Submitted:
09 July 2023
Posted:
10 July 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Contributions and Arrangement
- A shared PRM codebook that embeds zero patterns in the second-order RM codes according to a binary vector space partition principle is employed as the inner codebook for the coded compressed sensing protocol. On this basis, we propose an enhanced algorithm called the "list PRM projection algorithm" that uses a list of candidates to hinder error spreading in each layer detection.
- As for the multi-sequence scenario, an iterative list PRM projection algorithm is proposed. More specifically, except for the user’s information during the current loop, we consider all signals as interference. We remove the interference in priority and then employ the proposed list projection algorithm to recover the PRM sequence. The PRM estimations are then inserted into the channel estimator to enhance precision. After that, the modified channel estimations are utilized in the subsequent iteration to improve PRM detection further. As a result, the proposed iterative list PRM projection algorithm offers significant advantages regarding the convergence rate.
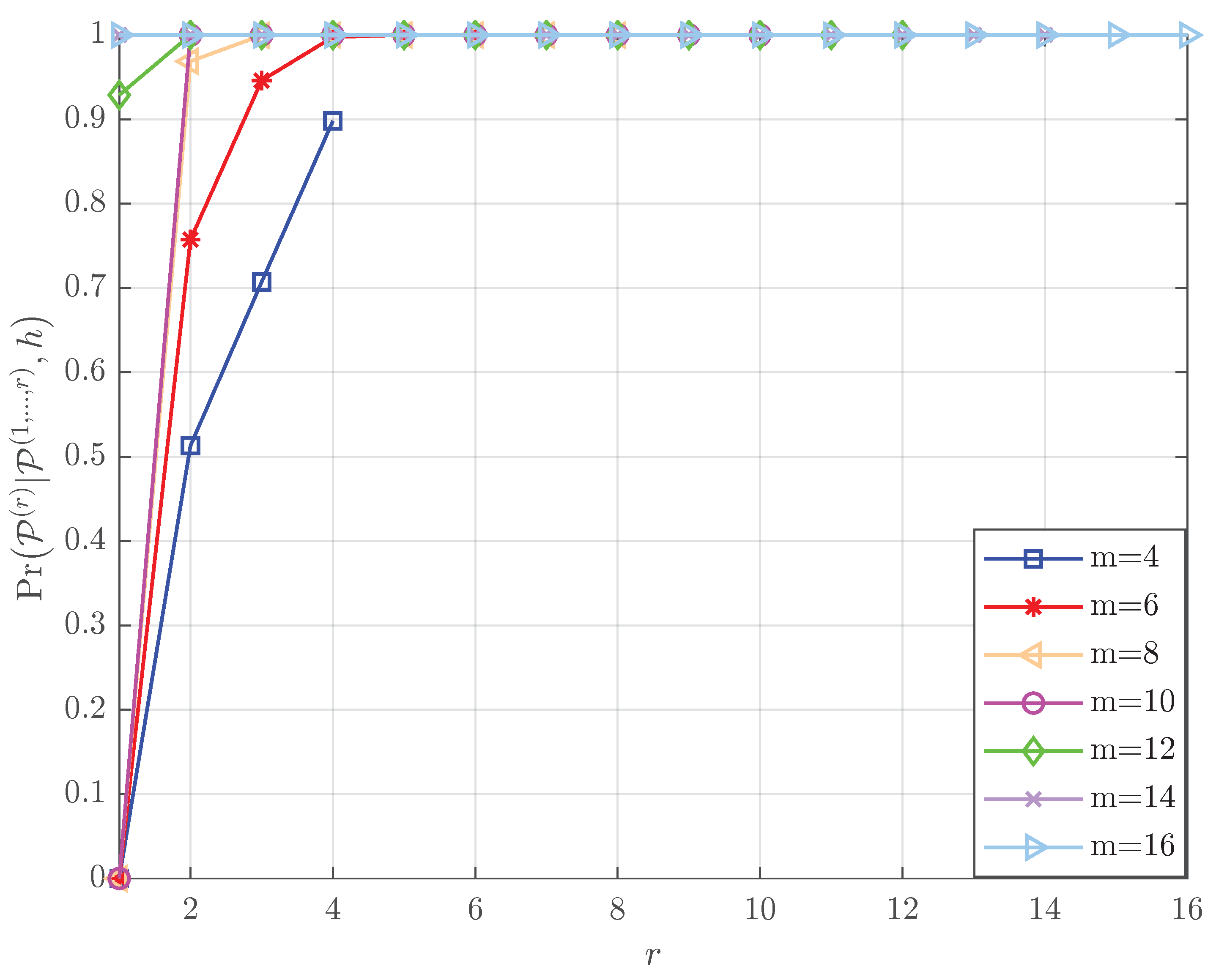
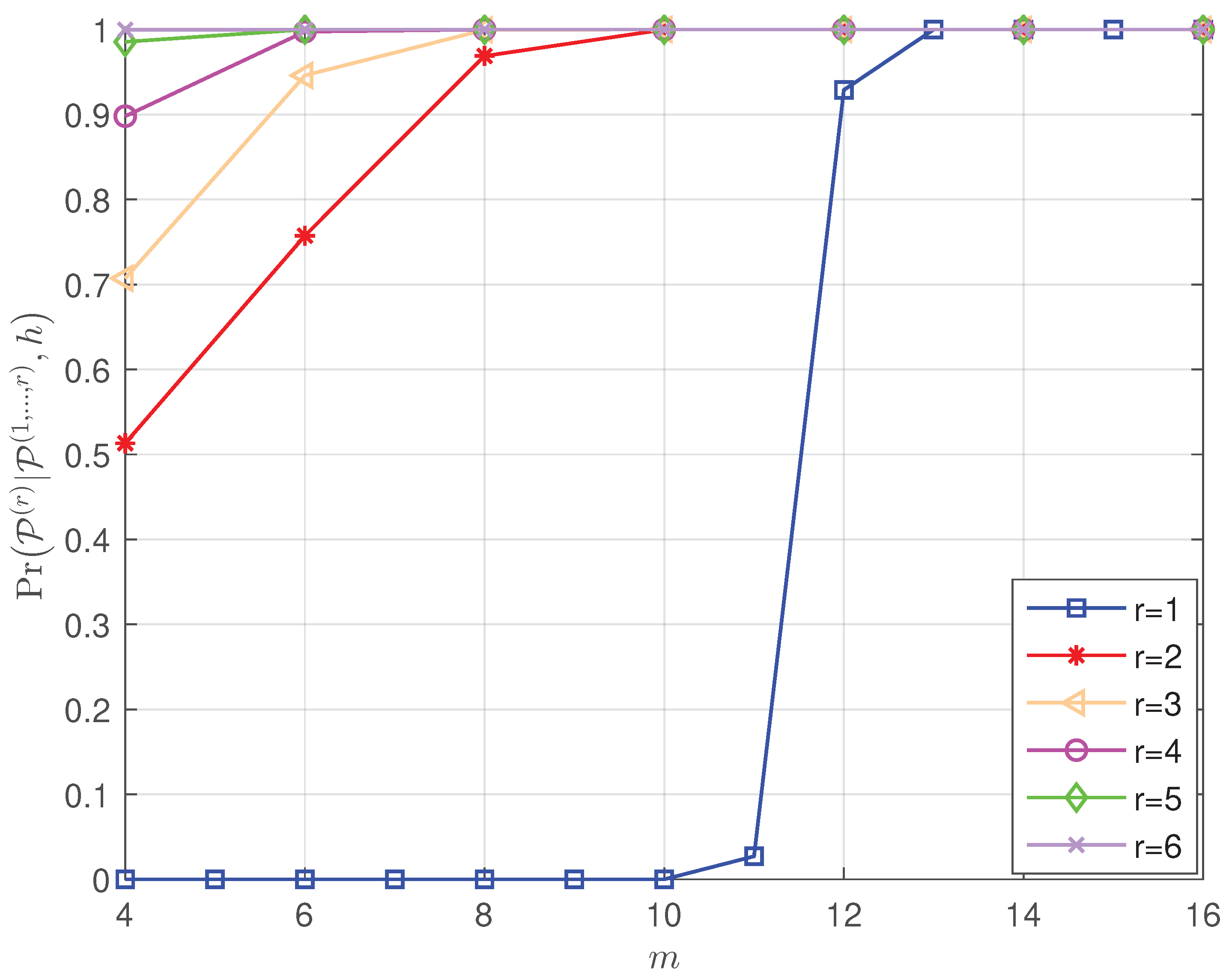
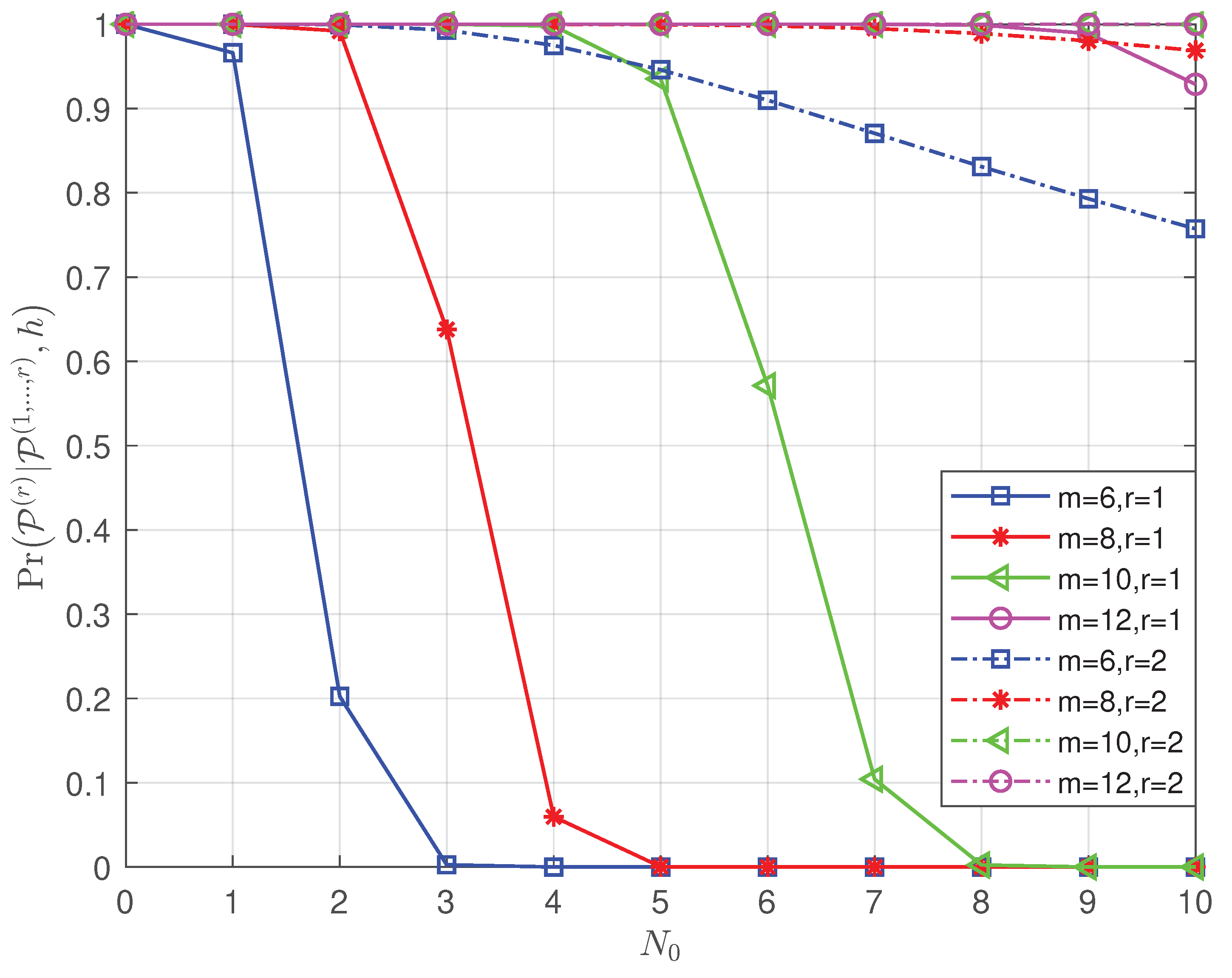
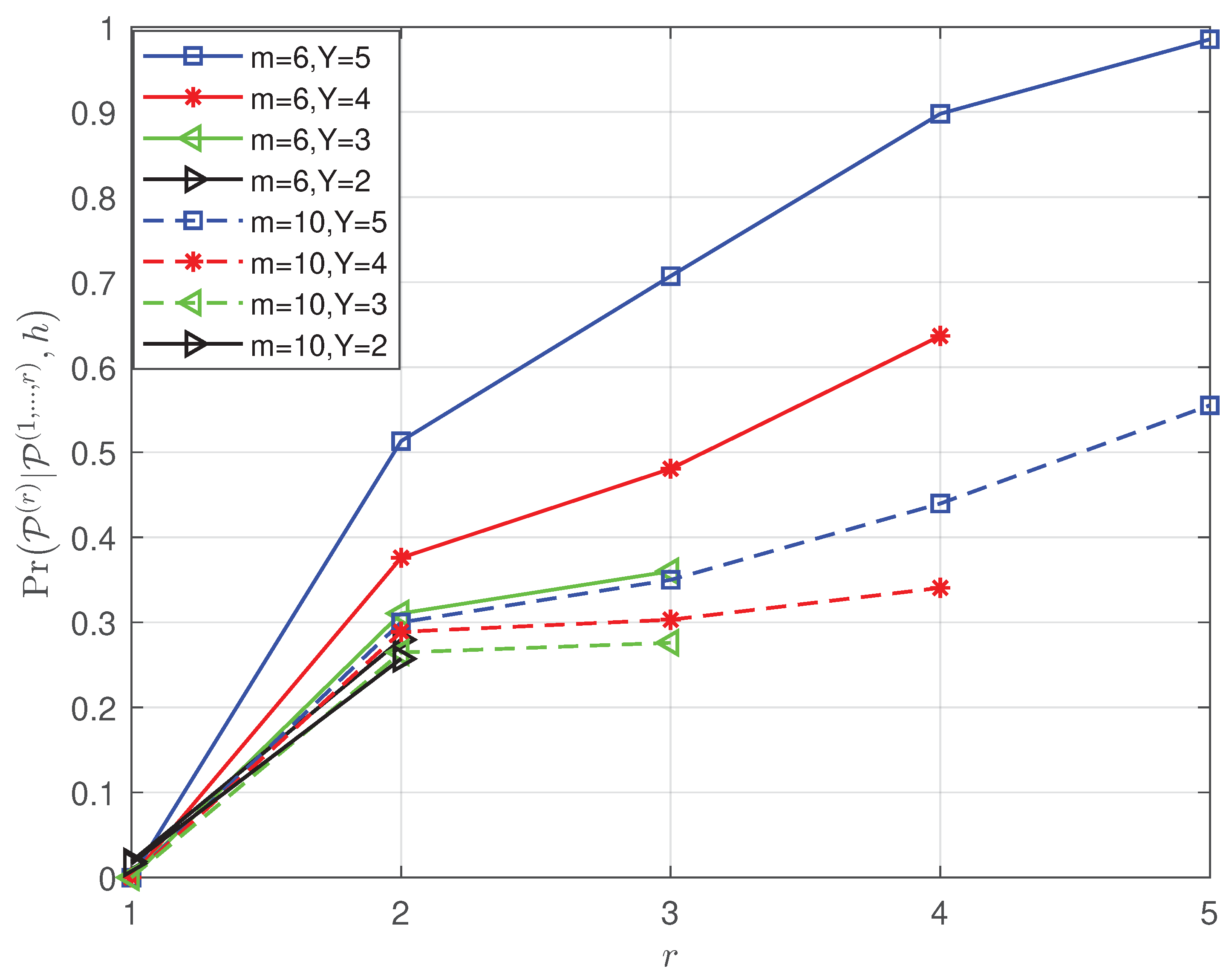
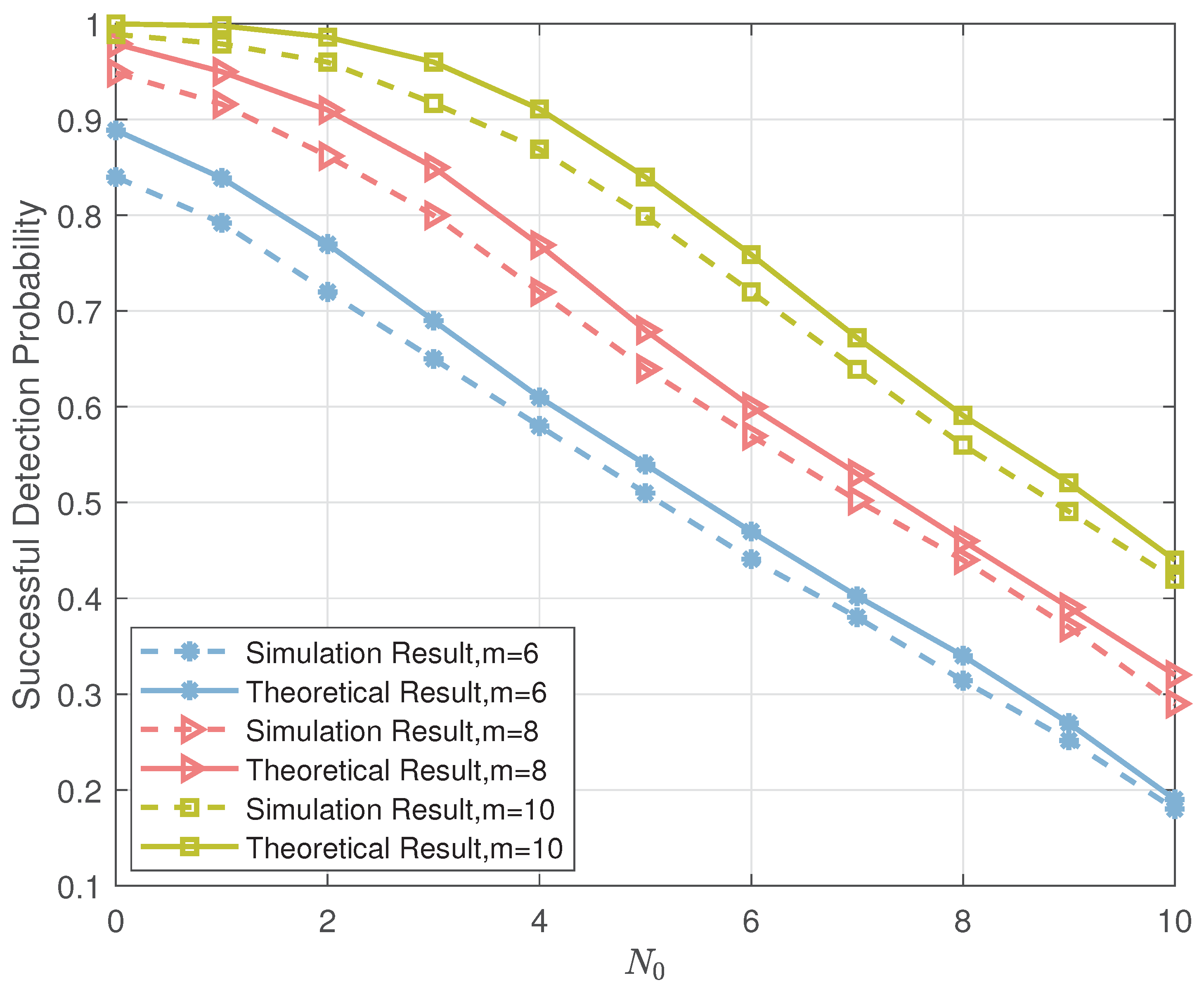
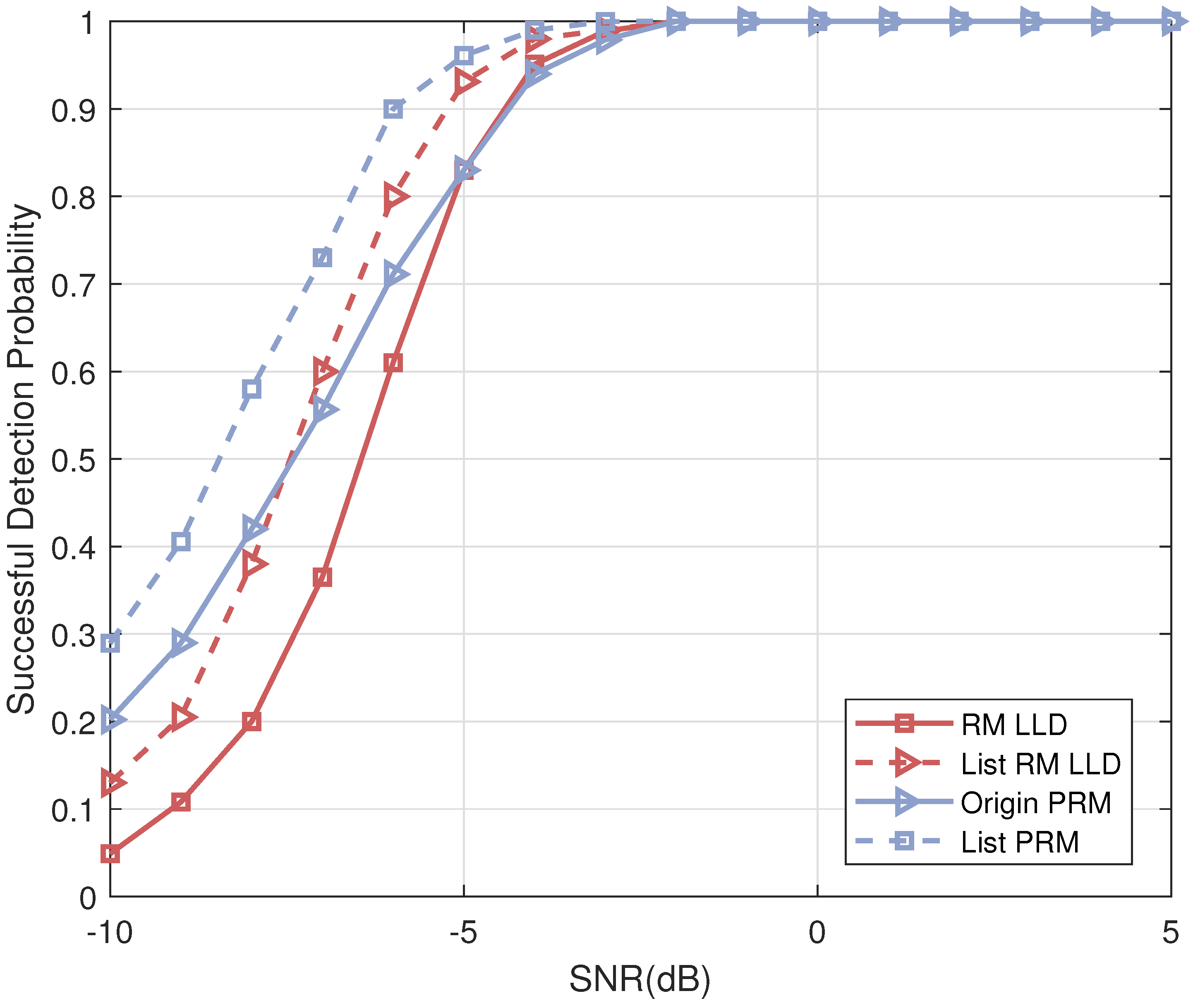
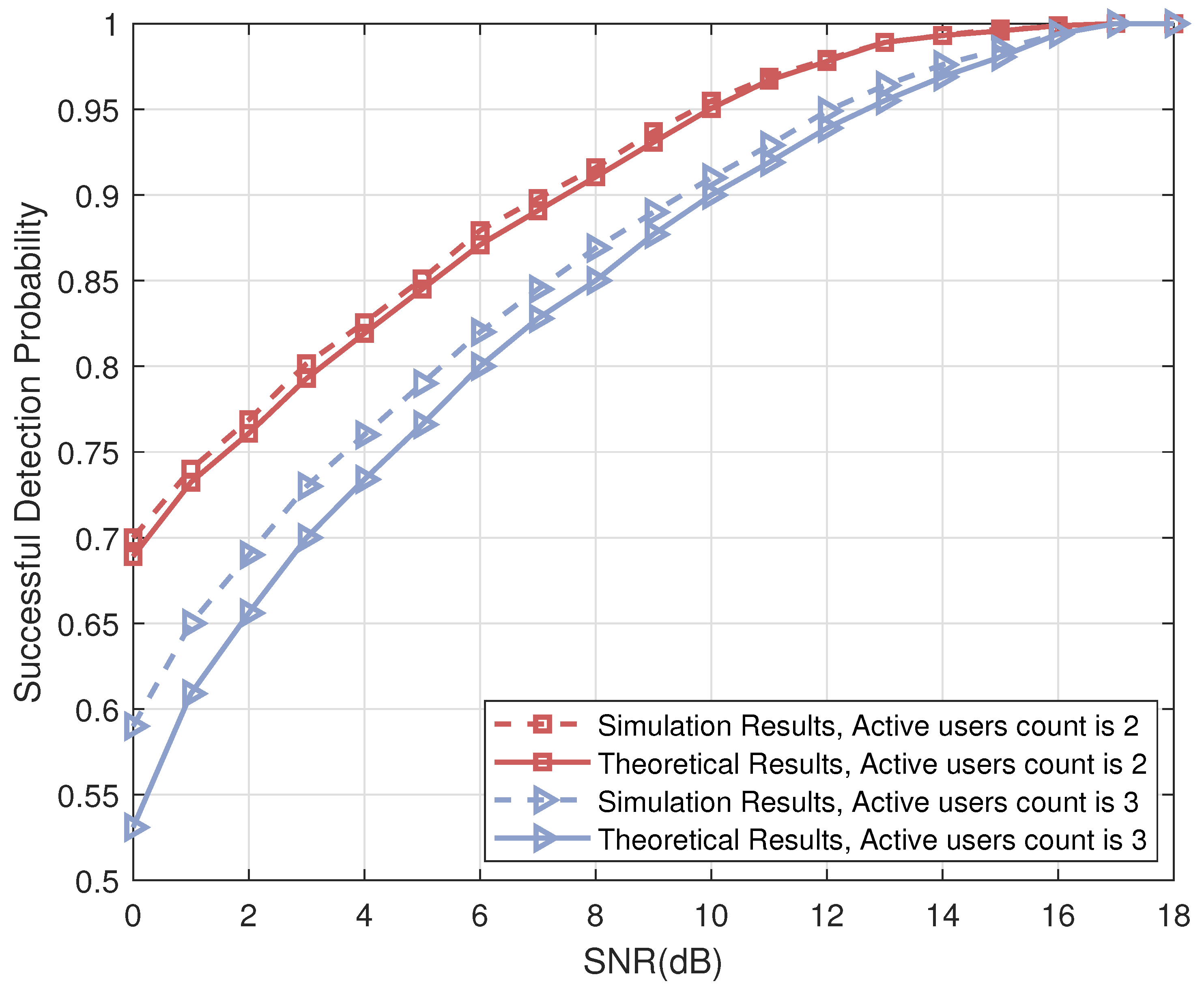
