Submitted:
09 November 2023
Posted:
09 November 2023
You are already at the latest version
Abstract
Keywords:
Introduction
Definition of Wireless Technology
Application Of Wireless Technology and Its Benefits
Importance of Protecting Wireless Technology
Scope of the Paper
Related Research Background
- A)
- Security and Privacy Issues of Wireless Networks
- I.
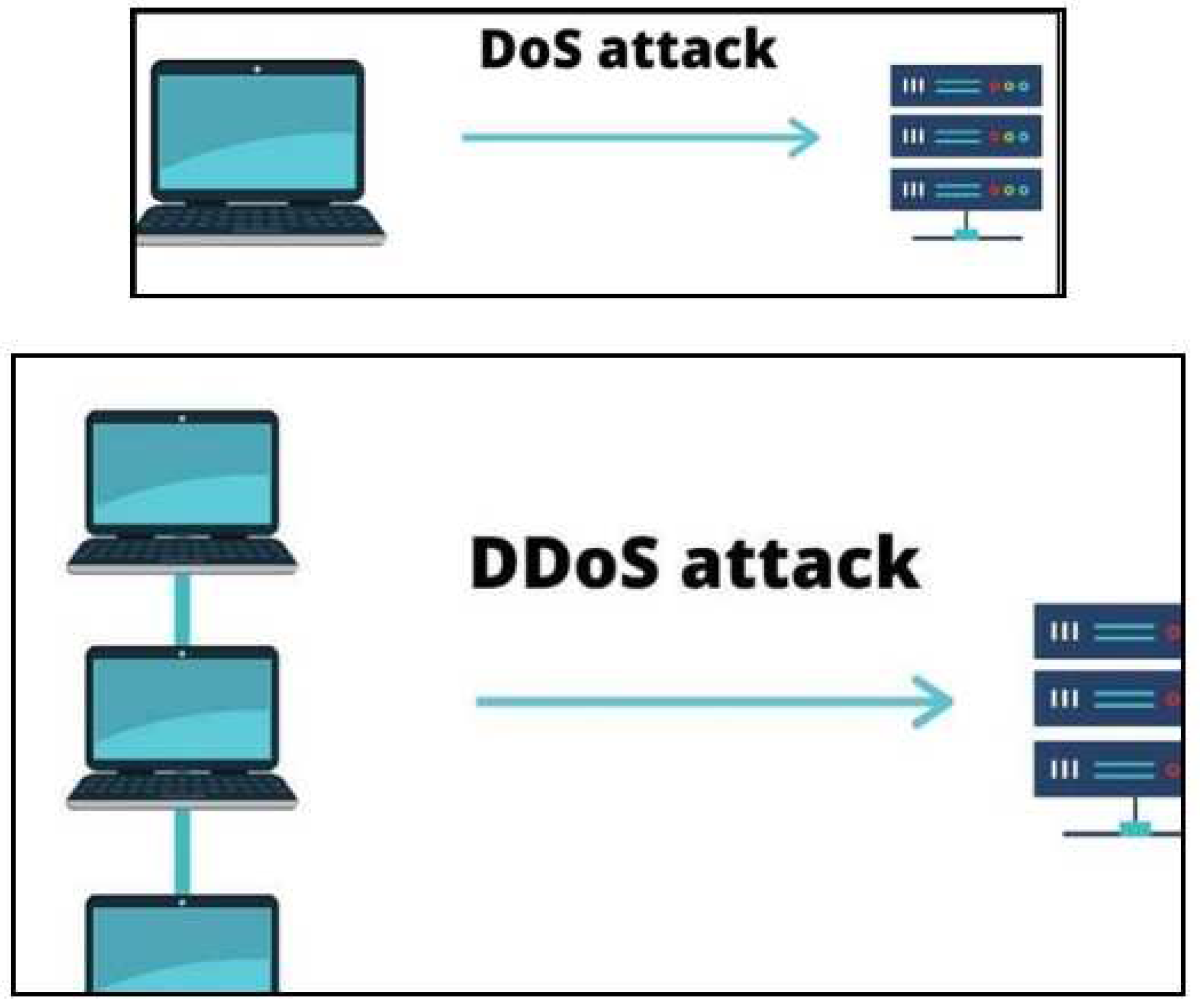
- Denial of Service (DoS)
| Victim | Year | Severity | Description of DDoS/DoS Attack |
|---|---|---|---|
| Amazon | 2020 | 2.3 Tbps*, world’s largestDDoS Attack in record. |
In February 2020, AWS was targeted by its own customer where they launched a full-scale DDoS attack against AWS. The transmission speed of the attack had reached a new record of the previous DDoS attacks. Luckily AWS’ intrusion prevention system known as AWS Shield had automatically intercepted the attack and prevented the largest system down ever from happening. |
| GitHub | 2018 | 1.3 Tbps*, recorded third largestDDoS attacks. Where includes shocking 126.9Million of packets per second. |
In February 2018, GitHub suffered a DDoS attack and caused a 20-minute of downtime. According to the IPS report, the recorded speed of the attack is 1.3 Terabytes per second and up to 127 million of internet packets were sent every second. |
| GitHub | 2018 | 1.7 Tbps*, the second largestscale of DDoS recorded past. | 2018 is not a good year for GitHub as they suffered another DDoS attack within a month after the last DDoS attack. The source of the attack is from a client that is hosted by a network company called NETSCOUT. And thanks to the reliable IPS of GitHub, the severity of the DDoS has been mitigated. |
| BBC | 2015 | 600 Gbps**, biggest DDoS attack recorded in 2015. And longest service downtime. |
In December 2015, the pioneer news broadcasting company BBC suffered a DDoS attack from a group of hackers called the “New World Hacking”. A speed of 600 Gigabytes per second attack was launched and caused BBC a shocking 3 hours of downtime. And the attack was launched by using a system pressure testing tool known as “BangStresser”. |
- II.
