1. Introduction
1.1. Overview of Agile Development Methodologies
Agile development methodologies represent a modern approach to software engineering that emphasizes flexibility, collaboration, and iterative progress. These methodologies enable teams to deliver high-quality software in incremental cycles known as sprints or iterations, allowing for continuous improvement and adaptation to changing requirements. Popular Agile frameworks include Scrum, Kanban, Extreme Programming (XP), and Feature-Driven Development (FDD), each focusing on specific principles such as rapid delivery, visual task management, and continuous feedback. The core idea is to break down projects into manageable parts, deliver working software frequently, and engage customers early and regularly throughout the development lifecycle.
1.2. Importance of Security in Rapid Development Cycles
In the fast-paced world of Agile, where development cycles are short and continuous delivery is the norm, integrating security practices becomes critical. Unlike traditional waterfall models where security might be a distinct phase near the end, Agile demands embedding security throughout each sprint. Rapid changes and frequent releases introduce the risk of security gaps if not managed properly. Security integration ensures vulnerabilities are detected and addressed early, reducing the risk of costly fixes later and preventing attackers from exploiting weaknesses in deployed software. Maintaining security in Agile also aligns with the methodology's principles of delivering value and quality to users consistently and reliably.
1.3. Rising Threat of Injection Vulnerabilities and Logic Flaws
Injection vulnerabilities, such as SQL injection and cross-site scripting, remain among the most prevalent and dangerous security threats in software development. These arise when untrusted input is improperly handled, allowing attackers to execute arbitrary commands or access sensitive data. Alongside injection flaws, logic flaws—errors in the intended behavior or business logic of an application—can cause severe security breaches and operational failures. As software complexity grows, the likelihood and impact of such vulnerabilities increase. This rising threat underscores the need for secure coding, vigilant testing, continuous developer training, and automated tools to detect and prevent these vulnerabilities effectively within Agile workflows.
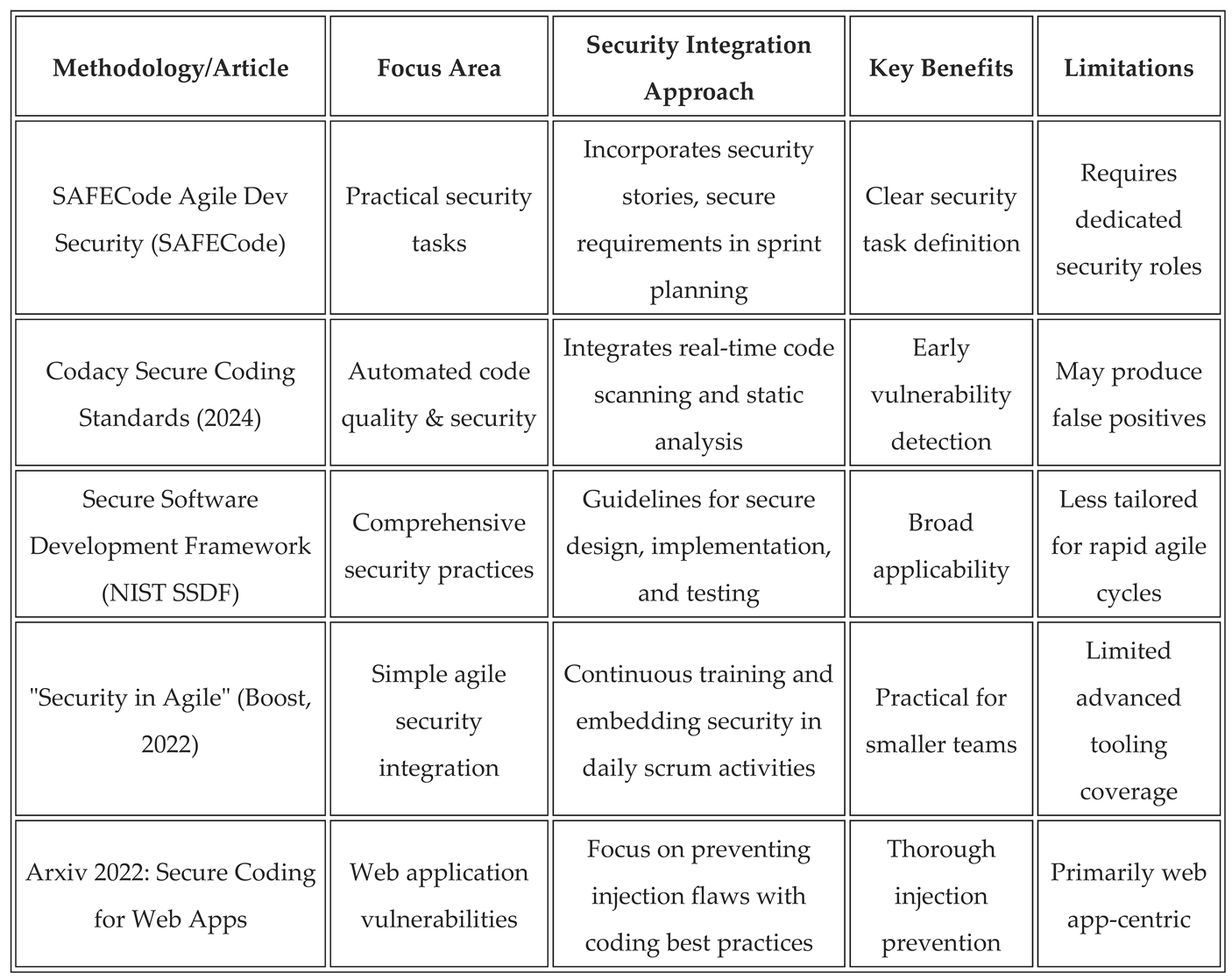
2. Literature Survey
The integration of secure coding practices in agile development explores existing studies, frameworks, and methodologies that address security challenges within fast-paced, iterative software development environments. This review highlights various approaches to embedding security measures, developer training, and automated tools to prevent injection vulnerabilities and logic flaws. It focuses on how different research and industry practices have evolved to balance security with the flexibility and speed demanded by agile methodologies.
