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering): Brussels, BEL, 2016; MobiMedia ’16, p. 159–166. [Google Scholar]
- Chopra, G.; Jha, R.K.; Jain, S. TPA: Prediction of Spoofing Attack Using Thermal Pattern Analysis in Ultra Dense Network for High Speed Handover Scenario. IEEE Access 2018, 6, 66268–66284. [Google Scholar] [CrossRef]
- Li, W.; Wang, N.; Jiao, L.; Zeng, K. Physical Layer Spoofing Attack Detection in MmWave Massive MIMO 5G Networks. IEEE Access 2021, 9, 60419–60432. [Google Scholar] [CrossRef]
- Wang, N.; Jiao, L.; Wang, P.; Li, W.; Zeng, K. Exploiting Beam Features for Spoofing Attack Detection in mmWave 60-GHz IEEE 802.11ad Networks. IEEE Transactions on Wireless Communications 2021, 20, 3321–3335. [Google Scholar] [CrossRef]
- Dang, Y.; Benzaïd, C.; Shen, Y.; Taleb, T. GPS Spoofing Detector with Adaptive Trustable Residence Area for Cellular based-UAVs. GLOBECOM 2020 - 2020 IEEE Global Communications Conference, 2020, pp. 1–6. [CrossRef]
- Pérez, M.G.; Celdrán, A.H.; Ippoliti, F.; Giardina, P.G.; Bernini, G.; Alaez, R.M.; Chirivella-Perez, E.; Clemente, F.J.G.; Pérez, G.M.; Kraja, E.; Carrozzo, G.; Calero, J.M.A.; Wang, Q. Dynamic Reconfiguration in 5G Mobile Networks to Proactively Detect and Mitigate Botnets. IEEE Internet Computing 2017, 21, 28–36. [Google Scholar] [CrossRef]
- Jagannath, A.; Jagannath, J.; Drozd, A. High Rate-Reliability Beamformer Design for 2×2 Mimo-OFDM System Under Hostile Jamming. 2020 29th International Conference on Computer Communications and Networks (ICCCN), 2020, pp. 1–9. [CrossRef]
- Hachimi, M.; Kaddoum, G.; Gagnon, G.; Illy, P. Multi-stage Jamming Attacks Detection using Deep Learning Combined with Kernelized Support Vector Machine in 5G Cloud Radio Access Networks. 2020 International Symposium on Networks, Computers and Communications (ISNCC), 2020, pp. 1–5. [CrossRef]
- Arjoune, Y.; Salahdine, F.; Islam, M.S.; Ghribi, E.; Kaabouch, N. A Novel Jamming Attacks Detection Approach Based on Machine Learning for Wireless Communication. 2020 International Conference on Information Networking (ICOIN), 2020, pp. 459–464. [CrossRef]
- Wang, N.; Jiao, L.; Alipour-Fanid, A.; Dabaghchian, M.; Zeng, K. Pilot Contamination Attack Detection for NOMA in 5G mm-Wave Massive MIMO Networks. IEEE Transactions on Information Forensics and Security 2020, 15, 1363–1378. [Google Scholar] [CrossRef]
- Wang, N.; Li, W.; Alipour-Fanid, A.; Jiao, L.; Dabaghchian, M.; Zeng, K. Pilot Contamination Attack Detection for 5G MmWave Grant-Free IoT Networks. IEEE Transactions on Information Forensics and Security 2021, 16, 658–670. [Google Scholar] [CrossRef]
- Adat, V.; Politis, I.; Tselios, C.; Kotsopoulos, S. Blockchain Enhanced SECRET Small Cells for the 5G Environment. 2019 IEEE 24th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), 2019, pp. 1–6. [CrossRef]
- Adat Vasudevan, V.; Tselios, C.; Politis, I. On Security Against Pollution Attacks in Network Coding Enabled 5G Networks. IEEE Access 2020, 8, 38416–38437. [Google Scholar] [CrossRef]
- Vasudevan, V.A.; Akhtar, T.; Tselios, C.; Politis, I.; Kotsopoulos, S. Study of Secure Network Coding Enabled Mobile Small Cells. ICC 2021 - IEEE International Conference on Communications, 2021, pp. 1–5. [CrossRef]
- Hakiri, A.; Dezfouli, B. Towards a Blockchain-SDN Architecture for Secure and Trustworthy 5G Massive IoT Networks. Proceedings of the 2021 ACM International Workshop on Software Defined Networks & Network Function Virtualization Security; Association for Computing Machinery: New York, NY, USA, 2021; SDN-NFV Sec’21, p. 11–18. [Google Scholar] [CrossRef]
