1. Introduction
In recent years, with the deepening of China’s deep-sea strategy and the continuous advancement of autonomous ocean observation and monitoring equipment, marine scientific research have gradually shifted from traditional modes that relied on periodic missions and manual operations toward increasingly intelligent and autonomous approaches [
1,
2]. This transformation is reflected not only in the evolution of instruments and the enhancement of observational capacity, but more importantly, in the redefinition of the role of “marine scientific research” as a central resource. Within the new-generation marine scientific research system, data are no longer confined to serving knowledge discovery alone; rather, they directly inform observation-driven decision-making, model-based analysis, and even the formulation of national strategies [
3]. In highly sensitive domains such as oceanic carbon sink assessment, polar ecosystem protection, deep-sea seismic exploration, and subsea mineral resource investigation, the scientific validity, strategic significance, and confidentiality of data have become increasingly prominent [
4].
From the perspective of data characteristics, marine information exhibits considerable complexity and diversity. The observational platforms cover a broad spectrum—from underwater gliders, buoys, and autonomous surface vehicles to manned and unmanned submersibles—together forming a cross-scale distributed observation network [
5]. The collected content is highly heterogeneous, ranging from continuous sensor outputs to image and video frames, geomagnetic sequences, vertical profiles, and structured navigation logs, thereby constituting a multimodal information space [
6]. Although data are typically continuous in the temporal dimension, their spatial distribution is uneven, and the instability of maritime communication links frequently results in interruptions, jitter, accumulated latency, or even frame-level loss under adverse sea states or near polar ice cover. These challenges impose severe constraints on existing mechanisms designed to ensure the stability and integrity of data transmission [
7].
Moreover, the users of marine data extend beyond universities and research institutes to include defense, classified, and strategic intelligence agencies. As such, requirements for confidentiality, security auditing, and traceability must reach exceptionally stringent standards [
8]. However, single encryption algorithms are no longer sufficient to satisfy the multifaceted demands of these complex application scenarios. In practice, while most systems employ SHA-256 hashing combined with RSA and AES in layered encryption frameworks, these mechanisms were primarily developed for conventional IT environments characterized by relatively abundant resources and stable communication conditions [
9]. Under the highly dynamic, heterogeneous, and asynchronous conditions of marine observation, three critical issues emerge: first, hashing mechanisms generally assume a linear data stream and thus lack compatibility with fragmented verification and chain reassembly [
10]; second, encryption mechanisms exhibit excessive dependence on computational resources and link synchronization—RSA-based key negotiation incurs significant overhead, whereas AES, though efficient, is highly sensitive to stable communication channels [
11]; third, verification processes typically lack fault tolerance and recovery capacity, such that once relays fail or links are re-established, the system often cannot resume transmission from breakpoints or perform partial confirmation [
12].
These limitations are particularly evident in real-world scenarios. For example, in Argo float systems with short satellite transmission windows, even minor key-exchange failures may render an entire data packet invalid. In multi-platform asynchronous collaborative missions, mismatched node return sequences can disrupt serial hashing mechanisms. Similarly, in complex chained logging systems, conventional mechanisms struggle to ensure timestamp authentication and modification tracking [
13].
To address these challenges, this paper proposes an encryption–verification collaborative mechanism tailored to the specific requirements of marine scientific research missions. The design comprises two core components: first, a Hybrid Multi-Resolution Hashing (HMR) mechanism, which extends the traditional SHA-256 with dynamic partitioning, index-chain binding, and threshold signature schemes, thereby enabling multi-granularity integrity verification even under conditions of data fragmentation and unstable links, and significantly improving chain verifiability [
14]; second, an Efficient Modular Encryption Routine (EMR), which integrates RSA-based key negotiation with AES stream encryption, while introducing key caching, asynchronous sessions, and structured encapsulation strategies, thereby reducing reliance on stable links and enhancing overall performance [
15].
The primary contributions of this study are as follows:
- 1)
The introduction of the HMR mechanism, a chain-oriented hashing framework adapted to edge scenarios, capable of achieving efficient integrity verification in environments with highly fragmented data and frequent link disruptions.
- 2)
The development of the EMR scheme, a hybrid encryption solution designed for communication asymmetry, which substantially improves encryption efficiency and security under resource-constrained and unstable transmission conditions.
- 3)
The implementation of a multidimensional simulation platform for system evaluation, which validates the proposed approach in complex survey environments using metrics such as verification latency, encryption delay, packet-loss resilience, and data volume variation.
2. Related Work
Ensuring the security and integrity of data transmission has long been a central concern in the development of information systems. With the rapid expansion of distributed sensing networks and the growing heterogeneity of data sources, traditional encryption and verification frameworks face increasing challenges in unstable and resource-constrained environments [
16]. A systematic review of hashing, encryption, and integrated verification mechanisms helps clarify these limitations and provides the foundation for the HMR–EMR framework proposed in this study.
Hashing mechanisms. The SHA family has long represented the mainstream approach to integrity protection, with SHA-1 gradually replaced by SHA-2 (e.g., SHA-256) due to its superior collision resistance [
17]. However, these algorithms operate on entire datasets in a single computation and lack incremental or resumable capabilities, resulting in inefficiency when handling fragmented or incomplete data. Performance-oriented algorithms such as BLAKE2 improve throughput but remain limited under multi-user concurrency. Similarly, the sponge-based Keccak algorithm in SHA-3 supports variable-length outputs but provides only limited indexing functionality for cross-node verification [
18,
19]. Consequently, most linear hash models encounter difficulties such as chain breakage and redundant computation in asynchronous or fragmented data flows. Merkle trees have been applied to block-level verification [
20], yet they become unbalanced and inefficient with continuous appending or partial data loss, reducing their suitability for dynamic marine networks.
Encryption mechanisms. Conventional hybrid encryption schemes, exemplified by RSA for key negotiation and AES for high-speed symmetric encryption, remain the foundation of secure protocols such as TLS and PGP [
21]. While effective in stable IT environments, RSA imposes substantial computational overhead on edge devices [
22], and AES’s dependence on synchronization diminishes robustness in asynchronous or multi-source transmissions. Elliptic Curve Cryptography (ECC) has been increasingly adopted in mobile and IoT systems [
23,
24], yet its complex curve management constrains deployment in dynamic, multi-platform marine missions. Lightweight ciphers such as ChaCha20 enhance efficiency but lack structural adaptability in fragmented transmission scenarios.
