Submitted:
12 October 2023
Posted:
17 October 2023
You are already at the latest version
Abstract
Keywords:
Introduction
Relevance of the subject
The aim of this study
- Which analytical approaches in the field of anomaly detection are the most developed in publications in the field of “Informatics and Mathematics” sciences?
- Which analytical approaches in the field of anomaly detection are most in demand in the oil and gas industry?
Literature review
Materials and Methods
Data
Clustering of bibliometric records
- First, the texts were subjected to stemming using the Krovetz method, which allowed the terms to be normalized while preserving their readability.
- A dictionary of normalized keywords was then compiled.
- Only terms from the above dictionary were kept in the ABSTRACT field.
- The original KEYWORDS and ABSTRACT fields in the bibliometric records were replaced with the transformed ones.
- The bibliometric data thus obtained were further used in the demo version of Carrot2.
Explanation of text preprocessing in progress
Search for publications in SPE search (search.spe.org)
Results
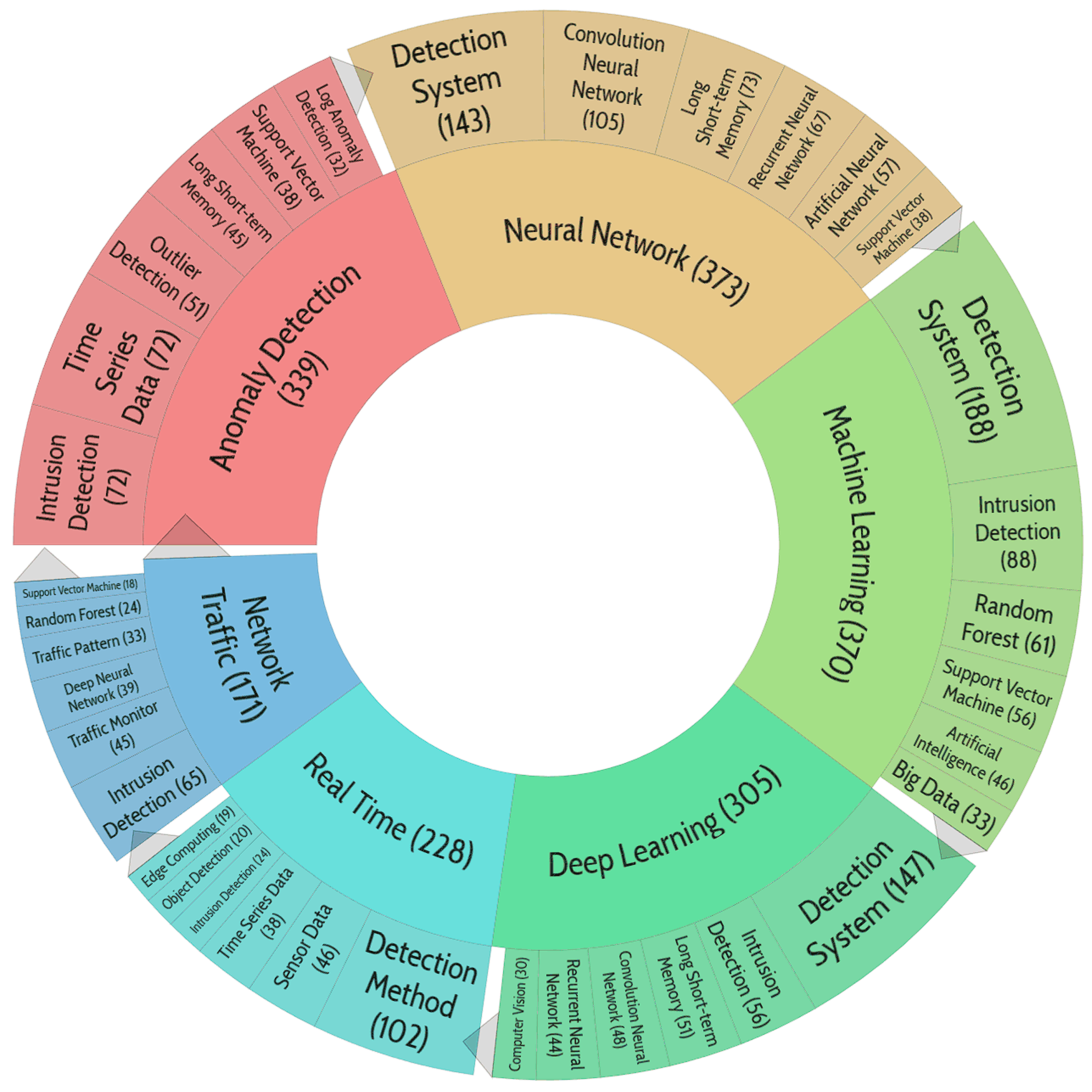
Clustering of bibliometric records
- Anomaly Detection (339 Docs, 14 Subclusters)
- Neural Network (373 Docs, 14 Subclusters)
- Machine Learning (370 Docs, 14 Subclusters)
- Deep Learning (305 Docs, 14 Subclusters)
- Real Time (228 Docs, 14 Subclusters)
- Network Traffic (171 Docs, 14 Subclusters)
- Time Series (125 Docs, 14 Subclusters)
- Future Research (107 Docs, 14 Subclusters)
- Security Privacy (69 Docs, 14 Subclusters)
- Blockchain Technology (38 Docs, 14 Subclusters)
- High Resolution (24 Docs, 11 Subclusters)
- Quality Assessment (18 Docs, 14 Subclusters)
- Wind Energy (19 Docs, 13 Subclusters)
- Signal Ratio (16 Docs, 13 Subclusters)
- Particle Swarm Optimization (15 Docs, 12 Subclusters)
- Knowledge Graph (13 Docs, 10 Subclusters)
- Fuzzy Sets (14 Docs, 12 Subclusters)
- Dimension Reduction (13 Docs, 12 Subclusters)
- Persistent Threat (13 Docs, 10 Subclusters)
- Texture Features (13 Docs, 13 Subclusters)
- Semantic Segmentation (11 Docs, 10 Subclusters)
- Energy Sector (12 Docs, 13 Subclusters)
- Electronic Control (13 Docs, 13 Subclusters)
- Hyperspectral Image (10 Docs)
- Maintenance Activity (9 Docs)
- Useful Life (8 Docs)
- Decision Boundary (8 Docs)
- Damage Severity (7 Docs)
- Other Topics (839 Docs)
Results of a search of SPE publications and a description of the main features of the methods
Conclusion
Possible applications of the findings
References
- Qassab A., Bhadran V., Sudevan V., et al. Autonomous Inspection System for Anomaly Detection in Natural Gas Pipelines // Day 4 Thu, November 12, 2020. Abu Dhabi, UAE: SPE, 2020. P. D041S105R002. [CrossRef]
- Snyder J., Scott S., Kassim R. Self-Adjusting Anomaly Detection Model for Well Operation and Production in Real-Time // Day 1 Tue, April 09, 2019. Oklahoma City, Oklahoma, USA: SPE, 2019. P. D011S002R005. [CrossRef]
- Santos P., Aldren L., Melvin E., et al. AI Augmented Engineering Intelligence for Industrial Equipment // Day 2 Wed, September 06, 2023. Aberdeen, Scotland, UK: SPE, 2023. P. D021S006R003. [CrossRef]
- Beduschi F., Turconi F., De Gregorio B., et al. Optimizing Rotating Equipment Maintenance Through Machine Learning Algorithm // Day 3 Wed, November 17, 2021. Abu Dhabi, UAE: SPE, 2021. P. D031S088R001. [CrossRef]
- Irani Z.S., George R., Dayal R. Technology for Continuous Cyber Monitoring of Offshore Assets // Day 3 Wed, October 04, 2023. Abu Dhabi, UAE: SPE, 2023. P. D031S101R003. [CrossRef]