- Piggybacking and Wardriving
- III.
- Spoofing and Keylogging
- IV.
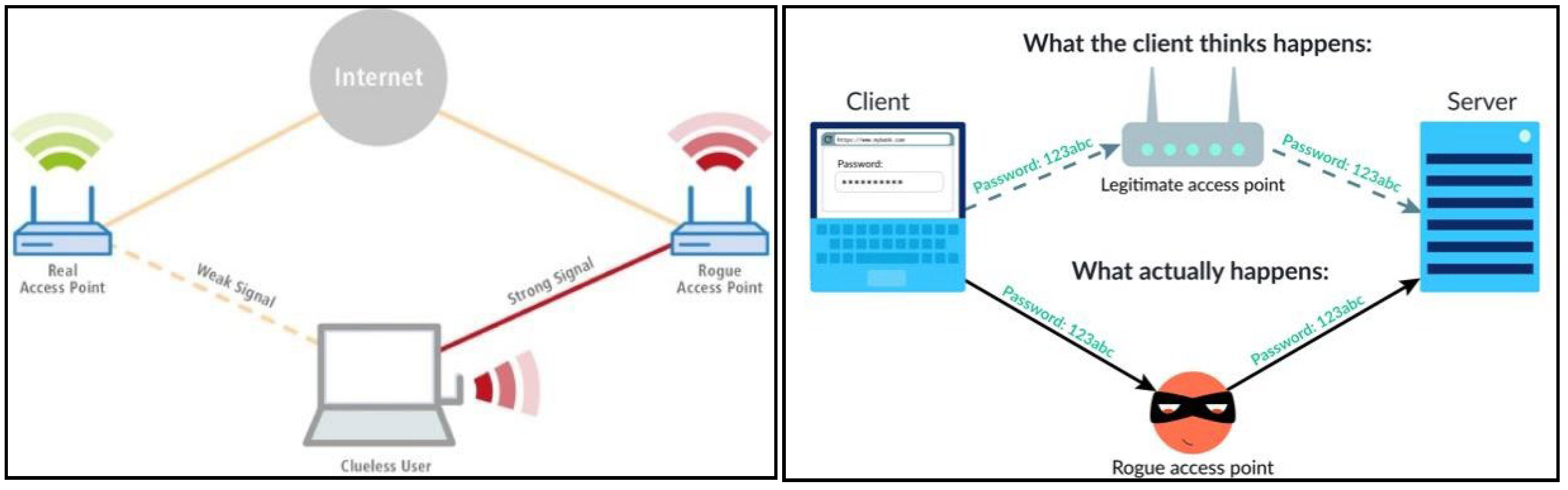
- Rogue Access Points
- B)
- Privacy Issues in Wireless Network
- I.
- Identity Theft
- II.
- Data Breach
| Company | Year | Affected | Description |
|---|---|---|---|
| Yahoo! | 2013-14 | 3B accounts |
In September 2016, Yahoo revealed the company's largest data breach to date. All of the email addresses were taken, along with their true names, phone numbers, passwords, and birth dates. |
| 2012 & 2016 |
165M accounts |
LinkedIn stated that the credentials of 165 million members were stolen and exposed on a Russian hacker website. The information was sold for only 5-bit coins (almost $2000) by the hacker. LinkedIn had finally reset all of the account passwords. |
|
| Zynga | 2019 | 218M accounts |
A Pakistani hacker claimed to have hacked the accounts of all 218 million players. Later, Zynga admitted that all user information, including user ids and passwords, had been taken. This entire event took place entirely on the Facebook gaming platform. |
| Adobe | 2013 | 153M accounts |
Hackers acquired over 150 million user login credentials, credit card records, and company data bases. As a result, Adobe agreed to pay $1 million to customers for breaching the Customer Records Act. |
- III.
- Eavesdropping
- IV.
- Phishing
- 1.
- Email Phishing: This is the most prevalent form of phishing, wherein attackers send rushed emails to victims, often claiming that their accounts have been compromised and urging immediate action. The goal is to trick victims into performing specific actions, such as clicking on malicious links that lead to fake login pages. When victims enter their credentials, their personal information is transmitted to the attackers [46].
- 2.
- Spear Phishing: This type of phishing necessitates thorough research to gather information about the victim. The research might involve gathering data from social media, such as the victim's name, friends, and locations. Armed with this information, attackers pose as a trusted contact and attempt to obtain confidential information through email or other messaging tools [46].
- 3.
- Evil Twin Phishing: In this type of phishing, attackers set up a counterfeit Wi-Fi network that directs users to a phishing site when they connect to it. Once on the phishing site, victims are prompted to provide personal information, including login credentials. With access to these credentials, attackers can infiltrate the network, monitor unencrypted traffic, and devise strategies to steal valuable data or information [47].
- 4.
