Submitted:
29 June 2023
Posted:
30 June 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Related Work
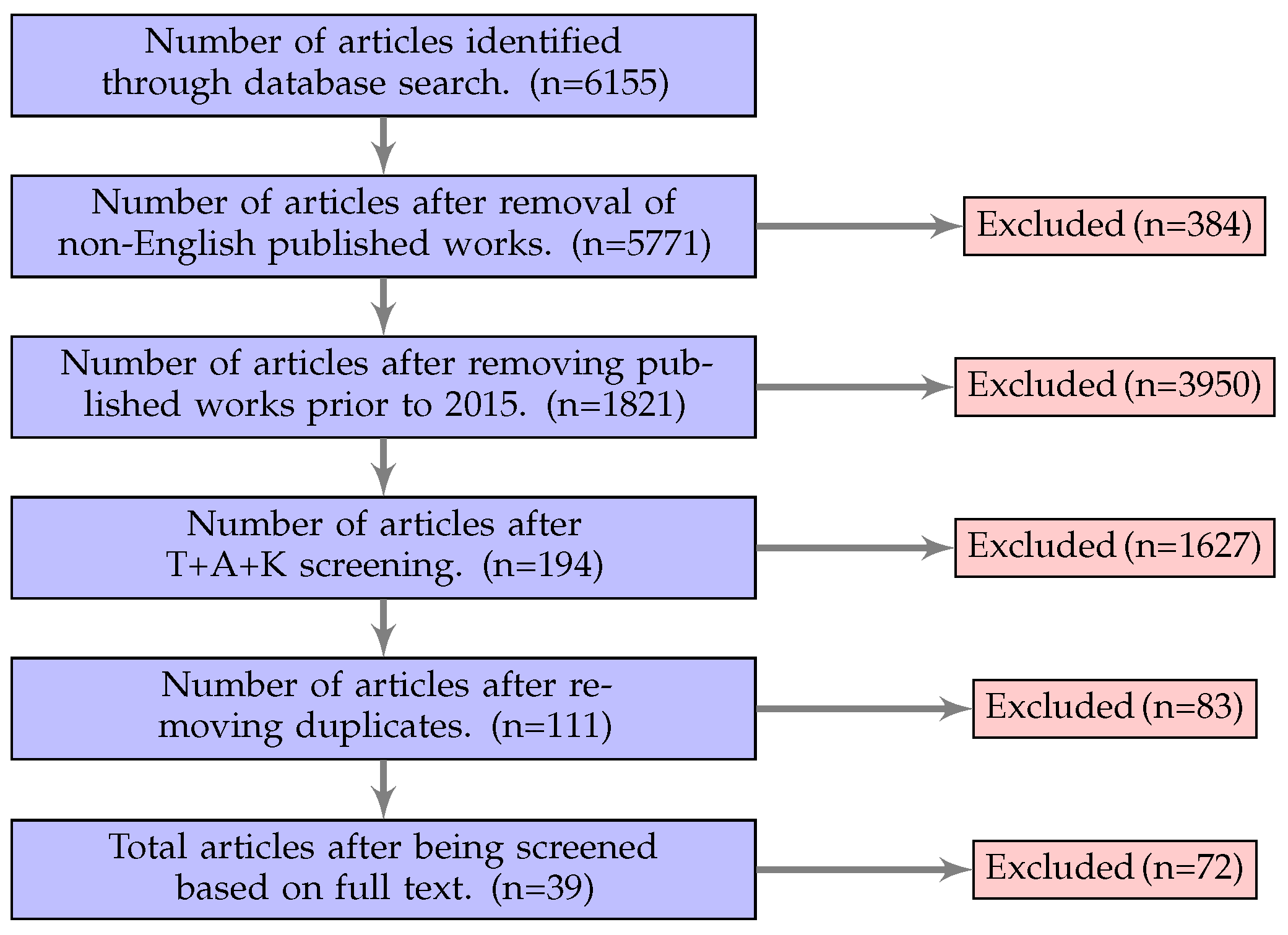
3. Materials and Methods
3.1. Research Questions
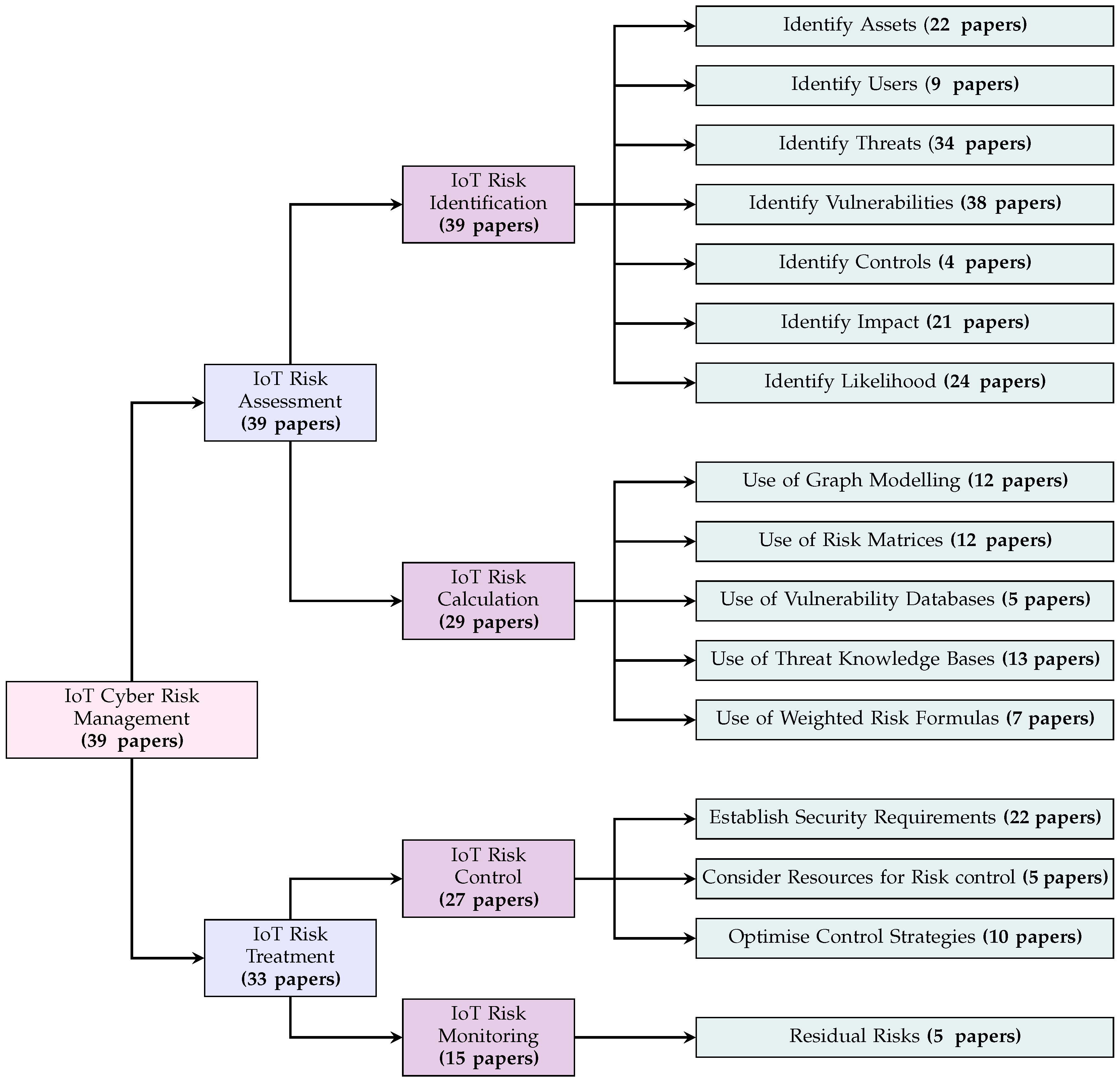
4. Cyber Risk Assessment for IoT Survey Results
4.1. IoT Cyber Risk Identification
4.1.1. Identification of IoT Assets
4.1.2. Identification of Users
4.1.3. Identification of Threats
4.1.4. Identification of Vulnerabilities
4.1.5. Identification of Controls
4.1.6. Identification of Impact
4.1.7. Identification of Likelihood
4.2. IoT Cyber Risk Calculation
4.2.1. Use of Graph Modelling
4.2.2. Use of Risk Matrices
4.2.3. Use of Threat Knowledge Bases
4.2.4. Use of Weighted Risk Formulas
5. Cyber Risk Treatment For IoT Survey Results
5.1. IoT Risk Control
5.1.1. Establish Security Requirements
5.1.2. Consider Resources for Risk control
5.1.3. Optimise Control Strategies
5.2. Risk Monitoring
5.2.1. Residual IoT Risk
6. Recommendations
6.1. Recommendations for IoT Cyber Risk Identification
6.2. Recommendations for IoT Cyber Risk Calculation
6.3. Recommendations for IoT Cyber Risk Control
6.4. Recommendations for IoT Cyber Risk Monitoring
7. Conclusion
References
- Herath, T.; Herath, H.S. Coping with the new normal imposed by the COVID-19 pandemic: Lessons for technology management and governance. Information Systems Management 2020, 37, 277–283. [CrossRef]
- Zikria, Y.B.; Ali, R.; Afzal, M.K.; Kim, S.W. Next-generation internet of things (iot): Opportunities, challenges, and solutions. Sensors 2021, 21, 1174. [CrossRef]
- Baruah, P.D.; Dhir, S.; Hooda, M. Impact of IOT in current era. In Proceedings of the 2019 International Conference on Machine Learning, Big Data, Cloud and Parallel Computing (COMITCon). IEEE, 2019, pp. 334–339.
