Submitted:
19 December 2025
Posted:
22 December 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Defining the API Security Gateway and Data Access Control Model for Multi-Tenant Full-Stack Systems
3. Building an Access Control Model for Multi-Tenant Full-Stack Systems
3.1. Role Activation Mechanism
3.2. Access Control Flow
3.3. Security Authentication and Authorization Decision
4. Implementation of API Security Gateway for Multi-Tenant Full-Stack Systems
4.1. System Architecture Design
4.2. Security Control Policies
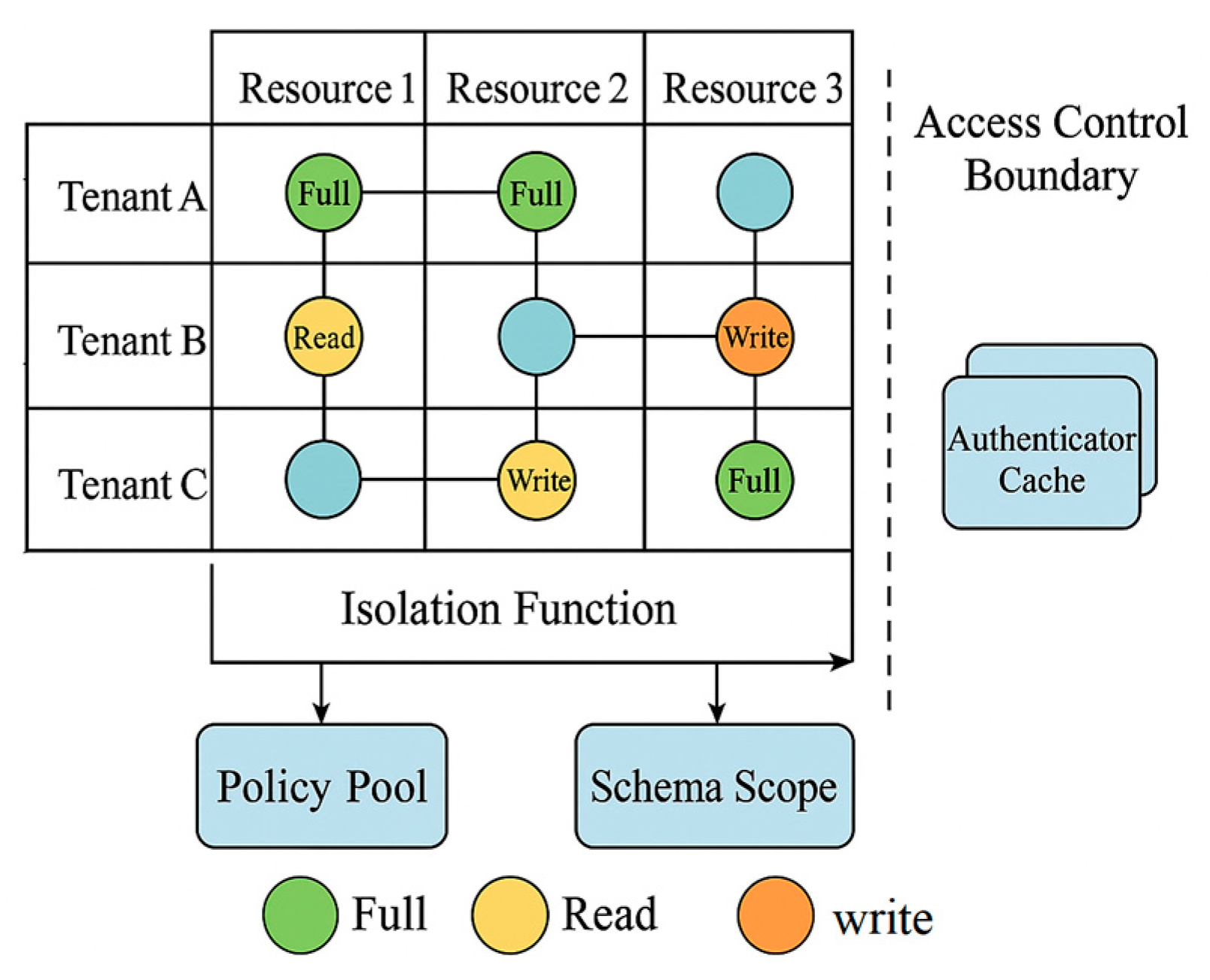
4.3. Multi-Tenant Isolation Mechanism
5. Experimental Validation and Analysis
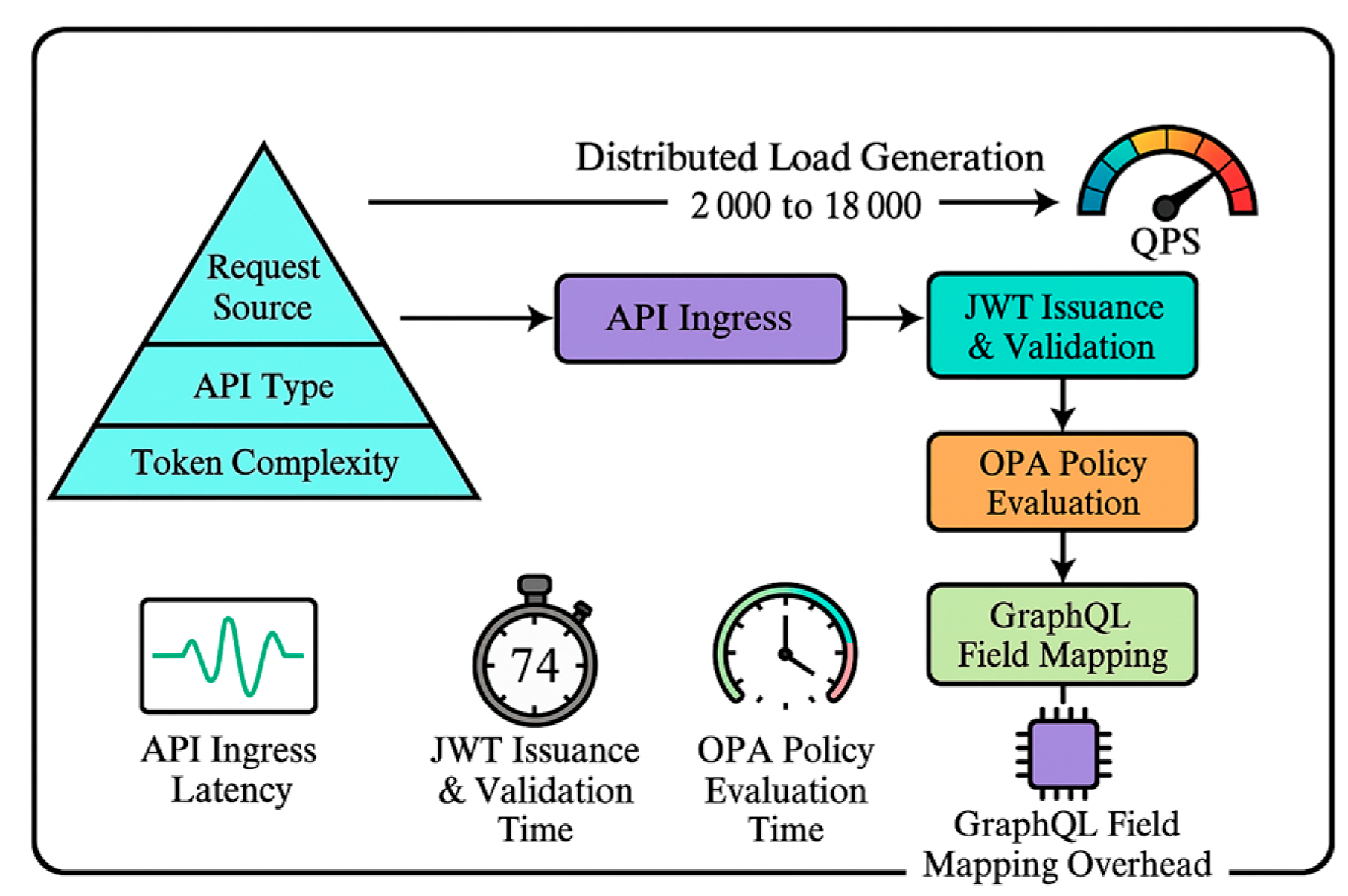
5.1. Experimental Design
5.2. Performance Testing
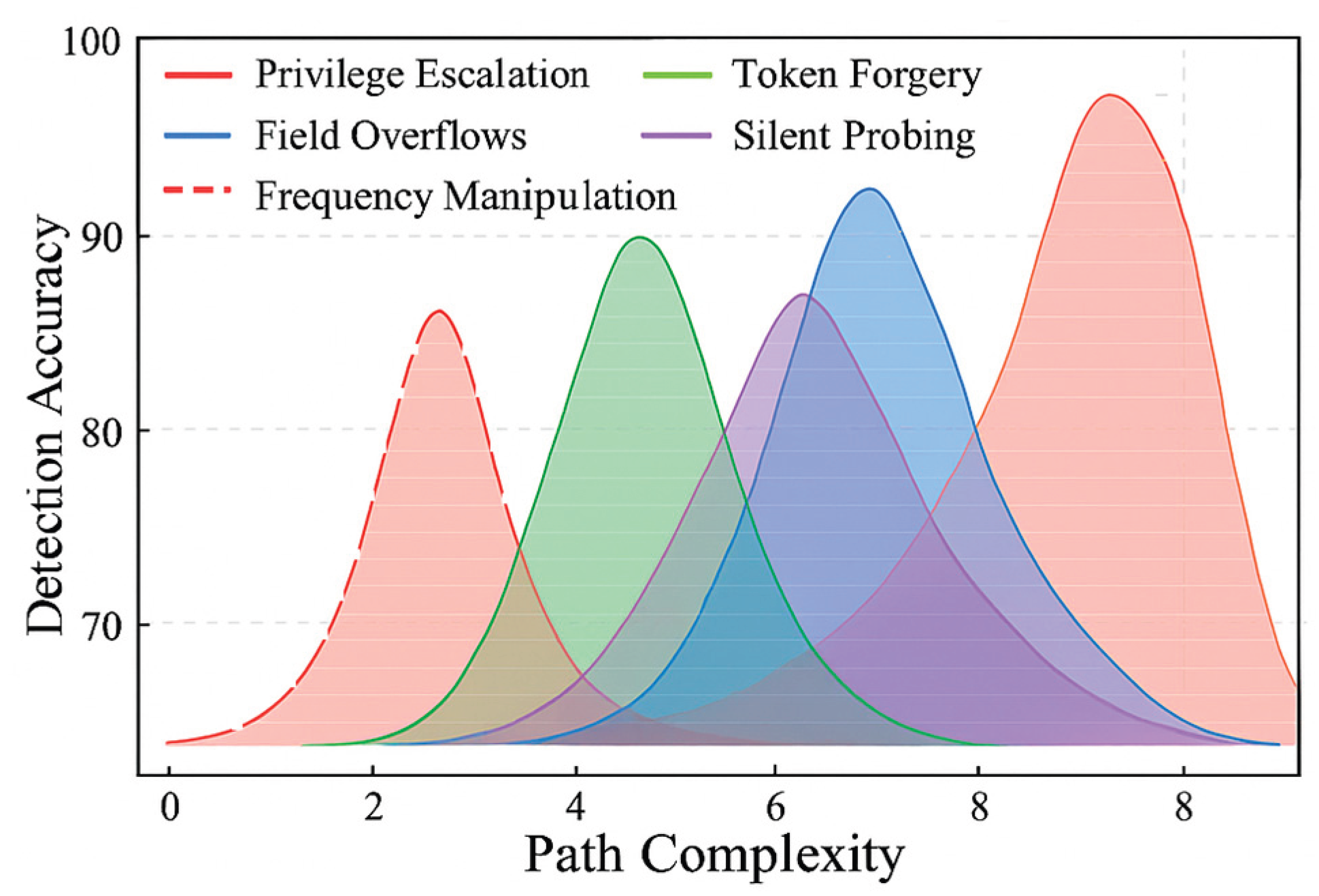
5.3. Security Assessment
6. Conclusion
References
- Ali, S.; Nasim, F.; Haider, K. Secure middleware model for public restful apis. Al-Aasar 2025, 2, 50–62. [Google Scholar]