- Clone Phishing: This form of phishing involves using a genuine email to create a nearly identical email that is then sent from a spoofed email account closely resembling the original sender. Links in the email are typically replaced with malicious ones. Since it replicates an existing email, clone phishing stands out from other forms of phishing due to its higher precision [48].
| Ref No |
Year | Domain | Description |
|---|---|---|---|
| [33] | 2017 | Identity Theft | Discusses the identity theft detection in the mobile social networks |
| [34] | 2016 | Identity Theft | Discusses the process of discovering identity theft in wireless networks |
| [35] | 2019 | Identity Theft | Discusses the type of identity theft and the protection strategies |
| [36] | 2018 | Data Breach | Discusses the analysis and visualization of a data breach, including the insights |
| [37] | 2021 | Data Breach | Discusses the Wi-Fi risks and the data breach, along with the measures to tackle the incident |
| [38] | 2019 | Data Breach | Discusses the analysis of issues in the data breach notification |
| [39] | 2018 | Eavesdropping | Discusses the issues in the mobile wireless networks, including the brief analysis of the issues |
| [40] | 2016 | Eavesdropping | Discusses the eavesdropping attack as a major threat in the wireless networks |
| [41] | 2017 | Eavesdropping | Discusses the protection in the eavesdropping attack using a novel anti-eavesdropping scheme |
| [42] | 2018 | Phishing | Discusses the phishing as a major threat, the challenges, and the solution |
| [43] | 2021 | Phishing | Discusses the phishing acts as an attack to hack wireless networks credentials |
| [44] | 2018 | Phishing | Discusses the detection of phishing, how to differentiate between real email and phishing email |
| [45] | 2020 | Phishing | Discusses the benchmarking and evaluation of detecting the phishing |
| [46] | 2019 | Phishing | Discusses the overview of phishing, along with the types and the countermeasures strategy |
| [47] | 2021 | Phishing | Discusses the review of a phishing attack in the internet of things as well as the countermeasures of the attack |
| [48] | 2019 | Phishing | Discusses the phishing attack in the blockchain projects as well as the protection of the attack |
Research Methodology
- A.
- Research questions
- Search strategy
- 1.
- Keywords
- 2.
- Search documentation and Selection of sources
- 3.
- Inclusion and exclusion criteria
- a.
- Inclusion criteria
- i.
- The research paper must be published during or after the year 2016.
- ii.
- Only papers written in the English language are included.
- iii.
- Publications relevant to the discussion topic were considered.
- b.
- Exclusion criteria
- i.
- All publications before 2016 are excluded.
- ii.
- All papers that do not answer any of the research questions have been excluded.
- iii.
- Papers with less than four pages of length were excluded.
- 4.
- In-Depth Discussion and Summary
- 5.
- Unique solution for the issues/challenges
Conclusion
References
- L. Chen et al., A Survey: Machine Learning Based Security Analytics Approaches and Applications of Blockchain in Network Security, 1st ed. IEEE, 2020, pp. 17-21. [Accessed 14 November 2021].
- A. Kavianpour and M. Anderson, An Overview of Wireless Network Security, 1st ed. IEEE, 2017, pp. 306-309. [Accessed 14 November 2021].
- D. Da Costa and H. Yang, Grand Challenges in Wireless Communications, 1st ed. Frontiers in Communications and Networks, 2020, pp. 1-4. [Accessed 14 November 2021].
- PERCEPTIONS AND ATTITUDES OF CANADIAN ORGANIZATIONS TOWARD CYBERSECURITY, 1st ed. The Strategic Counsel, 2021, pp. 6-62. [Accessed 14 November 2021].
- "A Construction Company Gets Hammered by A Keylogger", NIST, 2020. [Online]. Available: https://www.nist.gov/system/files/documents/2020/09/30/Cybersecurity-Case-2.pdf. [Accessed 14 November 2021].
- D. Winder, "Zoom Gets Stuffed: Here’s How Hackers Got Hold Of 500,000 Passwords", Forbes, 2020. [Online]. Available: https://www.forbes.com/sites/daveywinder/2020/04/28/zoom- gets-stuffed-heres-how-hackers-got-hold-of-500000-passwords/?sh=8d943235cdc4. [Accessed: 14- Nov- 2021].
- A. Ioannou, I. Tussyadiah, G. Miller, S. Li, and M. Weick, “Privacy nudges for disclosure of personal information: A systematic literature review and meta-analysis,” PLOS ONE, vol. 16, no. 8, p. e0256822, Aug. 2021. [Accessed 14 November 2021]. [CrossRef]
- A. Algarni, “A Survey and Classification of Security and Privacy Research in Smart Healthcare Systems,” IEEE Access, vol. 7, pp. 101879–101894, 2019. [Accessed 14 November 2021]. [CrossRef]
- J. Legrand, "The Future Use Cases of Blockchain for Cybersecurity", Cm-alliance.com, 2020. [Online]. Available: https://www.cm-alliance.com/cybersecurity-blog/the-future-use-cases-of- blockchain-for-cybersecurity. [Accessed: 14- Nov- 2021].
- S. SINGH, "Potential Use Cases of Blockchain Technology for Cybersecurity | ITBE", IT Business Edge, 2021. [Online]. Available: https://www.itbusinessedge.com/security/potential- use-cases-of-blockchain-technology-for-cybersecurity/. [Accessed: 14- Nov- 2021].
- "The 2020 Official Annual Cybercrime Report - Herjavec Group", Herjavec Group, 2020. [Online]. Available: https://www.herjavecgroup.com/the-2019-official-annual-cybercrime-report/. [Accessed: 14- Nov- 2021].
- A. Moncur-Beer, "TikTok: the impact it has on our society | Glebe Report", Glebereport.ca, 2021. [Online]. Available: https://www.glebereport.ca/tiktok-the-impact-it-has-on-our-society/. [Accessed: 14- Nov- 2021].
