Submitted:
09 May 2025
Posted:
09 May 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Materials and Methods
2.1. Experiment
2.2. Phase 1. Conceptual Model from the Literature Review
- Phase 2. Determining variables for the experiment.
2.3. Phase 3. Establishing Configuration Parameters and Creating the Testing Scenario
- Equipment for the experiment:
- Design of the indoor experiment.
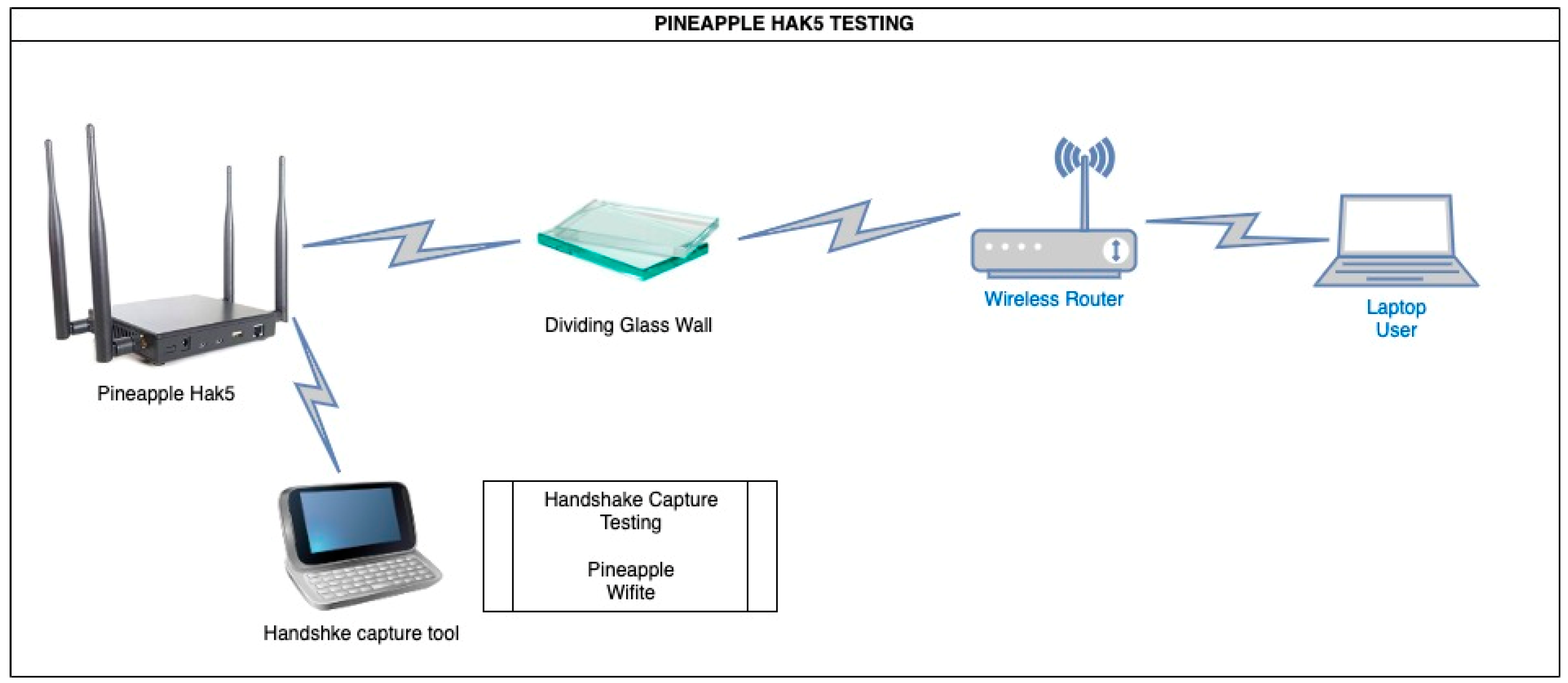
- Indoor testing topology
- Outdoor Experiment Design.