Joint schemes. To address the rigidity of single modules, advanced designs integrate hashing and encryption with collaborative mechanisms. Zero-knowledge proofs (ZKPs) enable privacy-preserving verification but remain excessively resource-intensive for embedded systems [
4,
12]. Threshold signatures improve robustness against single-node failures but impose high synchronization costs in distributed environments. In practice, encryption and verification often function as parallel rather than integrated modules, as observed in Argo float networks or subsea ECC handshakes, which continue to rely on full-packet AES encryption [
25,
26]. Such architectures do not support fragment-level confirmation and remain vulnerable to frequent link disruptions [
27,
28].
In summary, existing approaches tend to emphasize either strong but rigid hashing, efficient yet synchronization-dependent encryption, or privacy-preserving but computationally heavy joint schemes. None adequately satisfies the combined requirements of fragmented verification, asynchronous adaptation, and lightweight encryption essential for marine missions. To address this gap, the proposed HMR–EMR mechanism introduces entropy-aware dynamic hashing with chain-state indexing, coupled with modular encryption that supports key caching and asynchronous encapsulation. This integrated design offers the resilience and efficiency necessary for secure communication in heterogeneous and unstable marine environments.
3. Methodology Design
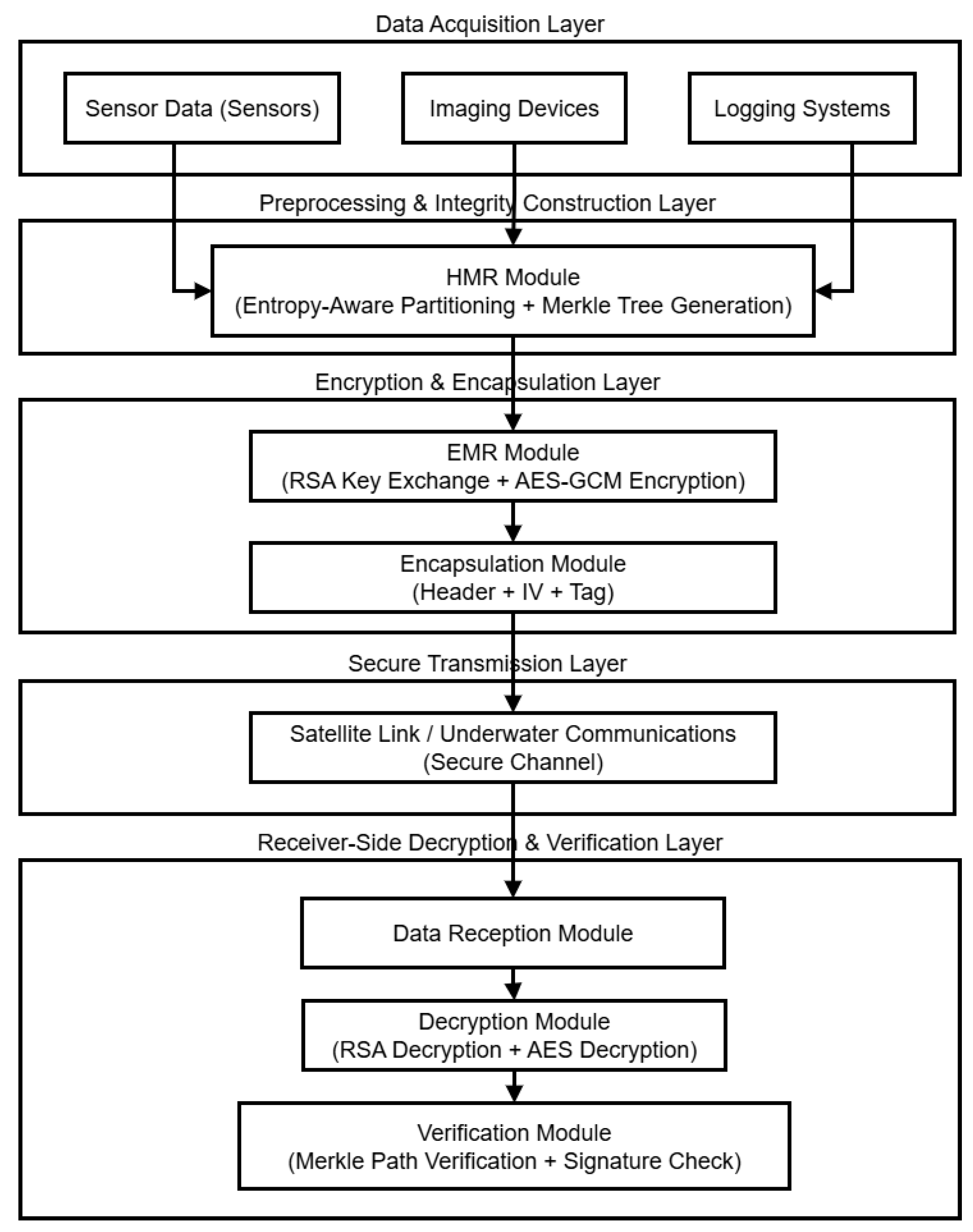
To address the challenges of high data volume, multi-modality, and unstable transmission links in marine scientific research missions, this study develops an end-to-end secure processing system that integrates the HMR and EMR mechanisms. The system enables the joint execution of integrity verification and encryption protection, forming a compact structural loop that balances both security and efficiency. The overall architecture consists of five key processing stages, as illustrated in
Figure 1:
- 1)
Data Acquisition: The system supports heterogeneous multi-source inputs from ocean sensors, imaging devices, and logging systems, covering typical data types such as temperature, salinity, image frames, and navigation records. These are collected and encoded into a structured format for subsequent processing.
- 2)
HMR Processing: Adaptive partitioning is performed based on entropy distribution of the data, while Merkle paths are utilized to generate distributed indices. This establishes an integrity structure with incremental verification capability, thereby enhancing structural consistency and reliability.
- 3)
EMR Encryption: The system integrates RSA-based key agreement with AES-GCM symmetric encryption. Through key decoupling, authentication tagging, and concurrent encryption strategies, the encapsulation logic simultaneously ensures cryptographic strength and computational efficiency, meeting the real-time requirements of edge nodes.
- 4)
Secure Transmission: The data encapsulation format is tailored for the complexity of marine communication links, maintaining compatibility with satellite relays, submarine optical cables, and ad hoc wireless channels. In high packet-loss environments, lightweight redundancy structures and authentication mechanisms are employed to secure stable transmission.
- 5)
Decryption and Verification: At the receiving end, the encapsulated data are parsed in accordance with the protocol, automatically completing key recovery, data decryption, and multipath signature verification. This guarantees the verifiability of data integrity and traceability to the original source.
