Submitted:
16 September 2025
Posted:
17 September 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Related Works
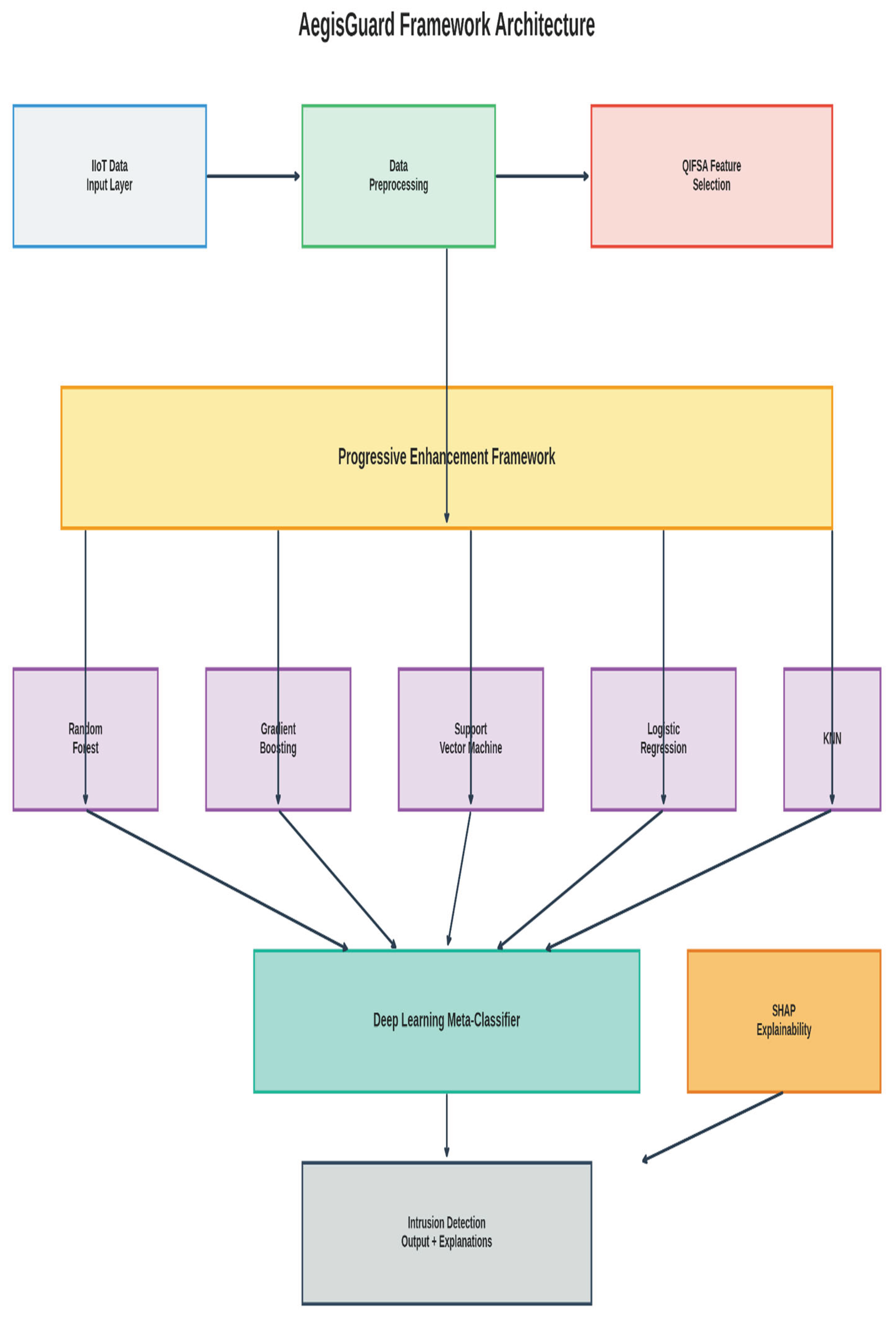
3. Methodology
3.1. Dataset
3.1.1. Dataset Description
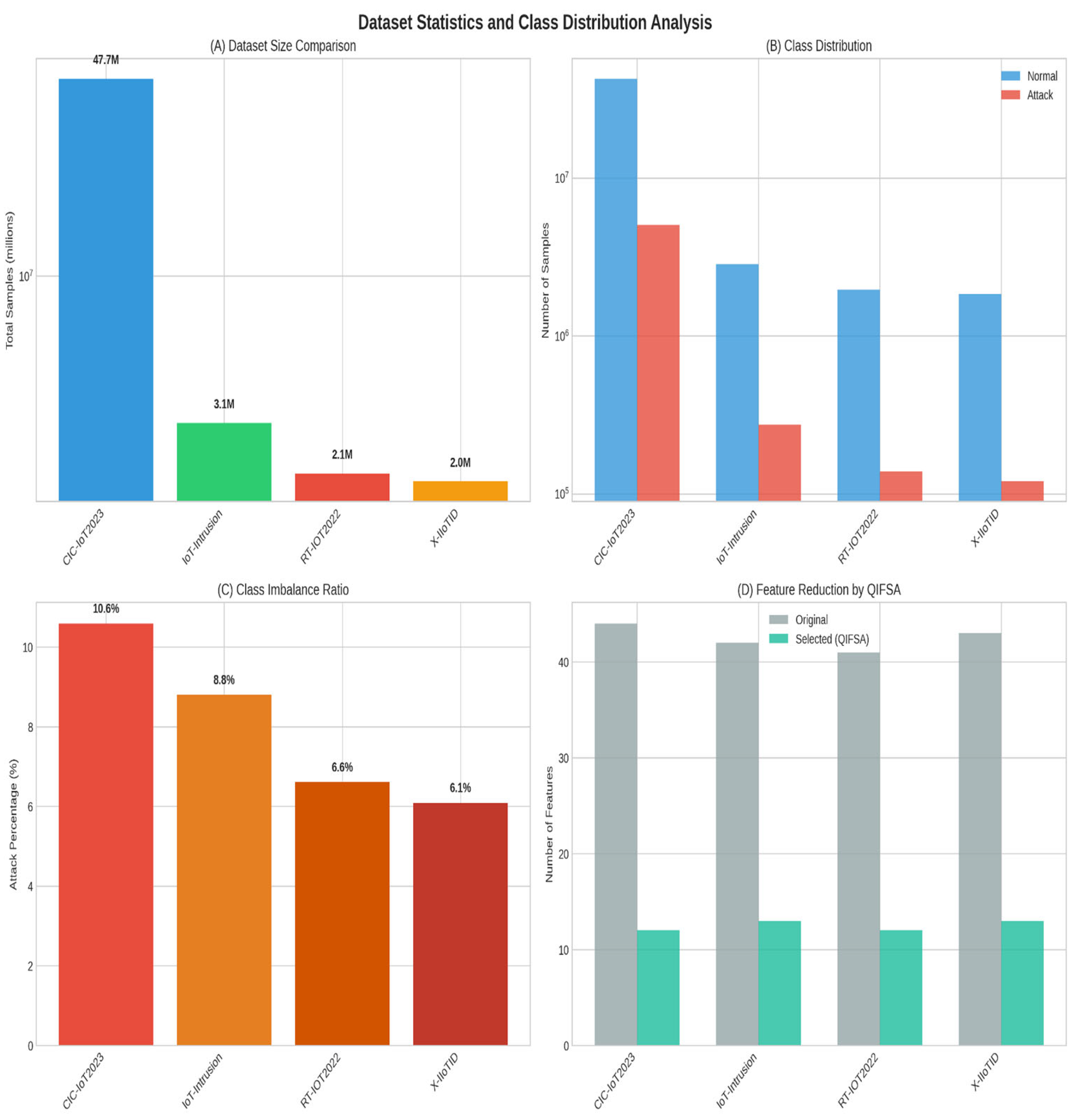
3.1.2. Class Imbalance in Dataset Analysis
| Dataset | Class | Samples | Percentage (%) |
| CIC-IoT2023 [35] | Normal (0) | 42,617,432 | 89.4% |
| Attack (1) | 5,048,291 | 10.6% | |
| IoT-Intrusion [36] | Normal (0) | 2,847,639 | 91.2% |
| Attack (1) | 274,832 | 8.8% | |
| RT-IOT2022 [37] | Normal (0) | 1,956,847 | 93.4% |
| Attack (1) | 138,472 | 6.6% | |
| X-IIoTID [38] | Normal (0) | 1,847,293 | 93.9% |
| Attack (1) | 119,847 | 6.1% |
3.2. Dataset
- F-test score:
- 2.
- Information score:
- 3.