- The theoretical successful detection probabilities of the proposed list projection and the iterative list projection algorithms are analyzed mathematically, and the results demonstrate that: (i) the factors that affect the efficiency of the list PRM projection algorithm are shown in the simulation results, which validate that the recovery reliability of the first few layers is crucial to the whole performance (see Figure 1); (ii) simulation results further explore the effect of the relation between rank and m for PRM sequence properties on the theoretical successful detection probability (see Figure 2, Figure 3 and Figure 4); (iii) we verified that the theoretical results are consistent with the simulation results (see Figure 5 and Figure 7).
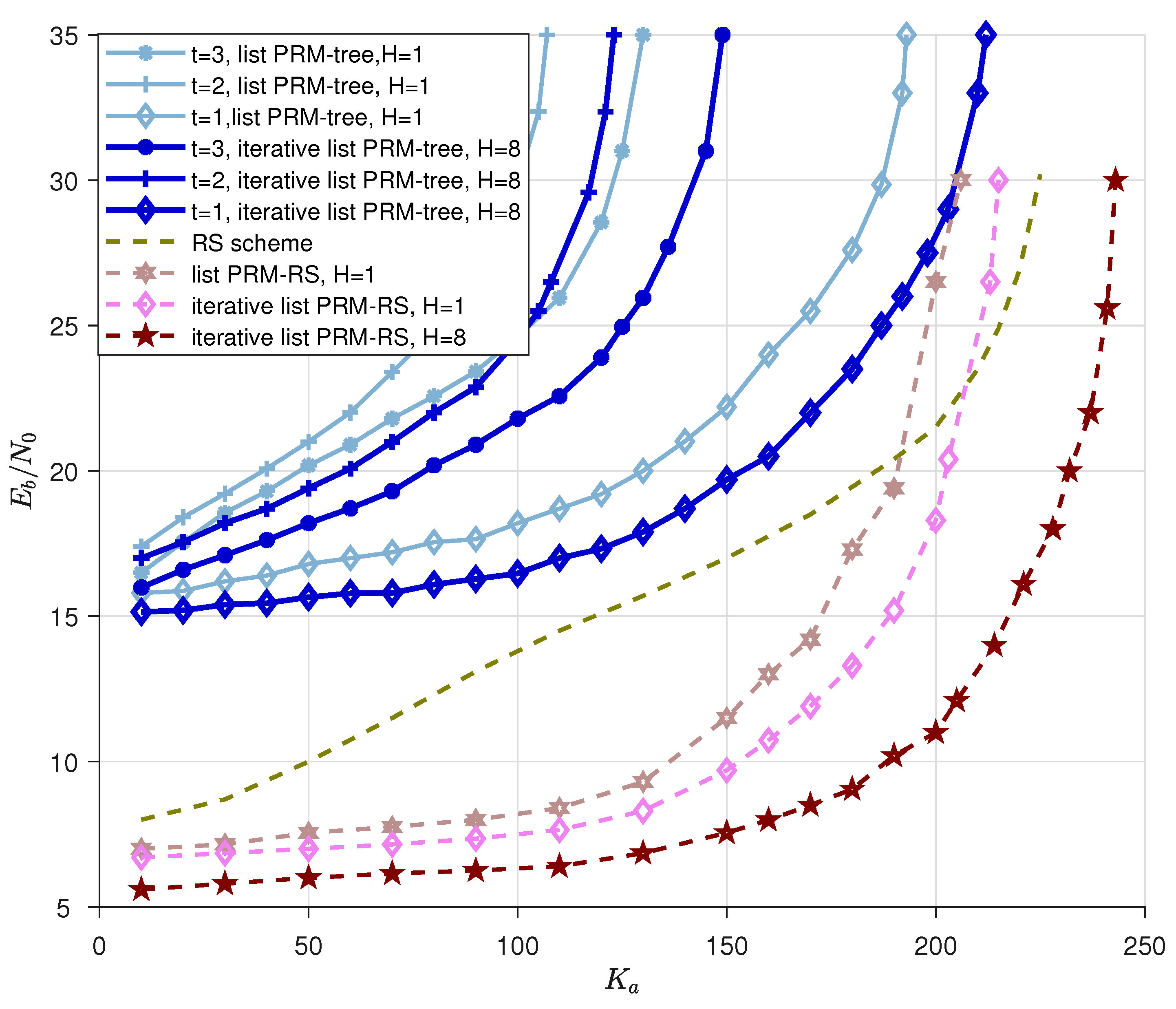