Table 1.
Comparison of Methodologies and Articles on Secure Coding in Agile Development.
Table 1.
Comparison of Methodologies and Articles on Secure Coding in Agile Development.
3. Fundamentals of Secure Coding Practices
3.1. Principles of Secure Software Design
Secure software design is grounded in fundamental principles that ensure applications are resilient to attacks and failures. Key among these principles is the "Principle of Least Privilege," which mandates that users and components have only the minimum permissions required for their tasks, reducing potential attack surfaces. Another is "Defense in Depth," which layers security controls so that breaching one layer does not compromise the entire system. Input validation is crucial, ensuring all incoming data is checked against expected types, lengths, and formats to prevent malicious input exploitation. The principle of "Fail-Secure" ensures that systems default to a secure state in case of errors, avoiding exposure of sensitive information. Collectively, these principles form a secure-by-design approach that proactively mitigates vulnerabilities from the outset of development.
3.2. Common Vulnerabilities: SQL Injection, XSS, CSRF, and Logic Exploits
Injection attacks like SQL Injection occur when untrusted inputs are concatenated directly into database queries, allowing attackers to execute arbitrary SQL commands. This vulnerability is often mitigated by using parameterized queries or prepared statements. Cross-Site Scripting (XSS) exploits occur when attackers inject malicious scripts into web pages viewed by other users, typically prevented by output encoding and content security policies. Cross-Site Request Forgery (CSRF) attacks trick authenticated users into submitting unauthorized requests, mitigated by implementing anti-CSRF tokens and strict validation. Logic flaws stem from errors in the application's intended workflow or rules, such as incorrect authorization checks, and often require thorough threat modeling and scenario-based testing to detect. Mathematically, validating inputs can be expressed as ensuring that for input , function outputs only values within an allowed range or set, formally where .
3.3. Security Standards and Compliance (OWASP, CERT, ISO/IEC)
Organizations rely on established security standards to guide secure coding practices. The OWASP Top Ten provides a prioritized list of prevalent web security risks, including injection flaws and broken authentication, serving as a basis for many secure coding frameworks. CERT offers coding standards that provide language-specific guidelines to avoid common security bugs. The ISO/IEC 27001 and 27034 standards define requirements for information security management systems and secure software development processes, respectively. Compliance with these standards ensures consistency in security implementation and helps organizations meet regulatory requirements. Formal models like the Bell-LaPadula model for information flow control underpin these standards by enforcing properties such as "no read up" and "no write down," ensuring data confidentiality and integrity across system interactions.
4. Integration of Secure Coding in Agile Workflows
4.1. Security-Focused Sprint Planning
In Agile workflows, sprint planning establishes the short development cycles for incremental delivery. Integrating secure coding involves embedding security objectives directly into sprint goals. This can be achieved by including security-related user stories such as vulnerability assessments, input validation, and authentication checks in each sprint backlog. Prioritizing these stories based on risk assessments ensures security concerns are addressed early. The sprint planning formula can conceptually be seen as optimizing the sprint backlog
to maximize both functionality
and security
, expressed as:
where
reflects the weighting given to security tasks, balancing feature development and risk mitigation effectively. This approach ensures a continuous focus on security without impeding delivery velocity.
4.2. Incorporating Threat Modeling in Agile Phases
Threat modeling is a proactive practice used to identify potential security risks by analyzing application architecture and design. In Agile, it is integrated iteratively in early phases such as sprint zero or initiation, and revisited as the feature scope evolves. Teams collaborate to identify threats using models like STRIDE (Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, Elevation of privilege). Threat identification
is mapped against mitigations
to generate a risk score
that helps prioritize security work:
This quantitative risk scoring supports risk-based prioritization within backlog grooming, ensuring security efforts align with threat severity and likelihood throughout development.
4.3. Security in Product Backlog and User Stories
Security must be a first-class citizen in the product backlog to guarantee consistent consideration. Security acceptance criteria are added to user stories, defining explicit conditions for secure behavior before stories are marked done. For example, a user story for login might require criteria such as enforced multi-factor authentication and prevention of brute-force attacks. This embeds secure coding expectations directly into development tasks, making security a shared responsibility. The backlog thus contains a mix of functional and security stories, with continuous refinement cycles adapting to emerging threats and compliance needs. Such integration enhances transparency, traceability, and accountability for security in every sprint cycle.
5. Continuous Developer Training for Vulnerability Prevention
5.1. Role of Security Awareness and Training Programs
Security awareness and training programs play a crucial role in equipping developers with the knowledge and mindset necessary to prevent vulnerabilities like injection flaws and logic errors. These programs foster a security-first culture where developers recognize security risks early and apply best practices consistently. Continuous training ensures that developers stay updated on emerging threats, secure coding conventions, and organizational policies. The effectiveness of these programs can be tracked using metrics such as training completion rates and improvement in secure coding practices, where an increase in secure code commits
over time
indicates positive impact:
5.2. Gamified Secure Coding Exercises and Skill Enhancement
Gamification integrates game mechanics into training to boost engagement, retention, and practical skill acquisition. Key features include interactive challenges, leaderboards, and rewards that motivate continuous learning. Studies show gamified training can increase developer engagement by over 60%, helping translate awareness into actionable secure coding behavior. Exercises like Capture the Flag (CTF) events simulate real-world attacks, allowing developers to practice identifying and fixing vulnerabilities in a competitive environment. Metrics such as knowledge retention rates
, engagement
, and behavior change
can be modeled to evaluate impact:
Higher values correlate with better training outcomes and fewer security incidents.
