Submitted:
11 November 2023
Posted:
14 November 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Need for Cloud Migration
2.1. Cloud Migration Advantages
- 1.
- Pay-as-per usage Model.
- 2.
- Cost Effective
- 3.
- Smooth Business Continuity (Data Backup & Recovery)
- 4.
- Inter-Organization Data Sharing at Multiple Geographical Locations
- 5.
- Mobility
- 6.
- Focused Business Processes
- 7.
- More Physical Space
2.2. Cloud Migration: A thoughtful Decision
- a)
- Cloud Migration Strategies
- b)
- Cloud Migration Timeline & Cost
- c)
- Use of Existing ICT Infrastructure
- d)
- Decreased Level of Control
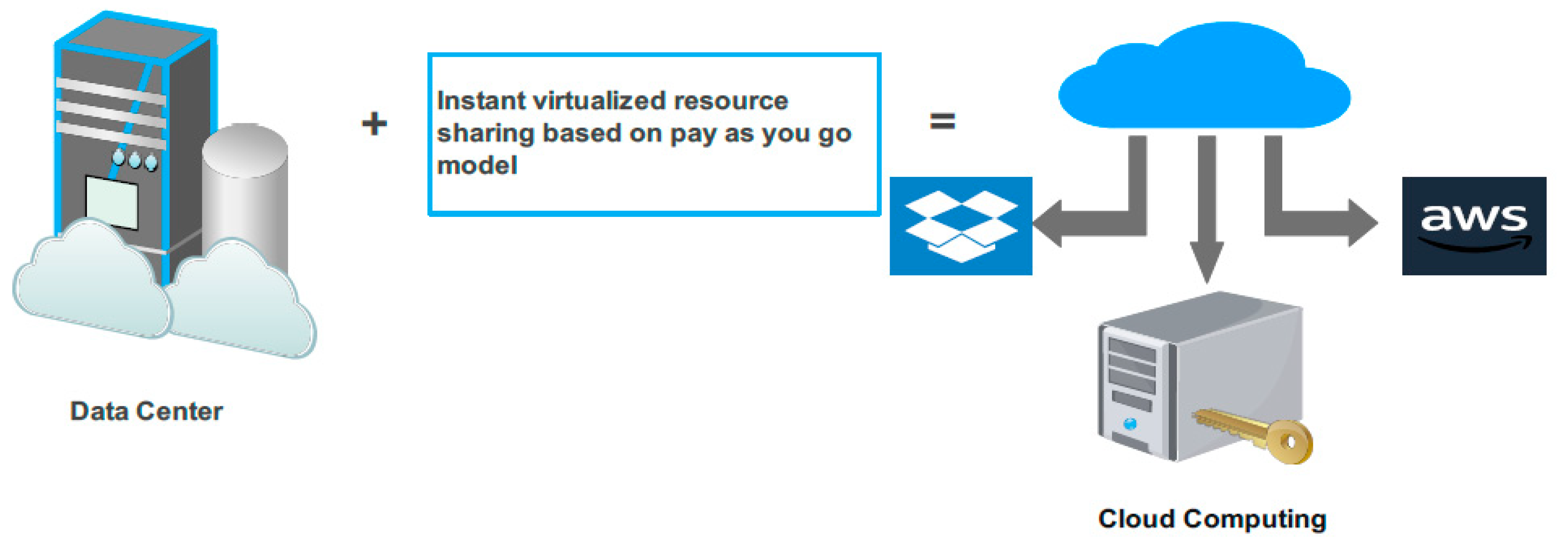
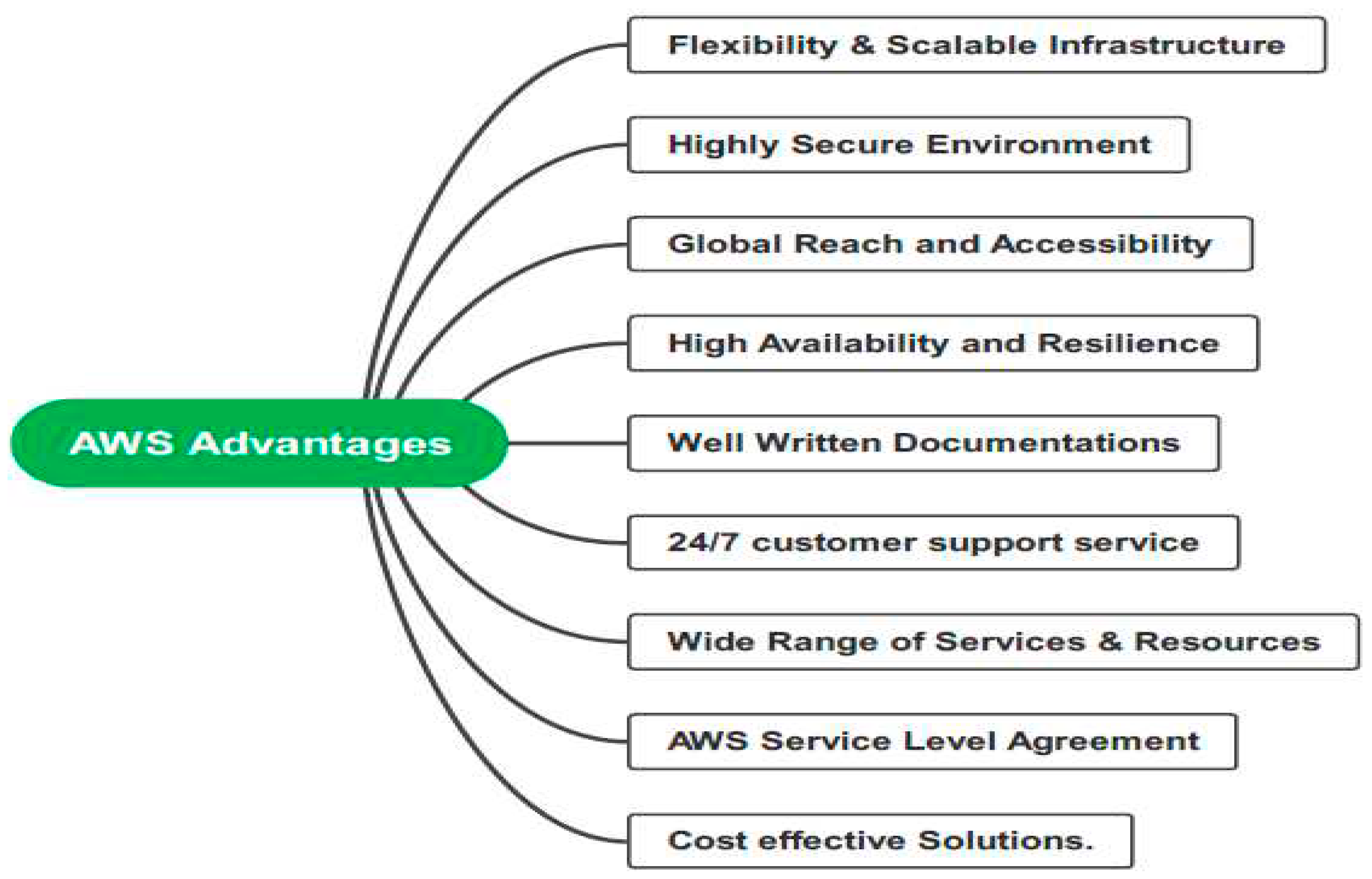
3. Amazon Web Services: An Appropriate Cloud Computing Solution
- a)
- Flexible and Scalable Infrastructure
- b)
- Highly Secure Environment
- c)
- Global Reach and Accessibility
- d)
- High Availability and Resilience
- e)
- Well Written Documentations
- f)
- 24/7 customer support service
- g)
- Wide Range of Services & Resources
- h)
- AWS Service Level Agreement
- i)
- Cost effective Solutions.
3.1. AWS merger with SDN - Data Security with Improved Performance
4. Conclusion
References
- Z. R. Alashhab, M. Anbar, M. M. Singh, Y. B. Leau, Z. A. Al-Sai, and S. A. Alhayja’a, “Impact of Coronavirus Pandemic Crisis on Technologies and Cloud Computing Applications,” J. Electron. Sci. Technol., vol. 19, no. 1, pp. 25–40, 2021. [CrossRef]
- “Message from Flexera.” https://www.flexera.com/about-us/press-center/flexera-releases-2021-state-of-the-cloud-report (accessed Jul. 17, 2023).