- We substitute the inner decoder of the scheme [33] with the proposed iterative list PRM projection algorithm. Simulations of the quasi-static Rayleigh fading multiple-access channel (MAC) are performed numerically (see Figure 8), and we conclude the observations as follows: (i) the proposed scheme is superior to the OMP-based inner codes detection, i.e., the chance of successful recovery is significantly improved since the PRM detector and channel estimator share information, and the negative impacts can be further reduced by eliminating those sequences that are incorrectly detected in each operation; (ii) by increasing the count of candidates in the first few layers, we can boost the origin PRM projection algorithm’s performance, which further confirms the above proof of importance for ensuring the reliable recovery of the first few layers; (iii) the simulation results of the overall URA system confirm that the packetized URA with the proposed iterative list projection detection works better than benchmarks in terms of the number of active users it can support in each slot and the amount of energy needed per bit to meet an expected error probability.
1.2. Conventions
2. System Model
2.1. Patterned Reed-Muller Sequence
2.2. Detection Algorithm of Multi-PRM Sequence
3. Iterative List PRM Projection Algorithm-based Inner-Code Detector
3.1. List PRM Projection Algorithm
 |
3.2. Iterative List PRM projection Algorithm
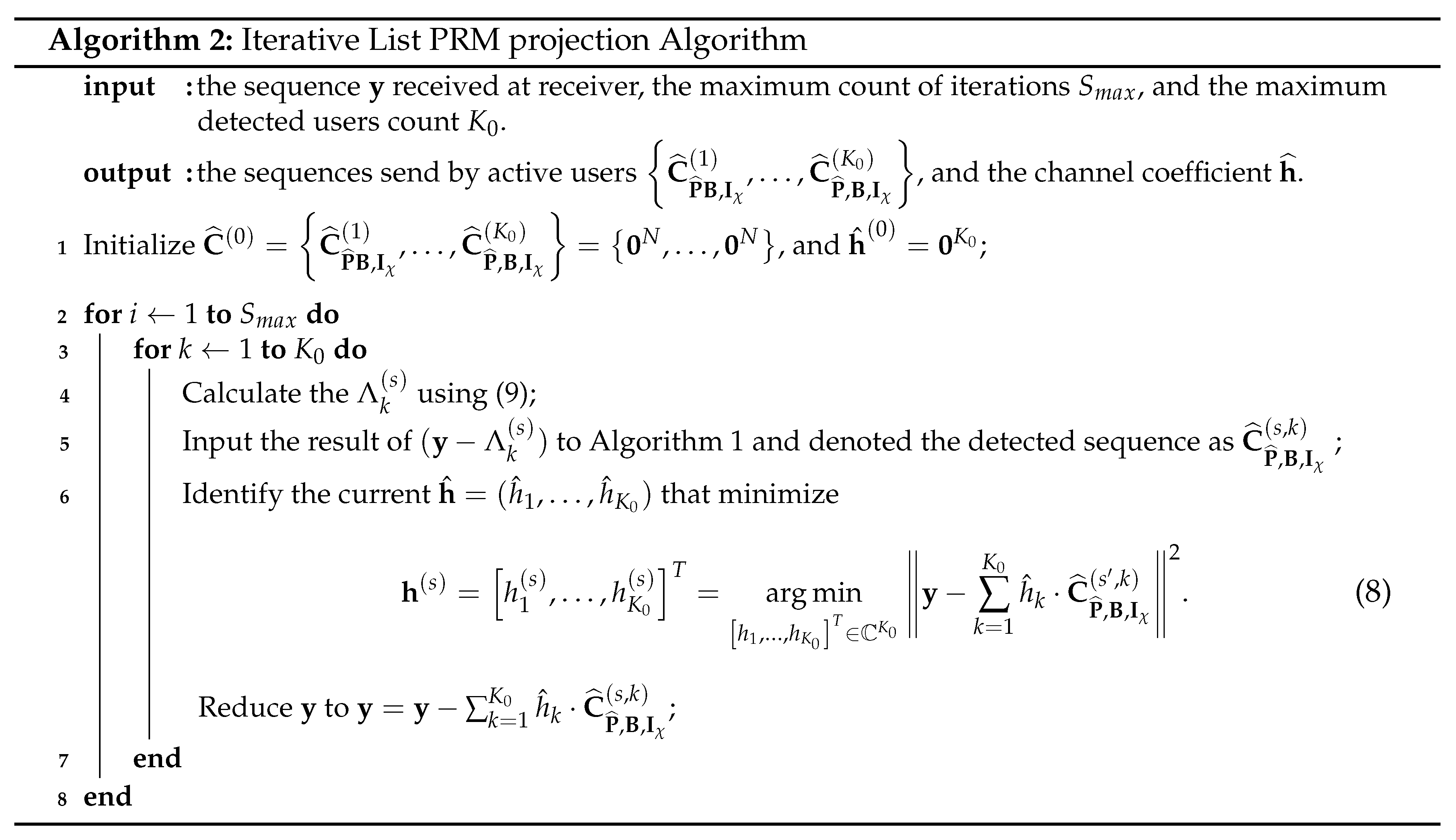 |
4. Performance Analysis
4.1. Successful Recovery Probability of the List PRM Projection Algorithm
- Assume that the PRM code is of full rank with , when m and are given, as increases from 1 to m, the value of increases (Figure 1). The results illustrate the properties of the projection algorithm: if the first few layers are error-free, the remaining layers are highly likely to be recovered correctly. Besides, a further conclusion can be drawn by observing the above proof that indicates that the noise power in each layer decreases exponentially as increases, leading to the successful recovery probability of the vector increasing layer by layer. Overall, the recovery reliability of the first few layers of the layer-by-layer PRM projection algorithm is crucial to its performance. This motivates us to increase the number of candidate paths in the first few layers to obtain better detections.