- Lee, S.K.; Bae, M.; Kim, H. Future of IoT networks: A survey. Applied Sciences 2017, 7, 1072. [CrossRef]
- Varga, P.; Plosz, S.; Soos, G.; Hegedus, C. Security threats and issues in automation IoT. In Proceedings of the 2017 IEEE 13th International Workshop on Factory Communication Systems (WFCS). IEEE, 2017, pp. 1–6.
- Whitman, M.E.; Mattord, H.J. Principles of information security; Cengage Learning, 2017.
- Ross, R.; Pillitteri, V.; Graubart, R.; Bodeau, D.J.; McQuaid, R.M. NIST Special Publication 800-160, Volume 2 Revision 1: Developing cyber resilient systems: a systems security engineering approach. Technical report, National Institute of Standards and Technology (US), 2019. Paper no. NIST SP 800-160, Vol. 2, Rev. 1; National Institute of Standards and Technology Special Publication 800-160, Vol. 2, Rev. 1.
- Radack, S.M.; et al. Managing information security risk: Organization, mission, and information system view. NIST 2011.
- Wunder, J.; Halbardier, A.; Waltermire, D. Specification for asset identification 1.1; Citeseer, 2011. [CrossRef]
- Mavropoulos, O.; Mouratidis, H.; Fish, A.; Panaousis, E. Apparatus: A framework for security analysis in internet of things systems. Ad Hoc Networks 2019, 92, 101743. [CrossRef]
- Mavropoulos, O.; Mouratidis, H.; Fish, A.; Panaousis, E. ASTo: A tool for security analysis of IoT systems. In Proceedings of the 2017 IEEE 15th International Conference on Software Engineering Research, Management and Applications (SERA). IEEE, 2017, pp. 395–400.
- Heartfield, R.; Loukas, G. Detecting semantic social engineering attacks with the weakest link: Implementation and empirical evaluation of a human-as-a-security-sensor framework. Computers & Security 2018, 76, 101–127. [CrossRef]
- Bada, M.; Nurse, J.R. The social and psychological impact of cyberattacks. In Emerging cyber threats and cognitive vulnerabilities; Elsevier, 2020; pp. 73–92.
- Chatterjee, S.; Sarker, S.; Valacich, J.S. The behavioral roots of information systems security: Exploring key factors related to unethical IT use. Journal of Management Information Systems 2015, 31, 49–87. [CrossRef]
- Cullen, A.; Armitage, L. A Human Vulnerability Assessment Methodology. In Proceedings of the 2018 International Conference On Cyber Situational Awareness, Data Analytics And Assessment (Cyber SA). IEEE, 2018, pp. 1–2.
- Aroms, E.; et al. NIST Special Publication 800-30 Risk Management Guide for Information Technology Systems. NIST 2012.
- Group, J.T.F.T.I.I.W.; et al. NIST Special Publication 800-53 Revision 4-Security and Privacy Controls for Federal Information Systems and Organizations. National Institute of Standards and Technology, Technical rep 2013.
- NIST, T. Managing Information Security Risk: Organization, Mission, and Information System View. Organization, Mission, and Information System View 2011, p. 88.
- DIN, E. 27001: 2017-06 Information technology–Security procedures–Information security management systems–Requirements ( 27001: 2013 including Cor 1: 2014 and Cor 2: 2015). German version EN 2017, 27001.
- Kandasamy, K.; Srinivas, S.; Achuthan, K.; Rangan, V.P. IoT cyber risk: A holistic analysis of cyber risk assessment frameworks, risk vectors, and risk ranking process. EURASIP Journal on Information Security 2020, 2020, 1–18. [CrossRef]
- Caralli, R.A.; Stevens, J.F.; Young, L.R.; Wilson, W.R. Introducing octave allegro: Improving the information security risk assessment process. Technical report, Carnegie-Mellon Univ Pittsburgh PA Software Engineering Inst, 2007. [CrossRef]
- Wynn, J.; Whitmore, J.; Upton, G.; Spriggs, L.; McKinnon, D.; McInnes, R.; Graubart, R.; Clausen, L. Threat assessment & remediation analysis (TARA): methodology description version 1.0. Technical report, MITRE CORP BEDFORD MA, 2011.