5.3. Embedding Secure Design Knowledge Across Teams
Embedding secure design knowledge across development teams ensures that security considerations permeate every phase, from architecture design to deployment. Cross-functional knowledge sharing sessions, secure design pattern libraries, and mentorship programs help disseminate critical insights. The diffusion of secure knowledge
within a team of size
over training sessions
can be approximated using the formula:
where
is the probability of knowledge transfer per session. Maximizing
maintains a collective security competency that reduces risks introduced by isolated or uninformed team members.
6. Real-Time Code Scanning and Continuous Security Validation
6.1. Static Application Security Testing (SAST) Integration
Static Application Security Testing (SAST) is a white-box testing method that analyzes an application’s source code, bytecode, or binary without executing it. SAST tools parse code to build internal representations such as Abstract Syntax Trees (AST) and Control Flow Graphs (CFG), enabling detection of vulnerabilities like SQL injection and cross-site scripting at early stages in the software development lifecycle. Integration into development environments and CI/CD pipelines provides continuous feedback, allowing developers to remediate issues before deployment. The effectiveness of SAST can be conceptualized through analyzing code against a rule set , with vulnerabilities detected when code segments violate rules , mathematically .
6.2. Dynamic Analysis (DAST) and Runtime Monitoring
Dynamic Application Security Testing (DAST) complements SAST by testing applications in runtime environments. DAST simulates external attacks on a live application to identify vulnerabilities that only manifest during execution, such as authentication bypass or injection flaws due to unexpected inputs. Runtime monitoring extends DAST by continuously observing application behavior for anomalies and policy violations to detect and respond to attacks in real-time. Combining static and dynamic methodologies provides comprehensive coverage across the application lifecycle.
6.3. CI/CD Pipeline Security with Automated Scanners
Automated security scanners integrated into Continuous Integration/Continuous Deployment (CI/CD) pipelines enable security validation as part of the build and release process. This integration enforces security gates that block progression upon detection of critical vulnerabilities, ensuring insecure code is not deployed. With incremental scanning and real-time feedback loops, the security posture improves while maintaining agile delivery speeds. The pipeline security effectiveness
can be modeled as a function of scan frequency
, detection accuracy
, and remediation rate
:
Maximizing these variables leads to reduced vulnerabilities and faster mitigation.
6.4. Secure Code Review and Pair Programming
Manual secure code review, enhanced through pair programming, allows developers to identify complex logic flaws, design weaknesses, and security issues that automated tools may miss. Pair programming facilitates knowledge sharing and cultivates security awareness in real time, increasing the likelihood of early vulnerability detection. The combined defect detection rate
when employing automated tools plus manual review can be expressed as:
where
and
represent defects found by automated and manual efforts respectively, and
accounts for duplicates. This synergistic approach enhances overall code quality and security validation.
7. Preventing Injection Vulnerabilities in Agile Development
7.1. Input Validation and Sanitization Strategies
Input validation and sanitization are foundational defenses against injection attacks in agile development. Validation ensures that all input data conforms to expected formats, types, and lengths before being processed. Whitelist validation—accepting only known good input patterns—is the most secure approach compared to blacklist validation. Sanitization removes or encodes potentially harmful characters to prevent malicious payloads from being executed. Formally, input
is deemed safe if it satisfies a predicate function
, where:
Only inputs passing are processed further, effectively blocking injection vectors.