- As shown in Figure 2, when , and are given, increases as m increases, which shows that we can improve the performance of the PRM sequence detection algorithm by increasing the length of the PRM sequence.
- Figure 3 gives the variation of with for fixed , m and . It is clear that as increases, the Signal-to-Noise Ratio (SNR) decreases, resulting in decreases consequently.
- Figure 4 gives the variation of with for fixed , m and : the larger indicates the better performance under the same m, and this result is consistent with the fact that a greater signal power will result in a greater signal-to-noise ratio. Furthermore, the larger the m, the worse the performance under the same layer , indicating that the closer to m, the better the performance will be.
4.2. Successful Recovery Probability of the Iterative List PRM Projection Algorithm
- in the first instance, sequence a is detected successfully firstly, which has a chance of ;
- in the second instance, sequence b is detected in priority with the probability of , followed by sequence a is detected from the substracted signal with the probability .
5. Simulation Results
5.1. Performances of the Algorithms 1 and 2
5.2. Iterative List PRM Projection Algorithm-based Slot-controlled URA
- as for all "List PRM-tree" schemes, since the outer-code length is suitable for scheme and for cases, the former case ( case) can accommodate more active users than owing to a smaller number of simultaneous appearances in each slot (the outer code length affects the probability of appearance over slots. See more setup details in [23]). Besides, a higher t for the outer code increases performance when the inner code has the same length. Therefore, is superior to Furthermore, when comparing the curves of "list PRM-tree" and "iterative list PRM-tree", we conclude that the enhanced inner code with the proposed iterative list projection algorithm can help the entire system lower the energy-per-bit requirement to meet a target error probability as well as boost the ability to accommodate more users’ transmission.
- Figure 8 illustrates how the "iterative list PRM-RS, " curve outperforms the "list PRM-RS, " curve regarding energy consumption when the number of active users is fixed. This observation is an unambiguous demonstration of the benefit of Algorithm 2, which carries out iterative detection.
- when compared with different schemes of "iterative list PRM-RS, " and "iterative list PRM-RS, ", we demonstrate that the performance of the detection can be refined by raising the count of candidates in the first few layers, thereby confirming the significance of Algorithm 1, which guarantees the first few layers’ reliable recoveries.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Saad, W.; Bennis, M.; Chen, M. A vision of 6G wireless systems: Applications, trends, technologies, and open research problems. IEEE network 2019, 34(3), 134–142. [Google Scholar] [CrossRef]
- Guo, F.; Yu, F. R.; Zhang, H.; Li, X.; Ji, H.; Leung, V. C. Enabling massive IoT toward 6G: A comprehensive survey. IEEE Internet of Things Journal 2021, 8(15), 11891–11915. [Google Scholar] [CrossRef]
- Pan, C.; Mehrpouyan, H.; Liu, Y.; Elkashlan, M.; Arumugam, N. Joint pilot allocation and robust transmission design for ultra-dense user-centric TDD C-RAN with imperfect CSI. IEEE Wirel. Commun 2018, 17(3), 2038–2053. [Google Scholar] [CrossRef]
- Chettri, L.; Bera, R. A comprehensive survey on Internet of Things (IoT) toward 5G wireless systems. IEEE Internet of Things Journal 2020, 7(1), 16–32. [Google Scholar] [CrossRef]
- Masoudi, M.; Azari, A.; Yavuz, E. A.; Cavdar, C. Grant-free radio access IoT networks: Scalability analysis in coexistence scenarios. In Proceedings of the IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20-24 May 2018; pp. 1–7. [Google Scholar]
- Shahab, M. B.; Abbas, R.; Shirvanimoghaddam, M.; Johnson, S. J. Grant-free non-orthogonal multiple access for IoT: A survey. IEEE Commun. Surv. Tut 2020, 22(3), 1805–1838. [Google Scholar] [CrossRef]
- Chen, X.; Chen, T. Y.; Guo, D. Capacity of Gaussian many-access channels IEEE Trans. Inf. Theory 2017, 63(6), 3516–3539. [Google Scholar] [CrossRef]
- Polyanskiy, Y. A perspective on massive random-access. In Proceedings of the IEEE International Symposium on Information Theory (ISIT), Aachen, Germany, 25–30 June 2017; pp. 2523–2527. [Google Scholar]
- Zadik, I.; Polyanskiy, Y.; Thrampoulidis, C. Improved bounds on Gaussian MAC and sparse regression via Gaussian inequalities. In Proceedings of the 2019 IEEE International Symposium on Information Theory (ISIT), Paris, France, 7-12 July 2019; pp. 430–434. [Google Scholar]
- Ngo, K. H.; Lancho, A.; Durisi, G. Unsourced multiple access with random user activity. IEEE Trans. Inf. Theory 2023, 1–1. [Google Scholar] [CrossRef]
- Ordentlich, O.; Polyanskiy, Y. Low complexity schemes for the random access Gaussian channel. In Proceedings of the 2017 IEEE International Symposium on Information Theory (ISIT), Aachen, Germany, 25–30 June 2017; pp. 2528–2532. [Google Scholar]
- Marshakov, E.; Balitskiy, G.; Andreev, K.; Frolov, A. A polar code based unsourced random access for the Gaussian MAC. In Proceedings of the 2019 IEEE 90th Vehicular Technology Conference (VTC2019-Fall), Honolulu, Hawaii, USA, 22–25 September 2019; pp. 1–5. [Google Scholar]
