Submitted:
15 October 2025
Posted:
15 October 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Research Status
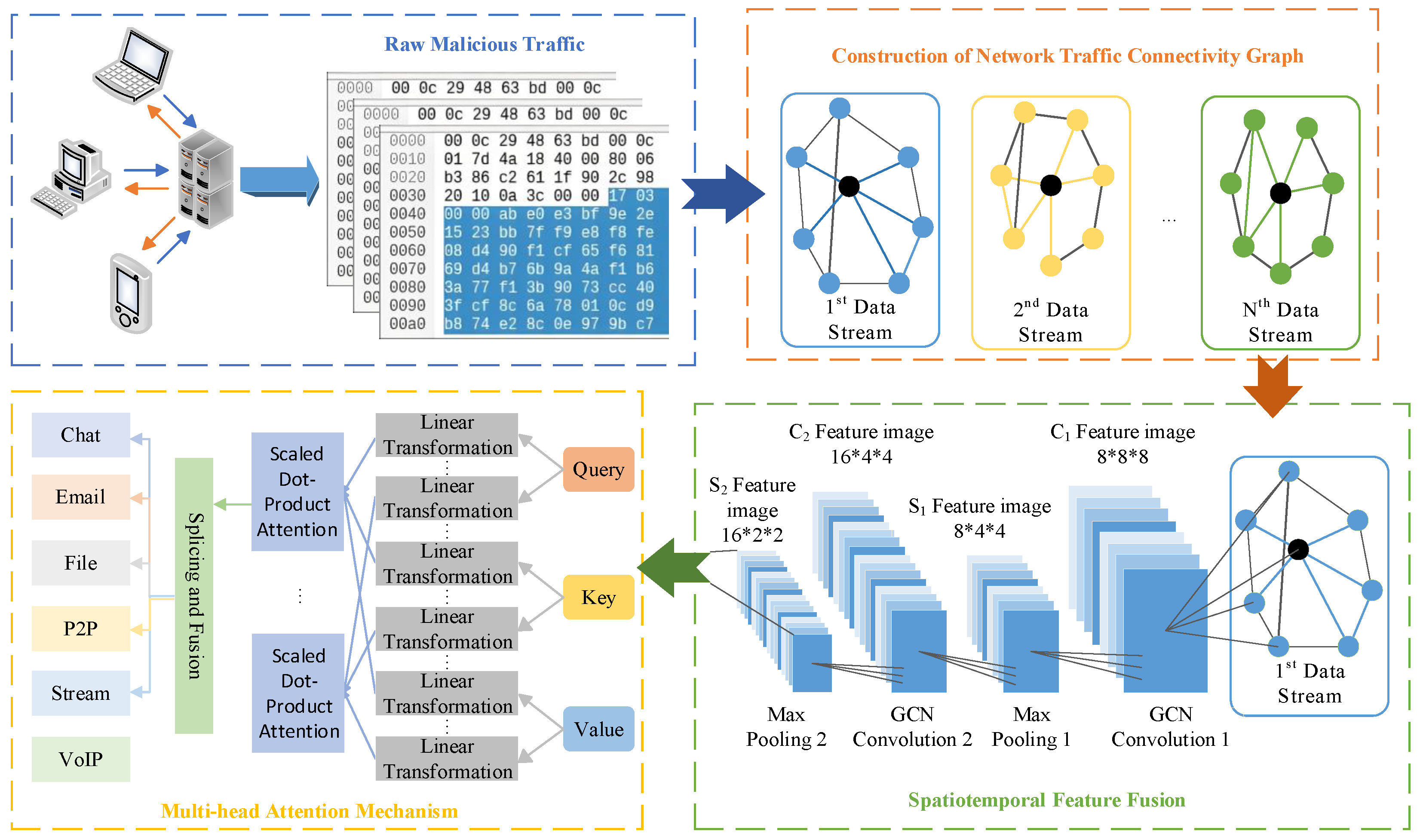
3. GAT-CNN Method
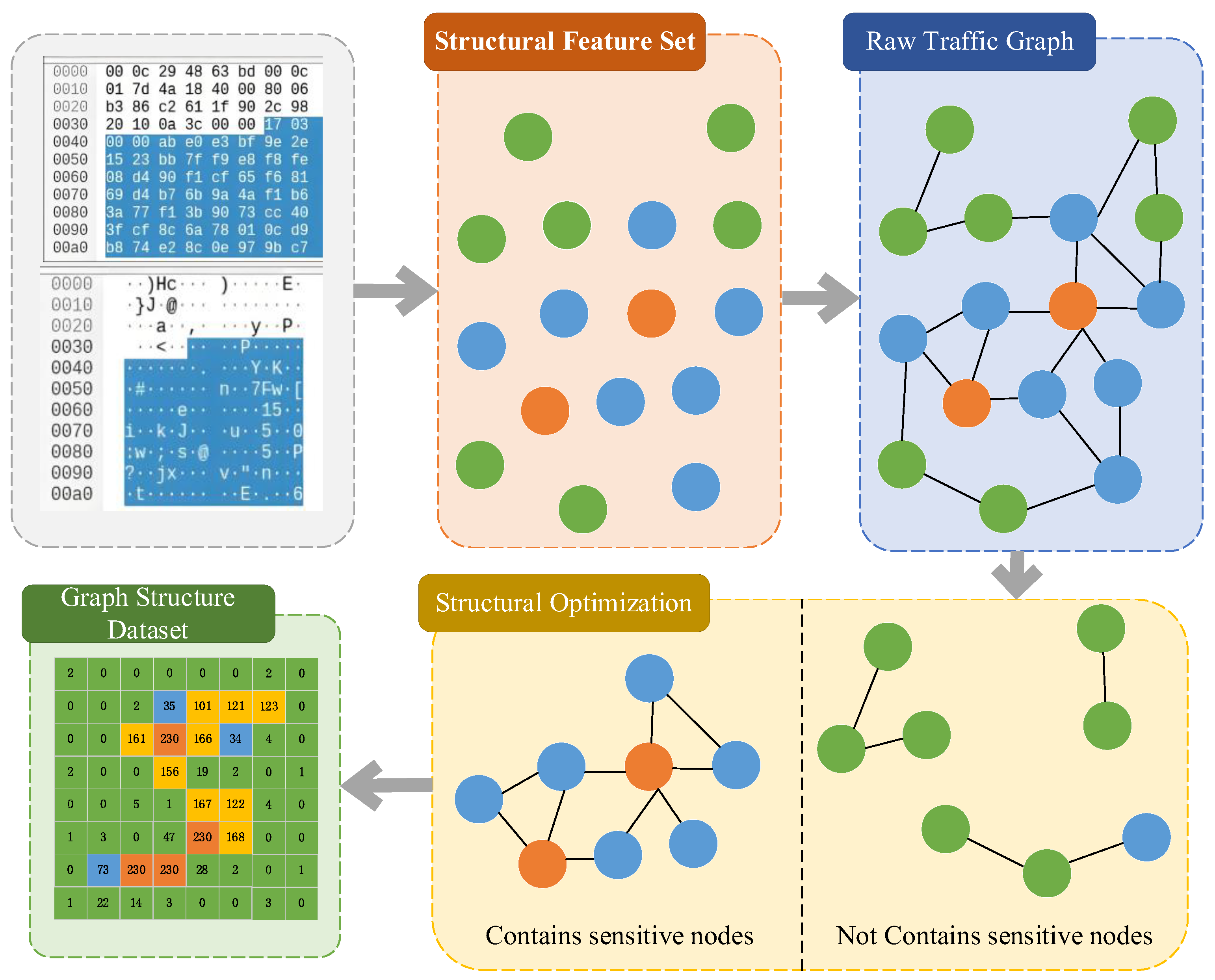
3.1. Connectivity Relationship Graph Construction
| Algorithm 1: Graph Structure Simplification Algorithm |
| Input:Graph G (Nodes represent network traffic nodes, edges represent associations between nodes) |
| Output: The processed and simplified graph G’ |
| 1. for node in G.nodes(): // Iterate through graph nodes 2. if is_sensitive(node): //Check if the node contains sensitive information 3. add_node_to_graph(G_prime, node) //If yes 4. else: neighbors = get_neighbors(G, node) //If no 5. for neighbor in neighbors: //Check neighbor nodes 6. if not all_non_sensitive: //At least one 7. add_node_to_graph(G_prime, node) 8. remove_edge(G, node, neighbor) //Remove the edge between nodes 9. return G’ //Return the simplified graph |