- Heartfield, R.; Loukas, G.; Budimir, S.; Bezemskij, A.; Fontaine, J.R.; Filippoupolitis, A.; Roesch, E. A taxonomy of cyber-physical threats and impact in the smart home. Computers & Security 2018, 78, 398–428. [CrossRef]
- Nifakos, S.; Chandramouli, K.; Nikolaou, C.K.; Papachristou, P.; Koch, S.; Panaousis, E.; Bonacina, S. Influence of human factors on cyber security within healthcare organisations: A systematic review. Sensors 2021, 21, 5119. [CrossRef]
- Lee, I. Internet of Things (IoT) cybersecurity: Literature review and IoT cyber risk management. Future Internet 2020, 12, 157. [CrossRef]
- Akinrolabu, O.; Nurse, J.R.; Martin, A.; New, S. Cyber risk assessment in cloud provider environments: Current models and future needs. Computers & Security 2019, 87, 101600. [CrossRef]
- Fernández-Alemán, J.L.; Señor, I.C.; Lozoya, P.Á.O.; Toval, A. Security and privacy in electronic health records: A systematic literature review. Journal of biomedical informatics 2013, 46, 541–562. [CrossRef]
- Trends, G. Google Trends, 2023.
- Iso, I.; et al. Risk management–Principles and guidelines. International Organization for Standardization, Geneva, Switzerland 2009.
- Zardari, S.; Nisar, N.; Fatima, Z.; Dhirani, L.L. IoT–Assets Taxonomy, Threats Assessment and Potential Solutions. In Proceedings of the 2023 Global Conference on Wireless and Optical Technologies (GCWOT). IEEE, 2023, pp. 1–8.
- Booth, H.; Rike, D.; Witte, G.A. The national vulnerability database (nvd): Overview. NVD 2013.
- Mitre., 1999.
- Stine, K.; Quinn, S.; Witte, G.; Gardner, R. Integrating cybersecurity and enterprise risk management (ERM). National Institute of Standards and Technology. DOI 2020, 10. [CrossRef]
- Maner, J.K.; Gailliot, M.T.; Butz, D.A.; Peruche, B.M. Power, risk, and the status quo: Does power promote riskier or more conservative decision making? Personality and Social Psychology Bulletin 2007, 33, 451–462. [CrossRef]
- Wolter, K.; Reinecke, P. Performance and security tradeoff. Formal Methods for Quantitative Aspects of Programming Languages: 10th International School on Formal Methods for the Design of Computer, Communication and Software Systems, SFM 2010, Bertinoro, Italy, June 21-26, 2010, Advanced Lectures 2010, pp. 135–167.
- Quinn, S.; Barrett, M.; Witte, G.; Gardner, R.; Ivy, N. Prioritizing Cybersecurity Risk for Enterprise Risk Management. NIST Interagency/Internal Report (NISTIR), National Institute of Standards and Technology 2022. [CrossRef]
- Viriyasitavat, W.; Anuphaptrirong, T.; Hoonsopon, D. When blockchain meets Internet of Things: Characteristics, challenges, and business opportunities. Journal of industrial information integration 2019, 15, 21–28. [CrossRef]
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Durumeric, Z.; Halderman, J.A.; Invernizzi, L.; Kallitsis, M.; et al. Understanding the mirai botnet. In Proceedings of the 26th {USENIX} security symposium ({USENIX} Security 17), 2017, pp. 1093–1110.
- Abbass, W.; Baina, A.; Bellafkih, M. ArchiMate based Security Risk Assessment as a service: preventing and responding to the cloud of things’ risks. In Proceedings of the 2019 International Conference on Wireless Networks and Mobile Communications (WINCOM). IEEE, 2019, pp. 1–5. [CrossRef]
- Aiken, W.; Ryoo, J.; Rizvi, S. An Internet of Things (IoT) Security Assessment for Households. In Proceedings of the 2020 International Conference on Software Security and Assurance (ICSSA). IEEE, 2020, pp. 53–59.
- Al Mousa, A.; Al Qomri, M.; Al Hajri, S.; Zagrouba, R.; Chaabani, S. Environment based IoT security risks and vulnerabilities management. In Proceedings of the 2020 International Conference on Computing and Information Technology (ICCIT-1441). IEEE, 2020, pp. 1–6.
- Ali, B.; Awad, A.I. Cyber and physical security vulnerability assessment for IoT-based smart homes. sensors 2018, 18, 817. [CrossRef]
- Ali, O.; Ishak, M.K.; Bhatti, M.K.L. Internet of things security: Modelling smart industrial thermostat for threat vectors and common vulnerabilities. In Intelligent Manufacturing and Mechatronics; Springer, 2021; pp. 175–186. [CrossRef]
- Alsubaei, F.; Abuhussein, A.; Shiva, S. Security and privacy in the internet of medical things: taxonomy and risk assessment. In Proceedings of the 2017 IEEE 42nd conference on local computer networks workshops (LCN workshops). IEEE, 2017, pp. 112–120.
- Andrade, R.O.; Tello-Oquendo, L.; Ortiz, I. Cybersecurity Risk of IoT on Smart Cities, 2021.
- Anisetti, M.; Ardagna, C.A.; Bena, N.; Foppiani, A. An Assurance-Based Risk Management Framework for Distributed Systems. In Proceedings of the 2021 IEEE International Conference on Web Services (ICWS). IEEE, 2021, pp. 482–492.