- Pradhan, A. K.; Amalladinne, V. K.; Vem, A.; Narayanan, K. R.; Chamberland, J. F. Sparse IDMA: A Joint Graph-Based Coding Scheme for Unsourced Random Access. IEEE Trans. Commun. 2022, 70(11), 7124–7133. [Google Scholar] [CrossRef]
- Ahmadi, M. J.; Duman, T. M. Random spreading for unsourced MAC with power diversity. IEEE Commun. Lett 2021, 25(12), 3995–3999. [Google Scholar] [CrossRef]
- Pradhan, A.K.; Amalladinne, V.K.; Narayanan, K.R.; Chamberland, J.F. LDPC Codes with Soft Interference Cancellation for Uncoordinated Unsourced Multiple Access. In Proceedings of the IEEE International Conference on Communications (ICC), Montreal, QC, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar]
- Amalladinne, V.K.; Chamberland, J.F.; Narayanan, K.R. A Coded Compressed Sensing Scheme for Unsourced Multiple Access. IEEE Trans. Inf. Theory 2020, 66, 6509–6533. [Google Scholar] [CrossRef]
- Amalladinne, V. K.; Vem, A.; Soma, D. K.; Narayanan, K. R.; Chamberland, J. F. A coupled compressive sensing scheme for unsourced multiple access. In Proceedings of the 2018 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Calgary, Alberta, Canada, April 15-20, 2018; pp. 6628–6632. [Google Scholar]
- Lancho, A.; Fengler, A.; Polyanskiy, Y. Finite-blocklength results for the A-channel: Applications to unsourced random access and group testing. In Proceedings of the 2022 58th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, Illinois, September 28–30, 2022; pp. 1–8. [Google Scholar]
- Amalladinne, V.K.; Pradhan, A.K.; Rush, C.; Chamberland, J.F.; Narayanan, K.R. Unsourced random access with coded compressed sensing: Integrating AMP and belief propagation. IEEE Trans. Inf. Theory 2022, 68, 2384–2409. [Google Scholar] [CrossRef]
- Andreev, K.; Rybin, P.; Frolov, A. Reed-Solomon coded compressed sensing for the unsourced random access. In Proceedings of the 2021 17th International Symposium on Wireless Communication Systems (ISWCS), Berlin, Germany, 6–9 September 2021; pp. 1–5. [Google Scholar]
- Che, J.; Zhang, Z.; Yang, Z.; Chen, X.; Zhong, C.; Ng, D.W.K. Unsourced random massive access with beam-space tree decoding. IEEE J. Sel. Areas Commun. 2021, 40, 1146–1161. [Google Scholar] [CrossRef]
- Fengler, A.; Haghighatshoar, S.; Jung, P.; Caire, G. Non-Bayesian Activity Detection, Large-Scale Fading Coefficient Estimation, and Unsourced Random Access With a Massive MIMO Receiver. IEEE Trans. Inf. Theory 2021, 67, 2925–2951. [Google Scholar] [CrossRef]
- Andreev, K.; Rybin, P.; Frolov, A. Coded Compressed Sensing with List Recoverable Codes for the Unsourced Random Access. IEEE Trans. Commun. 2022, 70, 7886–7898. [Google Scholar] [CrossRef]
- Liang, Z.; Zheng, J.; Ni, J. Index modulation–aided mixed massive random access. Front. Commun. Networks 2021, 2, 694557. [Google Scholar] [CrossRef]
- Fengler, A.; Jung, P.; Caire, G. SPARCs for unsourced random access. IEEE Trans. Inf. Theory 2021, 67, 6894–6915. [Google Scholar] [CrossRef]
- Ebert, J.R.; Amalladinne, V.K.; Rini, S.; Chamberland, J.F.; Narayanan, K.R. Coded demixing for unsourced random access. IEEE Trans. Signal Process. 2022, 70, 2972–2984. [Google Scholar] [CrossRef]
- Zhang, L.; Luo, J.; Guo, D. Neighbor discovery for wireless networks via compressed sensing. Perform. Eval. 2013, 70, 457–471. [Google Scholar] [CrossRef]
- Zhang, H.; Li, R.; Wang, J.; Chen, Y.; Zhang, Z. Reed-Muller sequences for 5G grant-free massive access. In Proceedings of the GLOBECOM 2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–7. [Google Scholar]
- Wang, J.; Zhang, Z.; Hanzo, L. Joint active user detection and channel estimation in massive access systems exploiting Reed–Muller sequences. IEEE J. Sel. Top. Signal Process 2019, 13, 739–752. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, Z.; Hanzo, L. Incremental massive random access exploiting the nested Reed-Muller sequences. IEEE Trans. Wirel. Commun. 2020, 20, 2917–2932. [Google Scholar] [CrossRef]
- Calderbank, R.; Thompson, A. CHIRRUP: A practical algorithm for unsourced multiple access. Inform. Inference J. IMA 2020, 9, 875–897. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, Z.; Chen, X.; Zhong, C.; Hanzo, L. Unsourced massive random access scheme exploiting reed-muller sequences. IEEE Trans. Commun. 2020, 70, 1290–1303. [Google Scholar] [CrossRef]
- Xie, W.; Zhang, H. Patterned Reed–Muller Sequences with Outer A-Channel Codes and Projective Decoding for Slot-Controlled Unsourced Random Access. Sensors 2023, 23(11), 5239. [Google Scholar] [CrossRef] [PubMed]
- Pllaha, T.; Tirkkonen, O.; Calderbank, R. Binary subspace chirps. IEEE Trans. Inf. Theory 2022, 68, 7735–7752. [Google Scholar] [CrossRef]
- Pllaha, T.; Tirkkonen, O.; Calderbank, R. Reconstruction of multi-user binary subspace chirps. In Proceedings of the 2020 IEEE International Symposium on Information Theory (ISIT), Los Angeles, CA, USA, 21–26 June 2020; pp. 531–536. [Google Scholar]
- Tirkkonen, O.; Calderbank, R. Codebooks of complex lines based on binary subspace chirps. In Proceedings of the 2019 IEEE Information Theory Workshop (ITW), Visby, Sweden, 25–28 August 2019; pp. 1–5. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