- Concetti L., Mazzuto G., Ciarapica F.E., Bevilacqua M. An Unsupervised Anomaly Detection Based on Self-Organizing Map for the Oil and Gas Sector // Applied Sciences. 2023. Vol. 13, No 6. P. 3725. [CrossRef]
- Aljameel S.S., Alomari D.M., Alismail S., et al. An Anomaly Detection Model for Oil and Gas Pipelines Using Machine Learning // Computation. 2022. Vol. 10, No 8. P. 138. [CrossRef]
- Coelho E Silva L., Murça M.C.R. A data analytics framework for anomaly detection in flight operations // Journal of Air Transport Management. 2023. Vol. 110. P. 102409. [CrossRef]
- Quatrini E., Costantino F., Di Gravio G., Patriarca R. Machine learning for anomaly detection and process phase classification to improve safety and maintenance activities // Journal of Manufacturing Systems. 2020. Vol. 56. P. 117–132. [CrossRef]
- He X., Robards E., Gamble R., Papa M. Anomaly Detection Sensors for a Modbus-Based Oil and Gas Well-Monitoring System // 2019 2nd International Conference on Data Intelligence and Security (ICDIS). South Padre Island, TX, USA: IEEE, 2019. P. 1–8. [CrossRef]
- Da Silva Arantes J., Da Silva Arantes M., Fröhlich H.B., et al. A novel unsupervised method for anomaly detection in time series based on statistical features for industrial predictive maintenance // International Journal of Data Science and Analytics. 2021. Vol. 12, No 4. P. 383–404. [CrossRef]
- Musa T.H.A., Bouras A. Anomaly Detection: A Survey // Proceedings of Sixth International Congress on Information and Communication Technology / ed. Yang X.-S., Sherratt S., Dey N., Joshi A. Singapore: Springer Singapore, 2022. Vol. 217. P. 391–401. [CrossRef]
- Nassif A.B., Talib M.A., Nasir Q., Dakalbab F.M. Machine Learning for Anomaly Detection: A Systematic Review // IEEE Access. 2021. Vol. 9. P. 78658–78700. [CrossRef]
- Osiński S., Weiss D. Carrot2: Design of a Flexible and Efficient Web Information Retrieval Framework // Advances in Web Intelligence / ed. Hutchison D., Kanade T., Kittler J., et al. Berlin, Heidelberg: Springer Berlin Heidelberg, 2005. Vol. 3528. P. 439–444. [CrossRef]
- Carpineto C., Osiński S., Romano G., Weiss D. A survey of Web clustering engines // ACM Computing Surveys. 2009. Vol. 41, No 3. P. 1–38. [CrossRef]
- Krovetz R. Viewing morphology as an inference process // Artificial Intelligence. 2000. Vol. 118, No 1–2. P. 277–294. [CrossRef]
- NMAM Institute of Technology, Dept. of Computer Science and Engineering, Nayak A.S., Kanive A.P. Survey on Pre-Processing Techniques for Text Mining // International Journal of Engineering and Computer Science. 2016. [CrossRef]
- Breiman L. Random Forests // Machine Learning. 2001. Vol. 45, No 1. P. 5–32. [CrossRef]
- AlSaihati A., Elkatatny S., Mahmoud A., Abdulraheem A. Early Anomaly Detection Model Using Random Forest while Drilling Horizontal Wells with a Real Case Study // Day 3 Thu, May 27, 2021. Abu Dhabi, UAE: SPE, 2021. P. D032S040R001. [CrossRef]
- Alharbi B., Liang Z., Aljindan J.M., et al. Explainable and Interpretable Anomaly Detection Models for Production Data // SPE Journal. 2022. Vol. 27, No 01. P. 349–363. [CrossRef]
- Akinsete O., Oshingbesan A. Leak Detection in Natural Gas Pipelines Using Intelligent Models // Day 2 Tue, August 06, 2019. Lagos, Nigeria: SPE, 2019. P. D023S009R001. [CrossRef]
