Submitted:
18 December 2023
Posted:
21 December 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
- (i)
- A novel closed loop system model of networked UMV systems with an event-triggered unit and a quantizer is established. The impact of network induced delay, external disturbance and aperiodic DoS attack are involved.
- (ii)
- A quantitative mechanism is installed on the basis of adaptive event-triggered unit which can further save the network resources. And an environment accompanied by more severe cyber attack is considered.
1.1. Notation
2. Preliminaries and problem formulation
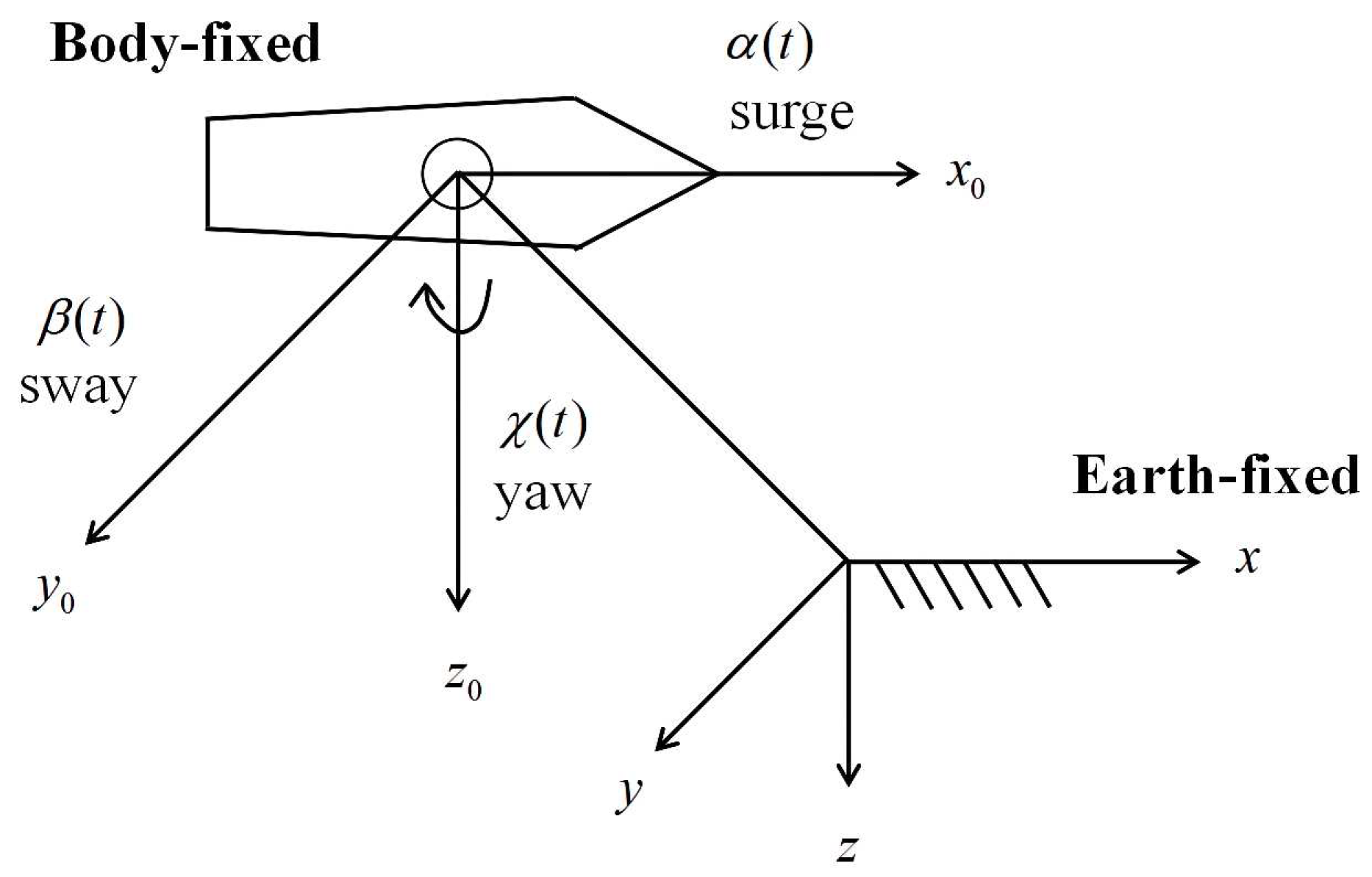
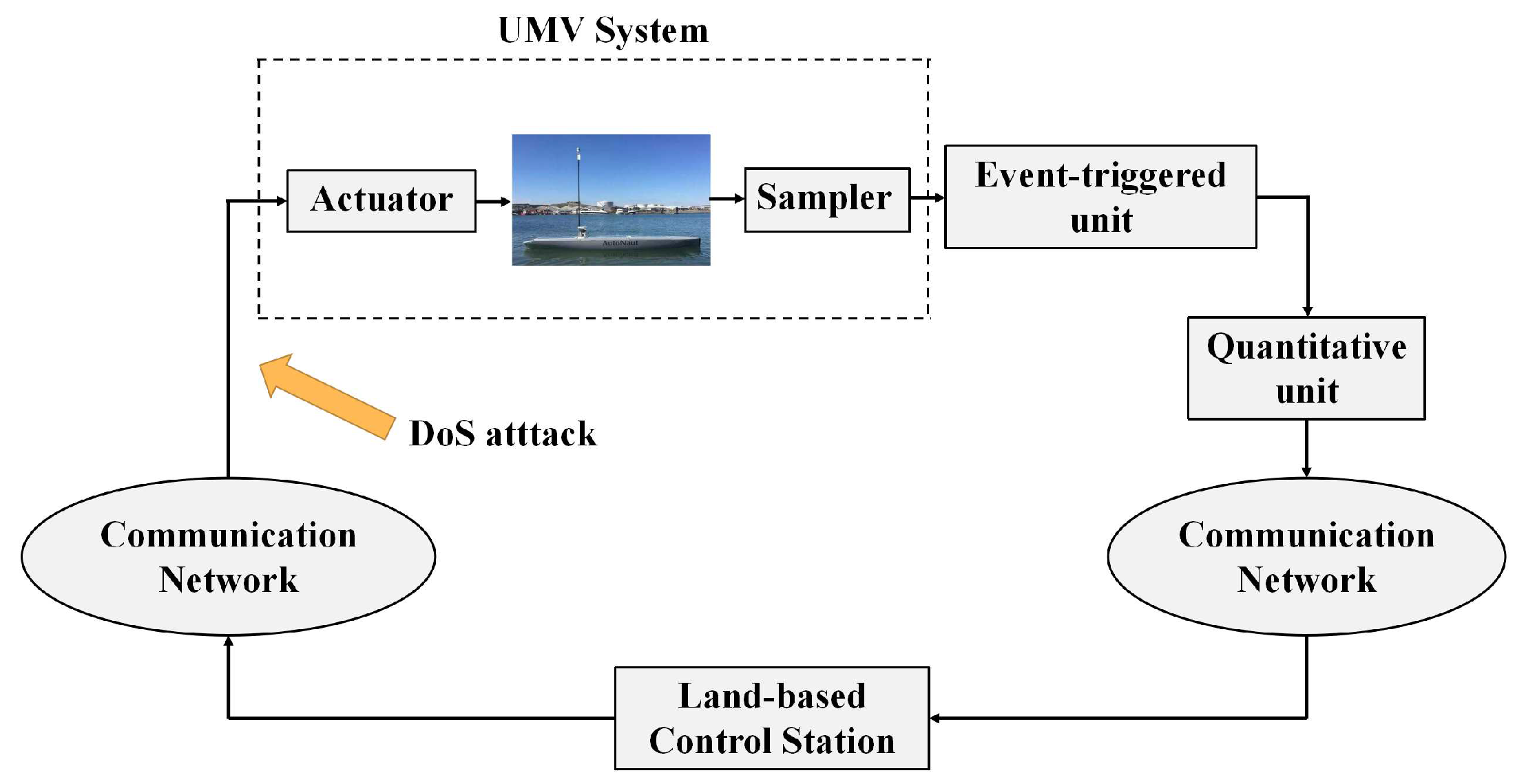
2.1. Networked modelling for the UMV system
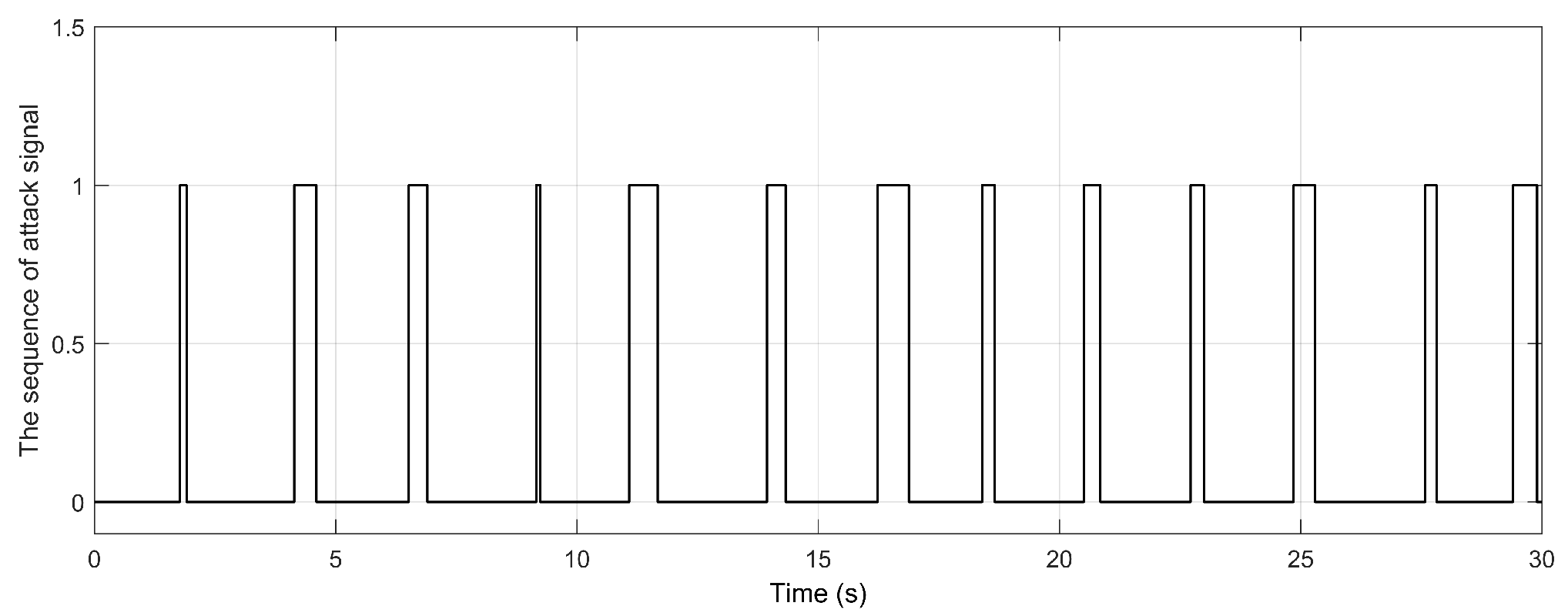
2.2. Aperiodic DoS attack
2.3. The adaptive event-triggered communication mechanism
2.4. The quantitative mechanism
2.5. The investigated dynamic output feedback control strategy
3. Main result
3.1. The analysis of stability
3.2. The analysis of performance
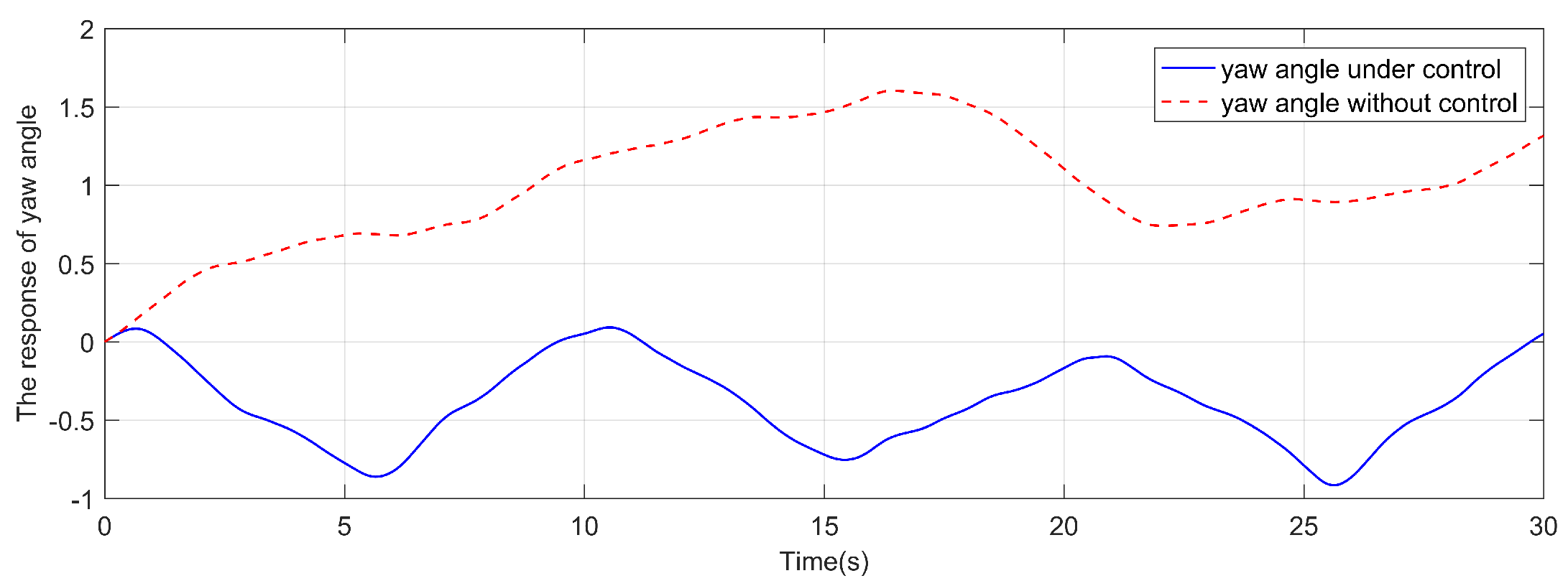
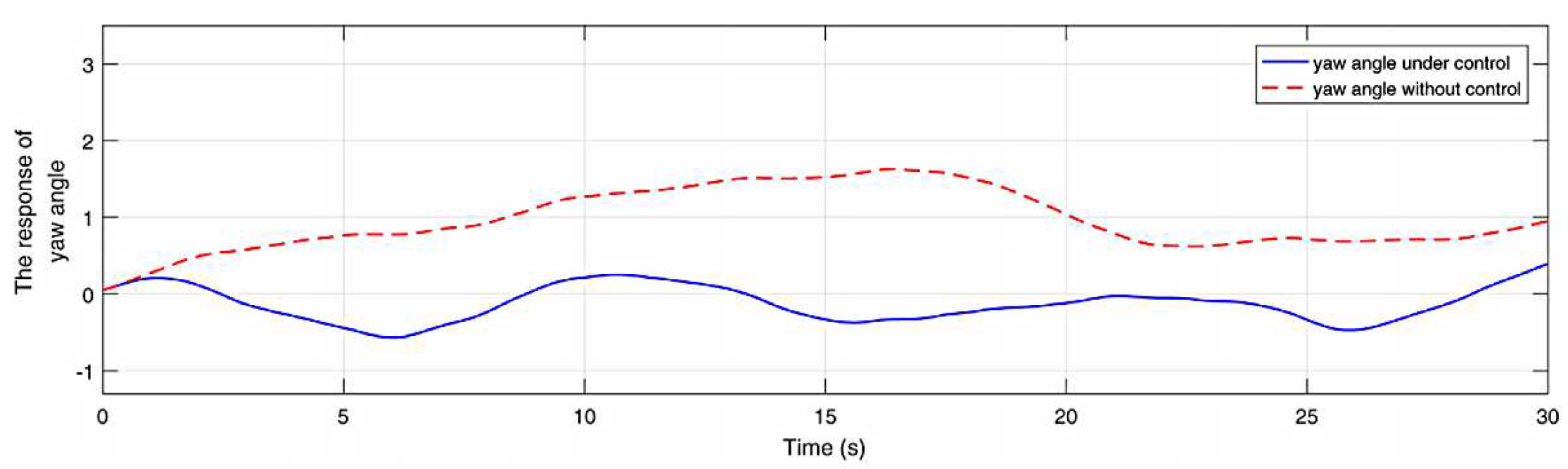
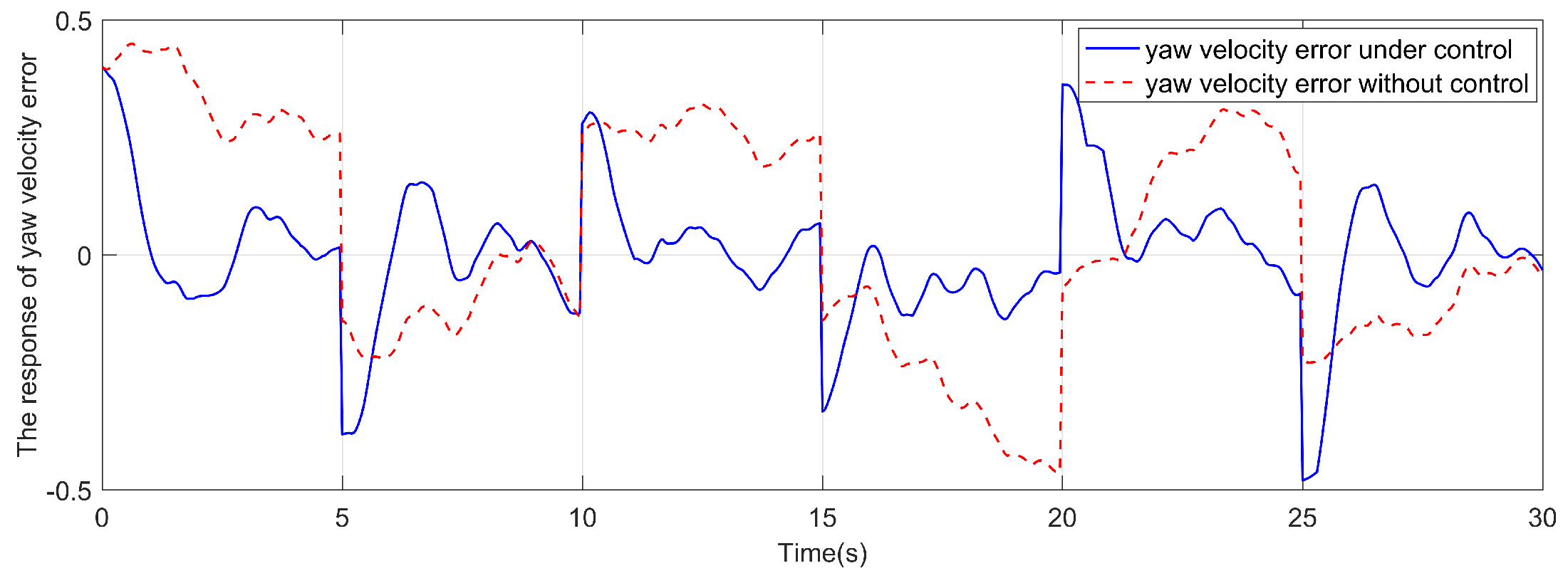
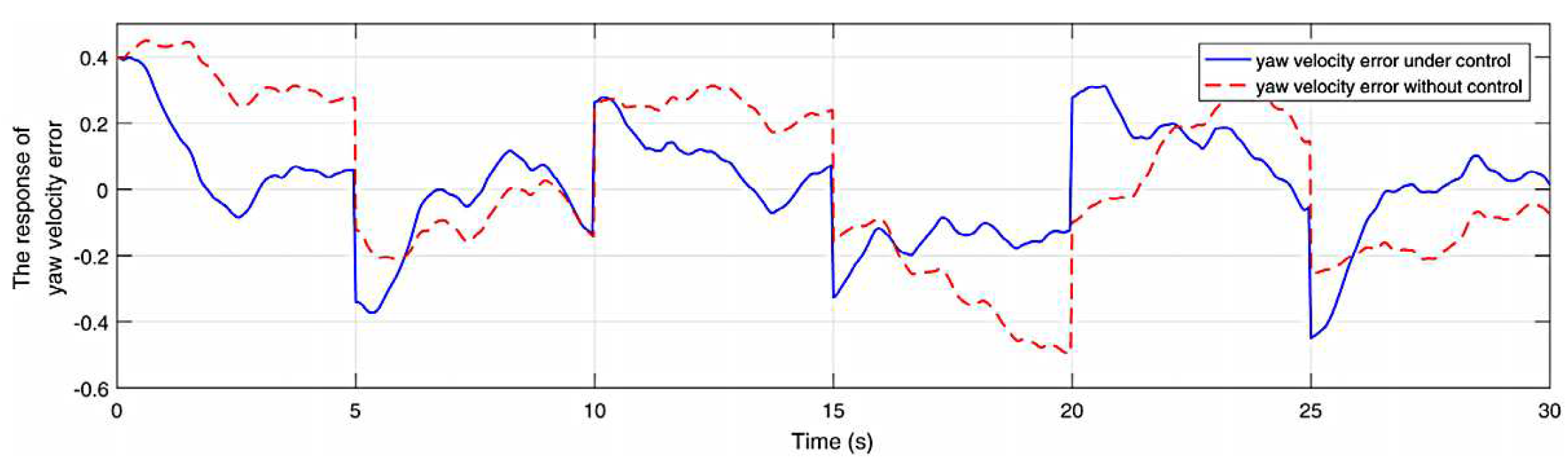
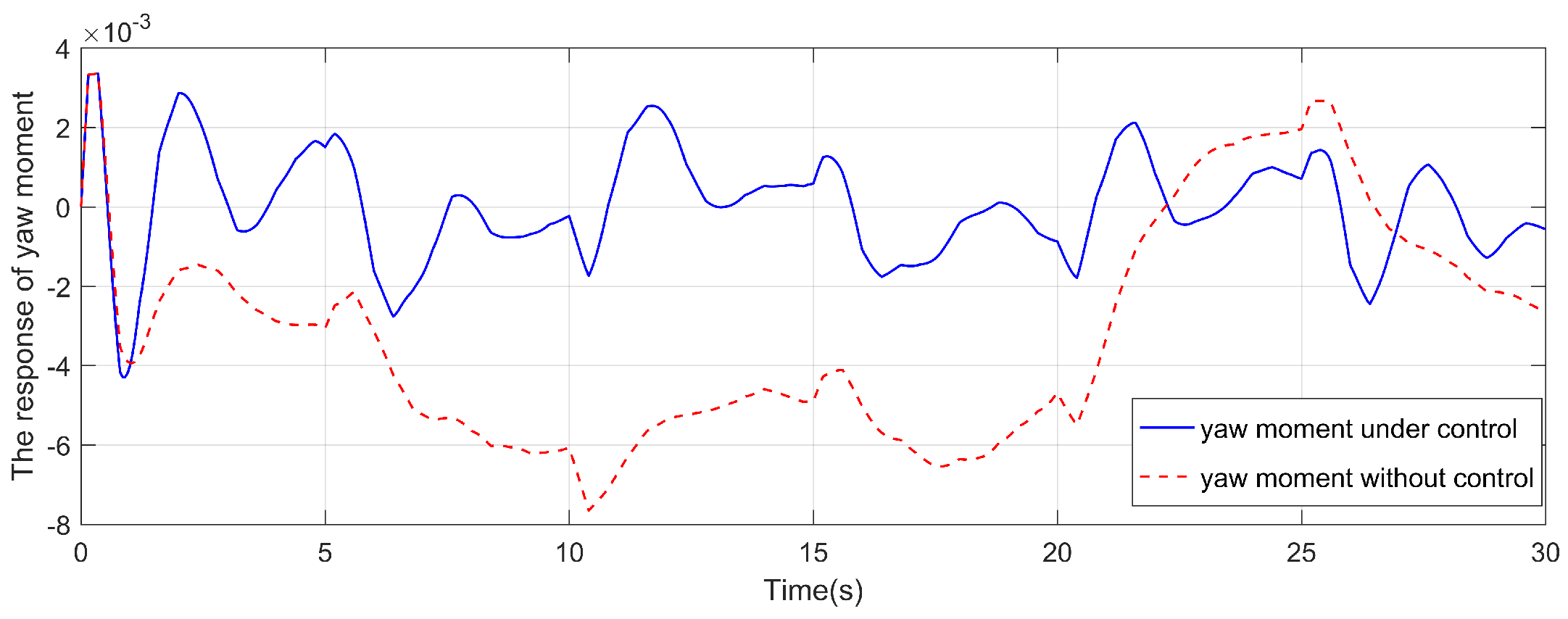
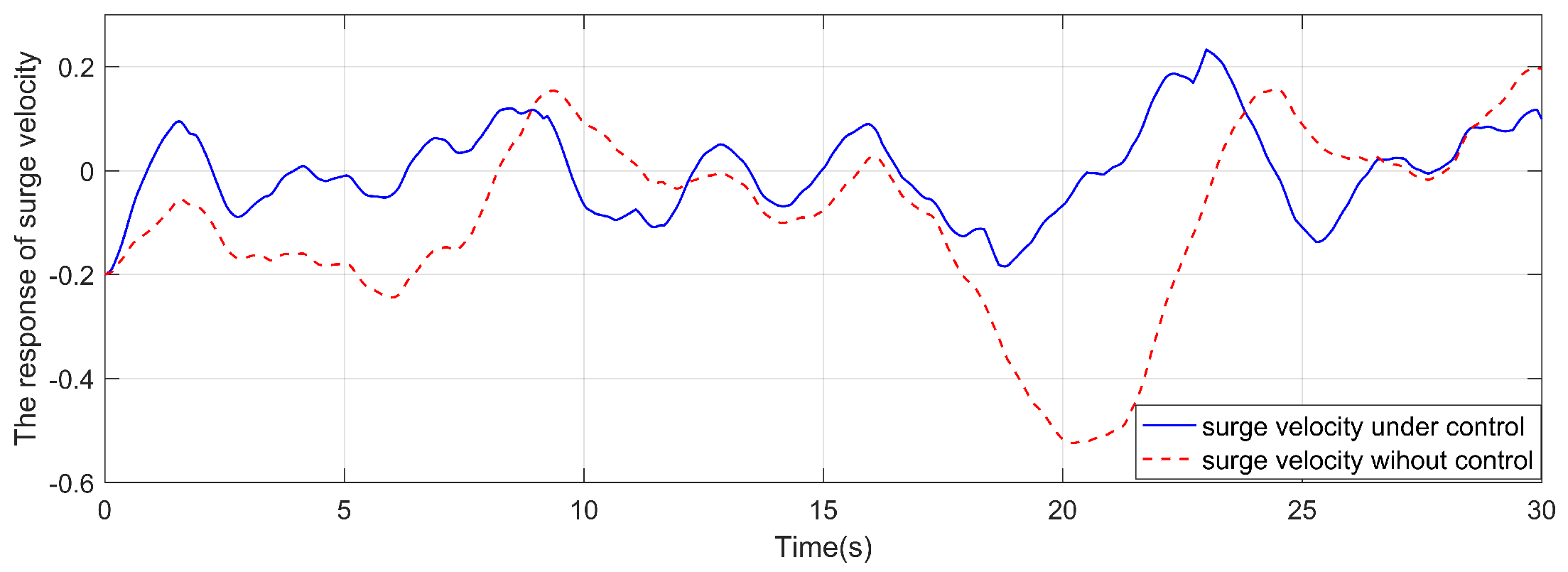
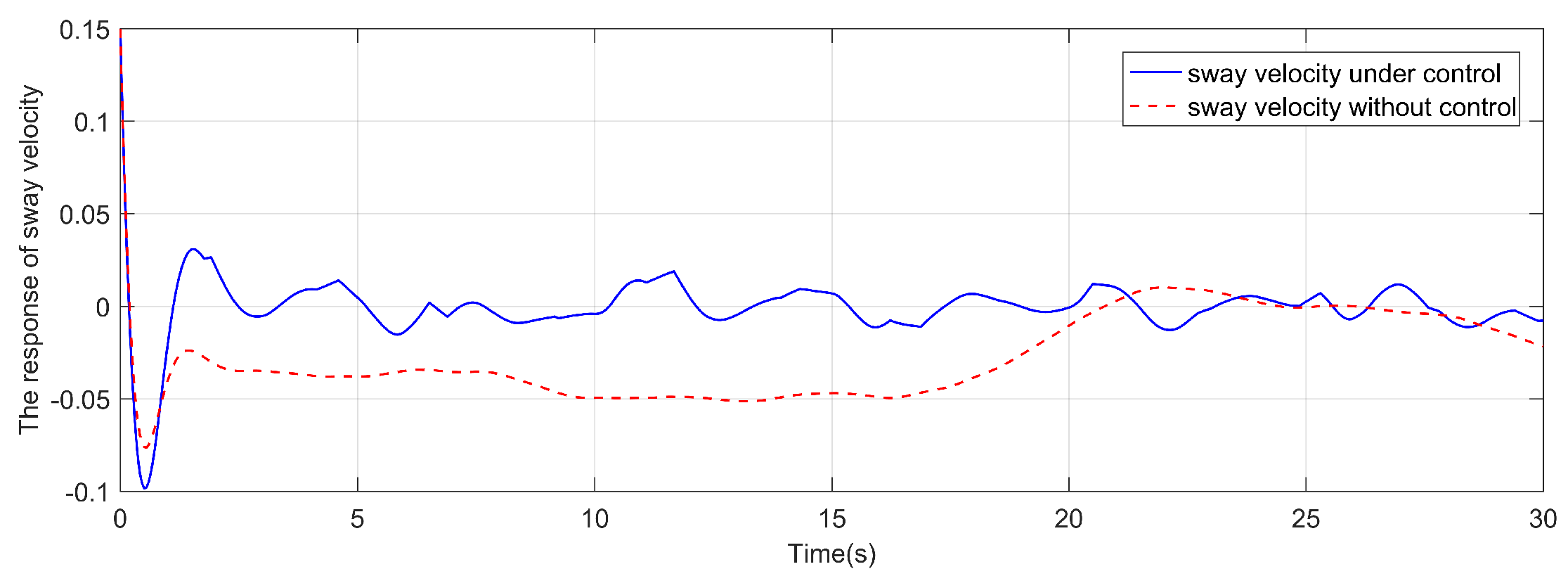
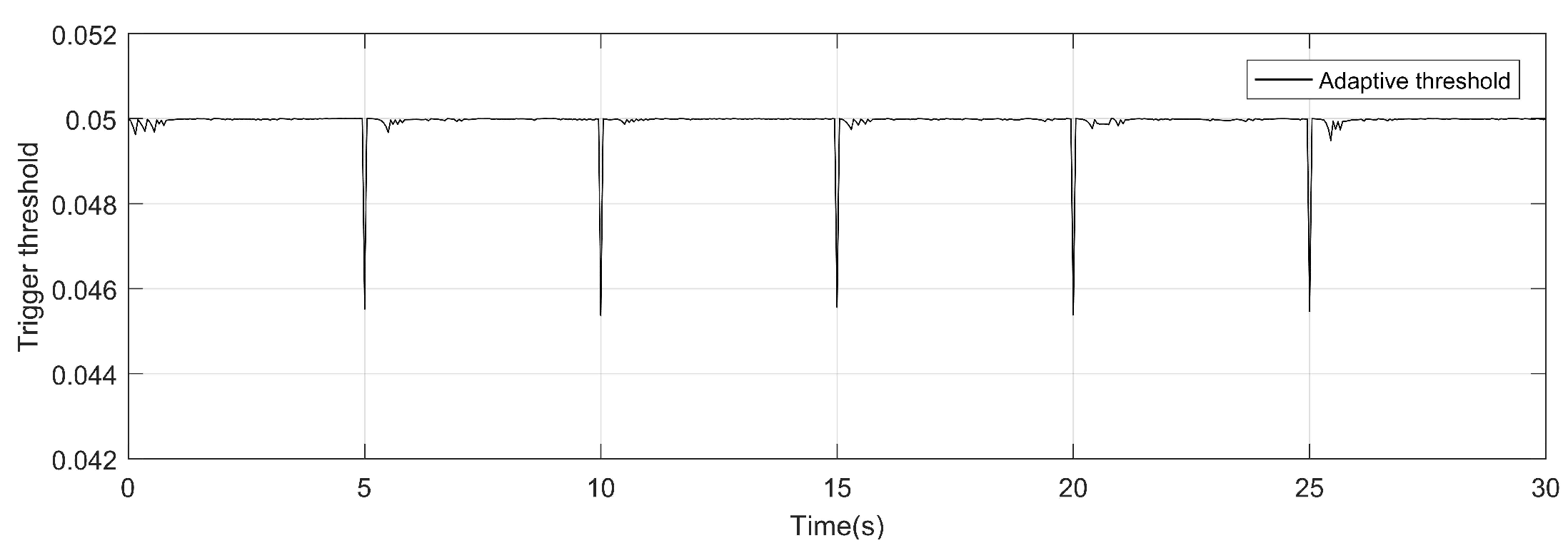
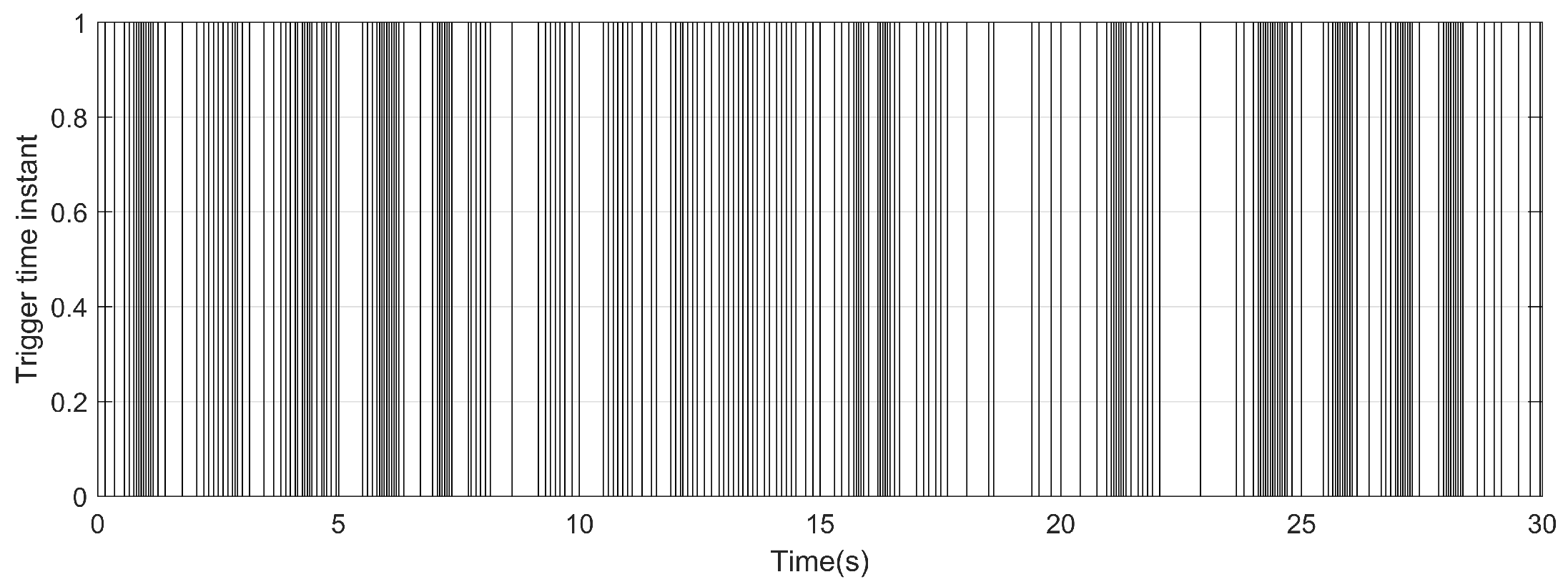
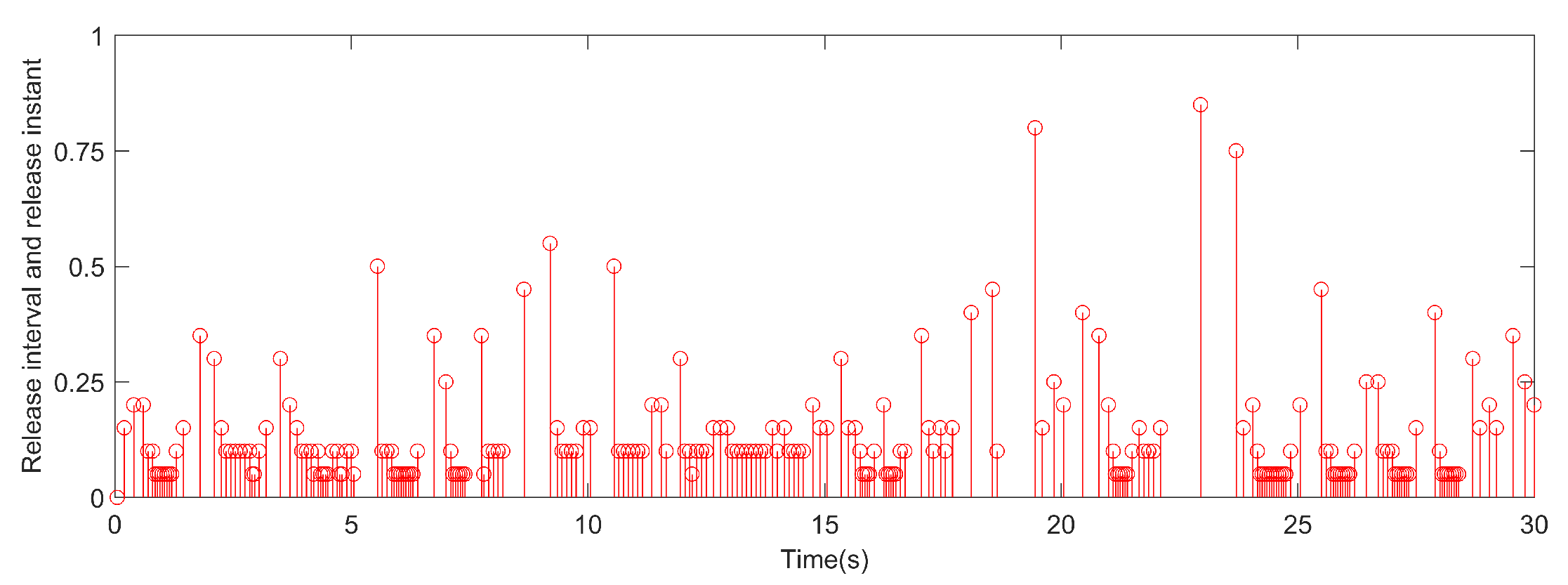
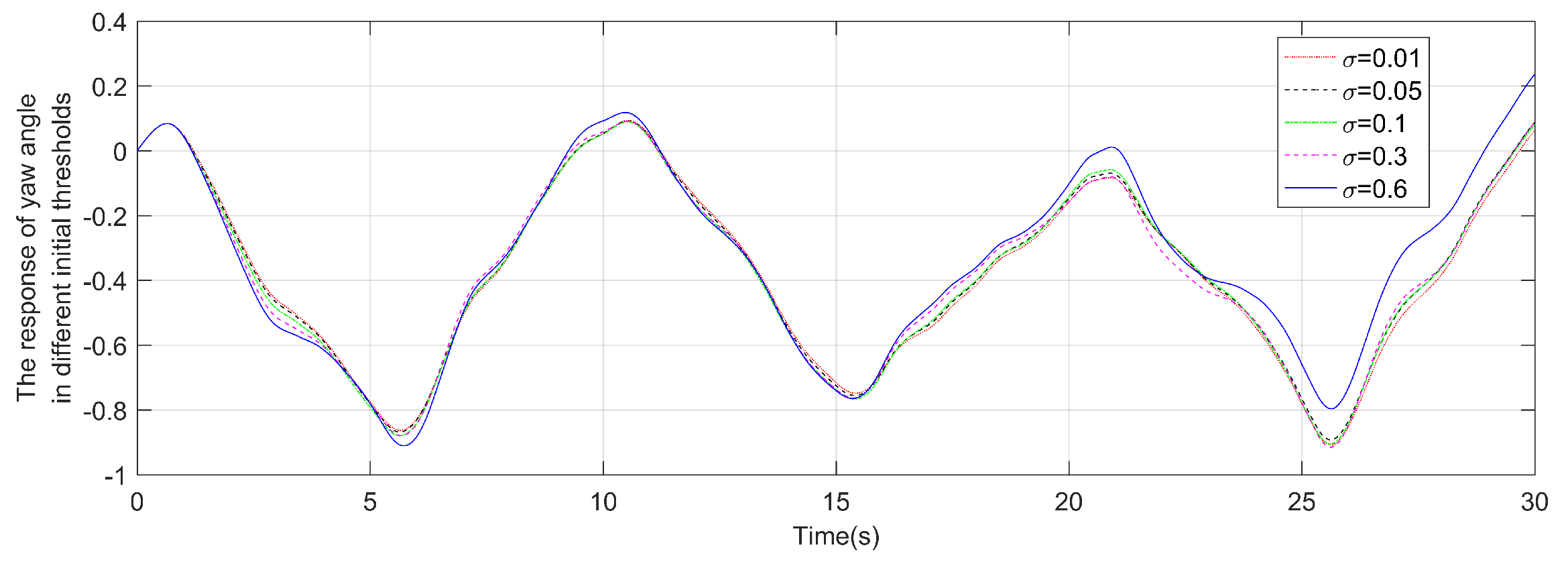
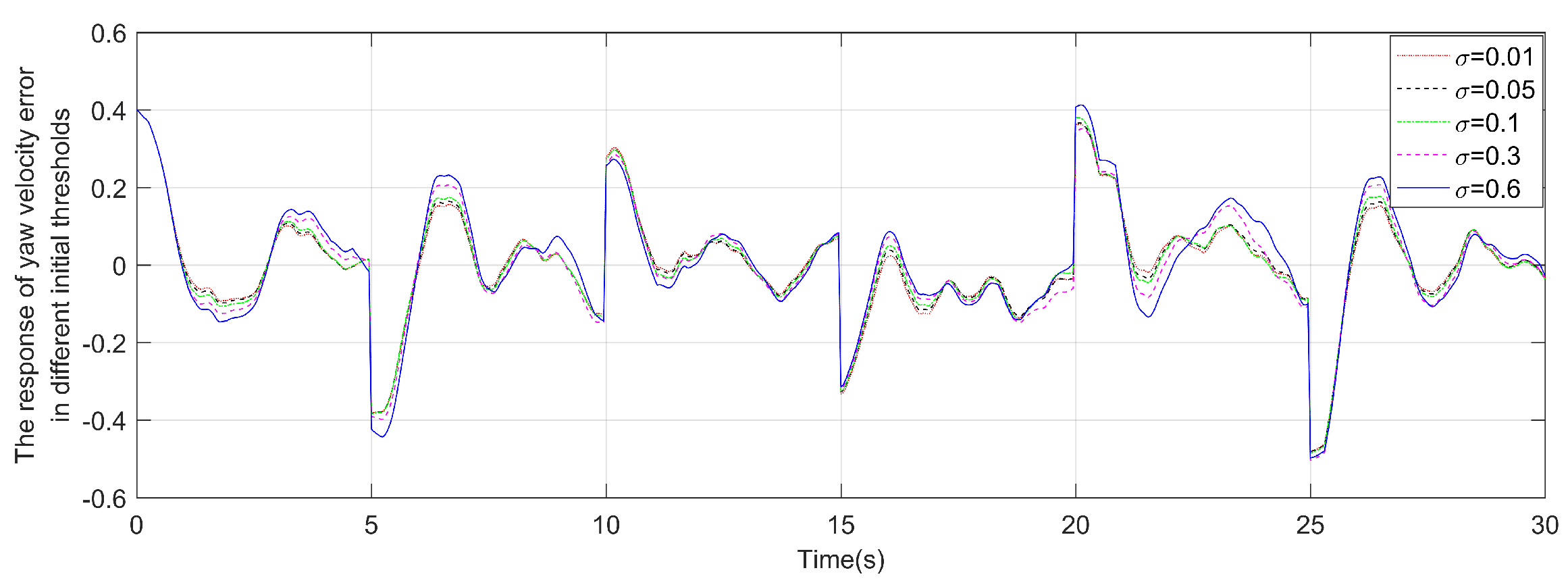
4. Simulation and analysis