- “What is 5G? | Everything You Need to Know | 5G FAQ | Qualcomm.” https://www.qualcomm.com/5g/what-is-5g (accessed Jul. 17, 2023).
- A. Maria, I. Nazurl, and J. NZ, “A Lightweight and Secure Authentication Scheme for IoT Based E-Health Application,” Int. J. Comput. Sci. Netw. Secur., vol. 19, no. 1, pp. 107–120, 2019.
- S. Ali et al., “Towards Pattern-Based Change Verification Framework for Cloud-Enabled Healthcare Component-Based,” IEEE Access, vol. 8, pp. 148007–148020, 2020. [CrossRef]
- S. A. Bello et al., “Cloud computing in construction industry: Use cases, benefits and challenges,” Autom. Constr., vol. 122, p. 103441, 2021. [CrossRef]
- “Cloud data migration | Accenture.” https://www.accenture.com/us-en/insights/technology/cloud-data-migration (accessed Jul. 17, 2023).
- D. A. Shafiq, N. Z. Jhanjhi, A. Abdullah, and M. A. Alzain, “A Load Balancing Algorithm for the Data Centres to Optimize Cloud Computing Applications,” IEEE Access, vol. 9, pp. 41731–41744, 2021. [CrossRef]
- R. Amin and S. Vadlamudi, “Opportunities and Challenges of Data Migration in Cloud,” Eng. Int., vol. 9, no. 1, pp. 41–50, 2021. [CrossRef]
- “Anticipated decreases in companies’ IT budget 2020 | Statista.” https://www.statista.com/statistics/1132047/it-budget-decrease-worldwide-2020/ (accessed Jul. 17, 2023).
- P. H. B. Patel and P. N. Kansara, “Cloud Computing Deployment Models: A Comparative Study,” Int. J. Innov. Res. Comput. Sci. Technol., vol. 9, no. 2, pp. 45–50, 2021. [CrossRef]
- A. Rashid and A. Chaturvedi, “Cloud Computing Characteristics and Services A Brief Review,” Int. J. Comput. Sci. Eng., vol. 7, no. 2, pp. 421–426, 2019. [CrossRef]
- “Benefits of IaaS | Infrastructure as a Service | Dataprise.” https://www.dataprise.com/resources/blog/iaas-benefits/ (accessed Jul. 24, 2023).
- M. Gopala and K. Sriram, “Challenges of Cloud Compute Load Balancing Algorithms,” www.irjmets.com @International Res. J. Mod. Eng., no. 1, pp. 1186–1190, 2022, [Online]. Available: www.irjmets.com.
- Z. A. Almusaylim and N. Jhanjhi, “Comprehensive Review: Privacy Protection of User in Location-Aware Services of Mobile Cloud Computing,” Wirel. Pers. Commun., vol. 111, no. 1, pp. 541–564, 2020. [CrossRef]
- P. Morawiec and A. Sołtysik-Piorunkiewicz, “Cloud Computing, Big Data, and Blockchain Technology Adoption in ERP Implementation Methodology,” Sustain., vol. 14, no. 7, 2022. [CrossRef]
- N. M. Gunturu, “A Framework for Successful Corporate Cloud Transformation,” Int. J. Comput. Trends Technol., vol. 70, no. 3, pp. 9–15, 2022. [CrossRef]
- “What Is Cloud Migration? What To Know Before Migrating.” https://www.cloudzero.com/blog/cloud-migration (accessed Jul. 17, 2023).
- “Google Cloud gains in Gartner’s 2019 cloud infrastructure Magic Quadrant | ZDNET.” https://www.zdnet.com/article/google-cloud-gains-in-gartners-2019-cloud-infrastructure-magic-quadrant/ (accessed Jul. 17, 2023).