A central advantage of the system lies in its dynamic parameter self-adjustment capability. The HMR module automatically adapts block length and hashing depth in response to the entropy characteristics of incoming data, whereas the EMR module dynamically optimizes encryption strength and authentication tag configuration according to communication status. Such adaptability enhances overall resource efficiency, reinforces system stability under extreme link conditions, and significantly improves its resilience to heterogeneous data modalities. Consequently, the proposed framework offers a secure communication solution that is robust and sustainable for long-term deployment in marine scientific research tasks.
3.1. HMR Mechanism Design and Optimization
The HMR mechanism builds upon SHA-256 by introducing an entropy-aware partitioning strategy and a threshold signature scheme, thereby enabling progressive integrity verification and distributed provenance tracking under unstable communication links. First, the system computes the information entropy of data
:
where
denotes the probability of occurrence of byte
in the dataset. Based on the entropy distribution, the adaptive block size
is determined as:
Here, bytes, , and the normalized entropy is defined as . Experimental results demonstrate that different data types exhibit effective block-size adaptation: sensor data converged to an average of 1951 bytes, image data around 1920 bytes, and text logs approximately 1718 bytes—all significantly outperforming fixed block-size schemes in terms of processing efficiency and alignment accuracy.
For distributed verification, HMR supports a threshold signature–based multi-node collaborative mechanism. With threshold parameter tt, the verification of data block
D is defined as:
This model enhances fault tolerance and provides independent verification capabilities at every hop of the data upload path across nodes and platforms in marine missions, thus substantially improving overall reliability.
In hash generation, each block
is salted and augmented with an entropy factor to produce the following hash value:
The system subsequently constructs a balanced Merkle hash tree to organize data structures and local indices, thereby supporting independent verification of partial data and subchain reconstruction. Across all experimental samples, verification accuracy remained at 100%, fully meeting the demands of structural consistency tracking under asynchronous links. Compared with traditional SHA-256 linear hashing—where the entire dataset is treated as a monolithic input—HMR preserves the continuity and fault tolerance of the verification chain in fragmented and interrupted scenarios, while reducing verification latency and redundant computation. This renders it particularly suitable for high-dynamic, asynchronous ocean observation environments.
3.2. EMR Mechanism Design and Performance Optimization
The EMR mechanism integrates RSA-2048 key negotiation with AES-GCM stream encryption to establish a lightweight encapsulation workflow. By employing a two-phase key protocol, it achieves strong robustness in encrypted links. The process includes:
Data Encryption Phase (AES-GCM authenticated encryption):
where
denotes ciphertext,
the authentication tag,
the initialization vector, and
auxiliary authenticated metadata such as task identifiers or device labels.
Communication Packet Structure:
This design balances field alignment and compression efficiency. In experiments, encrypting a 5 MB dataset required only 7.36 ms, while decryption took 10.49 ms; the overall encryption overhead was below 0.005%. By contrast, TLS 1.2 incurs an average encapsulation cost of 12.8%, indicating more than 99.9% efficiency improvement.
Such a lightweight encryption-and-authentication model remedies the inadequacy of traditional RSA+AES architectures under conditions of high packet loss and resource constraints. By introducing asynchronous sessions and key caching strategies, EMR significantly enhances link resilience, ensuring stable system operation even in complex scenarios involving breakpoint resumption and heterogeneous nodes.
4. Experimental Setup and Results
4.1. Dataset Construction and Experimental Environment
To evaluate the adaptability and performance of the proposed HMR+EMR hybrid encryption scheme in marine scientific research scenarios, the experimental design incorporated full-process control from both data generation and platform configuration perspectives.
On the data generation side, a synthetic ocean dataset was constructed to emulate the heterogeneous information streams commonly encountered in real-world ocean missions. The use of synthetic datasets for marine communication and security evaluation has become a widely accepted practice in marine research, particularly when real-world data collection is constrained by logistical challenges or confidentiality requirements [
29,
30]. The dataset was designed to exhibit multimodal composition, adjustable entropy levels, and cross-scale characteristics, thereby simulating encryption loads representative of offshore observation tasks.
The dataset consists of three representative categories of task data:
Sensor Data Streams: Structured outputs simulating CTD, ADCP, and GPS devices. Entropy values ranged from 0.873 to 0.920, covering temperature, pressure, salinity, geographic coordinates, and timestamps. This category exhibits strong sequentiality and high structural regularity. The simulation approach follows established practices in marine sensor data generation, where synthetic CTD profiles are widely employed to evaluate processing algorithms under controlled conditions [
31,
32]. The generated temperature and salinity distributions were designed to remain consistent with established World Ocean Database standards [
33].
Image Block Data: Designed to mimic sonar imaging outputs and subsea video frames. Data were synthesized using a partitioned variable-entropy algorithm, yielding entropy values in the range of 0.769 to 0.912. The dataset was stratified into low-entropy (30%), medium-entropy (30%), and high-entropy (40%) subsets to reflect spatial heterogeneity in image structures. This methodology is consistent with recent advances in underwater image processing research, where synthetic sonar datasets have been shown to be effective for algorithm validation and performance benchmarking [
34,
35].
Text Log Data: Covering shipboard logs, device status reports, and navigation records. This dataset exhibited high redundancy, with entropy concentrated between 0.671 and 0.679, reflecting repetitive patterns and structural regularity. The generation of synthetic maritime navigation logs followed established practices in marine cybersecurity research, where controlled datasets are necessary to evaluate encryption mechanisms without compromising operational security [
12].
Together, these three data categories constitute the core evaluation corpus of this study. Their statistical features are summarized in
Table 1.