| No control(Reference [19]) | 1.6805 | - | 6.3338 | - |
| No control | 1.6808 | - | 6.3868 | - |
| With control(Reference [19]) | 0.9602 | 42.9% | 3.7957 | 40.1% |
| With control | 0.9554 | 43.2% | 3.4580 | 45.9% |
| Threshold parameter | 0.05 | 0.1 | 0.6 | 0.8 |
| Reference [43] | 232 | 174 | 65 | 60 |
| Reference [44] | 302 | 236 | 96 | 86 |
| This work | 232 | 174 | 64 | 58 |
| Threshold parameter | 0.05 | 0.1 | 0.6 | 0.8 |
| Reference [43] | 0.9795 | 0.9848 | 1.2082 | 1.2317 |
| Reference [44] | 0.9712 | 0.9776 | 1.1970 | 1.2073 |
| This work | 0.9795 | 0.9848 | 1.2054 | 1.2119 |
| Threshold parameter | 0.05 | 0.1 | 0.6 | 0.8 |
| Reference [43] | 3.4709 | 3.5263 | 4.2739 | 4.4751 |
| Reference [44] | 3.4574 | 3.4992 | 3.8627 | 4.0627 |
| This work | 3.4680 | 3.5213 | 4.0428 | 4.4620 |
| Trigger times | |||||
| No control | 1.6808 | - | 6.3868 | - | 600 |
| 0.9249 | 45.0% | 3.4296 | 46.3% | 395 | |
| 0.9544 | 43.2% | 3.4680 | 45.9% | 232 | |
| 0.9595 | 42.9% | 3.5213 | 44.9% | 175 | |
| 0.9658 | 42.5% | 3.7041 | 42.0% | 99 | |
| 1.1420 | 32.1% | 4.0428 | 36.7% | 69 |
5. Conclusion
Author Contributions
Funding
Conflicts of Interest
References
- Nieto-Hidalgo, M.; Gallego, A.J.; Gil, P.; Pertusa, A. Two-Stage Convolutional Neural Network for Ship and Spill Detection Using SLAR Images. IEEE Transactions on Geoscience & Remote Sensing 2018, 56, 5217–5230. [Google Scholar]
- Zhang, D.; Liu, G. Predictive control for networked high-order fully actuated systems subject to communication delays and external disturbances. ISA Transactions 2023. [Google Scholar] [CrossRef] [PubMed]