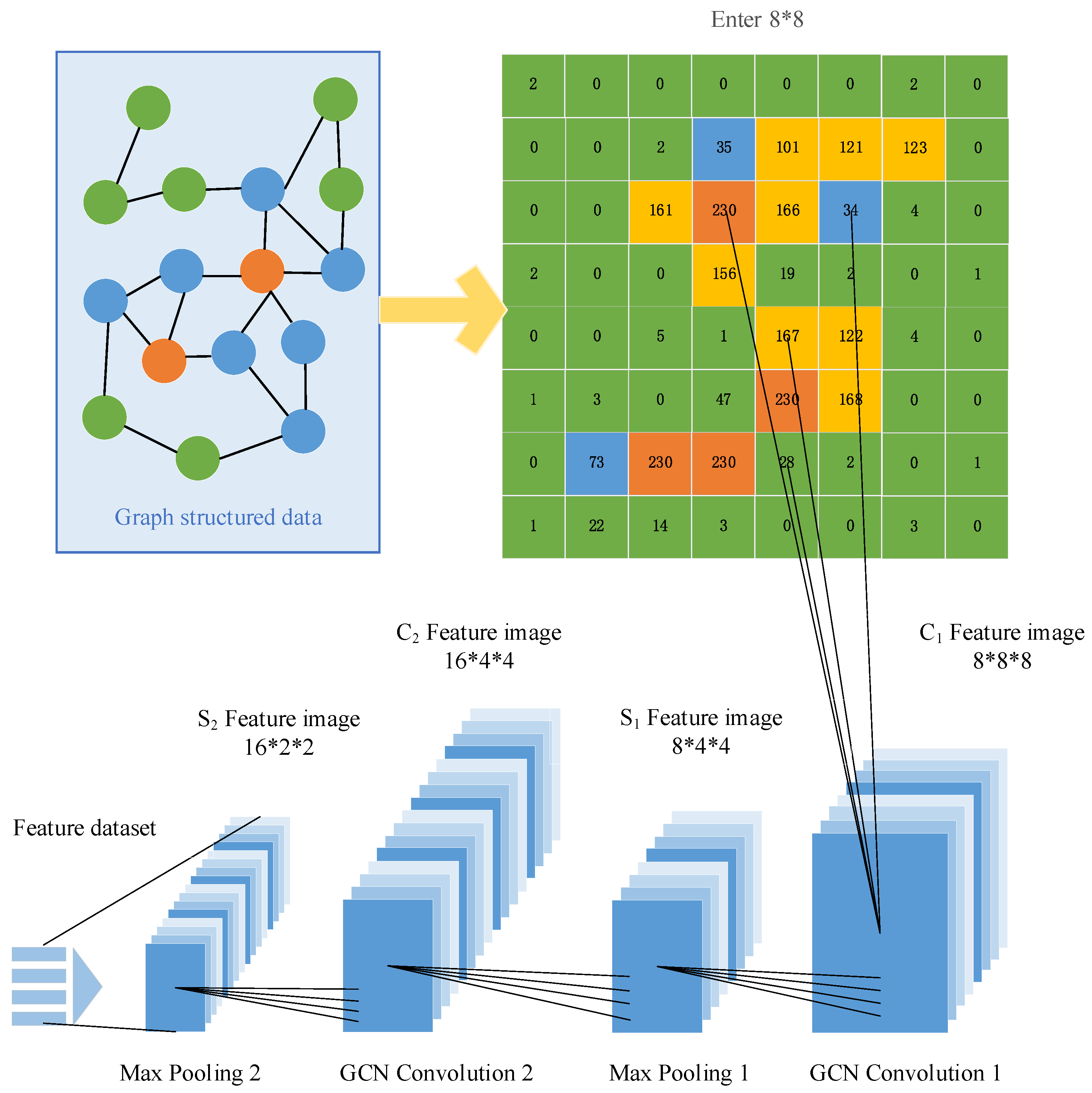
3.2. Spatiotemporal Feature Fusion
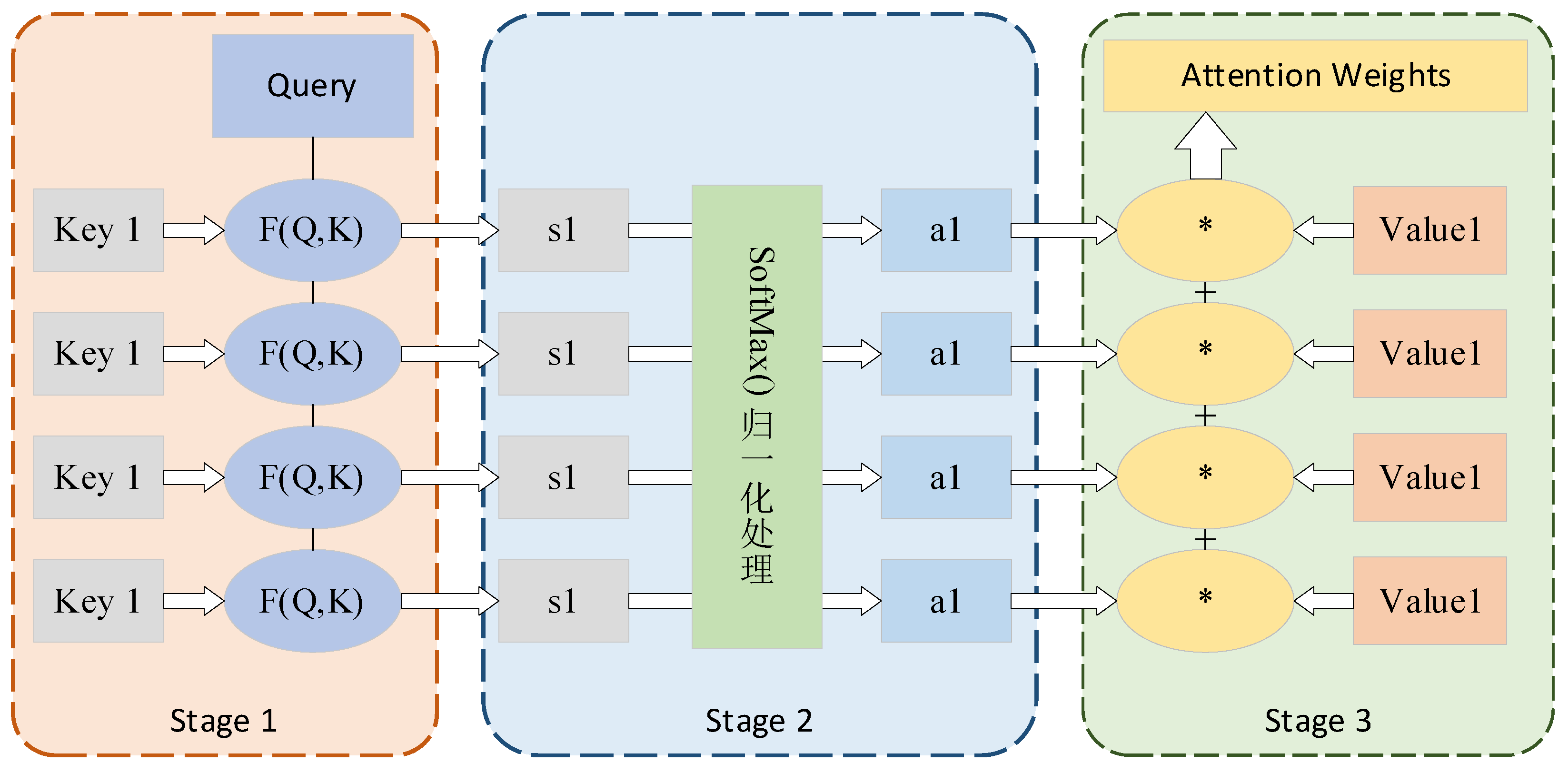
3.3. Multi-Head Attention Mechanism Weight Allocation
4. Experimental Analysis
4.1. Experimental Environment and Settings
4.2. Experimental Data Selection
4.3. Experimental Evaluation Metrics
4.4. Experiment and Analysis
4.4.1. Experimental Results
| Traffic Category | Accuracy | Precision | Recall | F₁-score |
|---|---|---|---|---|
| CHAT | 0.984 | 0.950 | 0.997 | 0.973 |
| 0.980 | 0.950 | 0.996 | 0.972 | |
| FILE | 0.996 | 0.915 | 0.931 | 0.923 |
| P2P | 1.000 | 1.000 | 1.000 | 1.000 |
| STREAM | 0.986 | 0.921 | 0.948 | 0.935 |
| VoIP | 0.992 | 0.938 | 0.979 | 0.958 |
| Overall | 0.9879 | 0.9478 | 0.9924 | 0.9696 |
| Traffic Type | Category (Detection Result / Total Dataset) | Accuracy | Recall | |||
|---|---|---|---|---|---|---|