- J. Ioannidis and S. Steven, "Implementing Pushback: Router-Based Defense Against DDoS Attacks", Network and Distributed System Security Symposium: NDSS '02, 2021 [Accessed 17 November 2021].
- P. Henry and Hui Luo, "WiFi: what's next?", IEEE Communications Magazine, vol. 40, no. 12, pp. 66-72, 2016. Available: 10.1109/mcom.2002.1106162 [Accessed 17 November 2021].
- R. Deshmukh and K. Devadkar, "Understanding DDoS Attack & its Effect in Cloud Environment", Procedia Computer Science, vol. 49, pp. 202-210, 2016. Available: 10.1016/j.procs.2015.04.245 [Accessed 17 November 2021].
- C. Zhang, "Impact of Defending Strategy Decision on DDoS Attack", Complexity, vol. 2021, pp. 1-11, 2021. Available: 10.1155/2021/6694383 [Accessed 17 November 2021].
- S. Zargar, J. Joshi and D. Tipper, "A Survey of Defense Mechanisms Against Distributed Denial of Service (DDoS) Flooding Attacks", IEEE Communications Surveys & Tutorials, vol. 15, no. 4, pp. 2046-2069, 2018. Available: 10.1109/surv.2013.031413.00127 [Accessed 15 November 2021].
- R. Rahim, H. Nurdiyanto, A. Saleh A, D. Abdullah, D. Hartama and D. Napitupulu, "Keylogger Application to Monitoring Users Activity with Exact String Matching Algorithm", Journal of Physics: Conference Series, vol. 954, p. 012008, 2018. Available: 10.1088/1742-6596/954/1/012008 [Accessed 17 November 2021].
- Venkatesh R. and Sekhar R. K. User Activity Monitoring Using Keylogger Asia Journal of Information Technology 15 4758-4762. 2017. [Accessed 15 November 2021].
- A. Sodiya, O. Folorunso, P. Komolafe and O. Ogunderu, "Preventing Authentication Systems From Keylogging Attack", Journal of Information Privacy and Security, vol. 7, no. 2, pp. 3-27, 2016. [Accessed 15 November 2021].
- S. Shinde and U. Wanaskar, "Keylogging: A Malicious Attack", International Journal of Advanced Research in Computer and Communication Engineering, vol. 5, no. 6, pp. 285-289, 2021 [Accessed 16 November 2021].
- S. Sagiroglu and G. Canbek, "Keyloggers", IEEE Technology and Society Magazine, vol. 28, no. 3, pp. 10- 17, 2016. Available: 10.1109/mts.2009.934159 [Accessed 17 November 2021].
- P. Ramesh, D. Bhaskari and C. -, "A Comprehensive Analysis of Spoofing", International Journal of Advanced Computer Science and Applications, vol. 1, no. 6, 2016. Available: 10.14569/ijacsa.2010.010623 [Accessed 17 November 2021].
- Lee. E, “WiFi Piggybacking – Is It Legal?”, Lee & Poh Partnetship. 2019. Available: https://lpplaw.my/wifi-piggybacking-is-it-legal-2/. [Accessed 15 November 2021].
- G. Guillot, Trespassing Through Cyberspace: Should Wireless Piggybacking Constitute a Crime or Tort Under Louisiana Law?, 69 La. L. Rev. (2009). Available: https://digitalcommons.law.lsu.edu/lalrev/vol69/iss2/6. [Accessed 15 November 2021].
- H. Lee, J. Kim and S. Cho, "A Delay-Based Piggyback Scheme in IEEE 802.11", 2017 IEEE Wireless Communications and Networking Conference, 2017. Available: 10.1109/wcnc.2007.87 [Accessed 17 November 2021].
- S. Kaul, R. Yates and M. Gruteser, "On Piggybacking in Vehicular Networks", 2011 IEEE Global Telecommunications Conference - GLOBECOM 2016, 2016. Available: 10.1109/glocom.2011.6134181 [Accessed 15 November 2021].
- N. Chandler and W. Fenlon, "How to Detect if Someone's Stealing Your WiFi" (2017). HowStuffWorks.com. Available: https://electronics.howstuffworks.com/how-to-tech/how-to- detect-stealing-wifi.htm. [Accessed 15 November 2021].
- P. Sapiezynski, R. Gatej, A. Mislove, and S. Lehmann. Opportunities and Challenges in Crowdsourced Wardriving. CCS.NEU.edu, 2016 [Accessed 15 November 2021].
- R. Jang, J. Kang, A. Mohaisen and D. Nyang, "Catch Me If You Can: Rogue Access Point Detection Using Intentional Channel Interference", IEEE Transactions on Mobile Computing, vol. 19, no. 5, pp. 1056-1071, 2020. Available: 10.1109/tmc.2019.2903052 [Accessed 17 November 2021].
- Y. Song, C. Yang and G. Gu, "Who is peeping at your passwords at Starbucks?; To catch an evil twin access point", 2010 IEEE/IFIP International Conference on Dependable Systems & Networks (DSN), 2010. Available: 10.1109/dsn.2010.5544302 [Accessed 15 November 2021].
- R. Beyah and A. Venkataraman, "Rogue-Access-Point Detection: Challenges, Solutions, and Future Directions", IEEE Security & Privacy Magazine, vol. 9, no. 5, pp. 56-61, 2016. Available: 10.1109/msp.2011.75. [Accessed 15 November 2021].
- C. Wang, B. Yang and J. Luo, "Identity Theft Detection in Mobile Social Networks Using Behavioral Semantics", IEEE International Conference on Smart Computing (SMARTCOMP), 2017. Available: 10.1109/smartcomp.2017.7947016 [Accessed 14 November 2021].