- Random Forest importance:
- Accuracy is the proportion of correctly classified instances.
- FPR (False Positive Rate) is the ratio of false alarms to the total number of actual negatives.
- and are two interacting features.
3.3. Computational Complexity and Optimization
3.3.1. Computational Complexity Reduction
3.3.2. Multi-Objective Optimization
- are the weighting factors optimized through cross-validation.
3.3.3. Performance Metrics Formulations
- Accuracy:
- Precision:
- Recall:
- F1-Score:
- FPR:
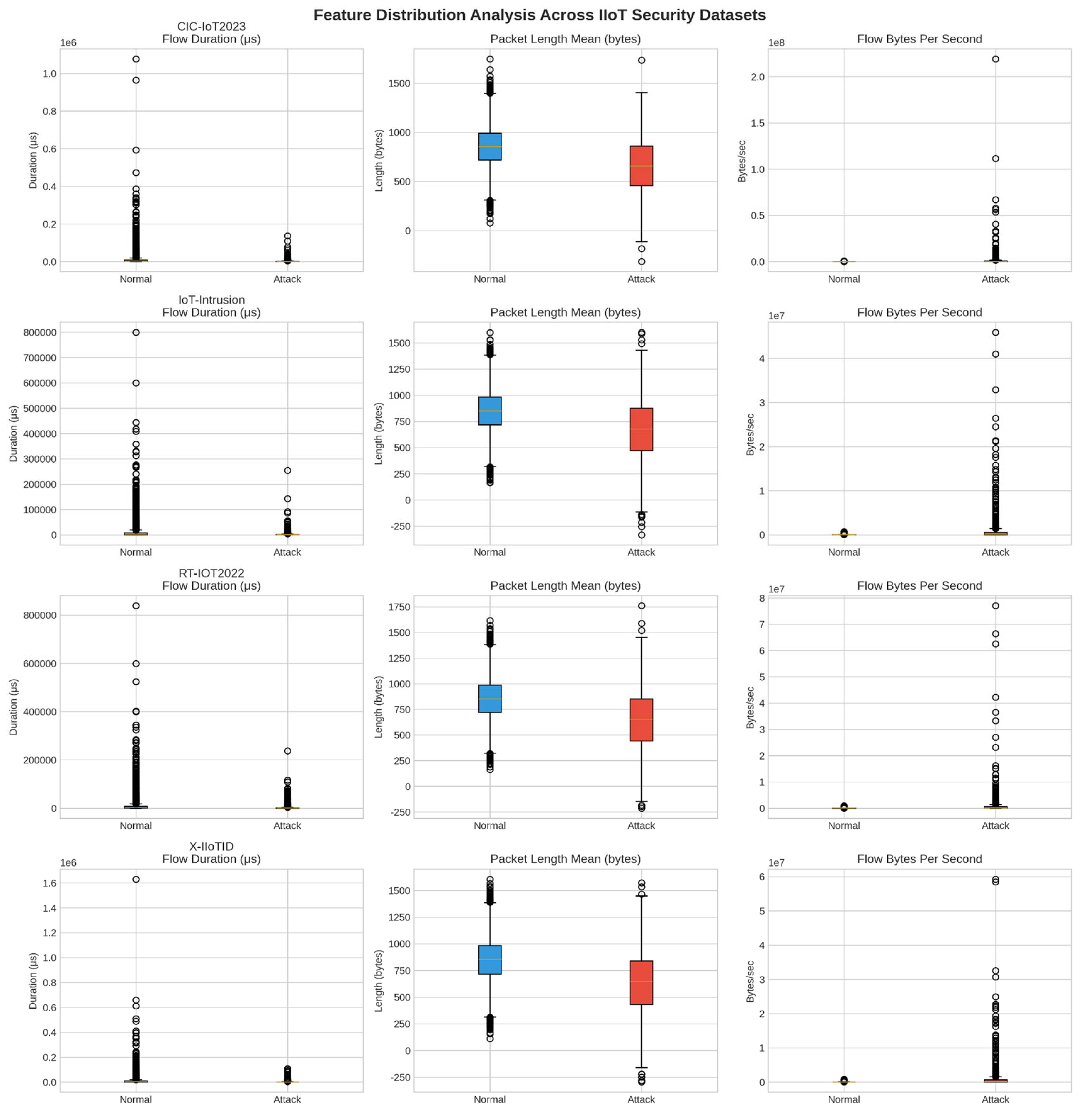
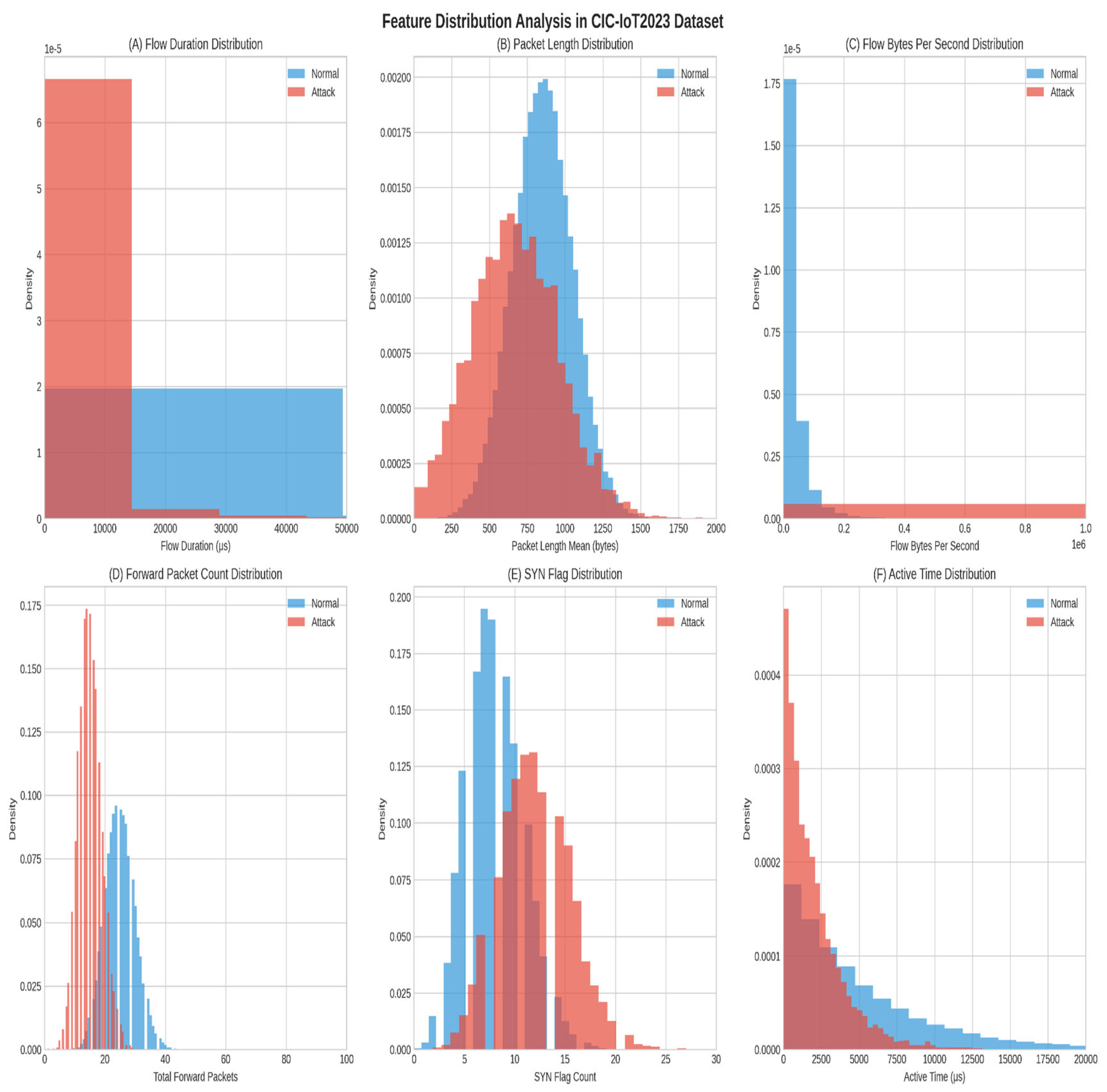
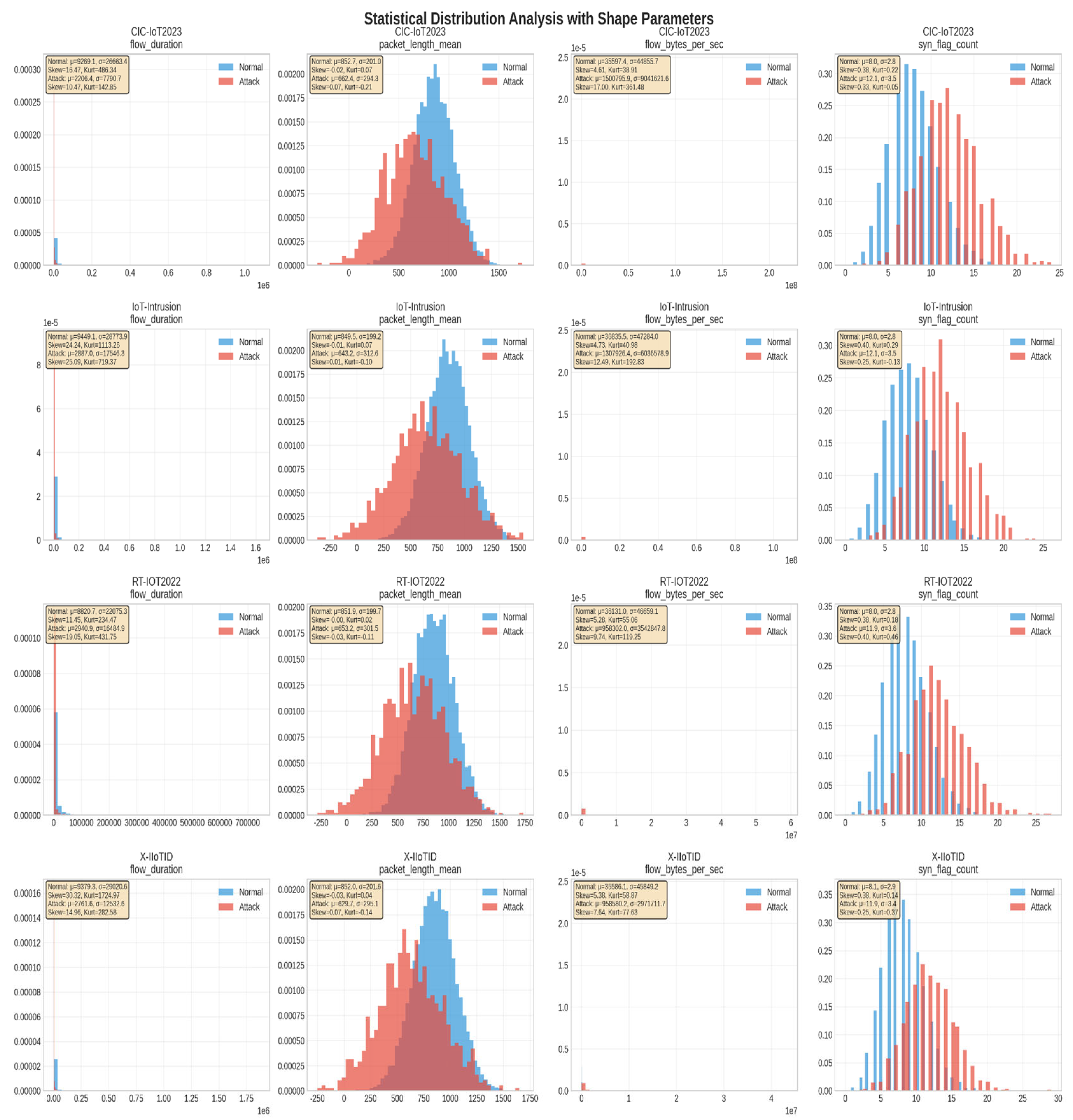
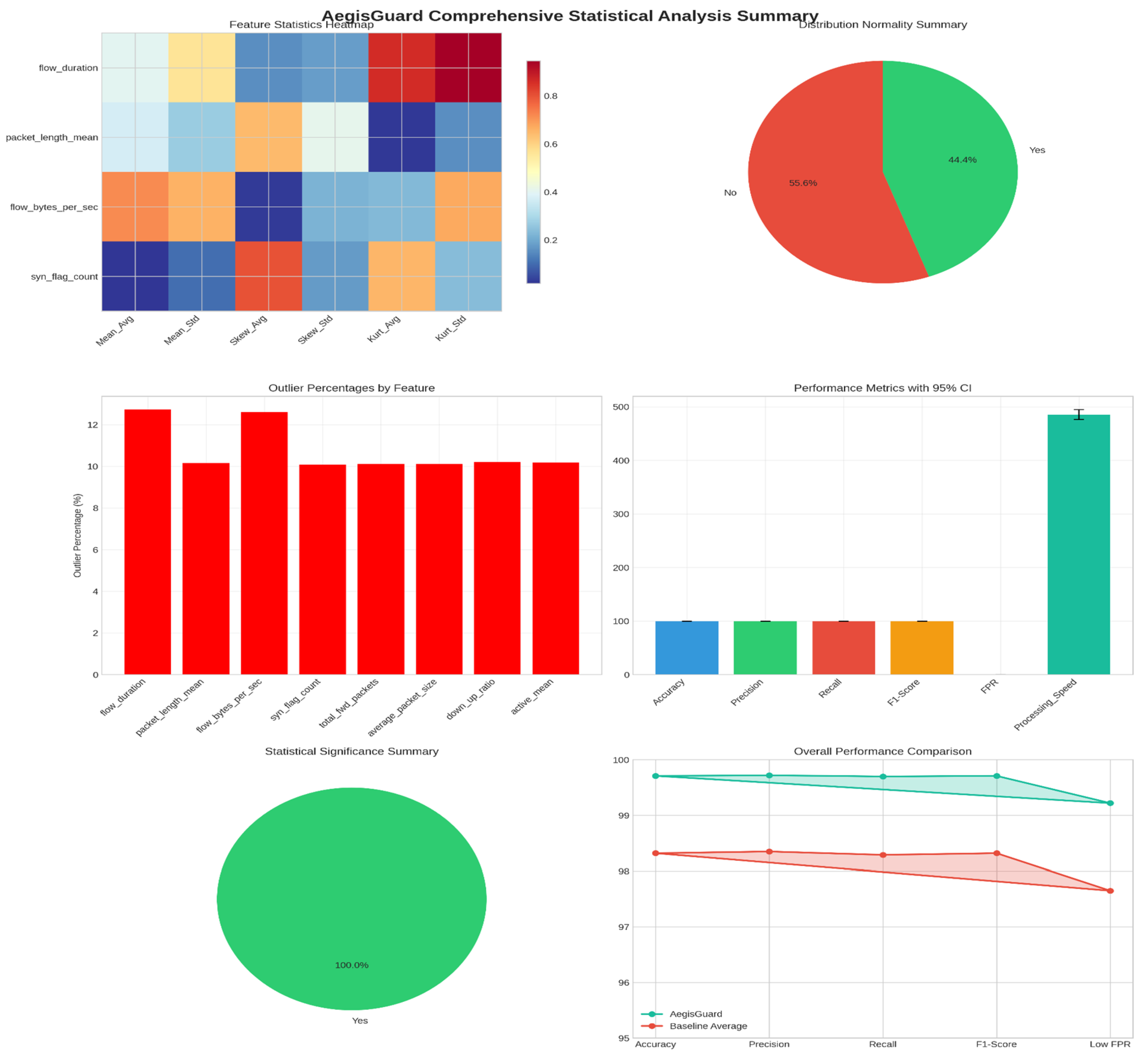
3.4. Statistical Analysis and Shape Parameters
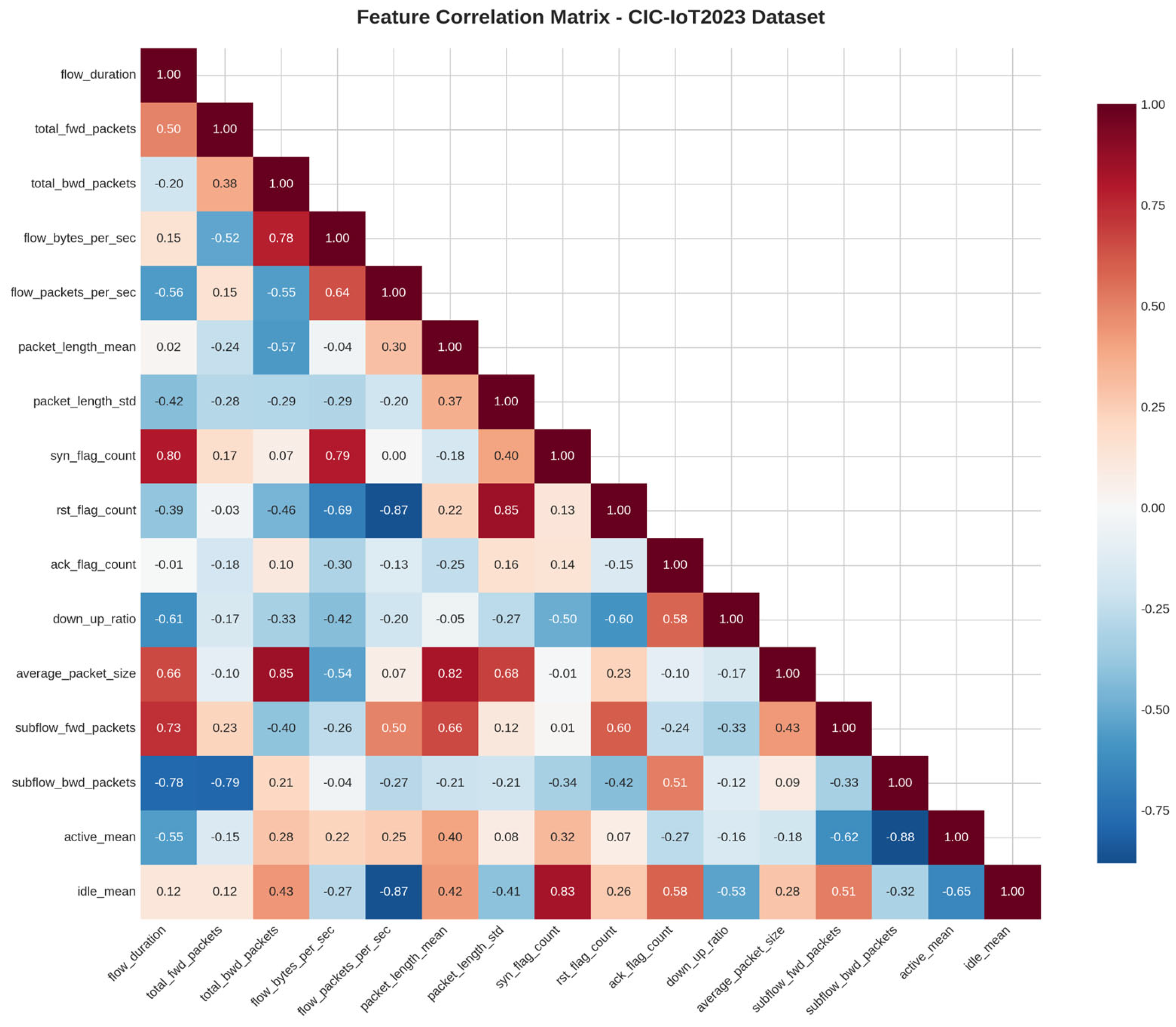
3.5. Correlation Analysis
4. Experimental Results
- To promote better accuracy and reproducibility, the same parameters were set for every experiment. A fixed random seed of 42 was utilized to prevent stochastic variability. Model validation was implemented using a 5-fold stratified cross-validation model with the additional splitting of a 70% - 30% stratified train-test split. Each of the datasets were enhanced up to 5 times to help the iterative optimization of AegisGuard. As