- Arfaoui, A.; Kribeche, A.; Senouci, S.M.; Hamdi, M. Game-based adaptive risk management in wireless body area networks. In Proceedings of the 2018 14th International Wireless Communications & Mobile Computing Conference (IWCMC). IEEE, 2018, pp. 1087–1093.
- Chehida, S.; Baouya, A.; Alonso, D.F.; Brun, P.E.; Massot, G.; Bozga, M.; Bensalem, S. Asset-Driven Approach for Security Risk Assessment in IoT Systems. In Proceedings of the International Conference on Risks and Security of Internet and Systems. Springer, 2020, pp. 149–163.
- Christensen, D.; Martin, M.; Gantumur, E.; Mendrick, B. Risk assessment at the edge: Applying NERC CIP to aggregated grid-edge resources. The Electricity Journal 2019, 32, 50–57. [CrossRef]
- Danielis, P.; Beckmann, M.; Skodzik, J. An ISO-Compliant Test Procedure for Technical Risk Analyses of IoT Systems Based on STRIDE. In Proceedings of the 2020 IEEE 44th Annual Computers, Software, and Applications Conference (COMPSAC). IEEE, 2020, pp. 499–504. [CrossRef]
- Duan, X.; Ge, M.; Le, T.H.M.; Ullah, F.; Gao, S.; Lu, X.; Babar, M.A. Automated Security Assessment for the Internet of Things. In Proceedings of the 2021 IEEE 26th Pacific Rim International Symposium on Dependable Computing (PRDC). IEEE, 2021, pp. 47–56.
- Echeverría, A.; Cevallos, C.; Ortiz-Garces, I.; Andrade, R.O. Cybersecurity model based on hardening for secure internet of things implementation. Applied Sciences 2021, 11, 3260. [CrossRef]
- García, S.N.M.; Hernandez-Ramos, J.L.; Skarmeta, A.F. Test-based risk assessment and security certification proposal for the Internet of Things. In Proceedings of the 2018 IEEE 4th World Forum on Internet of Things (WF-IoT). IEEE, 2018, pp. 641–646. [CrossRef]
- George, G.; Thampi, S.M. A graph-based security framework for securing industrial IoT networks from vulnerability exploitations. IEEE Access 2018, 6, 43586–43601. [CrossRef]
- George, G.; Thampi, S.M. Vulnerability-based risk assessment and mitigation strategies for edge devices in the Internet of Things. Pervasive and Mobile Computing 2019, 59, 101068. [CrossRef]
- Ivanov, D.; Kalinin, M.; Krundyshev, V.; Orel, E. Automatic security management of smart infrastructures using attack graph and risk analysis. In Proceedings of the 2020 Fourth World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4). IEEE, 2020, pp. 295–300. [CrossRef]
- James, F. IoT Cybersecurity based Smart Home Intrusion Prevention System. In Proceedings of the 2019 3rd Cyber Security in Networking Conference (CSNet). IEEE, 2019, pp. 107–113.
- James, F. A Risk Management Framework and A Generalized Attack Automata for IoT based Smart Home Environment. In Proceedings of the 2019 3rd Cyber Security in Networking Conference (CSNet). IEEE, 2019, pp. 86–90. [CrossRef]
- Kalinin, M.; Krundyshev, V.; Zegzhda, P. Cybersecurity risk assessment in smart city infrastructures. Machines 2021, 9, 78. [CrossRef]
- Kavallieratos, G.; Chowdhury, N.; Katsikas, S.; Gkioulos, V.; Wolthusen, S. Threat analysis for smart homes. Future Internet 2019, 11, 207. [CrossRef]
- Ksibi, S.; Jaidi, F.; Bouhoula, A. Cyber-Risk Management within IoMT: a Context-aware Agent-based Framework for a Reliable e-Health System. In Proceedings of the The 23rd International Conference on Information Integration and Web Intelligence, 2021, pp. 547–552. [CrossRef]
- Lally, G.; Sgandurra, D. Towards a framework for testing the security of IoT devices consistently. In Proceedings of the International workshop on emerging technologies for authorization and authentication. Springer, 2018, pp. 88–102.
- Mohsin, M.; Anwar, Z.; Husari, G.; Al-Shaer, E.; Rahman, M.A. IoTSAT: A formal framework for security analysis of the internet of things (IoT). In Proceedings of the 2016 IEEE conference on communications and network security (CNS). IEEE, 2016, pp. 180–188.
- Mohsin, M.; Sardar, M.U.; Hasan, O.; Anwar, Z. IoTRiskAnalyzer: A probabilistic model checking based framework for formal risk analytics of the Internet of Things. IEEE Access 2017, 5, 5494–5505. [CrossRef]
- Nakamura, E.T.; Ribeiro, S.L. A privacy, security, safety, resilience and reliability focused risk assessment in a health iot system: Results from ocariot project. In Proceedings of the 2019 Global IoT Summit (GIoTS). IEEE, 2019, pp. 1–6.