2.3.1. Determining the Type of Attack
2.3.2. Test Framework
2.3.3. Test Parameters with Pinneapple Hacking Device
- Type Atack: HandShake
- WPA Personal Encryption Method
- TKIP Encryption Algorithm
- CTS/RTS Communication Protection off
- Distance: 10, 20 and 30 meters
- Height: 1 meter
- Obstacle: Dividing wood wall and glass wall
- Weather [26]: 30 cº, 26 January 2022
|
Distance (mts) |
Height (mts) |
Time (seg) |
Weather (cº) |
Successful Aruba |
Successful Ruckus |
Successful TP-Link |
Successful Linksys |
| 10 | 1 | 3600 | 30 | No | No | Yes | Yes |
| 20 | 1 | 7200 | 30 | No | No | Yes | Yes |
| 30 | 1 | 14400 | 30 | No | No | No | No |
| 15 | 1 | 5400 | 30 | No | No | No | No |
| 25 | 1 | 10800 | 30 | No | No | No | No |
| 35 | 1 | 21600 | 30 | No | No | No | No |
| 10 | 1 | 3600 | 30 | No | No | Yes | Yes |
| 20 | 1 | 7200 | 30 | No | No | Yes | Yes |
| 30 | 1 | 14400 | 30 | No | No | Yes | Yes |
| 15 | 1 | 5400 | 30 | No | No | Yes | Yes |
| 25 | 1 | 10800 | 30 | No | No | No | No |
| 35 | 1 | 21600 | 30 | No | No | No | No |
- Type Atack: HandShake
- WPA2 Personal Encryption Method
- AES Encryption Algorithm
- CTS/RTS Communication Protection on
- Distance: 10, 20 and 30 meters
- Height: 1 meter
- Obstacle: Dividing wood wall and glass wall
- Weather [26]: 30 cº, 26 January 2022
|
Distance (mts) |
Height (mts) |
Time (seg) |
Weather (cº) |
Successful Aruba |
Successful Ruckus |
Successful TP-Link |
Successful Linksys |
| 10 | 1 | 3600 | 30 | No | No | No | No |
| 20 | 1 | 7200 | 30 | No | No | No | No |
| 30 | 1 | 14400 | 30 | No | No | No | No |
| 15 | 1 | 5400 | 30 | No | No | No | No |
| 25 | 1 | 10800 | 30 | No | No | No | No |
| 35 | 1 | 21600 | 30 | No | No | No | No |
| 10 | 1 | 3600 | 30 | No | No | No | No |
| 20 | 1 | 7200 | 30 | No | No | No | No |
| 30 | 1 | 14400 | 30 | No | No | No | No |
| 15 | 1 | 5400 | 30 | No | No | No | No |
| 25 | 1 | 10800 | 30 | No | No | No | No |
| 35 | 1 | 21600 | 30 | No | No | No | No |
- Type Atack: HandShake
- WPA Personal Encryption Method
- TKIP Encryption Algorithm
- CTS/RTS Communication Protection off
- Distance: 10, 20 and 30 meters
- Height: 30 meters
- Obstacle: Dividing wood wall and glass wall
- Weather [27]: 14 cº, 5 May 2024
|
Distance (mts) |
Height (mts) |
Time (seg) |
Weather (cº) |
Successful Aruba |
Successful Ruckus |
Successful TP-Link |
Successful Linksys |
| 10 | 30 | 3600 | 14 | No | No | Yes | Yes |
| 20 | 30 | 7200 | 14 | No | No | Yes | Yes |
| 30 | 30 | 14400 | 14 | No | No | No | No |
| 15 | 30 | 5400 | 14 | No | No | No | No |
| 25 | 30 | 10800 | 14 | No | No | No | No |
| 35 | 30 | 21600 | 14 | No | No | No | No |
| 10 | 30 | 3600 | 14 | No | No | Yes | Yes |