- Sattar, D.; Matrawy, A. Towards Secure Slicing: Using Slice Isolation to Mitigate DDoS Attacks on 5G Core Network Slices. 2019 IEEE Conference on Communications and Network Security (CNS), 2019, pp. 82–90. [CrossRef]
- Li, H.; Wang, L. Online orchestration of cooperative defense against DDoS attacks for 5G MEC. 2018 IEEE Wireless Communications and Networking Conference (WCNC), 2018, pp. 1–6. [CrossRef]
- Ettiane, R.; Chaoub, A.; Elkouch, R. Robust detection of signaling DDoS threats for more secure machine type communications in next generation mobile networks. 2018 19th IEEE Mediterranean Electrotechnical Conference (MELECON), 2018, pp. 62–67. [CrossRef]
- Tan, X.; Li, H.; Wang, L.; Xu, Z. Global Orchestration of Cooperative Defense against DDoS Attacks for MEC. 2019 IEEE Wireless Communications and Networking Conference (WCNC), 2019, pp. 1–6. [CrossRef]
- Huang, H.; Hu, L.; Chu, J.; Cheng, X. An Authentication Scheme to Defend Against UDP DrDoS Attacks in 5G Networks. IEEE Access 2019, 7, 175970–175979. [Google Scholar] [CrossRef]
- Chen, X.; Feng, W.; Ma, Y.; Ge, N.; Wang, X. Preventing DRDoS Attacks in 5G Networks: a New Source IP Address Validation Approach. GLOBECOM 2020 - 2020 IEEE Global Communications Conference, 2020, pp. 1–6. [CrossRef]
- Torroglosa-Garcia, E.M.; Calero, J.M.A.; Bernabe, J.B.; Skarmeta, A. Enabling Roaming Across Heterogeneous IoT Wireless Networks: LoRaWAN MEETS 5G. IEEE Access 2020, 8, 103164–103180. [Google Scholar] [CrossRef]
- Corici, A.A.; Shashi, Y.; Corici, M.; Shrestha, R.; Guzman, D. Enabling Dynamic IoT Security Domains: Cellular Core Network and Device Management Meet Authentication Framework. 2019 Global IoT Summit (GIoTS), 2019, pp. 1–6. [CrossRef]
- Ni, J.; Lin, X.; Shen, X.S. Efficient and Secure Service-Oriented Authentication Supporting Network Slicing for 5G-Enabled IoT. IEEE Journal on Selected Areas in Communications 2018, 36, 644–657. [Google Scholar] [CrossRef]
- Sharma, S.; Satapathy, S.; Singh, S.; Sahu, A.K.; Obaidat, M.S.; Saxena, S.; Puthal, D. Secure Authentication Protocol for 5G Enabled IoT Network. 2018 Fifth International Conference on Parallel, Distributed and Grid Computing (PDGC), 2018, pp. 621–626. [CrossRef]
- Ali, A.; Lin, Y.D.; Li, C.Y.; Lai, Y.C. Transparent 3rd-Party Authentication with Application Mobility for 5G Mobile Edge Computing. 2020 European Conference on Networks and Communications (EuCNC), 2020, pp. 219–224. [CrossRef]
- Sutrala, A.K.; Obaidat, M.S.; Saha, S.; Das, A.K.; Alazab, M.; Park, Y. Authenticated Key Agreement Scheme With User Anonymity and Untraceability for 5G-Enabled Softwarized Industrial Cyber-Physical Systems. IEEE Transactions on Intelligent Transportation Systems 2022, 23, 2316–2330. [Google Scholar] [CrossRef]
- Ouaissa, M.; Ouaissa, M. An Improved Privacy Authentication Protocol for 5G Mobile Networks. 2020 International Conference on Advances in Computing, Communication & Materials (ICACCM), 2020, pp. 136–143. [CrossRef]
- Abdel-Malek, M.A.; Akkaya, K.; Bhuyan, A.; Cebe, M.; Ibrahim, A.S. Enabling Second Factor Authentication for Drones in 5G using Network Slicing. 2020 IEEE Globecom Workshops (GC Wkshps, 2020, pp. 1–6. [CrossRef]
- Matos, B.; Dzogovic, B.; Feng, B.; Do, V.T.; Jacot, N.; Van Do, T. Towards Achieving a Secure Authentication Mechanism for IoT Devices in 5G Networks. 2019 6th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/ 2019 5th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom), 2019, pp. 130–135. [CrossRef]
- Han, B.; Wong, S.; Mannweiler, C.; Dohler, M.; Schotten, H.D. Security Trust Zone in 5G networks. 2017 24th International Conference on Telecommunications (ICT), 2017, pp. 1–5. [CrossRef]