- Pacheco, J.; Zhu, X.; Badr, Y.; Hariri, S. Enabling risk management for smart infrastructures with an anomaly behavior analysis intrusion detection system. In Proceedings of the 2017 IEEE 2nd International Workshops on Foundations and Applications of Self* Systems (FAS* W). IEEE, 2017, pp. 324–328.
- Pacheco, J.; Ibarra, D.; Vijay, A.; Hariri, S. IoT security framework for smart water system. In Proceedings of the 2017 IEEE/ACS 14th International Conference on Computer Systems and Applications (AICCSA). IEEE, 2017, pp. 1285–1292.
- Parsons, E.K.; Panaousis, E.; Loukas, G. How secure is home: Assessing human susceptibility to IoT threats. In Proceedings of the 24th Pan-Hellenic Conference on Informatics, 2020, pp. 64–71. [CrossRef]
- Rizvi, S.; Pipetti, R.; McIntyre, N.; Todd, J.; Williams, I. Threat model for securing internet of things (IoT) network at device-level. Internet of Things 2020, 11, 100240. [CrossRef]
- Ryoo, J.; Tjoa, S.; Ryoo, H. An IoT risk analysis approach for smart homes (work-in-progress). In Proceedings of the 2018 International Conference on Software Security and Assurance (ICSSA). IEEE, 2018, pp. 49–52.
- Seeam, A.; Ogbeh, O.S.; Guness, S.; Bellekens, X. Threat modeling and security issues for the internet of things. In Proceedings of the 2019 conference on next generation computing applications (NextComp). IEEE, 2019, pp. 1–8.
- Shivraj, V.; Rajan, M.; Balamuralidhar, P. A graph theory based generic risk assessment framework for internet of things (IoT). In Proceedings of the 2017 IEEE international conference on advanced networks and telecommunications systems (ANTS). IEEE, 2017, pp. 1–6.
- Shokeen, R.; Shanmugam, B.; Kannoorpatti, K.; Azam, S.; Jonkman, M.; Alazab, M. Vulnerabilities Analysis and Security Assessment Framework for the Internet of Things. In Proceedings of the 2019 Cybersecurity and Cyberforensics Conference (CCC). IEEE, 2019, pp. 22–29. [CrossRef]
- Tseng, T.W.; Wu, C.T.; Lai, F. Threat analysis for wearable health devices and environment monitoring internet of things integration system. IEEE Access 2019, 7, 144983–144994. [CrossRef]
- Vakhter, V.; Soysal, B.; Schaumont, P.; Guler, U. Threat Modeling and Risk Analysis for Miniaturized Wireless Biomedical Devices. IEEE Internet of Things Journal 2022. [CrossRef]
- Wangyal, S.; Dechen, T.; Tanimoto, S.; Sato, H.; Kanai, A. A Study of Multi-viewpoint Risk Assessment of Internet of Things (IoT). In Proceedings of the 2020 9th International Congress on Advanced Applied Informatics (IIAI-AAI). IEEE, 2020, pp. 639–644.
- Zahra, B.F.; Abdelhamid, B. Risk analysis in Internet of Things using EBIOS. In Proceedings of the 2017 IEEE 7th Annual Computing and Communication Workshop and Conference (CCWC). IEEE, 2017, pp. 1–7.
- de la Defense Nationale, S.G. EBIOS: Expression of Needs and Identification of Security Objectives, 2005.
- Pub, F. Minimum security requirements for federal information and information systems. FIPS Publication 200 2005.
- Ross, R. Guide for conducting risk assessments NIST special publication 800-30 revision 1. US Dept. Commerce, NIST, Gaithersburg, MD, USA, Tech. Rep 2012.
- Archiveddocs, M., 2009.
- Deng, M.; Wuyts, K.; Scandariato, R.; Preneel, B.; Joosen, W. A privacy threat analysis framework: supporting the elicitation and fulfillment of privacy requirements. Requirements Engineering 2011, 16, 3–32. [CrossRef]
- Michael, H.; David, L. Writing secure code, 2002.
- Wang, Z.; Zhu, H.; Sun, L. Social engineering in cybersecurity: Effect mechanisms, human vulnerabilities and attack methods. IEEE Access 2021, 9, 11895–11910. [CrossRef]
- Gan, D.; Heartfield, R. Social engineering in the internet of everything. Cutter IT Journal 2016, 29, 20–29.
- Souppaya, M.; Stine, K.; Simos, M.; Sweeney, S.; Scarfone, K. [Project Description] Critical Cybersecurity Hygiene: Patching the Enterprise. Technical report, National Institute of Standards and Technology, 2020.