- D. Vivek and V. Persis, "Discovering Identity Theft (Spoofing) Using the Spatial Correlation of Received Signal Strength in Wireless Networks", International Journal and Magazine of Engineering, Technology, Management & Research, vol. 3, no. 6, pp. 527-532, 2016. [Accessed 13 November 2021].
- R. Labong, "Identity Theft Protection Strategies: A Literature Review", Journal of Academic Research, vol. 4, no. 2, pp. 1-12, 2019. [Accessed 14 November 2021].
- L. Liu, Y. Wang and Y. Zhou, "Understanding Data Breach: A Visualization Aspect", Lecture Notes in Computer Science, pp. 884-890, 2018. Available: 10.1007/978-3-319-94268-1_81 [Accessed 14 November 2021].
- R. Kamurthi, S. Chopra and R. Sharma, "Confrontation- Wi-Fi Risks and Data Breach", International Conference on Emerging Smart Computing and Informatics (ESCI), pp. 633-638, 2021. Available: 10.1109/esci50559.2021.939704 [Accessed 14 November 2021].
- Y. Zou, S. Danino, K. Sun and F. Schaub, "You ‘Might’ Be Affected: An Empirical Analysis of Readability and Usability Issues in Data Breach Notifications", CHI Conference on Human Factors in Computing Systems, vol. 194, pp. 1-14, 2019. Available: 10.1145/3290605.3300424 [Accessed 14 November 2021].
- S. Bendale and J. Prasad, "Security Threats and Challenges in Future Mobile Wireless Networks", Global Conference on Wireless Computing and Networking (GCWCN), pp. 146-150, 2018. Available: 10.1109/gcwcn.2018.8668635 [Accessed 13 November 2021].
- H. Dai, H. Wang, H. Xiao, X. Li and Q. Wang, "On Eavesdropping Attacks in Wireless Networks", IEEE International Conference on Computational Science and Engineering, pp. 138- 141, 2016. Available: 10.1109/cse-euc-dcabes.2016.173 [Accessed 13 November 2021].
- X. Li, H. Dai, Q. Wang and A. Vasilakos, "AE-Shelter: An Novel Anti-Eavesdropping Scheme in Wireless Networks", IEEE International Conference on Communications (ICC), 2017. Available: 10.1109/icc.2017.7996847 [Accessed 14 November 2021].
- I. Vayansky and S. Kumar, "Phishing – challenges and solutions", Computer Fraud & Security, vol. 2018, no. 1, pp. 15-20, 2018. Available: 10.1016/s1361-3723(18)30007-1 [Accessed 13 November 2021].
- H. Musthyala and N. Reddy, "Hacking wireless network credentials by performing phishing attack using Python Scripting", 5th International Conference on Intelligent Computing and Control Systems (ICICCS), pp. 248-253, 2021. Available: 10.1109/iciccs51141.2021.9432 [Accessed 13 November 2021].
- M. Baykara and Z. Gürel, "Detection of phishing attacks", 6th International Symposium on Digital Forensic and Security (ISDFS), 2018. Available: 10.1109/isdfs.2018.8355389 [Accessed 14 November 2021].
- A. El Aassal, S. Baki, A. Das and R. Verma, "An In-Depth Benchmarking and Evaluation of Phishing Detection Research for Security Needs", IEEE Access, vol. 8, pp. 22170-22192, 2020. Available: 10.1109/access.2020.2969780 [Accessed 14 November 2021].
- A. Muntode and S. Parwe, "An Overview on Phishing- its types and Countermeasures", International Journal of Engineering Research and, vol. 8, no. 12, pp. 545- 548, 2019. Available: 10.17577/ijertv8is120260 [Accessed 13 November 2021].
- A. Sadiq et al., "A review of phishing attacks and countermeasures for internet of things- based smart business applications in industry 4.0", Human Behavior and Emerging Technologies, pp. 1-11, 2021. Available: 10.1002/hbe2.301 [Accessed 14 November 2021].
- A. Andryukhin, "Phishing Attacks and Preventions in Blockchain Based Projects", International Conference on Engineering Technologies and Computer Science (EnT), pp. 15-19, 2019. Available: 10.1109/ent.2019.00008 [Accessed 14 November 2021].
- A. Hassan et al., “A Systematic Literature Review on the Security and Privacy of the Blockchain and Cryptocurrency,” Journal of Cyber Security, vol. 2, no. 1, pp. 1–17, 2020 [Accessed 16 November 2021].
- B. Liao, Y. Ali, S. Nazir, L. He and H. Khan, "Security Analysis of IoT Devices by Using Mobile Computing: A Systematic Literature Review", IEEE Access, vol. 8, pp. 120331-120350, 2020. Available: 10.1109/access.2020.3006358 [Accessed 17 November 2021].
- Q. JIANG and L. HOU, "Research on the Influence of Science and Technology Advancement and Social Progress on the Ideological and Political Education Work in Colleges and Universities", 4th International Conference on Humanities Science and Society Development, vol. 328, pp. 87-90, 2019. [Accessed 17 November 2021].
- A. Burg, A. Chattopadhyay and K. Lam, "Wireless Communication and Security Issues for Cyber–Physical Systems and the Internet-of-Things", Proceedings of the IEEE, vol. 106, no. 1, pp. 38-60, 2018. Available: 10.1109/jproc.2017.2780172 [Accessed 17 November 2021].