- Blanc, G.; Kheir, N.; Ayed, D.; Lefebvre, V.; de Oca, E.M.; Bisson, P. Towards a 5G Security Architecture: Articulating Software-Defined Security and Security as a Service. Proceedings of the 13th International Conference on Availability, Reliability and Security; Association for Computing Machinery: New York, NY, USA, 2018; ARES 2018. [Google Scholar] [CrossRef]
- Fernández Maimó, L.; Perales Gómez, L.; García Clemente, F.J.; Gil Pérez, M.; Martínez Pérez, G. A Self-Adaptive Deep Learning-Based System for Anomaly Detection in 5G Networks. IEEE Access 2018, 6, 7700–7712. [Google Scholar] [CrossRef]
- Vijay, A.; Umadevi, K. Secured AI guided Architecture for D2D Systems of Massive MIMO deployed in 5G Networks. 2019 3rd International Conference on Trends in Electronics and Informatics (ICOEI), 2019, pp. 468–472. [CrossRef]
- Siddiqui, M.; Escalona, E.; Trouva, E.; Kourtis, M.; Kritharidis, D.; Katsaros, K.; Spirou, S.; Canales, C.; Lorenzo, M. Policy based virtualised security architecture for SDN/NFV enabled 5G access networks. 2016 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), 2016, pp. 44–49. [CrossRef]
- Mantas, E.; Papadopoulos, D.; Fernández, C.; Ortiz, N.; Compastié, M.; Martínez, A.L.; Pérez, M.G.; Kourtis, A.; Xylouris, G.; Mlakar, I.; Tsarsitalidis, S.; Klonidis, D.; Pedone, I.; Canavese, D.; Pérez, G.M.; Sanvito, D.; Logothetis, V.; Lopez, D.; Pastor, A.; Lioy, A.; Jacquin, L.; Bifulco, R.; Kapodistria, A.; Priovolos, A.; Gardikis, G.; Neokosmidis, I.; Rokkas, T.; Papadakis, N.; Paraschos, D.; Jeran, P.; Litke, A.; Athanasiou, G. Practical Autonomous Cyberhealth for resilient Micro, Small and Medium-sized Enterprises. 2021 IEEE International Mediterranean Conference on Communications and Networking (MeditCom), 2021, pp. 500–505. [CrossRef]
- Schmittner, M.; Asadi, A.; Hollick, M. SEMUD: Secure multi-hop device-to-device communication for 5G public safety networks. 2017 IFIP Networking Conference (IFIP Networking) and Workshops, 2017, pp. 1–9. [CrossRef]
- Meshram, C.; Imoize, A.L.; Elhassouny, A.; Aljaedi, A.; Alharbi, A.R.; Jamal, S.S. IBOOST: A Lightweight Provably Secure Identity-Based Online/Offline Signature Technique Based on FCM for Massive Devices in 5G Wireless Sensor Networks. IEEE Access 2021, 9, 131336–131347. [Google Scholar] [CrossRef]
- Shi, D.; Zhang, X.; Vladimirescu, A.; Shi, L.; Huang, Y.; Liu, Y. A Device Identification Method Based on LED Fingerprint for Visible Light Communication System. Proceedings of the 15th International Conference on Availability, Reliability and Security; Association for Computing Machinery: New York, NY, USA, 2020. [Google Scholar] [CrossRef]
- Abdulqadder, I.H.; Zhou, S.; Zou, D.; Aziz, I.T.; Akber, S.M.A. Bloc-Sec: Blockchain-Based Lightweight Security Architecture for 5G/B5G Enabled SDN/NFV Cloud of IoT. 2020 IEEE 20th International Conference on Communication Technology (ICCT), 2020, pp. 499–507. [CrossRef]
- Yao, Y.; Chang, X.; Mišić, J.; Mišić, V.B. Lightweight Batch AKA Scheme for User-Centric Ultra-Dense Networks. IEEE Transactions on Cognitive Communications and Networking 2020, 6, 597–606. [Google Scholar] [CrossRef]
- Chaikalis, C.; Kosmanos, D.; Samaras, N.S. Utilizing turbo codes for secure 5G V2X. 2020 IEEE Microwave Theory and Techniques in Wireless Communications (MTTW), 2020, Vol. 1, pp. 30–34. [CrossRef]
- Ali, B.; Gregory, M.A.; Li, S. Uplifting Healthcare Cyber Resilience with a Multi-access Edge Computing Zero-Trust Security Model. 2021 31st International Telecommunication Networks and Applications Conference (ITNAC), 2021, pp. 192–197. [CrossRef]
- Angelogianni, A.; Politis, I.; Mohammadi, F.; Xenakis, C. On Identifying Threats and Quantifying Cybersecurity Risks of Mnos Deploying Heterogeneous Rats. IEEE Access 2020, 8, 224677–224701. [Google Scholar] [CrossRef]