- M. Snehi and A. Bhandari, “Vulnerability retrospection of security solutions for software-defined Cyber-Physical System against DDoS and IoT-DDoS attacks,” Comput. Sci. Rev., vol. 40, p. 100371, 2021. [CrossRef]
- “What is AWS.” https://aws.amazon.com/what-is-aws/ (accessed Jul. 17, 2023).
- “AWS Whitepaper-2023.pdf.”.
- “Application Integration on AWS - Amazon Web Services.” https://aws.amazon.com/products/application-integration/ (accessed Jul. 17, 2023).
- “AWS Support Plan Comparison | Developer, Business, Enterprise, Enterprise On-Ramp | AWS Support.” https://aws.amazon.com/premiumsupport/plans/ (accessed Jul. 17, 2023).
- “AWS Migration Acceleration Program (MAP) – Amazon Web Services.” https://aws.amazon.com/migration-acceleration-program/ (accessed Jul. 17, 2023).
- “Why Migrating to AWS? (Technical Blog Series) – transACT Technology Solutions.” https://transactts.com/why-migrate-to-aws/ (accessed Jul. 17, 2023).
- “Amazon Compute Service Level Agreement.” https://aws.amazon.com/compute/sla/ (accessed Jul. 17, 2023).
- S. Muzafar and N. Jhanjhi, “DDoS Attacks on Software Defined Network: Challenges and Issues,” 2022 Int. Conf. Bus. Anal. Technol. Secur. ICBATS 2022, vol. 2022-Janua, 2022. [CrossRef]
- S. Badotra et al., “A DDoS Vulnerability Analysis System against Distributed SDN Controllers in a Cloud Computing Environment,” Electron., vol. 11, no. 19, pp. 1–15, 2022. [CrossRef]
- S. Muzafar, N. Z. Jhanjhi, N. A. Khan, and F. Ashfaq, “DDoS Attack Detection Approaches in on Software Defined Network,” 14th Int. Conf. Math. Actuar. Sci. Comput. Sci. Stat. MACS 2022, 2022. [CrossRef]
- Priyadarshini, I., Chatterjee, J. M., Sujatha, R., Jhanjhi, N., Karime, A., & Masud, M. (2022). Exploring internet meme activity during COVID-19 lockdown using Artificial Intelligence techniques. Applied Artificial Intelligence, 36(1), 2014218. [CrossRef]
- Muzammal, S. M., Murugesan, R. K., Jhanjhi, N. Z., Hossain, M. S., & Yassine, A. (2022). Trust and Mobility-Based Protocol for Secure Routing in Internet of Things. Sensors, 22(16), 6215. [CrossRef]
- Basavaraju, P. H., Lokesh, G. H., Mohan, G., Jhanjhi, N. Z., & Flammini, F. (2022). Statistical channel model and systematic random linear network coding based qos oriented and energy efficient uwsn routing protocol. Electronics, 11(16), 2590. [CrossRef]
- Muthukkumar, R., Garg, L., Maharajan, K., Jayalakshmi, M., Jhanjhi, N., Parthiban, S., & Saritha, G. (2022). A genetic algorithm-based energy-aware multi-hop clustering scheme for heterogeneous wireless sensor networks. PeerJ Computer Science, 8, e1029. [CrossRef]
- Sharma, U., Nand, P., Chatterjee, J. M., Jain, V., Jhanjhi, N. Z., & Sujatha, R. (Eds.). (2022). Cyber-Physical Systems: Foundations and Techniques. John Wiley & Sons.
- Anandan, R., Gopalakrishnan, S., Pal, S., & Zaman, N. (Eds.). (2022). Industrial Internet of Things (IIoT): Intelligent Analytics for Predictive Maintenance. John Wiley & Sons.