- Wang, W.; Wang, Y.; Liu, X.; Zhiwei, L. Quantized control for networked switched systems under denial-of-service attacks via a barrier event-triggered mechanism. Nonlinear Analysis: Hybrid Systems 2023, 49. [Google Scholar] [CrossRef]
- Chen, P.; Wu, J.; Tian, E. Stochastic Event-Triggered H∞ Control for Networked Systems Under Denial of Service Attacks. IEEE Transactions on Systems, Man, and Cybernetics: Systems 2022, 52, 4200–4210. [Google Scholar] [CrossRef]
- Zhang, L.; Nguang, S.; Yan, S. Event-triggered H∞ control for networked control systems under denial-of-service attacks. Transactions of the Institute of Measurement and Control 2021, 43(5), 1077–1087. [Google Scholar] [CrossRef]
- Wang, H.; Dong, Z.; Qi, S.; Zhang, Z.; Zhang, H. Trajectory-tracking control of an underactuated unmanned surface vehicle based on quasi-infinite horizon model predictive control algorithm. Transactions of the Institute of Measurement and Control 2022. [Google Scholar] [CrossRef]
- Wang, N.; Qian, C.; Sun, J.; Liu, Y. Adaptive Robust Finite-Time Trajectory Tracking Control of Fully Actuated Marine Surface Vehicles. IEEE Transactions on Control Systems Technology 2016, 24(4), 1454–1462. [Google Scholar] [CrossRef]
- Hao, L.; Yu, y.; Li, T.; Li, H. Quantized Output-Feedback Control for Unmanned Marine Vehicles With Thruster Faults via Sliding-Mode Technique. IEEE Transactions on Cybernetics 2022, 52, 9363–9376. [Google Scholar] [CrossRef] [PubMed]