- Ortiz, J.; Sanchez-Iborra, R.; Bernabe, J.B.; Skarmeta, A.; Benzaid, C.; Taleb, T.; Alemany, P.; Muñoz, R.; Vilalta, R.; Gaber, C.; Wary, J.P.; Ayed, D.; Bisson, P.; Christopoulou, M.; Xilouris, G.; de Oca, E.M.; Gür, G.; Santinelli, G.; Lefebvre, V.; Pastor, A.; Lopez, D. INSPIRE-5Gplus: Intelligent Security and Pervasive Trust for 5G and beyond Networks. Proceedings of the 15th International Conference on Availability, Reliability and Security; Association for Computing Machinery: New York, NY, USA, 2020; ARES ’20. [Google Scholar] [CrossRef]
- Ricart-Sanchez, R.; Malagon, P.; Alcaraz-Calero, J.M.; Wang, Q. NetFPGA-Based Firewall Solution for 5G Multi-Tenant Architectures. 2019 IEEE International Conference on Edge Computing (EDGE), 2019, pp. 132–136. [CrossRef]
- Cunha, V.A.; Maroulis, N.; Papagianni, C.; Sacido, J.; Jiménez, M.; Ubaldi, F.; Gharbaoui, M.; Chang, C.Y.; Koursioumpas, N.; Tomakh, K.; Corujo, D.; Barraca, J.P.; Barmpounakis, S.; Kucherenko, D.; Giorgetti, A.; Boddi, A.; Valcarenghi, L.; Kolodiazhnyi, O.; Zabala, A.; Salvat, J.X.; Garcia-Saavedra, A. 5 Growth: Secure and Reliable Network Slicing for Verticals. 2021 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), 2021, pp. 347–352. [CrossRef]
- Erel-Özçevik, M.; Tekçe, F. SDN/NFV based Secure SCMA design in SDR. 2021 17th International Conference on Network and Service Management (CNSM), 2021, pp. 319–325. [CrossRef]
- Pustišek, M.; Turk, J.; Kos, A. Secure Modular Smart Contract Platform for Multi-Tenant 5G Applications. IEEE Access 2020, 8, 150626–150646. [Google Scholar] [CrossRef]
- Tang, B.h.; Zhou, Z.x. High-Speed Mobile Communication Network and Wireless Sensor Network Convergence Service Traffic Prediction Model and Security Mechanism Design. Proceedings of the 2020 9th International Conference on Computing and Pattern Recognition; Association for Computing Machinery: New York, NY, USA, 2021. [Google Scholar] [CrossRef]
- Suraci, C.; Pizzi, S.; Molinaro, A.; Iera, A.; Araniti, G. An RSA-based Algorithm for Secure D2D-aided Multicast Delivery of Multimedia Services. 2020 IEEE International Symposium on Broadband Multimedia Systems and Broadcasting (BMSB), 2020, pp. 1–6. [CrossRef]
- Papadopoulos, S.; Drosou, A.; Kalamaras, I.; Tzovaras, D. Behavioural Network Traffic Analytics for Securing 5G Networks. 2018 IEEE International Conference on Communications Workshops (ICC Workshops), 2018, pp. 1–6. [CrossRef]
- Chen, K.; Wang, Y.; Yu, P.; Li, N. Security-Oriented Network Slice Backup Method. 2021 22nd Asia-Pacific Network Operations and Management Symposium (APNOMS), 2021, pp. 330–335. [CrossRef]
- Lou, D.; Kuang, R.; He, A. Entropy Transformation and Expansion with Quantum Permutation Pad for 5G Secure Networks. 2021 IEEE 21st International Conference on Communication Technology (ICCT), 2021, pp. 840–845. [CrossRef]
- Ma, N.; Zhong, X.; Liu, P.; Zhou, S. A SDN/NFV-based Core Network Slicing for Secure Mobile Communication. 2020 IEEE 91st Vehicular Technology Conference (VTC2020-Spring), 2020, pp. 1–5. [CrossRef]
- Priovolos, A.; Lioprasitis, D.; Gardikis, G.; Costicoglou, S. Using Anomaly Detection Techniques for Securing 5G Infrastructure and Applications. 2021 IEEE International Mediterranean Conference on Communications and Networking (MeditCom), 2021, pp. 519–524. [CrossRef]
- Nediyanchath, A.; Singh, C.; Singh, H.J.; Mangla, H.; Mangla, K.; Sakhala, M.K.; Balasubramanian, S.; Pareek, S. ; Shwetha. Anomaly Detection in Mobile Networks. 2020 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), 2020, pp. 1–5. [CrossRef]