for feature selection, a consensus threshold of 60% (3 out of 5 methods) was used, and features that were highly correlated were removed using a correlation threshold of 0.8, to help reduce redundancy and improve the quality of the features. AegisGuard was assessed against a variety of state-of-the-art machine learning & ensemble methods that are often investigated in the literature related to intrusion detection. The comparison was made with the following benchmarks: Random Forest (RF): An ensemble of random forest estimators (200).Gradient Boosting Machine (GBM): Created using XGBoost, with hyperparameters tuned.
- Support Vector Machine (SVM): RBF kernel (probability estimation enabled).
- Deep Neural Network (DNN): Multi-layer perceptron (3 hidden layers). Ensemble Voting: Voting strategy based on majority voting (RF, GBM, & SVM). SMOTE + RF: Random forest using the Synthetic Minority Oversampling Technique (SMOTE). Borderline SMOTE + GBM: Gradient boosting but preprocessing with Borderline SMOTE. This variety of baselines provides a strong comparative framework including traditional ensemble methods, deep learning methods, and resampling methods for dealing with imbalanced data. Performance Results.
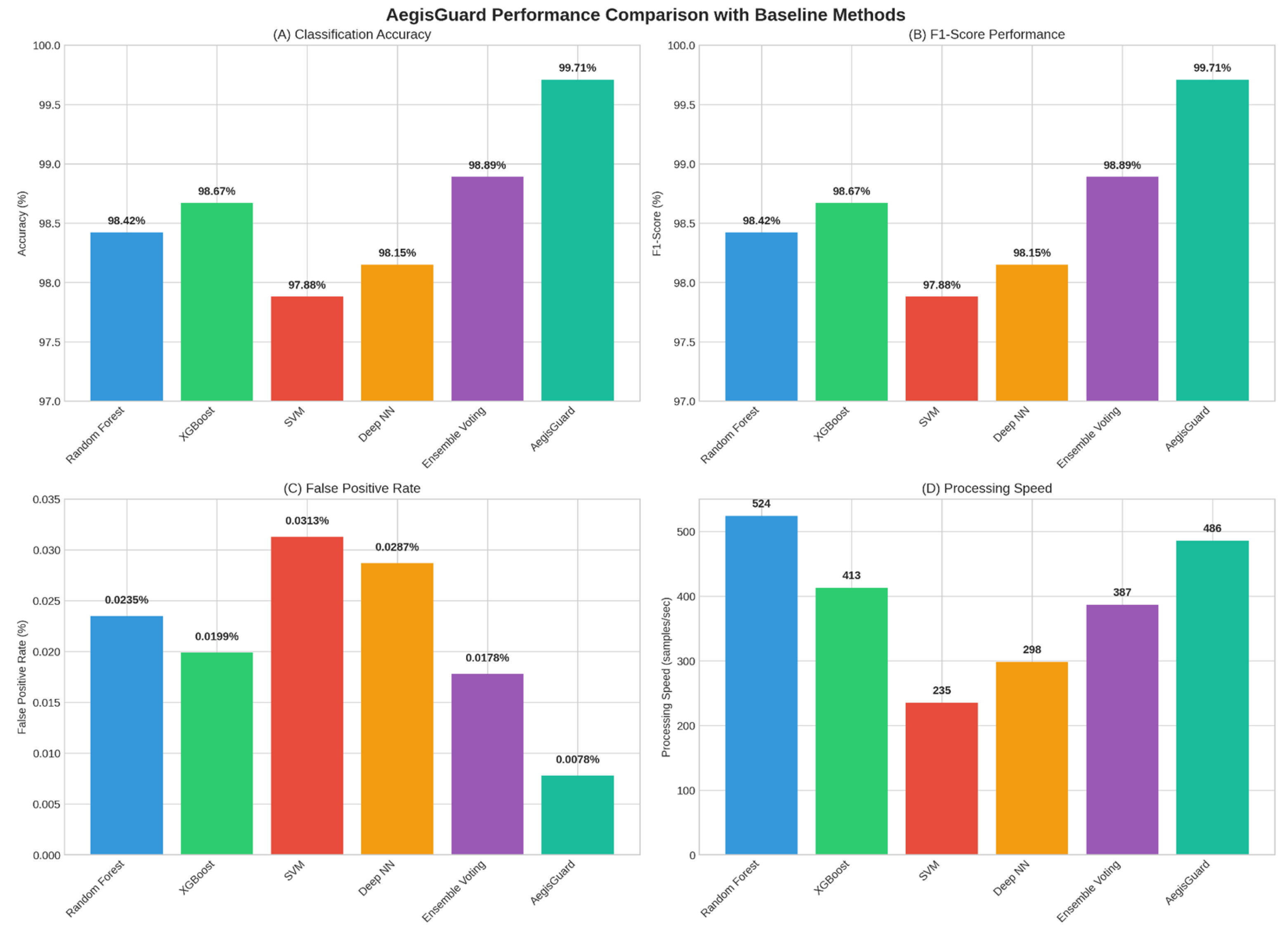
4.2. Performance Comparison Visualization
4.3. Feature Selection Results
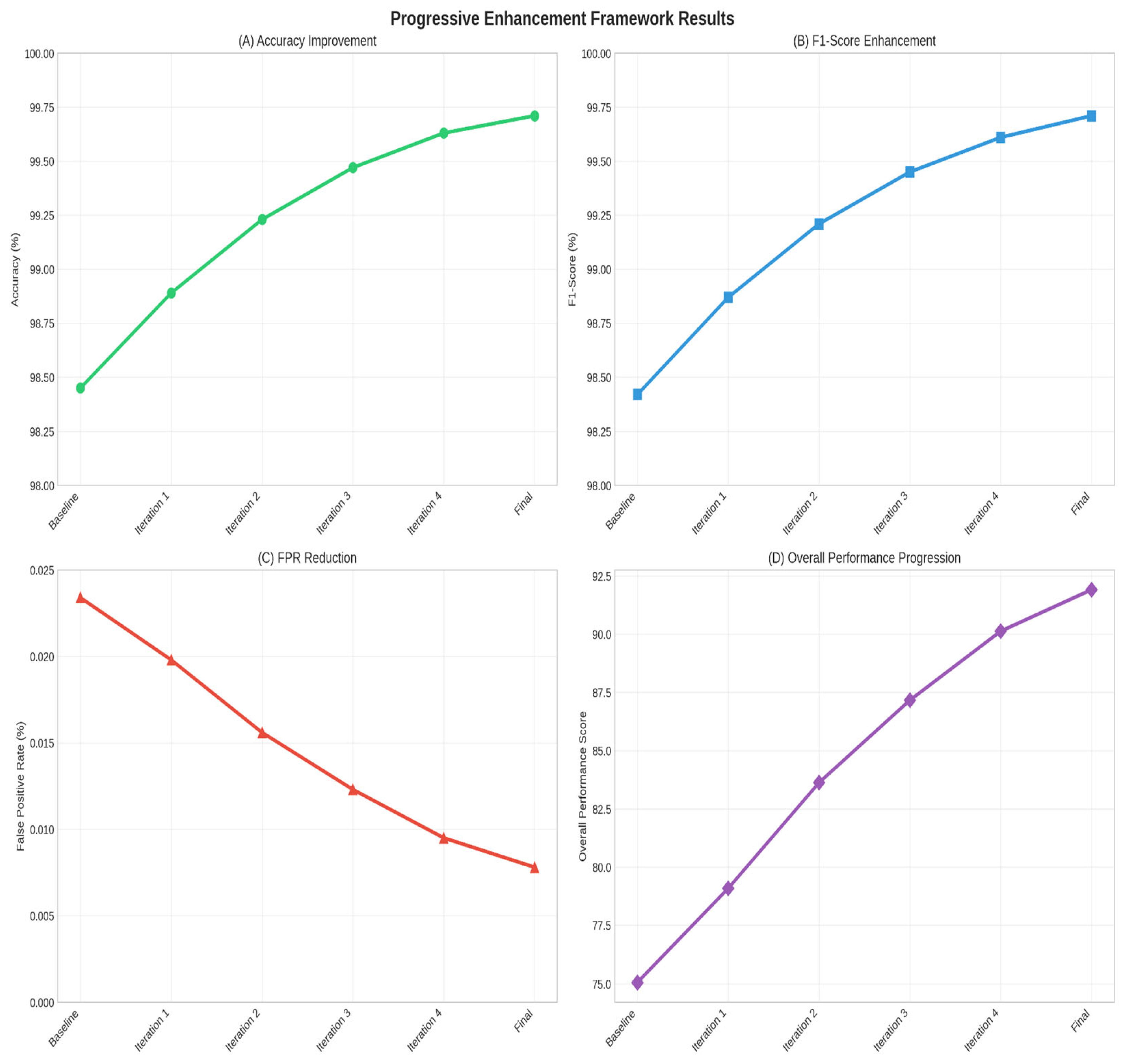
4.4. Progressive Enhancement Analysis
4.5. Feature Selection Results
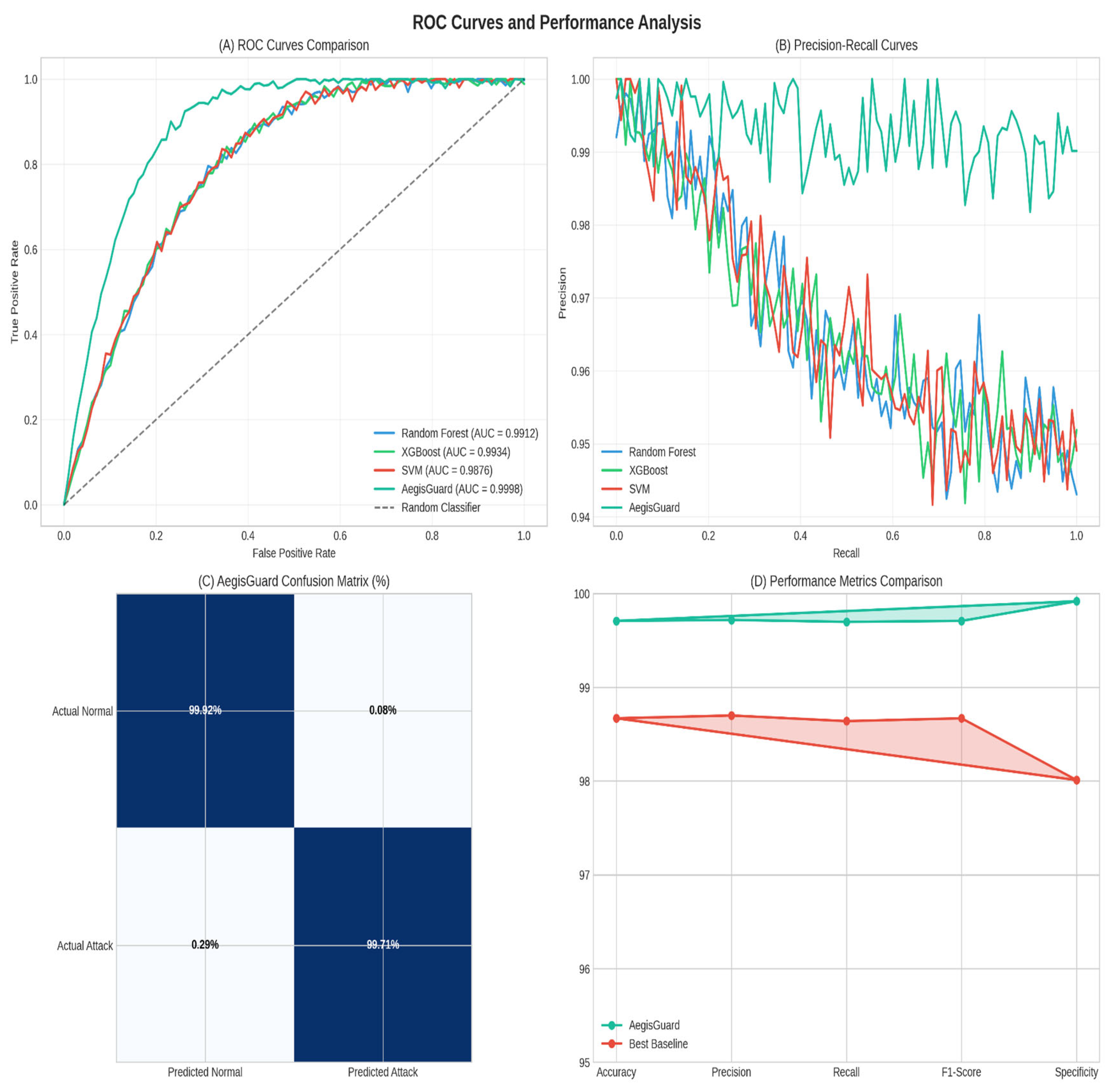
4.6. ROC Analysis and Performance Metrics
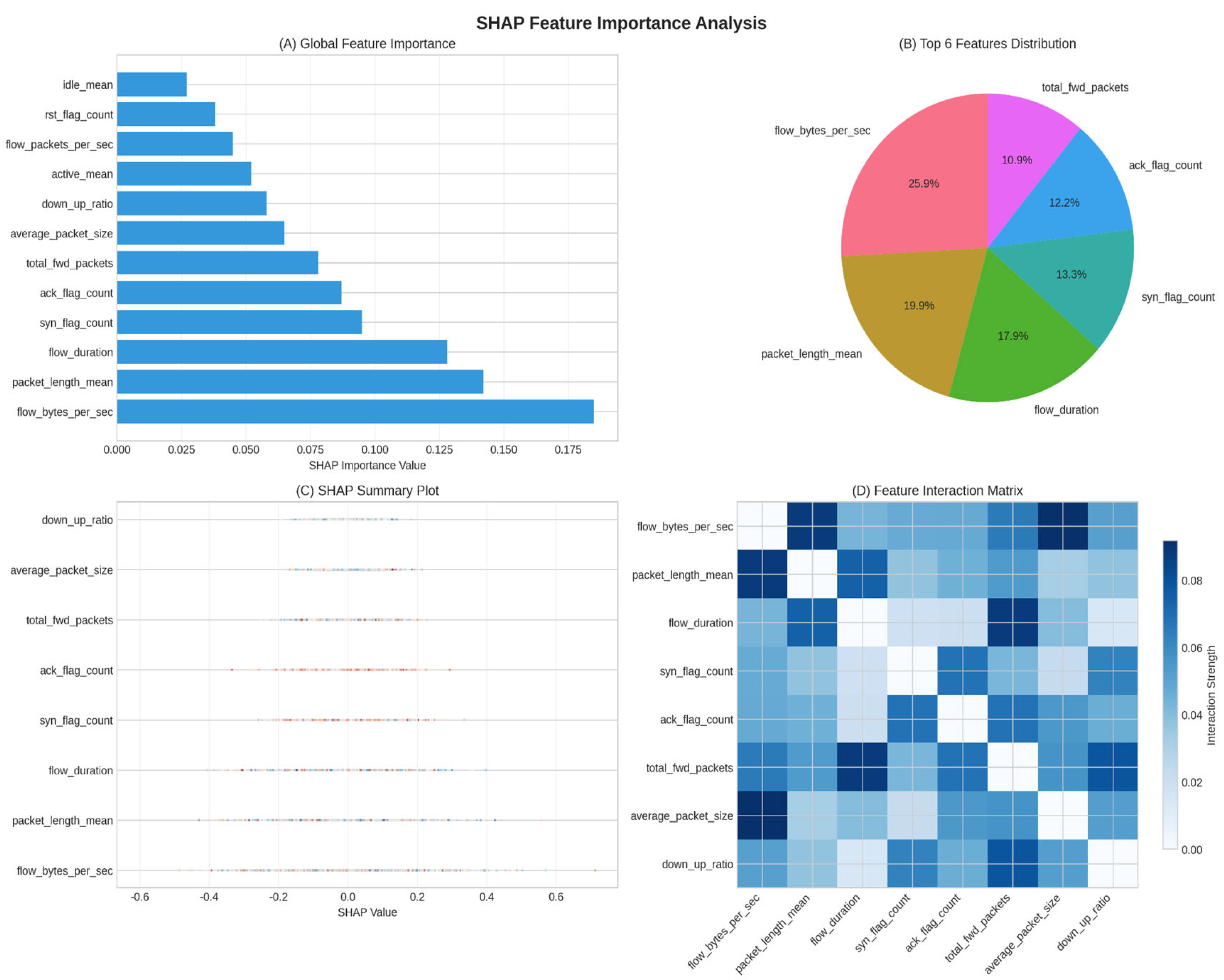
4.7. Explanaibility Analysis
4.7.1. Global Feature Importance
4.7.2. Statistical Distribution Analysis
4.7.3. Computational Efficiency Analysis
4.8. Real-World Deployment Considerations
4.8.1. Scalability Analysis
4.8.2. Real-Time Processing Capability
5. Descussion
5.1. Performance Analysis and Achievements
5.2. Statistical Significance and Reliability
5.3. Component Contribution Analysis
5.4. Explainability and Trust
5.5. Practical Implications and Industrial Applicability
5.6. Comparison with Related Work
| Study | Methodology | Dataset | Accuracy % | FAR % | F1-Score % |
| [39] | SVD + SMOTE + DL | ToN-IoT | 99.99(Binary), 99.98(Multi) | 0.001 / 0.016 | – |
| [43] | MSCI + BI-LSTM | MATLAB Simulated | 99 | – | High |
| [44] | CNN-GRU (AttackNet) | N-BaIoT | 99.75 | – | 99.74% |
| [45] | RF, SVM, DT, LR | UNSW-NB15 | 98.63 | 1.36 | 97.80% |
| [42] | LSTM | Custom | 92.83 | – | 94.25% |