- S. Kabanda, M. Tanner and C. Kent, "Exploring SME cybersecurity practices in developing countries", Journal of Organizational Computing and Electronic Commerce, vol. 28, no. 3, pp. 269-282, 2018. Available: 10.1080/10919392.2018.1484598 [Accessed 17 November 2021].
- R. Rahim, H. Nurdiyanto, A. Saleh A, D. Abdullah, D. Hartama and D. Napitupulu, "Keylogger Application to Monitoring Users Activity with Exact String Matching Algorithm", Journal of Physics: Conference Series, vol. 954, p. 012008, 2018. Available: 10.1088/1742-6596/954/1/012008 [Accessed 17 November 2021].
- M. Ilayaraja, K. Shankar and G. Devika, "A Modified Symmetric Key Cryptography Method for Secure Data Transmission", International Journal of Pure and Applied Mathematics, vol. 116, no. 10, pp. 301-308, 2017. [Accessed 17 November 2021].
- B. Pranggono and A. Arabo, "COVID -19 pandemic cybersecurity issues", Internet Technology Letters, vol. 4, no. 2, 2020. Available: 10.1002/itl2.247 [Accessed 17 November 2021].
- C. Townsley, "Are businesses getting complacent when it comes to DDoS mitigation?", Network Security, vol. 2018, no. 6, pp. 6-9, 2018. Available: 10.1016/s1353- 4858(18)30054-0 [Accessed 17 November 2021].
- K. Okereafor and P. Manny, "UNDERSTANDING CYBERSECURITY CHALLENGES OF TELECOMMUTING AND VIDEO CONFERENCING APPLICATIONS IN THE COVID-19 PANDEMIC", International Journal in IT & Engineering (IJITE), vol. 8, no. 6, pp. 13-23, 2020 [Accessed 17 November 2021].
- B. Bhushan and G. Sahoo, "Recent Advances in Attacks, Technical Challenges, Vulnerabilities and Their Countermeasures in Wireless Sensor Networks", Wireless Personal Communications, vol. 98, no. 2, pp. 2037-2077, 2017. Available: 10.1007/s11277-017-4962-0 [Accessed 17 November 2021].
- L. Chettri and R. Bera, "A Comprehensive Survey on Internet of Things (IoT) Toward 5G Wireless Systems", IEEE Internet of Things Journal, vol. 7, no. 1, pp. 16-32, 2020. Available: 10.1109/jiot.2019.2948888 [Accessed 17 November 2021].
- Atzeni, D., Bacciu, D., Mazzei, D., & Prencipe, G. (2022). A Systematic Review of Wi-Fi and Machine Learning Integration with Topic Modeling Techniques. Sensors, 22(13), 4925. [Accessed 11 October 11, 2023]. [CrossRef]
- T. S. Rappaport et al., "Wireless Communications and Applications Above 100 GHz: Opportunities and Challenges for 6G and Beyond," in IEEE Access, vol. 7, pp. 78729-78757, 2019. [CrossRef]
- LaBrie, G. (2017). 6 Benefits of Wireless Networking + Wireless Networking Solutions. Wei.com. https://blog.wei.com/6-benefits-of-wireless-networking-wireless-networking-solutions.
- Rathod, T., Jadav, N. K., Alshehri, M. D., Tanwar, S., Sharma, R., Felseghi, R. A., & Raboaca, M. S. (2022). Blockchain for Future Wireless Networks: A Decade Survey. Sensors, 22(11), 4182. [CrossRef]
- S. Muzafar, N. Z. Jhanjhi, N. A. Khan, and F. Ashfaq, “DDOS attack detection approaches in on software defined network,” 2022 14th International Conference on Mathematics, Actuarial Science, Computer Science and Statistics (MACS), Nov. 2022. [CrossRef]
- S. Muzafar and N. Z. Jhanjhi, “DDoS attacks on software defined Network: Challenges and issues,” 2022 International Conference on Business Analytics for Technology and Security (ICBATS), Feb. 2022. [CrossRef]
- R. Gopi et al., “Enhanced method of ANN based model for detection of DDoS attacks on multimedia internet of things,” Multimedia Tools and Applications, vol. 81, no. 19, pp. 26739–26757, Feb. 2021. [CrossRef]
- S. J. Hussain, M. Irfan, N. Z. Jhanjhi, K. Hussain, and M. Humayun, “Performance Enhancement in Wireless Body Area Networks with Secure Communication,” Wireless Personal Communications, vol. 116, no. 1, pp. 1–22, Aug. 2020. [CrossRef]
- K. N. Kumar, S. Verma, Kavita, N. Z. Jhanjhi, and M. Talib, “A Survey of The Design and Security Mechanisms of The Wireless Networks and Mobile Ad-Hoc Networks,” IOP Conference Series, vol. 993, p. 012063, Dec. 2020. [CrossRef]
- V. Ponnusamy, L. T. Jung, T. Ramachandran, and N. Z. Jhanjhi, “Bio-inspired energy scavenging in wireless ad hoc network,” 2017 International Conference on Innovations in Electrical Engineering and Computational Technologies (ICIEECT), Apr. 2017. [CrossRef]
- V. Ponnusamy, N. Z. Jhanjhi, T. J. Low, and A. H. M. Amin, Biologically-Inspired Energy Harvesting through Wireless Sensor Technologies. 2016. [CrossRef]
- N. Z. Jhanjhi, L. T. Jung, and V. Ponnusamy, “Application of Self-Healing in wireless sensor network,” in Advances in environmental engineering and green technologies book series, 2016, pp. 217–233. [CrossRef]
