Submitted:
06 September 2023
Posted:
08 September 2023
Read the latest preprint version here
Abstract
Keywords:
1. Introduction
2. Related Work
3. Classification of Jamming Attacks
- Constant jamming: Constant jamming is an interference attack where an attacker continuously transmits a random radio signal on the communication channel, without following the MAC protocol. As a result, legitimate users perceive the channel to be busy even when it is not.
- Deceptive jamming: Discusses deceptive ECM attacks and contrasts them with persistent ECM attacks. It states that deceptive ECM attackers do not send random bit streams but instead send semi-efficient knowledge packets. The paragraph implies that the information header of these packets is valid, but the payload is useless. It goes on to suggest that these attacks may keep the channels perceived by legitimate users busy all the time, making it difficult for legitimate users to communicate properly. The language used is generally clear and concise, but there are some areas where the meaning is unclear, or the wording could be improved for clarity. For example, the phrase "underneath constant police investigation" is unclear and could be revised to improve clarity. Additionally, the sentence "This makes legitimate users unable to enter. Communicate wrongfully." is unclear and could be rewritten to more clearly express the intended meaning.
- Random jamming: This type of attack consumes less power than the previous two types of attackers. Random jamming attacks operate by carrying out jamming attacks for a specific period (attack mode) and then stopping the jamming at another period (sleep mode). The amount of power lost due to the attack is determined by the ratio of the attack period to the sleep period. “Overall, the paragraph provides a good explanation of random jamming attacks and their power consumption characteristics.
- Reactive jamming: This type of jamming attack is triggered by the attacker only when they detect communication transmission in the network. The attacker does not expend resources other than