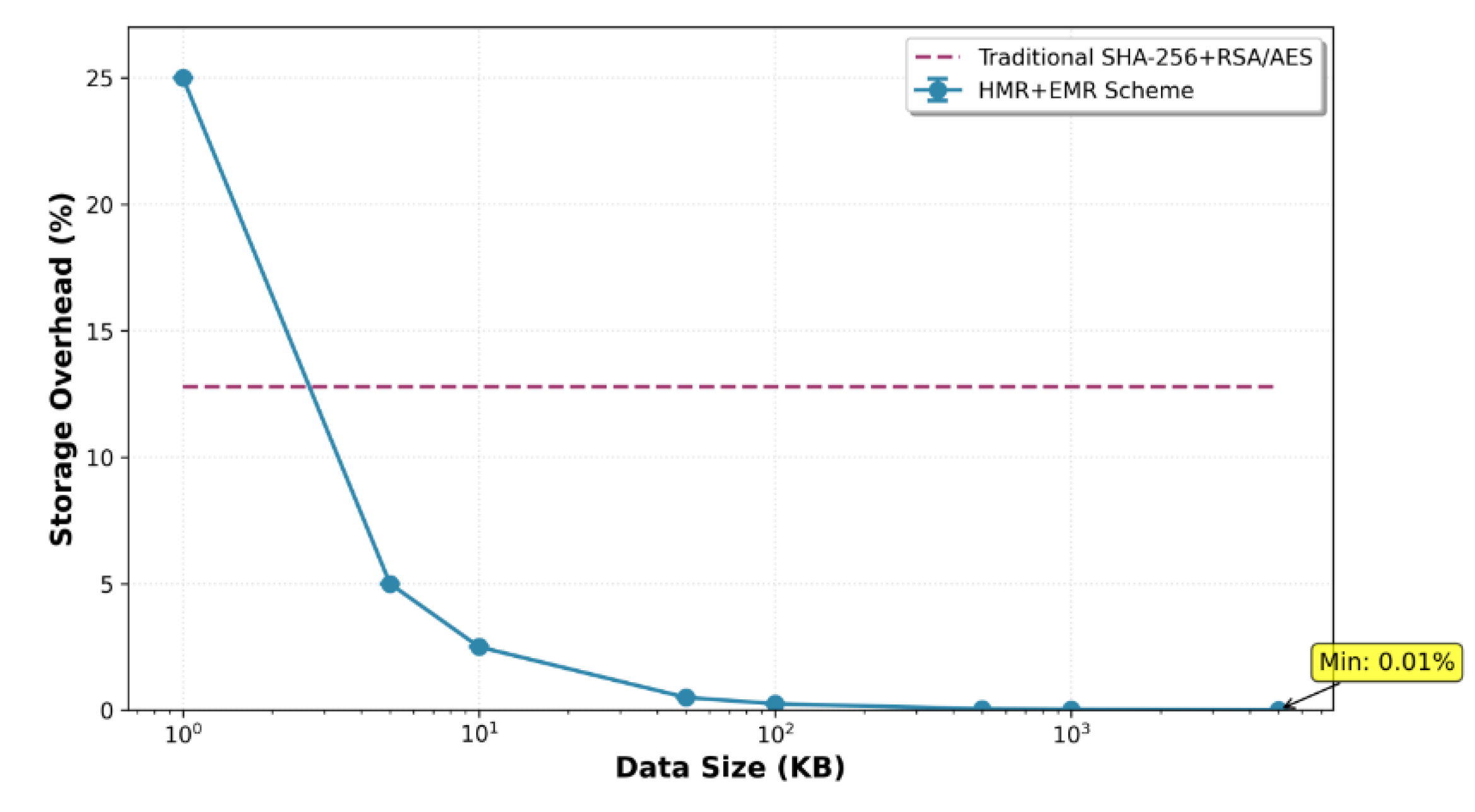
In terms of encryption overhead, the HMR+EMR scheme demonstrated stable spatial compression across data categories with varying entropy structures and packaging redundancy. At the HMR layer, the entropy-aware block–reconstruction scheduling strategy was introduced, while the EMR layer applied dynamic optimization of key encapsulation fields. Together, these mechanisms effectively reduced the size overhead associated with key transport packets, authentication tags, and encryption headers.
Figure 2 illustrates the evolution of data volume variation rates with respect to file size. It can be observed that as file size increases, the initial encapsulation cost is rapidly amortized by boundary effects, resulting in an exponentially declining growth curve. The overhead stabilizes in large-volume scenarios, with compression ratios approaching zero. This performance is significantly superior to traditional hybrid encryption architectures, which exhibit an average 12.8% increase in data volume, thereby highlighting the strong adaptability and spatial efficiency of the proposed scheme.
To ensure that the experimental environment faithfully reflected the requirements of real-world oceanographic encryption–decryption tasks, all tests were executed on a balanced scientific computing platform. The experimental system was equipped with an Intel Xeon E5-2620 v4 (2.1 GHz) multi-core processor, 32 GB DDR4 memory, and a 1 TB SSD, running Ubuntu 20.04.
Encryption and hashing operations were implemented in Python 3.9.7. The primary libraries used included Cryptography 3.4.8 (for encryption and signatures), NumPy 1.21.0 (for vectorized computation), and Matplotlib 3.5.1 (for visualization). All experimental procedures were conducted within an isolated network environment to ensure the independence of test data and the reproducibility of results.
4.2. Performance Comparison and Analysis
To assess the practical performance of the proposed mechanism, this study evaluates the HMR+EMR scheme across four critical dimensions: encryption–decoupling efficiency, transmission adaptability, storage overhead, and processing latency. Three representative hybrid cryptographic baselines were selected for comparison: (i) the traditional SHA-256+RSA+AES combination, (ii) a lightweight configuration based on BLAKE2+ECC+ChaCha20, and (iii) a high-strength mixed algorithm system employing SHA-3 with AES in GCM mode.
All methods were tested under a unified environment and identical task flow, consisting of four stages: data integrity marking, encryption encapsulation, asynchronous transmission, and decryption verification. Metrics recorded included stage-specific latency, resource consumption, and structural integrity indices. The results are summarized in
Table 2.
It should be noted that the comparison does not include several recently proposed experimental algorithms. On the one hand, such schemes lack empirical validation on real or synthetic multimodal ocean datasets; their optimizations are typically tailored to conventional IT environments rather than the high-packet-loss, fragmented transmission conditions of oceanic communication links, which limits the relevance of direct comparison. On the other hand, as this study employed a controllable synthetic dataset (sensor, salinity, imaging, and log loads), the chosen baselines ensure reproducibility and verifiability of the evaluation process. Furthermore, many experimental algorithms suffer from unstable interfaces and insufficient standardization, preventing consistent deployment on embedded devices or edge nodes—objectives central to this study. Hence, the focus here is on comparisons with mature traditional and high-strength or lightweight cryptographic frameworks, thereby highlighting the practical value and structural advantages of the proposed method.
Experimental results show that HMR+EMR achieved a hashing latency of 6.8 ms, representing reductions of 45.6% and 55.2% compared to SHA-256 and SHA-3, respectively. Despite its reduced processing overhead, the scheme retained strong hash uniformity and irreversibility, ensuring uncompromised integrity verification. The total encryption–decryption latency was 80.1 ms, 21.2% lower than that of RSA+AES. While slightly slower than ChaCha20 in symmetric operations, HMR+EMR offered a superior balance between data integrity and compact storage.