- N. Z. Jhanjhi, T. J. Low, and T. A. Alghamdi, “Enhancing routing energy efficiency of Wireless Sensor Networks,” ICACT Transactions on Advanced Communications Technology, Jul. 2015. [CrossRef]
- T. Jabeen, I. Jabeen, H. Ashraf, N. Z. Jhanjhi, A. Yassine, and M. S. Hossain, “An intelligent healthcare system using IoT in wireless sensor network,” Sensors, vol. 23, no. 11, p. 5055, May 2023. [CrossRef]
- S. K. Chaurasiya, A. Biswas, A. Nayyar, N. Z. Jhanjhi, and R. Banerjee, “DEICA: A differential evolution-based improved clustering algorithm for IoT-based heterogeneous wireless sensor networks,” International Journal of Communication Systems, vol. 36, no. 5, Jan. 2023. [CrossRef]
- H. Ashraf, F. Khan, U. Ihsan, F. Al-Quayed, N. Z. Jhanjhi, and M. Humayun, “MABPD: Mobile Agent-Based Prevention and Black Hole Attack Detection in Wireless Sensor Networks,” 2023 International Conference on Business Analytics for Technology and Security (ICBATS), Mar. 2023. [CrossRef]
- M. U. Hanif et al., “AI-Based wormhole attack detection techniques in wireless sensor networks,” Electronics, vol. 11, no. 15, p. 2324, Jul. 2022. [CrossRef]
- Q. W. Ahmed et al., “AI-Based Resource Allocation Techniques in Wireless Sensor Internet of Things Networks in Energy Efficiency with Data Optimization,” Electronics, vol. 11, no. 13, p. 2071, Jul. 2022. [CrossRef]
- L. Dash et al., “A Data Aggregation Approach Exploiting Spatial and Temporal Correlation among Sensor Data in Wireless Sensor Networks,” Electronics, vol. 11, no. 7, p. 989, Mar. 2022. [CrossRef]
- M. S. Dawood, N. Z. Jhanjhi, A. R. Khan, and M. Salih, “Designing of energy efficient routing protocol for Wireless Sensor Network (WSN) Using Location Aware (LA) Algorithm,” Journal of Information & Communication Technology JICT, vol. 3, no. 2, p. 15, Jan. 2009, [Online]. Available: http://jms.ilmauniversity.edu.pk/index.php/JICT/article/view/583.
- V. Ponnusamy, Y. Aun, N. Z. Jhanjhi, M. Humayun, and M. F. Almufareh, “IoT wireless intrusion detection and network Traffic Analysis,” Computer Systems Science and Engineering, vol. 40, no. 3, pp. 865–879, Jan. 2022. [CrossRef]
- A. A. Teoh, N. B. A. Ghani, M. Ahmad, N. Z. Jhanjhi, M. A. AlZain, and M. Masud, “Organizational data breach: Building conscious care behavior in incident response,” Computer Systems Science and Engineering, vol. 40, no. 2, pp. 505–515, Jan. 2022. [CrossRef]
- A. A. Ubing, S. K. B. Jasmi, A. Abdullah, N. Z. Jhanjhi, and M. Supramaniam, “Phishing Website Detection: An Improved Accuracy through Feature Selection and Ensemble Learning,” International Journal of Advanced Computer Science and Applications, vol. 10, no. 1, Jan. 2019. [CrossRef]
- İ. Ali, N. Z. Jhanjhi, and A. Laraib, “Cybersecurity and blockchain usage in contemporary business,” in Advances in information security, privacy, and ethics book series, 2022, pp. 49–64. [CrossRef]
- A. Khan, N. Z. Jhanjhi, and M. Humayun, “The role of cybersecurity in smart cities,” in Chapman and Hall/CRC eBooks, 2022, pp. 195–208. [CrossRef]
- M. Humayun, N. Z. Jhanjhi, M. Talib, M. H. Shah, and G. Suseendran, “Cybersecurity for data science: issues, opportunities, and challenges,” in Lecture notes in networks and systems, 2021, pp. 435–444. [CrossRef]
- Adeyemo Victor Elijah, Azween Abdullah, NZ JhanJhi, Mahadevan Supramaniam and Balogun Abdullateef O, “Ensemble and Deep-Learning Methods for Two-Class and Multi-Attack Anomaly Intrusion Detection: An Empirical Study” International Journal of Advanced Computer Science and Applications (IJACSA), 10(9), 2019. [CrossRef]
- K. Hussain, S. J. Hussain, N. Jhanjhi and M. Humayun, "SYN Flood Attack Detection based on Bayes Estimator (SFADBE) For MANET," 2019 International Conference on Computer and Information Sciences (ICCIS), Sakaka, Saudi Arabia, 2019, pp. 1-4. [CrossRef]
- Gaur, L., Singh, G., Solanki, A., Jhanjhi, N. Z., Bhatia, U., Sharma, S., ... & Kim, W. (2021). Disposition of youth in predicting sustainable development goals using the neuro-fuzzy and random forest algorithms. Human-Centric Computing and Information Sciences, 11, NA.
- Kumar, T., Pandey, B., Mussavi, S. H. A., & Zaman, N. (2015). CTHS based energy efficient thermal aware image ALU design on FPGA. Wireless Personal Communications, 85, 671-696.
- Lim, M., Abdullah, A., & Jhanjhi, N. Z. (2021). Performance optimization of criminal network hidden link prediction model with deep reinforcement learning. Journal of King Saud University-Computer and Information Sciences, 33(10), 1202-1210.