- Tewari S., Dwivedi U.D., Shiblee M. Assessment of Big Data Analytics Based Ensemble Estimator Module for the Real-Time Prediction of Reservoir Recovery Factor // Day 4 Thu, March 21, 2019. Manama, Bahrain: SPE, 2019. P. D041S038R003. [CrossRef]
- Del Pino Fiorillo M.A. Automating Dynamometer Charts Interpretation with Machine Learning // Day 2 Thu, June 15, 2023. Port of Spain, Trinidad and Tobago: SPE, 2023. P. D021S010R003. [CrossRef]
- Chang C.-C., Lin C.-J. LIBSVM: A library for support vector machines // ACM Transactions on Intelligent Systems and Technology. 2011. Vol. 2, No 3. P. 1–27. [CrossRef]
- Akkurt R., Sankaranarayanan B., Simoes V., et al. An Unsupervised Stochastic Machine Learning Approach for Well Log Outlier Identification // Proceedings of the 10th Unconventional Resources Technology Conference. Houston, Texas, USA: American Association of Petroleum Geologists, 2022. [CrossRef]
- Alotaibi B., Aman B., Nefai M. Real-Time Drilling Models Monitoring Using Artificial Intelligence // Day 2 Tue, March 19, 2019. Manama, Bahrain: SPE, 2019. P. D021S001R004. [CrossRef]
- Szegedy C., Wei Liu, Yangqing Jia, et al. Going deeper with convolutions // 2015 IEEE Conference on Computer Vision and Pattern Recognition (CVPR). Boston, MA, USA: IEEE, 2015. P. 1–9. [CrossRef]
- Zhang H., Zeng Y., Bao H., et al. Drilling and Completion Anomaly Detection in Daily Reports by Deep Learning and Natural Language Processing Techniques // Proceedings of the 8th Unconventional Resources Technology Conference. Online: American Association of Petroleum Geologists, 2020. [CrossRef]
- Mercante R., Netto T.A. Virtual Multiphase Flowmeter Using Deep Convolutional Neural Networks // SPE Journal. 2023. P. 1–14. [CrossRef]
- Zhang K., Wang Y., Li G., et al. Prediction of Field Saturations Using a Fully Convolutional Network Surrogate // SPE Journal. 2021. Vol. 26, No 04. P. 1824–1836. [CrossRef]
- Marhon S.A., Cameron C.J.F., Kremer S.C. Recurrent Neural Networks // Handbook on Neural Information Processing / ed. Bianchini M., Maggini M., Jain L.C. Berlin, Heidelberg: Springer Berlin Heidelberg, 2013. Vol. 49. P. 29–65. [CrossRef]
- Alakeely A., Horne R.N. Simulating the Behavior of Reservoirs with Convolutional and Recurrent Neural Networks // SPE Reservoir Evaluation & Engineering. 2020. Vol. 23, No 03. P. 0992–1005. [CrossRef]
- Ezechi C.G., Okoroafor E.R. Integration of Artificial Intelligence with Economical Analysis on the Development of Natural Gas in Nigeria; Focusing on Mitigating Gas Pipeline Leakages // Day 3 Wed, August 02, 2023. Lagos, Nigeria: SPE, 2023. P. D031S018R004. [CrossRef]
- Yin Q., Yang J., Tyagi M., et al. Machine Learning for Deepwater Drilling: Gas-Kick-Alarm Classification Using Pilot-Scale Rig Data with Combined Surface-Riser-Downhole Monitoring // SPE Journal. 2021. Vol. 26, No 04. P. 1773–1799. [CrossRef]
- Hochreiter S., Schmidhuber J. Long Short-Term Memory // Neural Computation. 1997. Vol. 9, No 8. P. 1735–1780. [CrossRef]
- Kara M.C., Majeran M., Peterson B., et al. A Machine Learning Workflow to Predict Anomalous Sanding Events in Deepwater Wells // Day 3 Wed, August 18, 2021. Virtual and Houston, Texas: OTC, 2021. P. D031S033R002. [CrossRef]
- Nivlet P., Bjorkevoll K.S., Tabib M., et al. Towards Real-Time Bad Hole Cleaning Problem Detection Through Adaptive Deep Learning Models // Day 2 Mon, February 20, 2023. Manama, Bahrain: SPE, 2023. P. D021S073R005. [CrossRef]
- Aditama P., Koziol T., Dillen Dr.M. Development of an Artificial Intelligence-Based Well Integrity Monitoring Solution // Day 3 Wed, November 02, 2022. Abu Dhabi, UAE: SPE, 2022. P. D031S110R004. [CrossRef]