- Li, X.; Pan, H.; Deng, Y.; Han, S.; Yu, H. Finite-time event-triggered sliding mode predictive control of unmanned underwater vehicles without velocity measurements. Ocean Engineering 2023, 276. [Google Scholar] [CrossRef]
- Huang, C.; Xu, H.; Batista, P.; Zhang, X.; Guedes Soares, C. Fixed-time leader-follower formation control of underactuated unmanned surface vehicles with unknown dynamics and ocean disturbances. European Journal of Control 2023, 70. [Google Scholar] [CrossRef]
- Tang, C.; Zhang, H.T.; Wang, J. Flexible Formation Tracking Control of Multiple Unmanned Surface Vessels for Navigating Through Narrow Channels with Unknown Curvatures. IEEE Transactions on Industrial Electronics 2023, 70, 2927–2938. [Google Scholar] [CrossRef]
- Ma, Y.; Zhu, P.; Zhu, G.; Yan, X. Cooperative towing for double unmanned surface vehicles connected with a floating rope via vertical formation and adaptive moment control. Ocean Engineering 2023, 279. [Google Scholar] [CrossRef]
- Qin, H.; Chen, X.; Sun, Y. Adaptive state-constrained trajectory tracking control of unmanned surface vessel with actuator saturation based on RBFNN and tan-type barrier Lyapunov function. Ocean Engineering 2022, 253. [Google Scholar] [CrossRef]
- Wan, L.; Cao, Y.; Sun, Y.; Hongde, Q. Fault-tolerant trajectory tracking control for unmanned surface vehicle with actuator faults based on a fast fixed-time system. ISA Transactions 2022, p. [Google Scholar] [CrossRef] [PubMed]
- Wang, Y.; Jiang, B.; Wu, Z.; Xie, S.; Peng, Y. Adaptive Sliding Mode Fault-Tolerant Fuzzy Tracking Control With Application to Unmanned Marine Vehicles. IEEE Transactions on Systems, Man, and Cybernetics: Systems 2021, 51, 6691–6700. [Google Scholar] [CrossRef]
