1. Introduction
Digital transformation (DT) has progressed furiously and organizations in all sectors are being swept by the transformation maelstrom – from moving to digital, adoptin g AI, deploying clouds, to agile software development as the IT infrastructure is becoming modernized and services delivered are being improved, while reducing operational complexity 1. With more and more enterprise organisations embracing cloud-native technologies, the need for scalable, secure and intelligent solutions which can better align cyber security functions with new threat vectors, compliance and innovation [
3]. Amid this emerging setting, AI contributes in automating cloud operations, in improving DevSecOps pipelines, and in fortifying cyber defenses through real-time threat identification, predictive analytics, and adaptive security actions [
4,
5]. At the same time, the diffusion of hybrid and multi-cloud set-ups brought new issues around data protection, workload management, access control, and policy enforcement that pending research sought to address leveraging solid encryption schemes, identity management procedures, and zero-trust paradigms [
6]. Inspired by the intersection of these technological areas, this survey is designed to bring together recent work and best practices in AI-driven cloud security, DevSecOps integration, generative AI, blockchain-enabled infrastructure, and enterprise automation. A detailed overview of how intelligent cloud ecosystems are adapting options to enable secure, scalable and adaptive enterprise solutions is given in [
7] different sources, including some of the academic experience, industry implementation, and technological frames [
8].
2. Advancements in Cloud-Native Architecture
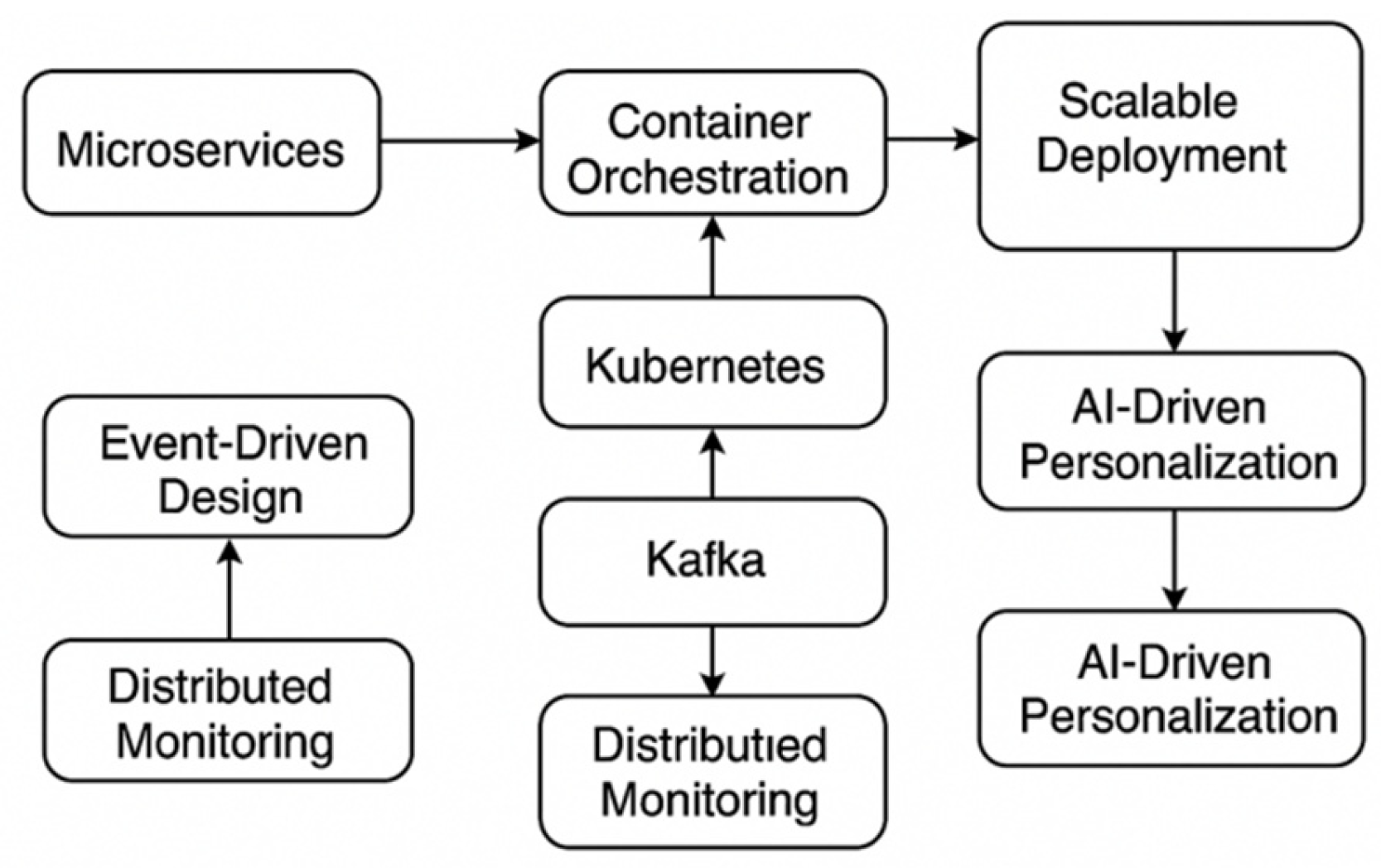
Cloud-native architecture has transformed the way applications are developed, deployed, and scaled through a combination of loosely coupled services, automation, and orchestration platforms. These architectures are mainly based on microservices, where monolithic systems are broken down into modular parts that can be developed, deployed, scaled and maintained independently [
7]. The trend towards serverless computing has simplified management of the backend part, where developers write code and do not worry sampling to provision or maintain servers and, thus, create more flexibility and cost effectiveness [
8]. They perform auto-scaling based on demand and are good for applications with burstable workloads and unpredictable traffic.
Container orchestration systems, such as Kubernetes, have emerged as the de facto technologies that underpin cloud native deployments. Kubernetes automatizes deployment, scaling and operation of containerized applications that come with built-in mechanisms for failure handling, service discovery and load balancing [
9]. Its resilience to keep its system healthy and to recover from different anomalies have made it used by many industries, including banking, healthcare, and retail, where uptime and compliance are very important. Event-driven designs, facilitated by platforms like Apache Kafka, reinforce such environments such that systems can act in a responsive fashion to real-time data streams, enhancing reactivity and integration across separate components [
10,
11].