- Ketzaki, E.; Drosou, A.; Papadopoulos, S.; Tzovaras, D. A light-weighted ANN architecture for the classification of cyber-threats in modern communication networks. 2019 10th International Conference on Networks of the Future (NoF), 2019, pp. 17–24. [CrossRef]
- Xu, S.; Fang, D.; Sharif, H. Efficient Network Anomaly Detection for Edge Gateway Defense in 5G. 2019 IEEE Globecom Workshops (GC Wkshps), 2019, pp. 1–5. [CrossRef]
- Martini, B.; Mori, P.; Marino, F.; Saracino, A.; Lunardelli, A.; Marra, A.L.; Martinelli, F.; Castoldi, P. Pushing Forward Security in Network Slicing by Leveraging Continuous Usage Control. IEEE Communications Magazine 2020, 58, 65–71. [Google Scholar] [CrossRef]
- Gonzalez, A.J.; Ordonez-Lucena, J.; Helvik, B.E.; Nencioni, G.; Xie, M.; Lopez, D.R.; Grønsund, P. The Isolation Concept in the 5G Network Slicing. 2020 European Conference on Networks and Communications (EuCNC), 2020, pp. 12–16. [CrossRef]
- Bordel, B.; Orúe, A.B.; Alcarria, R.; Sánchez-De-Rivera, D. An Intra-Slice Security Solution for Emerging 5G Networks Based on Pseudo-Random Number Generators. IEEE Access 2018, 6, 16149–16164. [Google Scholar] [CrossRef]
- Wang, M.; Yan, Z. Security in D2D Communications: A Review. 2015 IEEE Trustcom/BigDataSE/ISPA, 2015, Vol. 1, pp. 1199–1204. [CrossRef]
- Abd-Elrahman, E.; Ibn-khedher, H.; Afifi, H.; Toukabri, T. Fast group discovery and non-repudiation in D2D communications using IBE. 2015 International Wireless Communications and Mobile Computing Conference (IWCMC), 2015, pp. 616–621. [CrossRef]
- Abd-Elrahman, E.; Ibn-khedher, H.; Afifi, H. D2D group communications security. 2015 International Conference on Protocol Engineering (ICPE) and International Conference on New Technologies of Distributed Systems (NTDS), 2015, pp. 1–6. [CrossRef]
- Sedidi, R.; Kumar, A. Key exchange protocols for secure Device-to-Device (D2D) communication in 5G. 2016 Wireless Days (WD), 2016, pp. 1–6. [CrossRef]
- Saxena, N.; Kumbhar, F.H.; Roy, A. Exploiting Social Relationships for Trustworthy D2D Relay in 5G Cellular Networks. IEEE Communications Magazine 2020, 58, 48–53. [Google Scholar] [CrossRef]
- Luntovskyy, A.; Zobjack, T.; Shubyn, B.; Klymash, M. Energy Efficiency and Security for IoT Scenarios via WSN, RFID and NFC : Invited Paper. 2021 IEEE International Conference on Information and Telecommunication Technologies and Radio Electronics (UkrMiCo), 2021, pp. 1–6. [CrossRef]
- Vera-Rivera, A.; Refaey, A.; Hossain, E. Task Sharing and Scheduling for Edge Computing Servers Using Hyperledger Fabric Blockchain. 2021 IEEE Globecom Workshops (GC Wkshps), 2021, pp. 1–6. [CrossRef]
- Shukla, A.; Gupta, R.; Tanwar, S.; Kumar, N.; Rodrigues, J.J.P.C. Block-RAS: A P2P Resource Allocation Scheme in 6G Environment with Public Blockchains. GLOBECOM 2020 - 2020 IEEE Global Communications Conference, 2020, pp. 1–6. [CrossRef]
- Gabrielson, A.; Bauer, K.; Kelly, D.; Kearns, A.; Smith, W.M. CUE: A Standalone Testbed for 5G Experimentation. MILCOM 2021 - 2021 IEEE Military Communications Conference (MILCOM), 2021, pp. 745–750. [CrossRef]
- Shorov, A. 5G Testbed Development for Network Slicing Evaluation. 2019 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus), 2019, pp. 39–44. [CrossRef]
- Dzogovic, B.; Santos, B.; Do, V.T.; Feng, B.; Jacot, N.; Van Do, T. Connecting Remote eNodeB with Containerized 5G C-RANs in OpenStack Cloud. 2019 6th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/ 2019 5th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom), 2019, pp. 14–19. [CrossRef]
- Pepito, R.; Dutta, A. Open Source 5G Security Testbed for Edge Computing. 2021 IEEE 4th 5G World Forum (5GWF), 2021, pp. 388–393. [CrossRef]
- Lee, G.; Lee, J.; Kim, Y.; Park, J.G. Network Flow Data Re-collecting Approach Using 5G Testbed for Labeled Dataset. 2021 23rd International Conference on Advanced Communication Technology (ICACT), 2021, pp. 254–258. [CrossRef]