- Tang, F. Coverage path planning of unmanned surface vehicle based on improved biological inspired neural network. Ocean Engineering 2023, 278. [Google Scholar] [CrossRef]
- Zhang, G.; Dong, X.; Liu, J.; Zhang, X. Nussbaum-type function based robust neural event-triggered control of unmanned surface vehicle subject to cyber and physical attacks. Ocean Engineering 2023, 270. [Google Scholar] [CrossRef]
- Li, M.; Guo, C.; Yu, H. Global finite-time control for coordinated path following of multiple underactuated unmanned surface vehicles along one curve under directed topologies. Ocean Engineering 2021, 237. [Google Scholar] [CrossRef]
- Ye, Z.; Zhang, D.; Wu, Z. Adaptive event-based tracking control of unmanned marine vehicle systems with DoS attack. Journal of the Franklin Institute 2021, 358(3), 1915–1939. [Google Scholar] [CrossRef]
- Liang, X.; Qu, X.; Hou, Y.; Li, Y.; Zhang, R. Distributed coordinated tracking control of multiple unmanned surface vehicles under complex marine environments. Ocean Engineering 2020, 205. [Google Scholar] [CrossRef]
- Qu, Y.; Cai, L. Nonlinear station keeping control for underactuated unmanned surface vehicles to resist environmental disturbances. Ocean Engineering 2022, 246. [Google Scholar] [CrossRef]
- Deng, Y.; Yin, X.; Hu, S. Event-triggered predictive control for networked control systems with DoS attacks. Information Sciences 2021, 542, 71–91. [Google Scholar] [CrossRef]