- Sitorus, R.S.; Hutagaol, B.J.; Simanjuntak, D.M. Capability-Based API Gateway Technology Selection Analysis for Banking Cybersecurity Solution Using AHP Method. sinkron 2025, 9, 338–347. [Google Scholar] [CrossRef]
- Zhao, C. API Common Security Threats and Security Protection Strategies. Front. Comput. Intell. Syst. 2024, 10, 29–33. [Google Scholar] [CrossRef]
- Aydemir, F.; Başçiftçi, F. Performance and Availability Analysis of API Design Techniques for API Gateways. Arab. J. Sci. Eng. 2024, 50, 11485–11498. [Google Scholar] [CrossRef]
- Ahuja, D. Securing Container Isolation in Multi-Tenant Environments. J. Comput. Sci. Technol. Stud. 2025, 7, 225–232. [Google Scholar]
- Chen, X.; Huang, Y.; Jessney, B.; Sangha, J.; Gu, S.; Schönlieb, C.-B.; Bennett, M.; Roberts, M. Review and recommendations for using artificial intelligence in intracoronary optical coherence tomography analysis. Eur. Hear. J. - Digit. Heal. 2025, 6, 529–539. [Google Scholar] [CrossRef] [PubMed]
- De Simone, L.; Di Mauro, M.; Natella, R.; Postiglione, F. A Latency-Driven Availability Assessment for Multi-Tenant Service Chains. IEEE Trans. Serv. Comput. 2022, 16, 815–829. [Google Scholar] [CrossRef]
- Chirivella-Perez, E.; Salva-Garcia, P.; Sanchez-Navarro, I.; Alcaraz-Calero, J.M.; Wang, Q. E2E network slice management framework for 5G multi-tenant networks. J. Commun. Networks 2023, 25, 392–404. [Google Scholar] [CrossRef]
- Eboseremen, B.O.; Ogedengbe, A.O.; Obuse, E.; Oladimeji, O.; Ajayi, J.O.; Akindemowo, A.O.; Ayodeji, D.C.; Erigha, E.D. Secure Data Integration in Multi-Tenant Cloud Environments: Architecture for Financial Services Providers. J. Front. Multidiscip. Res. 2022, 3. [Google Scholar] [CrossRef]
- Wang, Y.; Yang, J.; Wang, Z. Multi-Tenant In-Memory Key-Value Cache Partitioning Using Efficient Random Sampling-Based LRU Model. IEEE Trans. Cloud Comput. 2023, 11, 3601–3618. [Google Scholar] [CrossRef]

| Module Name | Average Duration (ms) | P99 Latency (ms) | Peak (ms) |
|---|---|---|---|
| API Entry Parsing | 12.6 | 23.1 | 57.4 |
| JWT Issuance and Verification | 18.2 | 32.8 | 64.3 |
| OPA Policy Engine Evaluation | 24.7 | 44.9 | 85.6 |
| GraphQL Field Permission Matching | 9.4 | 17.2 | 41.8 |
| Policy Cache Hit and Fallback Mechanism | 8.1 | 14.6 | 37.5 |
| Attack Type | Number of Detection Rules | Average Hit Rate (%) |
|---|---|---|
| Privilege Escalation Attacks | 74 | 92.8 |
| Token Forgery Attacks | 63 | 89.5 |
| GraphQL Field Overrange | 81 | 94.1 |
| Silent Probe Behavior | 45 | 86.3 |
| High-frequency access manipulation | 56 | 91.7 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license.