- Astrakhantsev, A.; Globa, L.; Novogrudska, R.; Skulysh, M. ; O.Ye, S. Improving resource allocation system for 5G networks. 2021 International Conference on Information and Digital Technologies (IDT), 2021, pp. 182–188. [CrossRef]
- Hussein, A.; Elhajj, I.H.; Chehab, A.; Kayssi, A. SDN VANETs in 5G: An architecture for resilient security services. 2017 Fourth International Conference on Software Defined Systems (SDS), 2017, pp. 67–74. [CrossRef]
- Al-Turjman, F.; Alturjman, S. Context-Sensitive Access in Industrial Internet of Things (IIoT) Healthcare Applications. IEEE Transactions on Industrial Informatics 2018, 14, 2736–2744. [Google Scholar] [CrossRef]
- Khalid, H.; Hashim, S.J.; Ahmad, S.M.S.; Hashim, F.; Chaudhary, M.A. Robust Multi-Gateway Authentication Scheme for Agriculture Wireless Sensor Network in Society 5.0 Smart Communities. Agriculture 2021, 11. [Google Scholar] [CrossRef]
- Ghassemian, M.; Smith-Creasey, M.; Nekovee, M. Secure Non-Public Health Enterprise Networks. 2020 IEEE International Conference on Communications Workshops (ICC Workshops), 2020, pp. 1–6. [CrossRef]
- Li, X.; Hu, X.; Zhang, R.; Zhou, C.; Yin, Q.; Yang, L. A Model-Driven Security Analysis Approach for 5G Communications in Industrial Systems. IEEE Transactions on Wireless Communications 2023, 22, 889–902. [Google Scholar] [CrossRef]
- Kim, J.; Duguma, D.G.; Astillo, P.V.; Park, H.Y.; Kim, B.; You, I.; Sharma, V. A Formally Verified Security Scheme for Inter-gNB-DU Handover in 5G Vehicle-to-Everything. IEEE Access 2021, 9, 119100–119117. [Google Scholar] [CrossRef]
- Unal, D.; Hammoudeh, M.; Kiraz, M.S. Policy specification and verification for blockchain and smart contracts in 5G networks. ICT Express 2020, 6, 43–47. [Google Scholar] [CrossRef]
- Hou, W.; Sun, Y.; Li, D.; Guan, Z.; Liu, J. Lightweight and Privacy-Preserving Charging Reservation Authentication Protocol for 5G-V2G. IEEE Transactions on Vehicular Technology 2023, 72, 7871–7883. [Google Scholar] [CrossRef]
- Afaq, A.; Haider, N.; Baig, M.Z.; Khan, K.S.; Imran, M.; Razzak, I. Machine learning for 5G security: Architecture, recent advances, and challenges. Ad Hoc Networks 2021, 123, 102667. [Google Scholar] [CrossRef]
| Threats | Description | Vulnerabilities |
|---|---|---|
| Espionage and collection | An attacker can eavesdrop on communication and collect information about the user’s equipment, equipment capabilities (supported encryption algorithms), or signature. | Lack of encryption in certain signaling messages. |
| Redirection, discarding, and creation | An attacker can redirect, discard, or create calls/messages/authentication vectors. | Lack of mutual authentication in the context of 2G; lack of encryption in certain signaling messages; lack of integrity in signaling messages in the context of 2G; weak encryption algorithms (e.g., A5/1); lack of additional countermeasures for weak encryption algorithms. |
| Disabling or detaching user equipment | An attacker can disable or detach user equipment from the network. | Lack of mutual authentication; lack of encryption in certain signaling messages; lack of integrity; weak encryption algorithms (e.g., A5/1); lack of additional countermeasures for weak encryption algorithms. |
| Eavesdropping with access or listening | An attacker can eavesdrop on communication and subsequently access a message (SMS or packet) or listen to a call. | Weak encryption algorithms (e.g., A5/1); lack of network authentication by the user. |
| Threats | Description | Vulnerabilities |
|---|---|---|
