Submitted:
23 February 2025
Posted:
24 February 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
Key Challenges
Scope of the Paper
-
Graph Neural Networks (GNNs) for Security-aware Anomaly Detection:
- Facilitates circuit-level inconsistencies arising from Trojan insertions and stealthily modified routing.
-
AI-enhanced Design Rule Checking or Rule Closing Procedure (AI-DRC):
- This design begins with hand-picking matters (probabilistic) that can lead to security violations.
- Moves beyond judgment on a static set of rules, looking ahead to whether security violations result from their application.
-
Security-aware Routing Optimization:
- Under the framework of reinforcement learning-based dynamic path selection.
- Minimizes adjacent noise and parasitic power.
- Reduces the switching speed of crosstalk and number rays by prioritizing EM dissipation levels.
- This improves security vulnerability.
-
Lagrange Multiplier-based Constrained Optimization:
- Employed to make security constraints uniformly enforced mathematically.
- Ensures scalability and achieves efficiency.
-
Softmax Basis for Trojan Detection:
- Security scores are propagated through GNN node embeddings on an IC layout graph.
- Nodes are classified as benign or compromised.
Significance of Study
2. Methodology and Implementation
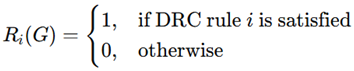
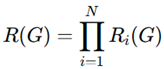
- V consists of nodes such as gates, vias, and interconnections.
- E is a collection of edges corresponding to the metal layers and routing interconnections on an integrated circuit.
- L indicates layer-specific information like diffusion and polysilicon.
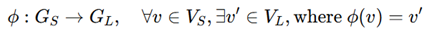
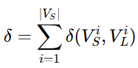
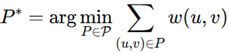
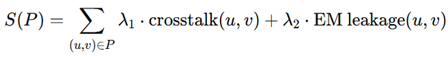

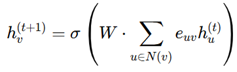
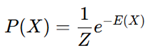
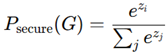
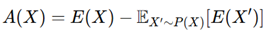
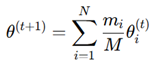
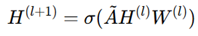
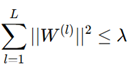
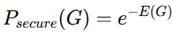
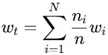
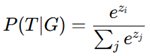
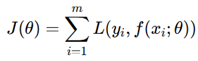

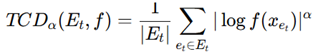
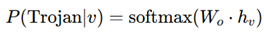

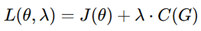
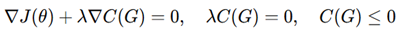
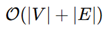
3. Evaluation based on Aggregator, Combination, and Readout Functions