- Maennel, K.; Mäses, S.; Maennel, O. Cyber hygiene: The big picture. In Proceedings of the Secure IT Systems: 23rd Nordic Conference, NordSec 2018, Oslo, Norway, November 28-30, 2018, Proceedings 23. Springer, 2018, pp. 291–305.
- Zevin, S. Standards for security categorization of federal information and information systems; DIANE Publishing, 2009.
- Hong, J.; Kim, D.S. Harms: Hierarchical attack representation models for network security analysis. Edith Cowan University 2012.
- for Standardization, I.O. Medical Devices: Application of Risk Management to Medical Devices; ISO, 2019.
- Johnson, C.; Badger, L.; Waltermire, D.; Snyder, J.; Skorupka, C. NIST special publication 800-150: guide to cyber threat information sharing. NIST, Tech. Rep 2016.
- ISO, I. 31000: 2018 Risk Management. Guidelines. Suomen standarditoimisliitto SFS ry 2018.
- AG, D.T. Privacy and security assessment process, 2012.
- Barker, E.B.; Smid, M.; Branstad, D. Profile for US Federal Cryptographic Key Management Systems. NIST 2015.
- Stouffer, K.; Falco, J.; Scarfone, K.; et al. Guide to industrial control systems (ICS) security. NIST special publication 2011, 800, 16–16.
- for Internet Security, C. CIS Controls v8 Internet of Things Companion Guide, 2021.
- Khouzani, M.; Liu, Z.; Malacaria, P. Scalable min-max multi-objective cyber-security optimisation over probabilistic attack graphs. European Journal of Operational Research 2019, 278, 894–903. [CrossRef]
- Zhang, Y.; Malacaria, P. Bayesian Stackelberg games for cyber-security decision support. Decision Support Systems 2021, 148, 113599. [CrossRef]
- Fielder, A.; Panaousis, E.; Malacaria, P.; Hankin, C.; Smeraldi, F. Decision support approaches for cyber security investment. Decision support systems 2016, 86, 13–23. [CrossRef]
- VARIoT. Variot databases of IOT exploits and vulnerabilities, 2022.
| IoT Risk Identification | IoT Cyber Risk Calculation | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Reference | Identify Assets | Users | Threats | Vulnerabilities | Controls | Impact | Likelihood | Graph | Risk | Vulnerability | Threat Knowledge | Weighted Risk |
| Modelling | Matrices | Databases | Bases | Formulas | ||||||||
| Abbass et al., [39] | √ | - | √ | √ | - | - | - | - | - | - | - | - |
| Aiken et al., [40] | - | - | - | √ | √ | - | - | - | - | - | - | √ |
| Al et al., [41] | √ | - | √ | √ | - | - | √ | - | - | - | - | - |
| Ali and Awad [42] | √ | √ | √ | √ | - | √ | - | - | - | - | √ | - |
| Ali et al., [43] | √ | - | √ | √ | - | - | - | - | √ | - | - | - |
| Alsubaei et al., [44] | - | - | √ | √ | √ | √ | √ | - | - | - | √ | √ |
| Andrade et al., [45] | √ | √ | √ | √ | - | √ | √ | √ | √ | - | - | √ |
| Anisetti et al., [46] | √ | - | √ | √ | - | √ | √ | √ | - | - | - | - |
| Arfaoui et al., [47] | - | - | √ | √ | - | √ | √ | - | - | - | - | - |
| Chehida et al., [48] | √ | √ | √ | √ | - | √ | - | - | √ | - | √ | - |
| Christensen et al., [49] | √ | - | √ | √ | - | - | √ | - | - | - | - | - |
| Danielis et al., [50] | √ | - | √ | √ | - | √ | √ | - | √ | - | - | - |
| Duan et al., [51] | √ | √ | - | √ | - | √ | √ | √ | - | √ | √ | - |
| Echeverria et al., [52] | √ | - | - | √ | - | √ | √ | - | √ | √ | √ | - |
| Garcia et al., [53] | - | - | - | √ | - | √ | √ | - | - | √ | √ | - |
| George and Thampi [54] | - | - | √ | √ | - | √ | √ | √ | √ | - | - | - |
| George and Thampi [55] | - | - | √ | √ | - | - | √ | √ | √ | - | - | √ |
| Ivanov et al., [56] | - | - | √ | √ | - | - | - | √ | - | √ | √ | - |
| James [57] | - | - | √ | √ | - | - | - | √ | - | - | - | - |
| James [58] | √ | - | √ | √ | - | - | √ | √ | - | - | - | - |