Kafka is not only used for messaging in cloud-native architectures, it is also adopted for log aggregation, metrics collection and cross-service communication, that can be essential for the event sourcing and state synchronization in high-throughput systems [
12,
13]. Distributed monitoring tools such as the Prometheus.IO monitoring solution and ELK (Elasticsearch, Logstash, Kibana) stacks enhance these setups by offering deep visibility into container health, resource usage, and service-level metrics.
Another addition that has received momentum in cloud-native AI systems is federated learning [
14] that allows for decentralized machine learning model training where data privacy is maintained across devices or regions of a cloud. This approach is essential when data cannot be centralized because of regulatory pressure, as in the financial services or healthcare industry, for example.
In the case of scalability, which along with performance and regulations is something that drives cloud-native adoption. Multi-tenanted systems enable a single system to be consumed by many users/organisations with high isolation.Such systems reuse or share the components of the system, which creates greater efficiency and lower management cost. Such system enables flexible scale and resource allocation, increases effective infrastructure utilization, and preserves application security [
15]. Besides, the AI incorporated into these architectures makes it possible to realize real-time fraud detection and user-behavior-driven service adaptation, providing not only more robust cloud-native services but also smarter ones [
16].
Figure 1: A typical example of modern cloud-native architecture which combines microservices, containers, Kubernetes orchestration, Kafka stream processing and federated AI systems in the cloud-based infrastructure.
Table 1 summarizes key cloud-native core technologies (examples include Kubernetes, Serverless Architecture, Kafka, Federated Learnin) by aspects like scalability, latency, use case as well as security consideration. In this table, we help the reader to understand the metrics side by side, so that stakeholders can make knowledgeable architectural and deployment decisions to construct scalable, resilient systems.
3. DevSecOps and Agile Security Integration
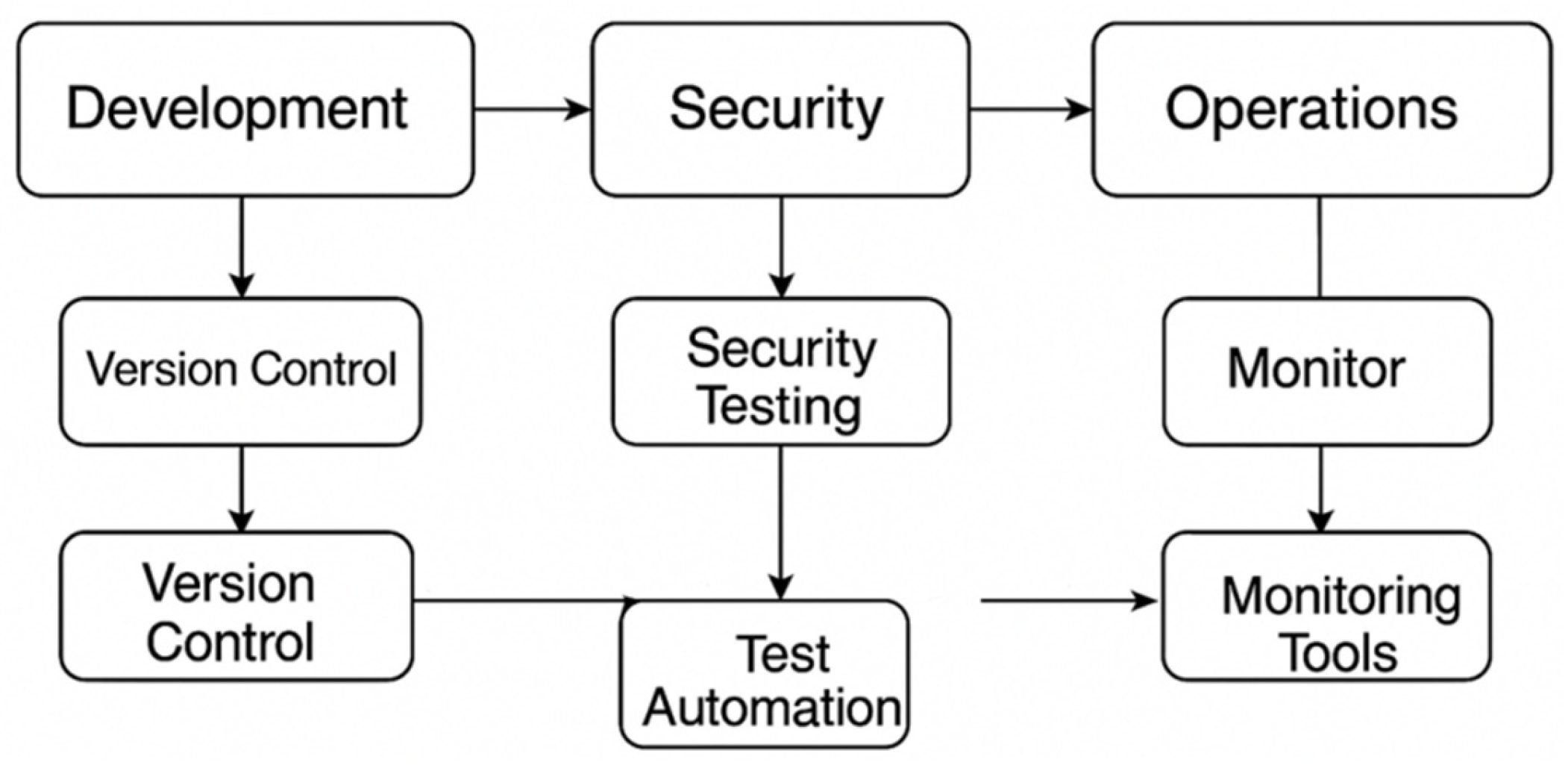
As an evolved discipline of DevOps, DevSecOps embeds security within the software development lifecycle (SDLC) so that security becomes part of the development process and is not treated as an afterthought but is automated and relentless [
17]. This approach is built on the concept that we can break through silos between devs, security, and ops and leverage a culture of collaboration and accountability to achieve shared responsibility for delivering secure code. DevSecOps is particularly critical in current agile development environments, given that the speed of releases and iterations require automated and integrated security gates that can keep up with innovation [
18].