| 20 | 30 | 7200 | 14 | No | No | Yes | Yes |
| 30 | 30 | 14400 | 14 | No | No | No | No |
| 15 | 30 | 5400 | 14 | No | No | No | No |
| 25 | 30 | 10800 | 14 | No | No | No | No |
| 35 | 30 | 21600 | 14 | No | No | No | No |
- Type Atack: HandShake
- WPA2 Personal Encryption Method
- AES Encryption Algorithm
- CTS/RTS Communication Protection on
- Distance: 10, 20 and 30 meters
- Height: 30 meters
- Obstacle: Dividing wood wall and glass wall
- Weather [27]: 14 cº, 5 May 2024
|
Distance (mts) |
Height (mts) |
Time (seg) |
Weather (cº) |
Successful Aruba |
Successful Ruckus |
Successful TP-Link |
Successful Linksys |
| 10 | 30 | 3600 | 14 | No | No | No | No |
| 20 | 30 | 7200 | 14 | No | No | No | No |
| 30 | 30 | 14400 | 14 | No | No | No | No |
| 15 | 30 | 5400 | 14 | No | No | No | No |
| 25 | 30 | 10800 | 14 | No | No | No | No |
| 35 | 30 | 21600 | 14 | No | No | No | No |
| 10 | 30 | 3600 | 14 | No | No | No | No |
| 20 | 30 | 7200 | 14 | No | No | No | No |
| 30 | 30 | 14400 | 14 | No | No | No | No |
| 15 | 30 | 5400 | 14 | No | No | No | No |
| 25 | 30 | 10800 | 14 | No | No | No | No |
| 35 | 30 | 21600 | 14 | No | No | No | No |
2.3.4. Test Results with Kali Linux Software, "Wifite"
- Type Atack: HandShake
- WPA Personal Encryption Method
- TKIP Encryption Algorithm
- CTS/RTS Communication Protection off
- Distance: 10, 20 and 30 meters
- Height: 1 meter
- Obstacle: Dividing wood wall and glass wall
- Weather [26]: 30 cº, 26 January 2022
|
Distance (mts) |
Height (mts) |
Time (seg) |
Weather (cº) |
Successful Aruba |
Successful Ruckus |
Successful TP-Link |
Successful Linksys |
| 10 | 1 | 3600 | 30 | No | No | Yes | Yes |
| 20 | 1 | 7200 | 30 | No | No | Yes | Yes |
| 30 | 1 | 14400 | 30 | No | No | No | No |
| 15 | 1 | 5400 | 30 | No | No | No | No |
| 25 | 1 | 10800 | 30 | No | No | No | No |
| 35 | 1 | 21600 | 30 | No | No | No | No |
| 10 | 1 | 3600 | 30 | No | No | Yes | Yes |
| 20 | 1 | 7200 | 30 | No | No | Yes | Yes |
| 30 | 1 | 14400 | 30 | No | No | No | Yes |
| 15 | 1 | 5400 | 30 | No | No | No | Yes |
| 25 | 1 | 10800 | 30 | No | No | No | No |
| 35 | 1 | 21600 | 30 | No | No | No | No |
- Type Atack: HandShake
- WPA2 Personal Encryption Method
- AES Encryption Algorithm
- CTS/RTS Communication Protection on
- Distance: 10, 20 and 30 meters
- Height: 1 meter
- Obstacle: Dividing wood wall and glass wall
- Weather [26]: 30 cº, 26 January 2022
|
Distance (mts) |
Height (mts) |
Time (seg) |
Weather (cº) |
Successful Aruba |
Successful Ruckus |
Successful TP-Link |
Successful Linksys |
| 10 | 1 | 3600 | 30 | No | No | No | No |
| 20 | 1 | 7200 | 30 | No | No | No | No |
| 30 | 1 | 14400 | 30 | No | No | No | No |
| 15 | 1 | 5400 | 30 | No | No | No | No |