jamming, and their focus is on jamming the receiving node rather than the signal transmitting node. In vehicular networks, the primary method of jamming attack is through the transmission of high-power interference signals by nodes. This action submerges the genuine communication signals in the interference signals, causing the receiving nodes to lose or significantly reduce their ability to receive signals. Such an attack is an example of a blocking active interference attack.
4. Jamming Detection and Description Scenario
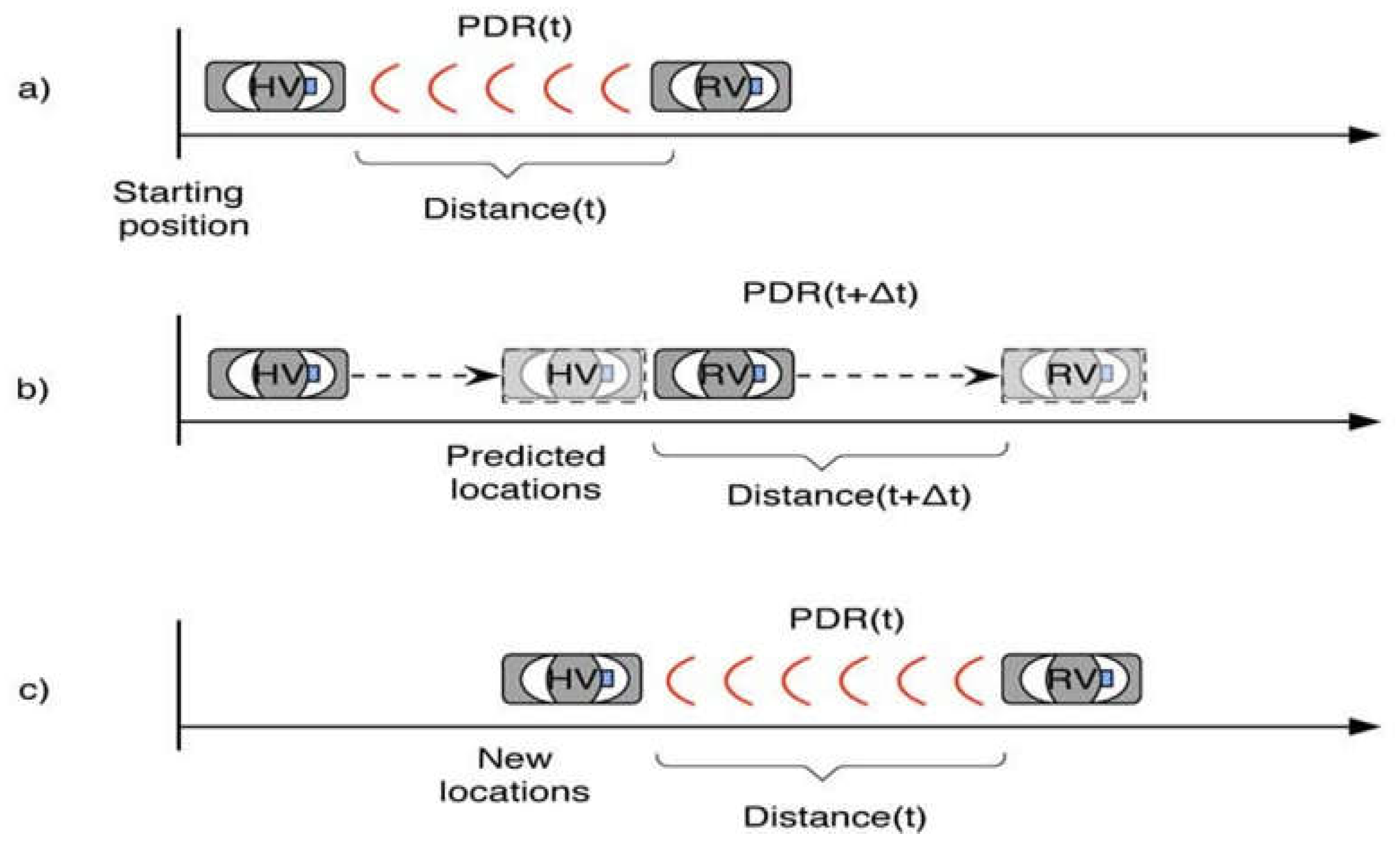
4.1. Predication Location
4.2. PDR Evaluation
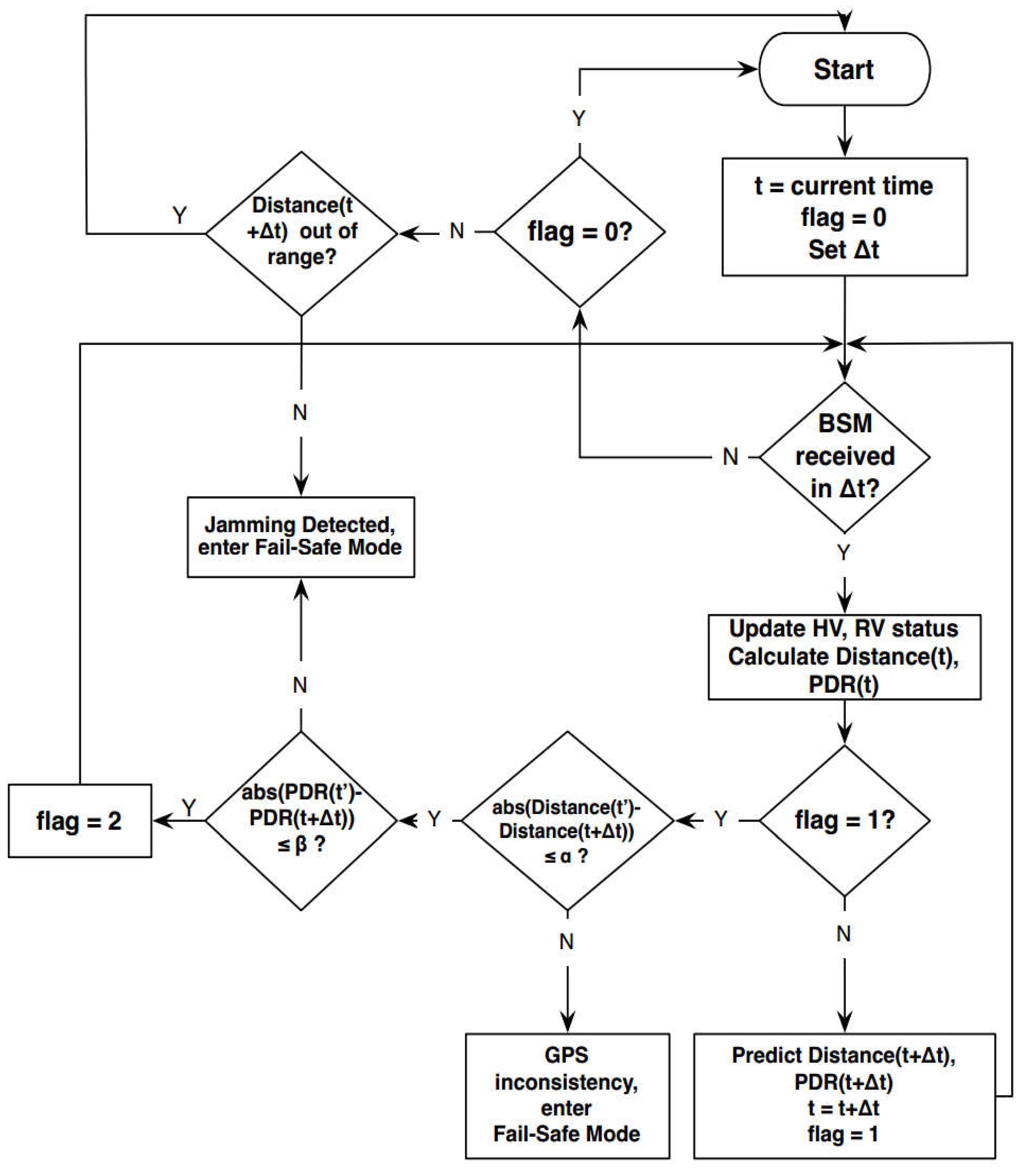
5. Model Designed to Detect Jamming Attacks on VANETs