| Benign Traffic | 67776/68678 | 98.69% | \ | |||
| Correctly Identified Malicious Flows | Misclassified Benign Flows | Unidentified Malicious Flows | ||||
| Malicious Traffic | CHAT | 6504/6523 | 341/15425 | 19/6523 | 98.36% | 99.71% |
| 7285/7312 | 386/13122 | 27/7312 | 97.98% | 99.63% | ||
| FILE | 257/276 | 24/10071 | 19/276 | 99.58% | 93.12% | |
| P2P | 178/178 | 0/9849 | 0/178 | 100% | 100% | |
| STREAM | 422/445 | 36/3781 | 23/445 | 98.58% | 94.83% | |
| VoIP | 1744/1781 | 115/16493 | 37/1781 | 99.17% | 97.92% | |
| Overall | 98.79% | 99.24% | ||||
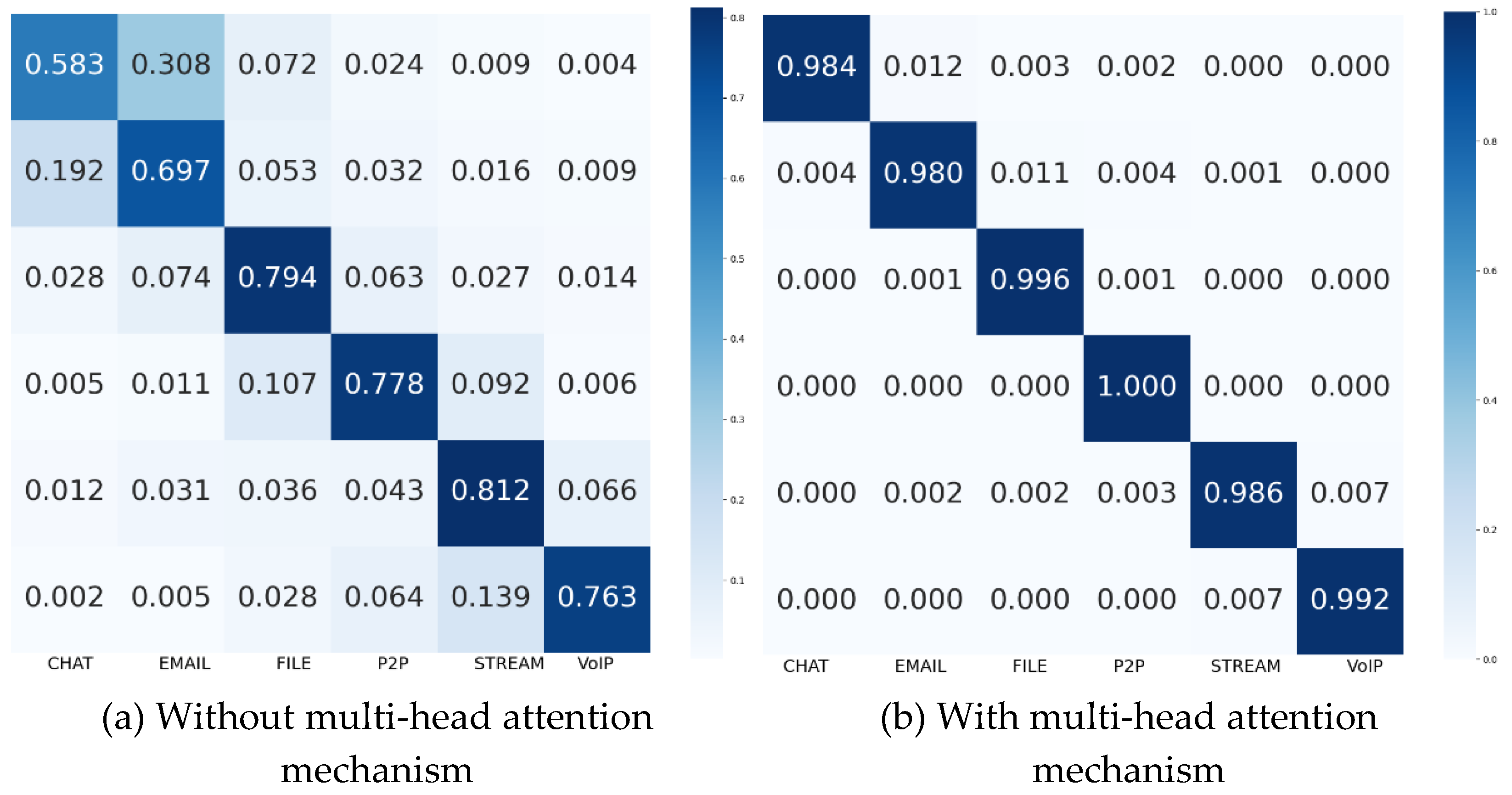
4.4.2. Ablation Experiment
4.4.3. Performance Comparison
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| TLS/SSL | Transport Layer Security/ Secure Sockets Layer |
| DDos | Distributed denial of service attack |
| SVM | Support Vector Machines |
| LSTM | Long Short-Term Memory |
| CNN | Convolutional Neural Networks |