| Redirection, dropping, and injection | An attacker can redirect, drop, or inject calls or messages (SMS or packets). | Lack of integrity in user data messages and certain signaling messages. |
| Location retrieval | An attacker can retrieve the subscriber’s location using the IMSI, TMSI/GUTI, and optionally, the TAI. | Lack of encryption in certain signaling messages, i.e., RRC connection and paging messages; infrequent TMSI/GUTI allocation; and allocation of IMSI instead of TMSI. |
| Inference mapping | An attacker can inferentially map information between different sources. | There is a lack of encryption in certain RRC signaling messages, pre-authentication traffic, and infrequent TMSI/GUTI allocation. |
| Denial of Service and QoS degradation attacks | An attacker can successfully perform a DoS attack against the network by impersonating a legitimate user. This attack makes a network resource unavailable, interfering or temporarily/definitively disrupting the service. | Lack of encryption in certain RRC signaling messages; lack of integrity in certain signaling messages; weak encryption algorithms (e.g., A5/1 or A5/2); infrequent AKA allocation; and infrequent TMSI/GUTI allocation. |
| Threats | Description | Vulnerabilities |
|---|---|---|
| DoS and QoS degradation attacks | An attacker can successfully launch a DoS attack on the network by impersonating a legitimate user. | Lack of encryption in certain RRC signaling messages; lack of integrity in certain signaling messages; rare allocation of AKA; and rare allocation of TMSI/GUTI. |
| UE or base station impersonation | The 5G NR specifications also use an RRC and NAS protocol architecture very similar to LTE, and therefore, an attacker can impersonate UE or a base station, collect all broadcast information, such as EARFCN, PCI, ECGI of neighboring cells, and thus impersonate authentic network elements. | Traditional IMS servers designed for VoIP do not validate the subscriber identifier in received call setup requests, allowing an attacker to impersonate other subscribers; IP address and SIP header can be falsified due to lack of protection mechanisms; lack of sufficient control to authorize X2 interface establishment. |
| Forced network technology downgrading for the user | An attacker can force the UE to use a communication technology older than 5G, downgrading the communication security level. | Absence of protection mechanisms in handover between different generation networks; the possibility of requesting UE radio access capabilities before RRC security configuration; the Attach Request message is sent unencrypted by the UE to the network; UE registration process is not interrupted even if integrity verification fails at the MME. |
| Threats | Architectural Part Affected | Risks |
|---|---|---|
| Perform Unauthorized Access to Confidential Data [54,55] | RAN, MEC, NG-CORE | Extortion, Data Privacy Violation Through Misuse and Disclosure |
| Analyze Air Interface Traffic [56,57] | RAN | Theft of Access Credentials, User Identifiers, and Location Parameters |
| Perform Data Leakage [58] | MEC | Personal, Corporate or Financial Damages |
| Extract Private Information of Other Users Using a Shared Service in an Unauthorized Manner [58] |
MEC, NG-CORE | Information Disclosure |
| Eavesdrop Messages to Legitimize Users [59] | RAN | Identity Forgery |
| Sniffing the Physical Broadcast Channel (PBCH) [60] | RAN | Collection of Base Station and User Equipment Information |
| Unauthorized Access to Home Subscriber Server to Steal User Parameters [61] | NG-CORE | Identity Forgery |
| Use Software to Compromise Encryption Algorithms (ex. compromise the advanced encryption standard) [61] |
RAN, MEC, NG-CORE | Exposure of Critical Information |