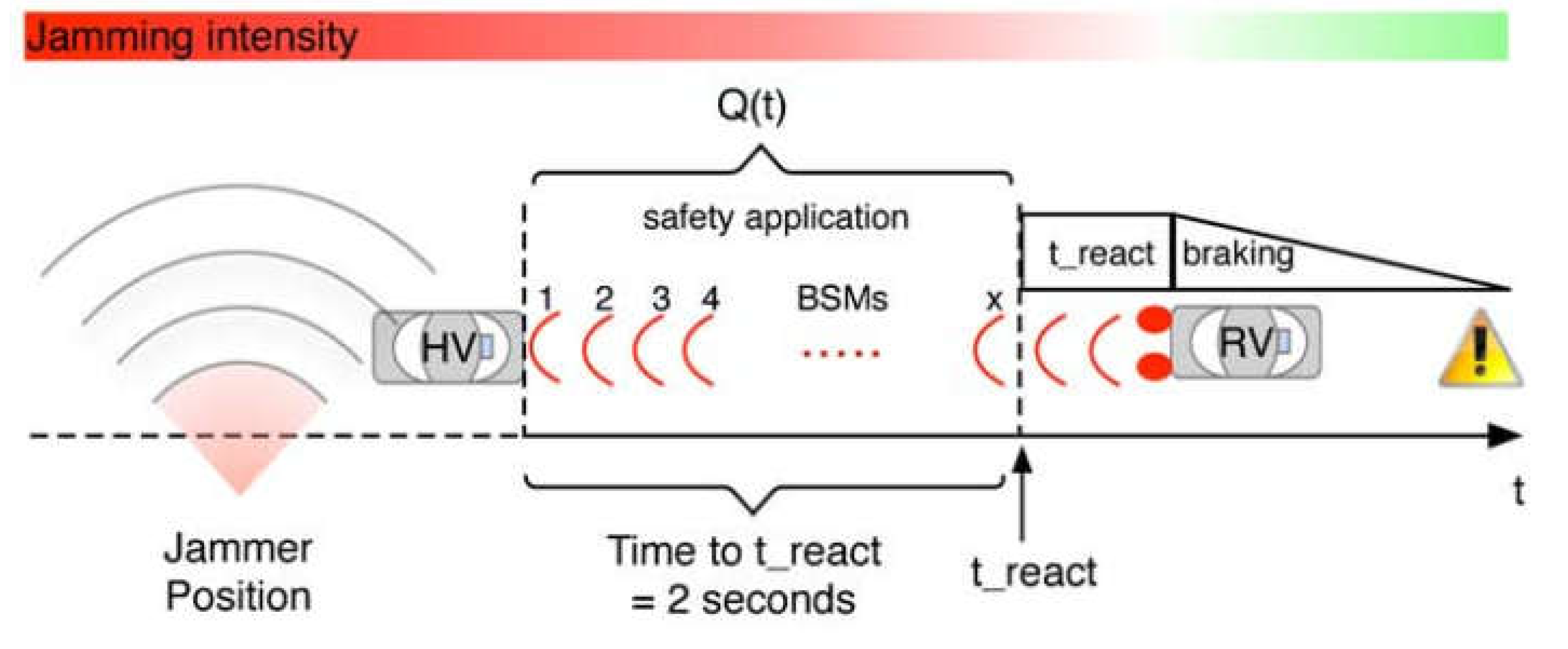
6. Jamming Attack Recovery Algorithm for Dedicated Short-Range Communications (DSRC) Safety Applications in Vehicular Ad-Hoc Networks (VANET)
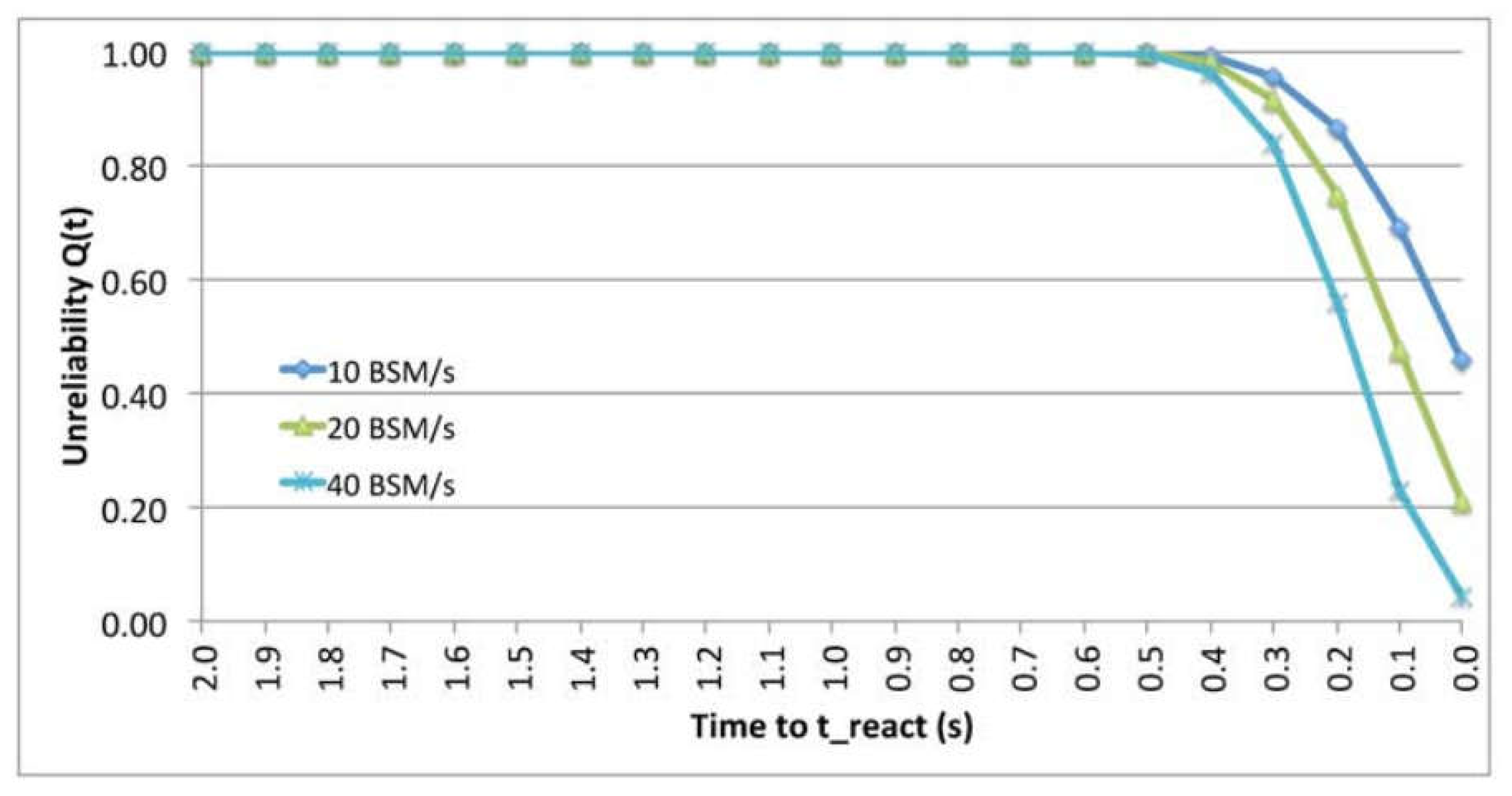
6.1. Reliability and Redundancy
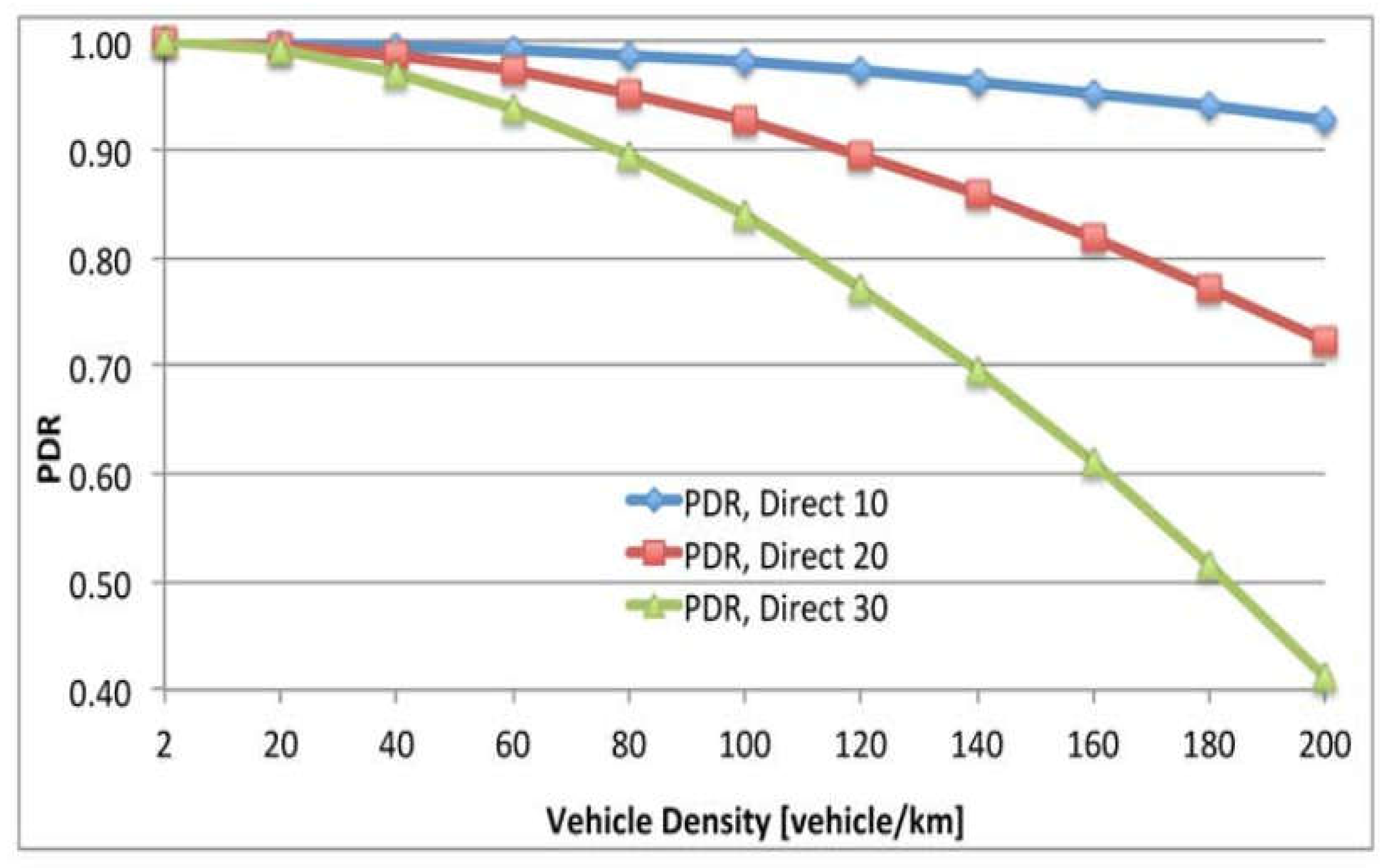
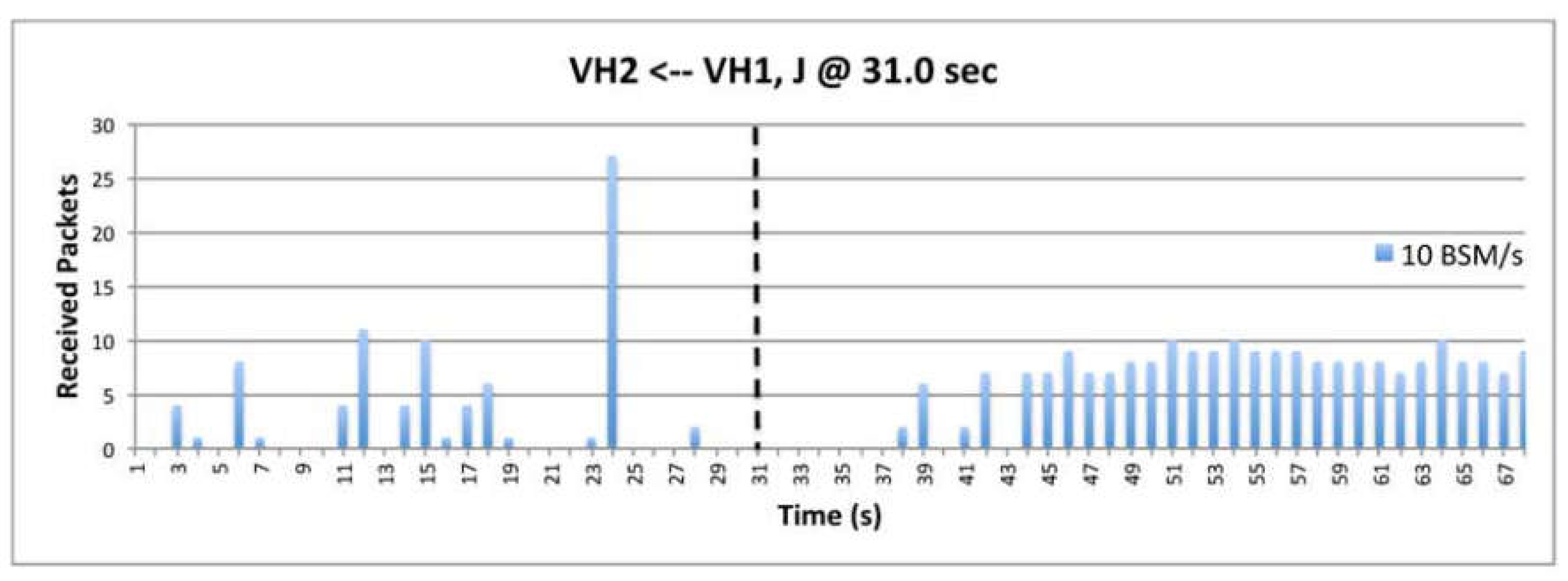
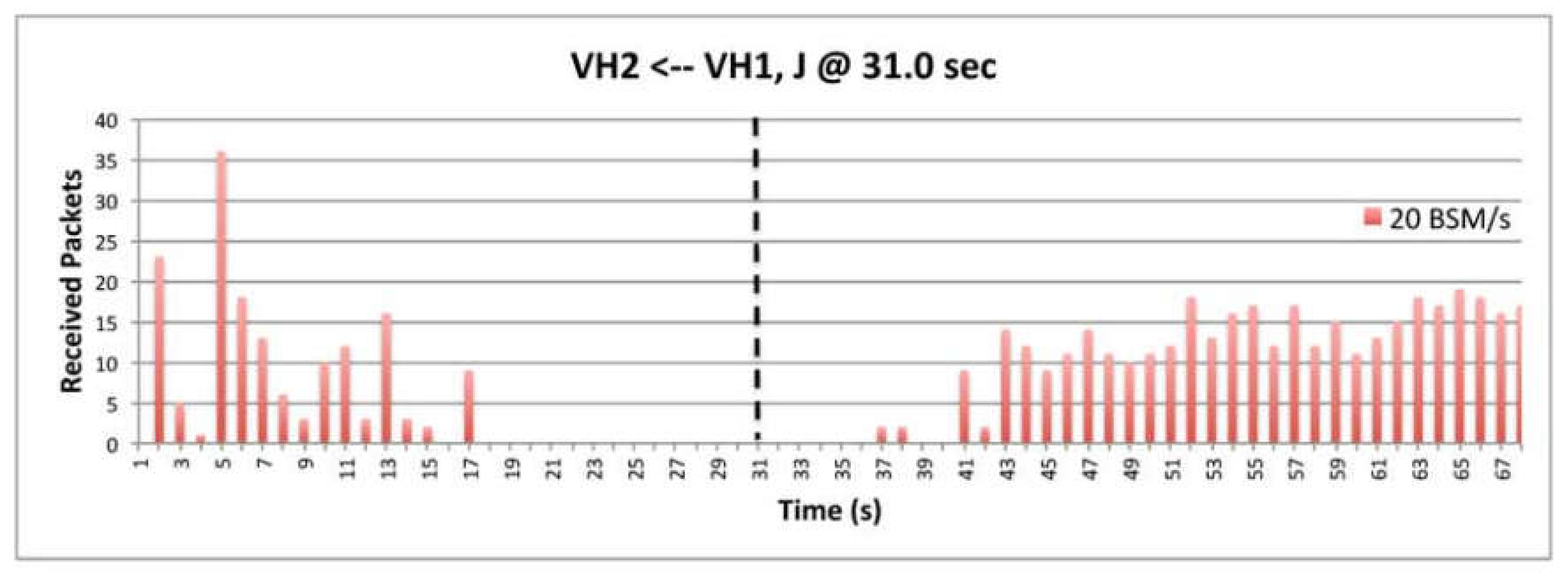
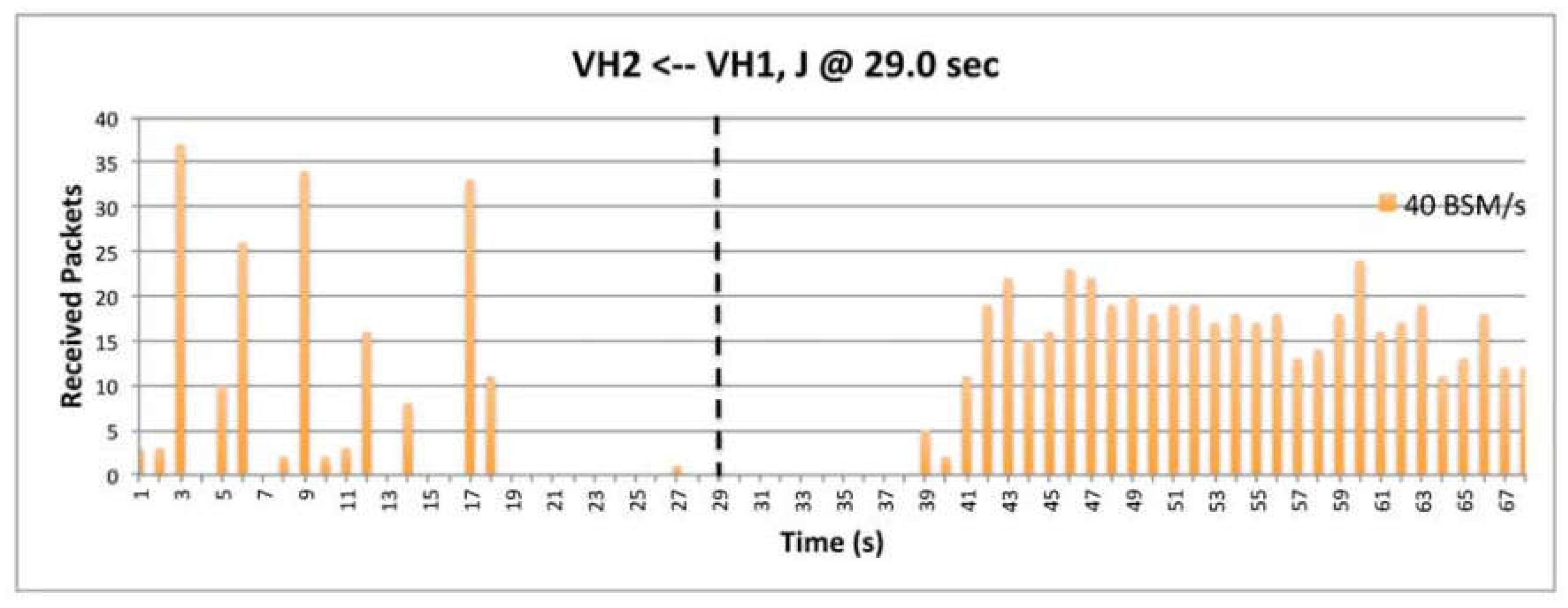
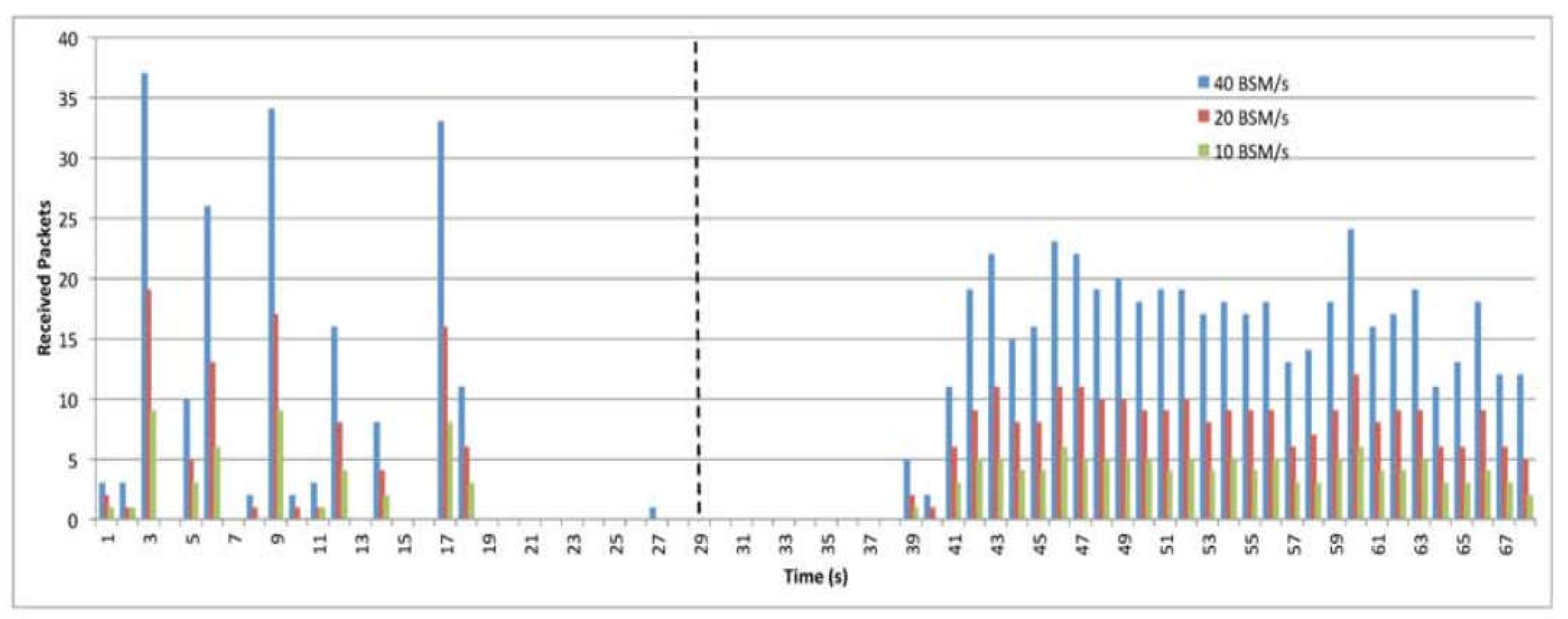
6.2. Effectiveness of Various BSM Rates
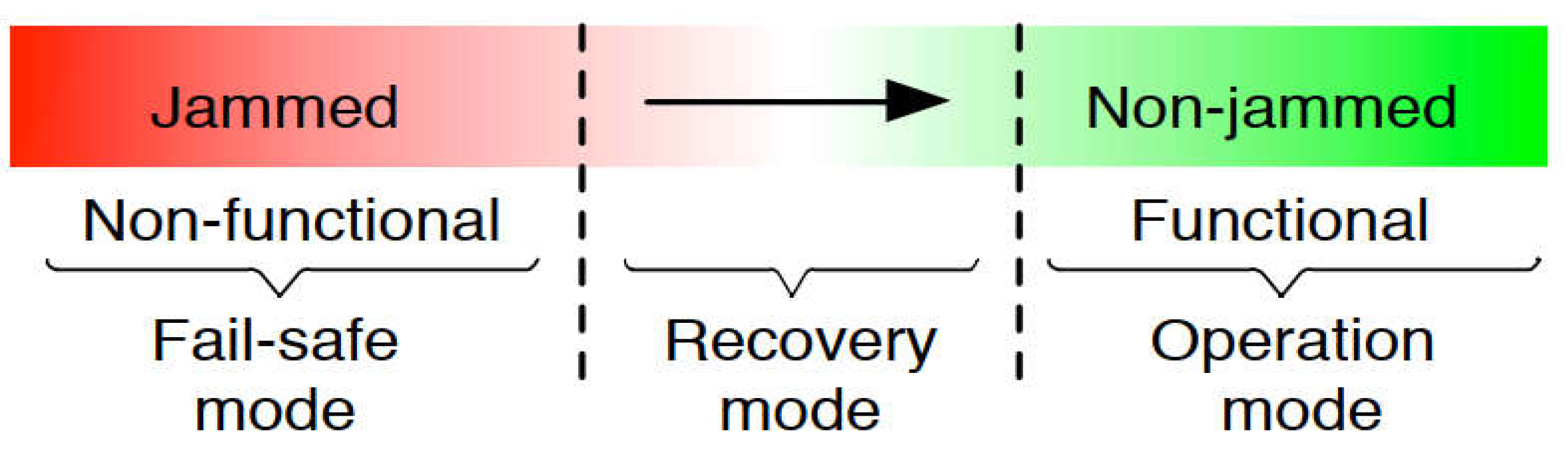
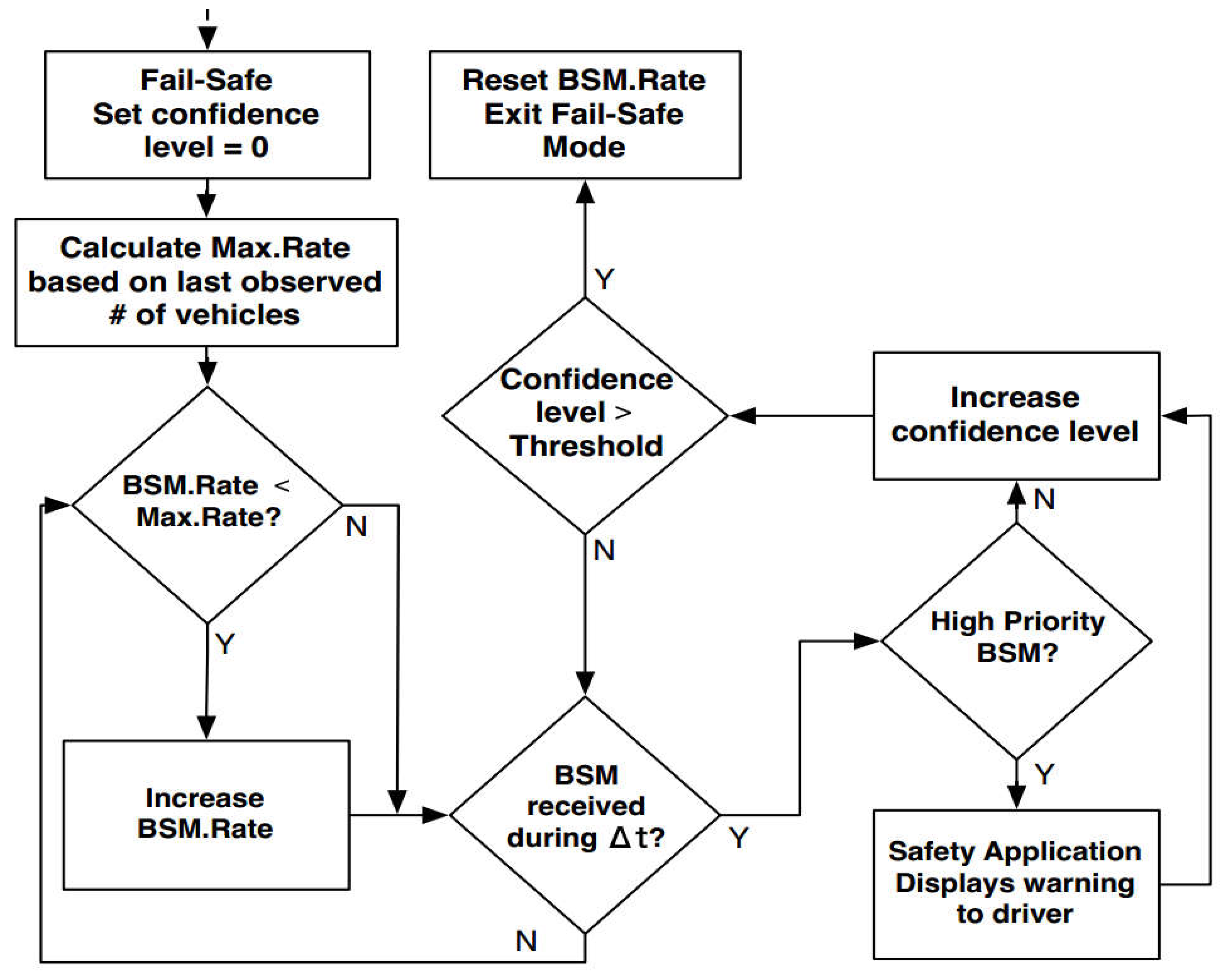
7. Jammer Fail-Safe Mode and Recovery Algorithm
8. Performances Evaluation
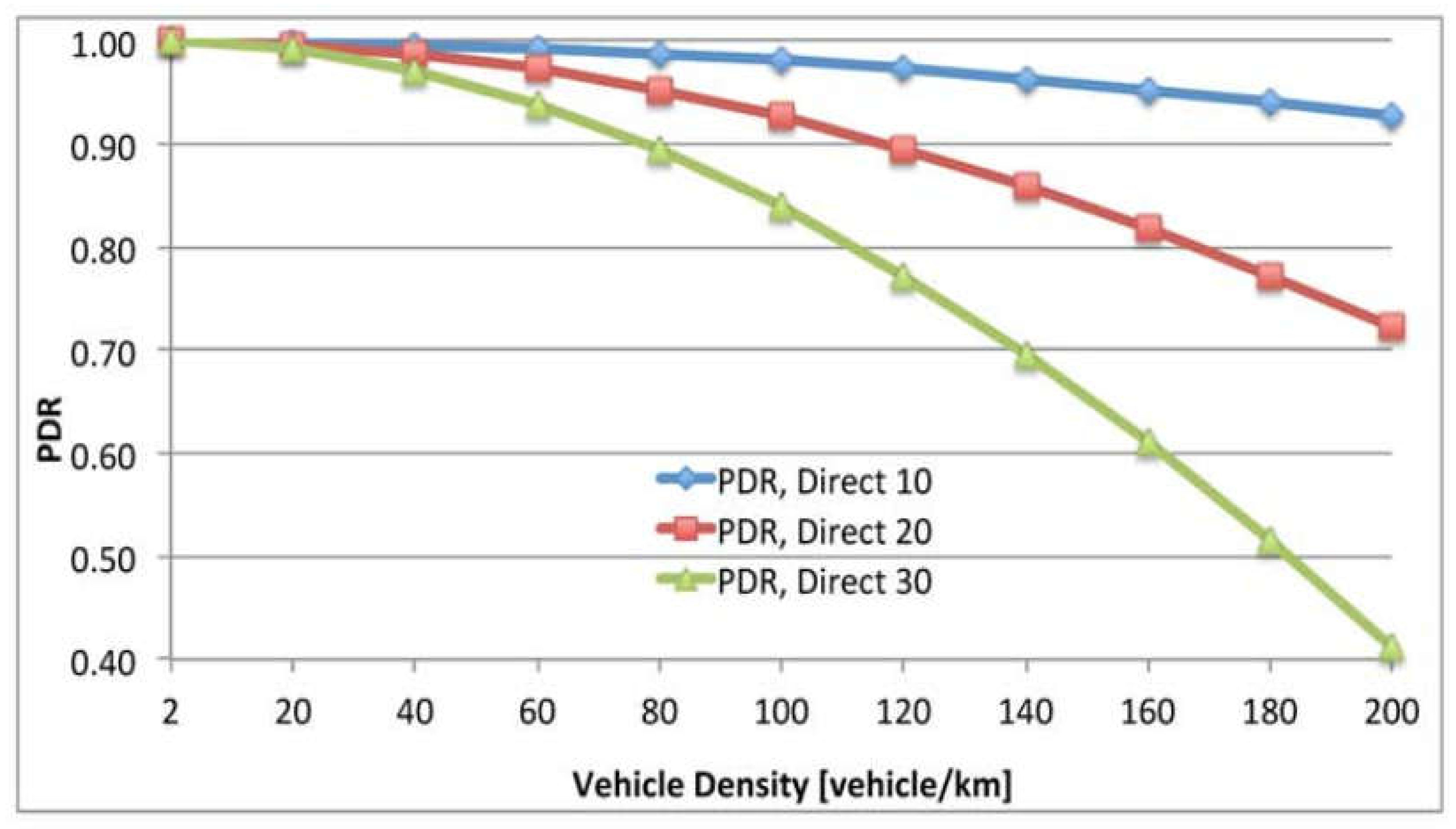