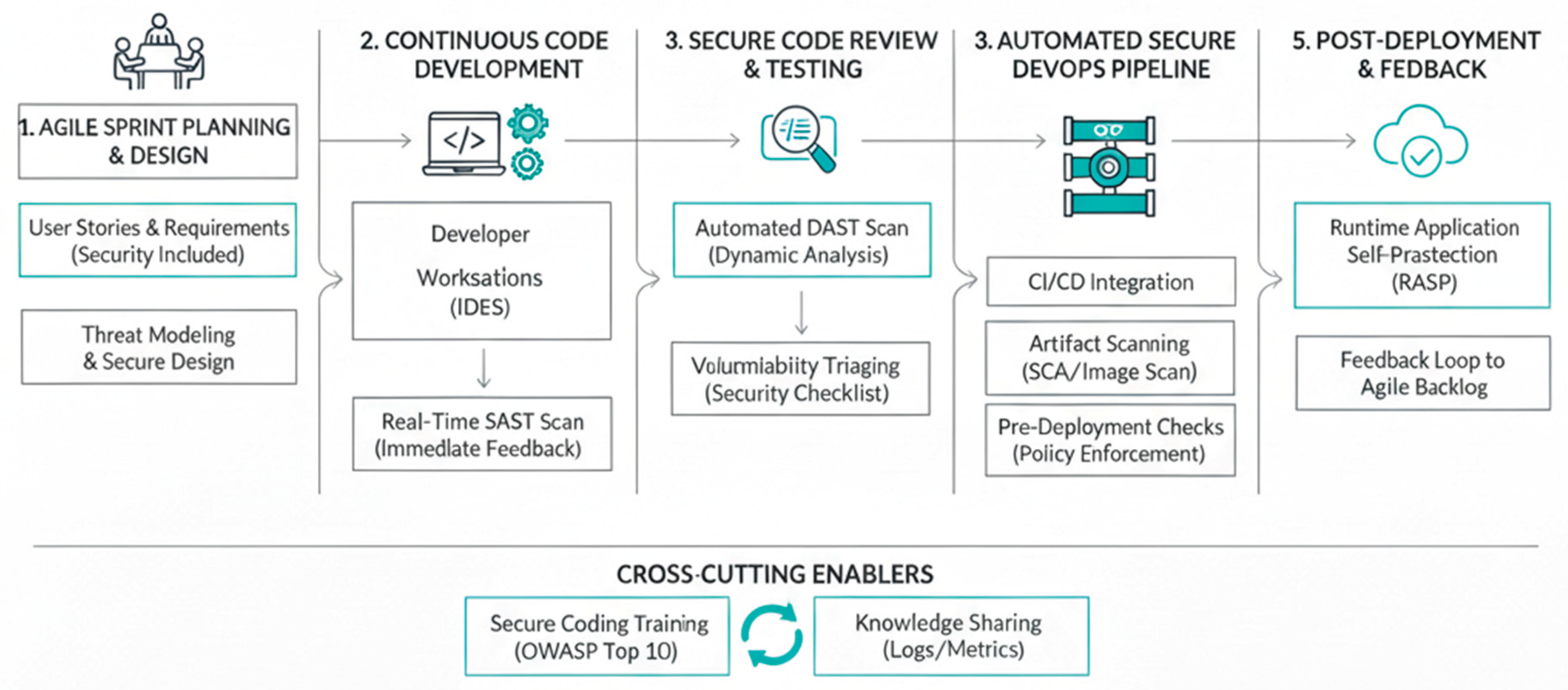
Figure 1.
Architecture Diagram for Secure Coding in Agile Development.
Figure 1.
Architecture Diagram for Secure Coding in Agile Development.
7.2. Secure API Design and Parameterized Queries
Secure API design minimizes injection risks by implementing strict input validation and avoiding direct concatenation of parameters into commands or queries. Parameterized queries or prepared statements separate code from data inputs, preventing attackers from injecting malicious code. For SQL queries, the use of parameterized queries ensures that user input is treated strictly as data, not executable commands, expressed as:
where parameters are bound at execution time, neutralizing injection attempts. APIs should also employ authentication, authorization, and rate limiting to further reduce attack surfaces.
7.3. Validation Frameworks and Defensive Coding Techniques
Validation frameworks provide reusable components and patterns for robust input validation, sanitization, and error handling that support secure coding in agile teams. Defensive coding involves anticipating and safely handling unexpected inputs or states to prevent security flaws. Techniques include boundary checks, input normalization, output encoding, and fail-safe defaults. For example, output encoding converts special characters into safe representations to avoid script execution in browsers, crucial for preventing cross-site scripting. These practices form layers of defense where the probability
of a successful injection decreases exponentially with the number of independent validation layers
:
where
is the probability that a single layer fails. Multiple validation layers vastly reduce the risk of injection vulnerability exploitation.
8. Preventing Logic Flaws Through Rigorous Design Controls
8.1. Business Logic Abuse Scenarios
Business logic flaws arise when attackers exploit weaknesses in an application’s intended workflows or rules, leading to outcomes such as unauthorized transactions, privilege escalations, or data corruption. These flaws often result from assumptions in the design or implementation that don’t hold under malicious use cases. Common abuse scenarios include bypassing payment controls, manipulating workflow sequences, or exploiting inadequate input validation in critical paths. Preventing these requires early threat modeling and clear documentation of business rules to identify potential misuse points and assumptions that need validation.
8.2. State Machine Validation and Access Control Logic
State machine validation enforces correct sequential states and transitions within applications, preventing unauthorized or invalid state changes that could lead to logic flaws. Formally, let
be the set of valid states and
the transition function mapping a current state and input
to the next state. Validation ensures that for each transition:
and unauthorized transitions are blocked. Access control logic enforces permissions by validating user roles and privileges against resources and actions using policies such as Role-Based Access Control (RBAC). By rigorously testing state transitions and access permissions, logic errors and abuse opportunities are minimized.
8.3. Behavioral Testing and Model-Based Security Validation
Behavioral testing focuses on verifying that the application behaves as expected under different inputs and scenarios, particularly edge cases and abuse conditions. Model-based security validation uses formal models of workflows and security policies to simulate and analyze potential violations. Automated tests can generate sequences of operations, monitoring for violations of expected behavior or security invariants
, such that:
where
encodes constraints like “no unauthorized fund transfer” or “no skipped approval steps.” Failure indicates a logic flaw requiring correction. These rigorous testing approaches help detect subtle flaws that could be overlooked by conventional static analysis or manual review.
9. Case Study: End-to-End Secure Agile Implementation
9.1. System Architecture Overview
The case study involves a large-scale enterprise implementing secure agile practices across distributed teams working on a complex access control system. The architecture blends modular microservices with tightly integrated DevSecOps pipelines, enabling both agility and security. Security is embedded at every layer from the API gateways enforcing authentication and authorization to secure coding standards within each microservice. Automated security tools orchestrate static and dynamic code scanning, while secure design principles guide component interactions and data flow. This layered architecture supports continuous delivery without sacrificing security vigilance.