| Use Application Instance to Intercept Traffic Flows or Perform Black Holes [62] | MEC | Leakage or Loss of Information |
| Intercept a Key [63] | RAN, NG-CORE | Exposure of Critical Information |
| Identify a Subscriber’s Identity [63] | RAN, NG-CORE | Identity Forgery |
| Track a Subscriber’s Location [63] | RAN, NG-CORE | Information Disclosure |
| Threats | Architectural Part Affected | Risks |
|---|---|---|
| Maliciously Use Legitimate Access to the Orchestrator [58] | RAN, MEC, NG-CORE | Manipulate the Configuration and Run a Compromised Network Function |
| Tampering of Data [54] | RAN, MEC, NG-CORE | Create Network Congestion for Performance Degradation |
| Modify Traffic [64] | RAN, MEC, NG-CORE | Create Network Congestion for Performance Degradation |
| Change Network Elements Configuration Using the Management Interface [58] | RAN | Route Switching, Packet Dropping, and Data Inteception |
| Transmit False Primary Synchronization Signal (PSS) and Secondary Synchronization Signal (SSS) [60] | RAN | Getting UEs Information and Network Configuration Parameters |
| Spoofing the Physical Broadcast Channel (PBCH) [60] | RAN | Misconfiguration of Parameters for Establishing Communication on the Channel |
| Spoof the Physical Random Access Channel (PRACH) [60] | RAN | Pejudicate the Transport of Random Access Preamble from the UE to the gNB |
| Reprogram or Attack Controller Functions [61] | RAN, MEC, NG-CORE | Malfunctioning or Unavailability of Services |
| Send Forged or Spoofed Traffic Streams [65] | UE, MEC | Overloading of Services, Interruption or Malfunctioning of Applications |
| Calculate Valid session Keys to Reproduce the Same Message [66] | NG-CORE | Breach of confidentiality, Forgery or Impersonation |
| Take Advantage of a Fake or Unauthorized MEC Gateway [67] | MEC | Packet hijacking, Information theft, Application Malfunctioning |
| Spoof DNS Servers and IP Addresses to Spread Viruses [68] | UE, RAN, MEC, NG-CORE | Malicious Code Installation, Host Hijacking, Network Device Infection |
| Threats | Architectural Part Affected | Risks |
|---|---|---|
| Take Advantage of Malicious Insiders Attacks [58] | RAN, MEC, NG-CORE | Inject Malicious Code, Infect Devices with Malware, and Intentional Misconfigurations of Devices |
| Perform Resource Exhaustion [13] | RAN | Generate Destructive Interference |
| Make Services Unavailable [67] | RAN, NG-CORE | Unavailability of Critical Parts of the System Can Interrupt the Entire Service of a Coverage Area |
| Perform Attacks for Resource Shortages [58] | RAN | Unavailable or Scarce Resources for Legitimate Applications or Devices |
| Use North and South Boundary Interfaces to Attack the SDN Controller [58] | RAN, MEC, NG-CORE | Misconfigurations, Malicious Code or Instance of Application |
| Communication Channels Attacks [59,60] | RAN | Block the Physical Broadcast Channel (PBCH), Block the Physical Downlink Control Channel (PDCCH), and Block Uplink or Downlink Signal (Data Plane) |
| Use Application Instance to Perform Black Holes [60] | MEC | Redirect or Interrupt Data Traffic |
| Attack Open Edge APIs [67] | MEC | Disable or Impair Services that Need Edge Processing for Low Latency |
| Disable IoT Device Power Saving Abilities [68] | UE | Reduced Battery Life, Shutdown of Devices with Only the Battery as Power Source, Overheating Can Lead to Poor Device Performance |
| Attack the Weakest Link of Heterogeneous 5G Networks [56] | RAN, MEC, NG-CORE | Partial or total interruption of the network, a Single Fragile Part in the Security of the System Can Impact the Rest of the Architecture that a Priori Would Be Well Protected |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