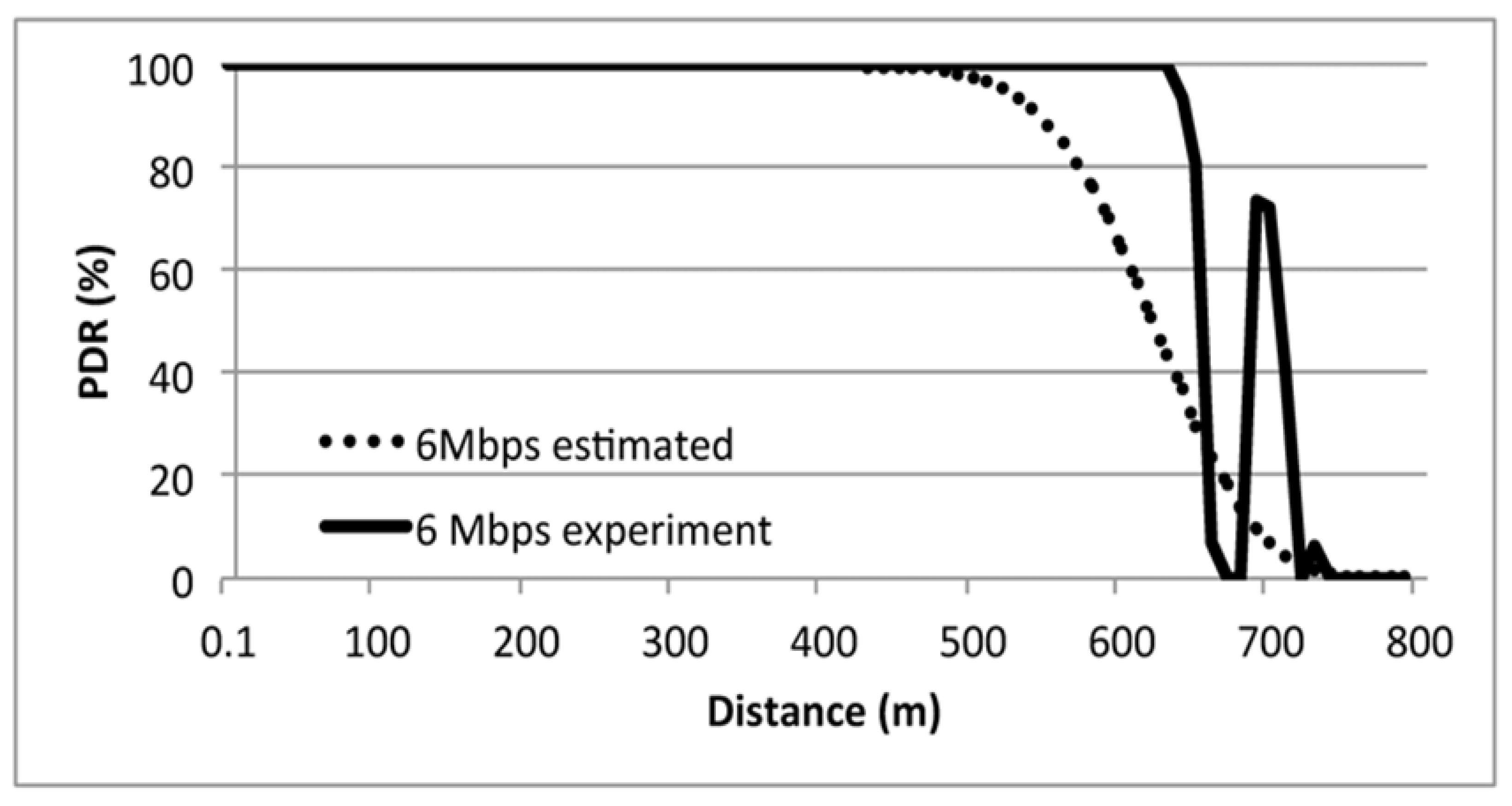
8.1. Indigenous PDR
8.2. The Effect Jamming for PDR
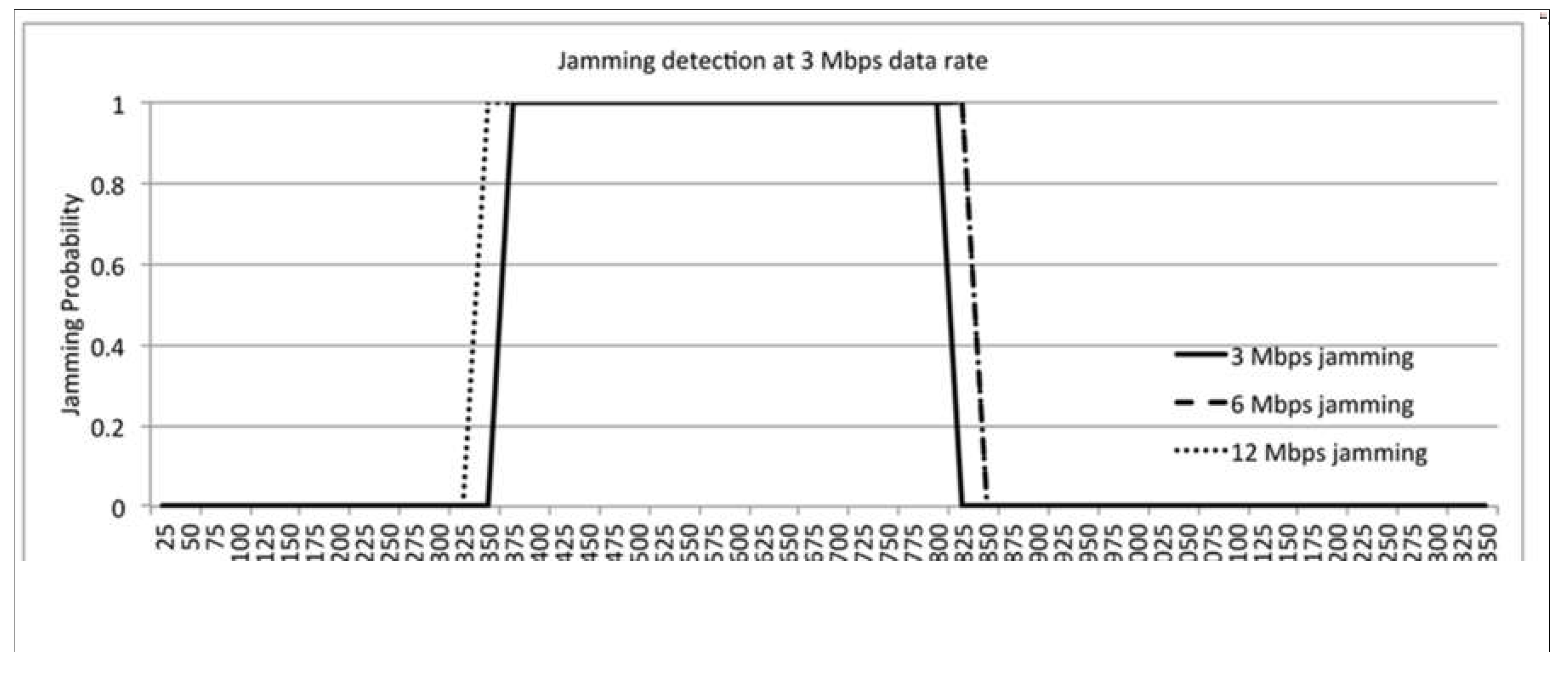
8.3. Jamming Detection Evaluation of Algorithm
9. Discussion and Results
9.1. Constant Jammer
9.2. The Impact of BSM Rats
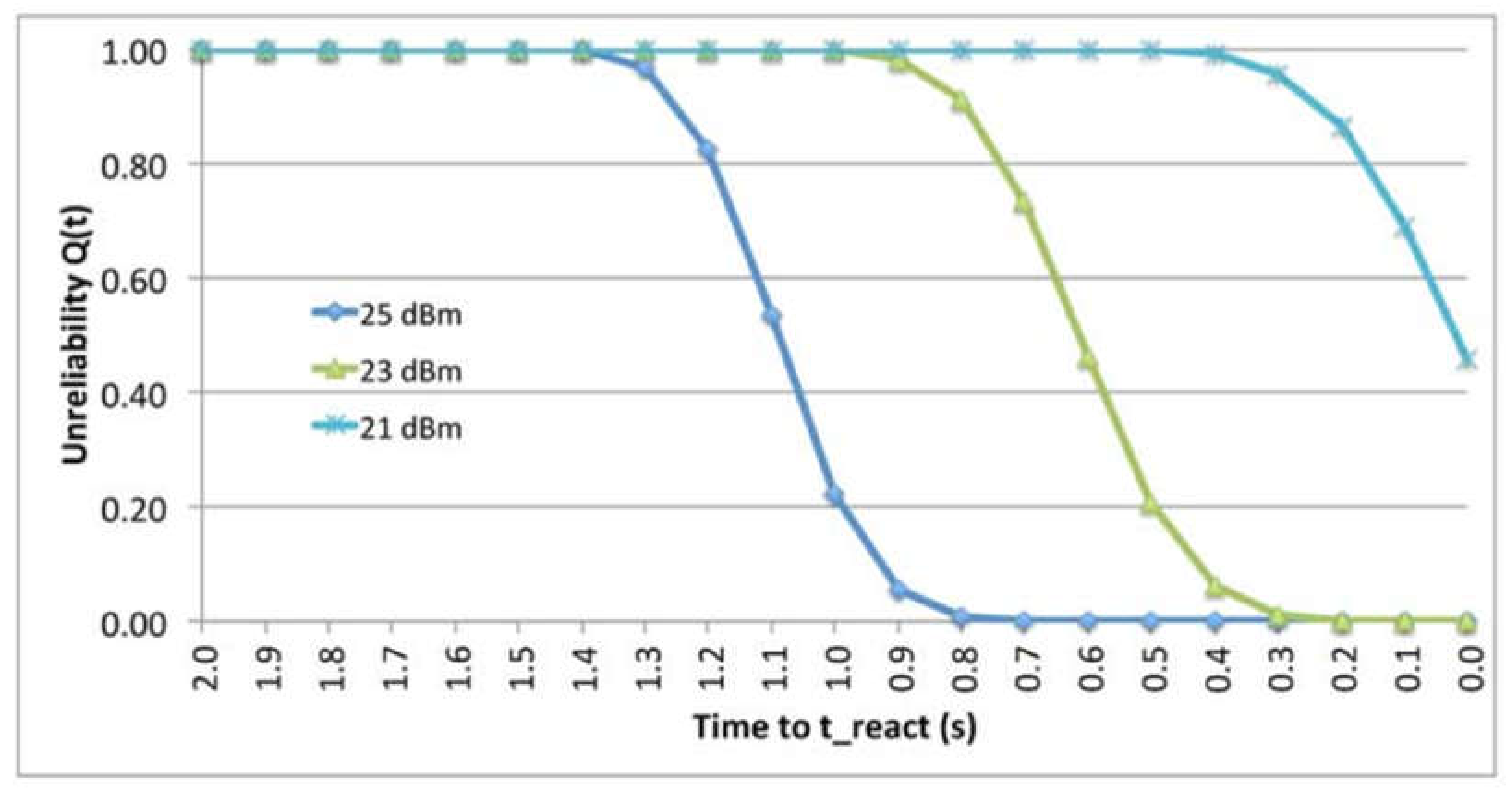
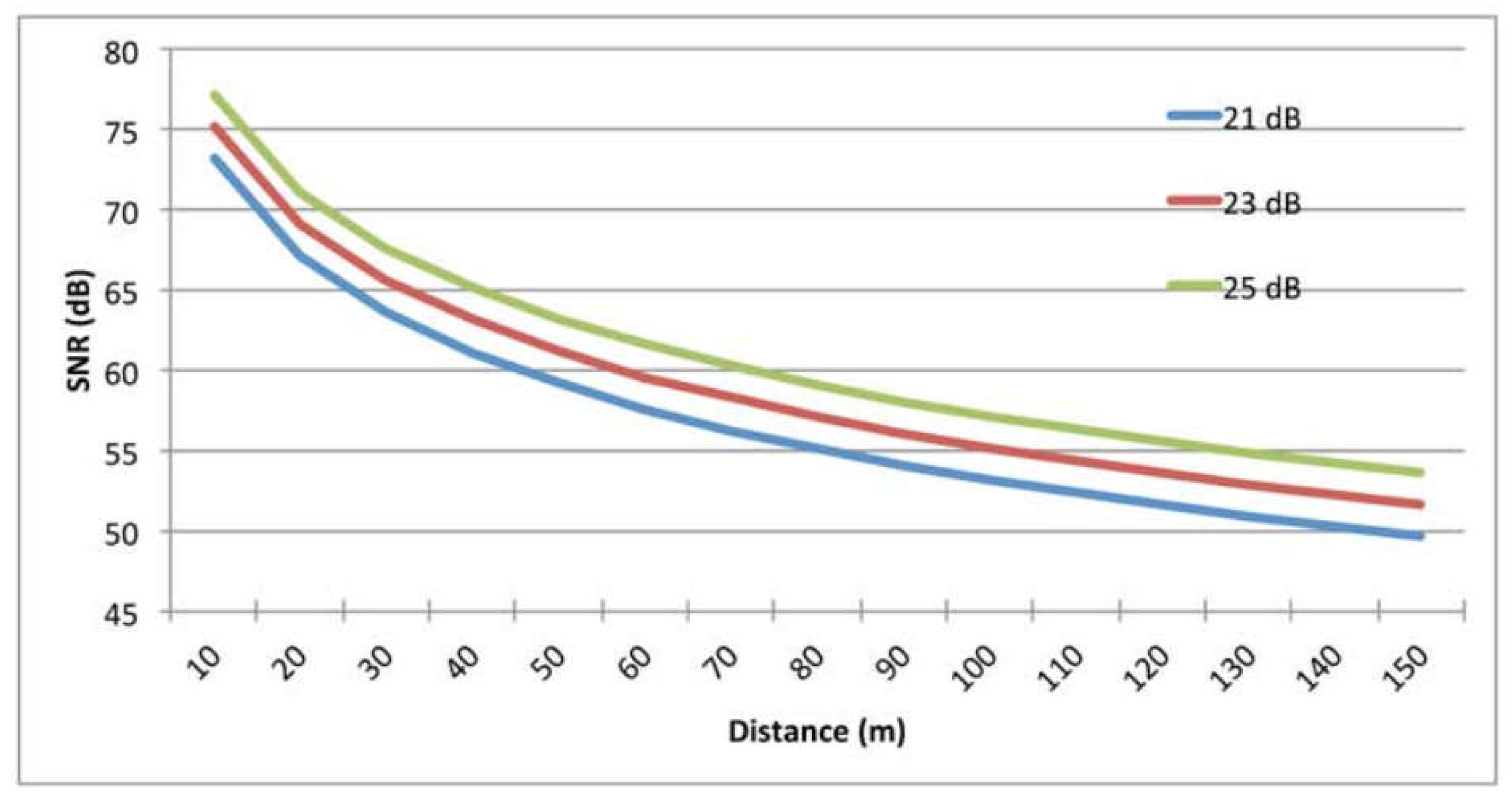
9.3. The effect of Transmission Power
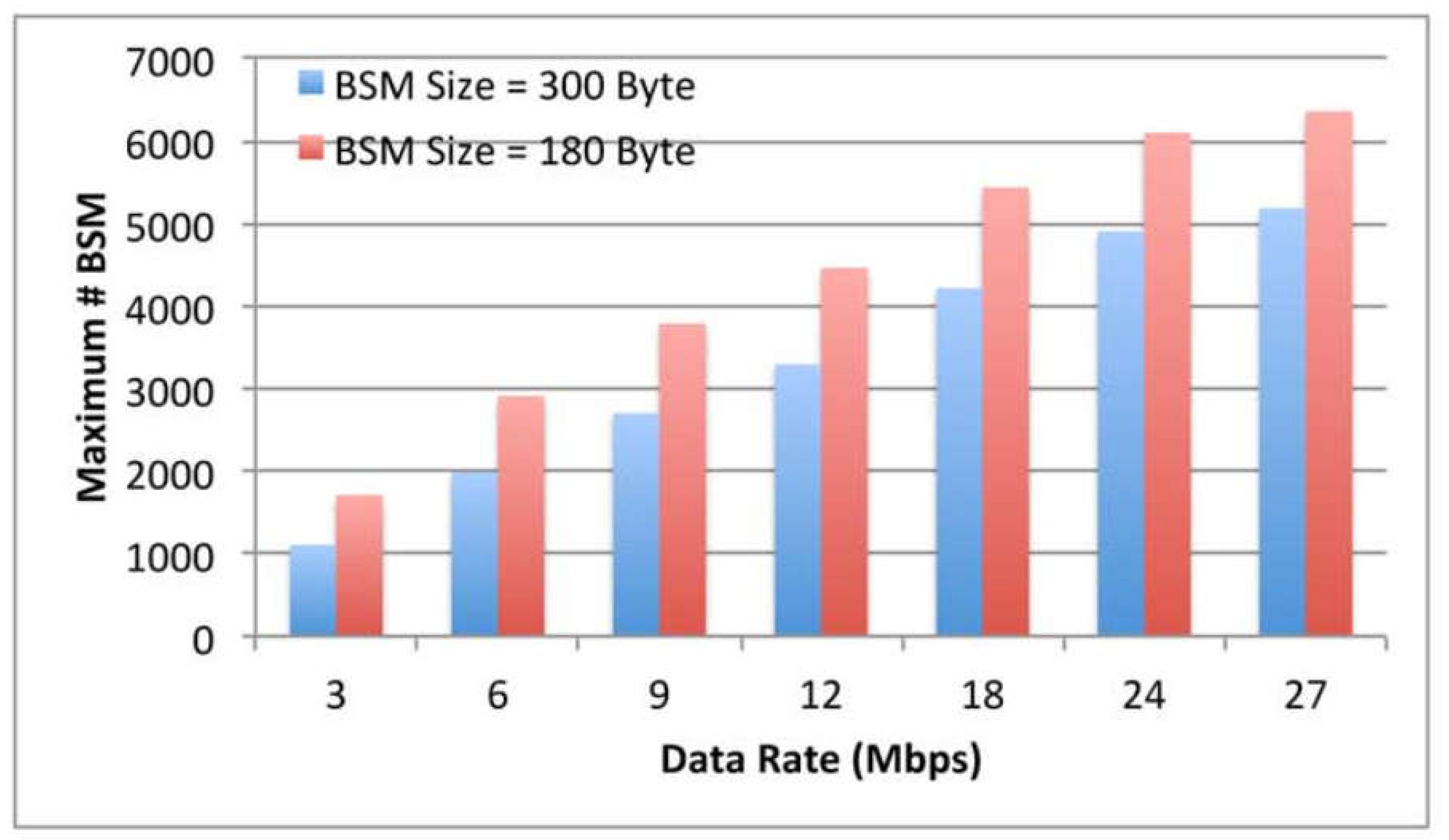
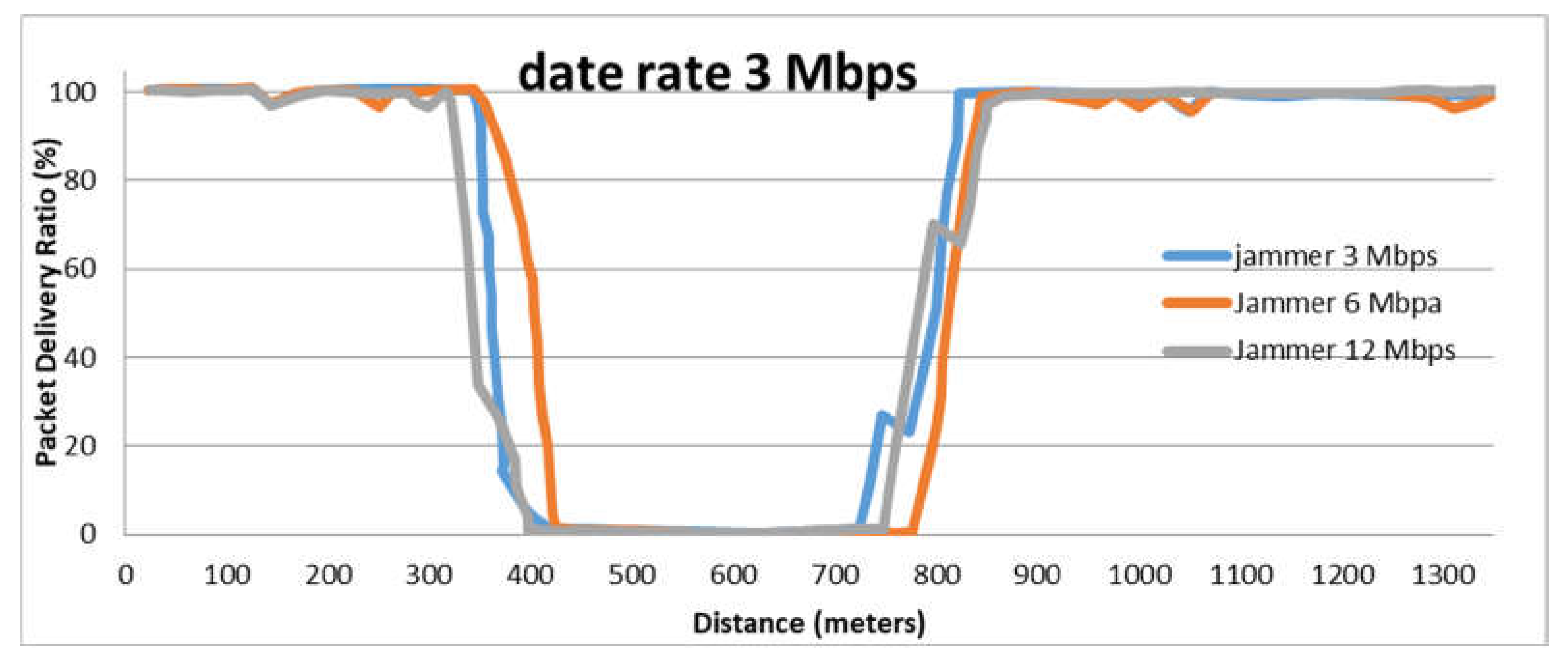
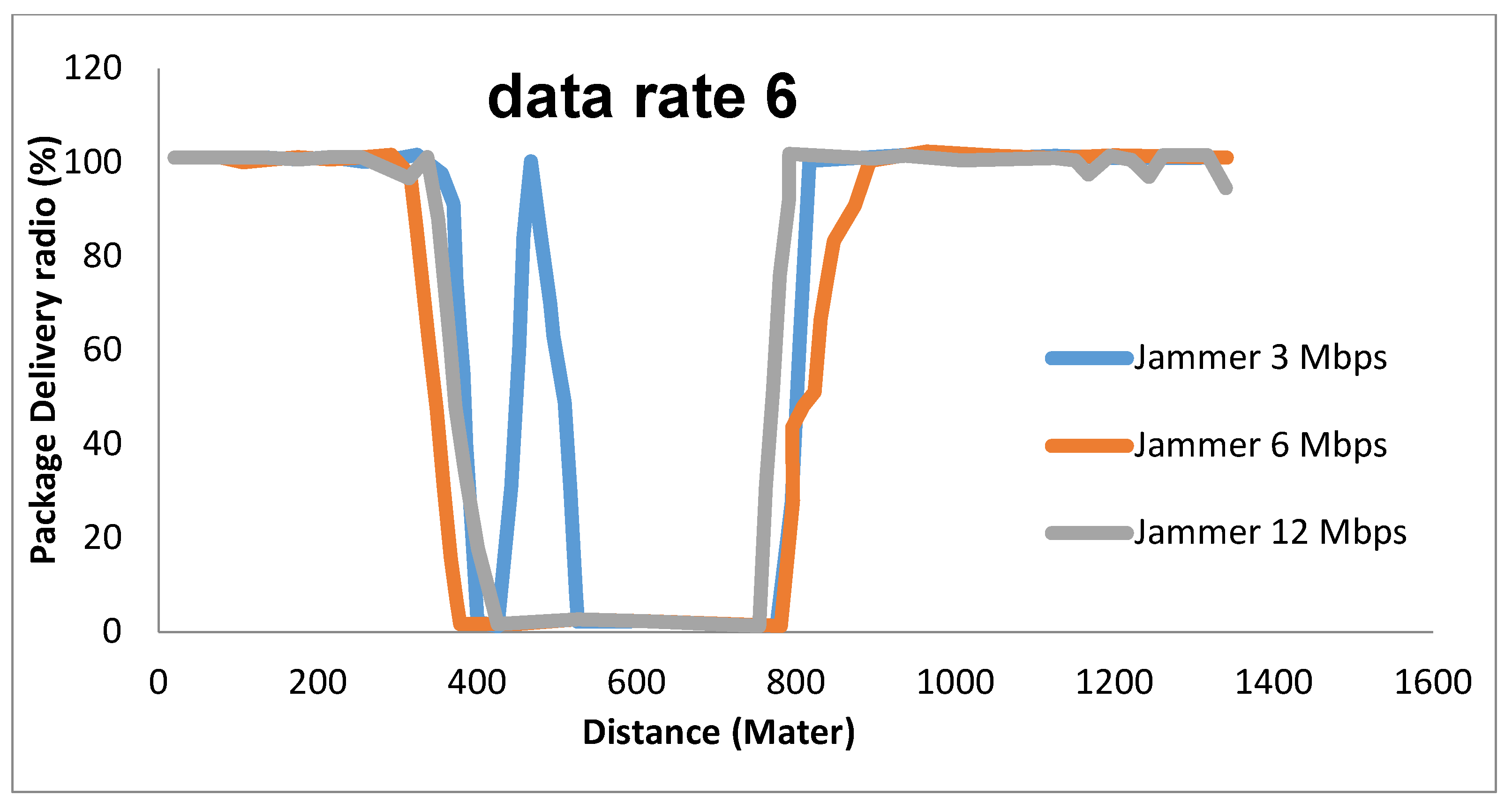
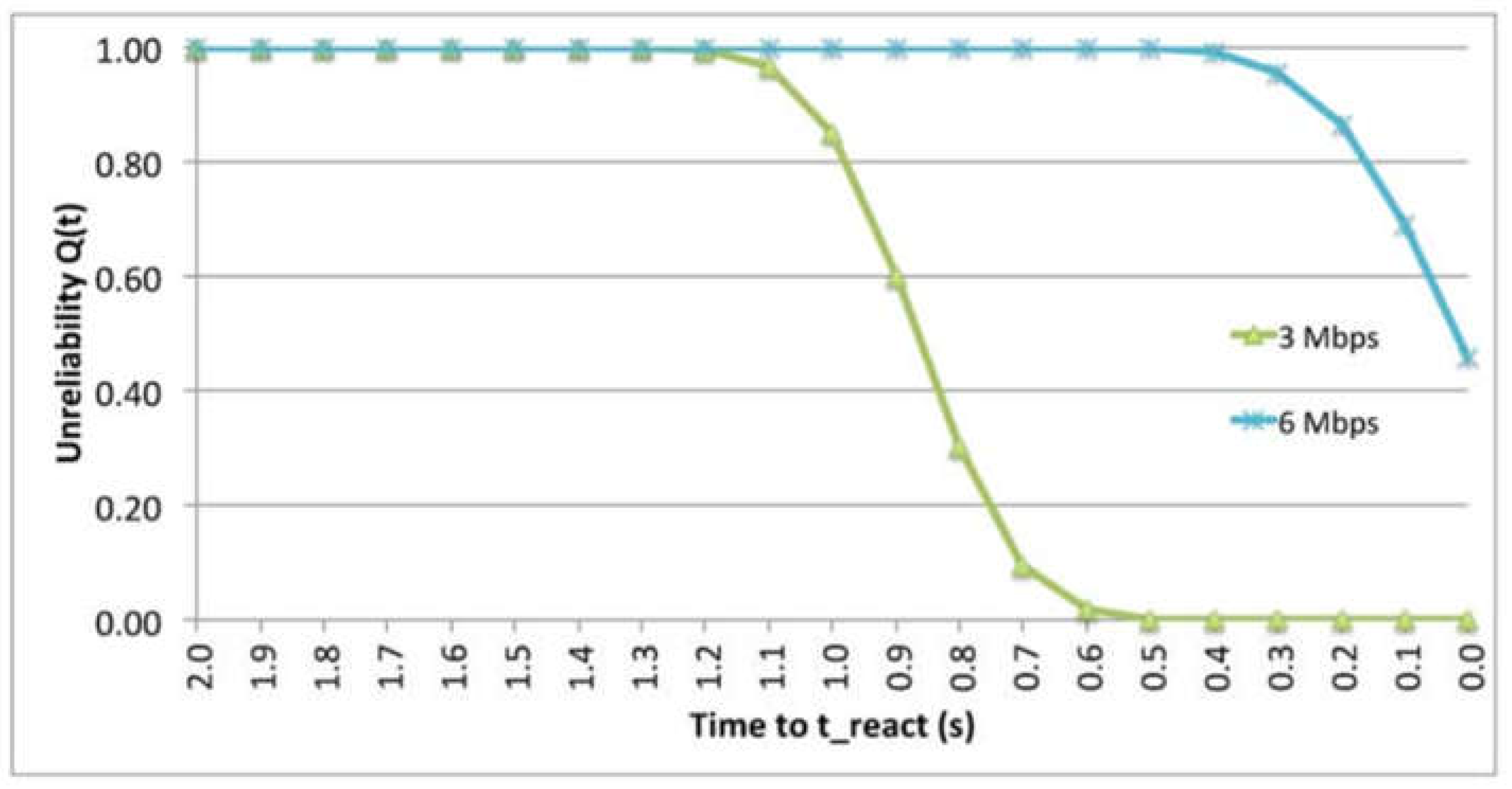
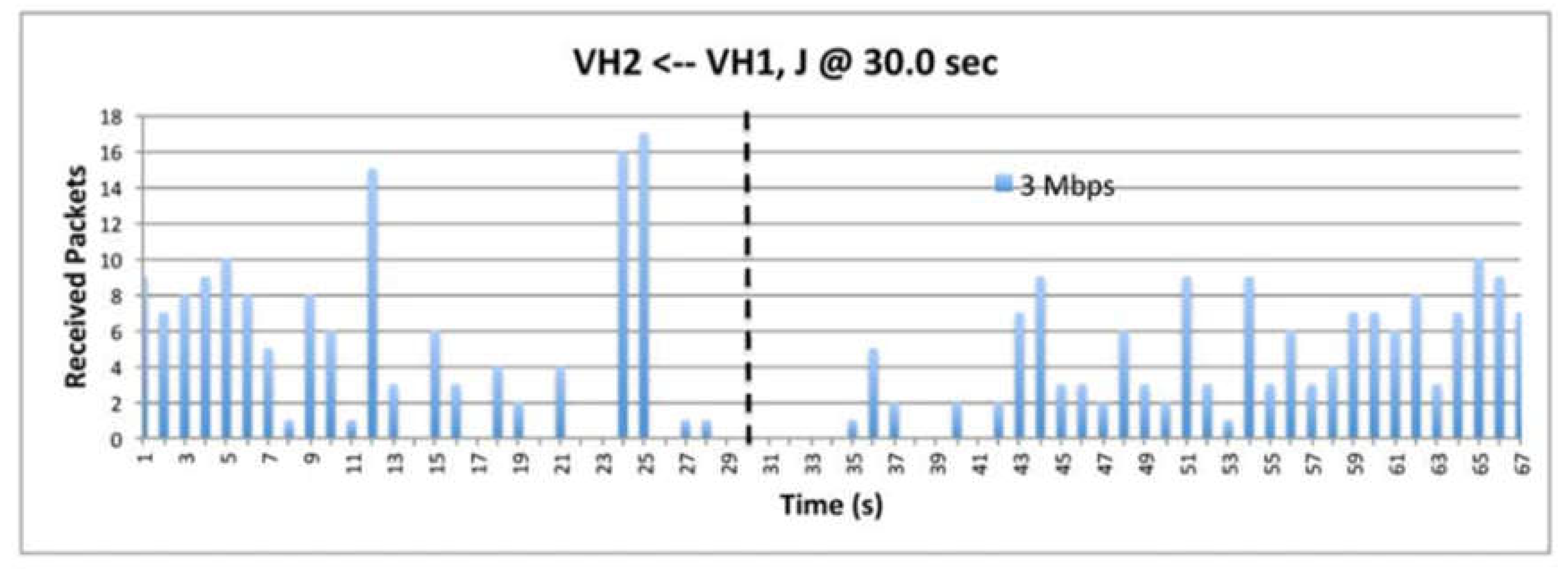
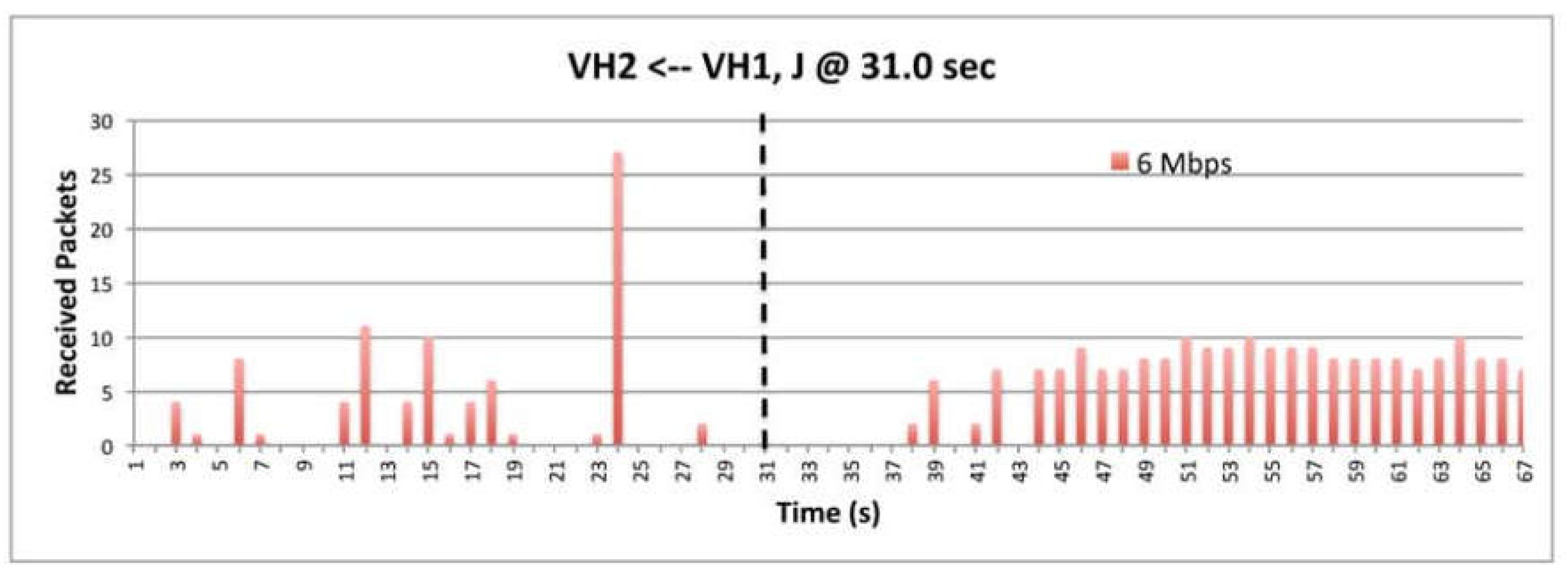
9.4. The effect of Data Rate
9.5. Deceptive Jammer
9.6. The Impact of BSM Rates