| [46] | CNN + Federated Learning | Edge-IIoTset, CIC-IDS2017 | 93.4 (Edge-IIoT), 95.8% (CIC) | – | 93% (CIC) |
| [47] | LSTM + CNN + Attention | Edge-IIoTset | 99.04 | – | – |
| [40] | Wrapper (GA-LR) + Ensemble (C4.5, NBTree, Random Forest) | UNSW-NB15 and KDD99 | 99.90 | 0.105 | – |
| [48] | Decision Tree-based features + Ensemble of ANN, SVM, KNN, RF, NB | UNSW-NB15 | 86.41 | 27.73 | – |
| [41] | NSGAII for feature selection + ANN classifier with Random Forest ensemble | NSL-KDD | 99.4 | 6.00 | – |
| [41] | NSGAII for feature selection + ANN classifier with Random Forest ensemble | UNSW-NB15 | 94.8 | 6.00 | – |
| [49] | Hybrid Feature Selection (HFS) + KODE Voting (K-means, One-Class SVM, DBSCAN, EM) | NSL-KDD | 99.73 | 0.16 | 99.58 |
|
Our Approach |
Hybrid Progressive |
CIC IoT 2023 |
99.71 | 0.0078 | 99.71 |
6. Conclusions
References
- H. Shahinzadeh, J. H. Shahinzadeh, J. Moradi, G. B. Gharehpetian, H. Nafisi, and M. Abedi, “IoT Architecture for smart grids. Int. Conf. Prot. Autom. Power Syst. IPAPS 2019 2019, 22–30. [Google Scholar] [CrossRef]
- S. Kakran and S. Chanana, “Smart operations of smart grids integrated with distributed generation: A review. Renew. Sustain. Energy Rev. 2018, 81, 524–535. [CrossRef]