- Lian, J.; Han, Y. Switching-Like Event-Triggered Control for Networked Markovian Jump Systems Under Deception Attack. IEEE Transactions on Circuits and Systems II: Express Briefs 2021, 68, 3271–3275. [Google Scholar] [CrossRef]
- Ye, Z.; Zhang, D.; Yan, H.; Wu, Z. A semi-Markovian jumping system approach to secure DPC of nonlinear networked unmanned marine vehicle systems with DoS attack. Journal of the Franklin Institute 2021. [Google Scholar] [CrossRef]
- Ye, Z.; Zhang, D.; Wu, Z.; Yan, H. A3C-Based Intelligent Event-Triggering Control of Networked Nonlinear Unmanned Marine Vehicles Subject to Hybrid Attacks. IEEE Transactions on Intelligent Transportation Systems 2021. [Google Scholar] [CrossRef]
- Arzen, K.E. A simple event-based PID controller. Proceedings of IFAC World Congress 1999, 32(2), 8687–8692. [Google Scholar]
- Han, X.; Zhao, X.; Sun, T.; Xu, N.; Zong, G. Event-Triggered Optimal Control for Discrete-Time Switched Nonlinear Systems With Constrained Control Input. IEEE Transactions on Systems Man Cybernetics-Systems 2021, 51, 7850–7859. [Google Scholar] [CrossRef]
- Li, Y.; Yang, G. Adaptive Neural Control of Pure-Feedback Nonlinear Systems With Event-Triggered Communications. IEEE Transactions on Neural Networks and Learning Systems 2018, 29(12), 6242–6251. [Google Scholar] [CrossRef] [PubMed]
- Hu, S.; Yue, D.; Xie, Y.; Ma, Y.; Yin, Y. Stabilization of Neural-Network-Based Control Systems via Event-Triggered Control With Nonperiodic Sampled Data. IEEE Transactions on Neural Networks and Learning Systems 2018, 29(3), 573–585. [Google Scholar] [CrossRef]