The author [
19] Organizations bring AI driven tools and frameworks to their DevSecOps pipelines (se-photo below) to detect vulner- abilities earlier, scanned on code and dynamics, and for automation of compliance check. For example, machine learning is currently employed to predict risky coding patterns, to identify suspicious activities in runtime and to improve the patch management cycle. Activities such as threat modeling helps in envisioning the attack surfaces in the design stage and the teams can plan controls beforehand using STRIDE, DREAD etc. [
20].
The notion of ‘moving security left’ has also seen considerable traction, whereby security checks and measures are being incorporated earlier within the CI/CD pipeline as opposed to it being the final gateway prior to deployment [
21]. This change facilitates shorter feedback loops, fasterities to investigate and resolves issues, and more economically standardizes risk. Today, automated tooling such as SAST (Static Application Security Testing), DAST (Dynamic Application Security Testing) and container vulnerability scanners are typically being included in build pipelines, increasing the security posture of every new release without impacting development velocity [
22].
Figure 2 is an example of a DevSecOps pipeline with embedded CI/CD stages, AI-powered security tools, automated compliance checks, feedback loops that help ensure secure software is delivered from code commit to production.
Table 2 illustrates the main challenges in embedding security into agile and DevOps flows, and links them with the efficient AI-enabled and automated solutions. Because it consolidates these two critical elements into a tabular format, the table is a tool to help organizations model secure software delivery practices, work around legacy barriers, and stay on the right side of regulatory authorities as developers work ever faster to get code to production.
Despite these progressions, achieving DevSecOps at scale continues to be difficult, especially in legacy or regulated organizations. Difficult-to-read org-org charts, fragmented tools, and disparate compliance needs can be a hindrance. In addition, the adaptation of DevSecOps practices to industry standards such as HIPAA, PCI-DSS, or GDPR often imply tailoring implementation and specific compliant monitoring [
23,
24]. As the number of microservices, distributed workloads, and cloud-native applications increase, scalability becomes a concern that requires efficient orchestration of security policies and real-time auditing across multiple platforms [
25].
Applying the same security principles of agility and DevOps, it offers a scalable security approach that also supports modern and rapid digital environments. It enables development teams to develop secure software faster, stay regulatory compliant, and respond to threats quickly, whilst reducing manual effort and operational overhead.
4. AI for Cloud Security and Cyber Defense
Cloud security and cyber defense are gradually more important with the prevalence and complexity of cyber threats, and the application of artificial intelligence (AI) in cloud security and cyber defense. AI is utilized to improve cloud security posture management (CSPM), which monitors cloud environments, identifies misconfigurations automatically, and enforces compliance across multi-cloud systems [
26]. In contrast, legacy security systems are rule-based and AI systems employ machine learning techniques to discover zeroday vulnerabilities, anticipate threat behavior, and dynamically respond to new attack vectors in a real-time manner [
27].
Generative AI, especially, is a game-changer for the Cyber security field. Apart from conventional supervised learning models, generative models (e.g., GANs or Generative Adversarial Networks) are also employed for simulating attack scenarios and generating synthetic malware datasets for training and evaluating the performance of a system under adversarial scenarios as we observe in [
28]. The problem of hypothesis in (security) investigation The above class of models is also being used in automating hypothesis generation in security research, which aims at decreasing the time to unveil (new) hidden vulnerabilities or anomalous behavior of complex systems [
29]. To address the risk of misuse, ethical considerations and guidelines are being developed to help ensure ethical use of generative AI in security-critical contexts [
30].
AI-powered security operations centers (SOCs) leverage automation to reduce human efforts and enhance the detection of threats. These systems analyze massive volumes of telemetry, logs, and network flows with techniques such as natural language processing (NLP) and anomaly detection to identify potentially suspicious activities as they occur [
31]. Financial and e-commerce fraud detection models are also using AI for the analysis of transactional behavior, triggering deviations of counsins with user profiles and with high precision is capable to detect fraudulent activity [
32]. Likewise, AI-enabled automatic data classification is common tool which is used to categorize the data so that it can be protected as per laws and regulations [
33].
To boost the barrier against unauthorized access, businesses are applying AI to their identity and access management (IAM) efforts. Zero trust architectures based on the premise of “never trust, always verify”, are augmented with AI for dynamic user authentication, behavior monitoring, and context-aware access policies enforcement [
34]. Zero-Trust Identity Security MFA solutions are the first wave of tools to use AI to assess risk on a real-time basis, and adaptive authentication workflows reduce friction slide for legitimate users, while ensuring tenants cannot be compromised (untrusted) [
35].