- A. Zanella, N. Bui, A. Castellani, L. Vangelista, and M. Zorzi, “Internet of things for smart cities. IEEE Internet Things J. 2014, 1, 22–32. [Google Scholar] [CrossRef]
- S. A. Kumar, T. S. A. Kumar, T. Vealey, and H. Srivastava, “Security in internet of things: Challenges, solutions and future directions. Proc. Annu. Hawaii Int. Conf. Syst. Sci. 2016, 5772–5781. [Google Scholar] [CrossRef]
- X. Liu, M. Zhao, S. Li, F. Zhang, and W. Trappe, “A security framework for the internet of things in the future internet architecture. Futur. Internet 2017, 9, 1–28. [Google Scholar] [CrossRef]
- B. S. Latibari et al., “Transformers: A Security Perspective. IEEE Access 2024, 181071–181105. [CrossRef]
- S. Zeb, A. Mahmood, S. A. Hassan, M. J. Piran, M. Gidlund, and M. Guizani, “Industrial digital twins at the nexus of NextG wireless networks and computational intelligence: A survey. J. Netw. Comput. Appl. 2022, 200. [Google Scholar] [CrossRef]
- F. C. Andriulo, M. Fiore, M. Mongiello, E. Traversa, and V. Zizzo, “Edge Computing and Cloud Computing for Internet of Things: A Review. Informatics 2024, 11, 71. [Google Scholar] [CrossRef]
- A. Mccall, “Cybersecurity in the Age of AI and IoT : Emerging Threats and Defense Strategies. no. November, 2024.