| GNN | Graph Neural Networks |
| MLP | Multi-Layer Perceptrons |
References
- Dang Y.J., Li Q.N. Research on the Development of Foreign Artificial Intelligence Hotspot Security Technology[J]. Information Security And Communications Privacy, 2024(12):1-8. [CrossRef]
- Bian Y, Zheng F, Wang Y, et al. AsyncGBP+: Bridging SSL/TLS and Heterogeneous Computing Power With GPU-Based Providers[J]. IEEE Transactions on Computers, 2025(2):74. [CrossRef]
- Aguru A, Erukala S. OTI-IoT: A Blockchain-based Operational Threat Intelligence Framework for Multi-vector DDoS Attacks[J]. ACM Transactions on Internet Technology (TOIT), 2024, 24(3):31. [CrossRef]
- Mosakheil J.H., Yang K. PKChain: Compromise-Tolerant and Verifiable Public Key Management System[J]. IEEE Internet of Things Journal, 2025, 12(3):3130-3144. [CrossRef]
- Mei H.T., Cheng G, Zhu Y.L., Zhou Y.Y. Survey on Tor Passive Traffic Analysis[J].Ruan Jian Xue Bao/Journal of Software, 2025,36(01):253-288. [CrossRef]
- Hazman C, Guezzaz A, Benkirane S, et al. Enhanced IDS with Deep Learning for IoT-Based Smart Cities Security[J]. Tsinghua Science and Technology, 2024, 29(4):929-947. [CrossRef]
- Yogesh, Goyal M L. Deep learning based network intrusion detection system: a systematic literature review and future scopes[J]. International Journal of Information Security, 2024:1-31. [CrossRef]
- Surjeet D, Kumar U L, Neetu F, et al. Next-generation cyber attack prediction for IoT systems: leveraging multi-class SVM and optimized CHAID decision tree [J]. Journal of Cloud Computing, 2023,12(1):137. [CrossRef]
- Gou J.J., Li J.H., Chen C., et al. Network Intrusion Detection Method Based on Random Forest[J].Computer Engineering and Applications, 2020, 56(2): 82-88. [CrossRef]
- Bakır H, Ceviz Ö. Empirical enhancement of intrusion detection systems: a comprehensive approach with genetic algorithm-based hyperparameter tuning and hybrid feature selection[J]. Arabian Journal for Science and Engineering, 2024, 49(9): 13025-13043. [CrossRef]
- Wang Y. Advanced Network Traffic Prediction Using Deep Learning Techniques: A Comparative Study of SVR, LSTM, GRU, and Bidirectional LSTM Models[C]//ITM Web of Conferences. EDP Sciences, 2025, 70: 03021. [CrossRef]
- PL S, Emmanuel W R S, Rani P A J. Network traffic classification based--masked language regression model using CNN[J]. Concurrency and Computation: Practice and Experience,2024,36(22):e8223-e8223. [CrossRef]
- Altaf T, Wang X, Ni W, et al. GNN-Based Network Traffic Analysis for the Detection of Sequential Attacks in IoT[J]. Electronics, 2024,13(12): 2274-2274. [CrossRef]
- Zhao D., Yin Z.C., Cao Z.H., Lu Z.G. Malicious TLS Traffic Detection Based on Graph Representation[J].Journal of Information Security Research, 2024, 10(03):209-215.