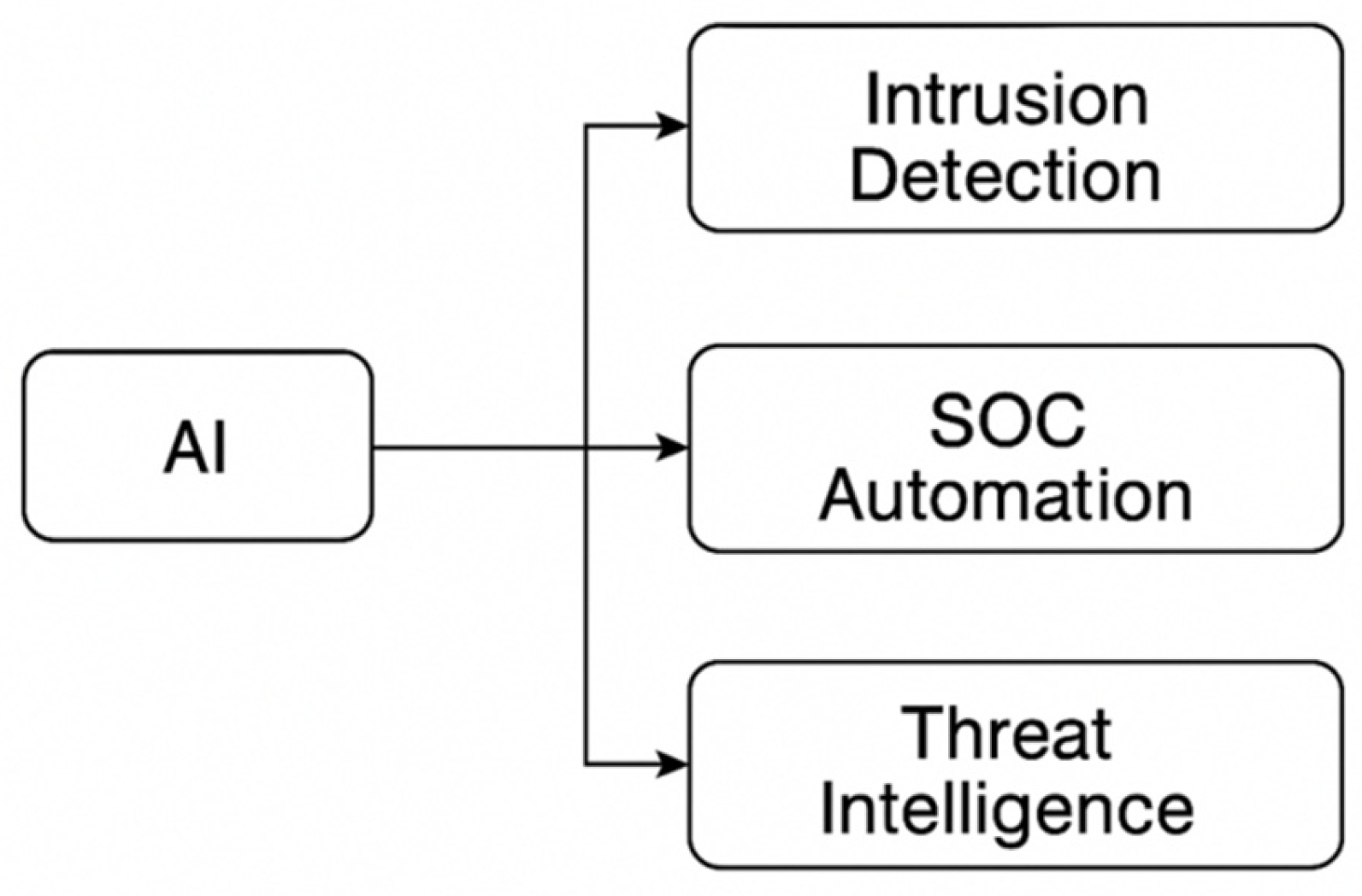
Figure 3 is an AI adoption overview for cloud security layers: intrusion detection systems, security operations center (SOC) automation, zero trust access policy enforcement, and endpoint protection workflows.
Table 3 Illustrative applications of AI in different Cyber security and compliance categories such as intrusion detection, fraud detection, SOC automation and access control. It shows how AI is both aligned to particular technologies providing organisations with a map to contextualise technologies against business needs and reinforces AI’s role in protecting digital infrastructure and ensuring regulatory alignment in complex environments.
By deploying AI throughout the cloud security stack—from the edge to the core and the client—organizations are attaining enhanced agility, resilience and predictive ability in their Cyber security operations. This AI-powered methodology is critical to out-smarting evolving cyber threats and safeguarding trust in digital fabric.
5. Blockchain, SAP, and ERP Integrations
ERP systems and platforms such as SAP represent one of the mission-critical backbone technologies to manage an organization’s business processes with respect to the core functions of finance, supply chain, HR and manufacturing. In the context of the proliferation of digital ecosystems, these platforms are increasingly using advanced technologies such as artificial intelligence (AI), blockchain and cloud computing [
36] for enhancing efficiency, security and data driven decision making. Integrating AI into SAP modules allows real-time data analysis, intelligent work-step automation, and advanced prognosticate for vital business functions [
37].
One of the important innovations is the combination of SAP HANA with cloud infrastructure to enable scalable in-memory computing. The design of SAP HANA, which supports both transactional and analytical processing at very high speed, is relevant for fields such as manufacturing and healthcare industries where real-time data is required [
38]. The researchers have suggested a model for turning SAP HANA into an AI platform that uses AI algorithms for anomaly detection, automatic reporting, and intelligent compliance monitoring [
39]. This is especially important in regulated sectors, such as the financial sector where auditability and transparency are critical to operations [
40].
And in ERP/SAP world the Blockchain technology is being integrated into the systems to bring in cost efficiency, right from the production and to efficient sourcing and root cause.It also ensures data security across the supply chain, achieves easier traceability and enhances data immutability. In a multi-party transaction, a blockchain provides all parties in a network with an auditable and indisputable set of all transactions, thus minimizing the incidence of fraud and reconciliation errors [
41]. Smart contracts (essentially self-executing contracts implemented as code on blockchain) have particularly been applied to automate compliance, policy-based workflows and procurement/ inventory systems across interconnected entities [
42].
Such tech developments are disrupting fields across the board. In retail, AI applications that are integrated with SAP can tailor customer experiences, automate inventory and manage logistics. In healthcare, for example, blockchain enabled SAP systems allow secure access to patient records, help meet data-privacy regulations, and even simplify the process of billing reconciliation across different organizations/providers. Also, in the manufacturing, AI and blockchain empowered ERP systems improve demand forecasting, production scheduling and predictive maintenance [
43].
AI, blockchain and cloud in ERP and SAP systems is not just about making everything run smoother – it creates new possibilities for innovation, data protection and ecosystem partnering. These integrations make the difference from antiquated monolithic systems to responsive and intelligent enterprise apps crafted to survive and thrive in today’s digital economy.
6. Generative AI and Synthetic Data
Generative Artificial Intelligence (Generative AI) is one of the most exciting advancements in artificial intelligence, where we teach machines to learn, and then apply that learning to come up with new, similar examples. Its most radical contribution in this domain is to the production of synthetic data—data that are artificially generated to preserve certain statistical properties of real data but at the same time protect confidentiality [
44]. One area where this can be particularly useful is in regulated domains, where privacy-preserving analytics are limited by legal constraints or ethical obligations [
45].
Automating the generation of high-quality synthetic datasets, generative AI models, like Variational Autoencoders (VAEs) and Generative Adversarial Networks (GANs), allow enterprises to rehearse rare or high-risk scenarios without any real-world data at risk. This capability has emerged as one of the powerful tools in the training and validation of machine learning models, especially in the face of the scarcity, imbalance, and restrictions of data because of privacy issues [
46]. Such models additionally facilitate hypothesis automation in basic science, enabling testing of theoretical constructs and prediction of simulated results to place bounds on experimental investigations [
47].