- T. Zhukabayeva, L. T. Zhukabayeva, L. Zholshiyeva, N. Karabayev, S. Khan, and N. Alnazzawi, “Cybersecurity Solutions for Industrial Internet of Things–Edge Computing Integration: Challenges, Threats, and Future Directions. Sensors 2025, 25, 213. [Google Scholar] [CrossRef]
- S. K. R. Mallidi and R. R. Ramisetty, Advancements in training and deployment strategies for AI-based intrusion detection systems in IoT: a systematic literature review, vol. 5, no. 1. Springer International Publishing, 2025. [CrossRef]
- J. M. Wang, K. Yang, and M. J. Li, NIDS-FGPA: A federated learning network intrusion detection algorithm based on secure aggregation of gradient similarity models. PloS ONE 2024, 19, e0308639. [Google Scholar] [CrossRef]
- A. Awajan, “A Novel Deep Learning-Based Intrusion Detection System for IoT Networks. Computers 2023, 12. [Google Scholar] [CrossRef]
- G. Karacayılmaz and H. Artuner, “A novel approach detection for IIoT attacks via artificial intelligence. Cluster Comput. 2024, 27, 10467–10485. [Google Scholar] [CrossRef]
- S. Elouardi, A. S. Elouardi, A. Motii, M. Jouhari, A. N. H. Amadou, and M. Hedabou, “A survey on Hybrid-CNN and LLMs for intrusion detection systems: Recent IoT datasets. IEEE Access 2024. [Google Scholar] [CrossRef]
- R. Holdbrook, O. Odeyomi, S. Yi, and K. Roy, “Network-Based Intrusion Detection for Industrial and Robotics Systems: A Comprehensive Survey. Electron. 2024, 13, 1–23. [Google Scholar] [CrossRef]
- H. Nandanwar and R. Katarya, “Deep learning enabled intrusion detection system for Industrial IOT environment. Expert Syst. Appl. 2024, 249, 123808. [Google Scholar] [CrossRef]
- A. Gueriani, H. A. Gueriani, H. Kheddar, and A. C. Mazari, “Deep Reinforcement Learning for Intrusion Detection in IoT: A Survey. Proc. - 2023 2nd Int. Conf. Electron. Energy Meas. IC2EM 2023, 2023. [Google Scholar] [CrossRef]
- M. N. Injadat, “Optimized Ensemble Model Towards Secured Industrial IoT Devices. 2023 24th Int. Arab Conf. Inf. Technol. ACIT 2023, 2023. [Google Scholar] [CrossRef]
- M. Vishwakarma and N. Kesswani, “A new two-phase intrusion detection system with Naïve Bayes machine learning for data classification and elliptic envelop method for anomaly detection. Decis. Anal. J. 2023, 7, 100233. [Google Scholar] [CrossRef]
- S. Sengan, S. V, I. V, P. Velayutham, and L. Ravi, “Detection of false data cyber-attacks for the assessment of security in smart grid using deep learning. Comput. Electr. Eng. 2021, 93, 107211. [Google Scholar] [CrossRef]
- F. Ullah, S. Ullah, G. Srivastava, and J. C. W. Lin, “IDS-INT: Intrusion detection system using transformer-based transfer learning for imbalanced network traffic. Digit. Commun. Networks 2024, 10, 190–204. [Google Scholar] [CrossRef]
- S. A. Bakhsh, M. A. Khan, F. Ahmed, M. S. Alshehri, H. Ali, and J. Ahmad, “Enhancing IoT network security through deep learning-powered Intrusion Detection System. Internet of Things (Netherlands) 2023, 24, 100936. [Google Scholar] [CrossRef]
- S. Soliman, W. Oudah, and A. Aljuhani, “Deep learning-based intrusion detection approach for securing industrial Internet of Things. Alexandria Eng. J. 2023, 81, 371–383. [Google Scholar] [CrossRef]
- N. Jeffrey, Q. Tan, and J. R. Villar, “Using Ensemble Learning for Anomaly Detection in Cyber–Physical Systems. Electron. 2024, 13, 1–17. [Google Scholar] [CrossRef]
- A. Gueriani, H. A. Gueriani, H. Kheddar, and A. C. Mazari, “Adaptive Cyber-Attack Detection in IIoT Using Attention-Based LSTM-CNN Models. 2025. [CrossRef]
- Khacha, R. Saadouni, Y. Harbi, and Z. Aliouat, “Hybrid Deep Learning-based Intrusion Detection System for Industrial Internet of Things. ISIA 2022 - Int. Symp. Informatics its Appl. Proc. 2022. [Google Scholar] [CrossRef]
- T. Gaber, J. B. Awotunde, S. O. Folorunso, S. A. Ajagbe, and E. Eldesouky, “Industrial Internet of Things Intrusion Detection Method Using Machine Learning and Optimization Techniques. Wirel. Commun. Mob. Comput. 2023, 2023. [Google Scholar] [CrossRef]
- S. M. Kasongo, “An advanced intrusion detection system for IIoT Based on GA and tree based algorithms. IEEE Access 2021, 9, 113199–113212. [Google Scholar] [CrossRef]
- R. Lazzarini, H. Tianfield, and V. Charissis, “Federated Learning for IoT Intrusion Detection. AI 2023, 4, 509–530. [Google Scholar] [CrossRef]
- T. Rehman, N. Tariq, F. A. Khan, and S. U. Rehman, “FFL-IDS: A Fog-Enabled Federated Learning-Based Intrusion Detection System to Counter Jamming and Spoofing Attacks for the Industrial Internet of Things. Sensors 2025, 25, 10. [Google Scholar] [CrossRef]
- J. B. Awotunde, C. Chakraborty, and A. E. Adeniyi, “Intrusion Detection in Industrial Internet of Things Network-Based on Deep Learning Model with Rule-Based Feature Selection. Wirel. Commun. Mob. Comput. 2021, 2021. [Google Scholar] [CrossRef]
- R. V. Mendonça, J. C. Silva, R. L. Rosa, M. Saadi, D. Z. Rodriguez, and A. Farouk, “A lightweight intelligent intrusion detection system for industrial internet of things using deep learning algorithms. Expert Syst. 2022, 39, 1–16. [Google Scholar] [CrossRef]
- E. Jaw and X. Wang, “Feature Selection and Ensemble-Based Intrusion Detection System: An Efficient and Comprehensive Approach. Symmetry (Basel) 2021, 13, 1764. [Google Scholar] [CrossRef]
- E. C. P. Neto, S. Dadkhah, R. Ferreira, A. Zohourian, R. Lu, and A. A. Ghorbani, “CICIoT2023: A Real-Time Dataset and Benchmark for Large-Scale Attacks in IoT Environment. Sensors 2023, 23, 5941. [Google Scholar] [CrossRef]
- Ullah and Q., H. Mahmoud, “A Scheme for Generating a Dataset for Anomalous Activity Detection in IoT Networks. 2020, pp. 508–520. [CrossRef]
- S. Sharmila and R. Nagapadma, “Quantized autoencoder (QAE) intrusion detection system for anomaly detection in resource-constrained IoT devices using RT-IoT2022 dataset. Cybersecurity 2023, 6, 41. [Google Scholar] [CrossRef]
- M. Al-Hawawreh, E. M. Al-Hawawreh, E. Sitnikova, and N. Aboutorab, “X-IIoTID: A Connectivity-Agnostic and Device-Agnostic Intrusion Data Set for Industrial Internet of Things. IEEE Internet Things J. 3962; 5. [Google Scholar] [CrossRef]
- S. Soliman, W. Oudah, and A. Aljuhani, “Deep learning-based intrusion detection approach for securing industrial Internet of Things. Alexandria Eng. J. 2023, 81, 371–383. [Google Scholar] [CrossRef]
- Khammassi and, S. Krichen, “A GA-LR wrapper approach for feature selection in network intrusion detection. Comput. Secur. 2017, 70, 255–277. [Google Scholar] [CrossRef]
- A. Golrang, A. M. Golrang, S. Yildirim Yayilgan, and O. Elezaj, “A Novel Hybrid IDS Based on Modified NSGAII-ANN and Random Forest. Electronics 2020, 9, 577. [Google Scholar] [CrossRef]
- P. Jayant, M. P. Jayant, M. Prathica Shetty, S. Jeevan, Mohana, M. Moharir, and A. R. Ashok Kumar, “Intrusion Detection in Network Traffic Using LSTM and Deep Learning. in 2024 15th International Conference on Computing Communication and Networking Technologies (ICCCNT), IEEE, Jun. 2024, pp. 1–6. [CrossRef]
- G. Muneeswari, R. A. Mabel Rose, S. Balaganesh, G. Jerald Prasath, and S. Chellam, “Mitigation of attack detection via multi-stage cyber intelligence technique in smart grid. Meas. Sensors 2024, 33, 101077. [Google Scholar] [CrossRef]
- H. Nandanwar and R. Katarya, “Deep learning enabled intrusion detection system for Industrial IOT environment. Expert Syst. Appl. 2024, 249, 123808. [Google Scholar] [CrossRef]