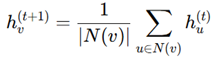
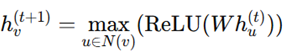
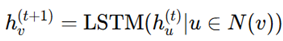
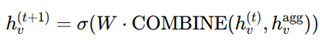
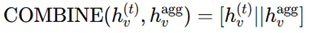
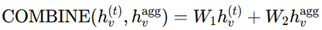
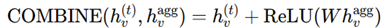
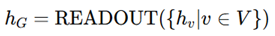
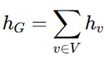
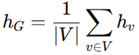
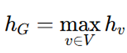
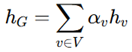
4. Comparison with Existing models
| Methodology | Strengths | Limitations | How Our Model Improves |
| Golden Reference-Based Verification | High accuracy for known threats | Requires trusting chips, and outsourced design cannot be accommodated | Our model eliminates the dependency on golden reference by employing AI-based anomaly detection. |
| Machine Learning (ML) for Security Verification | Adaptable to emerging threats | Fields require large amounts of labeled data. | Our GNN-based framework uses graph structure learning to achieve larger generalization |
| SAT-Based Trojan Detection | Effective for combinational Trojans | Fails on HTs (both sequential and deep). | Our approach uses deep learning to capture structural and behavioral anomalies. |
| Side-Channel Analysis for Hardware Security | Detects Trojans via power/EM signatures | Minor errors in the data or disturbances caused by environmental constraints | To mitigate side-channel hazards, our framework integrates power/routing optimization based on AI. |
5. Future Directions
| EDA Tool | Potential Integration |
| Cadence Innovus | AI-based security-aware routing optimization |
| Synopsys IC Compiler | AI-driven DRC and LVS validation |
| Siemens Calibre | Graph-based hardware Trojan detection |
- Computational Overhead: AI models require high-performance GPUs for training, yet one can use FPGAs to implement them in a real-time security monitoring application.
- Compatibility with Commercial Foundries: A federated learning approach ensures one can train AI models across different IC manufacturers while keeping the design confidential.
6. Conclusions
References
- Faezi, S. , Yasaei, R., & Al Faruque, M. A. HTnet: Transfer Learning for Golden Chip-Free Hardware Trojan Detection.
- Yasaei, R. , Yu, S.-Y., & Al Faruque, M. A. GNN4TJ: Graph Neural Networks for Hardware Trojan Detection at Register Transfer Level.
- Hasegawa, K. , Yanagisawa, M., & Togawa, N. Trojan-feature Extraction at Gate-level Netlists and Its Application to Hardware-Trojan Detection Using Random Forest Classifier.
- Lashen, H. , Alrahis, L., Knechtel, J., & Sinanoglu, O. TrojanSAINT: Gate-Level Netlist Sampling-Based Inductive Learning for Hardware Trojan Detection.
- Dey, S. , Park, J., Pundir, N., Saha, D., Shuvo, A. M., Mehta, D., Asadi, N., Rahman, F., Farahmandi, F., & Tehranipoor, M. Secure Physical Design.
- Yasaei, R. , Chen, L., Yu, S.-Y., & Al Faruque, M. A. Hardware Trojan Detection Using Graph Neural Networks.
- Kiruthika, R. , Saranraj, N., Chandru, K., Geethapriya, N., Kiruthika, S. V., & Raja, S. Exploring the Frontiers: Innovations in Semiconductor Technology and AI-Driven SoC Design.
- Alrahis, L. , Patnaik, S., Hanif, M. A., Shafique, M., & Sinanoglu, O. UNTANGLE: Unlocking Routing and Logic Obfuscation Using Graph Neural Networks-based Link Prediction.
- Alrahis, L. , Knechtel, J., Klemme, F., Amrouch, H., & Sinanoglu, O. GNN4REL: Graph Neural Networks for Predicting Circuit Reliability Degradation.
- Parikh, R. , & Parikh, K. Survey on Hardware Security: PUFs, Trojans, and Side-Channel Attacks. Preprints.org.
- Yasaei, R. , Faezi, S., & Al Faruque, M. A. Golden Reference-Free Hardware Trojan Localization Using Graph Convolutional Network.
- Alrahis, L. , Sengupta, A., Knechtel, J., Patnaik, S., Saleh, H., Mohammad, B., Al-Qutayri, M., & Sinanoglu, O. GNN-RE: Graph Neural Networks for Reverse Engineering of Gate-Level Netlists.
- Yao, F. , Fang, H., Doroslovački, M., & Venkataramani, G. COTSknight: Practical Defense against Cache Timing Channel Attacks using Cache Monitoring and Partitioning Technologies.
- Hasegawa, K. , Hidano, S., Nozawa, K., Kiyomoto, S., & Togawa, N. R-HTDetector: Robust Hardware-Trojan Detection Based on Adversarial Training.
- Klambauer, G. , Unterthiner, T., Mayr, A., & Hochreiter, S. Self-Normalizing Neural Networks.
- He, J. , Liu, Y., Yuan, Y., Hu, K., Xia, X., & Zhao, Y. Golden Chip-Free Trojan Detection Leveraging Electromagnetic Side-Channel Fingerprinting.
- Parikh, R. , & Parikh, K. Survey on Hardware Security: PUFs, Trojans, and Side-Channel Attacks. Volume 15, Issue 2, February 2025, Page No. 30-37. 20 February.
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