Additionally, generative AI is being applied to enhance scientific workflows, including creating natural language summaries, transforming unstructured data to structured datasets, and reasoning and simulation generation tasks in areas such as genomics, material science, and climate modeling. These improvements decrease research time and expense, and improve reproducibility and scale-ability of data-driven experiments.
While there is great promise in generative AI, the technology also creates multiple ethical challenges. The danger is to create misinformation, biased or deepfake information that can threat trust, data integrity and misused through bad or malicious actors [
48]. To mitigate these risks, developers and organizations are encouraged to adhere to ethical design principles (e.g., fairness, transparency, accountability) and to ensure model development complies with global privacy regulations (e.g., GDPR) and evolving AI governance benchmarks [
49].
In addition, responsible AI projects are emerging to ensure safe, explicable and auditable generative AI systems. These can range from the use of algorithmic guardrails, to bias detectors and (potential) stakeholder engagement throughout the development process. Enforcing these practices is necessary, not just to comply with regulations, but to foster public trust in AI-based platforms and data ecosystems [
50].
7. Cyber Security Innovations and Compliance
Amid mounting cyber attacks and increasingly advanced digital threats, organizations are emphasizing the need for a strong Cyber security defense to shield endpoints, networks and data across the entire digital landscape. Nowadays, endpoint security is more essential as we have witnessed the advent of remote work, IoT devices, and cloud-based infrastructures which have broadened the attack surface and has made more systems vulnerable to ransomware, phishing, and zero-day vulnerabilities [
51]. The next generation of IDS such as signature based IDS and anomaly based IDS utilize AI for more adaptive detection and prevention of threats across distributed environment [
52].
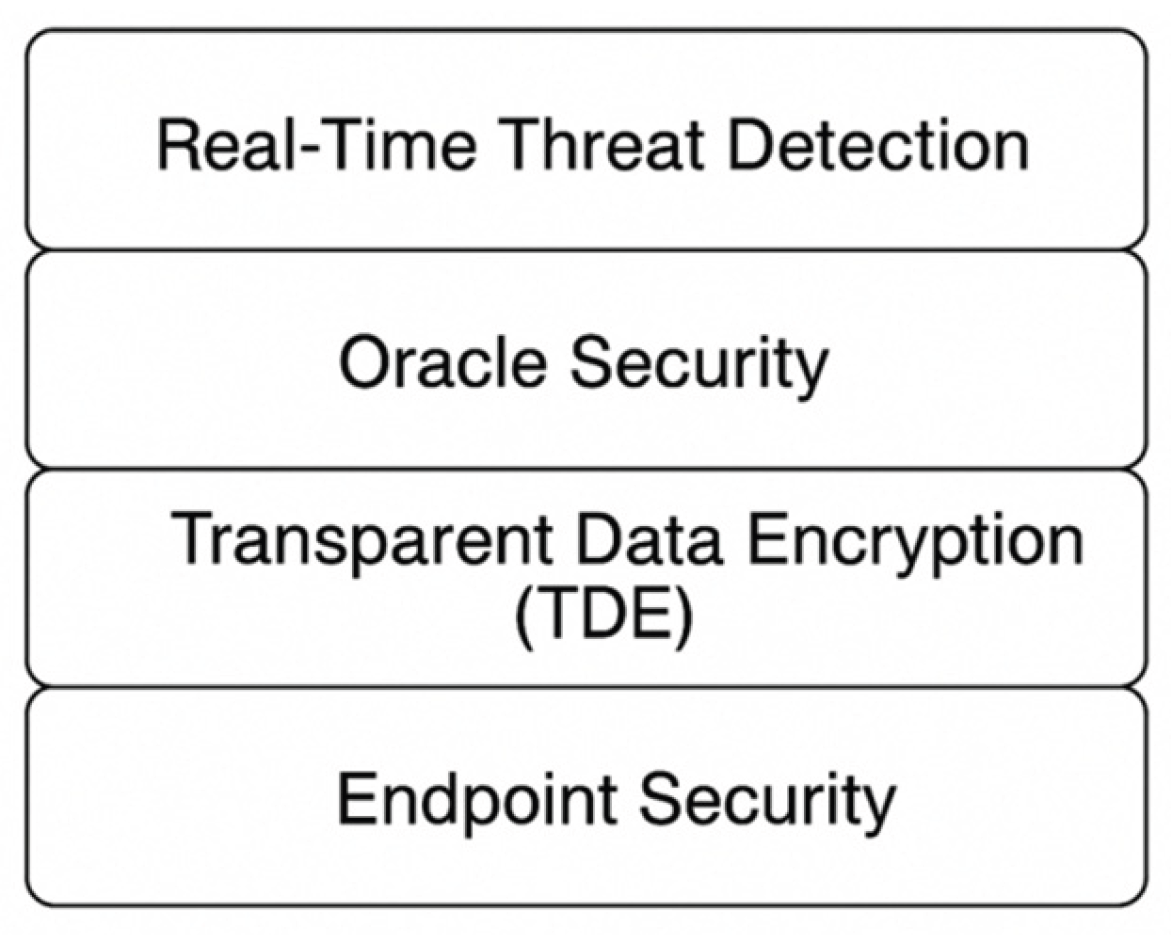
Modern Cyber security approach insists to have strong cryptography and access control mechanism to be in place for data confidentiality and integrity. Tools like TDE or Oracle Database Vault have been extensively deployed to secure sensitive data at rest and in transit, especially in the financial and government domains, which process high- value, or classified information [53, 54]. These encryption schemes, combined with Oracle’s Identity Management and strong authentication methodologies, provide defense in depth features that restrict unauthorized access and prevent insider attacks [
55].
AI is also a key enabler of national and enterprise cyber defense by providing real-time threat detection, automated incident response and proactive vulnerability management. AI models process network telemetry, internet of things (IoT) data, and citizen service systems in smart cities to identify anomalies and avoid cascading failures of essential services like energy, transportation, and emergency response [
56]. In the finance industry, AI-powered security tools track transactional behaviors, identify account takeovers, and pinpoint frauds at scale in real-time with high accuracy and low latencies [
57].