- Ledig C., Theis L., Huszar F., et al. Photo-Realistic Single Image Super-Resolution Using a Generative Adversarial Network // 2017 IEEE Conference on Computer Vision and Pattern Recognition (CVPR). Honolulu, HI: IEEE, 2017. P. 105–114. [CrossRef]
- Zhang Z., Song W., Wang W. Broadband reconstruction of seismic signal with generative recurrent adversarial network // Second International Meeting for Applied Geoscience & Energy. Houston, Texas: Society of Exploration Geophysicists and American Association of Petroleum Geologists, 2022. P. 2178–2182. [CrossRef]
- Marques F., Costa P., Castro F., Parente M. Self-Supervised Subsea SLAM for Autonomous Operations // Day 1 Mon, May 06, 2019. Houston, Texas: OTC, 2019. P. D011S002R006. [CrossRef]
- Sutton R.S., Barto A.G. Reinforcement Learning: An Introduction // IEEE Transactions on Neural Networks. 1998. Vol. 9, No 5. P. 1054–1054. [CrossRef]
- Alzahrani M., Alotaibi B., Aman B. Novel Stuck Pipe Troubles Prediction Model Using Reinforcement Learning // Day 2 Tue, February 22, 2022. Riyadh, Saudi Arabia: IPTC, 2022. P. D021S042R003. [CrossRef]
- Miftakhov R., Al-Qasim A., Efremov I. Deep Reinforcement Learning: Reservoir Optimization from Pixels // Day 2 Tue, January 14, 2020. Dhahran, Kingdom of Saudi Arabia: IPTC, 2020. P. D021S052R002. [CrossRef]
| Title and Reference | Short summary |
|---|---|
| Early Anomaly Detection Model Using Random Forest while Drilling Horizontal Wells with a Real Case Study [19] | This paper presents a machine learning model to predict drilling surface torque for early detection of operational problems. The model uses real horizontal drilling data from the day before the stuck pipe incident. It predicts surface drilling torque based on typical patterns observed over the past 24 hours, using train and test a random forest model. The model is integrated with the Mahalanobis metric to assess the closeness of real observations to the predicted normal trend. |
| Explainable and Interpretable Anomaly Detection Models for Production Data [20] | This study compares machine-learning models on two datasets for anomaly detection. It aims to understand how these models make decisions. The models used include K-nearest neighbors, logistic regression, support vector machines, decision tree, random forest, and rule fit classifier. In one data set, the rule fit classifier outperformed the remaining models in both F1 and complexity, where F1. In the second data set, random forest outperformed the rest in prediction performance with F1, yet it had the lowest complexity metric. |
| Leak Detection in Natural Gas Pipelines Using Intelligent Models [21] | This study investigates the effectiveness of intelligent models in detecting small leaks in natural gas pipelines using operational parameters like pressure, temperature, and flowrate. Five models were used: Gradient Boosting, Decision Trees, Random Forest, Support Vector Machine, and Artificial Neural Network. Results showed Random Forest and Decision Tree models were most sensitive, with a 0.1% leak detection rate in 2 hours. All models had high reliability, but low accuracy, with Artificial Neural Network and Support Vector Machine performing best. |