9.2. Implementation Strategy and Results
The implementation began with a comprehensive training initiative focused on secure coding, threat modeling, and agile security integration. Teams adopted security-focused sprint planning, embedding security stories and acceptance criteria into backlogs. Automated static application security testing (SAST) and dynamic testing (DAST) tools were integrated into CI/CD pipelines for continuous vulnerability scanning. Manual secure code reviews and pair programming further reinforced quality. Over multiple release trains, the organization saw significant improvements: release frequency increased by up to 4x, bug backlogs shrank by over 3x, and security incidents related to injection flaws and logic errors dropped markedly. Stakeholder engagement and feedback loops improved transparency and allowed early course corrections.
9.3. Lessons Learned and Risk Analysis
Key lessons included the importance of leadership buy-in to drive cultural change and the critical role of continuous developer training to maintain secure coding awareness. Early attempts to customize frameworks without sufficient training led to setbacks, highlighting the need for fidelity to proven agile security practices initially. Risk analysis emphasized ongoing vigilance against emerging threats and the benefit of integrating automated security tools for scalability. The blend of automated scanning, manual review, and continuous training created a resilient, adaptable security posture that could evolve with the product and threat landscape.
10. Challenges and Limitations
10.1. Developer Resistance and Learning Curve
One of the primary challenges in integrating secure coding practices in agile development is resistance from developers. Many developers are accustomed to existing workflows and perceive security as an obstacle that slows down rapid delivery cycles. This resistance, often linked with a steep learning curve for new security tools and practices, can hinder adoption and reduce collaboration between development and security teams. Overcoming this requires effective training, cultural change driven by leadership, and demonstrating how security integration can ultimately enhance rather than impede development velocity.
10.2. Tooling Overheads and False Positives
Security tools such as static and dynamic analyzers introduce overhead in build and test cycles, potentially slowing down agile pipelines if not optimized. Another common limitation is the prevalence of false positives—security warnings that are not actual vulnerabilities. These consume developer time and can lead to alert fatigue, where important issues may be overlooked. Balancing comprehensive scanning with prioritization of actionable findings is crucial, as is integrating tools that align well with the team's technology stack and processes to minimize disruptions.
10.3. Balancing Speed and Security in Agile
Agile development emphasizes rapid iteration and continuous delivery, which can conflict with comprehensive security validation if not well managed. The tension between shipping features quickly and ensuring thorough security requires careful sprint planning, risk-based prioritization, and automation of security testing within CI/CD pipelines. Maintaining this balance is a dynamic process too much focus on speed can increase vulnerabilities, while overly cautious approaches can slow down delivery and reduce agility.
11. Conclusion and Future Enhancements
Integrating secure coding practices within agile development frameworks is essential to effectively mitigate injection vulnerabilities and logic flaws while maintaining agility and rapid delivery. The continuous incorporation of security from sprint planning through real-time code scanning and developer training fosters a proactive security culture. Key enablers include embedding security requirements into product backlogs, leveraging automated static and dynamic analysis tools within CI/CD pipelines, and employing rigorous training programs including gamified secure coding exercises. These efforts collectively improve code quality, reduce vulnerabilities, and accelerate secure software delivery.
Future enhancements could focus on advancing AI-driven real-time vulnerability detection integrated deeply into developer environments, enabling personalized security feedback and adaptive learning pathways for developers. Further development of automated threat modeling tools that evolve dynamically with code changes will help anticipate logic flaws more efficiently. Additionally, enhancing collaboration platforms to seamlessly include security experts in agile ceremonies will strengthen early identification and mitigation of risks. Finally, balancing tooling efficiency to minimize false positives while maximizing detection accuracy will be critical to sustain developer engagement and productivity.
References
- Arora, A. (2025). THE SIGNIFICANCE AND ROLE OF AI IN IMPROVING CLOUD SECURITY POSTURE FOR MODERN ENTERPRISES. Available at SSRN 5268192.
- Singh, B. (2025). Building Secure Software Faster with DevSecOps Principles, Practices, and Implementation Strategies. Practices, and Implementation Strategies (May 23, 2025).
- Akat, G. B., & Magare, B. K. (2023). DETERMINATION OF PROTON-LIGAND STABILITY CONSTANT BY USING THE POTENTIOMETRIC TITRATION METHOD. MATERIAL SCIENCE, 22(07).
- Siddiqui, A., Chand, K., & Shahi, N. C. (2021). Effect of process parameters on extraction of pectin from sweet lime peels. Journal of The Institution of Engineers (India): Series A, 102(2), 469-478. [CrossRef]
- Kumar, J. D. S., Subramanyam, M. V., & Kumar, A. S. (2024). Hybrid Sand Cat Swarm Optimization Algorithm-based reliable coverage optimization strategy for heterogeneous wireless sensor networks. International Journal of Information Technology, 1-19. [CrossRef]
- Shinkar, A. R., Joshi, D., Praveen, R. V. S., Rajesh, Y., & Singh, D. (2024, December). Intelligent solar energy harvesting and management in IoT nodes using deep self-organizing maps. In 2024 International Conference on Emerging Research in Computational Science (ICERCS) (pp. 1-6). IEEE.
- Vikram, A. V., & Arivalagan, S. (2017). Engineering properties on the sugar cane bagasse with sisal fibre reinforced concrete. International Journal of Applied Engineering Research, 12(24), 15142-15146.