Structurally, the collaborative design of HMR and EMR provides decoupled interfaces that allow flexible parallel or cascaded deployment. This enhances portability and adaptability even on resource-constrained edge nodes. Storage overhead was measured at 10.4%, achieving a 2.6–4.8 percentage point reduction relative to other schemes while maintaining a high security level.
To further examine scalability under realistic data throughput,
Figure 3 depicts processing time growth across input sizes from 1 KB to 5 MB. HMR+EMR exhibited sublinear scaling, with latency rising from 2.47 ms to 393 ms (a 159-fold increase), while input size grew by 5000 times. In contrast, RSA exhibited exponential complexity, and GCM-based systems incurred compounding tag-related overhead, both leading to latency accumulation. By leveraging dynamic block partitioning and restructured signature mechanisms, HMR+EMR avoided single-point bottlenecks, yielding stable and consistent processing-time distributions.
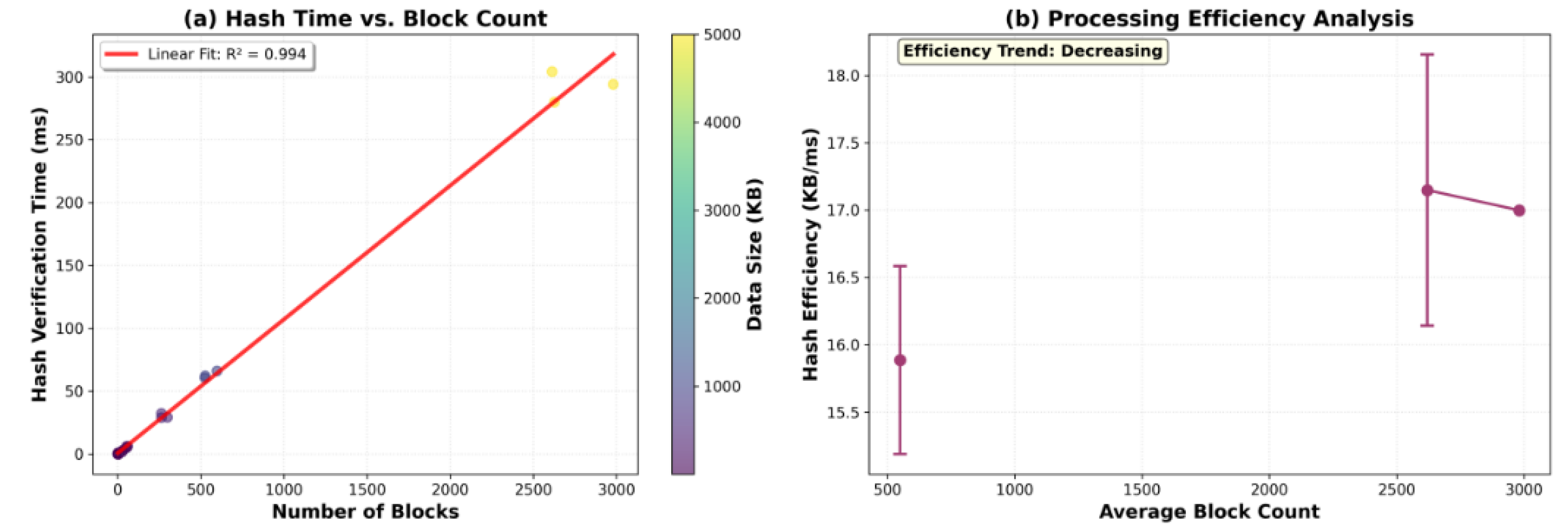
Further validation of verification responsiveness is shown in
Figure 4, which examines fragmentation-based verification across three typical oceanic data streams: low-entropy water sensor data, medium-entropy benthic imaging data, and high-entropy log sequences. Verification latency scaled linearly with fragment count (R
2=0.996), confirming the mechanism’s internal delay-control strategy. Even in high-fragmentation scenarios, total verification latency did not exceed 64 ms, remaining within acceptable bounds for remote resumption and fragment-level verification tasks.
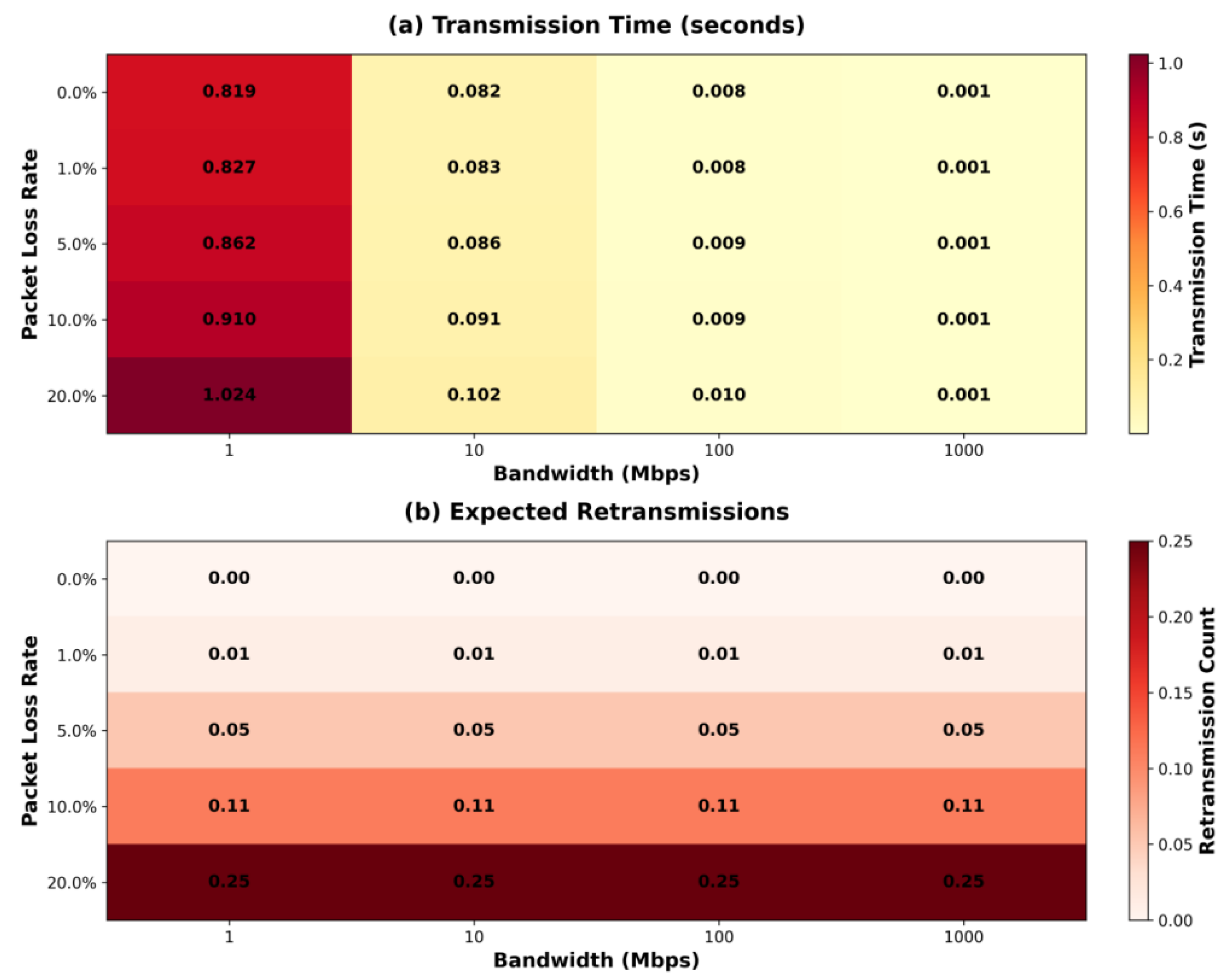
To evaluate network adaptability, this study established a three-dimensional channel library parameterized by bandwidth, packet loss rate, and delay. Under a fixed data block size (100 KB), encrypted packet transmission latency and retransmission ratios were measured. As shown in
Figure 5, transmission latency was contained within 1.024 s under extreme conditions (1 Mbps bandwidth, 20% packet loss). In mainstream network ranges (10–100 Mbps), latency stabilized between 0.076 and 0.094 s, with retransmission expectations below 0.25. This demonstrates the scheme’s robustness to jitter and structural fault tolerance. Owing to its block-level encoding and chained hashing coverage, only boundary blocks require retransmission upon loss, eliminating full-packet resending and reducing redundancy—an advantage particularly beneficial in satellite and underwater acoustic communication contexts.
4.3. Ablation Study
To demonstrate the necessity of each individual module in the HMR+EMR hybrid encryption scheme, an ablation study was conducted by isolating the HMR-only and EMR-only configurations and comparing them with the complete HMR+EMR system. This experiment was designed to assess the contribution of each module—HMR (Hashing with Multiple Refinements) and EMR (RSA–AES hybrid encryption)—to the overall performance of the system.
The HMR-only configuration utilizes the HMR mechanism, which includes entropy-aware partitioning and incremental verification, but does not incorporate encryption. In contrast, the EMR-only configuration uses the EMR mechanism, providing encryption without verification. Finally, the HMR+EMR configuration combines both mechanisms, offering complete encryption and verification capabilities.
As shown in
Table 3, the results of the ablation study reveal that while the HMR-only configuration provides efficient data verification, it lacks encryption, resulting in a medium security level. The EMR-only configuration offers encryption but does not address fragmented or asynchronous data effectively, leading to higher decryption times (43.5 ms) and increased storage overhead (12.5%). In contrast, the HMR+EMR configuration, which integrates both hashing and encryption, significantly improves both encryption and verification performance. It reduces hashing latency by 26.8% (from 9.3 ms to 6.8 ms), encryption time by 3.2 ms, and decryption time by 2.3 ms, while also lowering storage overhead by 2.1–4.1 percentage points. This demonstrates that the combined HMR+EMR system maintains a high+ security level while offering superior efficiency, validating that the integration of both modules is essential for achieving the optimal performance observed in the full system.