| Assessment of Big Data Analytics Based Ensemble Estimator Module for the Real-Time Prediction of Reservoir Recovery Factor [22] | Estimating reservoir recovery factor is a challenging task due to high uncertainty, large inexactness, noise, and high dimensionality in reservoir measurements. The paper presents a big data-driven ensemble estimator module, which uses wavelet-associated ensemble models to estimate reservoir recovery factor. The module uses bagging and random forest ensembles to correlate reservoir properties with the recovery factor, and the Relief algorithm to understand their significance. The random forest showing the highest coefficient of correlation and minimal estimation errors. |
| Automating Dynamometer Charts Interpretation with Machine Learning [23] | The aim of the study was to create a mathematical model for the interpretation of Dynamometer Charts from Sucker Rod Pumps. The paper describes a data processing pipeline for obtaining, normalizing, transforming, and evaluating graphs. About 1,000 models were trained and tested, including support vector machines, decision trees, K-nearest neighbors and neural networks. The XGBoost algorithm performed best, although Random Forest algorithms were significantly more accurate in certain conditions. |
| Title and Reference | Short summary |
|---|---|
| An Unsupervised Stochastic Machine Learning Approach for Well Log Outlier Identification [25] | Outlier detection is crucial in Log Quality Control workflows, and machine learning implementations must address challenges. This paper presents a stochastic outlier detection algorithm using the One-Class Support Vector Machine (1CSVM) method. This method creates outlier flags for all data vectors, providing a proxy for uncertainty. It is robust, efficient, and more efficient than processing all wells set at once. The methodology's unique feature is weighting input data vectors based on petrophysics and measurement physics. This automated workflow is ideal for unconventional applications involving large volumes of legacy data. |
| Real-Time Drilling Models Monitoring Using Artificial Intelligence [26] | Drilling and Workover operations are evolving at a rapid pace, requiring more data to predict drilling problems. This paper presents a new approach using the Wellsite Information Transfer Specification Markup Language, applying an improved mechanism to monitor and evaluate anomaly detection models and demonstrating the benefits of iterative improvements. A regression classifier model using a support vector machine was developed to predict the expected number of alerts. |
| Title and Reference | Short summary |
|---|---|
| Drilling and Completion Anomaly Detection in Daily Reports by Deep Learning and Natural Language Processing Techniques [28] | Unconventional oil & gas fields generate vast amounts of data, making data-driven methods challenging for analysis. Different activity coding systems and missing data make automatic anomaly detection difficult. An automatic text classification method was proposed using machine learning and natural language processing techniques for daily drilling and completion reports. Based on 460,000 operation records from 1,700 wells worldwide, Word2vec was used, and CNN was found to be the best method for text classification. |
| Virtual Multiphase Flowmeter Using Deep Convolutional Neural Networks [29] | This paper proposes a low-cost, instantaneous model for measuring oil, gas, and water volume in petroleum wells using artificial intelligence. The system uses pressure and temperature sensors from wells and opening control valve state to train a deep neural network with a convolutional layer to output fluid volume rate. The Schlumberger OLGA multiphase flow simulator software is used to provide data. Tests show the approximation achieves up to 99.6% accuracy, potentially replacing expensive multiphase meters or serving as a redundant digital sensor. |