And, strategic necessity: Embedding Cyber security and compliance as a competitive differentiator. Companies also need to adapt their security processes to reflect universal security standards like ISO/IEC 27001 or NIST frameworks and sector-specific directives like HIPAA, PCI-DSS or Basel III, depending on the sector. Real-time audit logs, ongoing compliance checks and automatic policy enforcement with AI are crucial to maintaining a posture in motion [
58].
Figure 4 presents an embedded database proxy, TDE, and AI powered threat monitoring solution, all working together to secure your database and data and meet the demands of modern day security. Unified with encryption, threat intelligence, and AI automation as well as governance controls, today’s Cyber security components are advancing into ‘living’ systems that don’t just prevent contemporary threats, but predict future attack vectors which secure business resilience strategic public trust at a period of unprecedented digital transformation.
8. Emerging Trends and Future Directions
With the advancement in AI and cloud, new-generation IT technologies are driving the next round of digital transformation in finance, cyber security, scientific research, enterprise it industry. One such pivotal trend is the quick rollout of AI-based chatbots that are transforming customer service by enabling real-time, personalized, multilingual technical support via the web and mobile [
59]. New, smarter digital agents are coming of age, able to provide advanced sentiment analysis and context awareness to sharply increase customer and agent satisfaction and system performance.
In finance, natural language processing (NLP) is leading to the rise of intelligent advisors that can understand intricate financial reports, give personalized investment advice and conduct voice-based transactions [
60]. Smart, AI-powered tools that fit into banking ecosystems, driving increased client engagement alongside advancements in, and adherence to, regulation. In addition, AI-augmented Cyber security systems are being used in institutions to oversee the digital transactions, scrutinize user behavior, and alert the authorities in case of any anomalies to make them compliant and safeguard them from financial fraud and cyberheist [
61].
Fraud detection continues to a high-value use case for AI in banking and fintech. State-of-the-art models are able to analyze user’s behavior on-the-fly and then detect patterns of identity theft, phishing or synthetic fraud with low false positive [
62,
63]. In addition to this, the orchestration and management of multi-clouds using platforms like Kubernetes and stream processing engines like Apache Kafka, permits scalable event driven computing, which is required in high frequency finance and the secure delivery of service [
64].
Generative AI will increasingly drive how synthetic datasets are generated, automate hypothesis testing, and drive organization-wide automation workflows. These techniques not only enhance model training and validation but also mitigate the data privacy and AI biases risks in the AI development [65-68]. In the Cyber security area, proactive measures like APT detection systems and zero-trust architectures are increasingly being used to protect enterprise networks and national infrastructures from sophisticated and long-lasting attacks [69-71].
Cloud-native and event-driven platforms are increasingly popular for running scalable applications, which react to user inputs and system events in real time [
72,
73]. These architectural patterns facilitate enhanced observability and AI model serving at scale for real time compliance, uptime, and dynamic capabilities in high-delay environments [
74]. In parallel, advances in multi-factor authentication (MFA), endpoint protection, and federated identity management solutions are essential to the security of distributed digital workplaces (especially in hybrid work settings) [75-77].
CoverageCCV MM Compliance-aware DevSecOps tools are also becoming available, which can enforce real-time regulatory checks, automated documentation and dynamic access control embedded in CI/CD pipelines to ensure audit readiness and improve security governance [
78,
79]. AI-Ushered Customer Engagement in Personalized Fintech Apps: The emergence of AI-powered personalized fintech apps is changing the way banks engage customers with personalized money insights, budget planning and predictive analytics to make smarter money decisions [
80].
Novel approaches such as federated learning make it feasible to train secure AI models over decentralized datasets, safeguarding privacy and enhancing model accuracy across organizations and geographies [
81]. Furthermore, payment systems based on blockchain are allowing tamper-resistant transaction trails and secure settlement network for digital banking [
82]. AI-backed backend systems—based on microservice architectures, serverless computing, and smart orchestration—provide robust and responsive financial applications that can handle the changing market conditions and regulatory requirements [83-85].
Moving forward, real-time infrastructure monitoring, predictive fraud protection and AI-powered risk analytics will be the vanguard of digital innovation strategies. Organizations that invest in resilient design, secure architecture, and automated threat intelligence capabilities will be able to manage the challenges of digital transformation, preserving trust, performance, and compliance in a competitive global environment [86-88].
9. Conclusions
This survey synthesize 88 references related to AI, Cloud computing, DevSecOps and Cybersecurity. As businesses adopt digital transformation, they need to rely on AI-driven cloud services, ethical generative AI models, and integrated security provisions to stay competitive and protect the corporation. The lessons learned in this chapter are a guideline for what will follow in term of exploration and enterprise-level application.
References
-
Dalal, A. (2025). Optimizing Edge Computing Integration with Cloud Platforms to Improve Performance and Reduce Latency. Available at SSRN 5268128. [CrossRef]
-
Arora, A. (2025). THE IMPACT OF GENERATIVE AI ON WORKFORCE PRODUCTIVITY AND CREATIVE PROBLEM SOLVING. Available at SSRN 5268208. [CrossRef]
-
Singh, B. (2025). Enhancing Real-Time Database Security Monitoring Capabilities Using Artificial Intelligence. Available at SSRN 5267988.
-
Kumar, T. V. (2020). Generative AI Applications in Customizing User Experiences in Banking Apps.
-
Singh, H. (2025). Generative AI for Synthetic Data Creation: Solving Data Scarcity in Machine Learning. Available at SSRN 5267914. [CrossRef]
-
Dalal, A. (2025). BRIDGING OPERATIONAL GAPS USING CLOUD COMPUTING TOOLS FOR SEAMLESS TEAM COLLABORATION AND PRODUCTIVITY. Available at SSRN 5268126. [CrossRef]
-
Arora, A. (2025). Developing Generative AI Models That Comply with Privacy Regulations and Ethical Principles. Available at SSRN 5268204. [CrossRef]
-
Singh, B. (2025). DevSecOps: A Comprehensive Framework for Securing Cloud-Native Applications. Available at SSRN 5267982.
-
Kumar, T. V. (2021). NATURAL LANGUAGE UNDERSTANDING MODELS FOR PERSONALIZED FINANCIAL SERVICES.