- Zaman, N., Gaur, L., & Humayun, M. (Eds.). (2022). Approaches and Applications of Deep Learning in Virtual Medical Care. IGI Global. [CrossRef]
- Gandam, A., Sidhu, J. S., Verma, S., Jhanjhi, N. Z., Nayyar, A., Abouhawwash, M., & Nam, Y. (2021). An efficient post-processing adaptive filtering technique to rectifying the flickering effects. PLoS One, 16(5), e0250959. [CrossRef]
- Talwani, S., Singla, J., Mathur, G., Malik, N., Jhanjhi, N. Z., Masud, M., & Aljahdali, S. (2022). Machine-Learning-Based Approach for Virtual Machine Allocation and Migration. Electronics, 11(19), 3249. [CrossRef]
- Muzammal, S. M., Murugesan, R. K., & Jhanjhi, N. Z. (2021, March). Introducing mobility metrics in trust-based security of routing protocol for internet of things. In 2021 National Computing Colleges Conference (NCCC) (pp. 1-5). IEEE. [CrossRef]
- Hafeez, Y., Ali, S., Jhanjhi, N., Humayun, M., Nayyar, A., & Masud, M. (2021). Role of Fuzzy Approach towards Fault Detection for Distributed Components. Computers, Materials & Continua, 67(2). [CrossRef]
- Jhanjhi, N. Z., Almusalli, F. A., Brohi, S. N., & Abdullah, A. (2018, October). Middleware power saving scheme for mobile applications. In 2018 Fourth International Conference on Advances in Computing, Communication & Automation (ICACCA) (pp. 1-6). IEEE. [CrossRef]
- Kumar, T., Pandey, B., Mussavi, S. H. A., & Zaman, N. (2015). CTHS based energy efficient thermal aware image ALU design on FPGA. Wireless Personal Communications, 85, 671-696. [CrossRef]
- Adeyemo, V. E., Abdullah, A., JhanJhi, N. Z., Supramaniam, M., & Balogun, A. O. (2019). Ensemble and deep-learning methods for two-class and multi-attack anomaly intrusion detection: an empirical study. International Journal of Advanced Computer Science and Applications, 10(9). [CrossRef]
- Khalil, M. I., Jhanjhi, N. Z., Humayun, M., Sivanesan, S., Masud, M., & Hossain, M. S. (2021). Hybrid smart grid with sustainable energy efficient resources for smart cities. sustainable energy technologies and assessments, 46, 101211. [CrossRef]
- Sennan, S., Somula, R., Luhach, A. K., Deverajan, G. G., Alnumay, W., Jhanjhi, N. Z., ... & Sharma, P. (2021). Energy efficient optimal parent selection based routing protocol for Internet of Things using firefly optimization algorithm. Transactions on Emerging Telecommunications Technologies, 32(8), e4171. [CrossRef]
- Kok, S. H., Abdullah, A., & Jhanjhi, N. Z. (2022). Early detection of crypto-ransomware using pre-encryption detection algorithm. Journal of King Saud University-Computer and Information Sciences, 34(5), 1984-1999. [CrossRef]
- Verma, S., Kaur, S., Rawat, D. B., Xi, C., Alex, L. T., & Jhanjhi, N. Z. (2021). Intelligent framework using IoT-based WSNs for wildfire detection. IEEE Access, 9, 48185-48196. [CrossRef]
- Hussain, K., Hussain, S. J., Jhanjhi, N. Z., & Humayun, M. (2019, April). SYN flood attack detection based on bayes estimator (SFADBE) for MANET. In 2019 International Conference on Computer and Information Sciences (ICCIS) (pp. 1-4). IEEE. [CrossRef]
- Gaur, L., Afaq, A., Solanki, A., Singh, G., Sharma, S., Jhanjhi, N. Z., & Hoang, M. & Le, DN (2021). Capitalizing on big data and revolutionary 5G technology: Extracting and visualizing ratings and reviews of global chain hotels. Computers and Electrical Engineering, 95, 107374. [CrossRef]
- Gaur, L., Singh, G., Solanki, A., Jhanjhi, N. Z., Bhatia, U., & Sharma, S. & Kim, W.(2021). Disposition of youth in predicting sustainable development goals using the neuro-fuzzy and random forest algorithms. Human-Centric Computing and Information Sciences, 11. [CrossRef]
- Almusaylim, A. Z., Jhanjhi, NZ, & Alhumam, A.(2020). Detection and mitigation of RPL rank and version number attacks in the internet of things: SRPL-RP. Sensors, 20(21), 5997. [CrossRef]
- Alsaade, F., Zaman, N., Hassan, M. F., and Abdullah, A. 2014. “An Improved Software Development Process for Small and Medium Software Development Enterprises Based on Client’s Perspective,” Trends in Applied Sciences Research (9:5), pp. 254–261. [CrossRef]
- Hamid, B., Jhanjhi, N. Z., & Humayun, M. (2020). Digital Governance for Developing Countries Opportunities, Issues, and Challenges in Pakistan. In Employing Recent Technologies for Improved Digital Governance (pp. 36-58). IGI Global. [CrossRef]
- Sangkaran, T., Abdullah, A., & JhanJhi, N. Z. (2020). Criminal network community detection using graphical analytic methods: A survey. EAI Endorsed Transactions on Energy Web, 7(26), e5-e5. [CrossRef]
- Bashir, I. R. A. M., Hamid, B. U. S. H. R. A., Jhanjhi, N. Z., & Humayun, M. A. M. O. O. N. A. (2020). Systematic literature review and empirical study for success factors: client and vendor perspective. J Eng Sci Technol, 15(4), 2781-2808.