| Prediction of Field Saturations Using a Fully Convolutional Network Surrogate [30] | The study focuses on developing surrogate models for predicting field saturations using a fully convolutional encoder/decoder network based on dense convolutional networks. The model extracts multiscale features from input data and uses these to recover input image resolution. It uses static and dynamic reservoir parameters as input features and outputs water-saturation distributions. This approach offers precision and cost-effectiveness, making it useful for production optimization and history matching. |
| Title and Reference | Short summary |
|---|---|
| Simulating the Behavior of Reservoirs with Convolutional and Recurrent Neural Networks [32] | Recurrent neural networks and convolutional neural networks have been applied to model reservoir behavior from data. Recurrent neural networks have the ability to retain information from previous patterns, making them suitable for interpreting permanent downhole gauge records. Convolutional neural networks, with specific design modifications, are as capable in modeling sequences of information and reliable in making inferences to cases not seen during training. The study discusses the differences in processing information and memory handling between these two architectures. |
| Integration of Artificial Intelligence with Economical Analysis on the Development of Natural Gas in Nigeria; Focusing on Mitigating Gas Pipeline Leakages [33] | Artificial intelligence is used to develop models using gas flow data to detect potential leakages in Nigeria's natural gas reserves. Machine learning algorithms like Recurrent Neural Networks and K-nearest neighbors are trained and evaluated for accuracy and precision. The results show that recurrent neural networks outperform K-nearest neighbors in leak detection, but all models possess high reliability. |
| Machine Learning for Deepwater Drilling: Gas-Kick-Alarm Classification Using Pilot-Scale Rig Data with Combined Surface-Riser-Downhole Monitoring [34] | Deepwater drilling often faces gas kicks due to the narrow mud-weight window. Traditional methods have time lag and can lead to severe gas influxes. A novel machine-learning model uses pilot-scale rig data and surface-riser-downhole monitoring for early detection and risk classification. Four ML algorithms are developed. The long short-term memory recurrent neural network algorithm showed the best performance, it is selected and deployed to early detect gas kicks and classify the corresponding kick alarms. The model achieves high recall, accuracy, precision, recall, and detection time delay. |
| Title and Reference | Short summary |
|---|---|
| A Machine Learning Workflow to Predict Anomalous Sanding Events in Deepwater Wells [36] | This study develops a predictive machine learning model using sensor and simulation data to inform Control Room Operators before significant damage occurs, using an anomaly detection architecture. The problem is addressed using Principal Component Analysis and Long Short-Term Memory Autoencoders, which reconstruct the original input. An alarm is triggered when the real-time anomaly score exceeds the training threshold. |