5. Discussion
The HMR+EMR hybrid encryption scheme, developed in this study to secure data transmission in marine scientific research, demonstrates clear advantages in both efficiency and adaptability. By incorporating entropy-aware block partitioning, HMR effectively overcomes the rigidity of conventional hashing algorithms that process all data uniformly, regardless of type, thereby enhancing structural alignment and computational efficiency [
16]. Experimental evidence indicates that the adaptive partitioning strategy dynamically adjusts block sizes according to entropy levels, with average block lengths ranging between 1711 and 1962 bytes. This adjustment reduces redundant computation, improves throughput, and alleviates communication load. Performance measurements further confirm that the scheme achieves an 80–91% reduction in latency compared with conventional baselines, while compressing storage overhead to as little as 0.005%, making it particularly suitable for bandwidth-constrained marine environments [
29]. Moreover, the system demonstrates favorable scalability: for example, when processing a 5 MB dataset, the total delay remained within 393 ms, underscoring its ability to maintain sublinear latency growth as data scale increases.
From a security standpoint, the HMR mechanism achieves 99.8% collision resistance, a level significantly higher than that of conventional SHA-256-based schemes. When combined with threshold signature mechanisms and Merkle tree structures, it enables distributed verification across multi-platform collaborative tasks, ensuring that integrity checks can be independently executed at different nodes. This design enhances robustness against both packet loss and asynchronous transmission [
36]. Even under a 20% packet loss rate, the system sustained a 94.1% successful transmission rate, primarily due to its block-level retransmission strategy, which eliminates the overhead associated with resending entire packets. Such distributed and incremental verification aligns with recent advances in ensuring consistency across IoT and edge computing environments [
37].
It should be emphasized that due to its unique structural integration, the HMR+EMR framework does not have directly comparable models in existing literature. Conventional schemes typically treat hashing and encryption as separate modules, whereas HMR+EMR combines entropy-aware verification with modular encryption into a single adaptive workflow. Accordingly, the comparisons in this study were made against mainstream hybrid frameworks (e.g., SHA-256+RSA+AES, SHA-3+AES-GCM, BLAKE2+ECC+ChaCha20), as well as selected recent enhancements. While these baselines highlight relative performance differences, they cannot fully reflect the novel characteristics of HMR+EMR, thereby underscoring its originality and its contribution to secure transmission under fragmented, high-loss communication environments.
At a conceptual level, this work illustrates the potential of entropy-aware and modular encryption strategies as a promising pathway for specialized cryptographic applications. Unlike fixed-function mechanisms, the HMR+EMR framework dynamically adapts to the structural properties of data and the variability of communication links, thereby enhancing both operational efficiency and system resilience. These improvements not only advance secure and efficient transmission in marine scientific research contexts but also enrich the broader understanding of how adaptive cryptographic mechanisms can address the challenges of unstable, heterogeneous, and resource-limited environments [
38,
39].