- Reddy, D. N., Venkateswararao, P., Vani, M. S., Pranathi, V., & Patil, A. (2025). HybridPPI: A Hybrid Machine Learning Framework for Protein-Protein Interaction Prediction. Indonesian Journal of Electrical Engineering and Informatics (IJEEI), 13(2). [CrossRef]
- Atheeq, C., Sultana, R., Sabahath, S. A., & Mohammed, M. A. K. (2024). Advancing IoT Cybersecurity: adaptive threat identification with deep learning in Cyber-physical systems. Engineering, Technology & Applied Science Research, 14(2), 13559-13566. [CrossRef]
- Arora, A. (2025). Zero Trust Architecture: Revolutionizing Cybersecurity for Modern Digital Environments. Available at SSRN 5268151.
- Mohammed Nabi Anwarbasha, G. T., Chakrabarti, A., Bahrami, A., Venkatesan, V., Vikram, A. S. V., Subramanian, J., & Mahesh, V. (2023). Efficient finite element approach to four-variable power-law functionally graded plates. Buildings, 13(10), 2577. [CrossRef]
- Kumar, N., Kurkute, S. L., Kalpana, V., Karuppannan, A., Praveen, R. V. S., & Mishra, S. (2024, August). Modelling and Evaluation of Li-ion Battery Performance Based on the Electric Vehicle Tiled Tests using Kalman Filter-GBDT Approach. In 2024 International Conference on Intelligent Algorithms for Computational Intelligence Systems (IACIS) (pp. 1-6). IEEE.
- Singh, H. (2025). Securing High-Stakes Digital Transactions: A Comprehensive Study on Cybersecurity and Data Privacy in Financial Institutions. Available at SSRN 5267850.
- Singh, B. (2025). Integrating Threat Modeling In Devsecops For Enhanced Application Security. Available at SSRN 5267976.
- Akat, G. B. (2023). Structural Analysis of Ni1-xZnxFe2O4 Ferrite System. MATERIAL SCIENCE, 22(05).
- Vijay Vikram, A. S., & Arivalagan, S. (2017). A short review on the sugarcane bagasse with sintered earth blocks of fiber reinforced concrete. Int J Civil Eng Technol, 8(6), 323-331.
- Yamuna, V., Praveen, R. V. S., Sathya, R., Dhivva, M., Lidiya, R., & Sowmiya, P. (2024, October). Integrating AI for Improved Brain Tumor Detection and Classification. In 2024 4th International Conference on Sustainable Expert Systems (ICSES) (pp. 1603-1609). IEEE.
- Sultana, R., Ahmed, N., & Sattar, S. A. (2018). HADOOP based image compression and amassed approach for lossless images. Biomedical Research, 29(8), 1532-1542. [CrossRef]
- Kumar, T. V. (2024). Enhanced Kubernetes Monitoring Through Distributed Event Processing.
- Boopathy, D., & Balaji, P. (2023). Effect of different plyometric training volume on selected motor fitness components and performance enhancement of soccer players. Ovidius University Annals, Series Physical Education and Sport/Science, Movement and Health, 23(2), 146-154.
- Rao, A. S., Reddy, Y. J., Navya, G., Gurrapu, N., Jeevan, J., Sridhar, M., ... & Anand, D. High-performance sentiment classification of product reviews using GPU (parallel)-optimized ensembled methods. [CrossRef]
- Arora, A. (2025). Securing Multi-Cloud Architectures using Advanced Cloud Security Management Tools. Available at SSRN 5268184.
- Singh, B. (2025). Mastering Oracle Database Security: Best Practices for Enterprise Protection. Available at SSRN 5267920.
- Lopez, S., Sarada, V., Praveen, R. V. S., Pandey, A., Khuntia, M., & Haralayya, D. B. (2024). Artificial intelligence challenges and role for sustainable education in india: Problems and prospects. Sandeep Lopez, Vani Sarada, RVS Praveen, Anita Pandey, Monalisa Khuntia, Bhadrappa Haralayya (2024) Artificial Intelligence Challenges and Role for Sustainable Education in India: Problems and Prospects. Library Progress International, 44(3), 18261-18271.
- Akat, G. B. (2022). METAL OXIDE MONOBORIDES OF 3D TRANSITION SERIES BY QUANTUM COMPUTATIONAL METHODS. MATERIAL SCIENCE, 21(06).
- Kumar, T. V. (2019). Cloud-Based Core Banking Systems Using Microservices Architecture.
- Kumar, J. D. S., Subramanyam, M. V., & Kumar, A. P. S. (2023). Hybrid Chameleon Search and Remora Optimization Algorithm-based Dynamic Heterogeneous load balancing clustering protocol for extending the lifetime of wireless sensor networks. International Journal of Communication Systems, 36(17), e5609. [CrossRef]
- Arora, A. (2025). Analyzing Best Practices and Strategies for Encrypting Data at Rest (Stored) and Data in Transit (Transmitted) in Cloud Environments. Available at SSRN 5268190.
- Sharma, S., Vij, S., Praveen, R. V. S., Srinivasan, S., Yadav, D. K., & VS, R. K. (2024, October). Stress Prediction in Higher Education Students Using Psychometric Assessments and AOA-CNN-XGBoost Models. In 2024 4th International Conference on Sustainable Expert Systems (ICSES) (pp. 1631-1636). IEEE.
- Arora, A. (2025). Transforming Cybersecurity Threat Detection and Prevention Systems using Artificial Intelligence. Available at SSRN 5268166.
- Nizamuddin, M. K., Raziuddin, S., Farheen, M., Atheeq, C., & Sultana, R. (2024). An MLP-CNN Model for Real-time Health Monitoring and Intervention. Engineering, Technology & Applied Science Research, 14(4), 15553-15558. [CrossRef]
- Arora, A. (2025). Evaluating Ethical Challenges in Generative AI Development and Responsible Usage Guidelines. Available at SSRN 5268196.