- Gaur, L., Afaq, A., Solanki, A., Singh, G., Sharma, S., Jhanjhi, N. Z., ... & Le, D. N. (2021). Capitalizing on big data and revolutionary 5G technology: Extracting and visualizing ratings and reviews of global chain hotels. Computers and Electrical Engineering, 95, 107374.
- Gouda, W., Sama, N. U., Al-Waakid, G., Humayun, M., & Jhanjhi, N. Z. (2022, June). Detection of skin cancer based on skin lesion images using deep learning. In Healthcare (Vol. 10, No. 7, p. 1183). MDPI.
- Nanglia, S., Ahmad, M., Khan, F. A., & Jhanjhi, N. Z. (2022). An enhanced Predictive heterogeneous ensemble model for breast cancer prediction. Biomedical Signal Processing and Control, 72, 103279.
- Diwaker, C., Tomar, P., Solanki, A., Nayyar, A., Jhanjhi, N. Z., Abdullah, A., & Supramaniam, M. (2019). A new model for predicting component-based software reliability using soft computing. IEEE Access, 7, 147191-147203.
- Hussain, S. J., Ahmed, U., Liaquat, H., Mir, S., Jhanjhi, N. Z., & Humayun, M. (2019, April). IMIAD: intelligent malware identification for android platform. In 2019 International Conference on Computer and Information Sciences (ICCIS) (pp. 1-6). IEEE.
- Kok, S. H., Azween, A., & Jhanjhi, N. Z. (2020). Evaluation metric for crypto-ransomware detection using machine learning. Journal of Information Security and Applications, 55, 102646.
| Ref No |
Year | Threat | Description |
|---|---|---|---|
| [13] | 2016 | Denial of Service | Discusses the effects of Denial of Service attacks towards a network |
| [14] | 2017 | Denial of Service | Discusses the process and the requirements in order to launch a Denial of Service attack towards a wireless network |
| [15] | 2015 | Denial of Service | Discusses the how Wireless Networks act as a catalyst for Denial of Service attack |
| [16] | 2021 | Denial of Service | Discusses the how Wireless Networks act as a catalyst for Denial of Service attack |
| [17] | 2013 | Denial of Service | Discusses the wireless network types that are more vulnerable to Denial of Service attacks |
| [18] | 2015 | Keylogging | Discusses how Keylogging methods evolve from wired to wireless network connection. |
| [19] | 2015 | Keylogging | Discusses how Keylogging methods evolve from wired to wireless network connection. |
| [20] | 2011 | Keylogging | Discusses the method of Keylogging during an attack |
| [21] | 2017 | Keylogging | Discusses the information that are retrieved/stolen from the Keylogging attacks |
| [22] | 2009 | Keylogging | Discusses the information that are retrieved/stolen from the keylogging attacks and how wireless networks are making Keylogging easier |
| [23] | 2011 | Spoofing | Discusses the Wireless Network Connections that might be at risk of Spoofing Attacks |
| [24] | 2019 | Piggybacking | Discusses the legal aspects of Piggybacking an unknown wireless network |
| [25] | 2009 | Piggybacking | Discusses the legal aspects of Piggybacking an unknown wireless network |
| [16] | 2017 | Piggybacking | Discusses the reason on why is Piggybacking a thing and what are the reasons of Piggybacking |
| [17] | 2011 | Piggybacking & Wardriving | Discusses the similarities of Piggybacking and Wardriving and what kind of wireless network is potentially targeted |
| [28] | 2017 | Piggybacking & Wardriving |
Discusses on why are Public Networks more prone to Piggybacking and Wardriving |
| [29] | 2015 | Wardriving | Discusses the consequences if the wireless network security is not well-configurated |
| [30] | 2019 | Rogue Access Point | Discusses the similarities of Legitimate Wi-Fi network and the Rogue Access Point network and how they work in real-life |
| [31] | 2019 | Rogue Access Point | Discusses on how does a Rouge Access Point works and how attackers benefit from it |
| [32] | 2019 | Rogue Access Point | Discusses the consequences and other risks of Rogue Access Point |
| Research Question | Keywords |
|---|---|
| What are the security and privacy issues in wireless networks? |
“Security Issues” Wireless Networks” OR “Privacy Issues” Wireless Networks” |
| Security Issues | |
| What to know about Denial of Service or Distributed Denial of Service? |
“Denial of Service” |
| What to know about Wireless Piggybacking and Wardriving? |
“Piggybacking” AND “Wardriving” |
| What to know about Spoofing and Keylogging? | “Spoofing” AND “Keylogging” |
| What to know about Rogue Access Points? | “Rogue Access Points” |
| Privacy Issues | |
| What to know about Identity Theft? | “Identity Theft” |
| What to know about Data Breach? | “Data Breach” |
| What to know about Eavesdropping? | “Eavesdropping” |
| What to know about Phishing? | “Phishing” |
| Source | Date Accessed | # of results retrieved without filter | # of results with filter (by years) |
|---|---|---|---|
| Security Issues | |||
| Google Scholar | 15 Nov, 2021 | 28,039 | 17,648 |
| Semantics Scholar | 15 Nov, 2021 | 16,485 | 7,438 |
| IEEE Explore | 15 Nov, 2021 | 5,578 | 2,914 |
| Science Direct | 15 Nov, 2021 | 3,891 | 1,596 |
| Springer | 15 Nov, 2021 | 10,396 | 6,365 |
| Privacy Issues | |||
| IEEE Explore | 13 Nov, 2021 | 5,758 | 2,574 |
| Science Direct | 13 Nov, 2021 | 1,591 | 884 |
| Springer | 13 Nov, 2021 | 17,164 | 8,694 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