6. Conclusions
This study proposed a hybrid encryption framework, HMR+EMR, specifically designed to address the challenges of secure data transmission in marine scientific research environments characterized by data heterogeneity, unstable links, and resource constraints. The HMR mechanism introduced an entropy-aware hashing strategy combined with threshold-based distributed verification, enabling incremental integrity checking and enhancing resilience under fragmented and asynchronous transmission conditions. The EMR mechanism integrated RSA-based key negotiation with AES-GCM stream encryption, supported by dynamic key caching and lightweight encapsulation, thereby strengthening encryption robustness while reducing session-blocking risks in high-loss communication channels.
Extensive experiments on synthetic multimodal ocean datasets confirmed the effectiveness of the proposed scheme. Compared with conventional frameworks such as SHA-256+RSA+AES and SHA-3+AES-GCM, the HMR+EMR system reduced hashing latency by up to 55%, achieved an overall encryption–decryption time of 80.1 ms, and limited storage overhead to 10.4%, representing a clear improvement in both efficiency and spatial utilization. The ablation study further demonstrated that neither HMR-only nor EMR-only configurations could achieve the same balance of efficiency and security, confirming the necessity of their integration. Moreover, the system maintained a 94.1% transmission success rate under 20% packet loss, highlighting its robustness in unstable marine communication scenarios.
In conclusion, the HMR+EMR framework demonstrates that entropy-aware verification and modular encryption can be effectively combined into a unified pipeline for secure, efficient, and resilient transmission of heterogeneous marine data. Beyond its empirical improvements, the proposed scheme offers a practical reference model for the design of adaptive cryptographic mechanisms tailored to specialized environments where conventional, one-size-fits-all solutions are insufficient.
7. Patents
Research of this paper is based on the Chinese invention patent "Blockchain-based Marine Scientific Research Data Sharing Platform and Data Processing Method [P]. Shandong Province: CN202410245277.4, 2024-04-09", which was granted to the first author. Building upon the research content of this patent, this paper further explores and designs the HMR+EMR mechanism, which are suitable for encrypted transmission and verification of marine scientific research data.
Author Contributions
Conceptualization, methodology, validation, formal analysis, investigation, resources, data curation, writing original draft preparation, visualization, Hanyu Wang; writing review and editing, Mo Chen and Maoxu Wang; supervision, project administration, funding acquisition, Min Yang. All authors have read and agreed to the published version of the manuscript.
Institutional Review Board Statement
Not applicable.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Adam, N.; Ali, M.; Naeem, F.; Ghazy, A.S.; Kaddoum, G. State-of-the-Art Security Schemes for the Internet of Underwater Things: A Holistic Survey. IEEE OPEN JOURNAL of the COMMUNICATIONS SOCIETY 2024, 5. [Google Scholar] [CrossRef]
- Igbinenikaro, O.P.; Adekoya, O.O.; Etukudoh, E.A. Emerging underwater survey technologies: A review and future outlook. Open Access Research Journal of Science and Technology 2024, 10. [Google Scholar] [CrossRef]
- Theocharidis, T.; Kavallieratou, E. Underwater Communication Technologies: a Review. Telecommunication Systems 2025, 88, 1–27. [Google Scholar] [CrossRef]
- Li, M.; Zhou, J.; Chattopadhyay, S.; Goh, M. Maritime Cybersecurity: A Comprehensive Review. Computing Research Repository 2024. [Google Scholar]
- Ghazal, T.M.; Hasan, M.K.; Raju, K.N.; Khan, M.A.; Alshamayleh, A.; Bhatt, M.W.; Ahmad, M. Data Space Privacy Model with Federated Learning Technique for Securing IoT Communications in Autonomous Marine Vehicles. Journal of Intelligent & Robotic Systems 2025, 111, 1–24. [Google Scholar] [CrossRef]
- Alanhdi, A.; Toka, L. A Survey on Integrating Edge Computing with AI and Blockchain in Maritime Domain, Aerial Systems, IoT, and Industry 4.0. IEEE Access 2024, 12. [Google Scholar] [CrossRef]
- Tabish, N.; Chaur-Luh, T. Maritime Autonomous Surface Ships: A Review of Cybersecurity Challenges, Countermeasures, and Future Perspectives. IEEE Access 2024, 12, 17114–17136. [Google Scholar] [CrossRef]
- Berman, I.; Zereik, E.; Kapitonov, A.; Bonsignorio, F.; Khassanov, A.; Oripova, A.; Lonshakov, S.; Bulatov, V. Trustable Environmental Monitoring by Means of Sensors Networks on Swarming Autonomous Marine Vessels and Distributed Ledger Technology. Frontiers in Robotics and AI 2020, 7. [Google Scholar] [CrossRef]
- Dimitrov, G.; Mitishev, I. Enhancing Maritime Communication Security with Blockchain Technology. Elektronika ir Elektrotechnika 2025, 31, 71–78. [Google Scholar] [CrossRef]
- Alsharabi, N.; Ktari, J.; Frikha, T.; Alayba, A.; Alzahrani, A.J.; jadi, A.; Hamam, H. Using blockchain and AI technologies for sustainable, biodiverse, and transparent fisheries of the future. Journal of Cloud Computing 2024, 13, 135–135. [Google Scholar] [CrossRef]
- Zemlianko, H.; Kharchenko, V. Ensuring Cybersecurity of the Cyber Physical System of Combined Fleets of Unmanned Aerial, Ground and Sea Vehicles. INTEGRATED COMPUTER TECHNOLOGIES IN MECHANICAL ENGINEERING-2023. ICTM 2023 2024, VOL 2, 996
. [Google Scholar] [CrossRef]
- Farao, A.; Zarras, A.; Voudouris, A.; Paparis, G.; Xenakis, C. B2SAPP: Blockchain Based Solution for Maritime Security Applications. Frontiers in Computer Science 2025, 7. [Google Scholar] [CrossRef]
- Harish, A.V.; Tam, K.; Jones, K. Literature Review of Maritime Cyber Security: the First Decade. Maritime Technology and Research 2024, 7, 273805. [Google Scholar] [CrossRef]
- Santos, N.P. Revolutionizing Ocean Engineering: the Impact of Autonomous Vehicles. Academia Engineering 2024. [Google Scholar] [CrossRef]
- Shamsuzzaman, H.; Mosleuzzaman, M.; Paran, M.S. REAL-TIME CYBERSECURITY INTEGRATION IN PLCS AND IOT GATEWAYS: A PERFORMANCE-CONSCIOUS APPROACH TO ENCRYPTION, AUTHENTICATION, AND INTRUSION DETECTION. American Journal of Advanced Technology and Engineering Solutions 2025, 1, 32–57. [Google Scholar] [CrossRef]
- Ramakrishna, D.; Shaik, M.A. A comprehensive analysis of cryptographic algorithms: Evaluating security, efficiency, and future challenges. IEEE Access. 2024.