- Ma, L.; Wang, Y.; Han, Q. Event-Triggered Dynamic Positioning for Mass-Switched Unmanned Marine Vehicles in Network Environments. IEEE Transactions on Cybernetics 2022, 52, 3159–3171. [Google Scholar] [CrossRef]
- Li, M.; Guo, C.; Yu, H.; Yuan, Y. Event-triggered containment control of networked underactuated unmanned surface vehicles with finite-time convergence. Ocean Engineering 2022, 246. [Google Scholar] [CrossRef]
- Zhang, G.; Chu, S.; Huang, J.; Zhang, W. Robust adaptive fault-tolerant control for unmanned surface vehicle via the multiplied event-triggered mechanism. Ocean Engineering 2022, 249. [Google Scholar] [CrossRef]
- Li, Z.; Xiong, J. Event-triggered fuzzy filtering for nonlinear networked systems with dynamic quantization and stochastic cyber attacks. ISA Transactions 2022, 121, 53–62. [Google Scholar] [CrossRef] [PubMed]
- Zhao, Z.; Yi, X.; Ma, L.; Bai, X. Quantized recursive filtering for networked systems with stochastic transmission delays. ISA Transactions 2022, 127, 99–107. [Google Scholar] [CrossRef] [PubMed]
- Kahveci, N.; Ioannou, P. Adaptive steering control for uncertain ship dynamics and stability analysis. Automatica 2013, 49, 685–697. [Google Scholar] [CrossRef]
- Ma, Y.; Nie, Z.; Hu, S.; Li, Z.; Malekian, R.; Sotelo, M. Fault Detection Filter and Controller Co-Design for Unmanned Surface Vehicles Under DoS Attacks. IEEE Transactions on Intelligent Transportation Systems 2021, 22(3), 1422–1434. [Google Scholar] [CrossRef]