| 25 | 1 | 10800 | 30 | No | No | No | No |
| 35 | 1 | 21600 | 30 | No | No | No | No |
| 10 | 1 | 3600 | 30 | No | No | No | No |
| 20 | 1 | 7200 | 30 | No | No | No | No |
| 30 | 1 | 14400 | 30 | No | No | No | No |
| 15 | 1 | 5400 | 30 | No | No | No | No |
| 25 | 1 | 10800 | 30 | No | No | No | No |
| 35 | 1 | 21600 | 30 | No | No | No | No |
- Type Atack: HandShake
- WPA Personal Encryption Method
- TKIP Encryption Algorithm
- CTS/RTS Communication Protection off
- Distance: 10, 20 and 30 meters
- Height: 30 meters
- Obstacle: Dividing wood wall and glass wall
- Weather [27]: 14 cº, 5 May 2024
|
Distance (mts) |
Height (mts) |
Time (seg) |
Weather (cº) |
Successful Aruba |
Successful Ruckus |
Successful TP-Link |
Successful Linksys |
| 10 | 30 | 3600 | 14 | Yes | Yes | Yes | Yes |
| 20 | 30 | 7200 | 14 | Yes | Yes | Yes | Yes |
| 30 | 30 | 14400 | 14 | No | No | No | No |
| 15 | 30 | 5400 | 14 | No | No | No | No |
| 25 | 30 | 10800 | 14 | No | No | No | No |
| 35 | 30 | 21600 | 14 | No | No | No | No |
| 10 | 30 | 3600 | 14 | Yes | Yes | Yes | Yes |
| 20 | 30 | 7200 | 14 | Yes | Yes | Yes | Yes |
| 30 | 30 | 14400 | 14 | No | No | No | No |
| 15 | 30 | 5400 | 14 | No | No | No | No |
| 25 | 30 | 10800 | 14 | No | No | No | No |
| 35 | 30 | 21600 | 14 | No | No | No | No |
- Type Atack: HandShake
- WPA2 Personal Encryption Method
- AES Encryption Algorithm
- CTS/RTS Communication Protection on
- Distance: 10, 20 and 30 meters
- Height: 30 meters
- Obstacle: Dividing wood wall and glass wall
- Weather [27]: 14 cº, 5 May 2024
|
Distance (mts) |
Height (mts) |
Time (seg) |
Weather (cº) |
Successful Aruba |
Successful Ruckus |
Successful TP-Link |
Successful Linksys |
| 10 | 30 | 3600 | 14 | No | No | No | No |
| 20 | 30 | 7200 | 14 | No | No | No | No |
| 30 | 30 | 14400 | 14 | No | No | No | No |
| 15 | 30 | 5400 | 14 | No | No | No | No |
| 25 | 30 | 10800 | 14 | No | No | No | No |
| 35 | 30 | 21600 | 14 | No | No | No | No |
| 10 | 30 | 3600 | 14 | No | No | No | No |
| 20 | 30 | 7200 | 14 | No | No | No | No |
| 30 | 30 | 14400 | 14 | No | No | No | No |
| 15 | 30 | 5400 | 14 | No | No | No | No |
| 25 | 30 | 10800 | 14 | No | No | No | No |
| 35 | 30 | 21600 | 14 | No | No | No | No |
3. Results
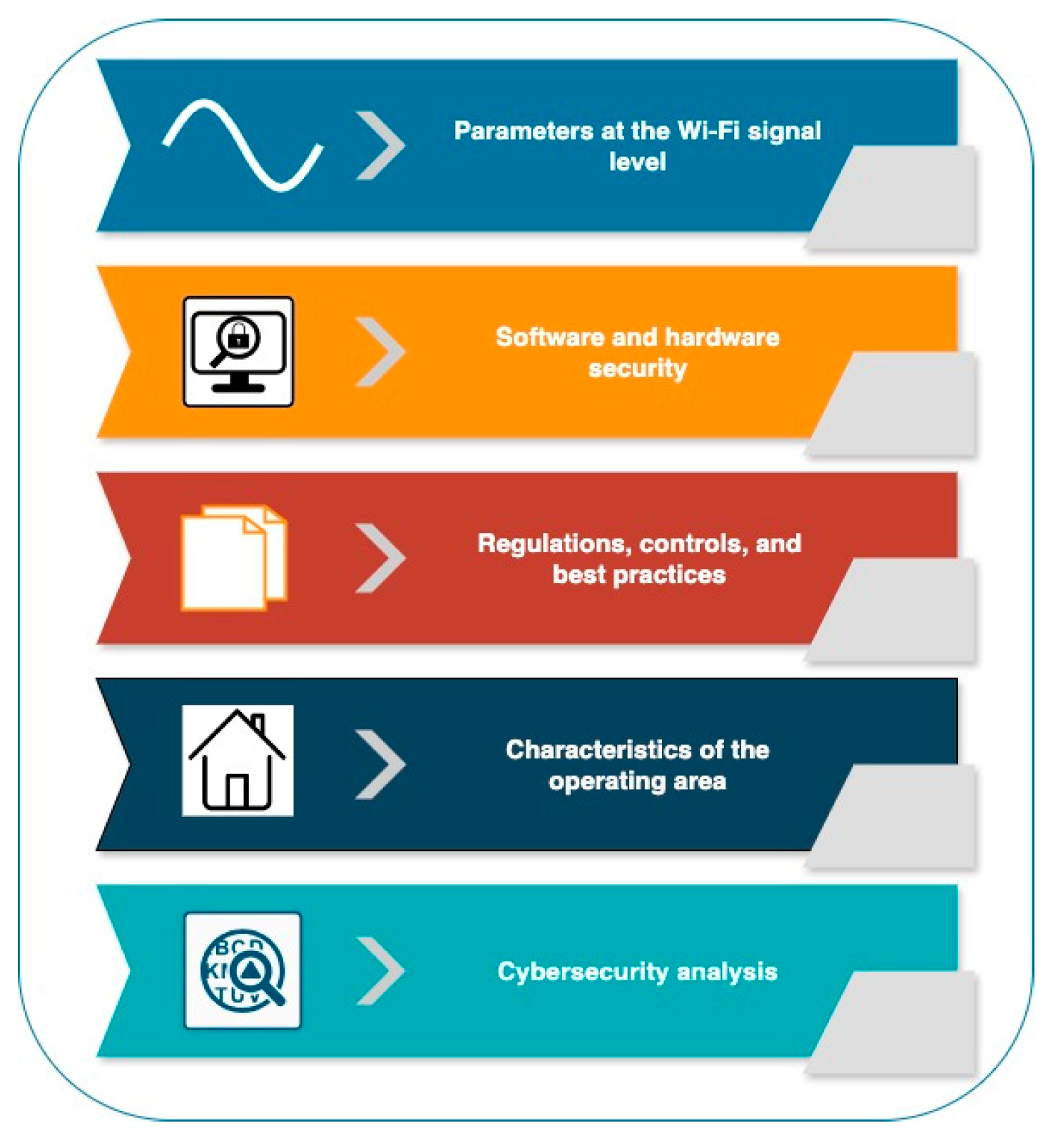
4. Conceptual and Methodological Framework: Evaluating and Designing Wireless Networks Wi-Fi Guide
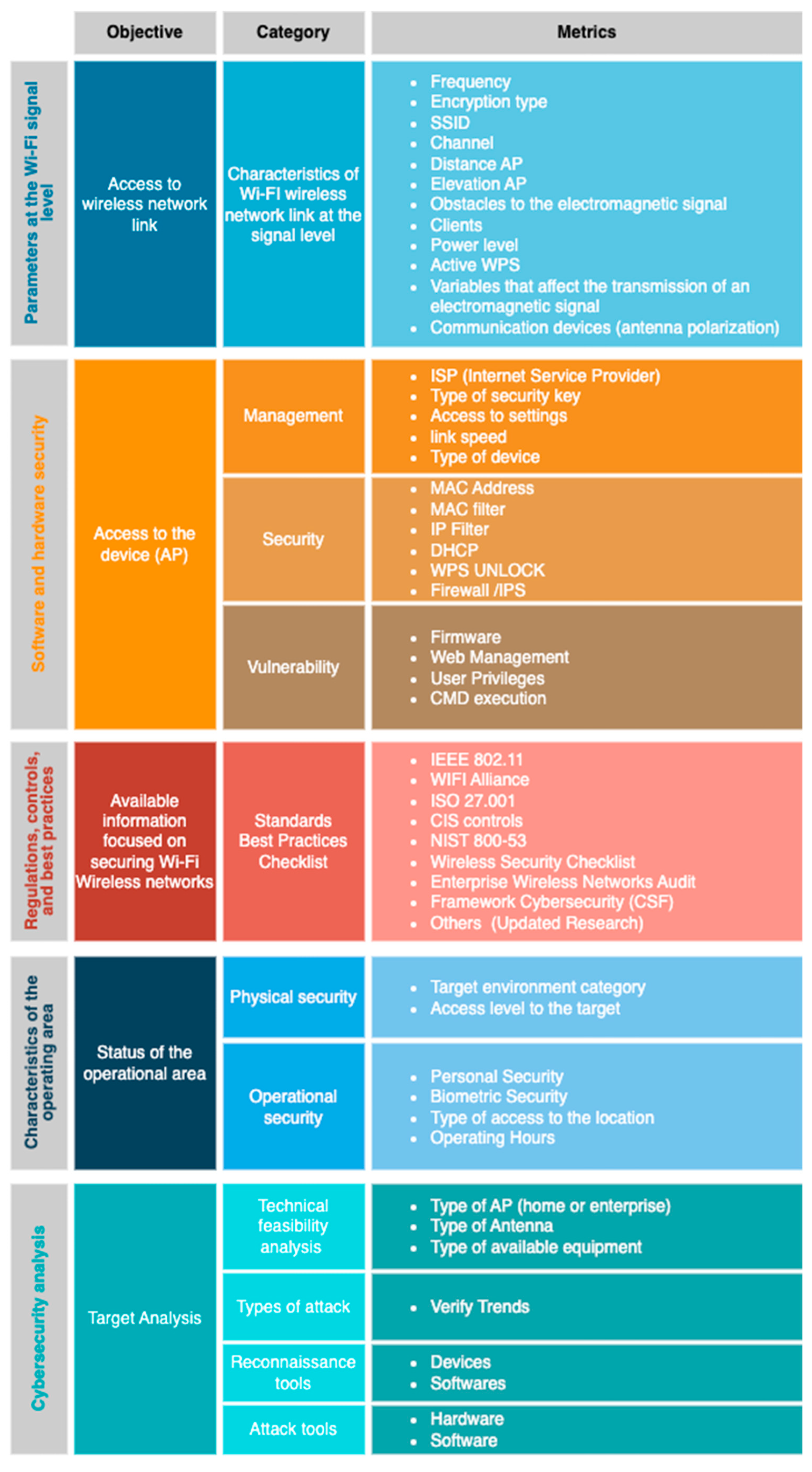
4.1. Wi-Fi Signal Level Parameters
4.1.1. Access to Wireless Network Link
- Frequency:
- 2.4 GHz: This frequency offers greater range due to its ability to penetrate obstacles, but it has lower speeds and may be more congested due to sharing with other devices such as Bluetooth and microwaves.