-
Singh, H. (2025). How Generative AI is Revolutionizing Scientific Research by Automating Hypothesis Generation. Available at SSRN 5267912. [CrossRef]
-
Dalal, Aryendra. (2023). Data Management Using Cloud Computing. Available at SSRN 5198760. [CrossRef]
-
Arora, A. (2025). Understanding the Security Implications of Generative AI in Sensitive Data Applications. [CrossRef]
-
Singh, B. (2025). Integrating Threat Modeling In DevSecOps For Enhanced Application Security. Available at SSRN 5267976.
-
Kumar, T. V. (2023). Efficient Message Queue Prioritization in Kafka for Critical Systems.
-
Singh, H. (2025). Building Secure Generative AI Models to Prevent Data Leakage and Ethical Misuse. Available at SSRN 5267908. [CrossRef]
-
Dalal, A. (2025). DEVELOPING SCALABLE APPLICATIONS THROUGH ADVANCED SERVERLESS ARCHITECTURES IN CLOUD ECOSYSTEMS. Available at SSRN 5268116. [CrossRef]
-
Arora, A. (2025). Evaluating Ethical Challenges in Generative AI Development and Responsible Usage Guidelines. Available at SSRN 5268196. [CrossRef]
-
Singh, B. (2025). Challenges and Solutions for Adopting DevSecOps in Large Organizations. Available at SSRN 5267971.
-
Kumar, T. V. (2018). Event-Driven App Design for High-Concurrency Microservices.
-
Singh, H. (2025). The Future Of Generative Ai: Opportunities, Challenges, And Industry Disruption Potential. (May 23, 2025). [CrossRef]
-
Dalal, A., et al. (2025, February). Developing a Blockchain-Based AI-IoT Platform for Industrial Automation and Control Systems. In IEEE CE2CT (pp. 744–749). [CrossRef]
-
Arora, A. (2025). Integrating Dev-Sec-Ops Practices to Strengthen Cloud Security in Agile Development Environments. Available at SSRN 5268194. [CrossRef]
-
Singh, B. (2025). Building Secure Software Faster with DevSecOps Principles, Practices, and Implementation Strategies. (May 23, 2025).
-
Kumar, T. V. (2025). Scalable Kubernetes Workload Orchestration for Multi-Cloud Environments.
-
Singh, H. (2025). Leveraging Cloud Security Audits for Identifying Gaps and Ensuring Compliance with Industry Regulations. Available at SSRN 5267898. [CrossRef]
-
Dalal, A. (2017). Advanced Governance, Risk, and Compliance Strategies for SAP and ERP Systems in the US and Europe: Leveraging Automation and Analytics. [CrossRef]
-
Arora, A. (2025). THE SIGNIFICANCE AND ROLE OF AI IN IMPROVING CLOUD SECURITY POSTURE FOR MODERN ENTERPRISES. Available at SSRN 5268192. [CrossRef]
-
Singh, B. (2025). Shifting Security Left Integrating DevSecOps into Agile Software Development Lifecycles. Available at SSRN 5267963.
-
Kumar, T. V. (2022). AI-Powered Fraud Detection in Real-Time Financial Transactions.
-
Singh, H. (2025). Key Cloud Security Challenges for Organizations Embracing Digital Transformation Initiatives. Available at SSRN 5267894. [CrossRef]
-
Dalal, A. (2019). AI Powered Threat Hunting in SAP and ERP Environments: Proactive Approaches to Cyber Defense. Available at SSRN 5198746. [CrossRef]
-
Arora, A. (2025). Analyzing Best Practices and Strategies for Encrypting Data at Rest (Stored) and Data in Transit (Transmitted) in Cloud Environments.Available at SSRN 5268190.
-
Singh, B. (2025). Automating Security Testing in CI/CD Pipelines using DevSecOps Tools: A Comprehensive Study. (May 23, 2025).
-
Kumar, T. V. (2016). Layered App Security Architecture for Protecting Sensitive Data.
-
Singh, H. (2025). STRATEGIES TO BALANCE SCALABILITY AND SECURITY IN CLOUD-NATIVE APPLICATION DEVELOPMENT. Available at SSRN 5267890. [CrossRef]
-
Dalal, A. (2025). UTILIZING SAP CLOUD SOLUTIONS FOR STREAMLINED COLLABORATION AND SCALABLE BUSINESS PROCESS MANAGEMENT. Available at SSRN 5268108. [CrossRef]
-
Arora, A. (2025). Securing Multi-Cloud Architectures using Advanced Cloud Security Management Tools. Available at SSRN 5268184. [CrossRef]
-
Singh, B. (2025). Integrating Security Seamlessly into DevOps Development Pipelines through DevSecOps: A Holistic Approach to Secure Software Delivery. Available at SSRN 5267955.
-
Kumar, T. V. (2019). BLOCKCHAIN-INTEGRATED PAYMENT GATEWAYS FOR SECURE DIGITAL BANKING.
-
Singh, H. (2025). The Role of Multi-Factor Authentication and Encryption in Securing Data Access of Cloud Resources in a Multitenant Environment. Available at SSRN 5267886. [CrossRef]
-
Dalal, A. (2025). Exploring Emerging Trends in Cloud Computing and Their Impact on Enterprise Innovation. Available at SSRN 5268114. [CrossRef]
-
Arora, A. (2025). Comprehensive Cloud Security Strategies for Protecting Sensitive Data in Hybrid Cloud Environments. [CrossRef]
-
Singh, B. (2025). Advanced Oracle Security Techniques for Safeguarding Data Against Evolving Cyber Threats. Available at SSRN 5267951.
-
Kumar, T. V. (2019). Cloud-Based Core Banking Systems Using Microservices Architecture.
-
Singh, H. (2025). The Impact of Advancements in Artificial Intelligence on Autonomous Vehicles and Modern Transportation Systems. Available at SSRN 5267884. [CrossRef]
-
Dalal, A. (2025). Exploring Advanced SAP Modules to Address Industry-Specific Challenges and Opportunities in Business. Available at SSRN 5268100. [CrossRef]
-
Arora, A. (2025). Enhancing Customer Experience across Multiple Business Domains using Artificial Intelligence. Available at SSRN 5268178. [CrossRef]
-
Singh, B. (2025). Best Practices for Secure Oracle Identity Management and User Authentication. Available at SSRN 5267949.
-
Kumar, T. V. (2018). REAL-TIME COMPLIANCE MONITORING IN BANKING OPERATIONS USING AI.