| Towards Real-Time Bad Hole Cleaning Problem Detection Through Adaptive Deep Learning Models [37] | The study presents an adaptive predictive deep-learning model that uses equivalent circulating density measurements, model results, and drilling data to predict potential bad hole cleaning conditions. The model has two components: an anomaly detector and a predictor. It uses Long Short-Term Memory cells to account for data correlations and generate future data conditioned to past observations. The approach is demonstrated on two real examples from offshore Norway. |
| Development of an Artificial Intelligence-Based Well Integrity Monitoring Solution [38] | The goal of an artificial intelligence-based well integrity monitoring solution was to create models to identify well annulus leakage events, accounting for the well type and all relevant anomalies. Artificial intelligence models were created using Long Short-Term Memory Autoencoders and classifier to identify complex irregularities. |
| Title and Reference | Short summary |
|---|---|
| Broadband reconstruction of seismic signal with generative recurrent adversarial network [40] | The resolution of seismic data depends on frequency and bandwidth, and complex exploration objects require higher resolution algorithms. Traditional methods can affect signal to noise ratio, reducing data reliability. A new method based on a generative recurrent adversarial network (GRAN) is proposed to generate pseudo sample sets constrained by geological layers and train the GRAN model for broadband seismic data reconstruction. The method's applicability is proven through blind well tests and is applied to actual work area seismic data processing, achieving excellent results. |
| Self-Supervised Subsea SLAM for Autonomous Operations [41] | The study proposes a deep learning-based Simultaneous Localization and Mapping (SLAM) method to estimate the 3D structure of a vehicle's surrounding environment from a single video. This method predicts a depth map of a given video frame while estimating the vehicle's movement between frames. The method is self-supervised and uses Generative Adversarial Networks to improve depth map prediction results. The study evaluates the method on the KITTI dataset and a private dataset of subsea inspection videos, showing it outperforms existing SLAM methods in depth prediction and pose estimation tasks. |
| Title and Reference | Short summary |
|---|---|
| Novel Stuck Pipe Troubles Prediction Model Using Reinforcement Learning [43] | This paper defines the stuck pipe prediction problem as a multi-class problem considering the dynamic nature of drilling operations. A reinforcement learning-based algorithm is proposed to solve this problem, with performance and evaluation results shared. The algorithm's accuracy is demonstrated, and performance improvement through feedback channel retraining is demonstrated. The reinforcement logic connects solutions to operation reporting, enhancing accuracy through neural networks. |
| Deep Reinforcement Learning: Reservoir Optimization from Pixels [44] | This paper uses Deep Reinforcement Learning to optimize the Net Present Value of waterflooding by altering the water injection rate. This is the first demonstration of AI's potential in understanding reservoir physics directly, without considering reservoir petrophysical properties or the number of wells in the reservoir. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