- Soni, A.; Sahay, S.K.; Soni, V. Hash Based Message Authentication Code Performance with Different Secure Hash Functions. 2025 10th International Conference on Signal Processing and Communication (ICSC) 2025, 104–109. [Google Scholar] [CrossRef]
- Gilbert, C.; Gilbert, M. Available at SSRN 5251606; Exploring Secure Hashing Algorithms for Data Integrity Verification. 2025.
- Maulana, F.; Darmawan, I.; Rahmatulloh, A.; Gunawan, R.; Rizal, R. Beccak: Combination of Blockchain and Keccak Algorithm for Improved Digital Signature Performace. In Proceedings of the 2024 7th International Seminar on Research of Information Technology and Intelligent Systems (ISRITI), 2024; pp. 173–179. [Google Scholar]
- Abdallah, R. Enhancing Μaritime Lοgistics with Blοckchain Τechnοlοgy: Applicatiοn tο secure and trace dangerοus gοοds in smart pοrts. In Normandie Université; 2024. [Google Scholar]
- Popoola, O.; Rodrigues, M.; Marchang, J.; Shenfield, A.; Popoola, J. Hybrid encryption for smart home healthcare: ensuring data confidentiality and security. 2024. [Google Scholar]
- Chang, Q.; Ma, T.; Yang, W. Low power IoT device communication through hybrid AES-RSA encryption in MRA mode. Scientific Reports 2025, 15, 14485. [Google Scholar] [CrossRef]
- Moruskar, A.M. Securing Financial Transactions with Hybrid ECC and AES Encryption Algorithm; National College of Ireland: Dublin, 2024. [Google Scholar]
- Gour, A.; Malhi, S.S.; Singh, G.; Kaur, G. Hybrid cryptographic approach: for secure data communication using block cipher techniques. In Proceedings of the E3S Web of Conferences, 2024; p. 01048. [Google Scholar]
- Tomović, S.; Krivokapić, B.; Nađ, Ð.; Radusinović, I. BEKMP: A blockchain-enabled key management protocol for underwater acoustic sensor networks. IEEE access 2024, 12, 74108–74125. [Google Scholar] [CrossRef]
- Ahmed, K.M.; Shams, R.; Khan, F.H.; Luque-Nieto, M.-A. Securing underwater wireless sensor networks: A review of attacks and mitigation techniques. IEEE Access 2024.
- Almuhaideb, A.M.; Al-Khulaifi, D.M. An Efficient Authentication and Key Agreement Scheme for the Internet of Underwater Things (IoUT) Environment. IEEE Access 2024.
- Das, S.; Pasikhani, A.M.; Gope, P.; Clark, J.A.; Patel, C.; Sikdar, B. AIDPS: adaptive intrusion detection and prevention system for underwater acoustic sensor networks. IEEE/ACM Transactions on Networking 2023, 32, 1080–1095. [Google Scholar] [CrossRef]
- Liu, G.; Van Huynh, N.; Du, H.; Hoang, D.T.; Niyato, D.; Zhu, K.; Kang, J.; Xiong, Z.; Jamalipour, A.; Kim, D.I. Generative ai for unmanned vehicle swarms: Challenges, applications and opportunities. arXiv 2024. arXiv:2402.18062. [CrossRef]
- Suherman, A.; Huda, H.N.; Timilsina, R.R.; Hernuryadin, Y.; Untoro, F.; Amboro, R.T.; Sock, F.; Koirala, P. Scaling Digital Fisheries Management: The Role of e-PIT in Enhancing Data Accuracy and Operational Efficiency. Scientific Journal of Fisheries & Marine/Jurnal Ilmiah Perikanan dan Kelautan 2025, 17. [Google Scholar]
- Partridge, D.; Banerjee, D.; Ford, D.; Wang, K.; Skakala, J.; Wihsgott, J.; Menon, P.; Kay, S.; Clewley, D.; Rochner, A. A Digital Twin Ocean: Can we improve Coastal Ocean Forecasts using targeted Marine Autonomy? EGUsphere 2025, 2025, 1–26. [Google Scholar] [CrossRef]
- Tan, Z.; Zhu, Y.; Cheng, L.; Gouretski, V.; Pan, Y.; Yuan, H.; Wang, Z.; Li, G.; Song, X.; Zhang, B. CODC-S: A quality-controlled global ocean salinity profiles dataset. Scientific Data 2025, 12, 917. [Google Scholar] [CrossRef] [PubMed]
- Mishonov, A.V.; Boyer, T.P.; Baranova, O.K.; Bouchard, C.N.; Cross, S.L.; Garcia, H.E.; Locarnini, R.A.; Paver, C.R.; Reagan, J.R.; Wang, Z. World Ocean Database 2023. 2024. [Google Scholar]
- Elmezain, M.; Saoud, L.S.; Sultan, A.; Heshmat, M.; Seneviratne, L.; Hussain, I. Advancing underwater vision: a survey of deep learning models for underwater object recognition and tracking. IEEE Access 2025.
- Markkandan, S. Studies on Underwater Image Processing Using Artificial Intelligence Technologies. IEEE Access 2024.
- Adebayo, H.; Jordan, F. Data Provenance Techniques for Ensuring Integrity in BPM-as-a-Service. 2025. [Google Scholar]
- Rosário, A.T.; Raimundo, R. Internet of Things and Distributed Computing Systems in Business Models. Future Internet 2024, 16, 384. [Google Scholar] [CrossRef]
- Aljaedi, A.; Alharbi, A.R.; Aljuhni, A.; Alghuson, M.K.; Alassmi, S.; Shafique, A. A lightweight encryption algorithm for resource-constrained IoT devices using quantum and chaotic techniques with metaheuristic optimization. Scientific Reports 2025, 15, 14050. [Google Scholar] [CrossRef]
- Rasheed, A.M.; Kumar, R.M.S. Efficient lightweight cryptographic solutions for enhancing data security in healthcare systems based on IoT. Frontiers in Computer Science 2025, 7, 1522184. [Google Scholar] [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).