- Alayda, S., Almowaysher, N. A., Humayun, M., & Jhanjhi, N. (2020). A novel hybrid approach for access control in cloud computing. Int. J. Eng. Res. Technol, 13(11), 3404-3414. [CrossRef]
- Srivastava, A., Verma, S., Jhanjhi, N. Z., Talib, M. N., & Malhotra, A. (2020, December). Analysis of Quality of Service in VANET. In IOP Conference Series: Materials Science and Engineering (Vol. 993, No. 1, p. 012061). IOP Publishing. [CrossRef]
- Lee, S., Abdullah, A., Jhanjhi, N. Z., & Kok, S. H. (2021). Honeypot Coupled Machine Learning Model for Botnet Detection and Classification in IoT Smart Factory–An Investigation. In MATEC Web of Conferences (Vol. 335, p. 04003). EDP Sciences. [CrossRef]
- Kaur, M., Singh, A., Verma, S., Kavita, Jhanjhi, N. Z., & Talib, M. N. (2021). FANET: Efficient routing in flying ad hoc networks (FANETs) using firefly algorithm. In Intelligent Computing and Innovation on Data Science: Proceedings of ICTIDS 2021 (pp. 483-490). Springer Singapore. [CrossRef]
- Nawaz, A. (2021). Feature engineering based on hybrid features for malware detection over Android framework. Turkish Journal of Computer and Mathematics Education (TURCOMAT), 12(10), 2856-2864.
- Ali, A. B. A., Ponnusamy, V., Sangodiah, A., Alroobaea, R., Jhanjhi, N. Z., Ghosh, U., & Masud, M. (2021). Smartphone security using swipe behavior-based authentication. Intelligent Automation & Soft Computing, 29(2), 571-585. [CrossRef]
- Shanmuganathan, V., Yesudhas, H. R., Madasamy, K., Alaboudi, A. A., Luhach, A. K., & Jhanjhi, N. Z. (2021). AI based forecasting of influenza patterns from twitter information using random forest algorithm. Hum. Cent. Comput. Inf. Sci, 11, 33. [CrossRef]
- Teoh, A. A., Ghani, N. B. A., Ahmad, M., Jhanjhi, N., Alzain, M. A., & Masud, M. (2022). Organizational Data Breach: Building Conscious Care Behavior in Incident. Organizational data breach: Building conscious care behavior in incident response. Computer Systems Science and Engineering, 40(2), 505-515. [CrossRef]
- Hussain, I., Tahir, S., Humayun, M., Almufareh, M. F., Jhanjhi, N. Z., & Qamar, F. (2022, November). Health monitoring system using internet of things (iot) sensing for elderly people. In 2022 14th International Conference on Mathematics, Actuarial Science, Computer Science and Statistics (MACS) (pp. 1-5). IEEE. [CrossRef]
- Jena, K. K., Bhoi, S. K., Malik, T. K., Sahoo, K. S., Jhanjhi, N. Z., Bhatia, S., & Amsaad, F. (2022). E-Learning Course Recommender System Using Collaborative Filtering Models. Electronics, 12(1), 157. [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).