- 5 GHz: Provides higher speeds and less interference thanks to its multiple channels, although its range is more limited due to its microwave characteristics.
- 6 GHz: Introduced with the arrival of Wi-Fi 6E, this band offers even greater capacity, higher speeds, and less interference, making it ideal for environments with multiple connected devices.
- Encryption type:
- WEP (Wired Equivalent Privacy) is the oldest and least secure standard. Although it was widely used in the past, it is now considered obsolete due to vulnerabilities that allow an attacker to crack it quickly. WEP is not recommended.
- WPA (Wi-Fi Protected Access) is an improvement over WEP, offering a higher level of security. WPA uses the TKIP (Temporal Key Integrity Protocol) to encrypt data. While more secure than WEP, it is still vulnerable to specific attacks.
- WPA2 (Wi-Fi Protected Access 2): The enhanced version of WPA, and for many years, the de facto standard for Wi-Fi security. It uses the AES (Advanced Encryption Standard) encryption protocol, which is much stronger than the TKIP used in WPA. WPA2 remains the recommended standard to this day.
- WPA3 (Wi-Fi Protected Access 3): WPA's latest and most secure version. It introduces improvements in authentication and protection against brute-force attacks. It also provides better security for public networks (such as open networks) and more effectively protects data during transmission.
- SSID:
- Channel:
- Distance AP:
- Elevation AP:
- Obstacles to the electromagnetic signal:
- Clients:
- Power level:
- Active WPS:
- Variables the affect the transmission of an electromagnetic signal:
- Communication devices (antenna polarization)
4.2. Software and Hardware Security
- ISP (Internet Service Provider):
- Type of security key:
- Access to settings:
- Guest access, which provides limited Internet-only access without compromising the internal network.
- Regular user access, which grants standard permissions for browsing and using services within the network.
- Administrator access, reserved for configuring and managing the AP, including modifying security settings, networks, and shared resources.
- Network control access, used in business environments to manage traffic, quality of service (QoS), and resource distribution; and
- Monitoring access, which allows for network performance monitoring without altering its configuration.
- Link speed:
- Type of device:
- MAC Address:
- MAC Filter:
- IP Filter
- DHCP
- WPS UNLOCK
- Firewall /IPS
- Firmware
- Web Management
- User Privileges
- CMD execution
4.3. Regulation, Controls, and Best Practices
- Standards
- Best Practices
- Checklist
- IEEE 802.11
- WIFI Alliance
- ISO 27.001
- CIS controls
- NIST 800-53
- Wireless Security Checklist
- Enterprise Wireless Networks Audit
- Framework Cybersecurity (CSF)
- Others (Updated Research)
4.4. Operating Area Characteristics
- Status of the operational area
- Target environment category
- Access level to the target
- Personal Security
- Biometric Security
- Type of access to the location
- Operating Hours
4.5. Cybersecurity Analysis.
- Technical feasibility analysis
- Type of AP (home or enterprise)
- Type of Antenna
- Type of available equipment
- Verify Trends
- Devices
- Software
- Hardware
- Software
5. Conclusions
References
- Yang, H.-C.; Alouini, M.-S. A. Advanced Wireless Transmission Technologies: Analysis and Design. 1ª edición ed. Cambridge CB2 8BS United Kingdom, 2020. [Google Scholar]
- WiFi Alliance. Available online: https://www.wi-fi.org/who-we-are (accessed on 10 Nov 2024).
- Van Puyvelde, D.; Brantly, A. Cybersecurity. 1ª edición ed. Medford, USA: Polity Press, 2019.
- Goralski, W. The Illustrated Network. 2ª edición ed. United States: Morgan Kaufmann, 2017.
- IEEE. Available online: https://standards.ieee.org/ (accessed on 10 Nov 2024).
- ISO. Available online: https://www.iso.org/about-us.html (accessed on 10 Nov 2024).
- NIST. Available online: https://www.nist.gov/ (accessed on 10 Nov 2024).
- CIS. Available online: https://www.cisecurity.org/about-us/ (accessed on 10 Nov 2024).
- De Haes, S.; Van Grembergen, W. Enterprise Governance of Information Technology. 2ª edición ed. Belgium: Springer, 2015.
- Barria, C. , Cordero, D., Galeazzi, L.; Acuña, A., Proposal of a Multi-standard Model for Measuring Maturity Business Levels with Reference to Information Security Standards and Controls. Intelligent Methods in Computing, Communications and Control, 1243(978-3-030-53650-3), 2020, pp. 121-132.
- Karnel, E. Hacking: 4 Books in 1- Hacking for Beginners, Hacker Basic Security, Networking Hacking, Kali Linux for Hackers. 1ª edición ed. United States: Independently Published, 2019.