9.7. The Impact of Transmission Power
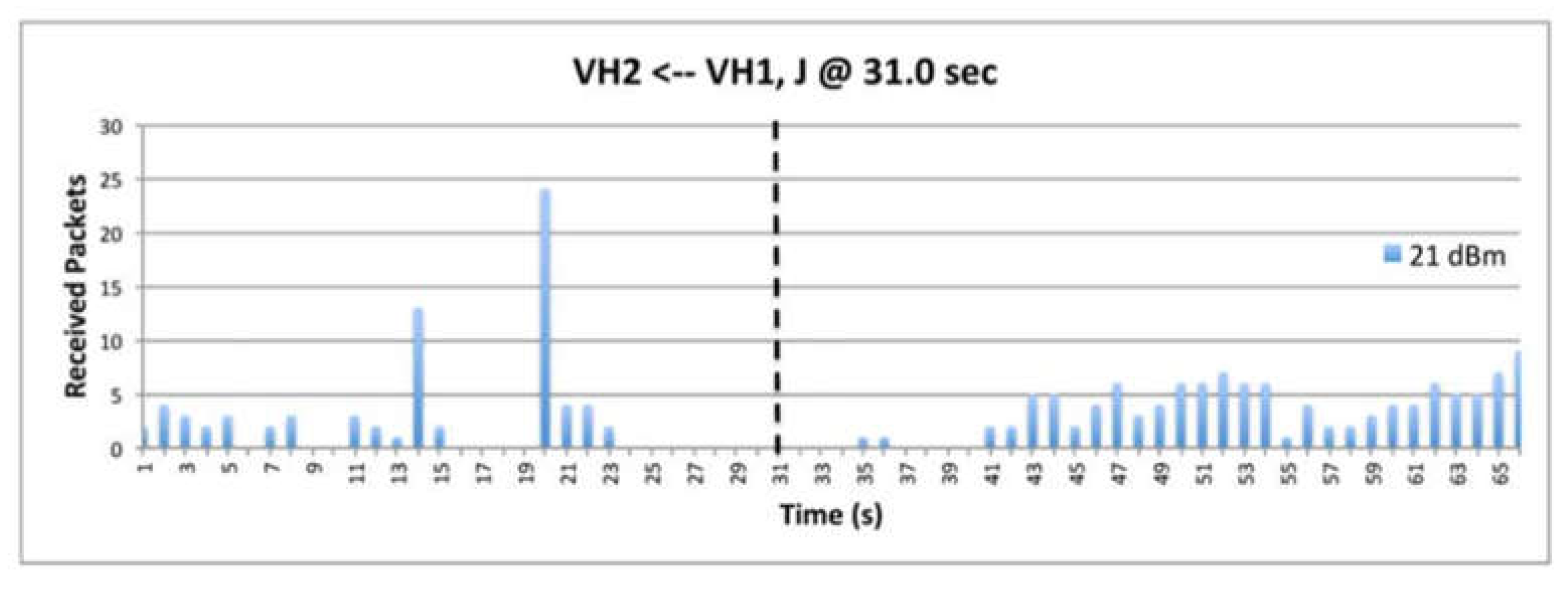
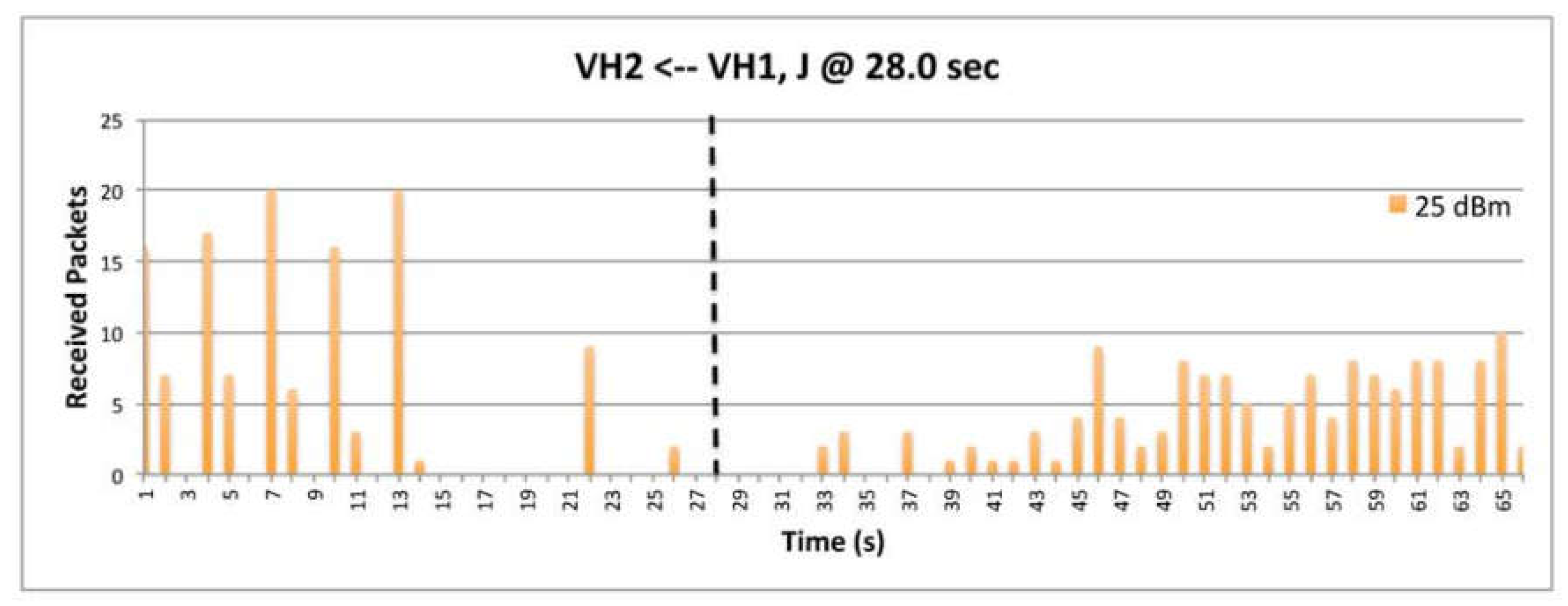
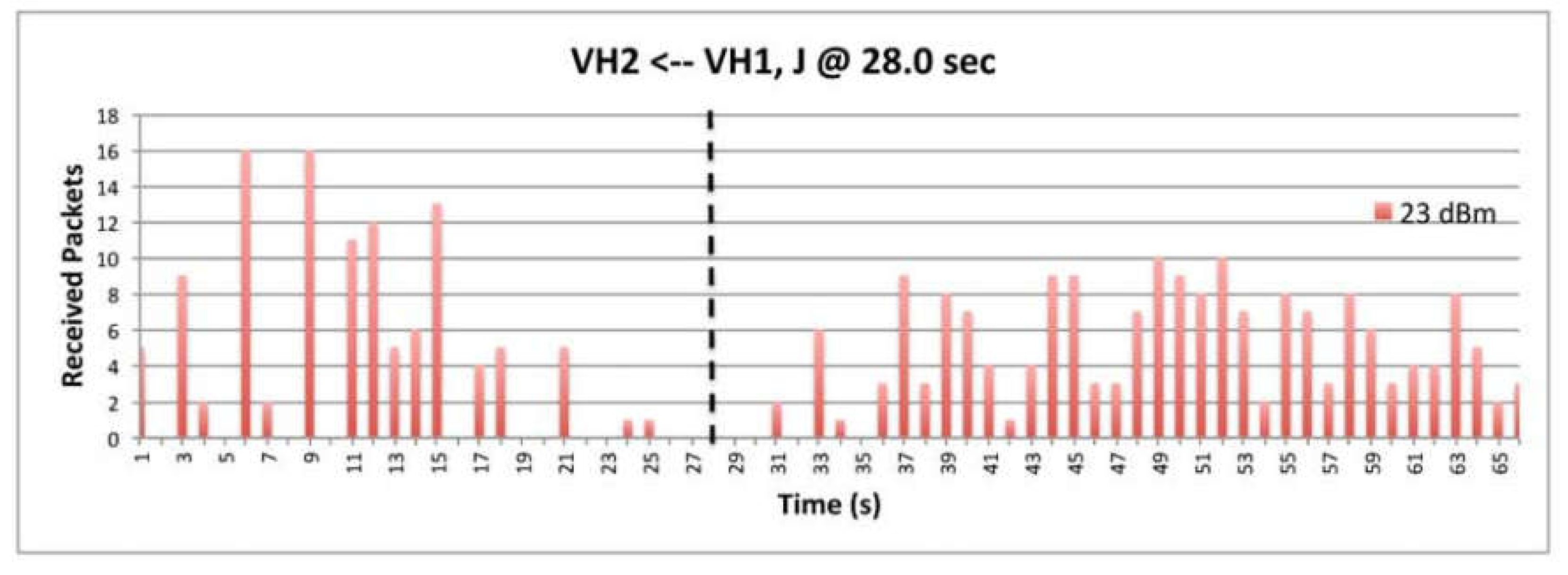
9.8. The Impact of Data
10. Conclusion
Author Contributions
Funding
Conflicts of Interest
References
- J. Puñal, Ó.; Pereira, C.; Aguiar, A. Experimental characterization and modeling of RF jamming attacks on VANETs. IEEE Trans. 2015, 64, 524–540. [Google Scholar]
- A. Devi, L.; Suganthi. Denial of Service Attacks in Wireless Networks. Case Jammers. Int. J. Comput. Sci. Mob. Comput. 2014, 3.
- M. Mohammad; Norrozila Sulaiman. A New Broadcast Algorithm to Optimize Routing Protocol in Mobile Ad Hoc Networks. J. Appl. Sci. 2013, 13.