- Kamatchi, S., Preethi, S., Kumar, K. S., Reddy, D. N., & Karthick, S. (2025, May). Multi-Objective Genetic Algorithm Optimised Convolutional Neural Networks for Improved Pancreatic Cancer Detection. In 2025 3rd International Conference on Data Science and Information System (ICDSIS) (pp. 1-7). IEEE.
- Sivakumar, S., Prakash, R., Srividhya, S., & Vikram, A. V. (2023). A novel analytical evaluation of the laboratory-measured mechanical properties of lightweight concrete. Structural engineering and mechanics: An international journal, 87(3), 221-229. [CrossRef]
- Praveen, R. V. S., Hemavathi, U., Sathya, R., Siddiq, A. A., Sanjay, M. G., & Gowdish, S. (2024, October). AI Powered Plant Identification and Plant Disease Classification System. In 2024 4th International Conference on Sustainable Expert Systems (ICSES) (pp. 1610-1616). IEEE.
- Akat, G. B. (2022). OPTICAL AND ELECTRICAL STUDY OF SODIUM ZINC PHOSPHATE GLASS. MATERIAL SCIENCE, 21(05).
- Singh, B. (2025). Oracle Database Vault: Advanced Features for Regulatory Compliance and Control. Available at SSRN 5267938.
- Kumar, T. V. (2018). Event-Driven App Design for High-Concurrency Microservices.
- Arora, A. (2025). Integrating Dev-Sec-Ops Practices to Strengthen Cloud Security in Agile Development Environments. Available at SSRN 5268194.
- Singh, B. (2025). Integrating Security Seamlessly into DevOps Development Pipelines through DevSecOpsA Holistic Approach to Secure Software Delivery. Available at SSRN 5267955.
- Kumar, T. V. (2016). Layered App Security Architecture for Protecting Sensitive Data.
- Charanya, J., Sureshkumar, T., Kavitha, V., Nivetha, I., Pradeep, S. D., & Ajay, C. (2024, June). Customer Churn Prediction Analysis for Retention Using Ensemble Learning. In 2024 15th International Conference on Computing Communication and Networking Technologies (ICCCNT) (pp. 1-10). IEEE.
- Nimma, D., Rao, P. L., Ramesh, J. V. N., Dahan, F., Reddy, D. N., Selvakumar, V., ... & Jangir, P. (2025). Reinforcement Learning-Based Integrated Risk Aware Dynamic Treatment Strategy for Consumer-Centric Next-Gen Healthcare. IEEE Transactions on Consumer Electronics. [CrossRef]
- Arora, A. (2025). The Future of Cybersecurity: Trends and Innovations Shaping Tomorrow's Threat Landscape. Available at SSRN 5268161.
- Akat, G. B. (2022). STRUCTURAL AND MAGNETIC STUDY OF CHROMIUM FERRITE NANOPARTICLES. MATERIAL SCIENCE, 21(03).
- Singh, H. (2025). The Role of Multi-Factor Authentication and Encryption in Securing Data Access of Cloud Resources in a Multitenant Environment. Available at SSRN 5267886.
- Raja, M. W., & Nirmala, D. K. (2016). Agile development methods for online training courses web application development. International Journal of Applied Engineering Research ISSN, 0973-4562.
- Anuprathibha, T., Praveen, R. V. S., Sukumar, P., Suganthi, G., & Ravichandran, T. (2024, October). Enhancing Fake Review Detection: A Hierarchical Graph Attention Network Approach Using Text and Ratings. In 2024 Global Conference on Communications and Information Technologies (GCCIT) (pp. 1-5). IEEE.
- Jeyaprabha, B., & Sundar, C. (2021). The mediating effect of e-satisfaction on e-service quality and e-loyalty link in securities brokerage industry. Revista Geintec-gestao Inovacao E Tecnologias, 11(2), 931-940.
- Arora, A. (2025). Comprehensive Cloud Security Strategies for Protecting Sensitive Data in Hybrid Cloud Environments.
- Sultana, R., Ahmed, N., & Basha, S. M. (2011). Advanced Fractal Image Coding Based on the Quadtree. Computer Engineering and Intelligent Systems, 2 3, 129, 136.
- Singh, H. (2025). Cybersecurity for Smart Cities Protecting Infrastructure in the Era of Digitalization. Available at SSRN 5267856.
- Kemmannu, P. K., Praveen, R. V. S., & Banupriya, V. (2024, December). Enhancing Sustainable Agriculture Through Smart Architecture: An Adaptive Neuro-Fuzzy Inference System with XGBoost Model. In 2024 International Conference on Sustainable Communication Networks and Application (ICSCNA) (pp. 724-730). IEEE.
- Singh, B. (2017). Enhancing Real-Time Database Security Monitoring Capabilities Using Artificial Intelligence. International Journal of Current Engineering and Scientific Research (IJCESR).
- Singh, H. (2025). STRATEGIES TO BALANCE SCALABILITY AND SECURITY IN CLOUD-NATIVE APPLICATION DEVELOPMENT. Available at SSRN 5267890.
- RAJA, M. W., PUSHPAVALLI, D. M., BALAMURUGAN, D. M., & SARANYA, K. (2025). ENHANCED MED-CHAIN SECURITY FOR PROTECTING DIABETIC HEALTHCARE DATA IN DECENTRALIZED HEALTHCARE ENVIRONMENT BASED ON ADVANCED CRYPTO AUTHENTICATION POLICY. TPM–Testing, Psychometrics, Methodology in Applied Psychology, 32(S4 (2025): Posted 17 July), 241-255.