-
Singh, H. (2025). Enhancing Cloud Security Posture with AI-Driven Threat Detection and Response Mechanisms. Available at SSRN 5267878. [CrossRef]
-
Dalal, A. (2025). Maximizing Business Value through Artificial Intelligence and Machine Learning in SAP Platforms. Available at SSRN 5268102. [CrossRef]
-
Arora, A. (2025). Challenges of Integrating Artificial Intelligence in Legacy Systems and Potential Solutions for Seamless Integration. Available at SSRN 5268176. [CrossRef]
-
Singh, B. (2025). Key Oracle Security Challenges and Effective Solutions for Ensuring Robust Database Protection. Available at SSRN 5267946.
-
Kumar, T. V. (2017). CROSS-PLATFORM MOBILE APPLICATION ARCHITECTURE FOR FINANCIAL SERVICES.
-
Singh, H. (2025). Evaluating AI-Enabled Fraud Detection Systems for Protecting Businesses from Financial Losses and Scams. Available at SSRN 5267872. [CrossRef]
-
Dalal, A. (2025). THE RESEARCH JOURNAL (TRJ): A UNIT OF I2OR. Available at SSRN 5268120. [CrossRef]
-
Arora, A. (2025). Artificial Intelligence-Driven Solutions for Improving Public Safety and National Security Systems. Available at SSRN 5268174. [CrossRef]
-
Singh, B. (2025). Oracle Database Vault: Advanced Features for Regulatory Compliance and Control. Available at SSRN 5267938.
-
Kumar, T. V. (2023). REAL-TIME DATA STREAM PROCESSING WITH KAFKA-DRIVEN AI MODELS.
-
Singh, H. (2025). Artificial Intelligence and Robotics Transforming Industries with Intelligent Automation Solutions. Available at SSRN 5267868. [CrossRef]
-
Dalal, A. (2025). Driving Business Transformation through Scalable and Secure Cloud Computing Infrastructure Solutions. Available at SSRN 5268120.
-
Arora, A. (2025). Transforming Cyber security Threat Detection and Prevention Systems using Artificial Intelligence. Available at SSRN 5268166.
-
Singh, B. (2025). Enhancing Oracle Database Security with Transparent Data Encryption (TDE) Solutions. Available at SSRN 5267924.
-
Kumar, T. V. (2016). Multi-Cloud Data Synchronization Using Kafka Stream Processing.
-
Singh, H. (2025). Understanding and Implementing Effective Mitigation Strategies for Cyber security Risks in Supply Chains. Available at SSRN 5267866. [CrossRef]
-
Dalal, A. (2025). Harnessing the Power of SAP Applications to Optimize Enterprise Resource Planning and Business Analytics. Available at SSRN 5268096. [CrossRef]
-
Arora, A. (2025). Zero Trust Architecture: Revolutionizing Cyber security for Modern Digital Environments. Available at SSRN 5268151. [CrossRef]
-
Singh, B. (2025). Mastering Oracle Database Security: Best Practices for Enterprise Protection. Available at SSRN 5267920.
-
Kumar, T. V. (2015). ANALYSIS OF SQL AND NOSQL DATABASE MANAGEMENT SYSTEMS INTENDED FOR UNSTRUCTURED DATA.
-
Singh, H. (2025). The Importance of Cyber security Frameworks and Constant Audits for Identifying Gaps, Meeting Regulatory and Compliance Standards. Presented in May 2025. [CrossRef]
-
Dalal, A. (2025). Revolutionizing Enterprise Data Management Using SAP HANA for Improved Performance and Scalability. Presented May 2025.
-
Arora, A. (2025). The Future of Cybersecurity: Trends and Innovations Shaping Tomorrow’s Threat Landscape. Available at SSRN 5268161. [CrossRef]
-
Singh, H. (2025). AI-Powered Chatbots Transforming Customer Support through Personalized and Automated Interactions. Available at SSRN 5267858. [CrossRef]
-
Kumar, T. V. (2015). CLOUD-NATIVE MODEL DEPLOYMENT FOR FINANCIAL APPLICATIONS.
-
Singh, H. (2025). Cyber security for Smart Cities: Protecting Infrastructure in the Era of Digitalization. Available at SSRN 5267856. [CrossRef]
-
Singh, H. (2025). Securing High-Stakes Digital Transactions: A Comprehensive Study on Cyber security and Data Privacy in Financial Institutions. Available at SSRN 5267850. [CrossRef]
-
Singh, H. (2025). Strengthening Endpoint Security to Reduce Attack Vectors in Distributed Work Environments. Available at SSRN 5267844. [CrossRef]
-
Singh, H. (2025). Advanced Cyber security Techniques for Safeguarding Critical Infrastructure Against Modern Threats. Available at SSRN 5267496. [CrossRef]
-
Jha, K., Dhakad, D., & Singh, B. (2020). Critical review on corrosive properties of metals and polymers in oil and gas pipelines. In Advances in Materials Science and Engineering: Select Proceedings of ICFMMP 2019 (pp. 99–113). [CrossRef]
-
Dalal, A. (2025). THE RESEARCH JOURNAL (TRJ): A UNIT OF I2OR. Available at SSRN 5268120. [CrossRef]
-
Dalal, A. (2025). Driving Business Transformation through Scalable and Secure Cloud Computing Infrastructure Solutions Aryendra Dalal Manager, Systems Administration, Deloitte Services LP. Available at SSRN 5268120. [CrossRef]
-
Dalal, A. (2025). Revolutionizing Enterprise Data Management Using SAP HANA for Improved Performance and Scalability Aryendra Dalal Manager, Systems Administration, Deloitte Services LP. Systems Administration, Deloitte Services LP (May 23, 2025). [CrossRef]
-
Arora, A. (2025). Detecting and Mitigating Advanced Persistent Threats in Cyber security Systems.
-
Singh, B. (2025). Practices, and Implementation Strategies. (May 23, 2025).
-
Singh, B. (2025). CD Pipelines using DevSecOps Tools: A Comprehensive Study. (May 23, 2025).
-
Singh, H. (2025). Meeting Regulatory and Compliance Standards. (May 23, 2025).
-
Kumar, T. V. (2015). Serverless Frameworks for Scalable Banking App Backends.
-
Kumar, T. V. (2019). Personal Finance Management Solutions with AI-Enabled Insights.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).