- Valchanov, H., Edikyan, J. & Aleksieva, V. An Empirical Study of Wireless Security in City Environment. In Proceedings of ACM Balkan conference in Informatics (BCI’19), 9(11), 2019, pp. 1-4.
- Osterhage, W. Wireless Network Security. 2ª edición ed. Frankfurt, Germany: CRC Press, 2018.
- Alan, C. & Steve, W. IT Governance An international guide to data security and ISO27001/ ISO27002. 6ª edición ed. London: KoganPage, 2015.
- Ávalos, L.G. , Huidobro, C.B., Hurtado, J.A. A Review of the Security Information Controls in Wireless Networks Wi-Fi. In: Mata-Rivera, M.F., Zagal-Flores, R., Barria-Huidobro, C. (eds) Telematics and Computing. WITCOM 2020. Communications in Computer and Information Science, vol 1280. Springer, Cham (2020). [CrossRef]
- Hurtado, J. Metodología de la Investigación: Guía para una comprensión holística de la ciencia. 4ª edición ed. Caracas: Quirón Ediciones, 2010.
- Hurtado, J. Cómo formular objetivos de investigación. 3ª edición ed. Caracas: Sypal, 2012.
- Galeazzi, L. , Barría, C., Hurtado, J. (2021). Conceptual Model of Security Variables in Wi-Fi Wireless Networks: Review. In: Latifi, S. (eds) ITNG18th International Conference on Information Technology-New Generations. Advances in Intelligent Systems and Computing, vol 1346. Springer, Cham, 2021. [CrossRef]