- Akat, G. B., & Magare, B. K. (2022). Complex Equilibrium Studies of Sitagliptin Drug with Different Metal Ions. Asian Journal of Organic & Medicinal Chemistry.
- Kumar, T. V. (2020). Generative AI Applications in Customizing User Experiences in Banking Apps.
- Jeyaprabha, B., Catherine, S., & Vijayakumar, M. (2024). Unveiling the Economic Tapestry: Statistical Insights Into India's Thriving Travel and Tourism Sector. In Managing Tourism and Hospitality Sectors for Sustainable Global Transformation (pp. 249-259). IGI Global Scientific Publishing.
- Arora, A. (2025). Understanding the Security Implications of Generative AI in Sensitive Data Applications.
- JEYAPRABHA, B., & SUNDAR, C. (2022). The Psychological Dimensions Of Stock Trader Satisfaction With The E-Broking Service Provider. Journal of Positive School Psychology, 6(5).
- Singh, H. (2025). How Generative AI is Revolutionizing Scientific Research by Automating Hypothesis Generation. Available at SSRN 5267912.
- Singh, B. (2025). Advanced Oracle Security Techniques for Safeguarding Data Against Evolving Cyber Threats. Available at SSRN 5267951.
- Praveen, R. V. S. (2024). Data Engineering for Modern Applications. Addition Publishing House.
- Akat, G. B., & Magare, B. K. (2022). Mixed Ligand Complex Formation of Copper (II) with Some Amino Acids and Metoprolol. Asian Journal of Organic & Medicinal Chemistry.
- Singh, B. (2025). DevSecOps: A Comprehensive Framework for Securing Cloud-Native Applications. Available at SSRN 5267982.
- Singh, H. (2025). The Future Of Generative Ai: Opportunities, Challenges, And Industry Disruption Potential. Challenges, And Industry Disruption Potential (May 23, 2025).
- Chand, K. (2013). Effect of pre-cooling treatments on shelf life of tomato in ambient condition.
- Rahman, Z., Mohan, A., & Priya, S. (2021). Electrokinetic remediation: An innovation for heavy metal contamination in the soil environment. Materials Today: Proceedings, 37, 2730-2734. [CrossRef]
- Singh, B. (2025). Enhancing Oracle Database Security with Transparent Data Encryption (TDE) Solutions. Available at SSRN 5267924.
- Singh, B. (2025). Challenges and Solutions for Adopting DevSecOps in Large Organizations. Available at SSRN 5267971.
- Singh, H. (2025). Key Cloud Security Challenges for Organizations Embracing Digital Transformation Initiatives. Available at SSRN 5267894.
- Kumar, T. V. (2022). AI-Powered Fraud Detection in Real-Time Financial Transactions.
- Raja, M. W. (2024). Artificial intelligence-based healthcare data analysis using multi-perceptron neural network (MPNN) based on optimal feature selection. SN Computer Science, 5(8), 1034. [CrossRef]
- Akat, G. B. (2021). EFFECT OF ATOMIC NUMBER AND MASS ATTENUATION COEFFICIENT IN Ni-Mn FERRITE SYSTEM. MATERIAL SCIENCE, 20(06).
- Thakur, R. R., Shahi, N. C., Mangaraj, S., Lohani, U. C., & Chand, K. (2021). Development of an organic coating powder and optimization of process parameters for shelf life enhancement of button mushrooms (Agaricus bisporus). Journal of Food Processing and Preservation, 45(3), e15306. [CrossRef]
- Kumar, T. V. (2015). ANALYSIS OF SQL AND NOSQL DATABASE MANAGEMENT SYSTEMS INTENDED FOR UNSTRUCTURED DATA.
- Kumar, T. V. (2023). REAL-TIME DATA STREAM PROCESSING WITH KAFKA-DRIVEN AI MODELS.
- Nasir, G., Chand, K., Azaz Ahmad Azad, Z. R., & Nazir, S. (2020). Optimization of Finger Millet and Carrot Pomace based fiber enriched biscuits using response surface methodology. Journal of Food Science and Technology, 57(12), 4613-4626. [CrossRef]
- Singh, H. (2025). Enhancing Cloud Security Posture with AI-Driven Threat Detection and Response Mechanisms. Available at SSRN 5267878.
- Praveen, R. V. S., Hundekari, S., Parida, P., Mittal, T., Sehgal, A., & Bhavana, M. (2025, February). Autonomous Vehicle Navigation Systems: Machine Learning for Real-Time Traffic Prediction. In 2025 International Conference on Computational, Communication and Information Technology (ICCCIT) (pp. 809-813). IEEE.
- Kumar, T. V. (2021). NATURAL LANGUAGE UNDERSTANDING MODELS FOR PERSONALIZED FINANCIAL SERVICES.
- Chand, K., Shahi, N. C., Lohani, U. C., & Garg, S. K. (2011). Effect of storage conditions on keeping qualities of jaggery. Sugar Tech, 13(1), 81-85. [CrossRef]
- Kumar, T. V. (2019). BLOCKCHAIN-INTEGRATED PAYMENT GATEWAYS FOR SECURE DIGITAL BANKING.
- Arunmohan, A. M., & Lakshmi, M. (2018). Analysis of modern construction projects using montecarlo simulation technique. International Journal of Engineering & Technology, 7(2.19), 41-44. [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).