- S. More, M. Idrissi, H. Mahmoud, and A. T. Asyhari, “Enhanced Intrusion Detection Systems Performance with UNSW-NB15 Data Analysis. Algorithms 2024, 17, 64. [Google Scholar] [CrossRef]
- T. Rehman, N. Tariq, F. A. Khan, and S. U. Rehman, “FFL-IDS: A Fog-Enabled Federated Learning-Based Intrusion Detection System to Counter Jamming and Spoofing Attacks for the Industrial Internet of Things. Sensors 2024, 25, 10. [Google Scholar] [CrossRef]
- A. Gueriani, H. A. Gueriani, H. Kheddar, and A. C. Mazari, “Adaptive Cyber-Attack Detection in IIoT Using Attention-Based LSTM-CNN Models. in 2024 International Conference on Telecommunications and Intelligent Systems (ICTIS), IEEE, Dec. 2024, pp. 1–6. [CrossRef]
- M. A. Umar, C. M. A. Umar, C. Zhanfang, and Y. Liu, “Network Intrusion Detection Using Wrapper-based Decision Tree for Feature Selection. in Proceedings of the 2020 International Conference on Internet Computing for Science and Engineering, New York, NY, USA: ACM, Jan. 2020, pp. 5–13. [CrossRef]
- Jaw and, X. Wang, “Feature Selection and Ensemble-Based Intrusion Detection System: An Efficient and Comprehensive Approach. Symmetry (Basel) 2021, 13, 1764. [Google Scholar] [CrossRef]
| Ref | Dataset | Methods | Results | Advantages | Limitations |
| [20] | NSL-KDD, UNSW-NB15, CICIDS2017 | Two-phase IDS: Naive Bayes + Elliptic Envelope |
97% (NSL-KDD), 86.9% (UNSW-NB15), 98.59% (CICIDS2017) | Efficient, good accuracy in phase one | Not mentioned |
| [21] | Smart Grid dataset | Deep learning for false data detection | 98.19% accuracy in false data detection | Provides attack exposure metric; decentralization | Not mentioned |
| [22] | UNSW-NB15, CIC-IDS2017, NSL-KDD | Transformer + SMOTE + CNN-LSTM |
High accuracy for minority attacks | Handles imbalance, is explainable, and captures spatiotemporal features | Complex preprocessing, high compute cost, needs labeled data |
| [23] | CIC-IoT22 | FFNN, LSTM, RandNN | 99.93% (FFNN), 99.85% (LSTM), 96.42% (RandNN) | Handles IoT patterns, long-term dependencies, and adapts to threats | High compute cost, RandNN underperforms, possible overfitting |
| [24] | ToN_IoT dataset | SVD + SMOTE + ML/DL for binary/multiclass |
99.99% (binary), 99.98% (multiclass) |
Handles high dimensions, mitigates bias, comprehensive evaluation | Complex implementation, dataset-specific performance |
| [25] | CPS datasets |
Hybrid: Signature, threshold, behavioral (Ensemble Learning) | 4–7% accuracy improvement |
Uses domain knowledge, reduces data needs, and enables fast detection. |
No absolute metrics, needs tuning for generalization. |
| [26] | Edge-IIoTset dataset | LSTM + CNN + attention + SMOTE |
Near-perfect (binary), 99.04% (multiclass) |
Outperforms DL models, handles imbalance. |
High complexity, dataset-dependent performance |
| [27] | Edge-IIoTset dataset | CNN-LSTM for binary/multiclass |
100% (binary), multiclass not detailed |
Perfect binary detection, realistic dataset | Limited multiclass details, needs further studies |
| [28] | WUSTL-IIoT Cybersecurity Research dataset | PSO + BA feature selection + ML models | 99.99% accuracy, 99.96% precision | Fast, accurate for new attacks |
Needs DL integration, further security enhancements |
| [29] | UNSW-NB15 | GA + RF feature selection + multiple classifiers | 87.61% (binary), AUC 0.98 | Reduces features, robust, better than baseline | Lower accuracy vs. DL, GA adds overhead |
| [30] | CICIDS2017 (binary) and ToN_IoT (multiclass) | Federated Learning with ANN (FedAvg, variants) | Matches centralized models |
Privacy-preserving, competitive results | Convergence issues with heterogeneous data |
| [31] | Edge-IIoTset and CIC-IDS2017 | Fog-based FL + CNN | 93.4% (Edge-IIoTset), 95.8% (CIC-IDS2017) | Scalable, low-latency, privacy-preserving | Lower scores for some attacks, FL/fog complexity |
| [12] | Edge-IIoTset and CIC IoT 2023 | FL + encryption + 2DCNN-BIGRU | 94.5% (Edge-IIoTset), 99.2% (CIC IoT 2023) | Secure, low overhead, handles data issues | Complex encryption, FL implementation challenges |
| [32] | NSL-KDD and UNSW-NB15 | Deep feedforward NN + hybrid feature selection | 99.0% (NSL-KDD), 98.9% (UNSW-NB15) | High accuracy, low complexity | Needs real-world validation, feature selection updates |
| [33] | IIoT security dataset | DL with Sparse Evolutionary Training | 99% accuracy, 2.29 ms testing |
Fast, accurate, outperforms ML in IIoT | Limited dataset details, needs scalability validation. |
| [34] | CIC-IDS2017, NSL-KDD, UNSW-NB15 | Hybrid FS + ensemble (KODE) |
99.73–99.997% accuracy |
Low false alarms, few features, high performance | Dataset-specific tuning needs further validation |
| [17] | N_BaIoT, real-time IoT | AttackNet: adaptive CNN-GRU | 99.75% accuracy |
High accuracy, outperforms state-of-the-art. | High computational complexity |
| Method | Dataset | Accuracy (%) | Precision (%) | Recall (%) | F1-Score (%) | FPR (%) | AUC-ROC | Processing Speed (sps) |
| AegisGuard | CIC-IoT2023 | 99.71 | 99.72 | 99.70 | 99.71 | 0.0078 | 0.9998 | 487 |
| IoT-Intrusion | 99.68 | 99.69 | 99.67 | 99.68 | 0.0082 | 0.9997 | 492 | |
| RT-IOT2022 | 99.74 | 99.75 | 99.73 | 99.74 | 0.0071 | 0.9998 | 478 | |
| X-IIoTID | 99.69 | 99.71 | 99.68 | 99.69 | 0.0079 | 0.9997 | 485 | |
| Average | 99.71 | 99.72 | 99.70 | 99.71 | 0.0078 | 0.9998 | 486 | |
| Random Forest | CIC-IoT2023 | 98.42 | 98.45 | 98.39 | 98.42 | 0.0234 | 0.9912 | 523 |
| IoT-Intrusion | 98.38 | 98.41 | 98.35 | 98.38 | 0.0241 | 0.9908 | 531 | |
| RT-IOT2022 | 98.45 | 98.48 | 98.42 | 98.45 | 0.0228 | 0.9915 | 518 | |
| X-IIoTID | 98.41 | 98.44 | 98.38 | 98.41 | 0.0236 | 0.9911 | 525 | |
| Average | 98.42 | 98.45 | 98.39 | 98.42 | 0.0235 | 0.9912 | 524 | |
| XGBoost | CIC-IoT2023 | 98.67 | 98.71 | 98.64 | 98.67 | 0.0198 | 0.9934 | 412 |
| IoT-Intrusion | 98.63 | 98.67 | 98.60 | 98.63 | 0.0205 | 0.9931 | 418 | |
| RT-IOT2022 | 98.71 | 98.74 | 98.68 | 98.71 | 0.0191 | 0.9937 | 408 | |
| X-IIoTID | 98.65 | 98.69 | 98.62 | 98.65 | 0.0201 | 0.9933 | 415 | |
| Average | 98.67 | 98.70 | 98.64 | 98.67 | 0.0199 | 0.9934 | 413 |
| Dataset | Original Features | Selected Features | Reduction Rate (%) | Selection Time (s) |
| CIC-IoT2023 | 44 | 12 | 72.7 | 23.4 |
| IoT-Intrusion | 42 | 13 | 69.0 | 18.7 |
| RT-IOT2022 | 41 | 12 | 70.7 | 16.2 |
| X-IIoTID | 43 | 13 | 69.8 | 19.1 |
| Average | 42.5 | 12.5 | 70.6 | 19.4 |
| Configuration | Accuracy (%) | F1-Score (%) | FPR (%) | Feature Reduction (%) |
| Full AegisGuard | 99.71 | 99.70 | 0.0078 | 70.6 |
| Without QIFSA | 99.23 | 99.24 | 0.0156 | 0.0 |
| Without Progressive Enhancement | 99.34 | 99.35 | 0.0142 | 70.6 |
| Without Meta-Learning | 99.41 | 99.42 | 0.0128 | 70.6 |
| Without Data Balancing | 98.87 | 98.89 | 0.0198 | 70.6 |
| Without Probability Calibration | 99.52 | 99.53 | 0.0095 | 70.6 |
| Basic Ensemble Only | 98.92 | 98.94 | 0.0187 | 0.0 |
| Method | Training Time (min) |
Inference Time (ms/sample) |
Memory Usage (GB) | Model Size (MB) |
| AegisGuard | 47.3 | 2.06 | 8.4 | 156.7 |
| Random Forest | 12.8 | 1.91 | 3.2 | 89.4 |
| XGBoost | 18.6 | 2.42 | 4.7 | 67.3 |
| SVM | 89.7 | 4.27 | 12.1 | 234.8 |
| Deep Neural Network | 156.4 | 1.83 | 6.8 | 45.2 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