- Galeazzi, L. , Garrido, C., & Barría, C. (2022, October). Validation of Security Variables for Audits in Wireless Wi-Fi Networks. In International Congress of Telematics and Computing (pp. 422-433). Springer vol 1659, Cham. [CrossRef]
- PlayGoogle. Available online: https://play.google.com/store/apps/details?id=abdelrahman.wifianalyzerpro&hl=es_CL (accessed on 10 Nov 2024).
- Wigle. Available online: https://wigle.net/ (accessed on 10 Nov 2024).
- Astudillo, K. Wireless Hacking 101. Babelcube Inc., 2017.
- El Fiky, A. Wireless Penetration Testing: Up and Running. BPB Online, 2023.
- Google. Available online: https://support.google.com/earth/answer/7365595?hl=en&co=GENIE.Platform%3DAndroid (accessed on 10 Nov 2024).
- Botwrite, R. Wireless Exploits And Countermeasures: Kali Linux Nethunter, Aircrack-NG, Kismet, And Wireshark, Pastor Publishing Ltd, 2024.
- Meteored. Available online: https://www.meteored.cl/tiempo-en_Santiago+de+Chile-America+Sur-Chile-Region+Metropolitana+de+Santiago-SCEL-sactual-18578.html (accessed on 10 Nov 2024).
- Meteored. Available online: https://www.meteored.cl/tiempo-en_Santiago+de+Chile-America+Sur-Chile-Region+Metropolitana+de+Santiago-SCEL-sactual-18578.html (accessed on 10 Nov 2024).