- Deng H., Yang A.M., Liu Y.D. P2P traffic classification method based on SVM[J].Computer Engineering and Applications,2008,(14):122-126. [CrossRef]
- Wang L., Feng H.M., Liu B., et al. SSL VPN Encrypted Traffic Identification Based on Hybrid Method[J]. Computer Applications and Software, 2019, 36(02):315-322. [CrossRef]
- Shi L., Shi S.S., Wen W.P. Research on APT Attack Detection Based on LSTM in Linux System[J]. Journal of Information Security Research, 2022,8(08):736-750.
- Cheng H., Xie J.X., Chen L.H. CNN-based Encrypted C&C Communication Traffic Identification Method[J]. Computer Engineering, 2019,45(08):31-34+41. [CrossRef]
- Xu H.P., Ma Z.W., Yi H., et al. Network Traffic Anomaly Detection Technology Based on Convolutional Recurrent Neural Network[J]. Netinfo Security, 2021, 21(7): 54-62. [CrossRef]
- Luo G.Y., Wang X.S, DAI J.Y. Random Feature Graph Neural Network for Intrusion Detection in Internet of Things[J]. Computer Engineering and Applications, 2024,60(21):264-273. [CrossRef]
- Zheng J, Zeng Z, Feng T. GCN--ETA: High--Efficiency Encrypted Malicious Traffic Detection[J]. Security and Communication Networks, 2022(1): 4274139. [CrossRef]
- Chen J, Xie H, Cai S, et al.GCN-MHSA: A novel malicious traffic detection method based on graph convolutional neural network and multi-head self-attention mechanism[J]. Computers & Security, 2024:147. [CrossRef]
| Traffic Classification | Content |
|---|---|
| Web Browsing | Chrome and Firefox |
| SMPTS, POP3S and IMAPS | |
| Chat | ICQ, AIM, Skype, Facebook and Hangouts |
| Streaming | Vimeo and Youtube |
| File Transfer | Skype, FTPS and SFTP using Filezilla and an external servive |
| VoIP | Facebook, Skype and Hangouts voice calls (1h duration) |
| P2P | uTorrent and Transmission (Bittorrent) |
| Model | Accuracy | Precision | Recall | F1-score |
|---|---|---|---|---|
| Support Vector Machine (SVM) | 0.923 | 0.924 | 0.867 | 0.895 |
| Random Forest | 0.903 | 0.909 | 0.892 | 0.907 |
| Long Short-Term Memory (LSTM) | 0.863 | 0.884 | 0.853 | 0.868 |
| Convolutional Neural Network (CNN) | 0.910 | 0.910 | 0.905 | 0.910 |
| Convolutional Recurrent Neural Network (CRNN) | 0.970 | 0.958 | 0.977 | 0.967 |
| Graph Neural Network (GNN) | 0.934 | 0.970 | 0.926 | 0.948 |
| GCN-ETA | 0.974 | 0.975 | 0.964 | 0.969 |
| GCN-MHSA | 0.963 | 0.968 | 0.971 | 0.970 |
| GAT-CNN | 0.988 | 0.987 | 0.989 | 0.988 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