- Ge, X.; Han, Q. Distributed formation control of networked multi-agent systems using a dynamic event-triggered communication mechanism. IEEE Transactions on Industrial Electronics 2017, 64(10), 8118–8127. [Google Scholar] [CrossRef]
- Fu, M.; Xie, L. The sector bound approach to quantized feedbackcontrol. IEEE Transactions on Automatic Control 2005, 50(11), 1698–1711. [Google Scholar]
- Ge, X.; Han, Q. Distributed event-triggered H∞ filtering over sensor networks with communication delays. Information Sciences 2015, 291, 128–142. [Google Scholar] [CrossRef]
- Zhang, X.; Han, Q. Event-triggered dynamic output feedback control for networked control systems. IET Control Theory and Applications 2014, 8(4), 226–234. [Google Scholar] [CrossRef]
- Xu, S.; Dooren, P.V.; Stefan, R.; J., L. Robust stability and stabilization for singular systems with state delay and parameter uncertainty. IEEE Transactions on Automatic Control 2002, 47, 1122–1128. [CrossRef]
- Wang, Y.; Han, Q. Network-based modelling and dynamic output feedback control for unmanned marine vehicles in network environments. Automatica 2018, 91, 43–53. [Google Scholar] [CrossRef]
- Ma, Y.; Nie, Z.; Hu, S.; Li, Z.; Malekian, R.; Sotelo, M. Fault Detection Filter and Controller Co-Design for Unmanned Surface Vehicles Under DoS Attacks. IEEE Transactions on Intelligent Transportation Systems 2021, 22, 1422–1434. [Google Scholar] [CrossRef]
- Wang, H.; Xue, A. Adaptive event-triggered H∞ filtering for discrete-time delayed neural networks with randomly occurring missing measurements. Signal Processing 2018, 153, 221–230. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