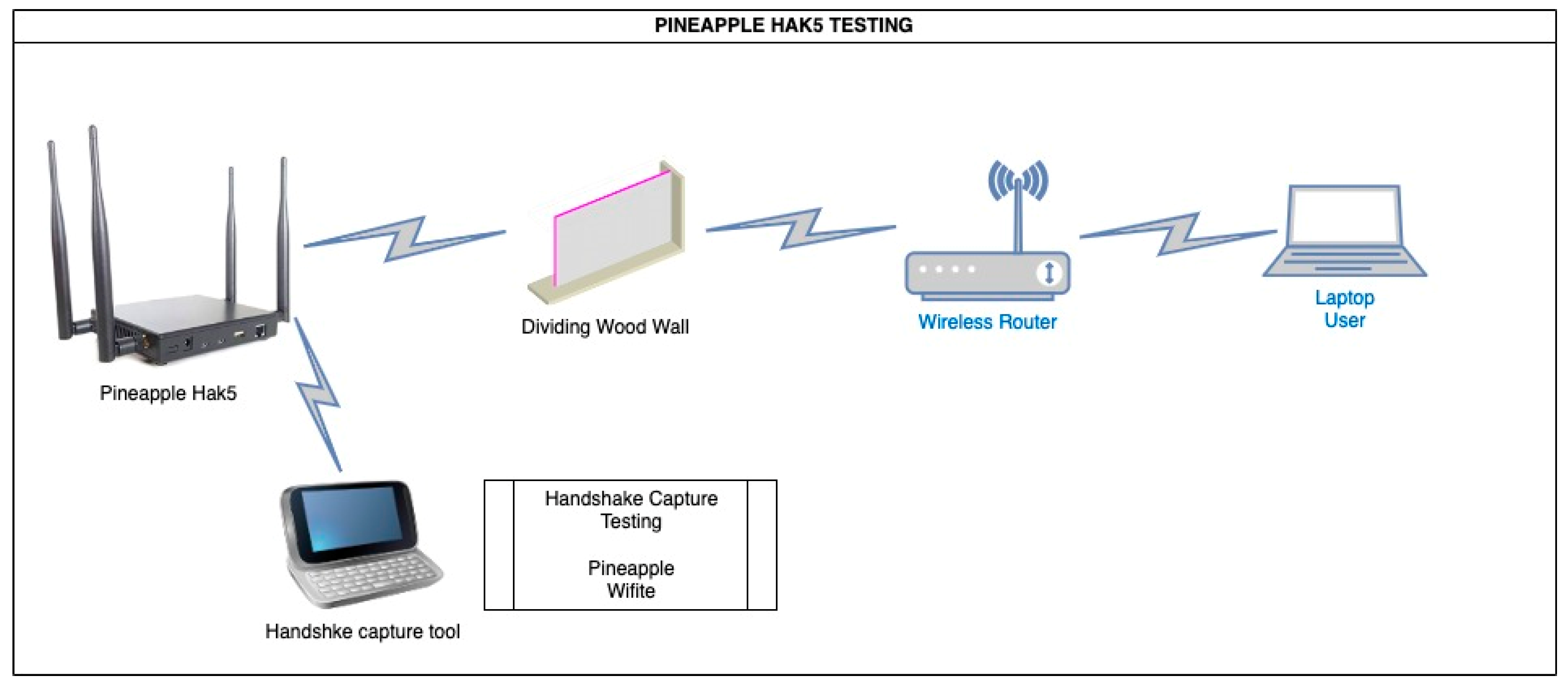
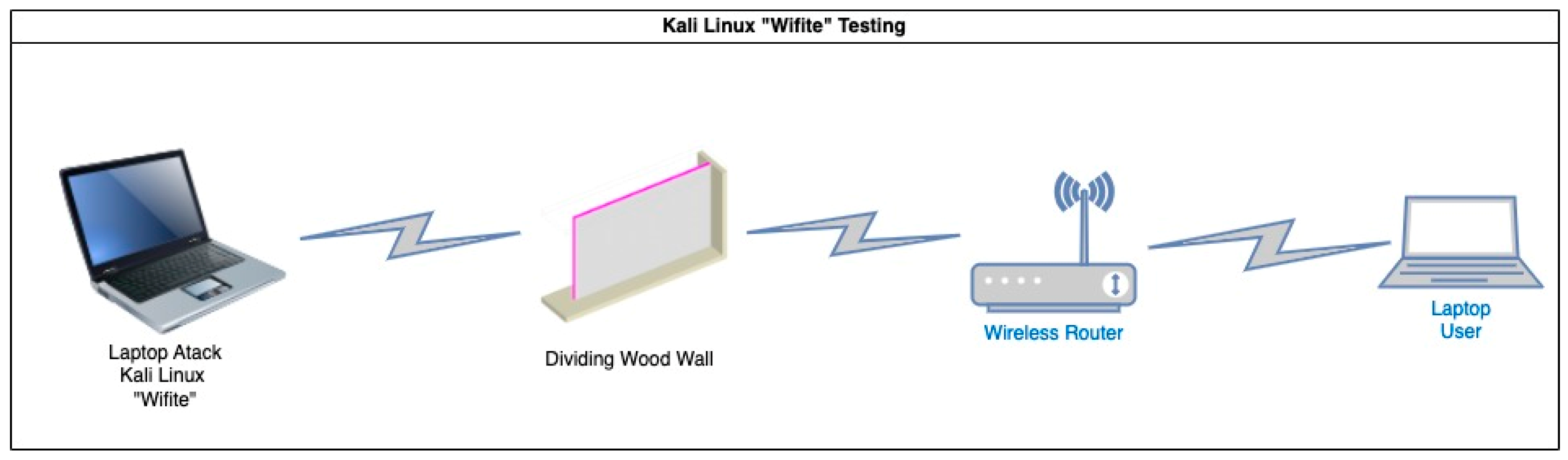
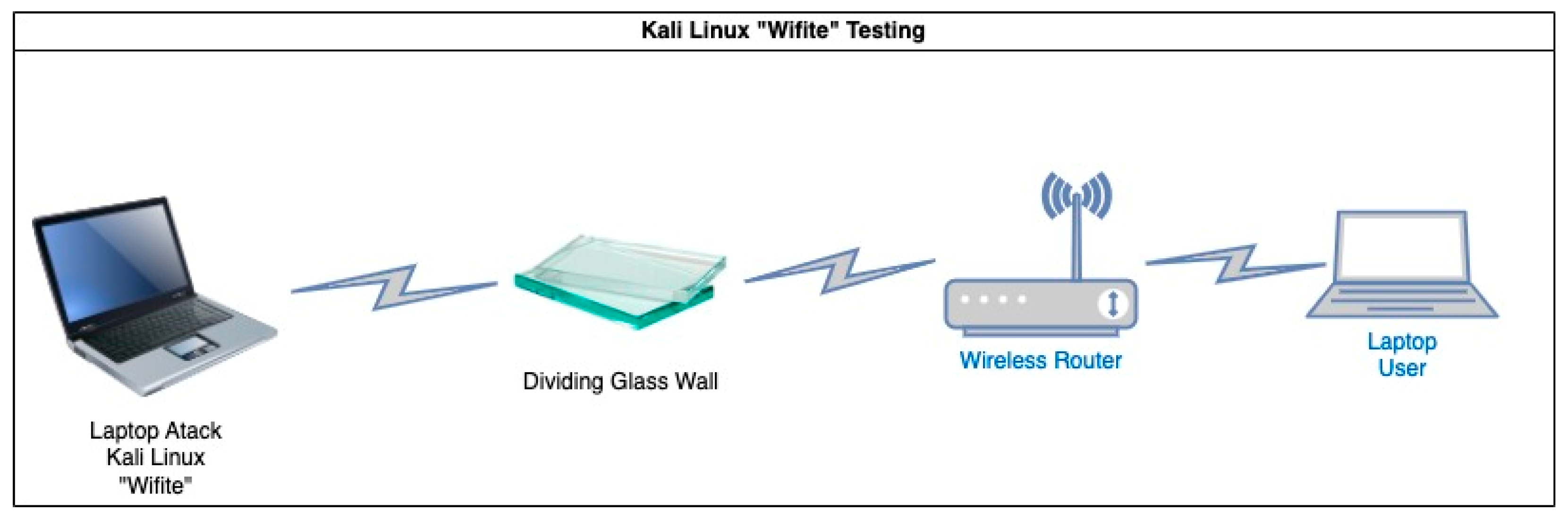
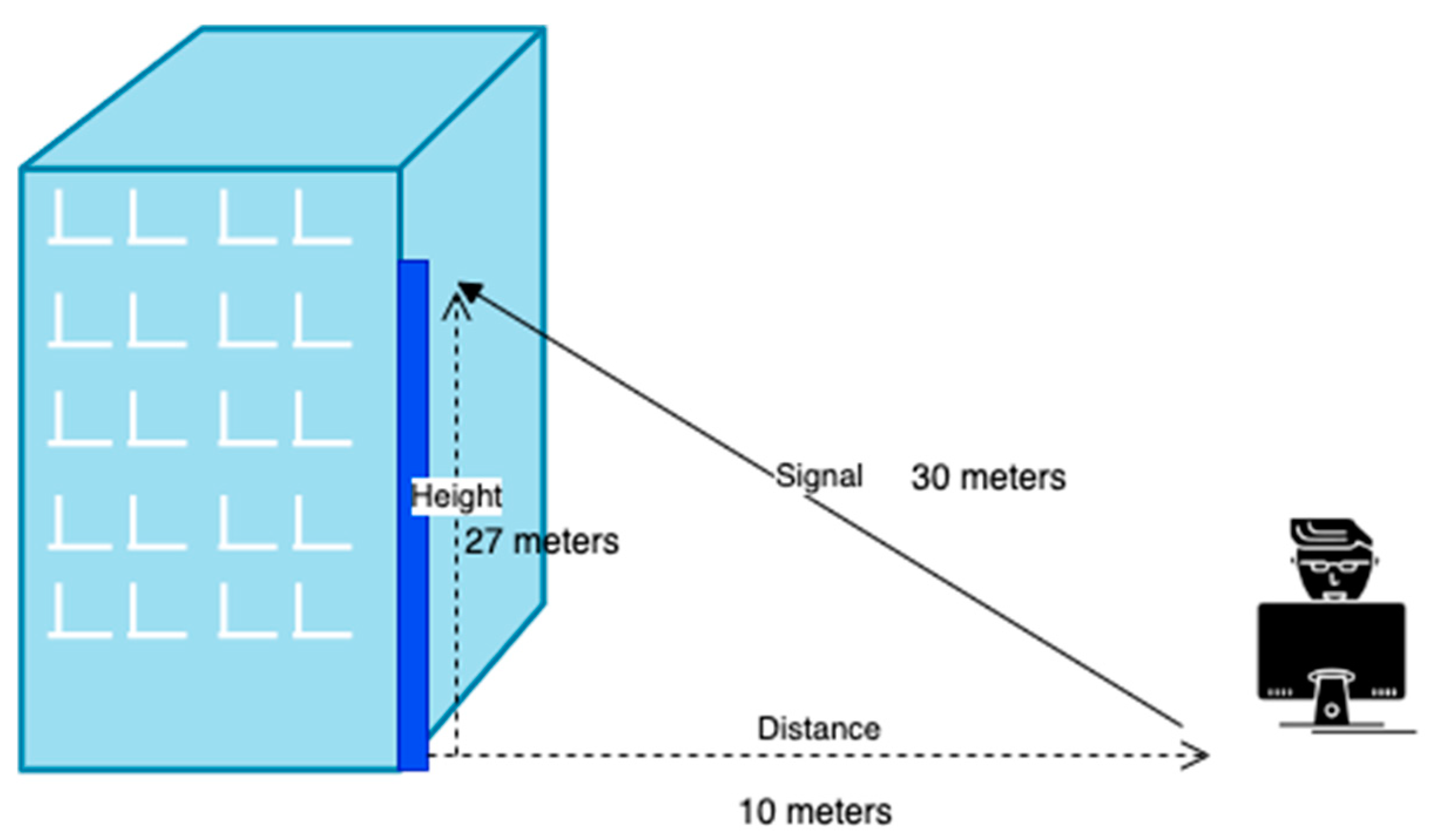
| Phase | Category | Parameters |
| Recognition | Data link connection | Encryption |
| Frequency | ||
| SSID | ||
| Channel | ||
| BSSID | ||
| Location (Latitude – Longitude) | ||
| Status | ||
| Speed | ||
| Signal strength | ||
| Security | ||
| IP address | ||
| Mac address (Vendor) | ||
| Signal meter | ||
| WPS | ||
| Connected AP clients |
| Phase | Category | Parameters |
| Recognition | Environmental variables | Distance |
| Height | ||
| Types of building materials | ||
| Signal obstacles |
| Device | Brand | Model | Category |
| Router | Cisco 2940 | -.- | -.- |
| Wireless Router | Linksys | WRT610N | Home |
| Wireless Router | TP-Link | TL-WR802N | Home |
| Wireless Router | Ruckus | R550 | Enterprise |
| Wireless Router | Aruba | IAP-330 | Enterprise |
| Notebook | MacBook Pro 2018 15" | -.- | -.- |
| Notebook | ASUS GV301q | -.- | -.- |
| Computer | Raspberry PI3 | -.- | -.- |
| Notebook | MacBook Pro 2017 13" | -.- | -.- |
| Notebook | Surface Pro 6 | -.- | -.- |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