- S. R.; A. LN. A Multi-channel Defense Against Jamming Attacks in Wireless Sensor Networks. In the Proceedings of the 3rd ACM Workshop on QoS and Security, 2007. .
- M. A.; R. Kieckhafer. Exploiting Omissive Faults in Synchronous Approximate Agreement. IEEE Trans. Comput. 2000, 49, 1031–1042. [CrossRef]
- T. Xu; W., Trappe, W., Zhang, Y.; Wood. The feasibility of launching and detecting jamming attacks in wireless networks. In the Proceedings 6th ACM Int. Symp. Mob. ad hoc Netw. Comput, 2005.
- C. C. SU; Hung min; HSU Shihpu. Mobile Jamming Attack and Its Countermeasure. In the proceeding of the Wireless Sensor Networks. dvanced Information Networking and Application Workshops, AINA W’ 07. 21st Int. Conf., 2007.
- A. Serageldin; A.; Krings. The impact of dissimilarity and redundancy on the reliability of DSRC safety applications. In the proceeding of 28th International Conference on IEEE In Advanced Information Networking and Applications Workshops (WAINA). 2014. 2014.
- S.J. Dedicated Short Range Communications (DSRC) Message Set Dictionary. Society of Automotive Engineers.
- L. Hamieh, A; Ben-Othman, J.; Mokdad. Detection of radio interference attacks in VANET. In the proceeding of Global Telecommunications Conference GLOBECOM, IEEE. 2009.
- A. E2213-03. Standard Specification for Telecommunications and Information Exchange Between Roadside and Vehicle Systems - 5 GHz Band Dedicated Short-Range Communications (DSRC) Medium Access Control (MAC) and Physical Layer (PHY) Specifications. 2018.
- J. Lyamin; N. Vinel; A. V.; Jonsson M; Loo. Real-Time Detection of Denial-of-Service Attacks in IEEE 802.11. Veh. Networks. IEEE Commun. Lett. 2015, 18, 110–113.
- J. Nguyen; A. T.; Mokdad, L.; Ben Othman. Solution of detecting jamming attacks in vehicle ad hoc networks. In the proceeding of the of the 16th ACM,” Int. Conf. Model. Anal. Simul. Wirel. Mob. Syst. 2013.
- Ayoob, A.A.; Su, G.; Al, G. Hierarchical Growing Neural Gas Network (HGNG)-Based Semicooperative Feature Classifier for IDS in Vehicular Ad Hoc Network (VANET). J. Sens. Actuator Netw. 2018, 7, 41. [Google Scholar] [CrossRef]
- J. G. O. Puñal; A. Aguiar. Characterizing RF Jamming in Vehicular Networks. In the proceeding of the ninth ACM international workshop on Vehicular inter-networking, systems, and applications, VANETs we Trust. 2012.
- J. O; L. Hamieh. Detection of Radio Interference Attacks in VANET. In the proceeding of IEEE Glob. Telecommun. Conf.2009.
- T. Xu; W. Trappe; Y. Zhang. The Feasibility of Launching and Detecting Jamming Attacks in Wireless Networks. In the proceeding of the 6th ACM Int. Symp. Mob. ad hoc Netw. Comput. 2005.
- M. J.; J. Lyamin; A. Vinel. Real-Time Detection of Denialof-Service Attacks in IEEE 802.11p Vehicular Networks. IEEE Commun. Lett. 2014, 18, 110–113. [CrossRef]
- J. B.-O; A.T. Nguyen; L. Mokdad. Solution of Detecting Jamming Attacks in Vehicle Ad Hoc Networks. In the proceeding of the 16th ACM Int. Conf. Model. Anal. Simul. Wirel. Mob. Syst. MSWiM. 2013.
- B. Sklar. Digit. Commun. Fundam. Appl, 2nd Ed. Prentice Hall PTR, 2011. .
- A. Systems. Available online: www.aradasystems.com (accessed on 22 08 2023).
- H. A.; A. Serageldin. On the Reliability of DSRC Safety Applications: A Case of Jamming, In the proceeding of the IEEE Int. Conf. Connect. VehExpo. 2013.
- A. S.; A. Krings. The Impact of Redundancy on DSRC Safety Application Reliability under Different Data Rates. In the proceeding of the Int. Conf. New Technol. Mobil. Secur..2014.
- A. S.; A. Krings. The Impact of . Dissimilarity and Redundancy on the Reliability of DSRC Safety Applications, In the proceeding of 28th Int. Conf. Adv. Inf. Netw. Appl. Work. 2014.
- D. S. R. C.; M. S. Dictionary. Dedicated Short Range Communications (DSRC) Message Set Dictionary, Society of Automotive Engineers, SAE J2735. 2009.
- DOT HS 811 492 A. U.S. Department of Transportation, NHTSA, Veh. Saf. Commun, Final Report, USA. 2011.
- W. B. Johnson. Design and Analysis of Fault-Tolerant Digital Systems. AddisonWesley Publ. Company, NewYork,USA. 1989.
- L. C.; B. Peng. A Wireless MAC Protocol with Collision Detection. IEEE Trans. Mob. Comput. 2007, 6, 1357–1369. [CrossRef]
- IEEE Standard for Information Technology--Telecommunications and Information Exchange between Systems - Local and Metropolitan Area Networks--Specific Requirements- Part 11, Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications," in IEEE Std 802.11.2021.
- T. S. M.I. Hassan; H.L.Vu. Performance Analysis of the IEEE 802.11 MAC Protocol for DSRC Safety Applications. IEEE Trans. Veh. Technol. 60, 3882–3896. [CrossRef]
- G. J.; K. Rumar. Drivers? Brake Reaction Times, in HumanFactors. The Journal of the Human Factors and Ergonomics Society 1971, 1, 23–27.
- Amendment of the Commission’s Rules Regarding Dedicated Short-Range Communication Services in the 5.850-5.925 GHz Band (5.9 GHz Band). Available online: www.fcc.gov (accessed on 22 08 2023).
- A. Serageldin, A.; Krings. The impact of redundancy on DSRC safety application reliability under different data rates. In the proceeding of the 6th International Conference on New Technologies, Mobility and Security (NTMS), Dubai, United Arab Emirates, 2014.
- ASTM E2213-03 Standard Specification for Telecommunications and Information Exchange Between Roadside and Vehicle Systems - 5 GHz Band Dedicated Short Range Communications (DSRC) Medium Access Control (MAC) and Physical Layer (PHY) Specifications. Available online: www.standards.its.dot.gov (accessed on 22 08 2023).
- M. S. R.; A. R. I. R. A. Shafik. On the Extended Relationships Among EVM, BER and SNR as Performance Metrics. In the proceeding of the Int. Conf. Electr. Comput. Eng. ICECE. 2006.
- A. Ayoob; G. Khalil, L. Yingzhuang; M. Chowdhury; T. Al. Efficiency Broadcast Base Safety Message BSM Through VANET Based on Transmit Packet Coding (TPC). In the proceeding of the IEEE 2nd Global Conference on Life Sciences and Technologies (LifeTech), Kyoto, Japan. 2020.
- Ayoob, A.; Khalil, G.; Chowdhury, M.; Doss, R.. Intrusion detection system classifier for VANET based on pre-processing feature extraction. In the proceeding of the Future Network Systems and Security 5th International Conference, FNSS2019, Melbourne, VIC, Australia. 2019.

| Average number of back-off slots, W | I6 |
| Transmission range, R | 6oo m |
| DIFS time | 64 micro s |
| Data rate | 6 Mbps |
| BSM rates | IO, 2o and 3o BSM/s |
| BSS size | i8o Bytes |
| Vehicle density | z-zoo vehicles/km |
| Vehicle speed | 16.6 m/s |
| OBU | Arada Systems LocoMate Classic |
| Length test range | 1.53 km |
| Test range | Straight of 2-lane road |
| Rate of BSM | 10 BSM/s (the BSM for every 100ms) |
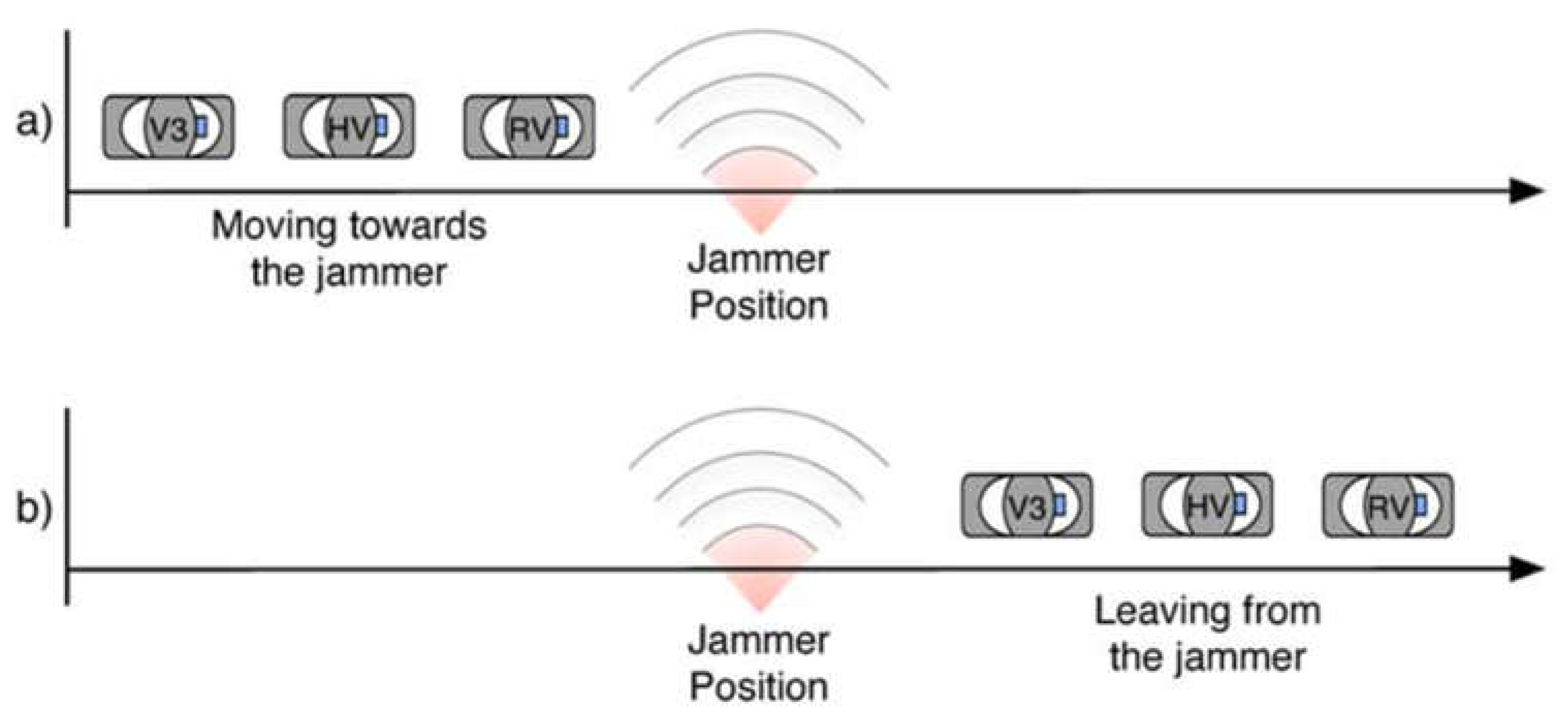
| Jammer position | 700 m from starting point |
| Effective bandwidth | 8.3 MHz |
| Channel | Safety Channel 172 |
| Rate of Data | 6and 3 Mbps |
| Power Transmitter | 19 dBm |
| Data rates jammer | 3, 6,, 12 Mbps |
| Jammer power | 18 dBm |
| OBU Model | Arada Systems LocoMate Classic |
| Vehicle speed | 20 m/s |
| Range test | Two lines for the road |
| Test range length | 1000 m |
| Jammer position | 500 m from starting point |
| BSM generation | 10,20 and 40 BSM/s |
| Channel | Safety Channel 172 |
| Effective bandwidth | 8.3 MHz |
| Transmitter power | 21,23 and 25 dBm |
| Data rate Transmission | 3 and 6 Mbps |
| Data rate Jammer power | 6 Mbps and 18 dBm |
| Deceptive Jammer (Field Experiment} | BSM /s | Power (dBm) |
Data Rate (Mbps) |
||||||
| 10 | 20 | 40 | 21 | 23 | 25 | 3 | 6 | ||
| Recovery Time (Seconds) | 12.0 | 9.0 | 9.0 | 9.0 | 9.0 | 7.0 | 10.0 | 11.0 | 12.0 |
| Distance (meters) |
145 | 115 | 125 | 106 | 68.5 | 120 | 125 | 150 | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