| Kalinin et al., [59] | √ | - | √ | √ | - | - | √ | - | - | - | - | - |
| Kavallieratos et al., [60] | √ | - | √ | √ | - | - | √ | √ | - | - | - | - |
| Ksibi et al., [61] | √ | √ | √ | √ | √ | √ | √ | - | - | - | - | √ |
| Lally and Sgandurra [62] | - | - | √ | √ | - | - | - | - | - | - | - | - |
| Mohsin et al., [63] | - | - | √ | - | - | - | - | √ | - | - | - | - |
| Mohsin et al., [64] | - | - | √ | √ | - | - | √ | √ | √ | - | - | - |
| Nakamura and Ribeiro [65] | - | √ | √ | √ | - | √ | √ | - | √ | - | √ | - |
| Pacheco et al., [66] | - | - | √ | √ | - | √ | - | - | - | - | - | - |
| Pacheco et al., [67] | - | - | √ | √ | - | √ | - | - | - | - | √ | - |
| Parsons et al., [68] | √ | √ | √ | √ | √ | √ | √ | - | - | - | √ | √ |
| Rizvi et al., [69] | - | - | √ | √ | - | √ | - | - | - | √ | √ | - |
| Ryoo et al., [70] | √ | - | √ | √ | - | - | - | - | - | - | - | - |
| Seeam et al., [71] | √ | - | √ | √ | - | √ | - | - | - | - | - | - |
| Shivraj et al., [72] | √ | - | √ | √ | - | √ | √ | √ | √ | - | - | √ |
| Shokeen et al., [73] | - | - | - | √ | - | - | - | - | - | - | - | - |
| Tseng et al., [74] | √ | √ | √ | √ | - | - | √ | - | - | - | √ | - |
| Vakhter et al., [75] | √ | - | √ | √ | - | √ | √ | - | √ | - | - | - |
| Wangyal et al., [76] | - | - | √ | √ | - | - | √ | - | √ | - | - | - |
| Zahra and Abdelhamid [77] | √ | √ | √ | √ | - | √ | √ | - | - | - | √ | - |
| IoT Risk Control | IoT Risk Monitoring | ||||||
|---|---|---|---|---|---|---|---|
| Reference | IoT Control Strategies |
IoT Security Requirements |
IoT Risk Resources |
Optimise IoT Control Strategies |
IoT Risk Monitoring |
Residual IoT Risk |
|
| Abbass et al., [39] | √ | √ | - | - | √ | - | |
| Aiken et al., [40] | - | - | - | - | - | - | |
| Al et al., [41] | √ | - | √ | - | √ | √ | |
| Ali and Awad [42] | √ | √ | - | - | - | - | |
| Ali et al., [43] | - | - | - | - | - | - | |
| Alsubaei et al., [44] | √ | - | - | - | - | - | |
| Andrade et al., [45] | √ | √ | √ | - | √ | √ | |
| Anisetti et al., [46] | √ | - | - | √ | √ | √ | |
| Arfaoui et al., [47] | √ | √ | - | √ | √ | - | |
| Chehida et al., [48] | √ | √ | - | - | √ | - | |
| Christensen et al., [49] | √ | √ | - | - | - | - | |
| Danielis et al., [50] | √ | - | - | √ | - | - | |
| Duan et al., [51] | - | - | - | - | - | - | |
| Echeverria et al., [52] | √ | √ | - | - | √ | - | |
| Garcia et al., [53] | - | - | - | - | √ | - | |
| George and Thampi [54] | √ | - | - | √ | - | - | |
| George and Thampi [55] | √ | √ | - | - | - | - | |
| Ivanov et al., [56] | √ | - | √ | √ | - | - | |
| James [57] | √ | √ | - | - | - | - | |
| James [58] | √ | √ | √ | - | - | - | |
| Kalinin et al., [59] | - | - | - | - | √ | - | |
| Kavallieratos et al., [60] | - | - | - | - | - | - | |
| Ksibi et al., [61] | - | √ | - | √ | √ | - | |
| Lally and Sgandurra [62] | - | - | - | - | - | - | |
| Mohsin et al., [63] | √ | √ | - | - | - | - | |
| Mohsin et al., [64] | √ | √ | - | - | - | - | |
| Nakamura and Ribeiro [65] | √ | √ | - | √ | - | - | |
| Pacheco et al., [66] | √ | √ | - | - | - | - | |
| Pacheco et al., [67] | √ | √ | - | - | - | - | |
| Parsons et al., [68] | √ | - | √ | √ | - | - | |
| Rizvi et al., [69] | √ | √ | - | √ | √ | - | |
| Ryoo et al., [70] | - | - | - | - | √ | √ | |
| Seeam et al., [71] | √ | √ | - | - | √ | - | |
| Shivraj et al., [72] | - | - | - | - | - | - | |
| Shokeen et al., [73] | √ | √ | √ | - | - | - | |
| Tseng et al., [74] | √ | √ | - | - | - | - | |
| Vakhter et al., [75] | √ | - | - | √ | √ | - | |
| Wangyal et al., [76] | √ | √ | - | - | - | - | |
| Zahra and Abdelhamid [77] | √ | √ | - | - | √ | √ | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




